Employee Cyber Security
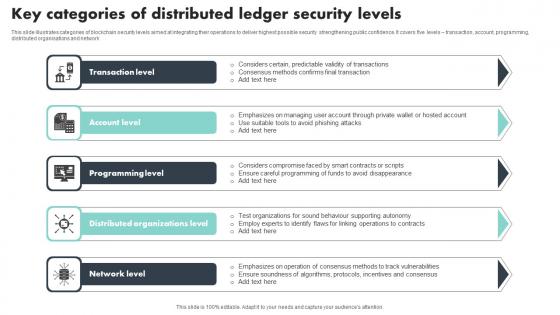
Key Categories Of Distributed Ledger Security Levels Portrait Pdf
This slide illustrates categories of blockchain security levels aimed at integrating their operations to deliver highest possible security strengthening public confidence. It covers five levels transaction, account, programming, distributed organisations and network Pitch your topic with ease and precision using this Key Categories Of Distributed Ledger Security Levels Portrait Pdf This layout presents information on Transaction Level, Account Level, Programming Level It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrates categories of blockchain security levels aimed at integrating their operations to deliver highest possible security strengthening public confidence. It covers five levels transaction, account, programming, distributed organisations and network
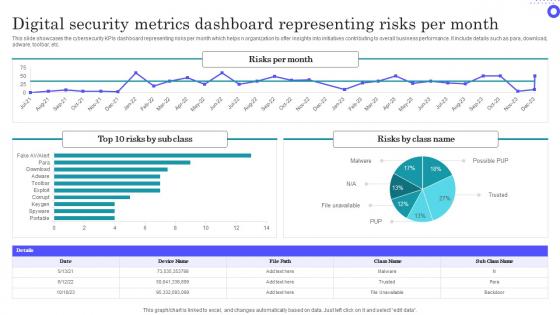
Digital Security Metrics Dashboard Representing Risks Per Month Themes Pdf
Showcasing this set of slides titled Digital Security Metrics Dashboard Representing Risks Per Month Themes Pdf The topics addressed in these templates are Digital Security, Metrics Dashboard, Representing Risks All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the cybersecurity KPIs dashboard representing risks per month which helps n organization to offer insights into initiatives contributing to overall business performance. It include details such as para, download, adware, toolbar, etc.

Benefits Of Zero Trust Network Security Portrait Pdf
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Zero Trust Network Security Portrait Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control AND visibility, invisible infrastructure, and simple app segmentation.

Five Elements Of Cloud Services Security Brochure PDF
This slide includes elements of cloud computing security to assure network protection and efficient management. It contains five elements architecture, security, due diligence, authentication, monitor and visibility.Presenting Five Elements Of Cloud Services Security Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Coverage, Intrusion Detection, Computing Regulations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
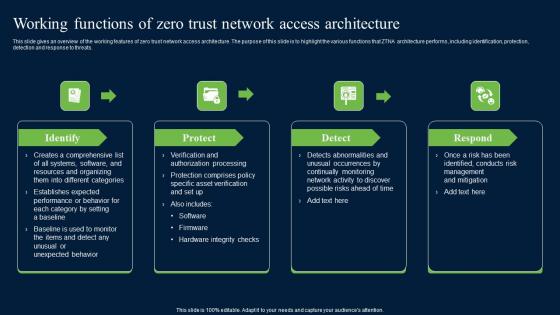
Working Functions Of Zero Trust Network Access Security Infographics Pdf
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Create an editable Working Functions Of Zero Trust Network Access Security Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Working Functions Of Zero Trust Network Access Security Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.
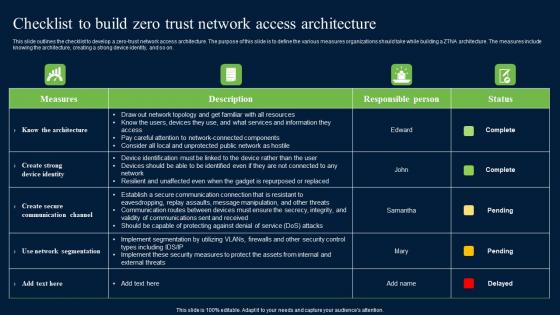
Checklist To Build Zero Trust Network Access Security Structure Pdf
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Build Zero Trust Network Access Security Structure Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Build Zero Trust Network Access Security Structure Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.
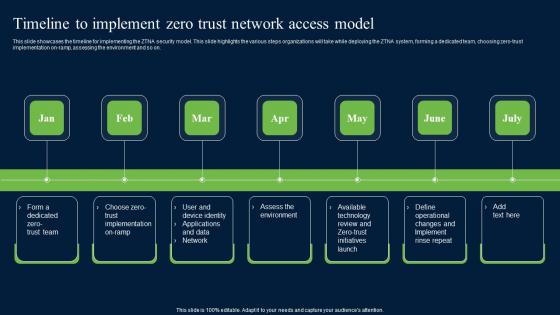
Timeline To Implement Zero Trust Network Security Themes Pdf
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Zero Trust Network Security Themes Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.
