Data Security And Protection
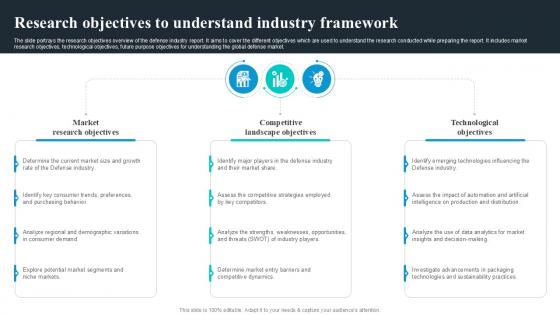
Research Objectives To Understand Global Security Industry PPT Template IR SS V
The slide highlights the SWOT analysis of Defense industry. The main purpose of this side is to understand and measure the comprehensive assessment of defense market. It further helps in mitigating the potential risks. Key components include strengths, weakness opportunities and threats. The slide portrays the research objectives overview of the defense industry report. It aims to cover the different objectives which are used to understand the research conducted while preparing the report. It includes market research objectives, technological objectives, future purpose objectives for understanding the global defense market. Are you searching for a Research Objectives To Understand Global Security Industry PPT Template IR SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Research Objectives To Understand Global Security Industry PPT Template IR SS V from Slidegeeks today. The slide highlights the SWOT analysis of Defense industry. The main purpose of this side is to understand and measure the comprehensive assessment of defense market. It further helps in mitigating the potential risks. Key components include strengths, weakness opportunities and threats.

Security Management Plan Steps In Detail Training And Building Role Competencies Portrait PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. This is a security management plan steps in detail training and building role competencies portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management system, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Hardware And Software Update In Company Ppt Outline Graphics Pictures PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a information security hardware and software update in company ppt outline graphics pictures pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like networks, technology, devices, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Methods To Develop Measures And Ways To Mitigate Security Monitoring Challenges Background PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver an awe inspiring pitch with this creative methods to develop measures and ways to mitigate security monitoring challenges background pdf bundle. Topics like security monitoring challenges, employee management, malware attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
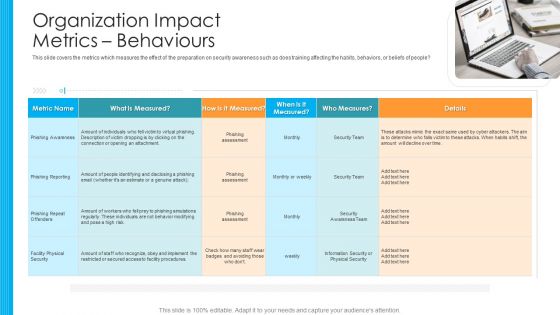
Organization Impact Metrics Behaviours Hacking Prevention Awareness Training For IT Security Designs PDF
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people. This is a organization impact metrics behaviours hacking prevention awareness training for it security designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like phishing awareness, phishing reporting, phishing repeat offenders, facility physical security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
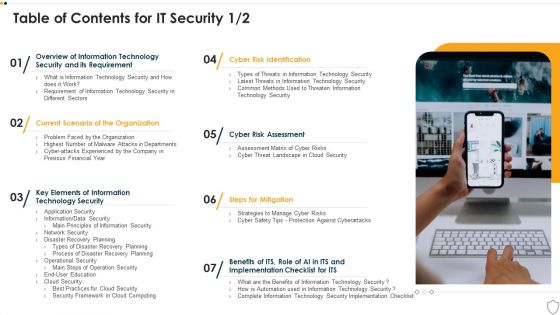
Table Of Contents For IT Security Cyber Ppt Inspiration Introduction PDF
This is a table of contents for it security cyber ppt inspiration introduction pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology security, implementation, organization, cyber risk assessment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Smart Home Security Solutions Company Profile Awards And Accolades Icons PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year. Presenting Smart Home Security Solutions Company Profile Awards And Accolades Icons PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Digital Trends Best, Smart Home Security, Systems Consumer Technology, Association Consumer Technology, Association Security Today. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Table Of Contents For IT Security IT Cont Tracking Ppt Infographics Graphics Example PDF
