Employee Cyber Security

Various Types E Learning Courses HR Retention Techniques For Business Owners Download Pdf
The purpose of this slide is to showcase different types of online courses through which managers can enhance the existing skills of the workforce. Graphic designing cyber security, ethical hacking, digital marketing and web development are the major courses that are mentioned in the slide. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Various Types E Learning Courses HR Retention Techniques For Business Owners Download Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The purpose of this slide is to showcase different types of online courses through which managers can enhance the existing skills of the workforce. Graphic designing cyber security, ethical hacking, digital marketing and web development are the major courses that are mentioned in the slide.
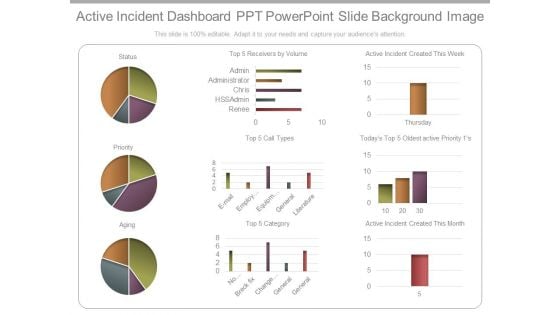
Active Incident Dashboard Ppt Powerpoint Slide Background Image
This is a active incident dashboard ppt powerpoint slide background image. This is a three stage process. The stages in this process are status, priority, aging, receivers by volume, renee, hssadmin, chris, administrator, admin, category, email, employee setup, equipment, general, literature, no category, breck fix, change management, general, active incident created this week, oldest active priority, active incident created this month, thursday.
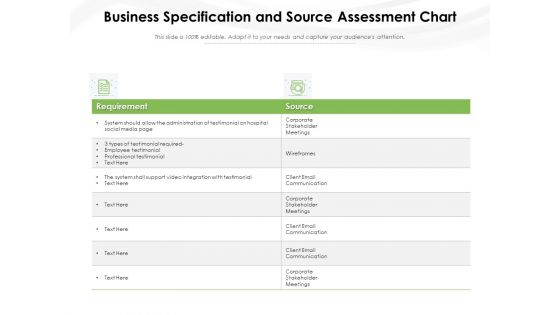
Business Specification And Source Assessment Chart Ppt PowerPoint Presentation Portfolio Clipart PDF
Presenting this set of slides with name business specification and source assessment chart ppt powerpoint presentation portfolio clipart pdf. The topics discussed in these slides are requirement, source, employee testimonial, professional testimonial, client email communication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
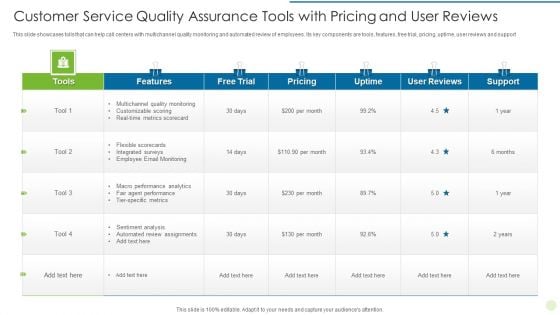
Customer Service Quality Assurance Tools With Pricing And User Reviews Guidelines PDF
Showcasing this set of slides titled Customer Service Quality Assurance Tools With Pricing And User Reviews Guidelines PDF The topics addressed in these templates are Multichannel Quality Monitoring, Employee Email Monitoring, Automated Review Assignments All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Technology Trends In Online Insurance Essential Personnel Required For Digital Transformation Team
The following slide outlines key personnel required to develop digital transformation team for converting insurer traditional to technology based. Team consists of members which are technologists, security and compliance specialists, business or technology liaisons, project managers, financial stakeholders, marketers, implementation leads and evangelists. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Technology Trends In Online Insurance Essential Personnel Required For Digital Transformation Team from Slidegeeks and deliver a wonderful presentation. The following slide outlines key personnel required to develop digital transformation team for converting insurer traditional to technology based. Team consists of members which are technologists, security and compliance specialists, business or technology liaisons, project managers, financial stakeholders, marketers, implementation leads and evangelists.
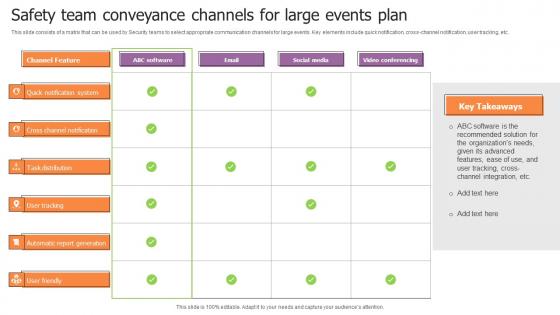
Safety Team Conveyance Channels For Large Events Plan Brochure Pdf
This slide consists of a matrix that can be used by Security teams to select appropriate communication channels for large events. Key elements include quick notification, cross-channel notification, user tracking, etc. Showcasing this set of slides titled Safety Team Conveyance Channels For Large Events Plan Brochure Pdf. The topics addressed in these templates are Channel Feature, Software, Email, Social Media. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide consists of a matrix that can be used by Security teams to select appropriate communication channels for large events. Key elements include quick notification, cross-channel notification, user tracking, etc.

Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF
This slide describes the critical functions of security operations. The purpose of this slide is to demonstrate the various functions performed by SecOps teams in an organization. The main functions include threat intelligence, security monitoring, incident response, forensics and root cause analysis, etc. Boost your pitch with our creative Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
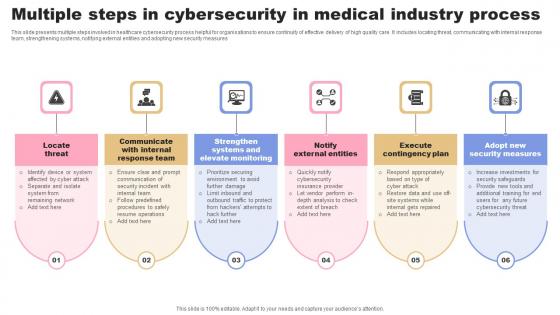
Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf
This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures Pitch your topic with ease and precision using this Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf This layout presents information on Locate Threat, Response Team, Elevate Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures
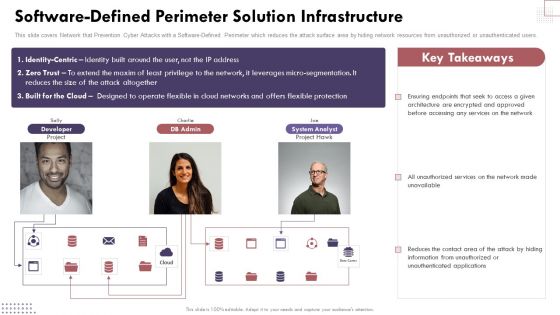
Software Defined Perimeter Solution Infrastructure Cloud Computing Complexities And Solutions Infographics PDF
This slide covers Network that Prevention Cyber Attacks with a Software-Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Software Defined Perimeter Solution Infrastructure Cloud Computing Complexities And Solutions Infographics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
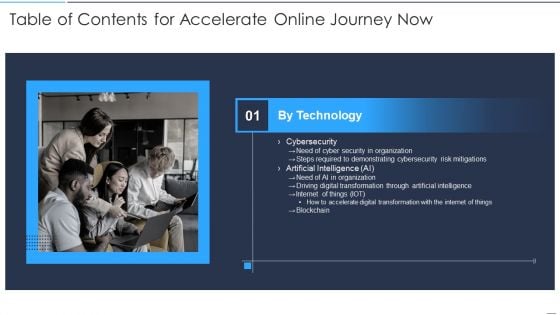
Table Of Contents For Accelerate Online Journey Now Slide Slides PDF
This is a Table Of Contents For Accelerate Online Journey Now Slide Slides PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cybersecurity, Security Organization, Demonstrating Cybersecurity You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
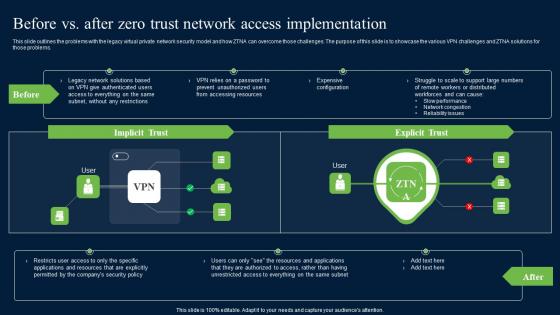
Before Vs After Zero Trust Network Access Brochure Pdf
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Zero Trust Network Access Step 3 Assess The Environment
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Network Access Step 3 Assess The Environment and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.

Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.
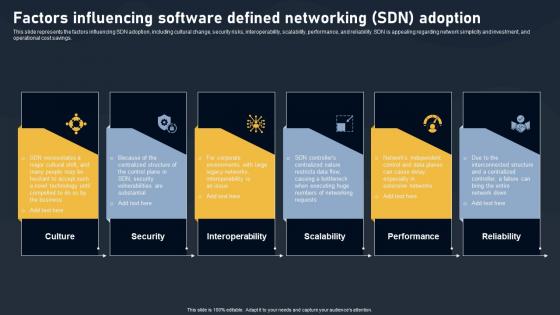
Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.Slidegeeks has constructed Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.
Zero Trust Network Access Performance Tracking Dashboard
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. Want to ace your presentation in front of a live audience Our Zero Trust Network Access Performance Tracking Dashboard can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.
Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF
This slide represents the main advantages of deploying security operations in an organization. The purpose of this slide is to showcase the critical benefits of SecOps implementation, covering an increased workforce to deal with threats, fewer buggy apps, quick response to threats, fewer security breaches, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
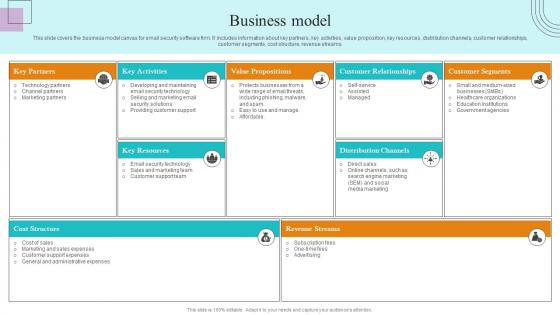
Business Model Paubox Capital Funding Pitch Deck Download Pdf
This slide covers the business model canvas for email security software firm. It includes information about key partners, key activities, value proposition, key resources, distribution channels, customer relationships, customer segments, cost structure, revenue streams. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Business Model Paubox Capital Funding Pitch Deck Download Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Business Model Paubox Capital Funding Pitch Deck Download Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers the business model canvas for email security software firm. It includes information about key partners, key activities, value proposition, key resources, distribution channels, customer relationships, customer segments, cost structure, revenue streams.

Factors Influencing Software Defined Networking SDN Adoption Evolution Of SDN Controllers Slides Pdf
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Factors Influencing Software Defined Networking SDN Adoption Evolution Of SDN Controllers Slides Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.

Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF
This slide depicts the challenges of adopting SOC as a service. The purpose of this slide is to highlight the main limitations of SOC as a service, including the onboarding process, enterprising data security, cost of log delivery, regulatory considerations, no dedicated IT security team, and limited customized options. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Machine To Machine Communication Outline Challenges Of Iot Ppt Gallery Graphics Tutorials PDF
The slide shows key challenges of IoT. This is a machine to machine communication outline challenges of iot ppt gallery graphics tutorials pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security challenges, network challenges, software development challenges, new and complex dependencies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
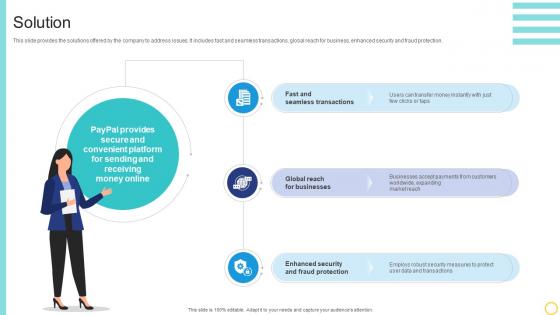
Solution Online Transaction Facilitator Business Model BMC SS V
This slide provides the solutions offered by the company to address issues. It includes fast and seamless transactions, global reach for business, enhanced security and fraud protection. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Online Transaction Facilitator Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides the solutions offered by the company to address issues. It includes fast and seamless transactions, global reach for business, enhanced security and fraud protection.
Zero Trust Model Zero Trust Network Access Performance Tracking
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Model Zero Trust Network Access Performance Tracking is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.
Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.

Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF
This slide talks about the overview of the co-managed security operation center, including its objective and benefits. The purpose of this slide is to highlight the main benefits of co-managed SOC, covering enhancing threat detection and response, scalability, cost savings and increased security knowledge. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
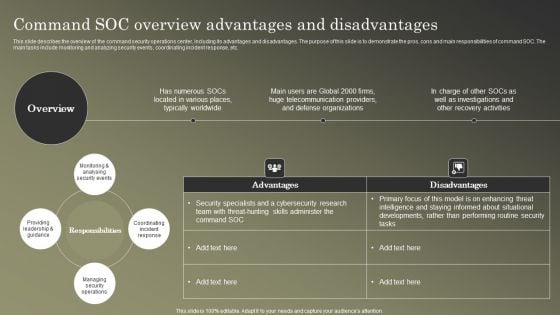
Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF
This slide describes the overview of the command security operations center, including its advantages and disadvantages. The purpose of this slide is to demonstrate the pros, cons and main responsibilities of command SOC. The main tasks include monitoring and analyzing security events, coordinating incident response, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF
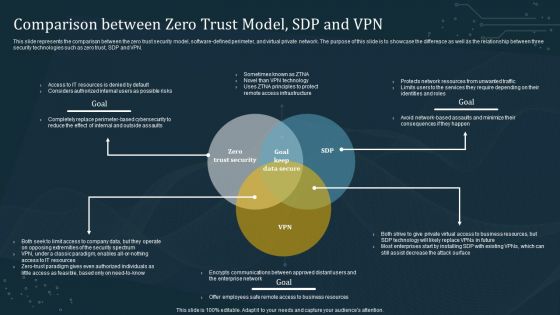
Comparison Between Zero Trust Model SDP And VPN Template PDF
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Zero Trust Model SDP And VPN Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Zero Trust Model SDP And VPN Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF
This slide represents the impact of implementing security operations in an organization. The purpose of this slide is to demonstrate how SecOps can benefit a company. The benefits include streamlined IT operations, prioritizing merge and consolidating proactive security, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Business Development Team Developing Multiple Follow Up Email Sequences SA SS V
The following slide includes a follow-up email sequence example that helps to build relationships with customers and improves employee productivity, including tools to utilise lead generation forum, email builder, and subject line checker. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Business Development Team Developing Multiple Follow Up Email Sequences SA SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Business Development Team Developing Multiple Follow Up Email Sequences SA SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide includes a follow-up email sequence example that helps to build relationships with customers and improves employee productivity, including tools to utilise lead generation forum, email builder, and subject line checker.

