Employee Cyber Security
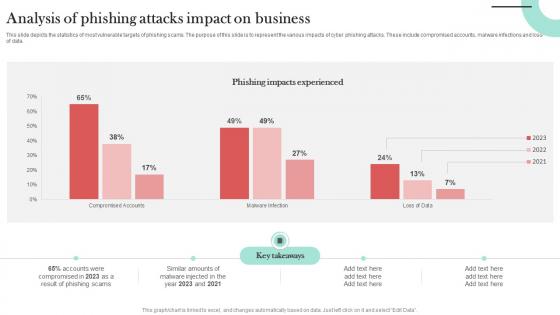
Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT
This slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data. If you are looking for a format to display your unique thoughts, then the professionally designed Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data.

Select Cybersecurity Training Program Courses Ppt PowerPoint Presentation File Styles PDF
The following slide showcases the best cybersecurity training courses to educate employees and minimize the possibility of cyber-attacks. It includes cloud, disaster recovery, hardware, information security programs, duration, mode and cost Get a simple yet stunning designed Select Cybersecurity Training Program Courses Ppt PowerPoint Presentation File Styles PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Select Cybersecurity Training Program Courses Ppt PowerPoint Presentation File Styles PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
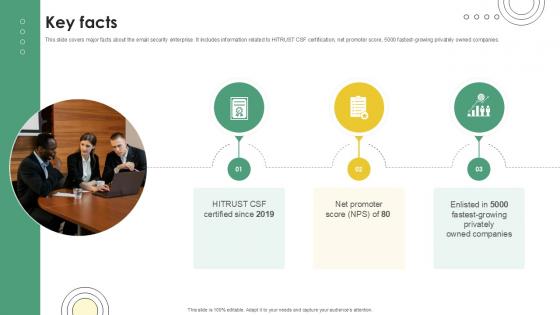
Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint
This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies. If you are looking for a format to display your unique thoughts, then the professionally designed Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies.

Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution. If you are looking for a format to display your unique thoughts, then the professionally designed Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution.
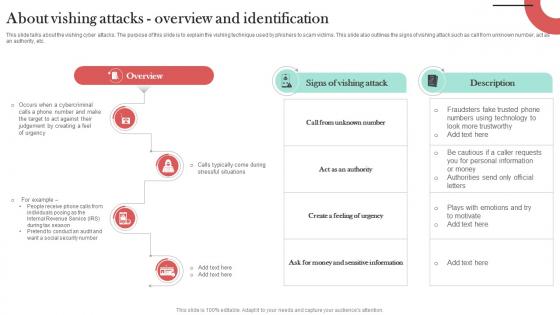
About Vishing Attacks Overview And Identification Man In The Middle Phishing IT
This slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. About Vishing Attacks Overview And Identification Man In The Middle Phishing IT can be your best option for delivering a presentation. Represent everything in detail using About Vishing Attacks Overview And Identification Man In The Middle Phishing IT and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc.
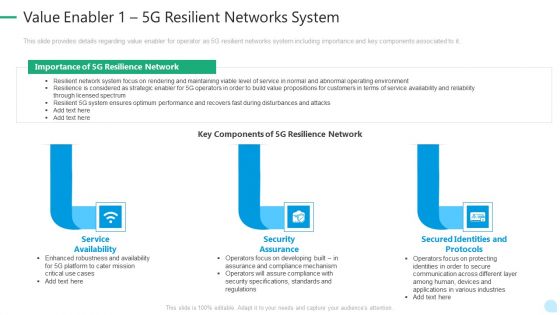
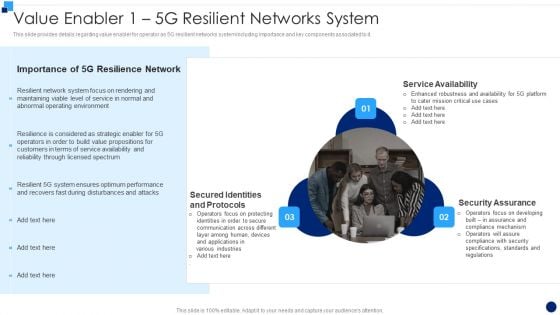
5G Network Technology Value Enabler 1 5G Resilient Networks System Ppt Layouts Diagrams PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a 5g network technology value enabler 1 5g resilient networks system ppt layouts diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like service availability, security assurance, secured identities and protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Value Enabler 1 5G Resilient Networks System Professional PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a Value Enabler 1 5G Resilient Networks System Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service Availability, Security Assurance, Secured Identities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
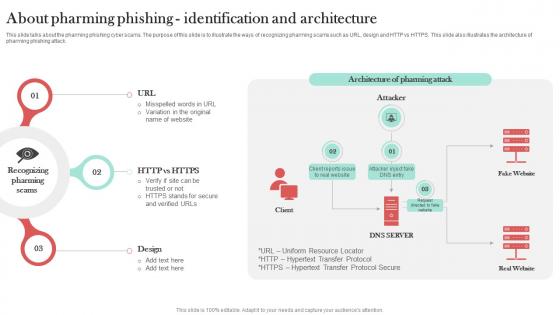
About Pharming Phishing Identification Man In The Middle Phishing IT
This slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give About Pharming Phishing Identification Man In The Middle Phishing IT a try. Our experts have put a lot of knowledge and effort into creating this impeccable About Pharming Phishing Identification Man In The Middle Phishing IT. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack.
