Edge Computing

Computer Virtualization Managing End User Computing In The Company Topics PDF
This slide represents how we will manage to end user computing and it includes to adopt centralized application deployment, preparation for changing job roles, know users and so on.Presenting Computer Virtualization Managing End User Computing In The Company Topics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Security Implications, Storage Consumption, Experience Server. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Computer Virtualization Why Is End User Computing Important For Business Designs PDF
This slide describes the reasons why end-user computing is important for business and it includes slow virtual desktop solutions, to recognize essential apps and adoption of HCI platform.Presenting Computer Virtualization Why Is End User Computing Important For Business Designs PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Desktop Infrastructure, Appears Deteriorating, Conjunction Regular. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Scientific Computing IT Fee Structure For Computational Science Program Clipart PDF
This slide represents the fee structure for the computational science program, including the application fee for masters and MBAs and the tuition fee for both.Deliver and pitch your topic in the best possible manner with this scientific computing it fee structure for computational science program clipart pdf. Use them to share invaluable insights on fee structure for computational science program and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
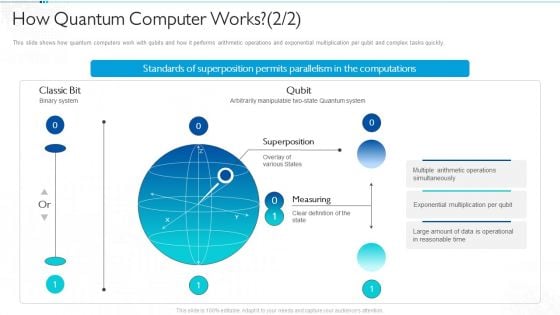
Quantum Computing For Everyone IT How Quantum Computer Works Formats PDF
This slide shows how quantum computers work with qubits and how it performs arithmetic operations and exponential multiplication per qubit and complex tasks quickly. Deliver an awe inspiring pitch with this creative quantum computing for everyone it how quantum computer works formats pdf bundle. Topics like superposition, measuring, qubit, classic bit can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
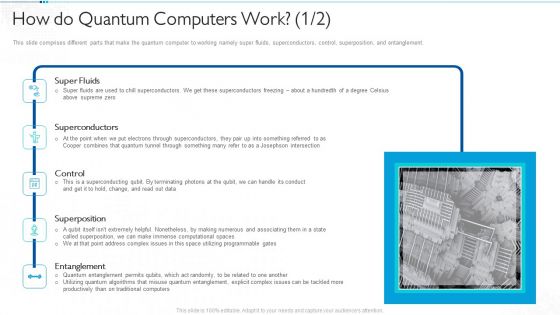
Quantum Computing For Everyone IT How Do Quantum Computers Work Ideas PDF
This slide comprises different parts that make the quantum computer to working namely super fluids, superconductors, control, superposition, and entanglement. Deliver an awe inspiring pitch with this creative quantum computing for everyone it how do quantum computers work ideas pdf bundle. Topics like super fluids, superconductors, control, superposition, entanglement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
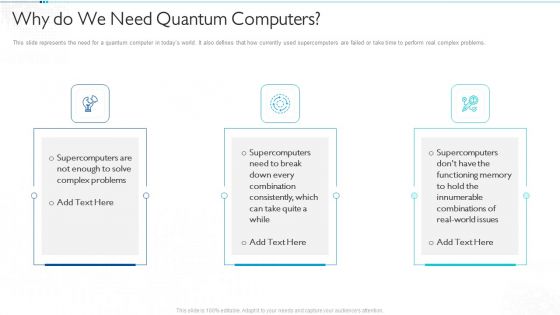
Quantum Computing For Everyone IT Why Do We Need Quantum Computers Slides PDF
This slide represents the need for a quantum computer in todays world. It also defines that how currently used supercomputers are failed or take time to perform real complex problems. This is a quantum computing for everyone it why do we need quantum computers slides pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like why do we need quantum computers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Scientific Computing IT How Can Enterprises Use Computational Science For Business Graphics PDF
This slide depicts how enterprises can use computational science for business to enhance the operational skills of the employees and get most of the technological investments.This is a scientific computing it how can enterprises use computational science for business graphics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like build crucial skills, create a workforce, technological investments You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Scientific Computing IT Structure Of The Computational Science Program Ideas PDF
This slide represents the structure of the computational science program by covering details of the modules to be covered and the mode of training.Presenting scientific computing it structure of the computational science program ideas pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like advanced programming, patterns for parallel programming, inversion and optimisation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Scientific Computing IT Teaching And Assessment Method For Computational Science Mockup PDF
