Ethical Values

Cost Performance Index Ppt PowerPoint Presentation Infographics Themes
This is a cost performance index ppt powerpoint presentation infographics themes. This is a two stage process. The stages in this process are cost performance index, ev term, value, finance.

Timeline Vision Ppt PowerPoint Presentation Slides Graphic Tips
This is a timeline vision ppt powerpoint presentation slides graphic tips. This is a three stage process. The stages in this process are timeline vision, value, process, management, planning.
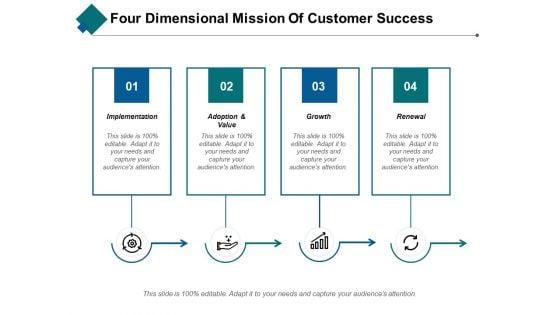
Four Dimensional Mission Of Customer Success Ppt PowerPoint Presentation Portfolio Slide Download
This is a four dimensional mission of customer success ppt powerpoint presentation portfolio slide download. This is a four stage process. The stages in this process are implementation, adoption, value, growth, renewal.
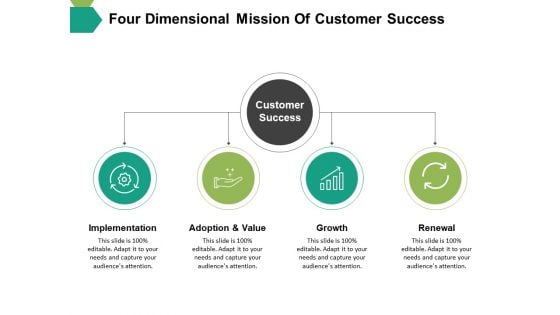
Four Dimensional Mission Of Customer Success Ppt PowerPoint Presentation Pictures Styles
This is a four dimensional mission of customer success ppt powerpoint presentation pictures styles. This is a four stage process. The stages in this process are implementation, adoption, value, growth, renewal.
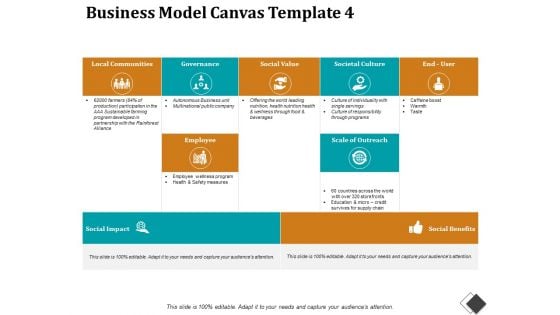
Business Model Canvas Template 4 Ppt PowerPoint Presentation Model
This is a business model canvas template 4 ppt powerpoint presentation model. This is a five stage process. The stages in this process are local communities, governance, social value, societal culture, employee.
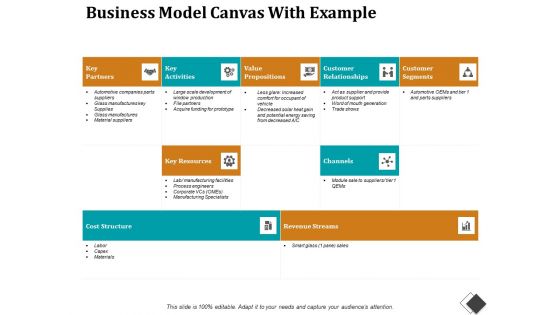
Business Model Canvas With Example Ppt PowerPoint Presentation Tips
This is a business model canvas with example ppt powerpoint presentation tips. This is a five stage process. The stages in this process are local communities, governance, social value, societal culture, employee.
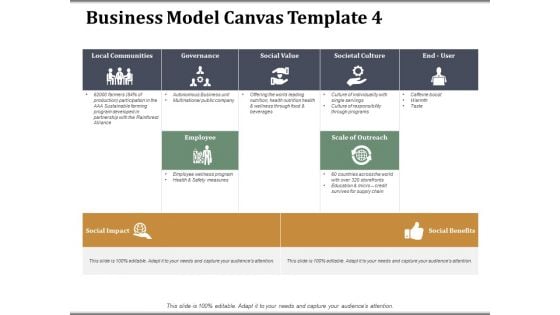
Business Model Canvas Template 4 Ppt PowerPoint Presentation Professional Background Image
This is a business model canvas template 4 ppt powerpoint presentation professional background image. This is a five stage process. The stages in this process are local communities, governance, social value, societal culture, scale of outreach.