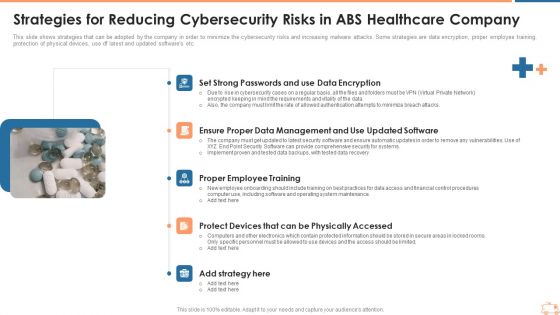
Strategies For Reducing Cybersecurity Risks In ABS Healthcare Company Rules PDF
This slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. Presenting strategies for reducing cybersecurity risks in abs healthcare company rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like set strong passwords and use data encryption, proper employee training, protect devices that can be physically accessed, strategy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies For Reducing Cybersecurity Risks In ABS Healthcare Company Ppt Gallery Background Images PDF
This slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. Deliver an awe inspiring pitch with this creative strategies for reducing cybersecurity risks in abs healthcare company ppt gallery background images pdf bundle. Topics like set strong passwords and use data encryption, ensure proper data management and use updated software, proper employee training, protect devices that can be physically accessed, strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf
Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues. If you are looking for a format to display your unique thoughts, then the professionally designed Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues.

Strategies For Reducing Cybersecurity Risks In Abs Healthcare Company Ppt File Images PDF
This is a strategies for reducing cybersecurity risks in abs healthcare company ppt file images pdf. template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data management, updated software, proper employee training, strategy, procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
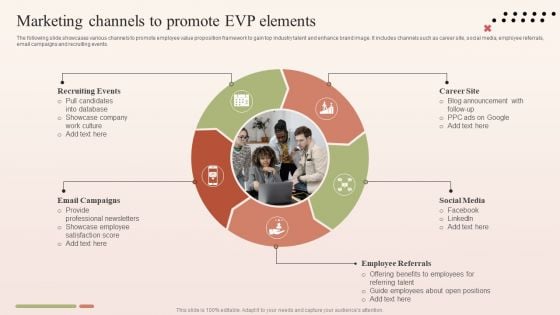
Marketing Channels To Promote EVP Elements Graphics PDF
The following slide showcases various channels to promote employee value proposition framework to gain top industry talent and enhance brand image. It includes channels such as career site, social media, employee referrals, email campaigns and recruiting events. Present like a pro with Marketing Channels To Promote EVP Elements Graphics PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
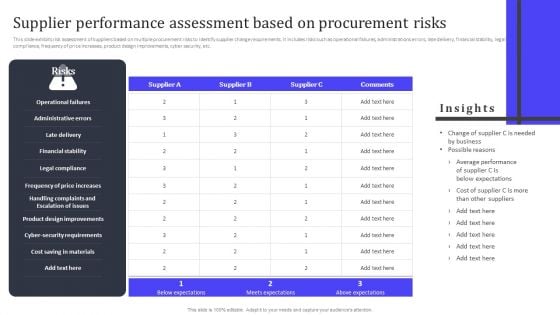
Supplier Performance Assessment Based On Procurement Risks Ppt PowerPoint Presentation File Slides PDF
This slide exhibits risk assessment of suppliers based on multiple procurement risks to identify supplier change requirements. It includes risks such as operational failures, administrations errors, late delivery, financial stability, legal compliance, frequency of price increases, product design improvements, cyber security, etc. Present like a pro with Supplier Performance Assessment Based On Procurement Risks Ppt PowerPoint Presentation File Slides PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
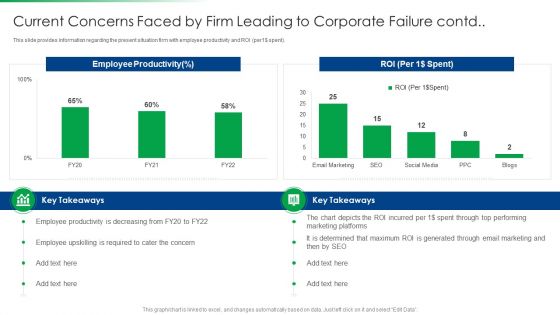
Strawman Project Action Plan Current Concerns Faced By Firm Leading Background PDF
This slide provides information regarding the present situation firm with employee productivity and ROI per1 currency spent. Deliver and pitch your topic in the best possible manner with this strawman project action plan current concerns faced by firm leading background pdf. Use them to share invaluable insights on determined, marketing, email and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
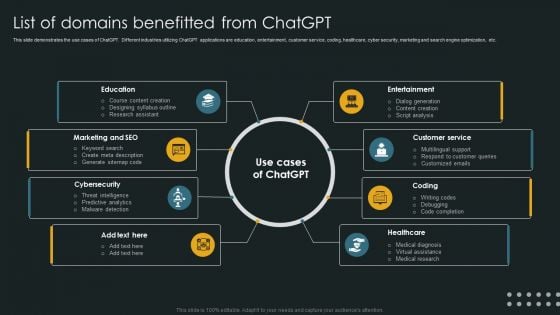
List Of Domains Benefitted From Chatgpt Slides PDF
This slide demonstrates the use cases of ChatGPT. Different industries utilizing ChatGPT applications are education, entertainment, customer service, coding, healthcare, cyber security, marketing and search engine optimization, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give List Of Domains Benefitted From Chatgpt Slides PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable List Of Domains Benefitted From Chatgpt Slides PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
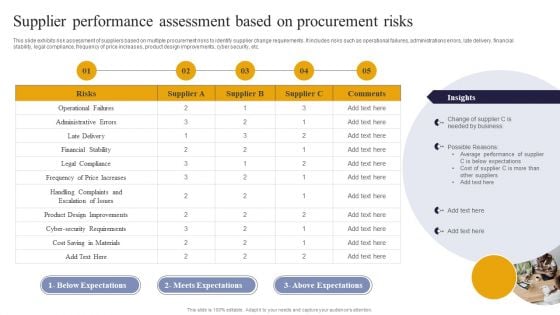