This slide describes the teaching and assessment method for computational science, including teaching and assessment and practices included in each.This is a scientific computing it teaching and assessment method for computational science mockup pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like formal presentations, exercising in groups, seminars and hands. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
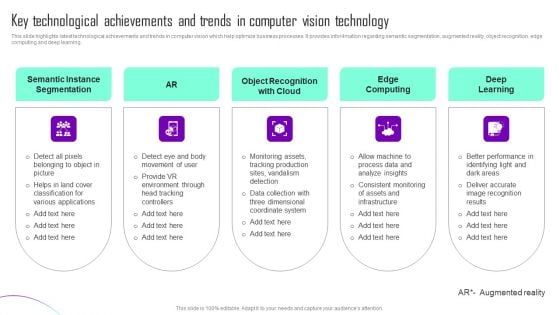
Key Technological Achievements And Trends In Computer Vision Technology Slides PDF
This slide highlights latest technological achievements and trends in computer vision which help optimize business processes. It provides infor4mation regarding semantic segmentation, augmented reality, object recognition, edge computing and deep learning. Presenting Key Technological Achievements And Trends In Computer Vision Technology Slides PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Semantic Instance Segmentation, Object Recognition Cloud, Edge Computing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
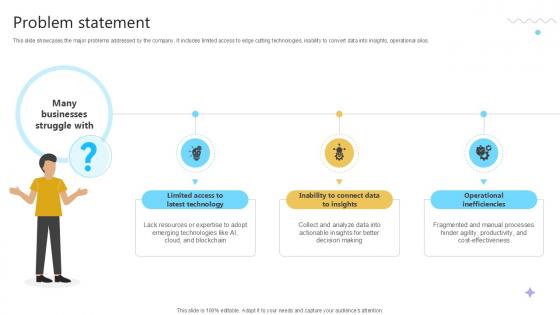
Problem Statement Cloud Computing Services Business Model PPT Presentation BMC SS V
This slide showcases the major problems addressed by the company. It includes limited access to edge cutting technologies, inability to convert data into insights, operational silos. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Problem Statement Cloud Computing Services Business Model PPT Presentation can be your best option for delivering a presentation. Represent everything in detail using Problem Statement Cloud Computing Services Business Model PPT Presentation and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the major problems addressed by the company. It includes limited access to edge cutting technologies, inability to convert data into insights, operational silos.
Network As A Service Naas Architecture Xaas Cloud Computing Models Ppt PowerPoint Presentation Icon Images PDF
This slide represents the network as a service architecture, including service provisioning layer, NaaS platform, Northbound APIs, network edge control and management, legacy network management, and so on.Deliver an awe inspiring pitch with this creative Network As A Service Naas Architecture Xaas Cloud Computing Models Ppt PowerPoint Presentation Icon Images PDF bundle. Topics like Internet Protocol, Phrase Characterize, Transmission Control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
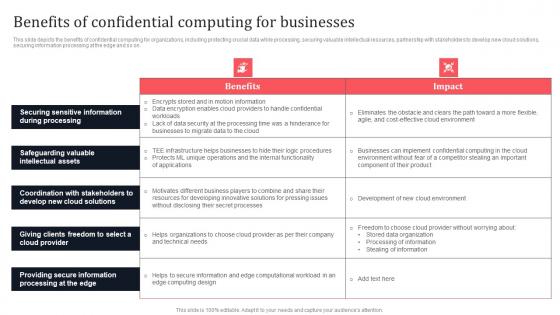
Benefits Of Confidential Computing For Businesses Secure Multi Party Ideas Pdf
This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Do you know about Slidesgeeks Benefits Of Confidential Computing For Businesses Secure Multi Party Ideas Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on.
1 Public Private Or Hybrid Cloud Computing Benefits Shown By Cloud Icons Surrounded Ppt Slides
This image slide displays public or private cloud or hybrid cloud computing benefits. This image slide has been designed with graphic of big cloud surrounded by small clouds. This image slide depicts cloud computing. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template to express views on networking and technology in your presentations. This image may be used to explain various concepts of cloud computing in your presentations. This image slide will impart professional appearance to your presentations.

Major Limitations Of Serverless Role Serverless Computing Modern Technology Graphics Pdf
This slide talks about the limitations of serverless computing systems. The purpose of this slide is to briefly explain the several drawbacks of serverless architecture. These include security, reliance on outside sources, architecture complexity, etc. Want to ace your presentation in front of a live audience Our Major Limitations Of Serverless Role Serverless Computing Modern Technology Graphics Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide talks about the limitations of serverless computing systems. The purpose of this slide is to briefly explain the several drawbacks of serverless architecture. These include security, reliance on outside sources, architecture complexity, etc.
