Employee Cyber Security

CYBER Security Breache Response Strategy Benefits Of Implementing Web Application Firewall Portrait PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Find a pre designed and impeccable CYBER Security Breache Response Strategy Benefits Of Implementing Web Application Firewall Portrait PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
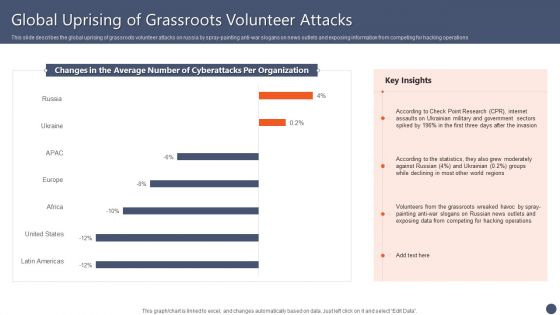
Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF
This slide describes the global uprising of grassroots volunteer attacks on russia by spray-painting anti-war slogans on news outlets and exposing information from competing for hacking operations. Boost your pitch with our creative Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
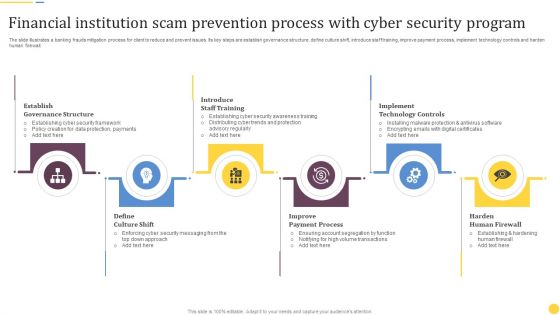
Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF
The slide illustrates a banking frauds mitigation process for client to reduce and prevent issues. Its key steps are establish governance structure, define culture shift, introduce staff training, improve payment process, implement technology controls and harden human firewall. Presenting Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Establish Governance Structure, Introduce Staff Training, Implement Technology Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
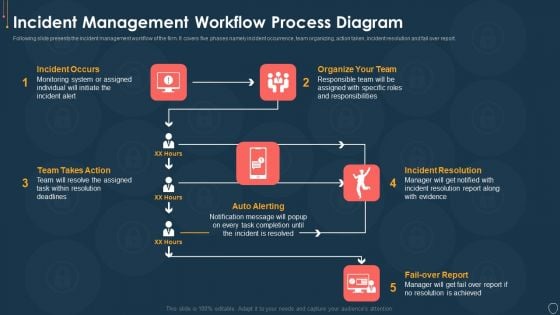
Cyber Security Risk Management Plan Incident Management Workflow Process Diagram Infographics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting cyber security risk management plan incident management workflow process diagram infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like fail over report, incident resolution, organize your team, incident occurs, team takes action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
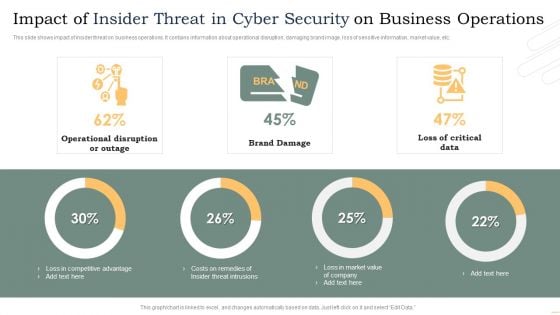
Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF
This slide shows impact of insider threat on business operations. It contains information about operational disruption, damaging brand image, loss of sensitive information, market value, etc. Pitch your topic with ease and precision using this Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF. This layout presents information on Operational Disruption Or Outage, Brand Damage, Loss Critical Data. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Risk Management Plan Threat Identification And Vulnerability Impact Assessment Brochure PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat identification and vulnerability impact assessment brochure pdf. Use them to share invaluable insights on threat agent, affected assets, potential vulnerability, vulnerability ranking, threats to firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CYBER Security Breache Response Strategy Comparative Analysis Of Web Application Firewall Products Slides PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. There are so many reasons you need a CYBER Security Breache Response Strategy Comparative Analysis Of Web Application Firewall Products Slides PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