Vendor Performance Analysis And Administration Supplier Performance Assessment Based On Procurement Risks Introduction PDF
This slide exhibits risk assessment of suppliers based on multiple procurement risks to identify supplier change requirements. It includes risks such as operational failures, administrations errors, late delivery, financial stability, legal compliance, frequency of price increases, product design improvements, cyber security, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Vendor Performance Analysis And Administration Supplier Performance Assessment Based On Procurement Risks Introduction PDF can be your best option for delivering a presentation. Represent everything in detail using Vendor Performance Analysis And Administration Supplier Performance Assessment Based On Procurement Risks Introduction PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

HR Process Automation Why Us For Human Resource Automation Proposal Demonstration PDF
Presenting this set of slides with name hr process automation why us for human resource automation proposal demonstration pdf. This is a seven stage process. The stages in this process are our client requires hr automation services for effective manpower management solution which includes routine task email reminders, keeping employee database, and automatic submission of applicant resumes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
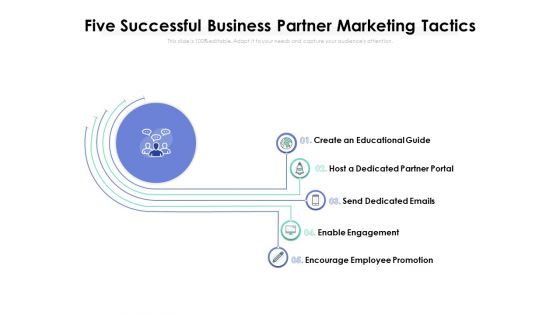
Five Successful Business Partner Marketing Tactics Ppt PowerPoint Presentation File Portrait PDF
Presenting this set of slides with name five successful business partner marketing tactics ppt powerpoint presentation file portrait pdf. This is a five stage process. The stages in this process are create an educational guide, host a dedicated partner portal, send dedicated emails, enable engagement, encourage employee promotion. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
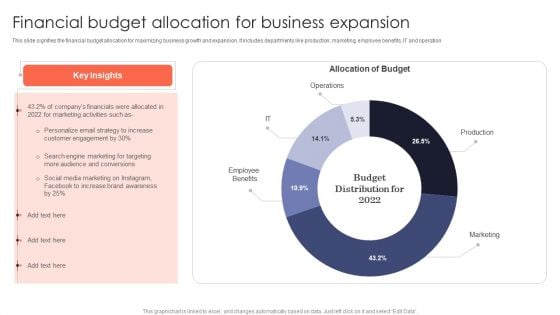
Financial Budget Allocation For Business Expansion Introduction PDF
This slide signifies the financial budget allocation for maximizing business growth and expansion. It includes departments like production, marketing, employee benefits, IT and operation. Deliver an awe inspiring pitch with this creative Financial Budget Allocation For Business Expansion Introduction PDF bundle. Topics like Personalize Email, Customer Engagement, Brand Awareness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Intranet And Mail Workplace Communication Comparative Analysis Icons PDF
This slide depicts a comparative analysis between using intranet and email for workplace communication needs. The basis of differentiation include information segmentation, reach, time-saving and company culture.Presenting Intranet And Mail Workplace Communication Comparative Analysis Icons PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Information Segmentation, internal communication, employee engagement This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
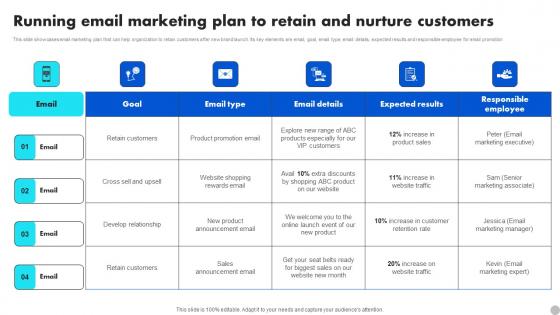
Running Email Marketing Plan To Retain And Nurture Brand Diversification Approach Download Pdf
This slide showcases email marketing plan that can help organization to retain customers after new brand launch. Its key elements are email, goal, email type, email details, expected results and responsible employee for email promotion. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Running Email Marketing Plan To Retain And Nurture Brand Diversification Approach Download Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Running Email Marketing Plan To Retain And Nurture Brand Diversification Approach Download Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. This slide showcases email marketing plan that can help organization to retain customers after new brand launch. Its key elements are email, goal, email type, email details, expected results and responsible employee for email promotion.