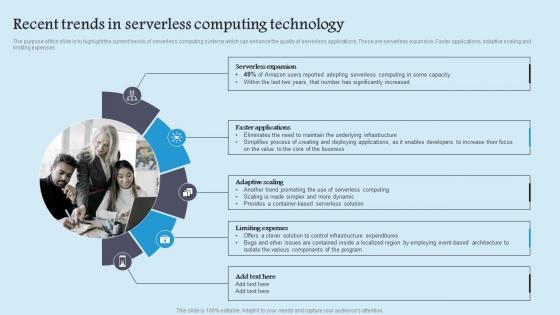
Recent Trends In Serverless Role Serverless Computing Modern Technology Microsoft Pdf
The purpose of this slide is to highlight the current trends of serverless computing systems which can enhance the quality of serverless applications. These are serverless expansion. Faster applications, adaptive scaling and limiting expenses. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Recent Trends In Serverless Role Serverless Computing Modern Technology Microsoft Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Recent Trends In Serverless Role Serverless Computing Modern Technology Microsoft Pdf today and make your presentation stand out from the rest The purpose of this slide is to highlight the current trends of serverless computing systems which can enhance the quality of serverless applications. These are serverless expansion. Faster applications, adaptive scaling and limiting expenses.
Icons Slide Cloud Computing Services Business Model PPT Slide BMC SS V
Introducing our well designed Icons Slide Cloud Computing Services Business Model PPT Slide set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide Cloud Computing Services Business Model PPT Slide BMC SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icons Slide For Cloud Data Computing Company Fund Raising Pitch Deck Diagrams PDF
Introducing our well designed Icons Slide For Cloud Data Computing Company Fund Raising Pitch Deck Diagrams PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Cloud Data Computing Company Fund Raising Pitch Deck Diagrams PDF are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icons Slide For Role Of Serverless Computing In Modern Technology Portrait Pdf
Introducing our well designed Icons Slide For Role Of Serverless Computing In Modern Technology Portrait Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Role Of Serverless Computing In Modern Technology Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
1 Cloud Computing Concept With Mobile Devices Connected To Public Cloud Ppt Slides
This image slide displays cloud computing concept with mobile devices connected to public. This image slide has been crafted with graphic of cloud and various technology devices like mobile, tablet, laptop, computer. Graphic of various business icons has also been used in this image slide. This image slide depicts cloud computing. Use this image slide, in your presentations to explain concepts like cloud computing, technology and business. This image slide will impart professional appearance to your presentations.
1 Cloud Computing Concept With Mobile Wireless Email Device Connected To The Cloud Ppt Slides
This image slide displays cloud computing concept with mobile wireless email devices connected to the cloud. This image slide has been crafted with graphic of cloud and various icons representing communication on blue color background. This image slide depicts cloud computing on wireless devices. Use this image slide, in your presentations to explain concepts like cloud computing, technology and business. This image slide will enhance the quality of your presentations.
1 Cloud Computing Icons Phone Ringing Email Social Laptop Tweet Communication Ppt Slides
This image slide displays cloud computing icons phone ringing, email, social, laptop, tweet and communication. This image slide has been crafted with graphic of clouds printed various icons representing communication and technology. This image slide depicts cloud computing on wireless devices. Use this image slide, in your presentations to explain concepts like cloud computing, technology and business. This image slide will enhance the quality of your presentations.
1 Cloud Computing Technology Icons Coming Out Of A Cloud Image Ppt Slides
This image slide displays cloud computing technology icons coming out of a cloud image. This image slide has been crafted with graphic of clouds and various icons representing communication. This image slide depicts cloud computing. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts like cloud computing, technology and business. This image slide will help you achieve your goal of making professional presentations.
1 Cloud Computing With Icons Of Communication Mobile Device Inside Ppt Slides
This image slide displays cloud computing with icons of communication and mobile device inside. This image slide has been crafted with graphic of cloud and various icons representing communication. This image slide depicts cloud computing. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts like cloud computing, technology and business. This image slide will help you create professional presentations.
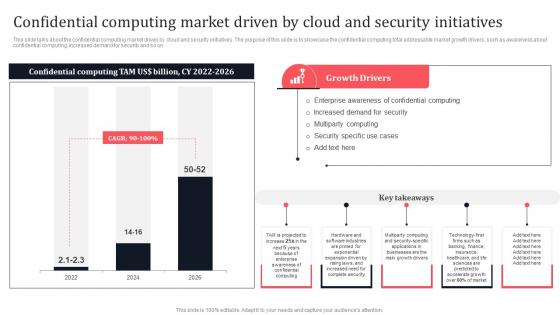
Confidential Computing Market Driven By Cloud And Security Secure Multi Party Microsoft Pdf
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Confidential Computing Market Driven By Cloud And Security Secure Multi Party Microsoft Pdf These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on.