Key Techniques In Phishing Attacks Awareness Training Program Themes PDF
This slide covers strategies to consider in phishing awareness training program. It involves strategies such as verify email address, consider every email as phishing attempt and update security software. Presenting Key Techniques In Phishing Attacks Awareness Training Program Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Implement, Secure Network Connectivity, Payment Service. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Wiper Spyware Attack Information And Technology Army Of Ukraine Structure PDF
This slide represents the information and technology army of Ukraine, a Telegram group against Russia. In total, 308,000 users have joined this group to help Ukraine mitigate Russian cyber attacks.This is a data wiper spyware attack information and technology army of ukraine structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like prevent misinformation, provide factual information, russian residents You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Online Risk Management Dashboard For Tracking Threats And Attacks Icons PDF
The purpose of this slide is to represent dashboard to monitor risks and cyber threats for efficient risk management. It includes various types of key performance indicators such as types of risks, severities, sources and risk meter. Showcasing this set of slides titled Online Risk Management Dashboard For Tracking Threats And Attacks Icons PDF. The topics addressed in these templates are Attack, Indication Severities, Sources. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Wiper Spyware Attack For The First Time In History Anyone Can Join A War Clipart PDF
This slide represents the official announcement from Lotem Finkelstein, head of threat intelligence at Check Point Software, that anyone can join Ukraine and Russia cyber warfare.This is a data wiper spyware attack for the first time in history anyone can join a war clipart pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like global digital volunteers, connected to the ukraine russia, official from check You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
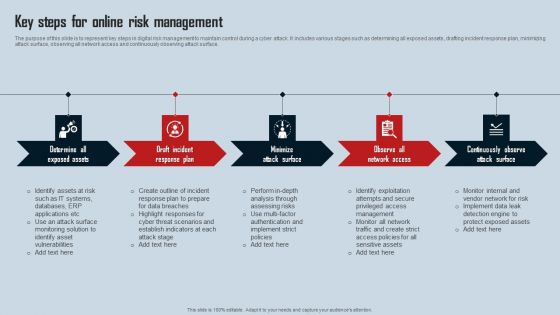
Key Steps For Online Risk Management Ideas PDF
The purpose of this slide is to represent key steps in digital risk management to maintain control during a cyber attack. It includes various stages such as determining all exposed assets, drafting incident response plan, minimizing attack surface, observing all network access and continuously observing attack surface. Presenting Key Steps For Online Risk Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Draft Incident Response Plan, Minimize Attack Surface, Observe All Network Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
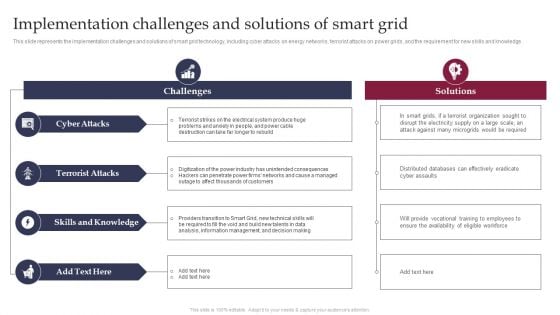
Smart Grid Technology Implementation Challenges And Solutions Designs PDF
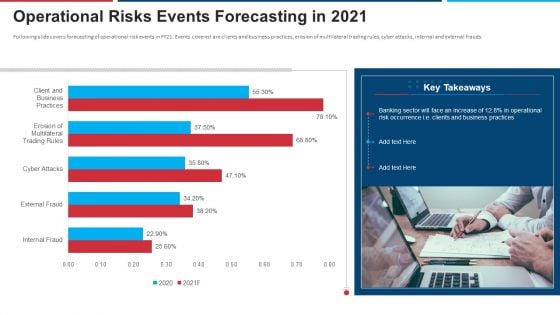