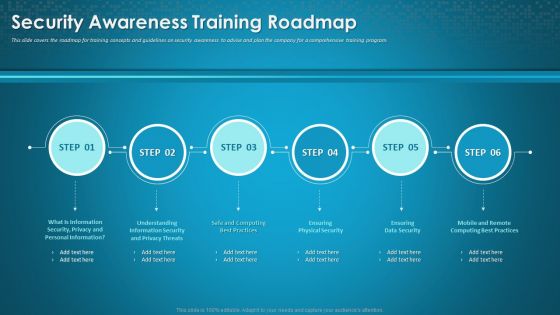
Organizational Network Staff Learning Security Awareness Training Roadmap Sample PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. Presenting organizational network staff learning security awareness training roadmap sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like ensuring data security, information security and privacy threats, ensuring physical security. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Network Staff Learning Security Awareness Program Checklist Background PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. Presenting organizational network staff learning security awareness program checklist background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security awareness program, implementing security awareness, sustaining security awareness. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
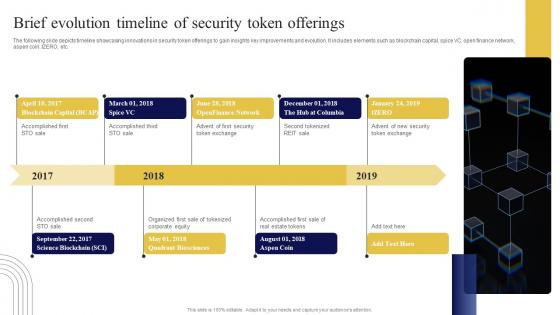
Brief Evolution Timeline Of Security Exploring Investment Opportunities Portrait Pdf
The following slide depicts timeline showcasing innovations in security token offerings to gain insights key improvements and evolution. It includes elements such as blockchain capital, spice VC, open finance network, aspen coin, tZERO, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Brief Evolution Timeline Of Security Exploring Investment Opportunities Portrait Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Brief Evolution Timeline Of Security Exploring Investment Opportunities Portrait Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide depicts timeline showcasing innovations in security token offerings to gain insights key improvements and evolution. It includes elements such as blockchain capital, spice VC, open finance network, aspen coin, tZERO, etc.
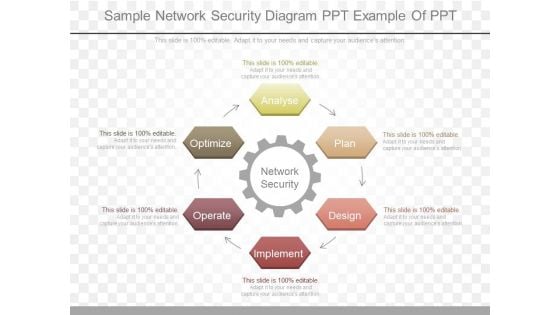
Sample Network Security Diagram Ppt Example Of Ppt
This is a sample network security diagram ppt example of ppt. This is a six stage process. The stages in this process are network security, analyse, plan, design, implement, operate, optimize.
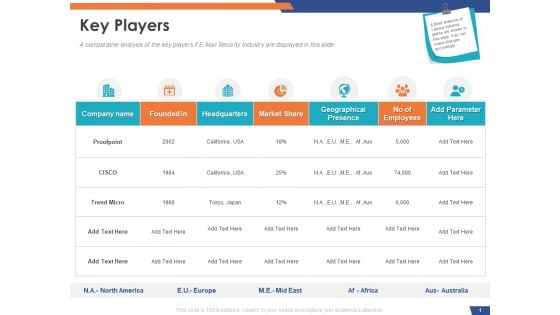
Email Security Market Research Report Key Players Ppt Model PDF
Presenting this set of slides with name email security market research report key players ppt model pdf. The topics discussed in these slides are company name, founded in, headquarters, market share, geographical presence, no of employees. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Electronic Voting System Voting System Standards Security Template PDF
This slide represents the security standard of the voting system that ensures the security of voting machines to prevent them from being tempered or manipulated through physical security, auditability, and internet connection.Presenting Electronic Voting System Voting System Standards Security Template PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Manipulated Tampered, Ensuring Security, Security Include. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
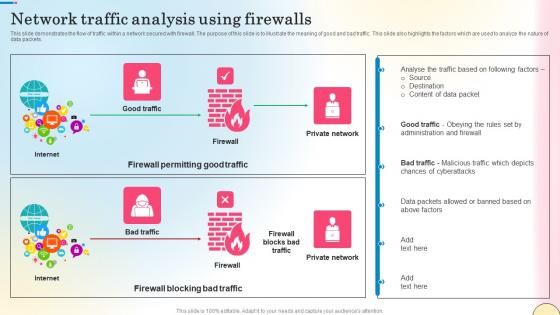
Network Traffic Analysis Using Firewalls Network Security Themes Pdf
This slide represents the architecture of Next generation Firewall as a Service technology. The purpose of this slide is to explain the working of next-generation FWaaS. The main components are branch, data center, internet, client, cloud, firewall, etc. Take your projects to the next level with our ultimate collection of Network Traffic Analysis Using Firewalls Network Security Themes Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents the architecture of Next generation Firewall as a Service technology. The purpose of this slide is to explain the working of next-generation FWaaS. The main components are branch, data center, internet, client, cloud, firewall, etc.