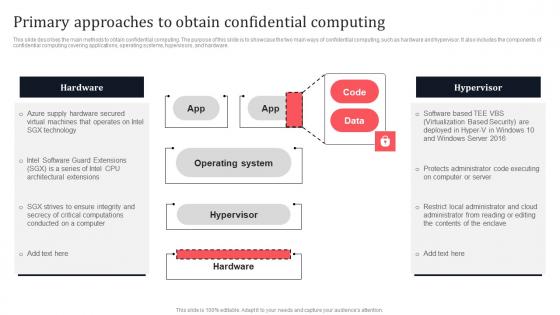
Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
Icons Slide For Integrating Cloud Computing To Enhance Projects Effectiveness Diagrams PDF
Introducing our well designed Icons Slide For Integrating Cloud Computing To Enhance Projects Effectiveness Diagrams PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Grid Computing For High Performance Solutions Slides PDF
Introducing our well designed Icons Slide For Grid Computing For High Performance Solutions Slides PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
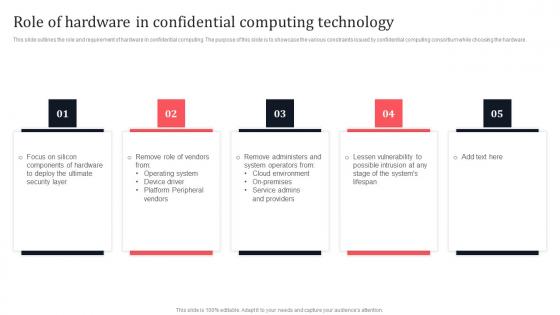
Role Of Hardware In Confidential Computing Technology Secure Multi Party Download Pdf
This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Role Of Hardware In Confidential Computing Technology Secure Multi Party Download Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Role Of Hardware In Confidential Computing Technology Secure Multi Party Download Pdf today and make your presentation stand out from the rest. This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware.

Key Benefits Of Cloud Computing Cloud Data Security Using Cryptography Pictures Pdf
This slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc. Create an editable Key Benefits Of Cloud Computing Cloud Data Security Using Cryptography Pictures Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Key Benefits Of Cloud Computing Cloud Data Security Using Cryptography Pictures Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc.
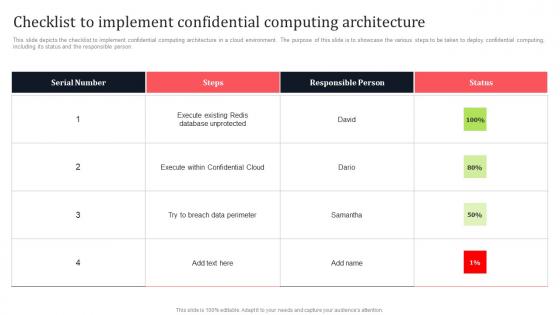
Checklist To Implement Confidential Computing Architecture Secure Multi Party Guidelines Pdf
This slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Checklist To Implement Confidential Computing Architecture Secure Multi Party Guidelines Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person.
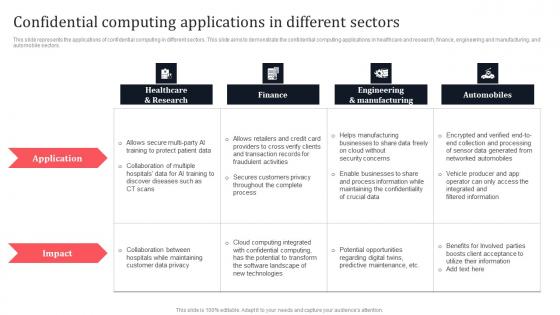
Confidential Computing Applications In Different Sectors Secure Multi Party Slides Pdf
This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors. Present like a pro with Confidential Computing Applications In Different Sectors Secure Multi Party Slides Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors.

Solar Computing IT Case Study Coca Cola Launches Green IT Strategy
This slide outlines the case study of Coca-Colas green computing strategy implementation. The purpose of this slide is to showcase the overview, requirements, solutions and impact of green computing adoption on the company. Want to ace your presentation in front of a live audience Our Solar Computing IT Case Study Coca Cola Launches Green IT Strategy can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the case study of Coca-Colas green computing strategy implementation. The purpose of this slide is to showcase the overview, requirements, solutions and impact of green computing adoption on the company.
Confidential Computing Architecture Based On Azure Services Secure Multi Party Icons Pdf
This slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Confidential Computing Architecture Based On Azure Services Secure Multi Party Icons Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Confidential Computing Architecture Based On Azure Services Secure Multi Party Icons Pdf today and make your presentation stand out from the rest. This slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc.
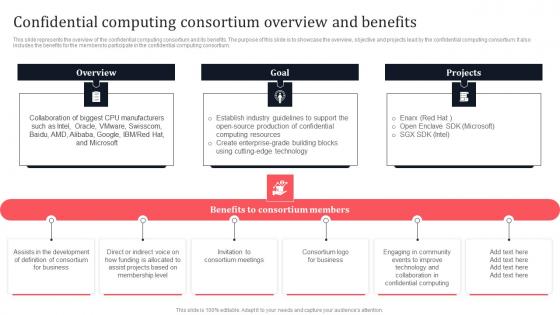
Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. If you are looking for a format to display your unique thoughts, then the professionally designed Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium.