Mitigation Strategies For Operational Threat Operational Risks Events Forecasting In 2021 Ppt Infographic Template Microsoft PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver and pitch your topic in the best possible manner with this mitigation strategies for operational threat operational risks events forecasting in 2021 ppt infographic template microsoft pdf. Use them to share invaluable insights on banking, operational risk, occurrence, business and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
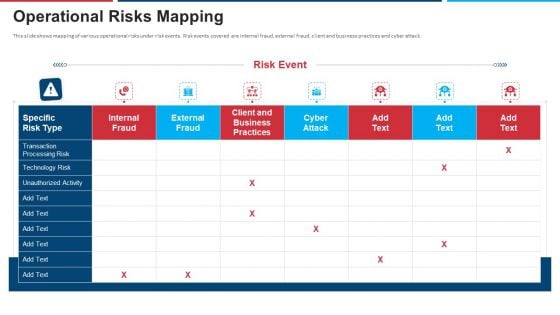
Mitigation Strategies For Operational Threat Operational Risks Mapping Ppt File Graphics PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver and pitch your topic in the best possible manner with this mitigation strategies for operational threat operational risks mapping ppt file graphics pdf. Use them to share invaluable insights on technology risk, transaction processing risk, unauthorized activity, business practices and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf
This slide outlines the drawbacks of the sidechain blockchain network. The purpose of this slide is to highlight some disadvantages of sidechain blockchain technology, including security risks, centralization, interoperability, complexity, and regulatory uncertainty. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Limitations Sidechain Blockchain Different Architectures Of Blockchain Professional Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the drawbacks of the sidechain blockchain network. The purpose of this slide is to highlight some disadvantages of sidechain blockchain technology, including security risks, centralization, interoperability, complexity, and regulatory uncertainty.
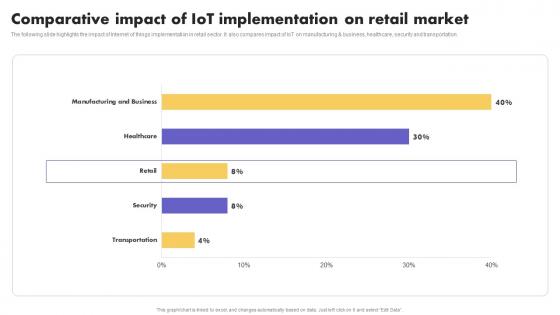
IoT Application In Global Comparative Impact Of IoT Implementation Guidelines Pdf
The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation. Create an editable IoT Application In Global Comparative Impact Of IoT Implementation Guidelines Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. IoT Application In Global Comparative Impact Of IoT Implementation Guidelines Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation
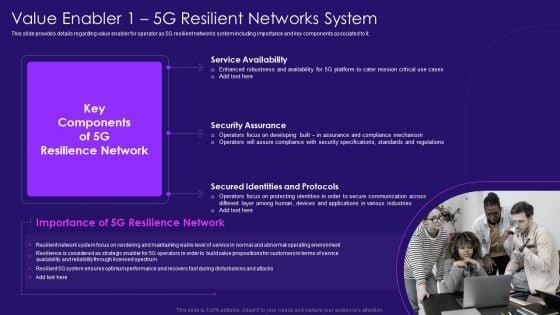
Value Enabler 1 5G Resilient Networks System 5G Network Architecture Instructions Sample PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. Presenting Value Enabler 1 5G Resilient Networks System 5G Network Architecture Instructions Sample PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Service Availability, Security Assurance, Secured Identities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
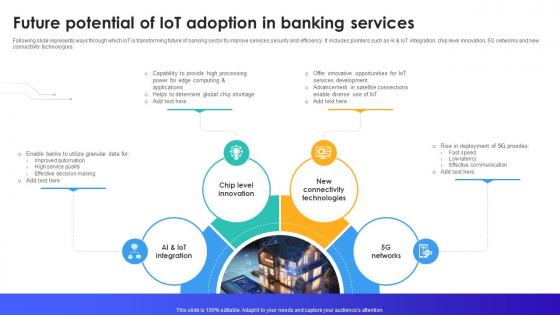
Future Potential Of IoT Adoption In Banking Services IoT In Banking For Digital Future IoT SS V
Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies. There are so many reasons you need a Future Potential Of IoT Adoption In Banking Services IoT In Banking For Digital Future IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies.

