Employee Cyber Security
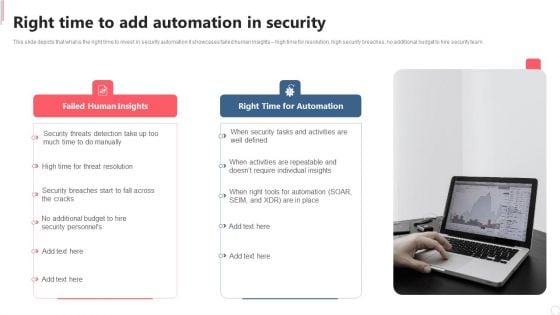
Cyber Security Automation Framework Right Time To Add Automation In Security Microsoft PDF
This slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Want to ace your presentation in front of a live audience Our Cyber Security Automation Framework Right Time To Add Automation In Security Microsoft PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Table Of Contents Cyber Security Administration In Organization Security Sample PDF
This is a table of contents cyber security administration in organization security sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring, financial, assets, security, workforce. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
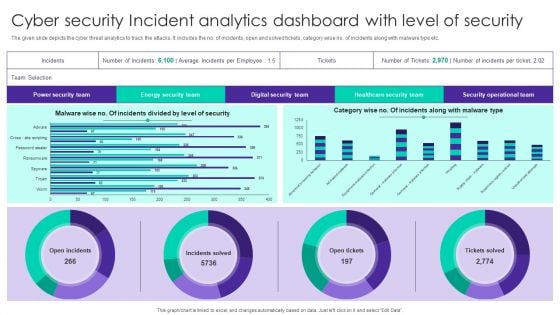
Cyber Security Incident Analytics Dashboard With Level Of Security Ppt Ideas Graphics Tutorials PDF
The given slide depicts the cyber threat analytics to track the attacks. It includes the no. of incidents, open and solved tickets, category wise no. of incidents along with malware type etc. Pitch your topic with ease and precision using this Cyber Security Incident Analytics Dashboard With Level Of Security Ppt Ideas Graphics Tutorials PDF. This layout presents information on Power Security Team, Open Incidents, Incidents Solved, Open Tickets. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
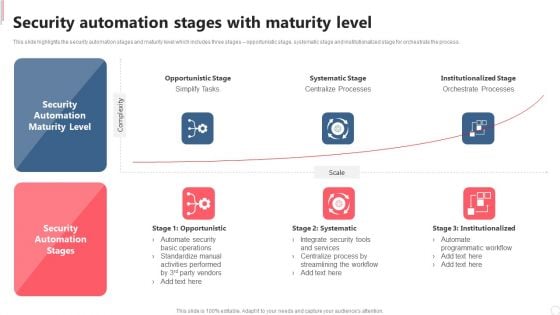
Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF
This slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
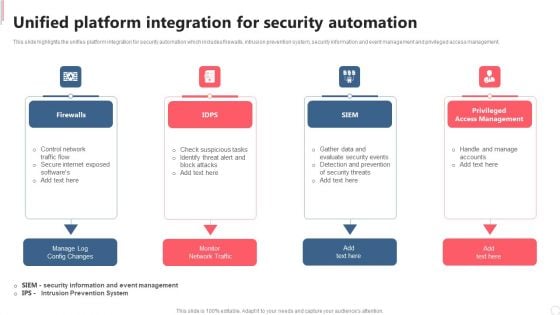
Cyber Security Automation Framework Unified Platform Integration For Security Automation Template PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Present like a pro with Cyber Security Automation Framework Unified Platform Integration For Security Automation Template PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
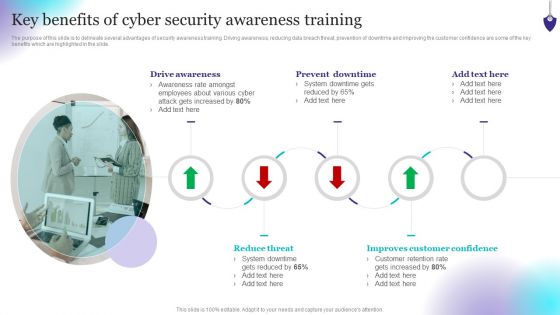
Organizing Security Awareness Key Benefits Of Cyber Security Awareness Training Rules PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Make sure to capture your audiences attention in your business displays with our gratis customizable Organizing Security Awareness Key Benefits Of Cyber Security Awareness Training Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cyber Safety Incident Management Workplace Employee Assistance Program Microsoft PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Presenting cyber safety incident management workplace employee assistance program microsoft pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like clinical services, work and life services, employer services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
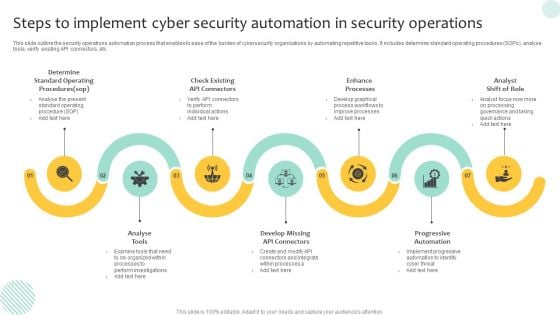
Steps To Implement Cyber Security Automation In Security Operations Demonstration PDF
This slide outline the security operations automation process that enables to ease of the burden of cybersecurity organizations by automating repetitive tasks. It includes determine standard operating procedures SOPs, analyse tools, verify existing API connectors, etc. Presenting Steps To Implement Cyber Security Automation In Security Operations Demonstration PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Progressive Automation, Enhance Processes, Analyse Tools. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