Security Operations Team Roles And Responsibilities Infographics PDF
This slide exhibits key roles on the SecOps team with their roles and responsibilities that manage cybersecurity threats and attacks. It includes a security investigator, advanced security analyst, SOC manager, and security manager. Presenting Security Operations Team Roles And Responsibilities Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Skills Required, Determine, Develop Mitigation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
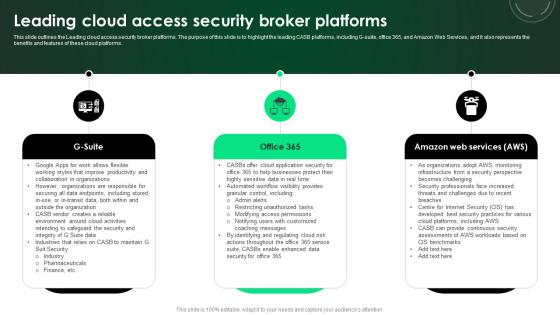
CASB 2 0 IT Leading Cloud Access Security Broker Platforms
This slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms. There are so many reasons you need a CASB 2 0 IT Leading Cloud Access Security Broker Platforms. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms.

Security Camera System Company Profile Our Expertise Pictures PDF
This slide highlights the security company expertise which includes integrated control of devices, internet protocol, RFID based security, wireless based communication and locality surveillance. This is a Security Camera System Company Profile Our Expertise Pictures PDF template with various stages. Focus and dispense information on Eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Internet Protocol, Physical Security, Communication Infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
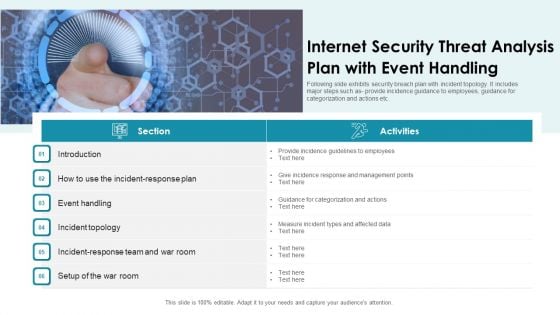
Internet Security Threat Analysis Plan With Event Handling Summary PDF
Following slide exhibits security breach plan with incident topology. It includes major steps such as- provide incidence guidance to employees, guidance for categorization and actions etc. Presenting internet security threat analysis plan with event handling summary pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including internet security threat analysis plan with event handling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
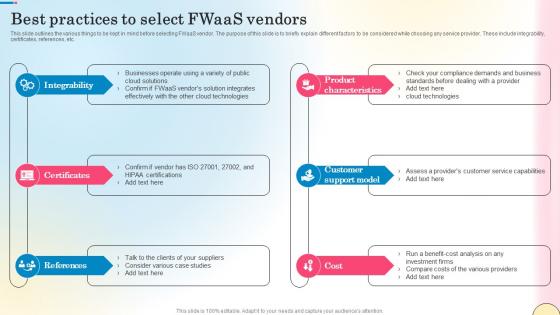
Best Practices To Select Fwaas Vendors Network Security Ideas Pdf
This slide outlines the various things to be kept in mind before selecting FWaaS vendor. The purpose of this slide is to briefly explain different factors to be considered while choosing any service provider. These include integrability, certificates, references, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Select Fwaas Vendors Network Security Ideas Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Select Fwaas Vendors Network Security Ideas Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the various things to be kept in mind before selecting FWaaS vendor. The purpose of this slide is to briefly explain different factors to be considered while choosing any service provider. These include integrability, certificates, references, etc.