Cloud Computing Service Level Agreement Model Management And Monitoring Framework Icon Clipart Pdf
Pitch your topic with ease and precision using this Cloud Computing Service Level Agreement Model Management And Monitoring Framework Icon Clipart Pdf. This layout presents information on Cloud Computing Service, Level Agreement Model. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cloud Computing Service Level Agreement Model Management And Monitoring Framework Icon Clipart Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icon Showcasing Cloud Computing Service Level Agreement Model Management Framework Topics Pdf
Pitch your topic with ease and precision using this Icon Showcasing Cloud Computing Service Level Agreement Model Management Framework Topics Pdf. This layout presents information on Showcasing Cloud Computing, Service Level Agreement, Model Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Icon Showcasing Cloud Computing Service Level Agreement Model Management Framework Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
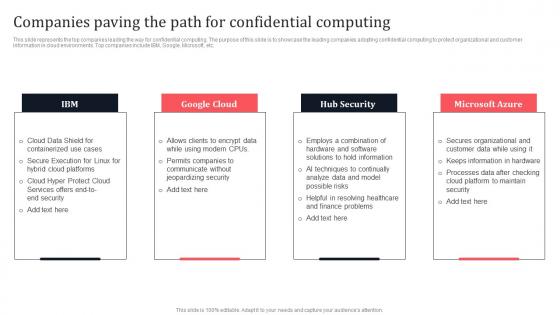
Companies Paving The Path For Confidential Computing Secure Multi Party Elements Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. There are so many reasons you need a Companies Paving The Path For Confidential Computing Secure Multi Party Elements Pdf The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc.
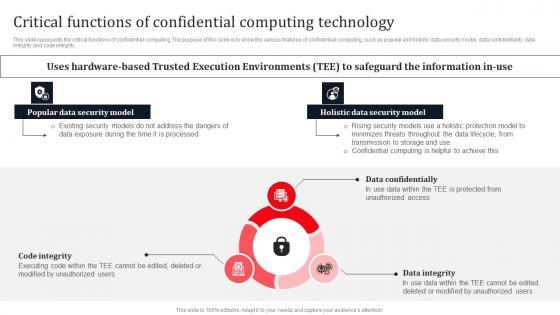
Critical Functions Of Confidential Computing Technology Secure Multi Party Information Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Critical Functions Of Confidential Computing Technology Secure Multi Party Information Pdf from Slidegeeks and deliver a wonderful presentation. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.

Need For Confidential Computing In Cloud Environment Secure Multi Party Sample Pdf
This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Need For Confidential Computing In Cloud Environment Secure Multi Party Sample Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems.
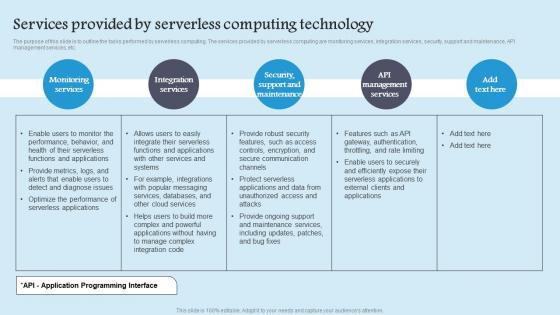
Services Provided By Serverless Role Serverless Computing Modern Technology Graphics Pdf
The purpose of this slide is to outline the tasks performed by serverless computing. The services provided by serverless computing are monitoring services, integration services, security, support and maintenance, API management services, etc. Do you know about Slidesgeeks Services Provided By Serverless Role Serverless Computing Modern Technology Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The purpose of this slide is to outline the tasks performed by serverless computing. The services provided by serverless computing are monitoring services, integration services, security, support and maintenance, API management services, etc.

About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf
This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc.
Cloud Data Repository Computing Server In Table With Open Screens Designs PDF
Presenting cloud data repository computing server in table with open screens designs pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including cloud data repository computing server in table with open screens. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Business PowerPoint Template Cloud Computing New Era Of Technology Ppt Slides
Our Business powerpoint template cloud computing new era of technology ppt Slides leave no one in doubt. Provide a certainty to your views. Some of your team maybe a little doubtful. Assure them with certainty through our Technology PowerPoint Templates. Our Network Diagrams PowerPoint Templates and your ideas make a great doubles pair. Play the net with assured hands. Tabulate goals with our Business PowerPoint Template Cloud Computing New Era Of Technology Ppt Slides. Download without worries with our money back guaranteee.
