Data Security And Protection
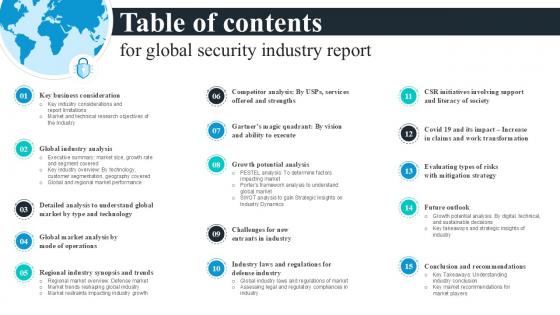
Table Of Contents For Global Security Industry Report PPT Template IR SS V
Slidegeeks has constructed Table Of Contents For Global Security Industry Report PPT Template IR SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. Our Table Of Contents For Global Security Industry Report PPT Template IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
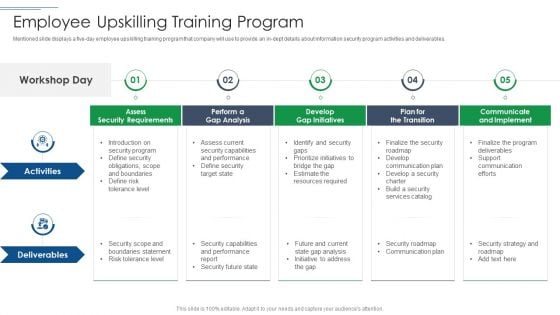
IT Security Risk Management Approach Introduction Employee Upskilling Training Program Pictures PDF
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in dept details about information security program activities and deliverables. This is a IT Security Risk Management Approach Introduction Employee Upskilling Training Program Pictures PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Develop Gap Initiatives, Communicate And Implement, Assess Security Requirements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Roles And Responsibilities Of Risk Management Team Information Security Risk Administration Designs PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are - information security manager, risk management officer and chief information officer.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Roles And Responsibilities Of Risk Management Team Information Security Risk Administration Designs PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
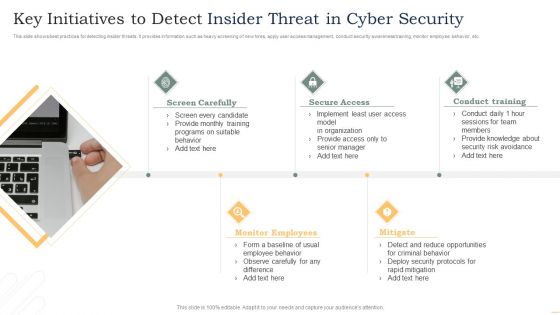
Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF
This slide shows best practices for detecting insider threats. It provides information such as heavy screening of new hires, apply user access management, conduct security awareness training, monitor employee behavior, etc. Presenting Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Screen Carefully, Secure Access, Conduct Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cybersecurity Dashboard For Threat Tracking In Electronic Information Security Ppt Ideas Graphics PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative cybersecurity dashboard for threat tracking in electronic information security ppt ideas graphics pdf bundle. Topics like dashboard for threat tracking in electronic information security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
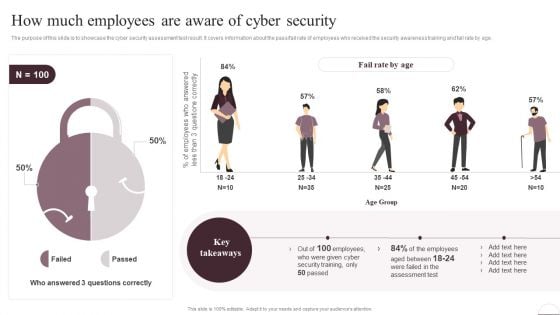
Prevention Of Information How Much Employees Are Aware Of Cyber Security Slides PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass or fail rate of employees who received the security awareness training and fail rate by age. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Prevention Of Information How Much Employees Are Aware Of Cyber Security Slides PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
Barriers And Solutions Icons Slide Security Technology Ppt PowerPoint Presentation Model Information