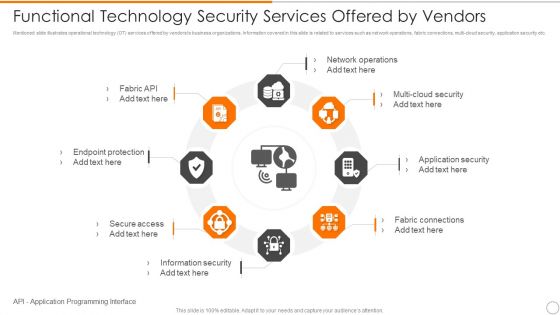
Functional Technology Security Services Offered By Vendors Microsoft PDF
Persuade your audience using this functional technology security services offered by vendors microsoft pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including network operations, security, application security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
6 Step Process To Implement Information Availability Security Icons PDF
This slide represents 6 step process to implement data availability security illustrating simplified recording, on site maintenance and online security, training, record disposal and plan. Presenting 6 step process to implement information availability security icons pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including required, develop, security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
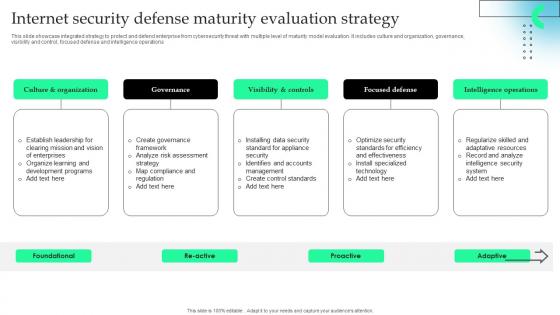
Internet Security Defense Maturity Evaluation Strategy Information Pdf
This slide showcase integrated strategy to protect and defend enterprise from cybersecurity threat with multiple level of maturity model evaluation. It includes culture and organization, governance, visibility and control, focused defense and intelligence operations.Pitch your topic with ease and precision using this Internet Security Defense Maturity Evaluation Strategy Information Pdf This layout presents information on Visibility Controls, Focused Defense, Intelligence Operations It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase integrated strategy to protect and defend enterprise from cybersecurity threat with multiple level of maturity model evaluation. It includes culture and organization, governance, visibility and control, focused defense and intelligence operations.
Organizational Network Staff Learning Security Awareness Tracking Kpis Demonstration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a organizational network staff learning security awareness tracking kpis demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
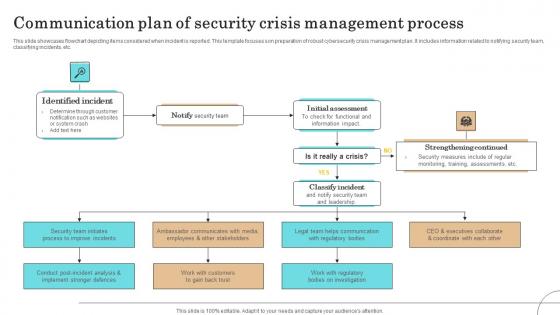
Communication Plan Of Security Crisis Management Process Pictures Pdf
This slide showcases flowchart depicting items considered when incident is reported. This template focuses son preparation of robust cybersecurity crisis management plan. It includes information related to notifying security team, classifying incidents, etc.Pitch your topic with ease and precision using this Communication Plan Of Security Crisis Management Process Pictures Pdf This layout presents information on Identified Incident, Initial Assessment, Strengthening Continued It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases flowchart depicting items considered when incident is reported. This template focuses son preparation of robust cybersecurity crisis management plan. It includes information related to notifying security team, classifying incidents, etc.

Web Consulting Business Performance Best Practices For Web Security
Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Web Consulting Business Performance Best Practices For Web Security a try. Our experts have put a lot of knowledge and effort into creating this impeccable Web Consulting Business Performance Best Practices For Web Security. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup
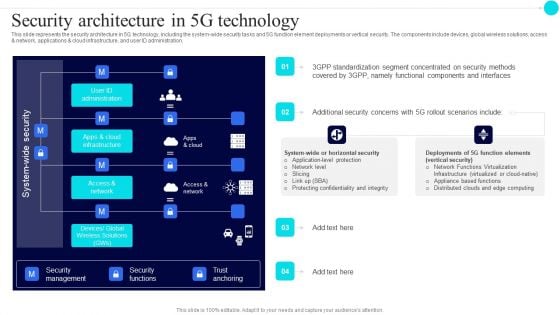
Security Architecture In 5G Technology 5G Functional Architecture Topics PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration.Deliver an awe inspiring pitch with this creative Security Architecture In 5G Technology 5G Functional Architecture Topics PDF bundle. Topics like Standardization Segment, Concentrated Security, Components Interfaces can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparison Between Fwaas And Cloud Firewalls Network Security Portrait Pdf
This slide illustrates the concept of cloud firewalls and Firewall-as-a-Service. The purpose of this slide is to explain if cloud firewalls, and Firewall-as-Service are same or not. This slide also talks about the correlation of both the terms with each other. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Comparison Between Fwaas And Cloud Firewalls Network Security Portrait Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide illustrates the concept of cloud firewalls and Firewall-as-a-Service. The purpose of this slide is to explain if cloud firewalls, and Firewall-as-Service are same or not. This slide also talks about the correlation of both the terms with each other.
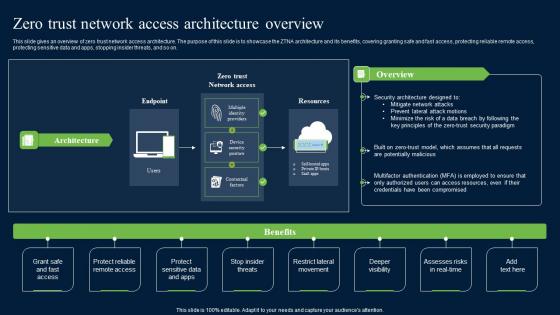
Zero Trust Network Security Access Architecture Overview Graphics Pdf
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Network Security Access Architecture Overview Graphics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.