Presenting table of contents for it security it cont tracking ppt infographics graphics example pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cyber security, implementation, communication, administrative, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Identifying Goals And Objectives Download PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, security, management, organizational, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
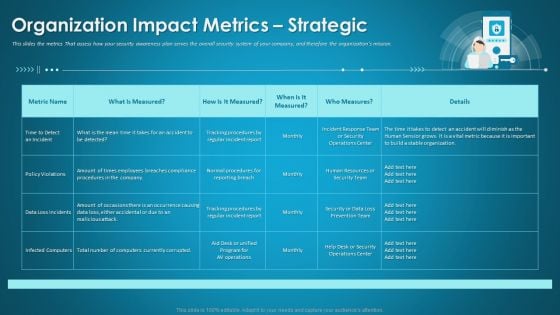
Organizational Network Security Awareness Staff Learning Organization Impact Metrics Strategic Structure PDF
This slides the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning organization impact metrics strategic structure pdf. Use them to share invaluable insights on human resources, security operations, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail System Maintenance And Monitoring Portrait PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. System Maintenance and Monitoring. This is a security management plan steps in detail system maintenance and monitoring portrait pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail system maintenance and monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Types Of Access Control In Application Security Testing Ppt Powerpoint Topics
This slide outlines the different types of access control safeguards in application security which include Role-based Access Control RBAC, Access Control Lists, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Types Of Access Control In Application Security Testing Ppt Powerpoint Topics to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Types Of Access Control In Application Security Testing Ppt Powerpoint Topics. This slide outlines the different types of access control safeguards in application security which include Role-based Access Control RBAC, Access Control Lists, etc.
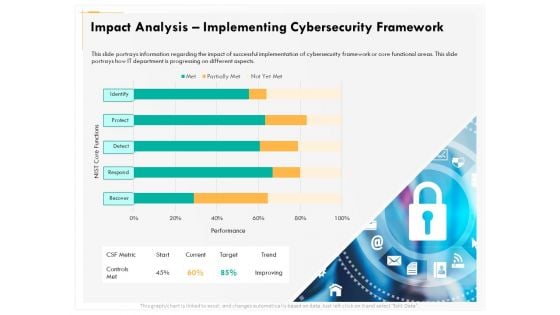
Computer Security Incident Handling Impact Analysis Implementing Cybersecurity Framework Designs PDF
Presenting this set of slides with name computer security incident handling impact analysis implementing cybersecurity framework designs pdf. The topics discussed in these slides are recover, detect, respond, protect, identify. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Key Security Controls To Be Addressed In The Program Ppt Professional Vector PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. This is a key security controls to be addressed in the program ppt professional vector pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like key security controls to be addressed in the program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategies To Mitigate Cyber Security Risks Determining Firm Current Capabilities Ppt Inspiration Smartart PDF
Presenting this set of slides with name strategies to mitigate cyber security risks determining firm current capabilities ppt inspiration smartart pdf. The topics discussed in these slides are identify, protect, detect, response, recovery, key enablers, minimum standard, evolving strength. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
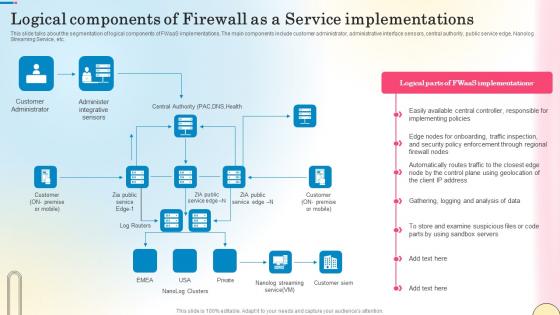
Logical Components Of Firewall As A Service Network Security Designs Pdf
This slide talks about the segmentation of logical components of FWaaS implementations. The main components include customer administrator, administrative interface sensors, central authority, public service edge, Nanolog Streaming Service, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Logical Components Of Firewall As A Service Network Security Designs Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Logical Components Of Firewall As A Service Network Security Designs Pdf. This slide talks about the segmentation of logical components of FWaaS implementations. The main components include customer administrator, administrative interface sensors, central authority, public service edge, Nanolog Streaming Service, etc.