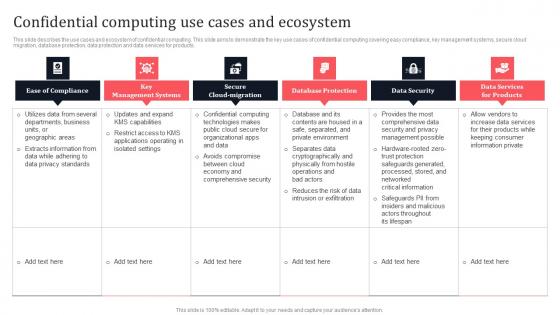
Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Explore a selection of the finest Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
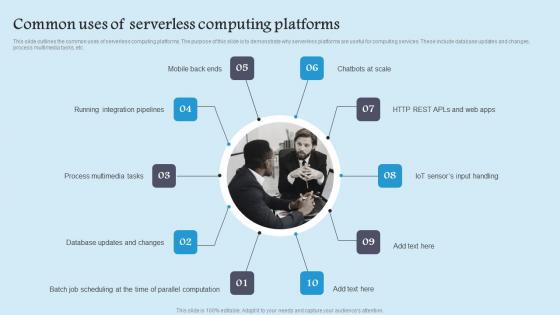
Common Uses Of Serverless Role Serverless Computing Modern Technology Download Pdf
This slide outlines the common uses of serverless computing platforms. The purpose of this slide is to demonstrate why serverless platforms are useful for computing services. These include database updates and changes, process multimedia tasks, etc. Explore a selection of the finest Common Uses Of Serverless Role Serverless Computing Modern Technology Download Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Common Uses Of Serverless Role Serverless Computing Modern Technology Download Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the common uses of serverless computing platforms. The purpose of this slide is to demonstrate why serverless platforms are useful for computing services. These include database updates and changes, process multimedia tasks, etc.
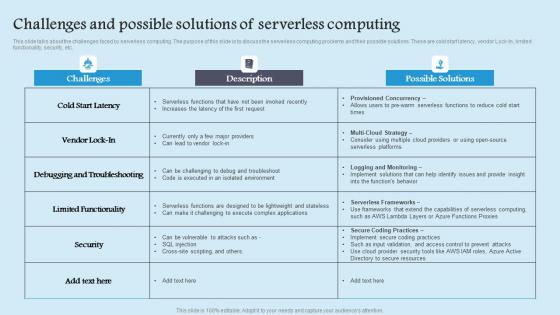
Challenges And Possible Solutions Role Serverless Computing Modern Technology Clipart Pdf
This slide talks about the challenges faced by serverless computing. The purpose of this slide is to discuss the serverless computing problems and their possible solutions. These are cold start latency, vendor Lock In, limited functionality, security, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Challenges And Possible Solutions Role Serverless Computing Modern Technology Clipart Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the challenges faced by serverless computing. The purpose of this slide is to discuss the serverless computing problems and their possible solutions. These are cold start latency, vendor Lock In, limited functionality, security, etc.
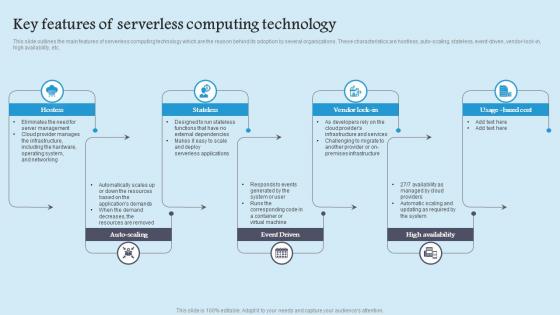
Key Features Of Serverless Role Serverless Computing Modern Technology Designs Pdf
This slide outlines the main features of serverless computing technology which are the reason behind its adoption by several organizations. These characteristics are hostless, auto scaling, stateless, event driven, vendor lock in, high availability, etc. Create an editable Key Features Of Serverless Role Serverless Computing Modern Technology Designs Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Key Features Of Serverless Role Serverless Computing Modern Technology Designs Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the main features of serverless computing technology which are the reason behind its adoption by several organizations. These characteristics are hostless, auto scaling, stateless, event driven, vendor lock in, high availability, etc.
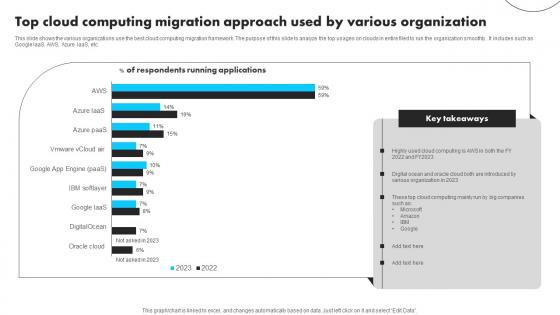
Top Cloud Computing Migration Approach Used By Various Organization Mockup Pdf
This slide shows the various organizations use the best cloud computing migration framework. The purpose of this slide to analyze the top usages on clouds in entire filed to run the organization smoothly . It includes such as Google IaaS, AWS, Azure IaaS, etc. Showcasing this set of slides titled Top Cloud Computing Migration Approach Used By Various Organization Mockup Pdf The topics addressed in these templates are Cloud Computing, Migration Approach, Various Organization All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows the various organizations use the best cloud computing migration framework. The purpose of this slide to analyze the top usages on clouds in entire filed to run the organization smoothly . It includes such as Google IaaS, AWS, Azure IaaS, etc.