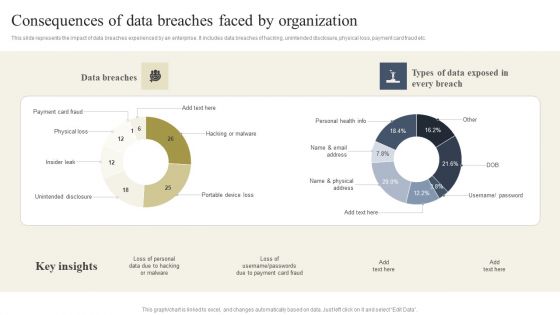
Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Boost your pitch with our creative Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
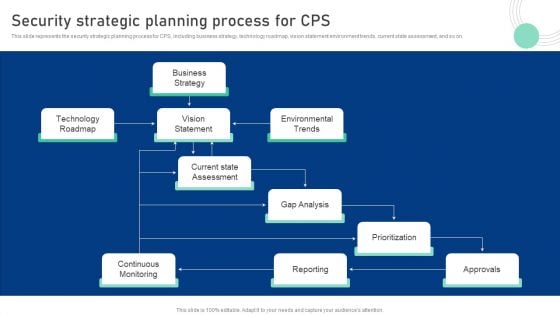
Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Slidegeeks is here to make your presentations a breeze with Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
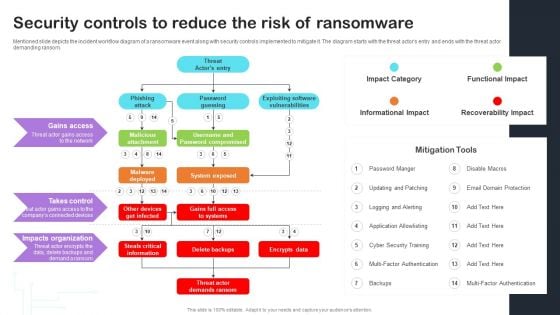
Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Take your projects to the next level with our ultimate collection of Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
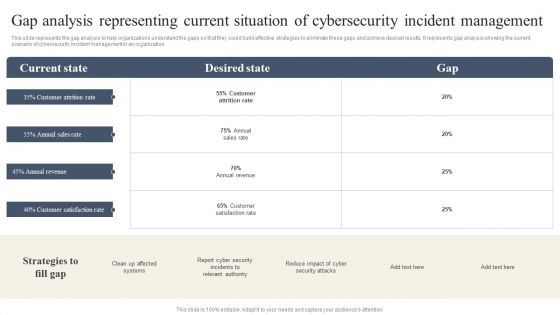
CYBER Security Breache Response Strategy Gap Analysis Representing Current Situation Cybersecurity Incident Professional PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Slidegeeks has constructed CYBER Security Breache Response Strategy Gap Analysis Representing Current Situation Cybersecurity Incident Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
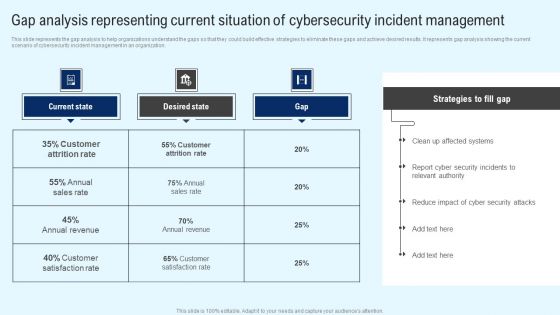
Implementing Cyber Security Incident Gap Analysis Representing Current Situation Ideas PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Retrieve professionally designed Implementing Cyber Security Incident Gap Analysis Representing Current Situation Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
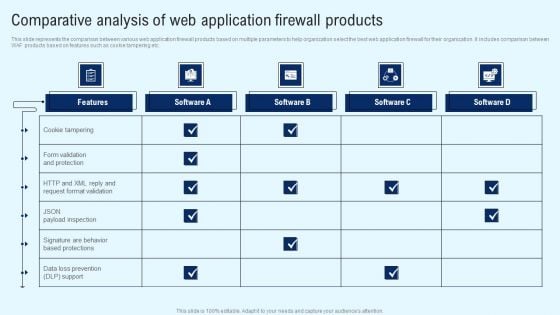
Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Boost your pitch with our creative Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
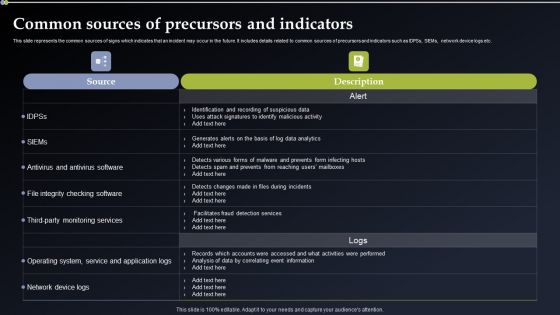
Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. This modern and well arranged Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Deploying Cyber Security Incident Response Administration Ppt PowerPoint Presentation Complete Deck With Slides
Starting a presentation on business is a decision to make. As you think about it, you realize that everything is a decision. Our Deploying Cyber Security Incident Response Administration Ppt PowerPoint Presentation Complete Deck With Slides will make all your business tasks and decisions a bit easier, with its emphasis on planning. The sixty nine slide complete deck allows you to present the daily challenges of business in your own way to your team, key stakeholders, and external vendors etc. With each slide being 100 percent editable and customizable, you may decide to fiddle around with the design or the content ready nature to arrive at your own, presentation on a topic of your choosing. Download now.