Web App Firewall Services IT Impact Of Web Application Firewall Sample PDF
This slide represents the Web Application Firewall deployment pricing, and it covers the price list for resource types such as bot control, requests, and management. Deliver an awe inspiring pitch with this creative web app firewall services it impact of web application firewall sample pdf bundle. Topics like reduced, security expenses, revenue can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
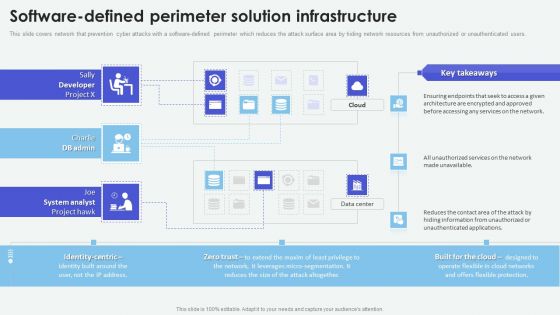
Cloud Based Computing Analysis Software Defined Perimeter Solution Infrastructure Summary PDF
This slide covers network that prevention cyber attacks with a software-defined perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Take your projects to the next level with our ultimate collection of Cloud Based Computing Analysis Software Defined Perimeter Solution Infrastructure Summary PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest
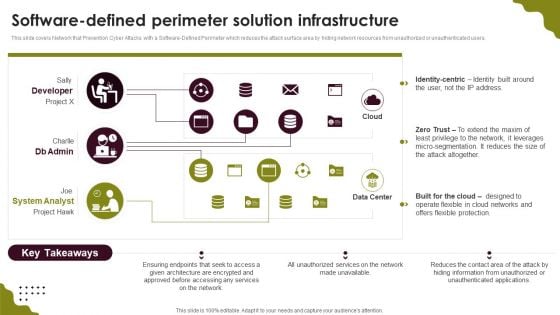
Cloud Computing Scalability Software Defined Perimeter Solution Infrastructure Guidelines PDF
This slide covers Network that Prevention Cyber Attacks with a Software-Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Take your projects to the next level with our ultimate collection of Cloud Computing Scalability Software Defined Perimeter Solution Infrastructure Guidelines PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
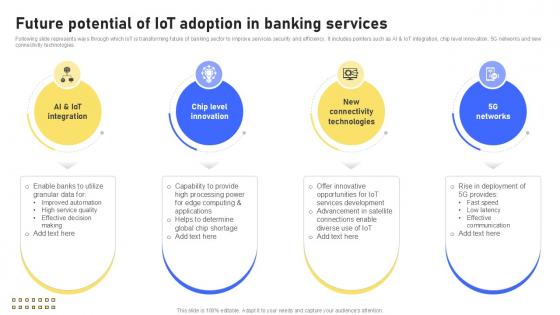
Future Potential Of IoT Adoption Banking Future With IoT Ppt Presentation IoT SS V
Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies. There are so many reasons you need a Future Potential Of IoT Adoption Banking Future With IoT Ppt Presentation IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies.
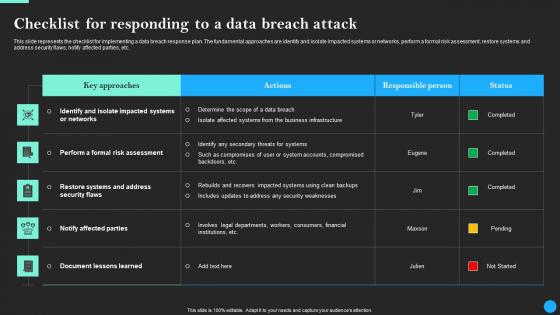
Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.

Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.
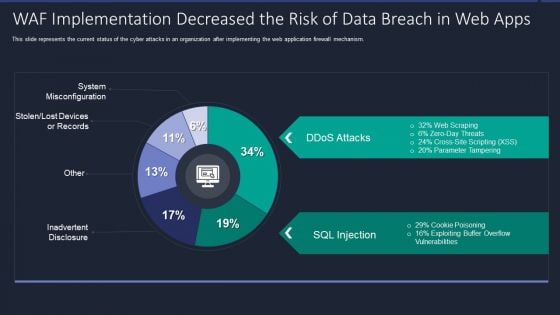
Web App Firewall Services IT WAF Implementation Decreased The Risk Of Data Breach In Web Apps Portrait PDF
This slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver and pitch your topic in the best possible manner with this web app firewall services it waf implementation decreased the risk of data breach in web apps portrait pdf. Use them to share invaluable insights on waf implementation decreased the risk of data breach in web apps and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
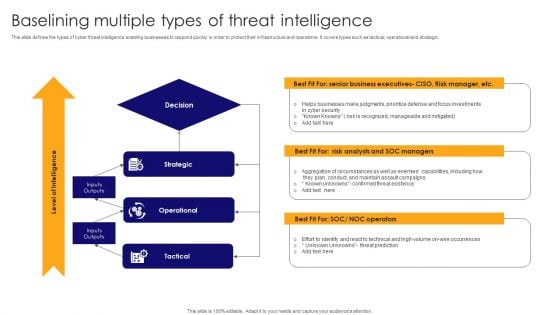
Baselining Multiple Types Of Threat Intelligence Pictures PDF
This slide defines the types of cyber threat intelligence enabling businesses to respond quickly in order to protect their infrastructure and operations. It covers types such as tactical, operational and strategic. Presenting Baselining Multiple Types Of Threat Intelligence Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Strategic, Operational, Tactical . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Impact Of Web Application Firewall Deployment On Client Company WAF Platform Professional PDF