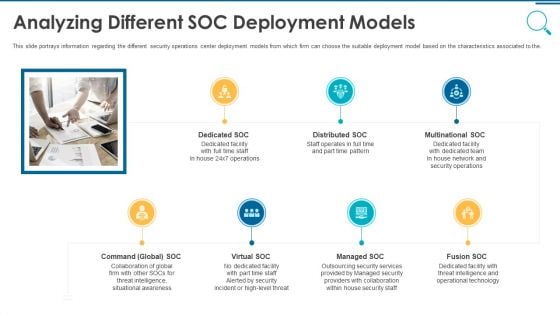
Information And Technology Security Operations Analyzing Different SOC Deployment Models Rules PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a information and technology security operations analyzing different soc deployment models rules pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Iot Security Smart Home Vector Icon Ppt PowerPoint Presentation Diagram Templates PDF
Presenting iot security smart home vector icon ppt powerpoint presentation diagram templates pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including iot security smart home vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cloud Computing Security Operations Vector Icon Ppt PowerPoint Presentation Outline Influencers PDF
Presenting cloud computing security operations vector icon ppt powerpoint presentation outline influencers pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cloud computing security operations vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Vector Showing Private Cloud Security Icon Ppt PowerPoint Presentation File Design Ideas PDF
Presenting vector showing private cloud security icon ppt powerpoint presentation file design ideas pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including vector showing private cloud security icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Digital Investigation For Cyber Security Vector Icon Ppt PowerPoint Presentation File Layout Ideas PDF
Presenting digital investigation for cyber security vector icon ppt powerpoint presentation file layout ideas pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including digital investigation for cyber security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Digital Investigation Icon For Cyber Security Ppt PowerPoint Presentation Gallery Graphic Images PDF
Presenting digital investigation icon for cyber security ppt powerpoint presentation gallery graphic images pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including digital investigation icon for cyber security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Person Holding Smart Phone With Security Shield Vector Icon Ppt Infographics Format PDF
Presenting person holding smart phone with security shield vector icon ppt infographics format pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including person holding smart phone with security shield vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Security Operations Center Icon For Monitoring Functions Ppt Gallery Professional PDF
Presenting cyber security operations center icon for monitoring functions ppt gallery professional pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cyber security operations center icon for monitoring functions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Firewall Security Solutions Vector Illustration Ppt PowerPoint Presentation Gallery Professional PDF
Presenting business firewall security solutions vector illustration ppt powerpoint presentation gallery professional pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including business firewall security solutions vector illustration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Face Recognition Security App On Computer Vector Icon Ppt PowerPoint Presentation Gallery Rules PDF
Presenting face recognition security app on computer vector icon ppt powerpoint presentation gallery rules pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including face recognition security app on computer vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Managing Cyber Security Incident Management Icon Ppt Infographics Design Templates PDF
Presenting Managing Cyber Security Incident Management Icon Ppt Infographics Design Templates PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Managing Cyber Security, Incident Management, Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon Of Digital Transformation To Boost Financial Institution Industry Security Graphics PDF