Developing Cyber Security Threat Awareness Staff Training Program Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the seventy eight slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.
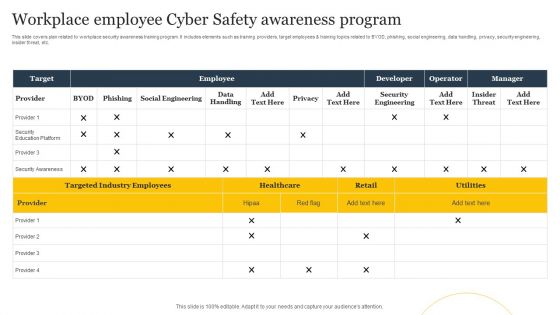
Workplace Employee Cyber Safety Awareness Program Ppt Layouts Slide Portrait PDF
This slide covers plan related to workplace security awareness training program. It includes elements such as training providers, target employees and training topics related to BYOD, phishing, social engineering, data handling, privacy, security engineering, insider threat, etc. Pitch your topic with ease and precision using this Workplace Employee Cyber Safety Awareness Program Ppt Layouts Slide Portrait PDF. This layout presents information on Employee, Target, Developer. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
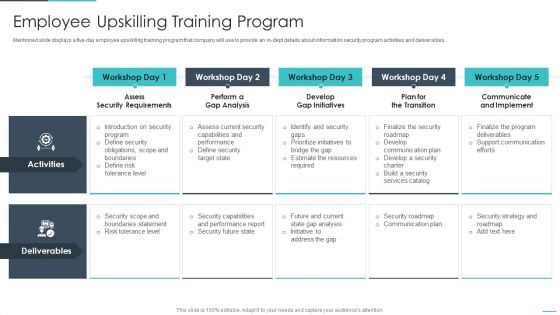
Handling Cyber Threats Digital Era Employee Upskilling Training Program Ppt Professional Master Slide
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. This is a handling cyber threats digital era employee upskilling training program ppt professional master slide template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assess security requirements, perform a gap analysis, develop gap initiatives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Security Of Employees Devices Ppt Styles Graphic Images PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. This is a cybersecurity security of employees devices ppt styles graphic images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security of employees devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
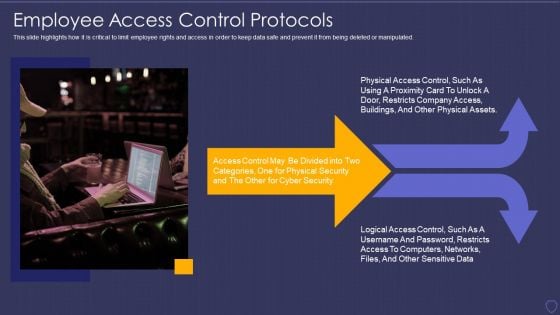
Global Cyber Terrorism Incidents On The Rise IT Employee Access Control Protocols Download PDF
This slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated. Presenting global cyber terrorism incidents on the rise it employee access control protocols download pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like employee access control protocols. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Management Model For Data Security Online And Onsite Training Schedule For Employee Rules PDF
This slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Online And Onsite Training Schedule For Employee Rules PDF bundle. Topics like Course Type, Training Mode, Training Duration, Employee can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Info Security Employee Awareness Training Budget For FY2022 Ppt PowerPoint Presentation File Graphics Download PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Deliver an awe inspiring pitch with this creative info security employee awareness training budget for fy2022 ppt powerpoint presentation file graphics download pdf bundle. Topics like build and maintain, secure network and system, protect cardholder data, maintain a vulnerability, management program can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
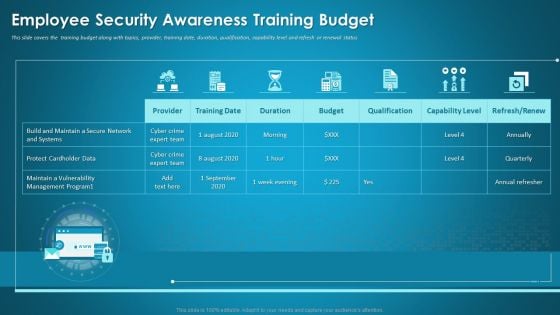