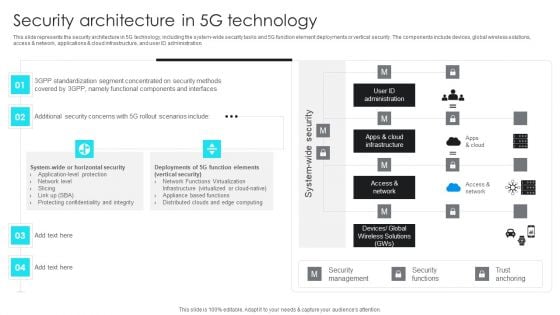
5G Network Operations Security Architecture In 5G Technology Inspiration PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications cloud infrastructure, and user ID administration. Presenting this PowerPoint presentation, titled 5G Network Operations Security Architecture In 5G Technology Inspiration PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this 5G Network Operations Security Architecture In 5G Technology Inspiration PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable 5G Network Operations Security Architecture In 5G Technology Inspiration PDFthat is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
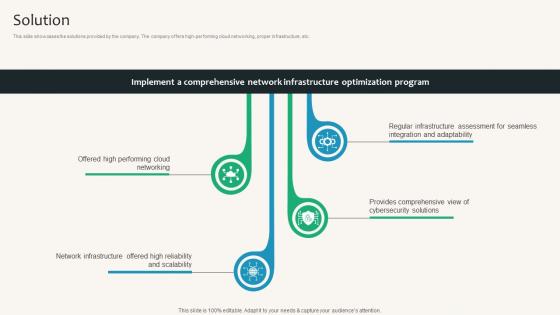
Solution Security Service Provider Business Model BMC SS V
This slide showcases the solutions provided by the company. The company offers high-performing cloud networking, proper infrastructure, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Security Service Provider Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases the solutions provided by the company. The company offers high-performing cloud networking, proper infrastructure, etc.
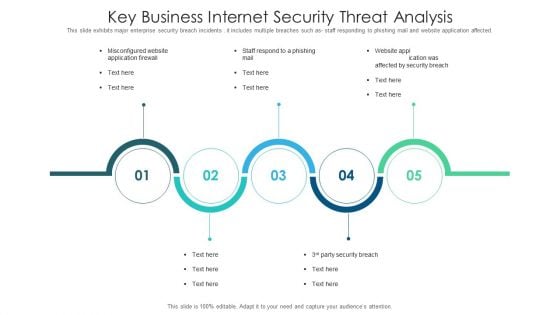
Key Business Internet Security Threat Analysis Slides PDF
This slide exhibits major enterprise security breach incidents . it includes multiple breaches such as staff responding to phishing mail and website application affected. Presenting key business internet security threat analysis slides pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including key business internet security threat analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF
This slide depicts the main tasks of the command security operations center. The purpose of this slide is to highlight the main responsibilities, responsible team members, and task status. The main tasks include monitoring and analyzing security events, coordinating incident response, managing security operations, etc. Get a simple yet stunning designed Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
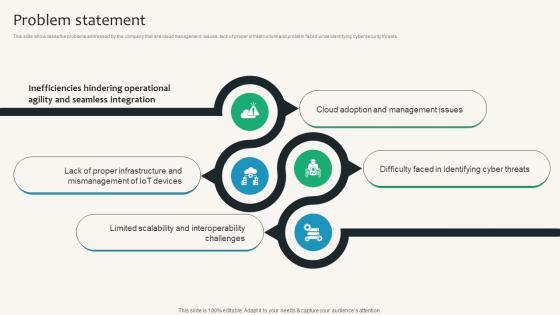
Problem Statement Security Service Provider Business Model BMC SS V
This slide showcases the problems addressed by the company that are cloud management issues, lack of proper infrastructure and problem faced while identifying cybersecurity threats. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Problem Statement Security Service Provider Business Model BMC SS V can be your best option for delivering a presentation. Represent everything in detail using Problem Statement Security Service Provider Business Model BMC SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the problems addressed by the company that are cloud management issues, lack of proper infrastructure and problem faced while identifying cybersecurity threats.