Presenting Icon Of Digital Transformation To Boost Financial Institution Industry Security Graphics PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Digital Transformation, Boost Financial Institution, Industry Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Management Plan Steps In Detail Risk Assessment And Analysis Summary PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Risk Assessment and Analysis. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail risk assessment and analysis summary pdf. Use them to share invaluable insights on security management plan steps in detail risk assessment and analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
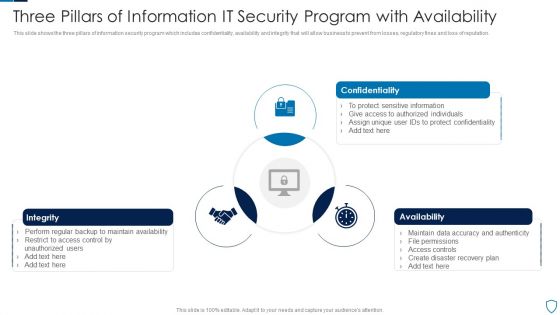
Three Pillars Of Information IT Security Program With Availability Summary PDF
This slide shows the three pillars of information security program which includes confidentiality, availability and integrity that will allow business to prevent from losses, regulatory fines and loss of reputation.Presenting Three Pillars Of Information IT Security Program With Availability Summary PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Confidentiality, Integrity, Availability This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Building Trust With IoT Security And Privacy Measures IoT CD V
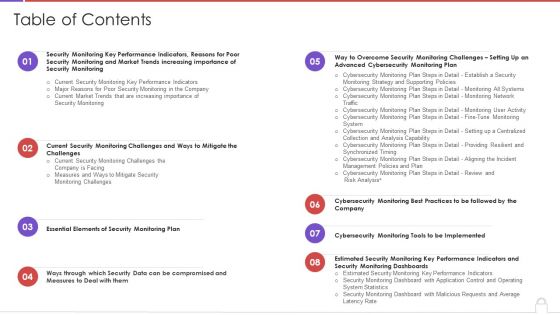
Table Of Contents Methods To Develop Advanced It Security Monitoring Plan Structure PDF
Deliver and pitch your topic in the best possible manner with this table of contents methods to develop advanced it security monitoring plan structure pdf. Use them to share invaluable insights on security monitoring, key performance indicators, security monitoring plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Automation Tools Integration Table Of Contents Ppt Ideas Graphic Tips PDF
This is a IT Security Automation Tools Integration Table Of Contents Ppt Ideas Graphic Tips PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ineffective Security System, Security Automation, Architecture And Importance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
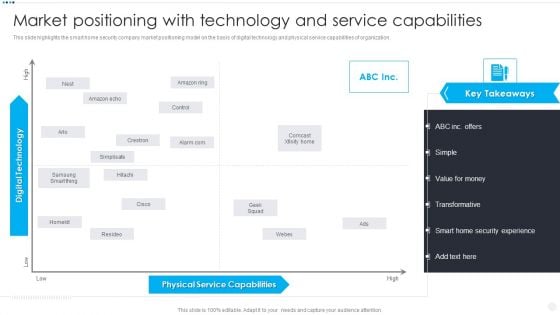
Smart Home Security Solutions Company Profile Market Positioning With Technology Information PDF
This slide highlights the smart home security company market positioning model on the basis of digital technology and physical service capabilities of organization. This is a Smart Home Security Solutions Company Profile Market Positioning With Technology Information PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Physical Service Capabilities, Digital Technology High. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Components To Enhance Processes Career Opportunities In Cybersecurity Profession Sample PDF
This slide depicts the career opportunities in cybersecurity, including various job roles such as chief information security officer, chief security office, security engineers, architects, analysts and penetration testers. Create an editable Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
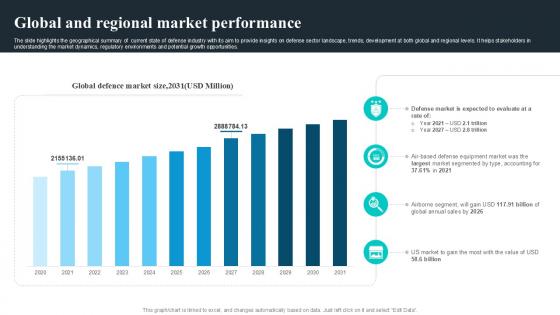
Global And Regional Market Performance Global Security Industry PPT Slide IR SS V
The slide highlights the geographical summary of current state of defense industry with its aim to provide insights on defense sector landscape, trends, development at both global and regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities. If you are looking for a format to display your unique thoughts, then the professionally designed Global And Regional Market Performance Global Security Industry PPT Slide IR SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global And Regional Market Performance Global Security Industry PPT Slide IR SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The slide highlights the geographical summary of current state of defense industry with its aim to provide insights on defense sector landscape, trends, development at both global and regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities.