Organizational Network Staff Learning Employee Security Awareness Training Budget Information PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver and pitch your topic in the best possible manner with this organizational network staff learning employee security awareness training budget information pdf. Use them to share invaluable insights on capability level, budget, duration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF
This slide covers employee questionnaire to assess cybersecurity training program effectiveness. It involves questions to determine trainer effectiveness in teaching, knowledge and skills of trainer and details about training organization. Showcasing this set of slides titled Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF. The topics addressed in these templates are Good Knowledge, Cyberattacks And Methods, Awareness Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Employee Awareness Training Budget For FY2020 IT Security IT Ppt Show Slides PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. This is a employee awareness training budget for fy2020 it security it ppt show slides pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like maintain, vulnerability, management, secure, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Terrorism Assault Peroration Of Cyber Terrorism Attacks Sample PDF
This slide explains the conclusion or peroration of cyber terrorism and how it is different from information warfare as it targets civilians rather than operations. This is a cyber terrorism assault peroration of cyber terrorism attacks sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitored closely, implemented and every aspect, ideological gain oriented You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizing Security Awareness Security Awareness Training Program Challenges Formats PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Organizing Security Awareness Security Awareness Training Program Challenges Formats PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
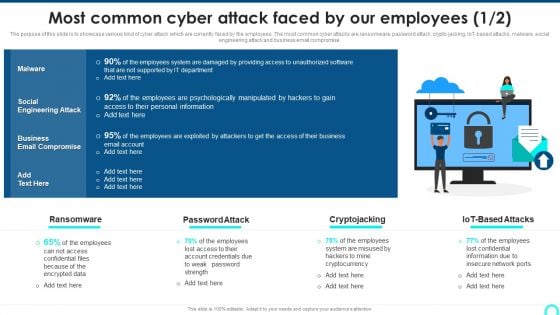
Most Common Cyber Attack Faced By Our Employees Clipart PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. This is a Most Common Cyber Attack Faced By Our Employees Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employees Psychologically, Personal Information, Psychologically Manipulated. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Key Template PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Presenting global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats key template pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Infographics PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. This is a global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats infographics pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
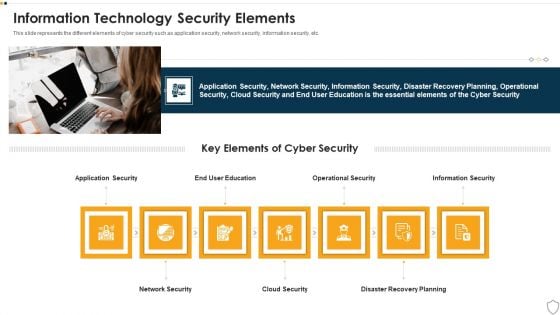
IT Security Information Technology Security Elements Ppt Images PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a it security information technology security elements ppt images pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, cloud security, disaster recovery planning, operational security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Key Elements Of Computer Security Download PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a desktop security management key elements of computer security download pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, information security, application security, network security, cloud security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