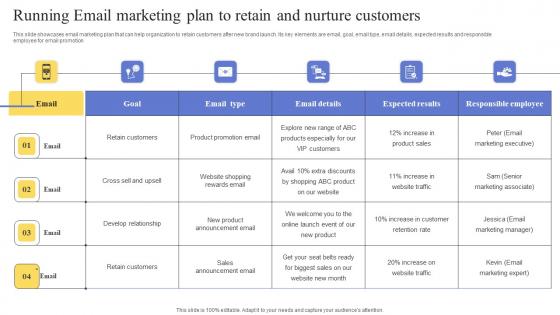
Running Email Marketing Plan To Retain And Nurture Maximizing Revenue Using Infographics Pdf
This slide showcases email marketing plan that can help organization to retain customers after new brand launch. Its key elements are email, goal, email type, email details, expected results and responsible employee for email promotion. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Running Email Marketing Plan To Retain And Nurture Maximizing Revenue Using Infographics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Running Email Marketing Plan To Retain And Nurture Maximizing Revenue Using Infographics Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. This slide showcases email marketing plan that can help organization to retain customers after new brand launch. Its key elements are email, goal, email type, email details, expected results and responsible employee for email promotion.
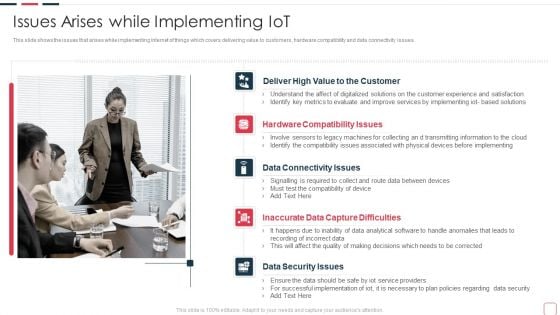
Price Benefit Internet Things Digital Twins Execution After Covid Issues Arises While Implementing Slides PDF
This slide shows the issues that arises while implementing internet of things which covers delivering value to customers, hardware compatibility and data connectivity issues. This is a price benefit internet things digital twins execution after covid issues arises while implementing slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data connectivity issues, inaccurate data capture difficulties, data security issues. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Different Training Formats For Different Organization Levels Brochure PDF
This slide covers the training format at different organization levels including strategy improves the actions of the customers and helps create a cybersafe atmosphere. Presenting different training formats for different organization levels brochure pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like automated security awareness platform, interactive protection simulation, cybersecurity for it online. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
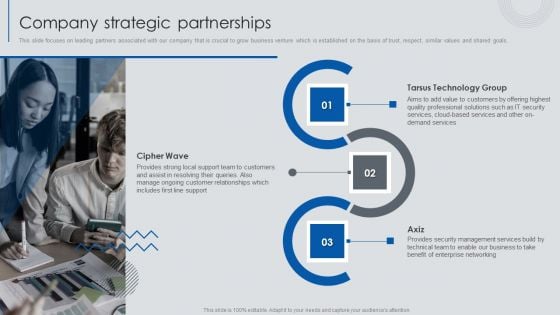
Information Technology Solutions Business Profile Company Strategic Partnerships Structure PDF
This slide focuses on leading partners associated with our company that is crucial to grow business venture which is established on the basis of trust, respect, similar values and shared goals.This is a Information Technology Solutions Business Profile Company Strategic Partnerships Structure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Quality Professional, Security Management, Enterprise Networking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Policy And Processes Email And Chat Policy Objective And Guidelines Themes PDF
This slide represents the email and chat policy, including its objective and general guidelines. It also includes the ways to ensure email security which covers the installation of antivirus and spam filters. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Information Technology Policy And Processes Email And Chat Policy Objective And Guidelines Themes PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Information Technology Solutions Business Profile Offers Diverse Range Of Products Themes PDF
This slide covers the range of products offered by our company such as network operating systems, data security applications, business management software, repair and maintenance, monitoring tools, etc.This is a Information Technology Solutions Business Profile Offers Diverse Range Of Products Themes PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Operating Systems, Productivity Applications, Parts Accessories. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF
The purpose of this slide is to represent a process for cybersecurity digital risk assessment to analyze business threats. It includes various stages such as classifying information assets, evaluating risks, examining risk, observing and reviewing effectiveness and implementing security controls. Presenting Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Classify Information Assets, Evaluate Risk, Examine Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Present like a pro with Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
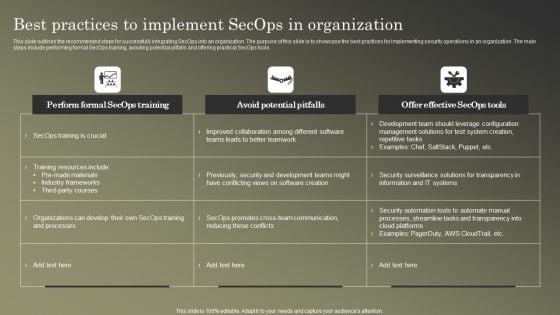