Presenting this set of slides with name barriers and solutions icons slide security technology ppt powerpoint presentation model information. The topics discussed in these slides are technology, communication, planning, strategy, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
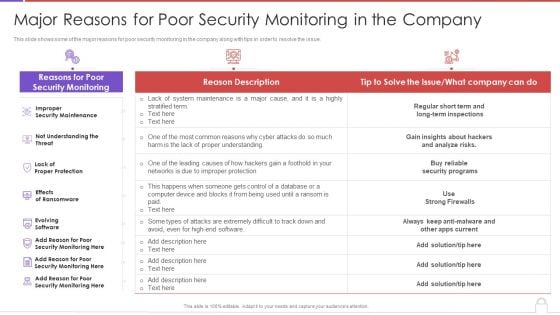
Methods To Develop Major Reasons For Poor Security Monitoring In The Company Information PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver and pitch your topic in the best possible manner with this methods to develop major reasons for poor security monitoring in the company information pdf. Use them to share invaluable insights on improper security maintenance, evolving software, high end software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Exit Strategy Voice Assistance Security Platform Investor Funding Presentation Structure Pdf
The slide provides most profitable feasible ways for investors to exit from their investment in the company. It consists of strategies like IPO Initial Public Offering and partnership exit. Welcome to our selection of the Exit Strategy Voice Assistance Security Platform Investor Funding Presentation Structure Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today The slide provides most profitable feasible ways for investors to exit from their investment in the company. It consists of strategies like IPO Initial Public Offering and partnership exit.

IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. This is a IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Specific Measures, Security Control, Cybersecurity Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
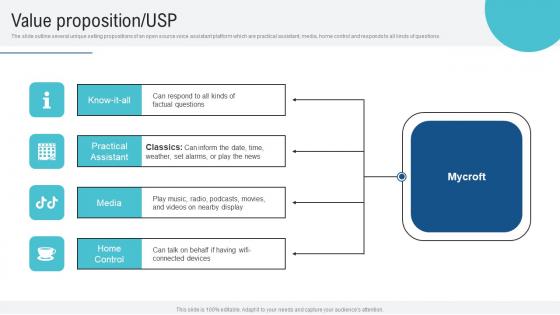
Value Proposition USP Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf
The slide outline several unique selling propositions of an open source voice assistant platform which are practical assistant, media, home control and responds to all kinds of questions. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Value Proposition USP Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The slide outline several unique selling propositions of an open source voice assistant platform which are practical assistant, media, home control and responds to all kinds of questions.
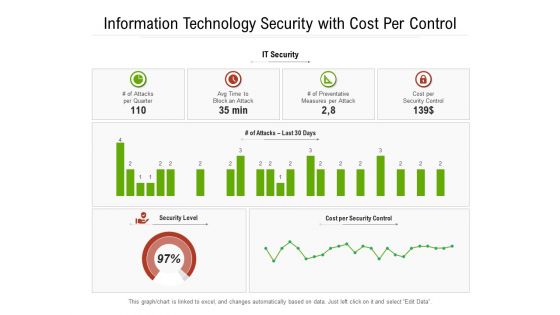
Information Technology Security With Cost Per Control Ppt PowerPoint Presentation Gallery Maker PDF
Presenting this set of slides with name information technology security with cost per control ppt powerpoint presentation gallery maker pdf. The topics discussed in these slides are cost, quarter, measures. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
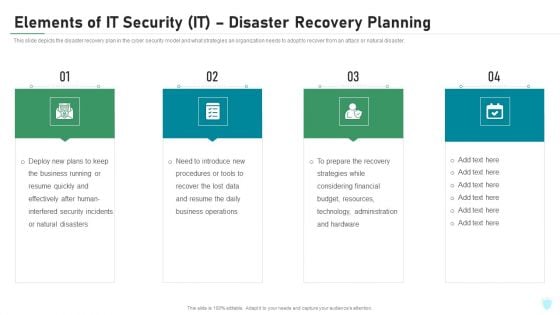
Elements Of IT Security IT Disaster Recovery Planning Ppt Styles Influencers PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Presenting elements of it security it disaster recovery planning ppt styles influencers pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like effectively, business, technology, budget, resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