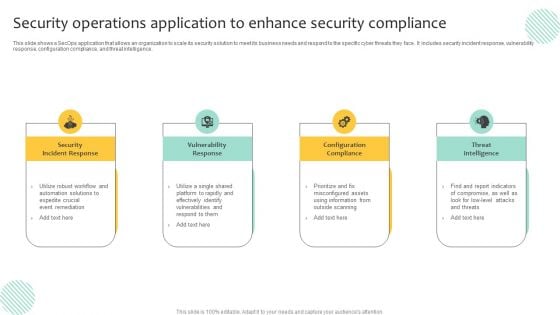
Security Operations Application To Enhance Security Compliance Rules PDF
This slide shows a SecOps application that allows an organization to scale its security solution to meet its business needs and respond to the specific cyber threats they face. It includes security incident response, vulnerability response, configuration compliance, and threat intelligence. Persuade your audience using this Security Operations Application To Enhance Security Compliance Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Configuration Compliance, Threat Intelligence, Vulnerability Response. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
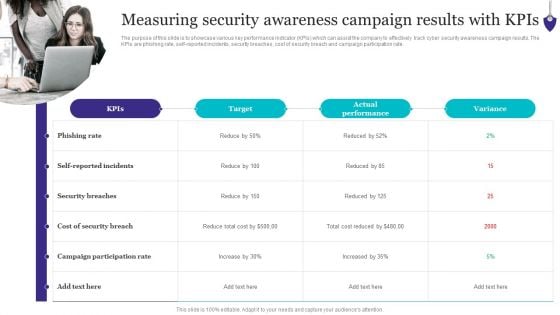
Organizing Security Awareness Measuring Security Awareness Campaign Results Download PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. Explore a selection of the finest Organizing Security Awareness Measuring Security Awareness Campaign Results Download PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Organizing Security Awareness Measuring Security Awareness Campaign Results Download PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Handling Cyber Threats Digital Era Key Security Controls To Be Addressed In The Program Ppt Infographics Samples PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Presenting handling cyber threats digital era key security controls to be addressed in the program ppt infographics samples pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like prevents attacks, limits extent of attacks, data recovery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies To Mitigate Cyber Security Risks Backup Maintenance Selecting Offsite Storage Facility Vendor Ppt Model Graphic Images PDF
Presenting this set of slides with name strategies to mitigate cyber security risks backup maintenance selecting offsite storage facility vendor ppt model graphic images pdf. This is a five stage process. The stages in this process are geographic location, accessibility, security, cost, operational fees, environment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
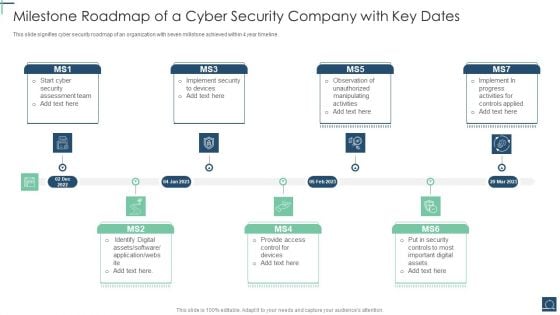
Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF
This slide signifies cyber security roadmap of an organization with seven millstone achieved within 4 year timeline. Persuade your audience using this Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Security Assessment Team, Identify Digital Assets, Provide Access Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
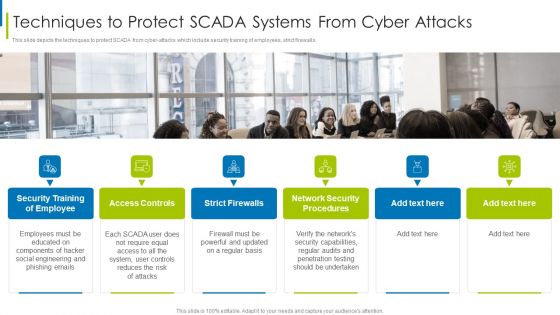
Cyber Terrorism Assault Techniques To Protect SCADA Systems From Cyber Attacks Demonstration PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls.Presenting cyber terrorism assault techniques to protect scada systems from cyber attacks demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like access controls, strict firewalls, network security procedures In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