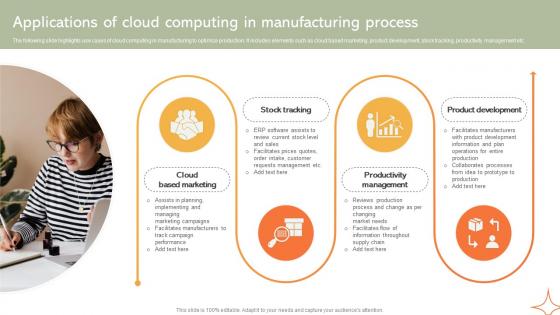
Applications Of Cloud Computing In Manufacturing Implementing Manufacturing Strategy SS V
The following slide highlights use cases of cloud computing in manufacturing to optimize production. It includes elements such as cloud based marketing, product development, stock tracking, productivity management etc. Get a simple yet stunning designed Applications Of Cloud Computing In Manufacturing Implementing Manufacturing Strategy SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Applications Of Cloud Computing In Manufacturing Implementing Manufacturing Strategy SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide highlights use cases of cloud computing in manufacturing to optimize production. It includes elements such as cloud based marketing, product development, stock tracking, productivity management etc.
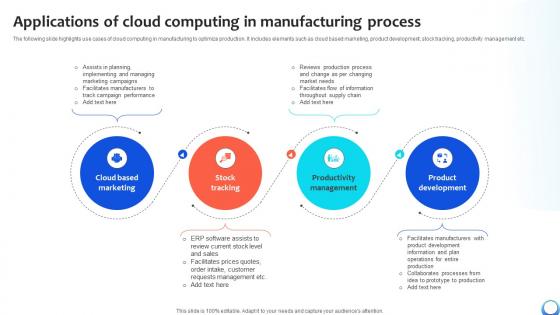
Applications Of Cloud Computing In Manufacturing Automating Production Process Strategy SS V
The following slide highlights use cases of cloud computing in manufacturing to optimize production. It includes elements such as cloud based marketing, product development, stock tracking, productivity management etc. Get a simple yet stunning designed Applications Of Cloud Computing In Manufacturing Automating Production Process Strategy SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Applications Of Cloud Computing In Manufacturing Automating Production Process Strategy SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide highlights use cases of cloud computing in manufacturing to optimize production. It includes elements such as cloud based marketing, product development, stock tracking, productivity management etc.
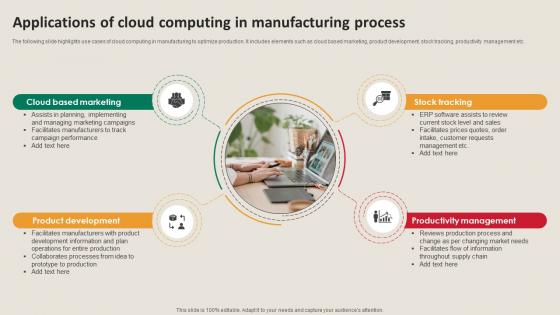
Applications Of Cloud Computing In Manufacturing Strategy Driving Industry 4 0
The following slide highlights use cases of cloud computing in manufacturing to optimize production. It includes elements such as cloud based marketing, product development, stock tracking, productivity management etc. Get a simple yet stunning designed Applications Of Cloud Computing In Manufacturing Strategy Driving Industry 4 0. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Applications Of Cloud Computing In Manufacturing Strategy Driving Industry 4 0 can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide highlights use cases of cloud computing in manufacturing to optimize production. It includes elements such as cloud based marketing, product development, stock tracking, productivity management etc.

Overview And Key Benefits Of Cloud Computing Manufacturing Strategy Driving Industry 4 0
The following slide represents brief introduction of how cloud computing assist in optimizing manufacturing process. It includes elements such as flexibility, production quality, shared accounts, load sharing etc. Get a simple yet stunning designed Overview And Key Benefits Of Cloud Computing Manufacturing Strategy Driving Industry 4 0. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Overview And Key Benefits Of Cloud Computing Manufacturing Strategy Driving Industry 4 0 can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide represents brief introduction of how cloud computing assist in optimizing manufacturing process. It includes elements such as flexibility, production quality, shared accounts, load sharing etc.
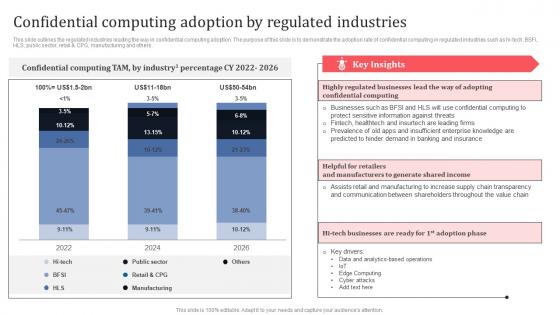
Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf
This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Get a simple yet stunning designed Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others.