Cybersecurity Operations Cybersecops Best Practices To Implement Secops Information PDF
This slide outlines the recommended steps for successfully integrating SecOps into an organization. The purpose of this slide is to showcase the best practices for implementing security operations in an organization. The main steps include performing formal SecOps training, avoiding potential pitfalls and offering practical SecOps tools. Make sure to capture your audiences attention in your business displays with our gratis customizable Cybersecurity Operations Cybersecops Best Practices To Implement Secops Information PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
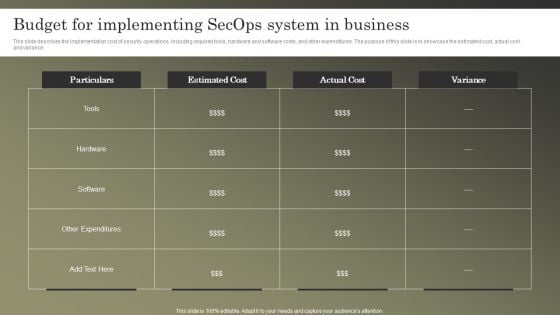
Cybersecurity Operations Cybersecops Budget For Implementing Secops System Elements PDF
This slide describes the implementation cost of security operations, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Boost your pitch with our creative Cybersecurity Operations Cybersecops Budget For Implementing Secops System Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
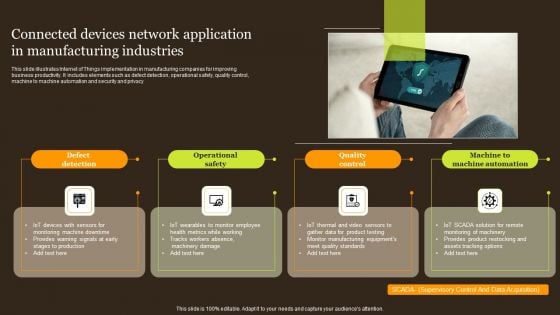
Connected Devices Network Application In Manufacturing Industries Portrait PDF
This slide illustrates Internet of Things implementation in manufacturing companies for improving business productivity. It includes elements such as defect detection, operational safety, quality control, machine to machine automation and security and privacy. Presenting Connected Devices Network Application In Manufacturing Industries Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Defect Detection, Operational Safety, Quality Control . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
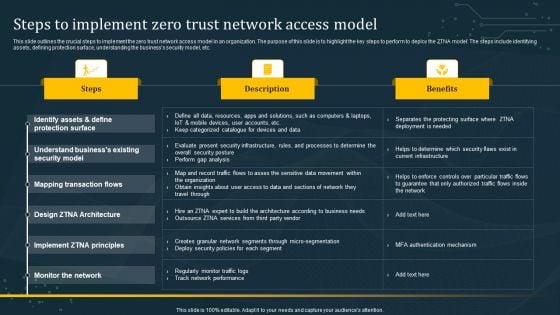
Steps To Implement Zero Trust Network Access Model Graphics PDF
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Steps To Implement Zero Trust Network Access Model Graphics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
Developing 5G Wireless Cellular Network Value Enabler 1 5G Resilient Networks System Clipart PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a Developing 5G Wireless Cellular Network Value Enabler 1 5G Resilient Networks System Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Assurance, Service Availability, Protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
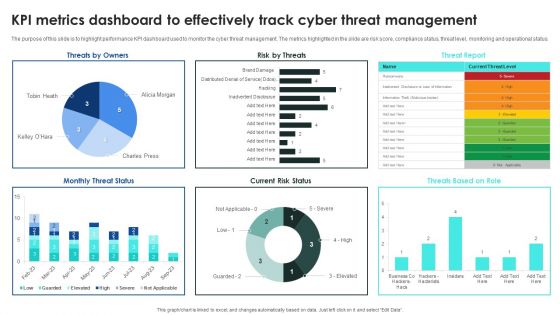
Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Metrics Dashboard To Effectively Track Inspiration PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Welcome to our selection of the Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Metrics Dashboard To Effectively Track Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
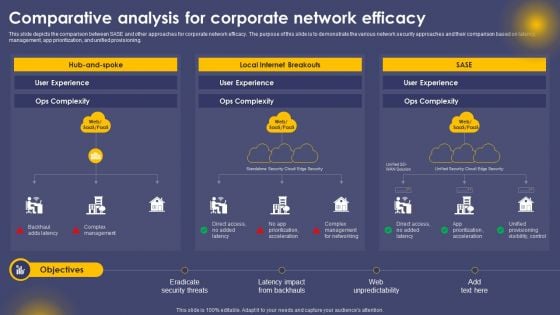
Comparative Analysis For Corporate Network Efficacy Ppt Model Master Slide PDF
This slide depicts the comparison between SASE and other approaches for corporate network efficacy. The purpose of this slide is to demonstrate the various network security approaches and their comparison based on latency, management, app prioritization, and unified provisioning. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Comparative Analysis For Corporate Network Efficacy Ppt Model Master Slide PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
Zero Trust Network Access Performance Tracking Dashboard Template PDF
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. Find a pre-designed and impeccable Zero Trust Network Access Performance Tracking Dashboard Template PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
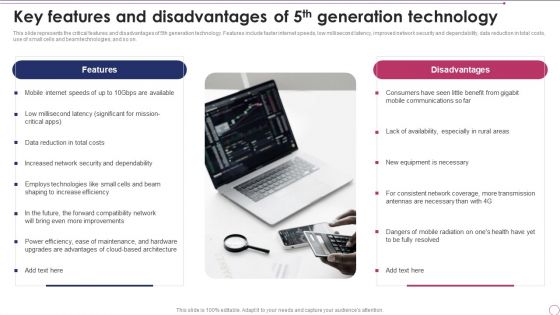
1G To 5G Wireless Communication System IT Key Features And Disadvantages Of 5Th Generation Technology Formats PDF
This slide represents the critical features and disadvantages of 5th generation technology. Features include faster internet speeds, low millisecond latency, improved network security and dependability, data reduction in total costs, use of small cells and beam technologies, and so on. This is a 1G To 5G Wireless Communication System IT Key Features And Disadvantages Of 5Th Generation Technology Formats PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Features, Disadvantages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

1G To 5G Cellular Key Features And Disadvantages Of 5Th Generation Technology Guidelines PDF