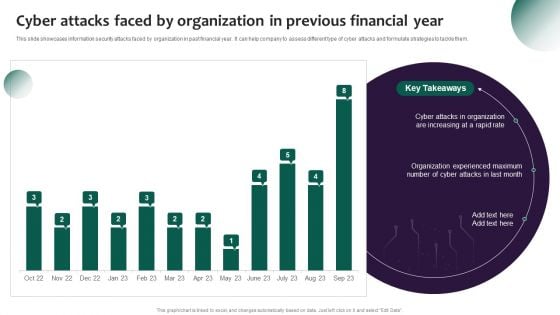
Information Systems Security And Risk Management Plan Cyber Attacks Faced By Organization In Previous Financial Year Graphics PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Information Systems Security And Risk Management Plan Cyber Attacks Faced By Organization In Previous Financial Year Graphics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Series Of Cyber Security Attacks Against Ukraine 2022 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Infographics PDF
This slide represents the cybersecurity risks associated with russia and ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Series Of Cyber Security Attacks Against Ukraine 2022 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Infographics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Series Of Cyber Security Attacks Against Ukraine 2022 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Infographics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
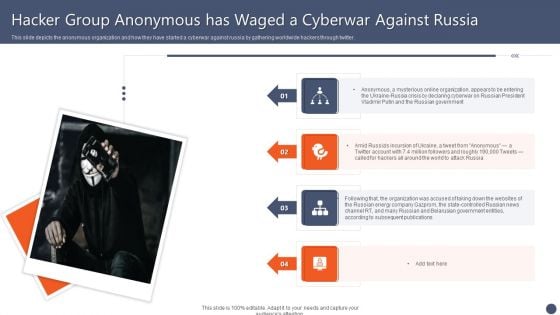
Series Of Cyber Security Attacks Against Ukraine 2022 Hacker Group Anonymous Has Waged A Cyberwar Against Russia Summary PDF
This slide depicts the anonymous organization and how they have started a cyberwar against russia by gathering worldwide hackers through twitter. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Series Of Cyber Security Attacks Against Ukraine 2022 Hacker Group Anonymous Has Waged A Cyberwar Against Russia Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Series Of Cyber Security Attacks Against Ukraine 2022 Hacker Group Anonymous Has Waged A Cyberwar Against Russia Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
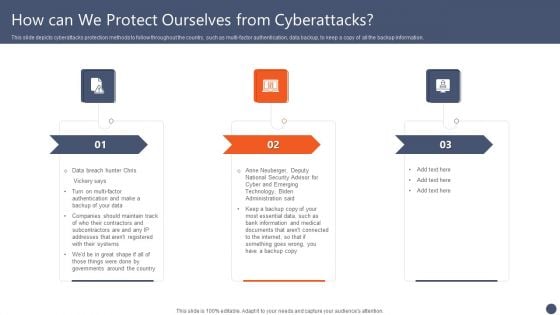
Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi-factor authentication, data backup, to keep a copy of all the backup information. Create an editable Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Series Of Cyber Security Attacks Against Ukraine 2022 Us Is Unmasking Russian Hackers Faster Than Ever Guidelines PDF
This slide represents the rapid announcements made by the united states about russian cyberattacks against ukraine within the 48 hours of the cyberwar. Explore a selection of the finest Series Of Cyber Security Attacks Against Ukraine 2022 Us Is Unmasking Russian Hackers Faster Than Ever Guidelines PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Series Of Cyber Security Atta to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
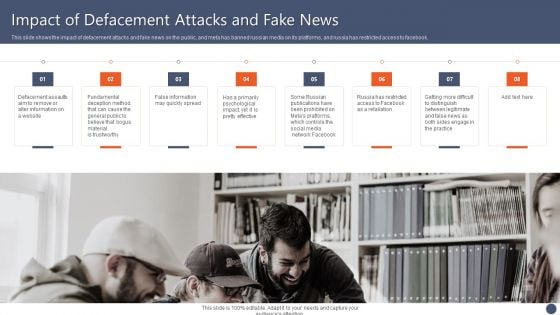
Series Of Cyber Security Attacks Against Ukraine 2022 Impact Of Defacement Attacks And Fake News Topics PDF
This slide shows the impact of defacement attacks and fake news on the public, and meta has banned russian media on its platforms, and russia has restricted access to facebook. There are so many reasons you need a Series Of Cyber Security Attacks Against Ukraine 2022 Impact Of Defacement Attacks And Fake News Topics PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
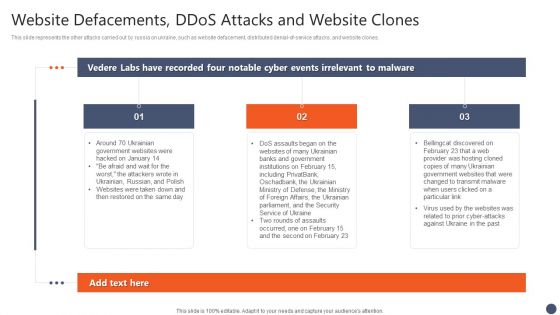