Certified Information Systems Security Professional Cissp Examination Details Topics PDF
Presenting Certified Information Systems Security Professional Cissp Examination Details Topics PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Software Development, Security Assessment, Communications And Network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
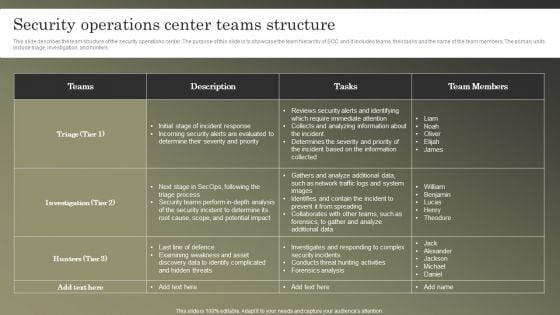
Cybersecurity Operations Cybersecops Security Operations Center Teams Structure Introduction PDF
This slide describes the team structure of the security operations center. The purpose of this slide is to showcase the team hierarchy of SOC and it includes teams, their tasks and the name of the team members. The primary units include triage, investigation, and hunters. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cybersecurity Operations Cybersecops Security Operations Center Teams Structure Introduction PDF can be your best option for delivering a presentation. Represent everything in detail using Cybersecurity Operations Cybersecops Security Operations Center Teams Structure Introduction PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
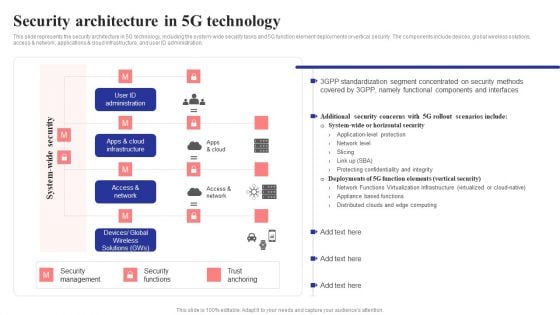
Security Architecture In 5G Technology 5G Network Structure Background PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Are you searching for a Security Architecture In 5G Technology 5G Network Structure Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Architecture In 5G Technology 5G Network Structure Background PDF from Slidegeeks today.
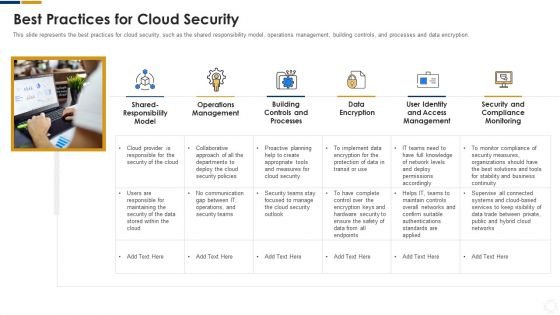
Cybersecurity Best Practices For Cloud Security Ppt Ideas Images PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting cybersecurity best practices for cloud security ppt ideas images pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like measures, security, planning, network, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF. Use them to share invaluable insights on Project Managers, Senior Executives, Security Introduction and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Operations Cybersecops Security Operations Model And Incidents Diagrams PDF
This slide represents the security operations model, covering the incidents managed by the security operations center. The model includes three teams such as hunters, investigators, and triage. The incidents include multi-stage incidents, known campaign tracking, and high-volume incidents. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cybersecurity Operations Cybersecops Security Operations Model And Incidents Diagrams PDF from Slidegeeks and deliver a wonderful presentation.

Computer System Security PowerPoint Templates And PowerPoint Themes 1012
Computer System Security PowerPoint Templates And PowerPoint Themes 1012-Deliver amazing Presentations with our above template consists of laptop and lifesaver. This image represents the concept of computer help or assistance. This template also depicts the concept of computer security. Use this template for web services, technical support etc. It signifies assistance, nteworking, rescue and save. It is a useful captivating tool conceived to enable you to define your message in your Business PPT presentations. Deliver amazing presentations to mesmerize your audience.-Computer System Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Computer network , marketing, finance, internet, computer, technology Our Computer System Security PowerPoint Templates And PowerPoint Themes 1012 come at a comfortable cost. They are definitely an economical choice.
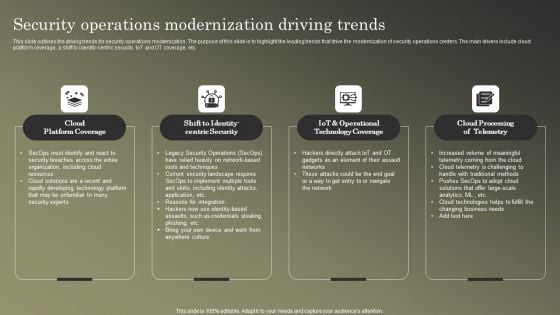
Cybersecurity Operations Cybersecops Security Operations Modernization Driving Slides PDF