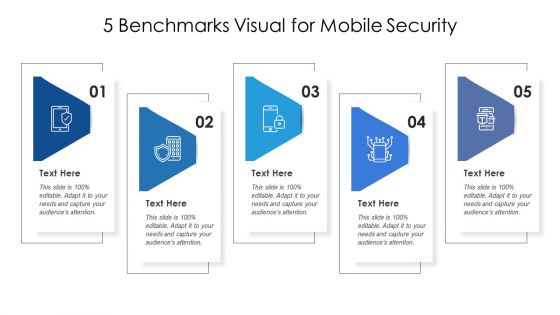
5 Benchmarks Visual For Mobile Security Ppt PowerPoint Presentation Gallery Tips PDF
Presenting 5 benchmarks visual for mobile security ppt powerpoint presentation gallery tips pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including 5 benchmarks visual for mobile security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
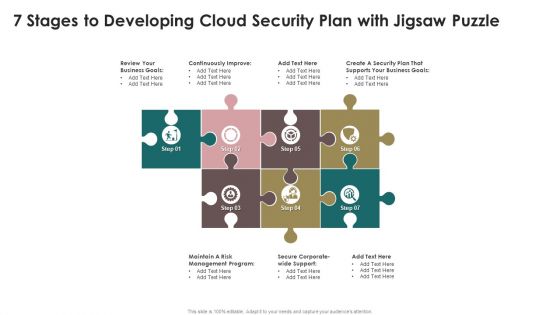
7 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Mockup PDF
Presenting 7 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Mockup PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
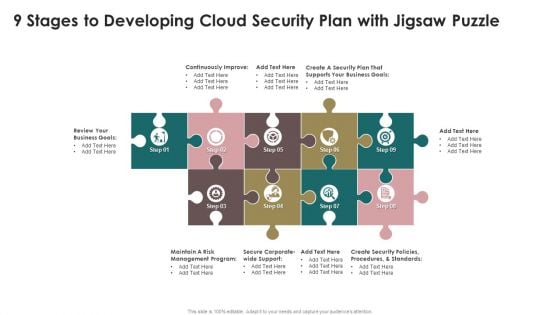
9 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Microsoft PDF
Presenting 9 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Microsoft PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Management Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
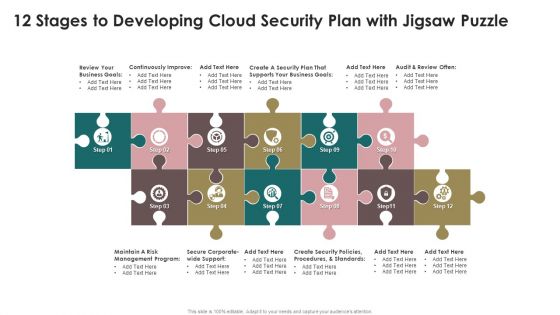
12 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Infographics PDF
Presenting 12 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Infographics PDF to dispense important information. This template comprises tweleve stages. It also presents valuable insights into the topics including Continuously Improve, Business Goals, Security Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon For Strategic Plan Roadmap To Improve Cyber Security Clipart PDF
Presenting Icon For Strategic Plan Roadmap To Improve Cyber Security Clipart PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Strategic Plan, Roadmap Improve, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
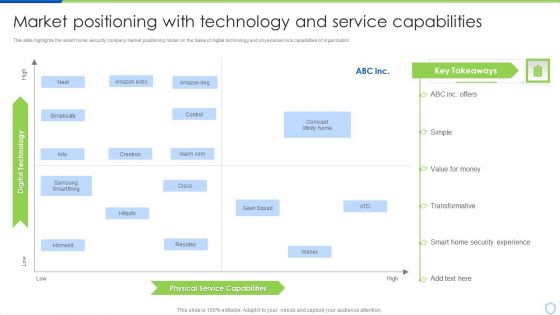
Security And Surveillance Company Profile Market Positioning With Technology Mockup PDF
This slide highlights the smart home security company market positioning model on the basis of digital technology and physical service capabilities of organization. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Market Positioning With Technology Mockup PDF bundle. Topics like Monitoring, Bluestone Security, Launched Integrated can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
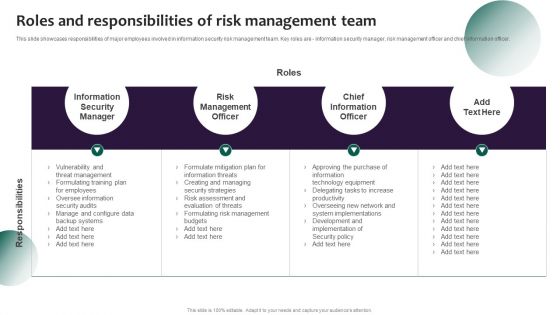
Information Systems Security And Risk Management Plan Roles And Responsibilities Of Risk Management Team Pictures PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are - information security manager, risk management officer and chief information officer. Are you searching for a Information Systems Security And Risk Management Plan Roles And Responsibilities Of Risk Management Team Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Information Systems Security And Risk Management Plan Roles And Responsibilities Of Risk Management Team Pictures PDF from Slidegeeks today.