Series Of Cyber Security Attacks Against Ukraine 2022 Website Defacements Ddos Attacks And Website Clones Brochure PDF
This slide represents the other attacks carried out by russia on ukraine, such as website defacement, distributed denial-of-service attacks, and website clones. The Series Of Cyber Security Attacks Against Ukraine 2022 Website Defacements Ddos Attacks And Website Clones Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
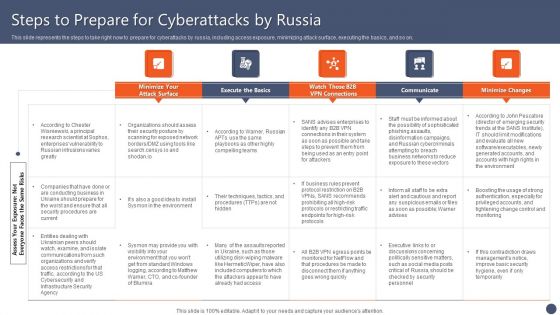
Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF
This slide represents the steps to take right now to prepare for cyberattacks by russia, including access exposure, minimizing attack surface, executing the basics, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Series Of Cyber Security Attacks Against Ukraine 2022 Technical Analysis Of Ddos Attacks Against Ukrainian Websites Elements PDF
This slide represents the technical analysis of ddos attacks against ukrainian websites by showing the internet traffic to the oschad bank website on 15 16 february 2022. Present like a pro with Series Of Cyber Security Attacks Against Ukraine 2022 Technical Analysis Of Ddos Attacks Against Ukrainian Websites Elements PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Series Of Cyber Security Attacks Against Ukraine 2022 Facebook And Twitter Suggest Users In Ukraine Lock Their Accounts Professional PDF
This slide depicts facebook and twitters suggestion for ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. Present like a pro with Series Of Cyber Security Attacks Against Ukraine 2022 Facebook And Twitter Suggest Users In Ukraine Lock Their Accounts Professional PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
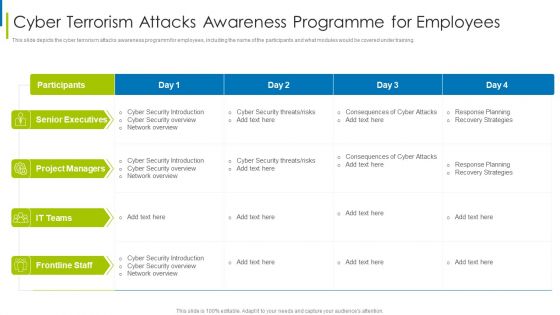
Cyber Terrorism Assault Cyber Terrorism Attacks Awareness Programme For Employees Clipart PDF
This slide depicts the cyber terrorism attacks awareness programm for employees, including the name of the participants and what modules would be covered under training.Deliver an awe inspiring pitch with this creative cyber terrorism assault cyber terrorism attacks awareness programme for employees clipart pdf bundle. Topics like Unanticipated Occurrence, Multiple Copies Of Data, Malicious Assaults can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
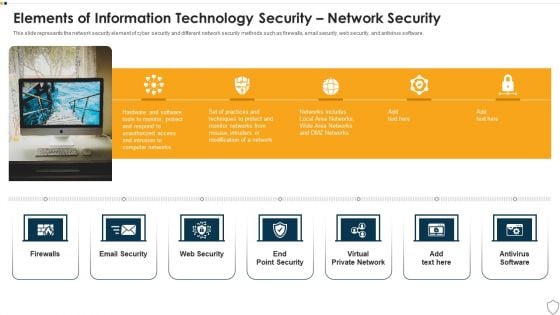
IT Security Elements Of Information Technology Security Network Security Ppt Pictures Graphics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting it security elements of information technology security network security ppt pictures graphics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like web security, end point security, virtual private network, email security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Budget Allocation For Implementing Application Security Application Security Testing
This slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc. Find highly impressive Budget Allocation For Implementing Application Security Application Security Testing on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Budget Allocation For Implementing Application Security Application Security Testing for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc.