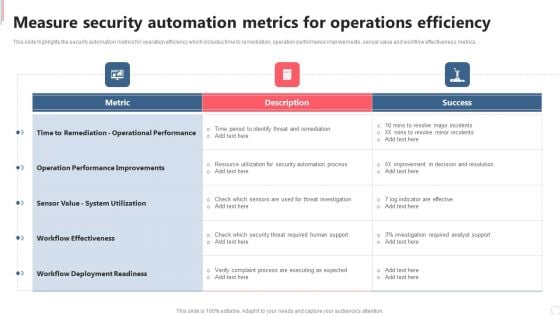
Cyber Security Automation Framework Measure Security Automation Metrics For Operations Efficiency Formats PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Automation Framework Measure Security Automation Metrics For Operations Efficiency Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Safety Lock Cyber Security Global Security Ppt PowerPoint Presentation Complete Deck
Boost your confidence and team morale with this well-structured safety lock cyber security global security ppt powerpoint presentation complete deck. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of fourteen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.
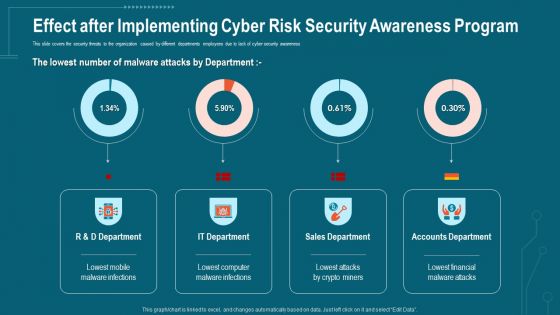
Companys Data Safety Recognition Effect After Implementing Cyber Risk Security Awareness Program Formats PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative companys data safety recognition effect after implementing cyber risk security awareness program formats pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Security Of Employees Devices Microsoft PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Deliver an awe inspiring pitch with this creative desktop security management security of employees devices microsoft pdf bundle. Topics like security of employees devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
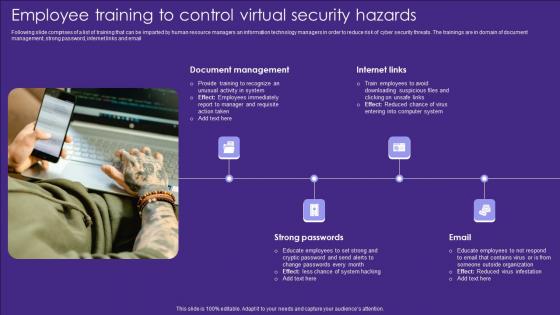
Employee Training To Control Virtual Security Hazards Designs Pdf
Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email Pitch your topic with ease and precision using this Employee Training To Control Virtual Security Hazards Designs Pdf. This layout presents information on Internet Links, Email, Strong Passwords. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email
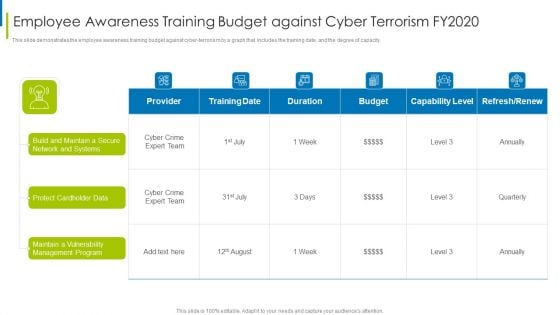
Cyber Terrorism Assault Employee Awareness Training Budget Against Cyber Terrorism FY2020 Inspiration PDF
This slide demonstrates the employee awareness training budget against cyber-terrorism by a graph that includes the training date, and the degree of capacity. Deliver an awe inspiring pitch with this creative cyber terrorism assault employee awareness training budget against cyber terrorism fy2020 inspiration pdf bundle. Topics like Protect Cardholder Data, Maintain A Vulnerability, Management Program can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
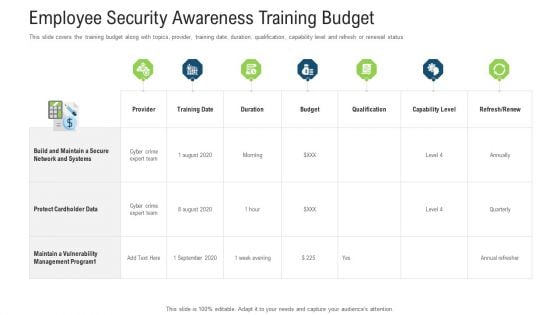
Employee Security Awareness Training Budget Ppt Infographics Shapes PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver an awe inspiring pitch with this creative employee security awareness training budget ppt infographics shapes pdf bundle. Topics like management program, secure network, budget can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
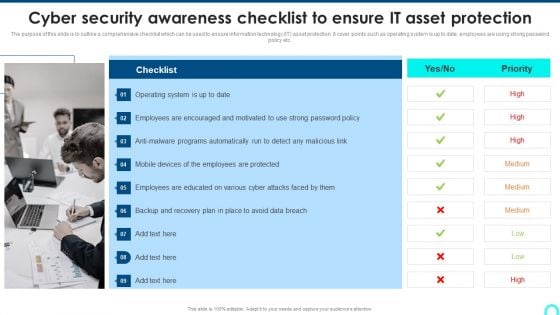