Security Best Practices For Infrastructure IAC Tools For Performance Analysis PPT Slide
This slide discusses the best security practices for infrastructure as code. The purpose of this slide is to highlight the best practices such as enforcing the passwords, installing the firewall, checking for updates, using content fillers, etc. Find highly impressive Security Best Practices For Infrastructure IAC Tools For Performance Analysis PPT Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Best Practices For Infrastructure IAC Tools For Performance Analysis PPT Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide discusses the best security practices for infrastructure as code. The purpose of this slide is to highlight the best practices such as enforcing the passwords, installing the firewall, checking for updates, using content fillers, etc.
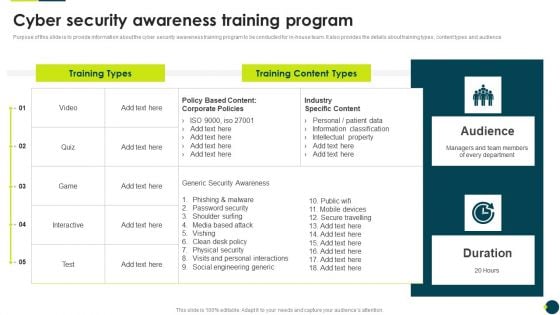
IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF bundle. Topics like Phishing Malware, Password Security, Shoulder Surfing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
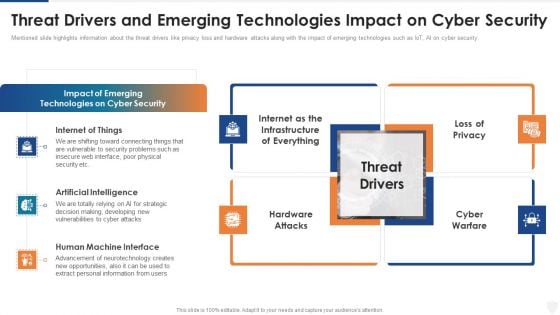
Threat Drivers And Emerging Technologies Impact On Cyber Security Ppt Slides Graphic Images PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. This is a threat drivers and emerging technologies impact on cyber security ppt slides graphic images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, developing, strategic, opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
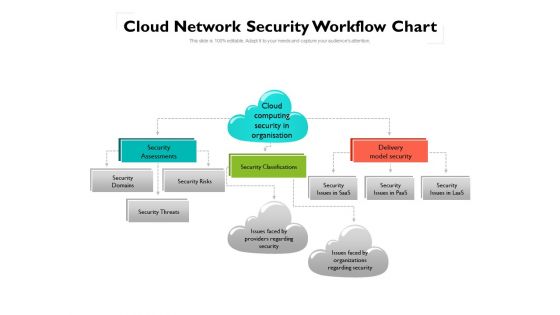
Cloud Network Security Workflow Chart Ppt PowerPoint Presentation Gallery Ideas PDF
This is a cloud network security workflow chart ppt powerpoint presentation gallery ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, organizations, domains. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF
This slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Get a simple yet stunning designed Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
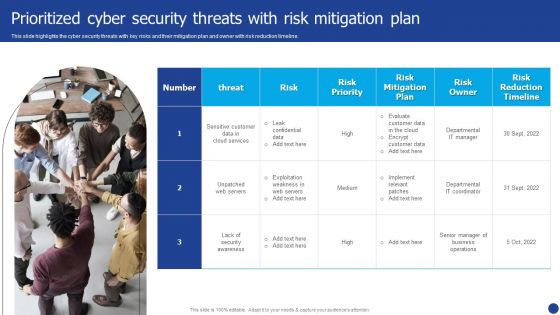
Information Technology Threat Mitigation Methods Prioritized Cyber Security Threats With Risk Mitigation Plan Sample PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. This is a Information Technology Threat Mitigation Methods Prioritized Cyber Security Threats With Risk Mitigation Plan Sample PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Owner, Risk Priority, Risk Mitigation Plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
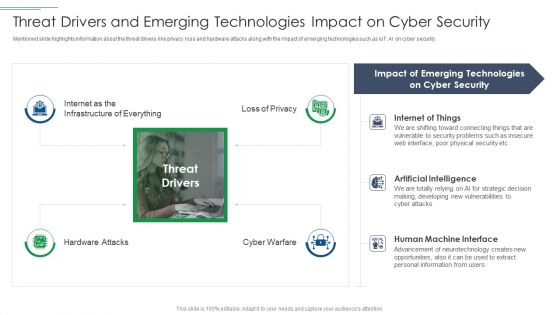
IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF
Presenting IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Cyber Security, Emerging Technologies, Artificial Intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
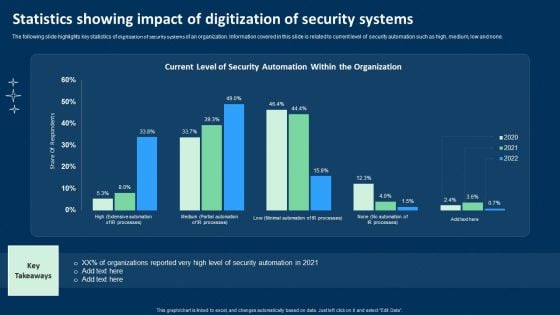
Statistics Showing Impact Of Digitization Of Security Systems Ppt Show Ideas PDF