This slide represents the critical features and disadvantages of 5th generation technology. Features include faster internet speeds, low millisecond latency, improved network security and dependability, data reduction in total costs, use of small cells and beam technologies, and so on. There are so many reasons you need a 1G To 5G Cellular Key Features And Disadvantages Of 5Th Generation Technology Guidelines PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Key Features And Disadvantages Of 5Th Generation System Wireless Technology Transformation Diagrams PDF
This slide represents the critical features and disadvantages of 5th generation technology. Features include faster internet speeds, low millisecond latency, improved network security and dependability, data reduction in total costs, use of small cells and beam technologies, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Features And Disadvantages Of 5Th Generation System Wireless Technology Transformation Diagrams PDF from Slidegeeks and deliver a wonderful presentation.

Use Case Of Online Risk Management For Health Care Sector Background PDF
This slide represents a use case of digital risk management in health care sector to understand its impact. It includes components like goal, issues faced by hospital, risk mitigation action steps and result. Presenting Use Case Of Online Risk Management For Health Care Sector Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Security Threats, Risk Mitigation Action Steps, Results. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Impeccable Information Technology Facility Assessment Of Firm Service Desk At Present Formats PDF
Service Desk capabilities will be determined based on several parameters such as handling network, system, database operations by comparing firms standard to industry benchmark. This is a impeccable information technology facility assessment of firm service desk at present formats pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like database operations, security management, network operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Why ESO System Center Is Required Ppt PowerPoint Presentation File Skills PDF
This slide covers need of enterprise security operation center. It involves reasons such as continuous monitoring, centralized visibility, reduced cybersecurity costs and ensures better collaboration. Presenting Why ESO System Center Is Required Ppt PowerPoint Presentation File Skills PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Continuous Monitoring, Centralized Visibility, Reduced Cybersecurity Costs. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Communication Infrastructure Services Download PDF
The following slide demonstrates information and communication technology infrastructure services for optimizing output, mitigate internal and external security threat. It includes components such as operations and network management etc. Persuade your audience using this IT Communication Infrastructure Services Download PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Applications, Description, Operations Management . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

ESO System Center Best Practices Ppt PowerPoint Presentation File Structure PDF
This slide covers enterprise security operation center best practices. It involves practices such as setting up right time, align strategy with business goals, leverage best tools and continuously monitor network. Presenting ESO System Center Best Practices Ppt PowerPoint Presentation File Structure PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Practices, Leverage Best Tools, Continuously Monitor Network. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
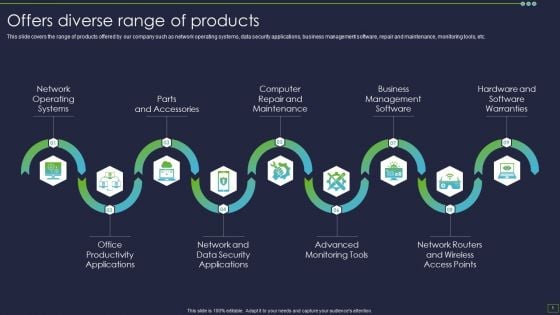
IT Consultancy Services Company Profile Offers Diverse Range Of Products Rules PDF
This slide covers the range of products offered by our company such as network operating systems, data security applications, business management software, repair and maintenance, monitoring tools, etc.This is a IT Consultancy Services Company Profile Offers Diverse Range Of Products Rules PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Operating Systems, Parts Accessories, Computer Repair. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
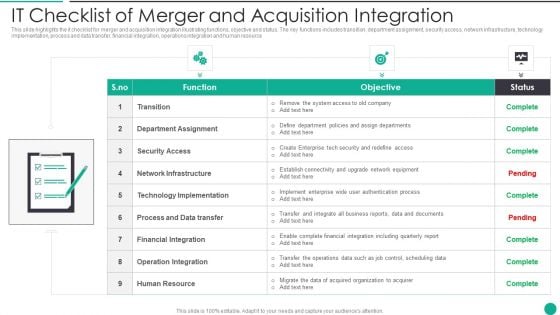