Cyber Security Awareness Checklist To Ensure IT Asset Protection Microsoft PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password.This is a Cyber Security Awareness Checklist To Ensure IT Asset Protection Microsoft PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employees Encouraged, Programs Automatically, Employees Protected. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Assessment Matrix Of Cyber Risks IT Security IT Ppt Ideas Display PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Presenting assessment matrix of cyber risks it security it ppt ideas display pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like industrial, multifamily, data center, retail, health care. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
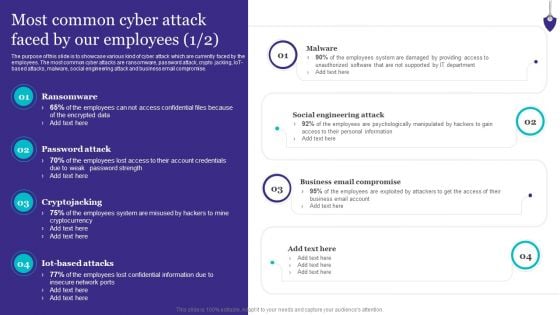
Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF
The Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
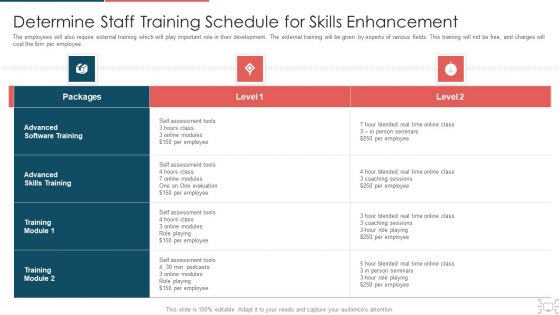
Cyber Security Administration In Organization Determine Staff Training Schedule For Skills Diagrams PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine staff training schedule for skills diagrams pdf bundle. Topics like determine staff training schedule for skills enhancement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
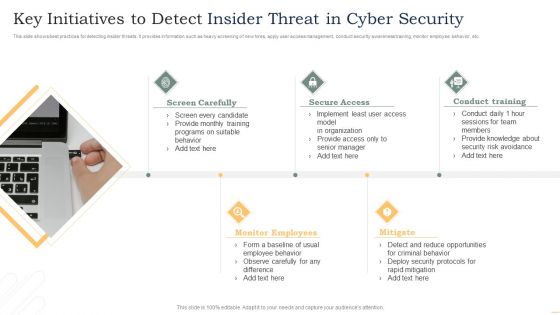
Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF
This slide shows best practices for detecting insider threats. It provides information such as heavy screening of new hires, apply user access management, conduct security awareness training, monitor employee behavior, etc. Presenting Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Screen Carefully, Secure Access, Conduct Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
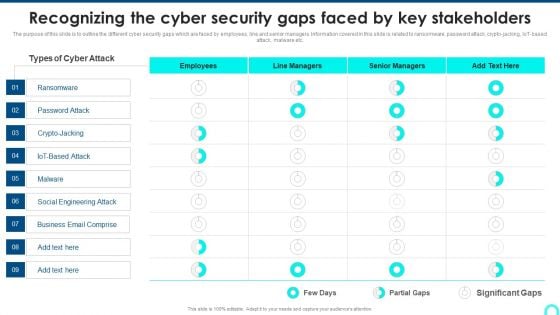
Recognizing The Cyber Security Gaps Faced By Key Stakeholders Portrait PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Deliver and pitch your topic in the best possible manner with this Recognizing The Cyber Security Gaps Faced By Key Stakeholders Portrait PDF. Use them to share invaluable insights on Ransomware, Engineering Attack, Email Comprise and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Prevention Of Information Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre-designed and impeccable Prevention Of Information Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
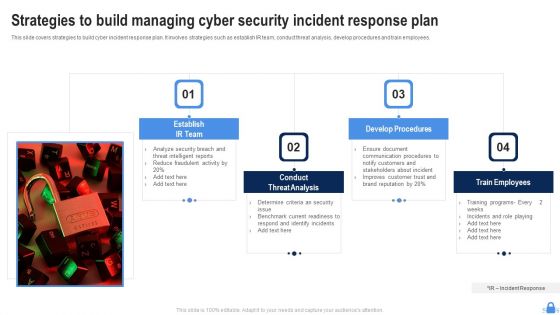
Strategies To Build Managing Cyber Security Incident Response Plan Demonstration PDF
This slide covers strategies to build cyber incident response plan. It involves strategies such as establish IR team, conduct threat analysis, develop procedures and train employees. Persuade your audience using this Strategies To Build Managing Cyber Security Incident Response Plan Demonstration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Establish IR Team, Conduct Threat Analysis, Develop Procedures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Administration In Organization Determine Threat Management Team Structure Information PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting cyber security administration in organization determine threat management team structure information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like determine threat management team structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