The following slide highlights key statistics of digitization of security systems of an organization. Information covered in this slide is related to current level of security automation such as high, medium, low and none. Showcasing this set of slides titled Statistics Showing Impact Of Digitization Of Security Systems Ppt Show Ideas PDF. The topics addressed in these templates are Current Level, Security Automation, Organization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF
This slide outlines the business plan for managed security service which includes services such as antivirus, anti-malware, anti-spam etc. it also provides information about the total cost of services, status of purchase, security goal, etc. Pitch your topic with ease and precision using this Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF. This layout presents information on Revenue, Security Goal, IT Security Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Building Trust With IoT Security Best Practices To Provision Devices And Systems IoT SS V
This slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem. It includes allocate unique identifies, set up access control, and backup and recovery. There are so many reasons you need a Building Trust With IoT Security Best Practices To Provision Devices And Systems IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem. It includes allocate unique identifies, set up access control, and backup and recovery.
Icon For Managed Cyber Security Service Provider Ppt Slides Good PDF
Presenting Icon For Managed Cyber Security Service Provider Ppt Slides Good PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Icon, Managed, Cyber Security, Service Provider. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Risks And Incident Response Playbook Addressing The Various Security Incidents And Attacks Slides PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques. Create an editable Cyber Risks And Incident Response Playbook Addressing The Various Security Incidents And Attacks Slides PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Risks And Incident Response Playbook Addressing The Various Security Incidents And Attacks Slides PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
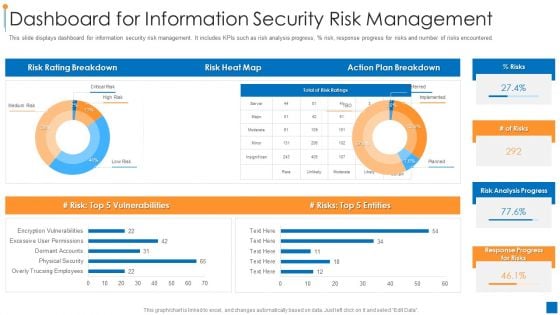
International Organization Standardization 270001 Dashboard For Information Security Risk Management Pictures PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, parcent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative international organization standardization 270001 dashboard for information security risk management pictures pdf bundle. Topics like dashboard for information security risk management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf
This slide showcases the assessment and improvement of safety program which includes monitoring performance, examining program and checking improvement opportunities. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf This slide showcases the assessment and improvement of safety program which includes monitoring performance, examining program and checking improvement opportunities.