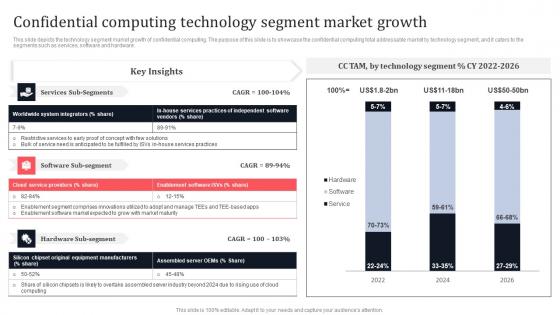
Confidential Computing Technology Segment Market Growth Secure Multi Party Guidelines Pdf
This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. This Confidential Computing Technology Segment Market Growth Secure Multi Party Guidelines Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing Technology Segment Market Growth Secure Multi Party Guidelines Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware.
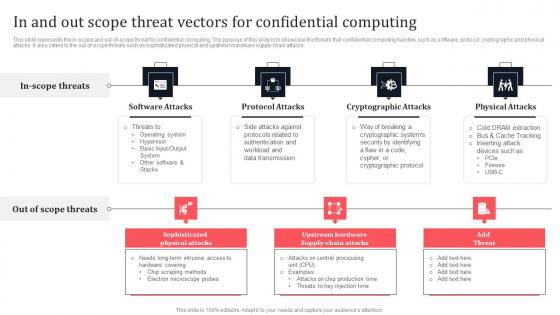
In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.

Role Of Cloud Providers Role Serverless Computing Modern Technology Inspiration Pdf
This slide talks about the role of cloud providers in serverless computing. The purpose of this slide is to explain the two main categories of cloud computing services. These types are known as Backend as a Service BaaS and Function as a Service FaaS. Find highly impressive Role Of Cloud Providers Role Serverless Computing Modern Technology Inspiration Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Cloud Providers Role Serverless Computing Modern Technology Inspiration Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide talks about the role of cloud providers in serverless computing. The purpose of this slide is to explain the two main categories of cloud computing services. These types are known as Backend as a Service BaaS and Function as a Service FaaS.
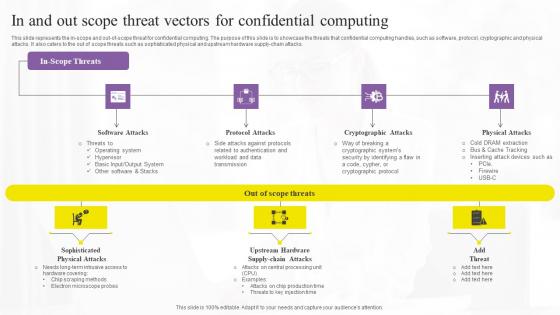
In And Out Scope Threat Vectors For Confidential Computing Technologies Infographics Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Are you searching for a In And Out Scope Threat Vectors For Confidential Computing Technologies Infographics Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download In And Out Scope Threat Vectors For Confidential Computing Technologies Infographics Pdf from Slidegeeks today. This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.

IoT Solutions For Oil Ways Cloud Computing Is Utilized In Oil And Gas IoT SS V
This slide exhibits methods through which cloud computing is applied in the oil and gas industry. It includes applications such as data storage and management, data analytics, and high performance computing. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IoT Solutions For Oil Ways Cloud Computing Is Utilized In Oil And Gas IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable IoT Solutions For Oil Ways Cloud Computing Is Utilized In Oil And Gas IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide exhibits methods through which cloud computing is applied in the oil and gas industry. It includes applications such as data storage and management, data analytics, and high performance computing.
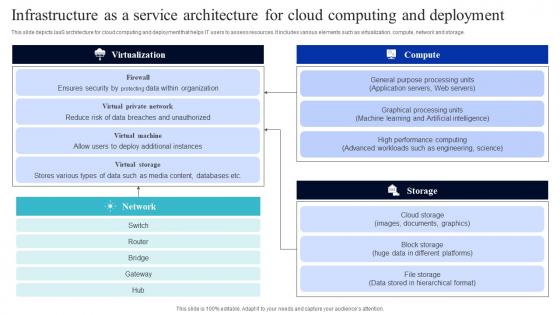
Infrastructure As A Service Architecture For Cloud Computing And Deployment Download Pdf
This slide depicts IaaS architecture for cloud computing and deployment that helps IT users to assess resources. It includes various elements such as virtualization, compute, network and storage. Pitch your topic with ease and precision using this Infrastructure As A Service Architecture For Cloud Computing And Deployment Download Pdf. This layout presents information on Virtualization, Compute, Network And Storage. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts IaaS architecture for cloud computing and deployment that helps IT users to assess resources. It includes various elements such as virtualization, compute, network and storage.


 Continue with Email
Continue with Email

 Home
Home


