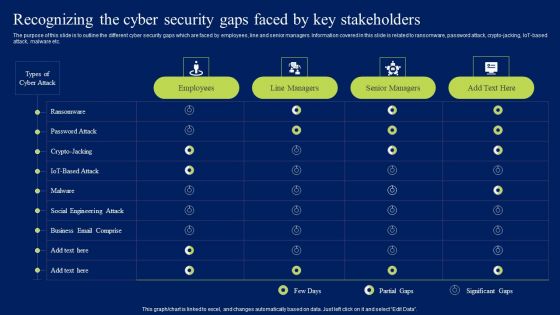
Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Get a simple yet stunning designed Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
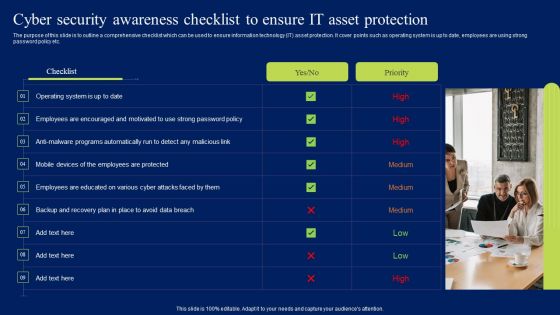
Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Create an editable Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Series Of Cyber Security Attacks Against Ukraine 2022 Hybrid Warfare Cyber Rapid Response Team CRRT Themes PDF
This slide talks about the cyber rapid response team deployed to protect ukraine from russian cyber attacks, including experts from lithuania, croatia, poland, estonia, romania, and the netherlands. Want to ace your presentation in front of a live audience Our Series Of Cyber Security Attacks Against Ukraine 2022 Hybrid Warfare Cyber Rapid Response Team CRRT Themes PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Series Of Cyber Security Attacks Against Ukraine 2022 Shuckworm Continues Cyber Espionage Attacks Against Ukraine Rules PDF
This slide represents the continuous cyber espionage attacks held by the shuckworm group against ukraine. Most of these attacks were phishing emails to spread the malware among devices that could control remotely. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Series Of Cyber Security Attacks Against Ukraine 2022 Shuckworm Continues Cyber Espionage Attacks Against Ukraine Rules PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Series Of Cyber Security Attacks Against Ukraine 2022 Shuckworm Continues Cyber Espionage Attacks Against Ukraine Rules PDF.

Series Of Cyber Security Attacks Against Ukraine 2022 Are There International Laws Establishing Cyber Policies Microsoft PDF
This slide describes the establishment of cyber policies by international laws, including the budapest convention on cybercrime and the united nations group of governmental experts. Create an editable Series Of Cyber Security Attacks Against Ukraine 2022 Are There International Laws Establishing Cyber Policies Microsoft PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Series Of Cyber Security Attacks Against Ukraine 2022 Are There International Laws Establishing Cyber Policies Microsoft PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Series Of Cyber Security Attacks Against Ukraine 2022 Ukraine And Russia Cyber Warfare Impact On Western Countries Designs PDF
This slide represents the ukraine and russia cyber warfare impact on western countries such as the united states, united kingdom, and estonia. This Series Of Cyber Security Attacks Against Ukraine 2022 Ukraine And Russia Cyber Warfare Impact On Western Countries Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Series Of Cyber Security Attacks Against Ukraine 2022 Ukraine And Russia Cyber Warfare Impact On Western Countries Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.