IT Checklist Of Merger And Acquisition Integration Designs PDF
This slide highlights the it checklist for merger and acquisition integration illustrating functions, objective and status. The key functions includes transition, department assignment, security access, network infrastructure, technology implementation, process and data transfer, financial integration, operations integration and human resource Presenting IT Checklist Of Merger And Acquisition Integration Designs PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Department Assignment, Financial Integration, Operation Integration This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
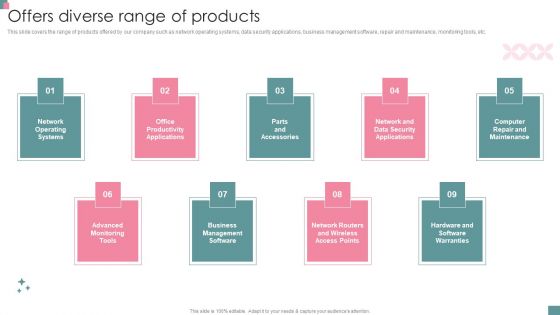
Small Business Venture Company Profile Offers Diverse Range Of Products Clipart PDF
This slide covers the range of products offered by our company such as network operating systems, data security applications, business management software, repair and maintenance, monitoring tools, etc.This is a Small Business Venture Company Profile Offers Diverse Range Of Products Clipart PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Operating Systems, Advanced Monitoring, Management Software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
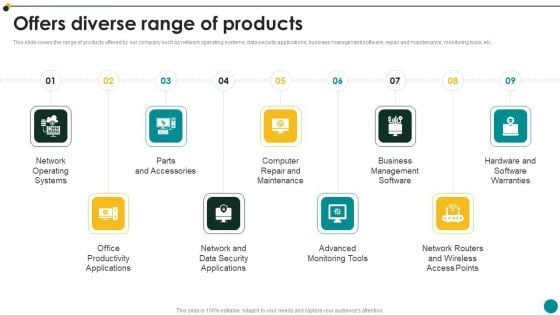
IT Services And Consulting Company Profile Offers Diverse Range Of Products Themes PDF
This slide covers the range of products offered by our company such as network operating systems, data security applications, business management software, repair and maintenance, monitoring tools, etc.This is a IT Services And Consulting Company Profile Offers Diverse Range Of Products Themes PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Parts And Accessories, Business Management Software, Advanced Monitoring You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
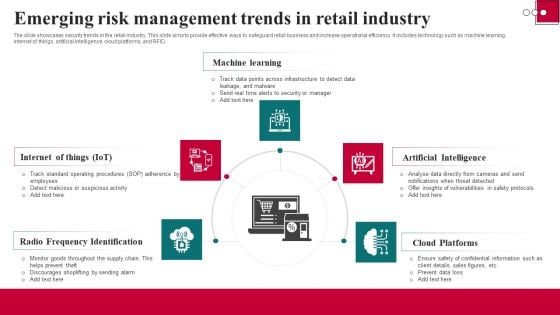
Emerging Risk Management Trends In Retail Industry Background PDF
The slide showcases security trends in the retail industry. This slide aims to provide effective ways to safeguard retail business and increase operational efficiency. It includes technology such as machine learning, internet of things, artificial intelligence, cloud platforms, and RFID. Persuade your audience using this Emerging Risk Management Trends In Retail Industry Background PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Radio Frequency Identification, Artificial Intelligence, Cloud Platforms. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
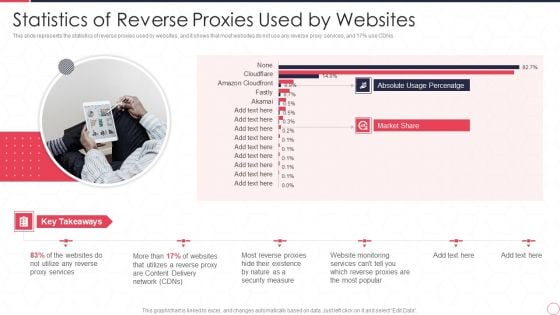
Reverse Proxy Server IT Statistics Of Reverse Proxies Used By Websites Ppt Show Introduction PDF
This slide represents the statistics of reverse proxies used by websites, and it shows that most websites do not use any reverse proxy services, and 17 percent use CDNs. Presenting reverse proxy server it statistics of reverse proxies used by websites ppt show introduction pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like proxy services, content delivery network, security measure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
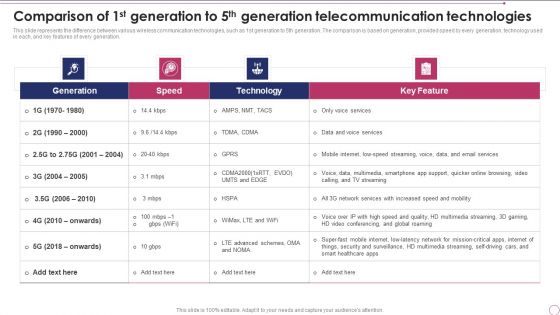
Comparison Of 1St Generation To 5Th Generation Telecommunication Technologies Template PDF
This slide represents the difference between various wireless communication technologies, such as 1st generation to 5th generation. The comparison is based on generation, provided speed by every generation, technology used in each, and key features of every generation. Deliver and pitch your topic in the best possible manner with this Comparison Of 1St Generation To 5Th Generation Telecommunication Technologies Template PDF. Use them to share invaluable insights on Technology, Network Services, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
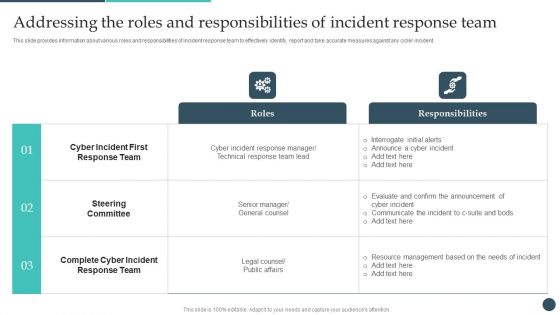
Safety Breach Response Playbook Addressing The Roles And Responsibilities Of Incident Themes PDF
This slide provides information about various roles and responsibilities of incident response team to effectively identify, report and take accurate measures against any cyber incident. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Safety Breach Response Playbook Addressing The Roles And Responsibilities Of Incident Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Safety Breach Response Playbook Addressing The Roles And Responsibilities Of Incident Themes PDF.