This slide outlines the driving trends for security operations modernization. The purpose of this slide is to highlight the leading trends that drive the modernization of security operations centers. The main drivers include cloud platform coverage, a shift to identify-centric security, IoT and OT coverage, etc. Present like a pro with Cybersecurity Operations Cybersecops Security Operations Modernization Driving Slides PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
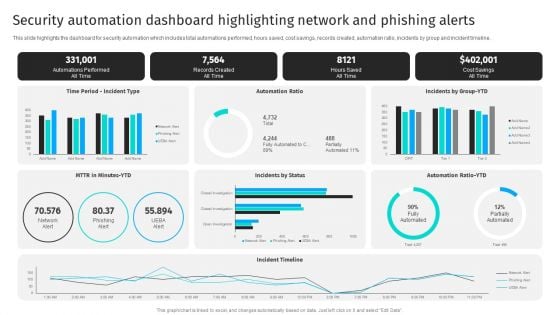
Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline.Get a simple yet stunning designed Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
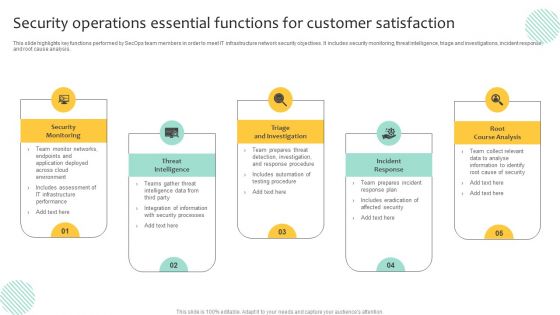
Security Operations Essential Functions For Customer Satisfaction Inspiration PDF
This slide highlights key functions performed by SecOps team members in order to meet IT infrastructure network security objectives. It includes security monitoring, threat intelligence, triage and investigations, incident response, and root cause analysis. Persuade your audience using this Security Operations Essential Functions For Customer Satisfaction Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Triage And Investigation, Incident Response, Root Course Analysis. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
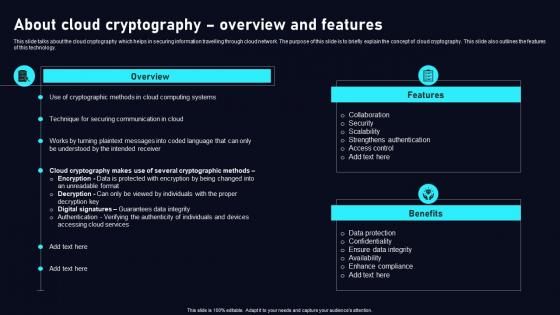
About Cloud Cryptography Cloud Data Security Using Cryptography Mockup Pdf
This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology. Present like a pro with About Cloud Cryptography Cloud Data Security Using Cryptography Mockup Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology.
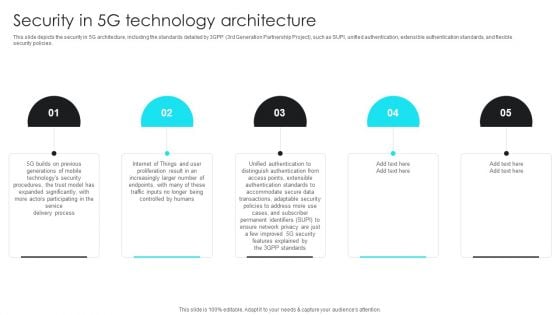
5G Network Operations Security In 5G Technology Architecture Template PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download 5G Network Operations Security In 5G Technology Architecture Template PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the 5G Network Operations Security In 5G Technology Architecture Template PDF.
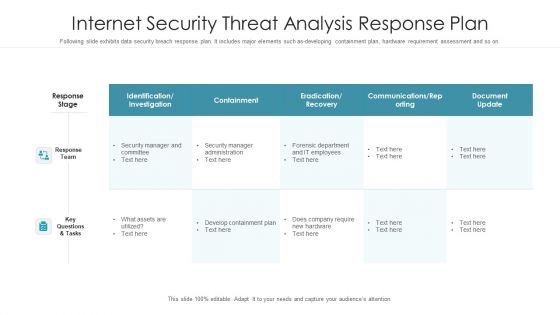
Internet Security Threat Analysis Response Plan Graphics PDF
Following slide exhibits data security breach response plan. It includes major elements such as-developing containment plan, hardware requirement assessment and so on. Pitch your topic with ease and precision using this internet security threat analysis response plan graphics pdf. This layout presents information on response team, response stage, key questions and tasks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
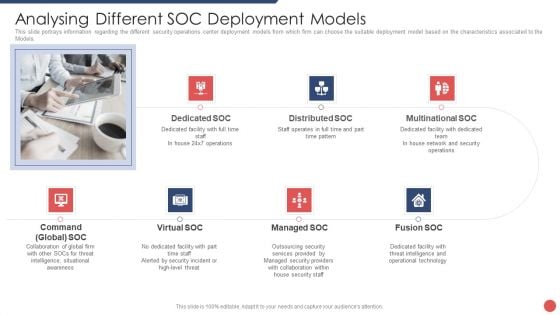
Security Functioning Centre Analysing Different SOC Deployment Models Template PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the Models. This is a security functioning centre analysing different soc deployment models template pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like distributed, network, security operations, operational technology, threat intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
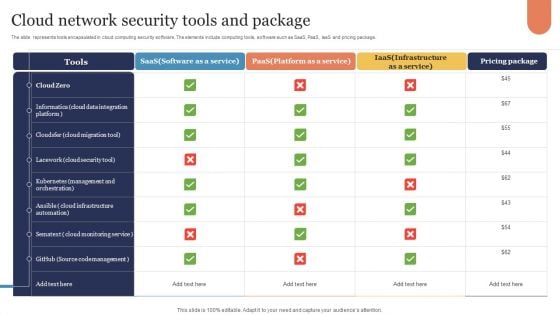
Cloud Network Security Tools And Package Graphics PDF
The slide represents tools encapsulated in cloud computing security software. The elements include computing tools, software such as SaaS, PaaS, IaaS and pricing package. Showcasing this set of slides titled Cloud Network Security Tools And Package Graphics PDF. The topics addressed in these templates are Saas, Paas, Iaas. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
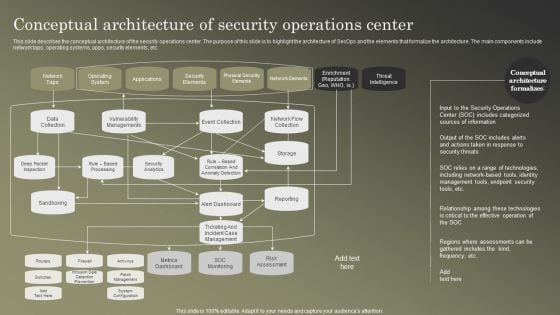
Cybersecurity Operations Cybersecops Conceptual Architecture Of Security Operations Summary PDF