Business Phases Action Plan Template Ppt PowerPoint Presentation Show File Formats
This is a business phases action plan template ppt powerpoint presentation show file formats. This is a three stage process. The stages in this process are hared value, shared merit, shared worth.

Complete Business Framework Strategy Structure System Ppt PowerPoint Presentation Ideas Templates
This is a complete business framework strategy structure system ppt powerpoint presentation ideas templates. This is a seven stage process. The stages in this process are hared value, shared merit, shared worth.
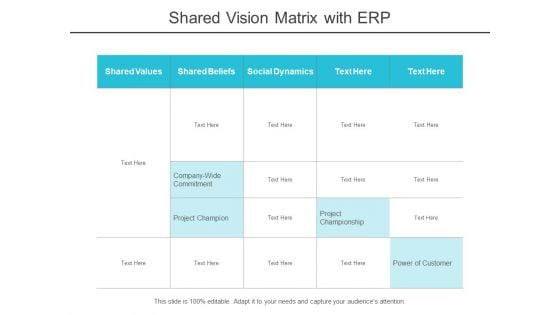
Shared Vision Matrix With Erp Ppt PowerPoint Presentation Infographics Background Images
This is a shared vision matrix with erp ppt powerpoint presentation infographics background images. This is a five stage process. The stages in this process are hared value, shared merit, shared worth.
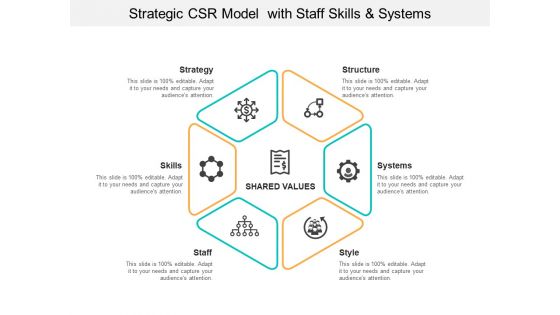
Strategic Csr Model With Staff Skills And Systems Ppt PowerPoint Presentation Show Graphics Tutorials
This is a strategic csr model with staff skills and systems ppt powerpoint presentation show graphics tutorials. This is a six stage process. The stages in this process are hared value, shared merit, shared worth.
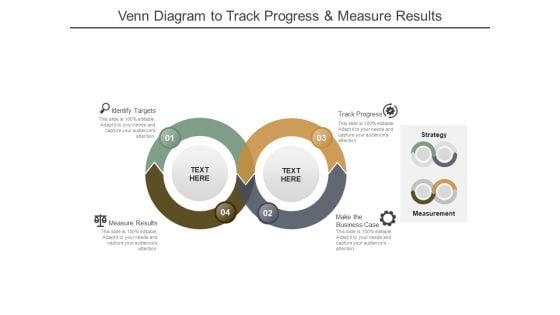
Venn Diagram To Track Progress And Measure Results Ppt PowerPoint Presentation Inspiration Slides
This is a venn diagram to track progress and measure results ppt powerpoint presentation inspiration slides. This is a four stage process. The stages in this process are hared value, shared merit, shared worth.