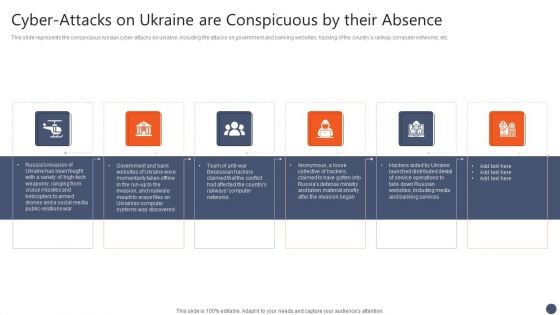
Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF
This slide represents the conspicuous russian cyber attacks on ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. There are so many reasons you need a Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
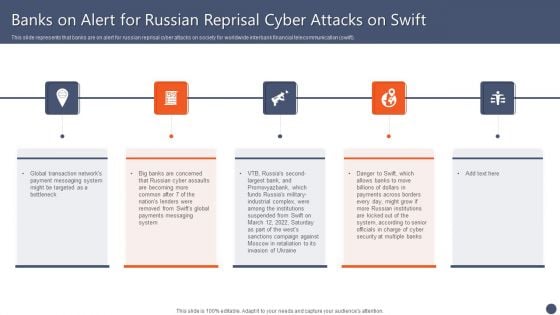
Series Of Cyber Security Attacks Against Ukraine 2022 Banks On Alert For Russian Reprisal Cyber Attacks On Swift Background PDF
This slide represents that banks are on alert for russian reprisal cyber attacks on society for worldwide interbank financial telecommunication swift. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Series Of Cyber Security Attacks Against Ukraine 2022 Banks On Alert For Russian Reprisal Cyber Attacks On Swift Background PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
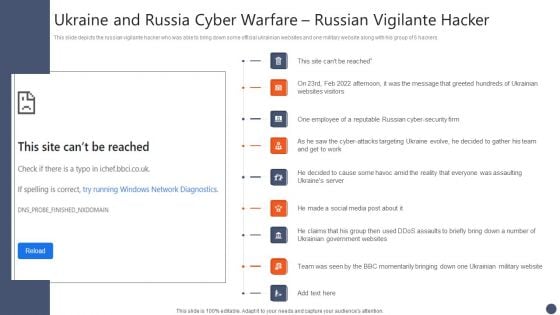
Series Of Cyber Security Attacks Against Ukraine 2022 Ukraine And Russia Cyber Warfare Russian Vigilante Hacker Portrait PDF
This slide depicts the russian vigilante hacker who was able to bring down some official ukrainian websites and one military website along with his group of 6 hackers. Welcome to our selection of the Series Of Cyber Security Attacks Against Ukraine 2022 Ukraine And Russia Cyber Warfare Russian Vigilante Hacker Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
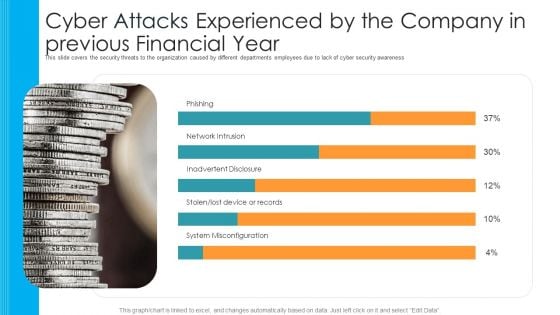
Cyber Attacks Experienced By The Company In Previous Financial Year Hacking Prevention Awareness Training For IT Security Template PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year hacking prevention awareness training for it security template pdf bundle. Topics like phishing, network intrusion, inadvertent disclosure, stolen or lost device or records, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Info Security Assessment Matrix Of Cyber Risks Ppt PowerPoint Presentation Icon Styles PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative info security assessment matrix of cyber risks ppt powerpoint presentation icon styles pdf bundle. Topics like employee devices, webserver network, cloud, retail, data center can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
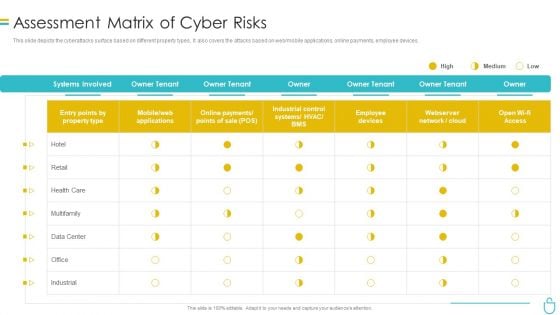
Information Security Assessment Matrix Of Cyber Risks Ppt Infographics Sample PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative information security assessment matrix of cyber risks ppt infographics sample pdf bundle. Topics like employee devices, retail, industrial, owner can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
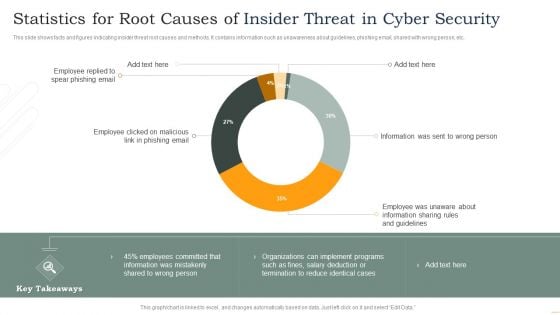
Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF
This slide shows facts and figures indicating insider threat root causes and methods. It contains information such as unawareness about guidelines, phishing email, shared with wrong person, etc. Showcasing this set of slides titled Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF. The topics addressed in these templates are Employee Replied, Spear Phishing Email, Employee Clicked, Phishing Email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Of Employees Devices IT Security IT Ppt Summary Background PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. This is a security of employees devices it security it ppt summary background pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security of