This slide describes the conceptual architecture of the security operations center. The purpose of this slide is to highlight the architecture of SecOps and the elements that formalize the architecture. The main components include network taps, operating systems, apps, security elements, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cybersecurity Operations Cybersecops Conceptual Architecture Of Security Operations Summary PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Cybersecurity Main Principle Of Information Security Ppt Pictures Show PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver and pitch your topic in the best possible manner with this cybersecurity main principle of information security ppt pictures show pdf. Use them to share invaluable insights on integrity, confidentiality, availability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Organizational Network Security Awareness Staff Learning Comparison Formats PDF
This is a organizational network security awareness staff learning comparison formats pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like comparison. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Organizational Network Security Awareness Staff Learning Financials Portrait PDF
Presenting organizational network security awareness staff learning financials portrait pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like minimum, medium, maximum. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Network Security Awareness Staff Learning Idea Generation Designs PDF
This is a organizational network security awareness staff learning idea generation designs pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like idea generation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
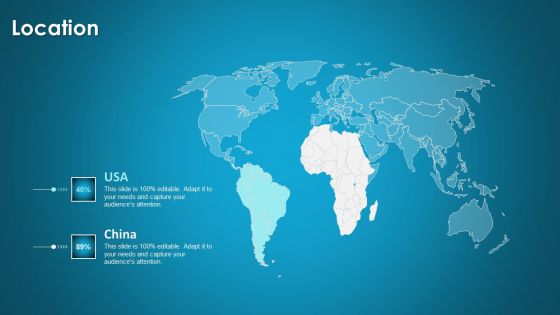
Organizational Network Security Awareness Staff Learning Location Information PDF
Presenting organizational network security awareness staff learning location information pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like location. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Organizational Network Security Awareness Staff Learning Post It Icons PDF
This is a organizational network security awareness staff learning post it icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Organizational Network Security Awareness Staff Learning Venn Summary PDF
Presenting organizational network security awareness staff learning venn summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like venn. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Challenges With Traditional Network Security Approaches Ppt Gallery Icon PDF
This slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Present like a pro with Challenges With Traditional Network Security Approaches Ppt Gallery Icon PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF
This slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. The Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
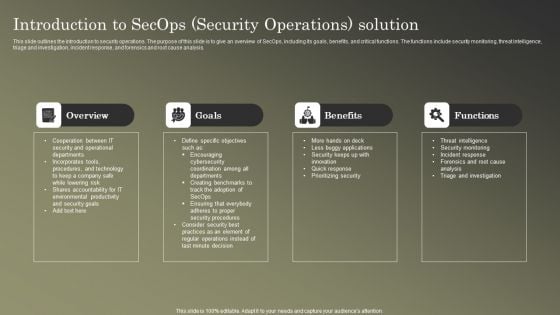
Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF
This slide outlines the introduction to security operations. The purpose of this slide is to give an overview of SecOps, including its goals, benefits, and critical functions. The functions include security monitoring, threat intelligence, triage and investigation, incident response, and forensics and root cause analysis. Want to ace your presentation in front of a live audience Our Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
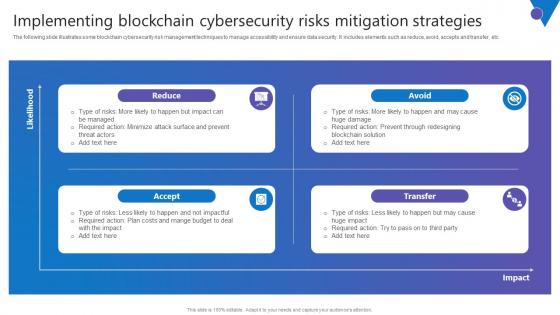
Implementing Blockchain Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Blockchain Comprehensive Guide To Blockchain Digital Security Ideas Pdf can be your best option for delivering a presentation. Represent everything in detail using Implementing Blockchain Comprehensive Guide To Blockchain Digital Security Ideas Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc.


 Continue with Email
Continue with Email

 Home
Home


