Implementing Safety Administration Initiative For Risk Mitigation Way To Overcome Security Demonstration PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide. This is a implementing safety administration initiative for risk mitigation way to overcome security demonstration pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like goals, information, risk, analysis, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
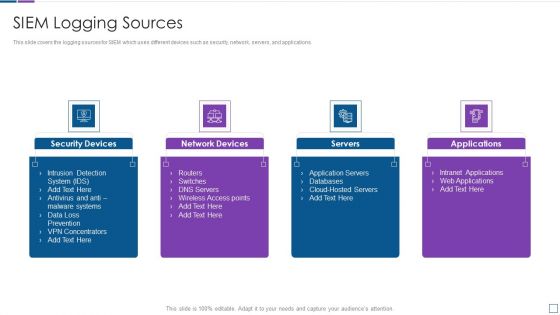
Real Time Assessment Of Security Threats SIEM Logging Sources Infographics PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. This is a real time assessment of security threats siem logging sources infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security devices, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
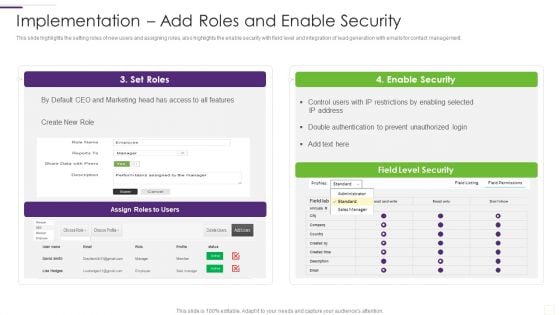
CRM Implementation Strategy Implementation Add Roles And Enable Security Rules PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative CRM Implementation Strategy Implementation Add Roles And Enable Security Rules PDF bundle. Topics like Enable Security, Double Authentication, Prevent Unauthorized can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
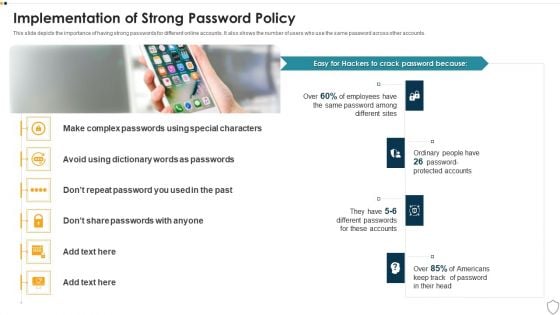
IT Security Implementation Of Strong Password Policy Ppt Summary Gridlines PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. This is a it security implementation of strong password policy ppt summary gridlines pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation of strong password policy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Operations Certifications And Training Courses For IT Professionals Topics PDF
This slide exhibits training courses for security operations administrators to enhance their cyber threat management skills. It includes elements such as course, course outline, rating, pricing, frequency, and mode of training. Showcasing this set of slides titled Security Operations Certifications And Training Courses For IT Professionals Topics PDF. The topics addressed in these templates are Security Operations, Fundamental, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Implementation Of Strong Password Policy IT Security IT Ppt Styles Topics PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Presenting implementation of strong password policy it security it ppt styles topics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like implementation of strong password policy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Employee Awareness Training Budget For FY2020 IT Security IT Ppt Show Slides PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. This is a employee awareness training budget for fy2020 it security it ppt show slides pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like maintain, vulnerability, management, secure, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
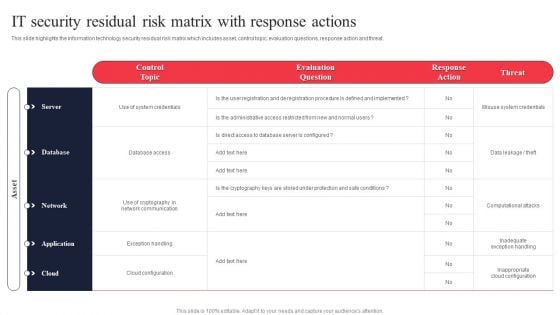
IT System Risk Management Guide IT Security Residual Risk Matrix With Response Actions Slides PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT System Risk Management Guide IT Security Residual Risk Matrix With Response Actions Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT System Risk Management Guide IT Security Residual Risk Matrix With Response Actions Slides PDF.