employees devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Security Of Employees Devices Ppt Summary Layout Ideas PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Presenting it security security of employees devices ppt summary layout ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security of employees devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Info Security Security Of Employees Devices Ppt PowerPoint Presentation Icon Files PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Presenting info security security of employees devices ppt powerpoint presentation icon files pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security, employees devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
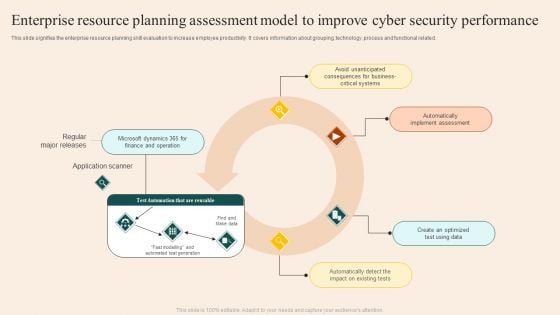
Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF
This slide signifies the enterprise resource planning skill evaluation to increase employee productivity. It covers information about grouping, technology ,process and functional related. Showcasing this set of slides titled Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF. The topics addressed in these templates are Regular Major Releases, Application Scanner, Implement Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
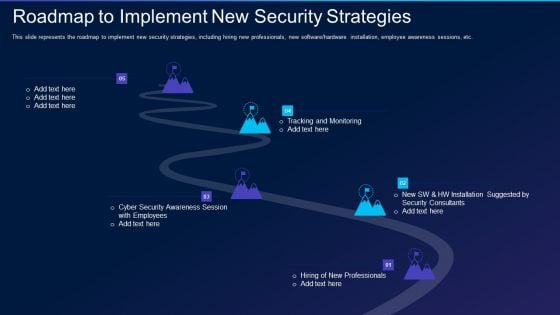
Cyber Exploitation IT Roadmap To Implement New Security Strategies Information PDF
This slide represents the roadmap to implement new security strategies, including hiring new professionals, new software or hardware installation, employee awareness sessions, etc. This is a cyber exploitation it roadmap to implement new security strategies information pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like tracking and monitoring, security consultants, cyber security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
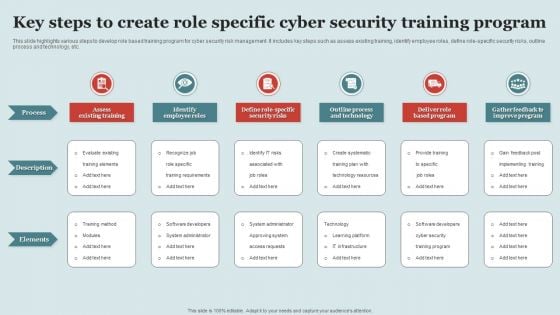
Key Steps To Create Role Specific Cyber Security Training Program Structure PDF
This slide highlights various steps to develop role based training program for cyber security risk management. It includes key steps such as assess existing training, identify employee roles, define role-specific security risks, outline process and technology, etc. Persuade your audience using this Key Steps To Create Role Specific Cyber Security Training Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Process, Description, Elements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Administration In Organization Addressing Threat Management Team Training Schedule Inspiration PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing threat management team training schedule inspiration pdf. Use them to share invaluable insights on probing, unexpected, decision, skills, managerial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cyber Security Cases Action Plan Response Team Icon Ppt PowerPoint Presentation Icon Diagrams PDF
Persuade your audience using this Cyber Security Cases Action Plan Response Team Icon Ppt PowerPoint Presentation Icon Diagrams PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security, Cases Action Plan, Response Team, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
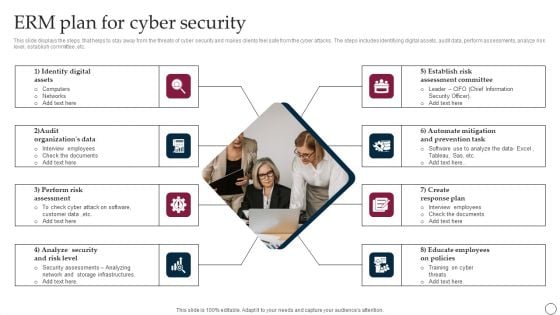
ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF