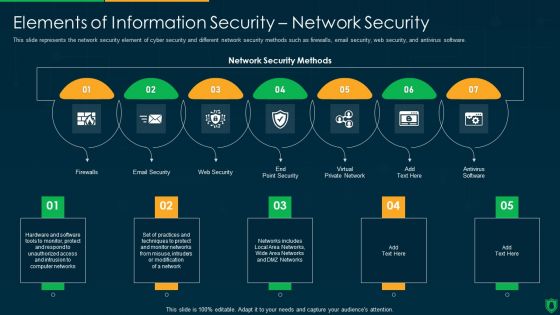
Info Security Elements Of Information Security Network Security Ppt PowerPoint Presentation File Vector PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting info security elements of information security network security ppt powerpoint presentation file vector pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like email security, web security, virtual private network, firewalls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
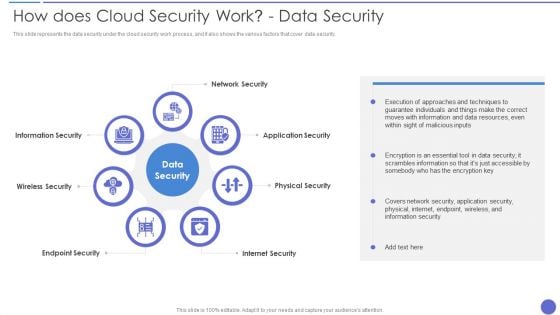
How Does Cloud Security Work Data Security Infographics PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. This is a How Does Cloud Security Work Data Security Infographics PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Application Security, Physical Security, Internet Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
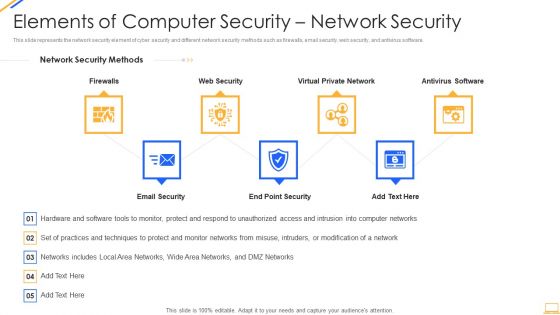
Desktop Security Management Elements Of Computer Security Network Security Infographics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting desktop security management elements of computer security network security infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
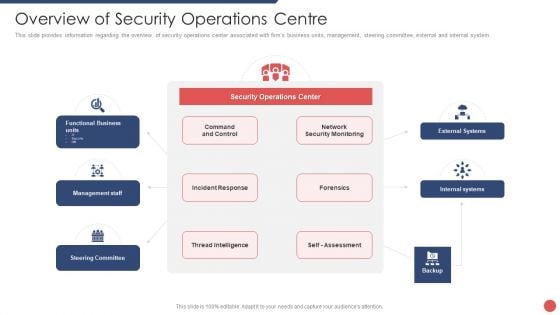
Security Functioning Centre Overview Of Security Operations Centre Summary PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this security functioning centre overview of security operations centre summary pdf. Use them to share invaluable insights on management, thread intelligence, network security monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management Elements Of Computer Security Operational Security Themes PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a desktop security management elements of computer security operational security themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, resources, require, security, plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Elements Of Information Technology Security Operational Security Ppt Professional Format Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a it security elements of information technology security operational security ppt professional format ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, restrict device access, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
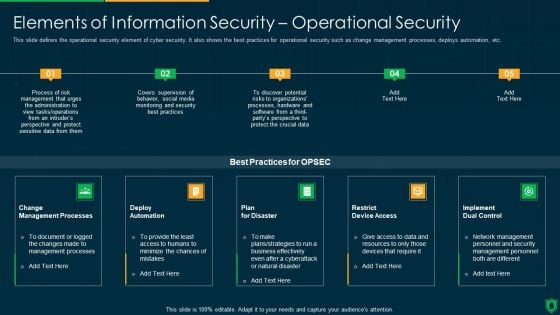
Info Security Elements Of Information Security Operational Security Ppt PowerPoint Presentation File Backgrounds PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a info security elements of information security operational security ppt powerpoint presentation file backgrounds pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