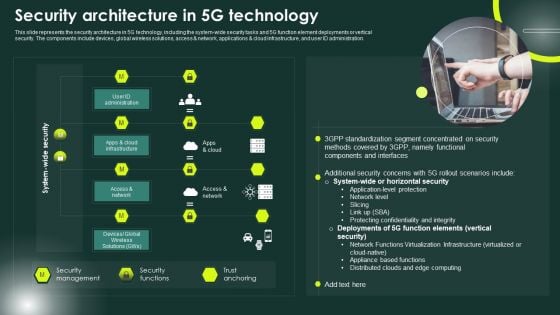
5G Network Applications And Features Security Architecture In 5G Technology Elements PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Whether you have daily or monthly meetings, a brilliant presentation is necessary. 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF can be your best option for delivering a presentation. Represent everything in detail using 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
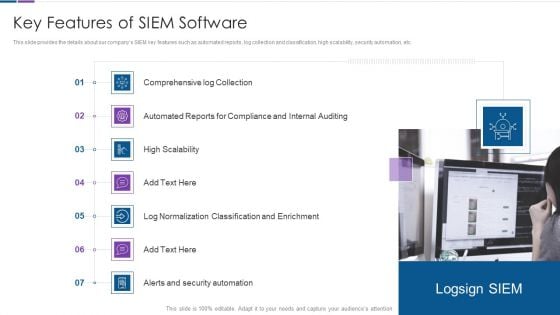
Real Time Assessment Of Security Threats Key Features Of SIEM Software Inspiration PDF
This slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. Presenting real time assessment of security threats key features of siem software inspiration pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like compliance and internal auditing, high scalability, classification and enrichment, security automation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Figures Icon Infographics For Security Best Practices Ppt PowerPoint Presentation File Graphics Example PDF
Persuade your audience using this figures icon infographics for security best practices ppt powerpoint presentation file graphics example pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including figures icon infographics for security best practices. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
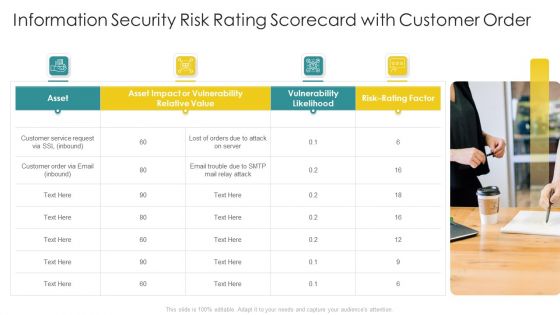
Cybersecurity Risk Scorecard Information Security Risk Rating Scorecard With Customer Order Slides PDF
This is a cybersecurity risk scorecard information security risk rating scorecard with customer order slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security risk rating scorecard with customer order. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Corporate Security Vendor Analysis Ppt PowerPoint Presentation Infographic Template Information Cpb Pdf
Presenting this set of slides with name corporate security vendor analysis ppt powerpoint presentation infographic template information cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like corporate security vendor analysis to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Cybersecurity Elements Of Electronic Information Security End User Education Ppt Show Brochure PDF
This is a cybersecurity elements of electronic information security end user education ppt show brochure pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like social media, measures, security, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security Camera System Company Profile Market Positioning With Technology Icons PDF
Presenting Security Camera System Company Profile Market Positioning With Technology Icons PDF to provide visual cues and insights. Share and navigate important information on One stage that need your due attention. This template can be used to pitch topics like Transformative, Security Experience, Service Capabilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Identifying Goals And Objectives Graphics PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives graphics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail identifying goals and objectives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