Organization Ppt PowerPoint Presentation Infographics Graphic Tips
This is a organization ppt powerpoint presentation infographics graphic tips. This is a six stage process. The stages in this process are customer lifetime value, omni channel behavior, business.
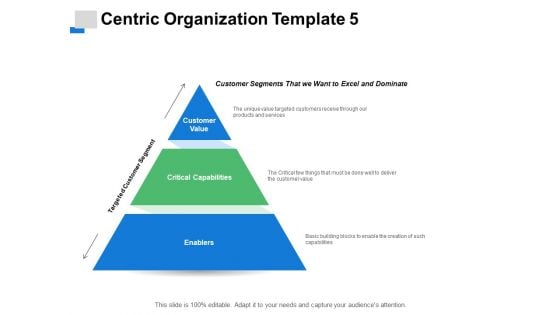
Centric Organization Enablers Ppt PowerPoint Presentation Pictures Brochure
This is a centric organization enablers ppt powerpoint presentation pictures brochure. This is a three stage process. The stages in this process are critical capabilities, customer value, enablers, marketing, management.

Evaluations Techniques Of Projects Ppt Powerpoint Presentation Summary Example File
This is a evaluations techniques of projects ppt powerpoint presentation summary example file. This is a four stage process. The stages in this process are return of investment, payback method, net present value, the internal rate of return.
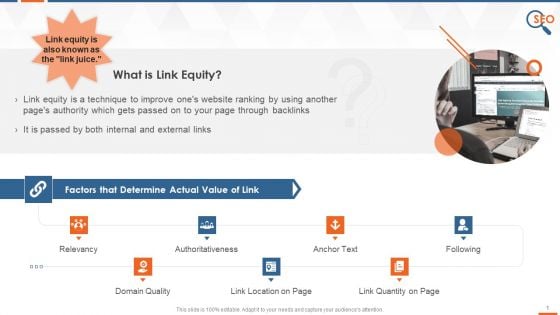
Building Link Equity And Contributing Factors Training Ppt
This slide provides information regarding the link juice and multiple factors that determine the links actual value, such as relevancy, authoritativeness, anchor text, following, domain quality, link location and quantity on page, and HTTPS status.

Red Ocean Technique Overcoming Competition Determining Product Price Before The Launch Inspiration PDF
The following slide exhibits the multiple ways to determine the price of various products before launching it to the market. It covers information about super high value, high value, premium, good value, mid value, overarching, economy, false economy and rip-off. Get a simple yet stunning designed Red Ocean Technique Overcoming Competition Determining Product Price Before The Launch Inspiration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Red Ocean Technique Overcoming Competition Determining Product Price Before The Launch Inspiration PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for. Grab this template today.