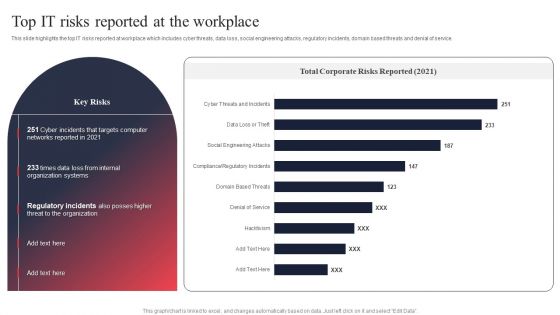
IT System Risk Management Guide Top IT Risks Reported At The Workplace Infographics PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT System Risk Management Guide Top IT Risks Reported At The Workplace Infographics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT System Risk Management Guide Top IT Risks Reported At The Workplace Infographics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
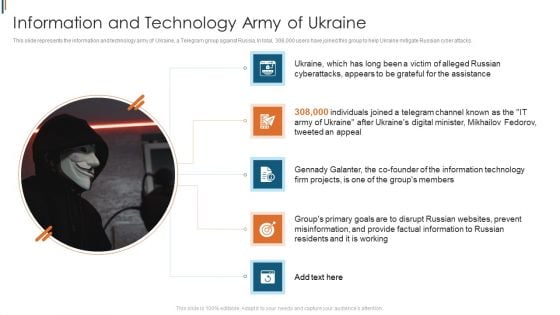
Ukraine Cyberwarfare Information And Technology Army Of Ukraine Topics Pdf
This slide represents the information and technology army of Ukraine, a Telegram group against Russia. In total, 308,000 users have joined this group to help Ukraine mitigate Russian cyber attacks. Presenting ukraine cyberwarfare information and technology army of ukraine topics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like ukraine, which has long been a victim of alleged russian cyberattacks, appears to be grateful for the assistance, gennady galanter, the co founder of the information technology firm projects, is one of the groups members. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
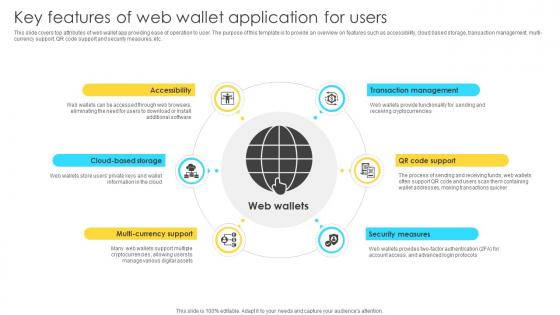
Mastering Blockchain Wallets Key Features Of Web Wallet Application For Users BCT SS V
This slide covers top attributes of web wallet app providing ease of operation to user. The purpose of this template is to provide an overview on features such as accessibility, cloud based storage, transaction management, multi-currency support, QR code support and security measures, etc. Get a simple yet stunning designed Mastering Blockchain Wallets Key Features Of Web Wallet Application For Users BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mastering Blockchain Wallets Key Features Of Web Wallet Application For Users BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers top attributes of web wallet app providing ease of operation to user. The purpose of this template is to provide an overview on features such as accessibility, cloud based storage, transaction management, multi-currency support, QR code support and security measures, etc.

Zero Trust Model Timeline To Implement Zero Trust Network Access
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Model Timeline To Implement Zero Trust Network Access can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Model Timeline To Implement Zero Trust Network Access and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.
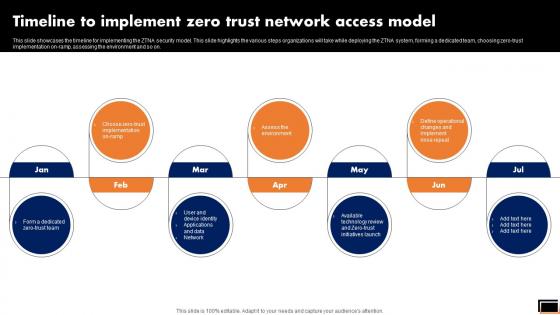
Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.

Zero Trust Network Access Timeline To Implement Zero Trust Network Access Model
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Zero Trust Network Access Timeline To Implement Zero Trust Network Access Model was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Zero Trust Network Access Timeline To Implement Zero Trust Network Access Model This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.


 Continue with Email
Continue with Email

 Home
Home


