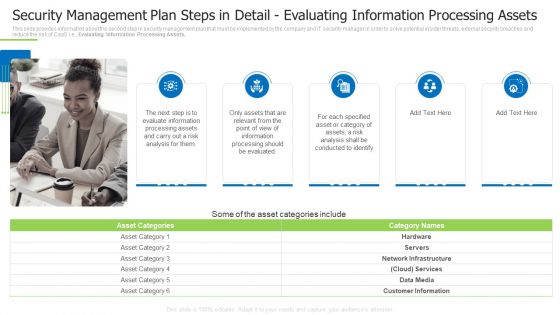
Security Management Plan Steps In Detail Evaluating Information Processing Assets Demonstration PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluate information, conducted to identify, specified asset You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
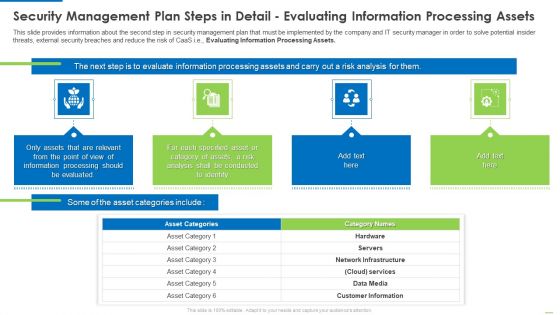
Security Management Plan Steps In Detail Evaluating Information Processing Assets Summary PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e.Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like processing should be evaluated, conducted to identify, category of assets You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Present like a pro with Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
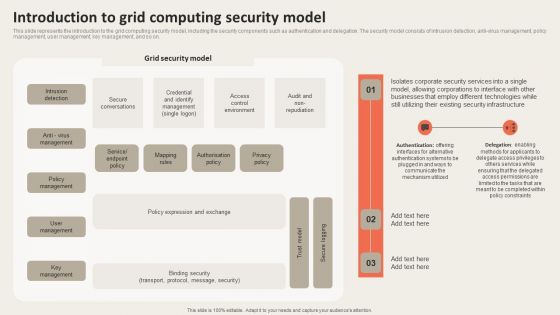
Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. There are so many reasons you need a Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
User Profile Lock For Security Vector Icon Ppt PowerPoint Presentation Gallery Professional PDF
Presenting user profile lock for security vector icon ppt powerpoint presentation gallery professional pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including user profile lock for security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Security Strategy Roadmap Icon With Lock Symbol Ppt PowerPoint Presentation File Gridlines PDF
Presenting Cyber Security Strategy Roadmap Icon With Lock Symbol Ppt PowerPoint Presentation File Gridlines PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cyber Security Strategy, Roadmap Icon, Lock Symbol. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
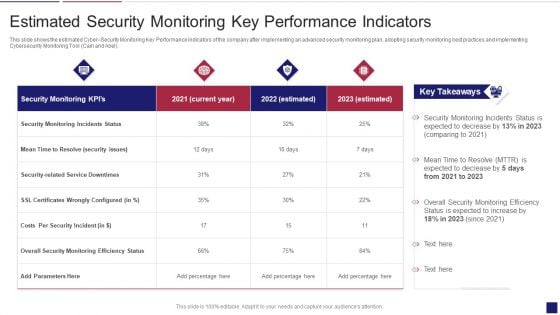
Continuous Development Evaluation Plan Eliminate Cyber Attacks Estimated Security Monitoring Designs PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks estimated security monitoring designs pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
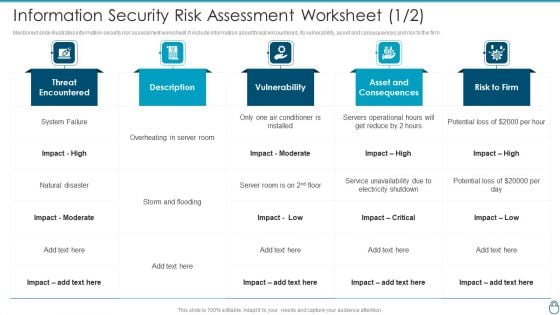
Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF bundle. Topics like Conditioner Is Installed, Asset And Consequences, Electricity Shutdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
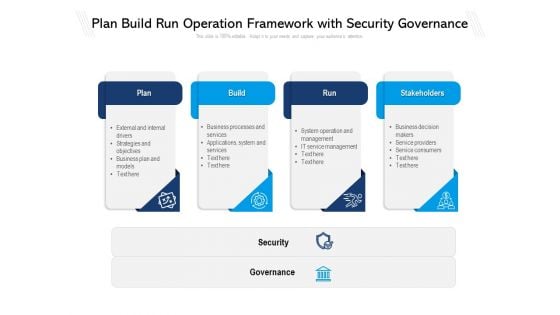
Plan Build Run Operation Framework With Security Governance Ppt PowerPoint Presentation Infographics Master Slide PDF
Presenting plan build run operation framework with security governance ppt powerpoint presentation infographics master slide pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Plan, Build, Run, Stakeholders, Security, Governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Guards Standing Outside Bank Building Vector Icon Ppt PowerPoint Presentation Icon Files PDF