This slide represents the Web Application Firewall deployment pricing, and it covers the price list for resource types such as bot control, requests, and management. Deliver an awe inspiring pitch with this creative Impact Of Web Application Firewall Deployment On Client Company WAF Platform Professional PDF bundle. Topics like Web Application, Revenue, Security Expenses can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
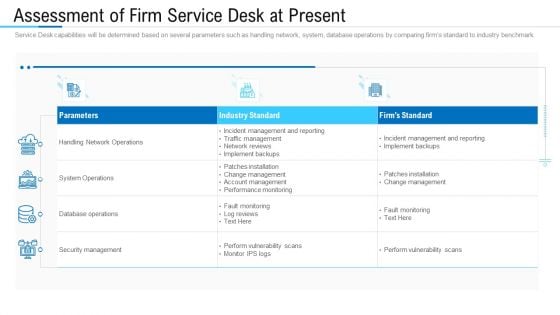
Information Technology Facility Flow Administration Assessment Of Firm Service Desk At Present Brochure PDF
Service Desk capabilities will be determined based on several parameters such as handling network, system, database operations by comparing firms standard to industry benchmark. Deliver and pitch your topic in the best possible manner with this information technology facility flow administration assessment of firm service desk at present brochure pdf. Use them to share invaluable insights on network operations, security management, database operations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Technology Facility Maintenance And Provider Assessment Of Firm Service Desk At Present Brochure PDF
Service Desk capabilities will be determined based on several parameters such as handling network, system, database operations by comparing firms standard to industry benchmark. Deliver an awe inspiring pitch with this creative technology facility maintenance and provider assessment of firm service desk at present brochure pdf bundle. Topics like system operations, security management, performance monitoring, network reviews, database operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

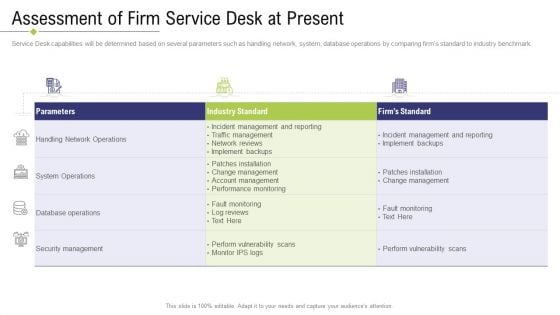
Assessment Of Firm Service Desk At Present Ppt Professional Files PDF
Service Desk capabilities will be determined based on several parameters such as handling network, system, database operations by comparing firms standard to industry benchmark. Deliver and pitch your topic in the best possible manner with this assessment of firm service desk at present ppt professional files pdf. Use them to share invaluable insights on database operations, security management, network operations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
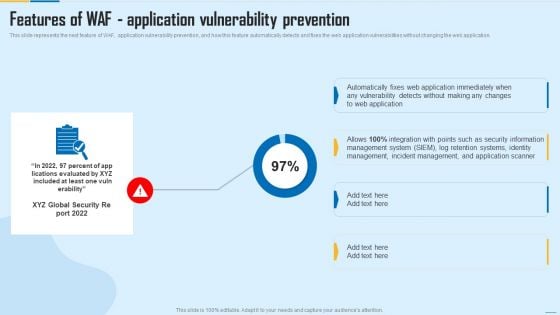
Features Of WAF Application Vulnerability Prevention WAF Platform Designs PDF
This slide represents the next feature of WAF, application vulnerability prevention, and how this feature automatically detects and fixes the web application vulnerabilities without changing the web application. Deliver and pitch your topic in the best possible manner with this Features Of WAF Application Vulnerability Prevention WAF Platform Designs PDF. Use them to share invaluable insights on Management System, Incident Management, Security Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Facilities Governance Assessment Of Firm Service Desk At Present Slides PDF
Service Desk capabilities will be determined based on several parameters such as handling network, system, database operations by comparing firms standard to industry benchmark. Deliver an awe inspiring pitch with this creative information technology facilities governance assessment of firm service desk at present slides pdf bundle. Topics like performance monitoring, implement backups, security management, database operations, industry standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