This slide displays the steps that helps to stay away from the threats of cyber security and makes clients feel safe from the cyber attacks. The steps includes Identifying digital assets, audit data, perform assessments, analyze risk level, establish committee ,etc. Persuade your audience using this ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Establish Risk Assessment Committee, Create Response Plan, Educate Employees On Policies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
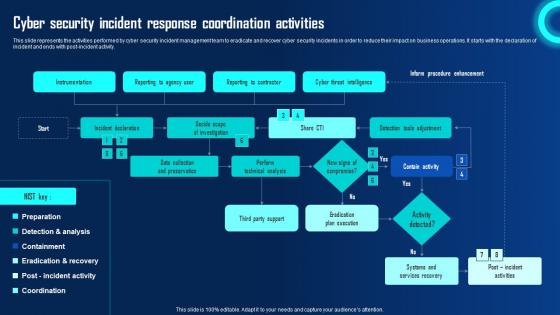
Cyber Security Incident Response Coordination Activities Ppt Powerpoint Presentation File Portfolio Pdf
This slide represents the activities performed by cyber security incident management team to eradicate and recover cyber security incidents in order to reduce their impact on business operations. It starts with the declaration of incident and ends with post incident activity. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Security Incident Response Coordination Activities Ppt Powerpoint Presentation File Portfolio Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the activities performed by cyber security incident management team to eradicate and recover cyber security incidents in order to reduce their impact on business operations. It starts with the declaration of incident and ends with post incident activity.
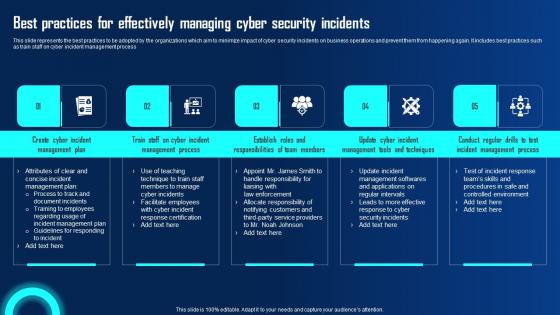
Best Practices For Effectively Managing Cyber Security Ppt Powerpoint Presentation File Model Pdf
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as train staff on cyber incident management process If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Best Practices For Effectively Managing Cyber Security Ppt Powerpoint Presentation File Model Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as train staff on cyber incident management process
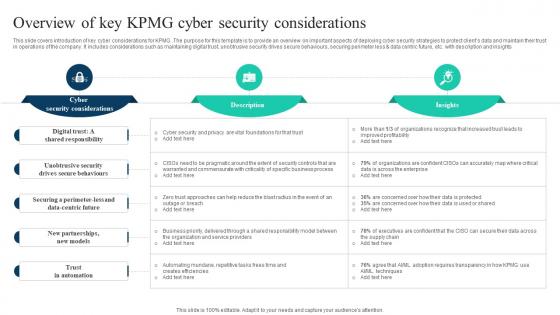
The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V
This slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights Find a pre-designed and impeccable The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights

Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf
This slide represents the emerging trends in cyber attacks faced by the enterprises. It includes details related to cyber attacks experienced by enterprises, top global fraud types and volume of cyber security incidents by sector. Explore a selection of the finest Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents the emerging trends in cyber attacks faced by the enterprises. It includes details related to cyber attacks experienced by enterprises, top global fraud types and volume of cyber security incidents by sector.
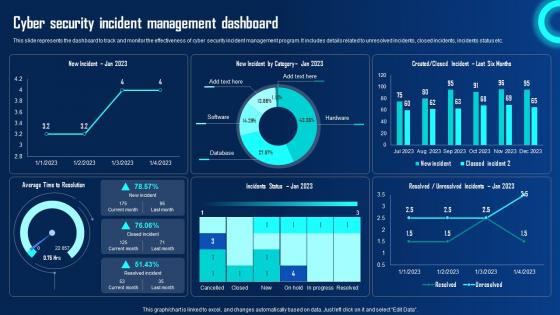
Cyber Security Incident Management Dashboard Ppt Powerpoint Presentation File Ideas Pdf
This slide represents the dashboard to track and monitor the effectiveness of cyber security incident management program. It includes details related to unresolved incidents, closed incidents, incidents status etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Security Incident Management Dashboard Ppt Powerpoint Presentation File Ideas Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Security Incident Management Dashboard Ppt Powerpoint Presentation File Ideas Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the dashboard to track and monitor the effectiveness of cyber security incident management program. It includes details related to unresolved incidents, closed incidents, incidents status etc.

Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf
This slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc. Find highly impressive Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc.
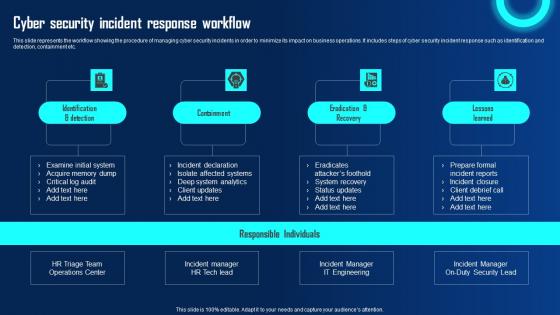
Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf
This slide represents the workflow showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It includes steps of cyber security incident response such as identification and detection, containment etc. This Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the workflow showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It includes steps of cyber security incident response such as identification and detection, containment etc.

Cyber Security Risk Assessment And Management Ppt Powerpoint Presentation File Example File Pdf
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Welcome to our selection of the Cyber Security Risk Assessment And Management Ppt Powerpoint Presentation File Example File Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution.

Cyber Security Incident Response Preparation Ppt Powerpoint Presentation Diagram Templates Pdf
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to activities such as document incident response plan with policies and procedures etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Incident Response Preparation Ppt Powerpoint Presentation Diagram Templates Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to activities such as document incident response plan with policies and procedures etc.
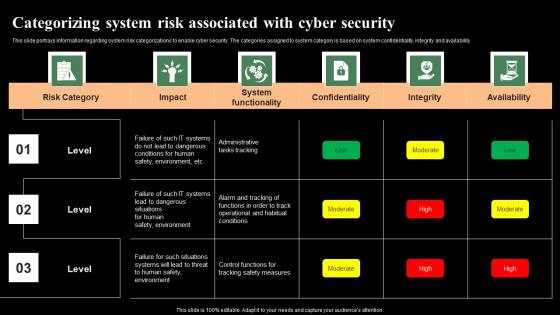
Categorizing System Risk Associated With Cyber Security Monitoring Digital Assets Professional Pdf
This slide portrays information regarding system risk categorizations to enable cyber security. The categories assigned to system category is based on system confidentiality, integrity and availability. Take your projects to the next level with our ultimate collection of Categorizing System Risk Associated With Cyber Security Monitoring Digital Assets Professional Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide portrays information regarding system risk categorizations to enable cyber security. The categories assigned to system category is based on system confidentiality, integrity and availability.

What Is The Cyber Security Role Web Designing User Engagement Rules PDF
Boost your pitch with our creative What Is The Cyber Security Role Web Designing User Engagement Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.
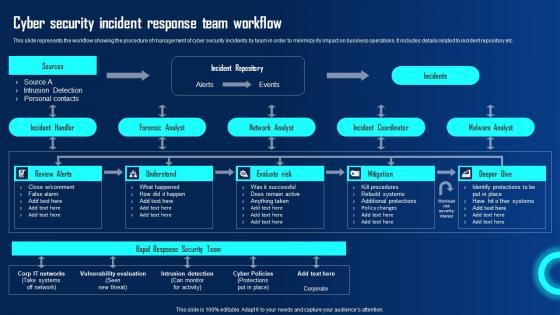
Cyber Security Incident Response Team Workflow Ppt Powerpoint Presentation File Deck Pdf
This slide represents the workflow showing the procedure of management of cyber security incidents by team in order to minimize its impact on business operations. It includes details related to incident repository etc. This modern and well arranged Cyber Security Incident Response Team Workflow Ppt Powerpoint Presentation File Deck Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the workflow showing the procedure of management of cyber security incidents by team in order to minimize its impact on business operations. It includes details related to incident repository etc.
Strategies To Develop Effective Cyber Security Plan Ppt Powerpoint Presentation File Icon Pdf
This slide represents the techniques to be adopted by administration to effectively manage cyber security incidents in order to reduce their impact on business operations. It includes strategies to develop cyber security plan such as establish IR team, conduct threat analysis etc. The Strategies To Develop Effective Cyber Security Plan Ppt Powerpoint Presentation File Icon Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the techniques to be adopted by administration to effectively manage cyber security incidents in order to reduce their impact on business operations. It includes strategies to develop cyber security plan such as establish IR team, conduct threat analysis etc.

Cyber Security Crisis Management Action Plan Timeline Ppt Powerpoint Presentation File Example File Pdf
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. If you are looking for a format to display your unique thoughts, then the professionally designed Cyber Security Crisis Management Action Plan Timeline Ppt Powerpoint Presentation File Example File Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cyber Security Crisis Management Action Plan Timeline Ppt Powerpoint Presentation File Example File Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery.


 Continue with Email
Continue with Email

 Home
Home


