Presenting security guards standing outside bank building vector icon ppt powerpoint presentation icon files pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including security guards standing outside bank building vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
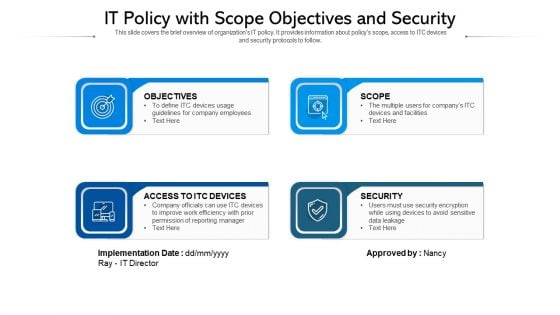
IT Policy With Scope Objectives And Security Ppt PowerPoint Presentation Infographics Show PDF
This slide covers the brief overview of organizations IT policy. It provides information about policys scope, access to ITC devices and security protocols to follow. Persuade your audience using this IT policy with scope objectives and security ppt powerpoint presentation infographics show pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including objectives, access to itc devices, security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
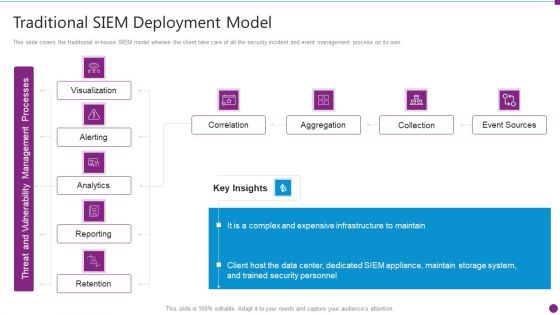
Security Information And Event Management Strategies For Financial Audit And Compliance Traditional SIEM Deployment Guidelines PDF
This slide covers the traditional in-house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver an awe inspiring pitch with this creative security information and event management strategies for financial audit and compliance traditional siem deployment guidelines pdf bundle. Topics like correlation, aggregation, collection, event sources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Guards In Music Concert For People Safety Ppt PowerPoint Presentation Outline Guide PDF
Pitch your topic with ease and precision using this security guards in music concert for people safety ppt powerpoint presentation outline guide pdf. This layout presents information on security guards in music concert for people safety. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
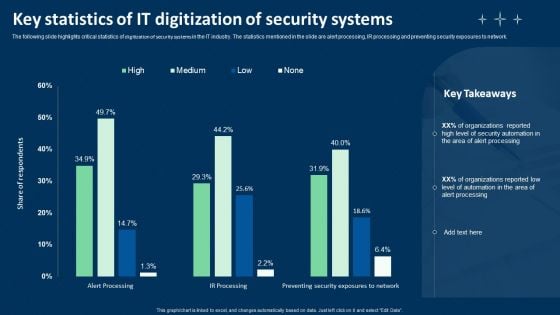
Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF
The following slide highlights four step process of cloud digitization of security systems. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Persuade your audience using this Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Container Configure Management, Use Infrastructure, Code Automate Asset Tagging. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
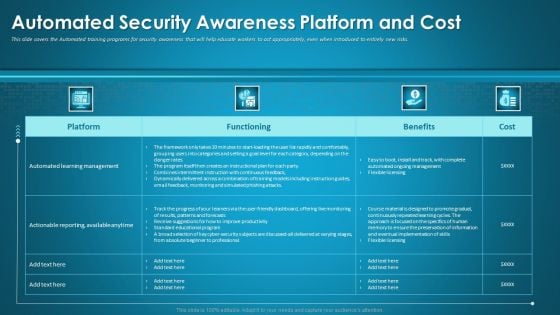
Organizational Network Staff Learning Automated Security Awareness Platform And Cost Introduction PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks. Deliver an awe-inspiring pitch with this creative organizational network staff learning automated security awareness platform and cost introduction pdf bundle. Topics like automated security awareness platform and cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
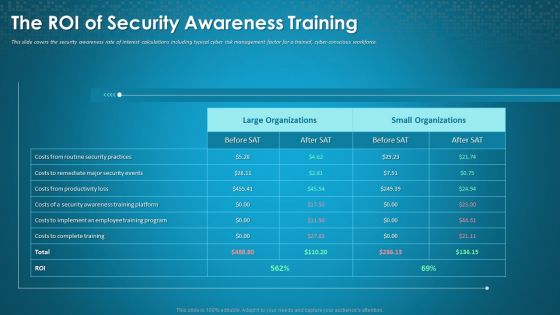