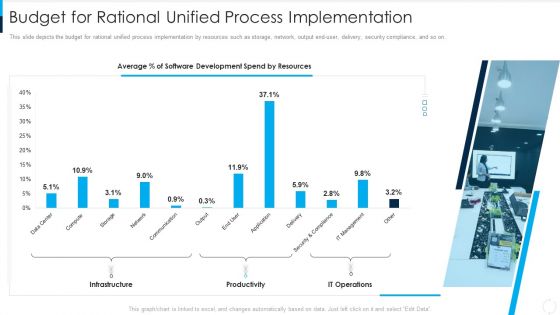
RUP Model Budget For Rational Unified Process Implementation Ppt Outline Layout PDF
This slide depicts the budget for rational unified process implementation by resources such as storage, network, output end-user, delivery, security compliance, and so on. Deliver an awe inspiring pitch with this creative rup model budget for rational unified process implementation ppt outline layout pdf bundle. Topics like infrastructure, productivity, it operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
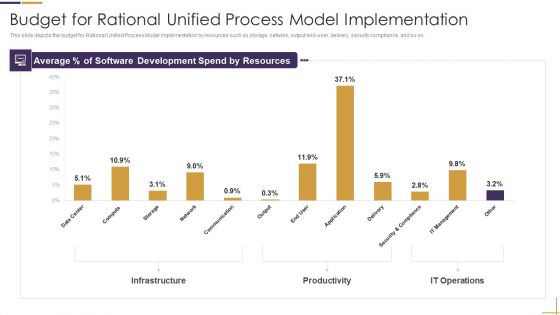
RUP Model Budget For Rational Unified Process Model Implementation Ppt Styles Inspiration PDF
This slide depicts the budget for Rational Unified Process Model implementation by resources such as storage, network, output end-user, delivery, security compliance, and so on. Deliver an awe inspiring pitch with this creative rup model budget for rational unified process model implementation ppt styles inspiration pdf bundle. Topics like infrastructure, productivity, it operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
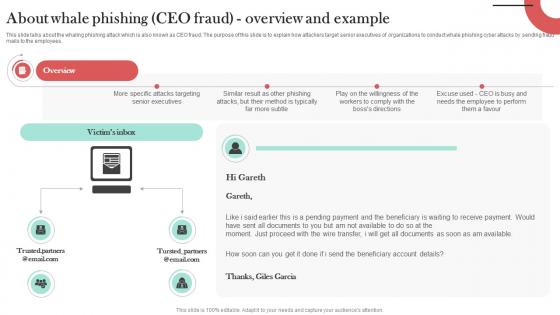
About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT
This slide talks about the whaling phishing attack which is also known as CEO fraud. The purpose of this slide is to explain how attackers target senior executives of organizations to conduct whale phishing cyber attacks by sending fraud mails to the employees. Find highly impressive About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide talks about the whaling phishing attack which is also known as CEO fraud. The purpose of this slide is to explain how attackers target senior executives of organizations to conduct whale phishing cyber attacks by sending fraud mails to the employees.
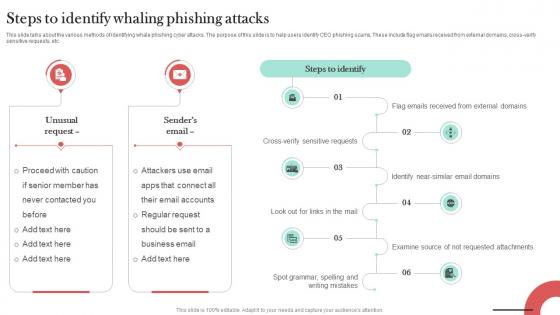
Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT
This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc.

Empowering The Future Strategies To Reduce Cybersecurity Concerns In IoT SS V
This slide exhibits key cybersecurity concerns solving methods for IoT-enabled smart grid. These strategies include multiple authentication, employee training, password strength, and operating system protection. Are you searching for a Empowering The Future Strategies To Reduce Cybersecurity Concerns In IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Empowering The Future Strategies To Reduce Cybersecurity Concerns In IoT SS V from Slidegeeks today. This slide exhibits key cybersecurity concerns solving methods for IoT-enabled smart grid. These strategies include multiple authentication, employee training, password strength, and operating system protection.
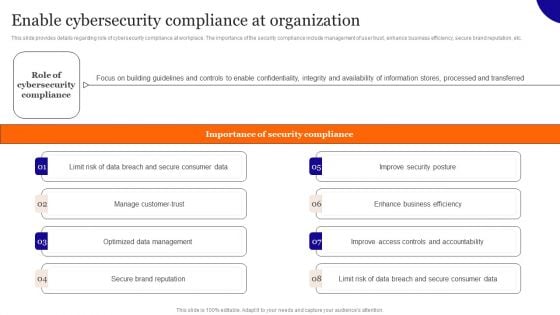
Enable Cybersecurity Compliance At Organization Mockup PDF
This slide provides details regarding role of cybersecurity compliance at workplace. The importance of the security compliance include management of user trust, enhance business efficiency, secure brand reputation, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Enable Cybersecurity Compliance At Organization Mockup PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates


 Continue with Email
Continue with Email

 Home
Home


