Risk Administration Plan Icon To Improve Cyber Security Project Summary PDF
Presenting Risk Administration Plan Icon To Improve Cyber Security Project Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Risk Administration Plan, Icon To Improve, Cyber Security, Project. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Prevention Of Information Functional Chart Of Cyber Security Team Themes PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Prevention Of Information Functional Chart Of Cyber Security Team Themes PDF can be your best option for delivering a presentation. Represent everything in detail using Prevention Of Information Functional Chart Of Cyber Security Team Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
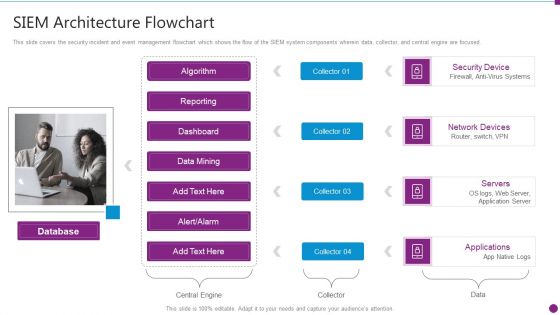
Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Architecture Flowchart Microsoft PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a security information and event management strategies for financial audit and compliance siem architecture flowchart microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like database, security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Communication Plan For Information Technology Security Based On Audience Type Demonstration PDF
This slide consists of a communication plan information technology security to be deployed by managers based on the type of audience. Key elements include communication, frequency, communication goal, owner, etc. Presenting Communication Plan For Information Technology Security Based On Audience Type Demonstration PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Project Status Report, Team Standup, Task Progress Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
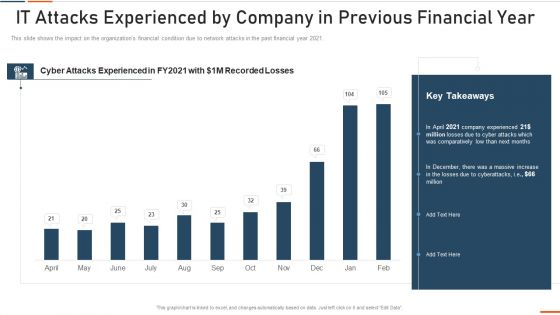
Information Technology Security IT Attacks Experienced By Company Ppt Show Grid PDF
This slide shows the impact on the organizations financial condition due to network attacks in the past financial year 2021. Deliver an awe inspiring pitch with this creative information technology security it attacks experienced by company ppt show grid pdf bundle. Topics like it attacks experienced by company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Solutions To Manage Saas Cloud Security Issues Ppt PowerPoint Presentation Gallery Visuals PDF
The following slide highlights multiple solutions to prevent security risks and issues. It also includes elements such as risk evaluation, security awareness, checklist, policies and regulation, recovery plan etc. Presenting Key Solutions To Manage Saas Cloud Security Issues Ppt PowerPoint Presentation Gallery Visuals PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Risk Evaluation, Security Awareness, Security Checklist, Policies And Regulation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF
The following slide represents checklist for SaaS security implementation and assessment. It includes activities such as run security test, training staff, planning backup, installing automated security alert along with their status. Presenting Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Run Security Test, Planned Backup, New Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Key Industry Considerations And Report Global Security Industry PPT PowerPoint IR SS V
The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile. The slide presents the key assumptions and limitations considered while building the Defense industry report. The purpose of this slide is to provide the analysis and projections in acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Industry Considerations And Report Global Security Industry PPT PowerPoint IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile.

Security Management Plan Steps In Detail Remote Access Control Mockup PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Remote Access Control. Deliver an awe inspiring pitch with this creative security management plan steps in detail remote access control mockup pdf bundle. Topics like security management plan steps in detail remote access control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Adopting Access Controls Microsoft PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls microsoft pdf bundle. Topics like implementation costs, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