Organizational Network Staff Learning The ROI Of Security Awareness Training Designs PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this organizational network staff learning the roi of security awareness training designs pdf. Use them to share invaluable insights on employee training program, security awareness training platform, productivity loss and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Badge Showing Sign Of Reliability Ppt PowerPoint Presentation Gallery Slide PDF
Presenting security badge showing sign of reliability ppt powerpoint presentation gallery slide pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including security badge showing sign of reliability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

3Rd Party API Integration To Check Security Ppt PowerPoint Presentation Gallery Example Topics PDF
Presenting 3rd party api integration to check security ppt powerpoint presentation gallery example topics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including check security, implementation, mission. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Financial Security Guidelines Document Vector Icon Ppt PowerPoint Presentation Icon Outline PDF
Presenting financial security guidelines document vector icon ppt powerpoint presentation icon outline pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including financial security guidelines document vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Global Financial Transactions Security Vector Icon Ppt PowerPoint Presentation Show Background PDF
Presenting global financial transactions security vector icon ppt powerpoint presentation show background pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including global financial transactions security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Smart Phone Application With Global Security Vector Icon Ppt PowerPoint Presentation Summary Shapes PDF
Presenting smart phone application with global security vector icon ppt powerpoint presentation summary shapes pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including smart phone application with global security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
3 Groups Slide For Cloud Native Security Assessments Ppt PowerPoint Presentation File Professional PDF
Presenting 3 groups slide for cloud native security assessments ppt powerpoint presentation file professional pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including 3 groups slide for cloud native security assessments. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

4 Phases Funnel Diagram For Security Metrics Strategy Ppt PowerPoint Presentation Gallery Graphics Tutorials PDF
Presenting 4 phases funnel diagram for security metrics strategy ppt powerpoint presentation gallery graphics tutorials pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including 4 phases funnel diagram for security metrics strategy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