Determining Product Price Before The Launch Ppt File Elements PDF
The following slide exhibits the multiple ways to determine the price of various products before launching it to the market. It covers information about super high value, high value, premium, good value, mid value, overarching, economy, false economy and rip-off. This Determining Product Price Before The Launch Ppt File Elements PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
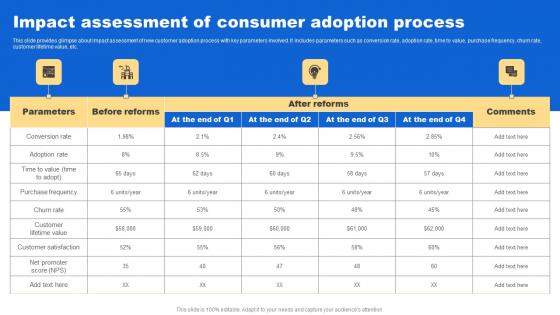
Impact Assessment Consumer Analyzing Customer Buying Behavior Enhance Conversion Template Pdf
This slide provides glimpse about impact assessment of new customer adoption process with key parameters involved. It includes parameters such as conversion rate, adoption rate, time to value, purchase frequency, churn rate, customer lifetime value, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Impact Assessment Consumer Analyzing Customer Buying Behavior Enhance Conversion Template Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides glimpse about impact assessment of new customer adoption process with key parameters involved. It includes parameters such as conversion rate, adoption rate, time to value, purchase frequency, churn rate, customer lifetime value, etc.
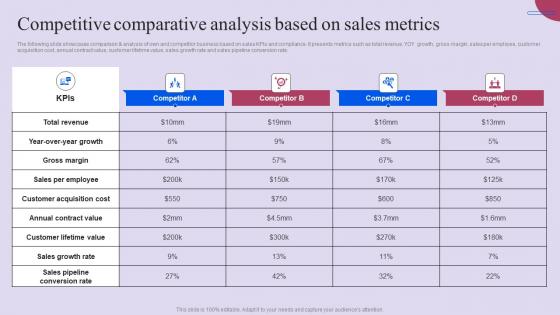
Competitive Comparative Analysis Based On Sales Metrics Ppt File Designs Pdf
The following slide showcases comparison and analysis of own and competitor business based on sales KPIs and compliance. It presents metrics such as total revenue, YOY growth, gross margin, sales per employee, customer acquisition cost, annual contract value, customer lifetime value, sales growth rate and sales pipeline conversion rate. There are so many reasons you need a Competitive Comparative Analysis Based On Sales Metrics Ppt File Designs Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide showcases comparison and analysis of own and competitor business based on sales KPIs and compliance. It presents metrics such as total revenue, YOY growth, gross margin, sales per employee, customer acquisition cost, annual contract value, customer lifetime value, sales growth rate and sales pipeline conversion rate.
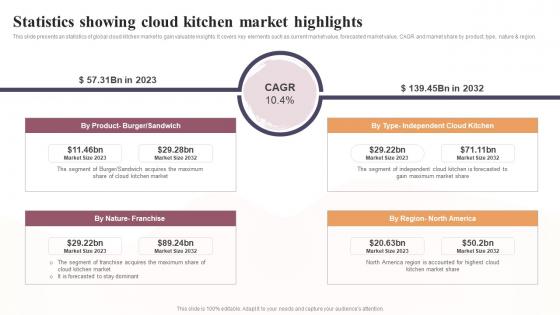
Statistics Showing Cloud Kitchen Market Highlights Global Virtual Restaurant Ideas Pdf
This slide presents an statistics of global cloud kitchen market to gain valuable insights. It covers key elements such as current market value, forecasted market value, CAGR and market share by product, type, nature and region. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Statistics Showing Cloud Kitchen Market Highlights Global Virtual Restaurant Ideas Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide presents an statistics of global cloud kitchen market to gain valuable insights. It covers key elements such as current market value, forecasted market value, CAGR and market share by product, type, nature and region.

Capex Expenditure Approval Report With Multiple Valuation Methods Guidelines PDF
This slide illustrates capital expenditure valuation with different valuation methods and approvals. It includes asset, internal rate of return, net present value, payback period, etc. Showcasing this set of slides titled Capex Expenditure Approval Report With Multiple Valuation Methods Guidelines PDF. The topics addressed in these templates are Internal Rate Return, Net Present Value, Project Period. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
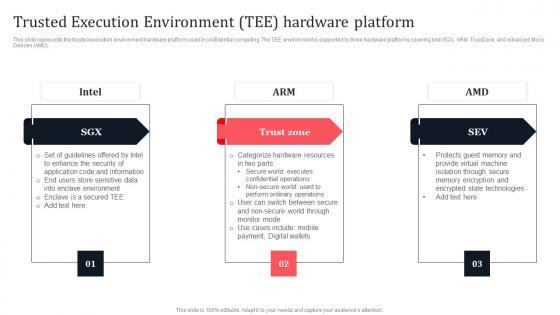
Trusted Execution Environment Tee Hardware Platform Secure Multi Party Microsoft Pdf
This slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Trusted Execution Environment Tee Hardware Platform Secure Multi Party Microsoft Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Trusted Execution Environment Tee Hardware Platform Secure Multi Party Microsoft Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. This slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD.

Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.
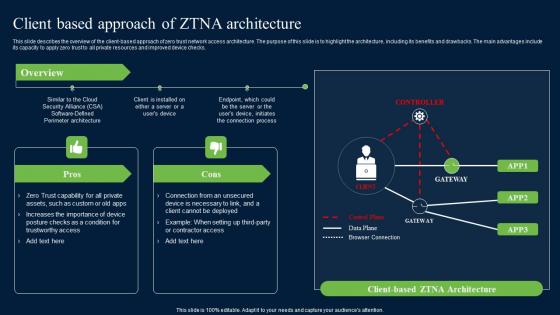
Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Get a simple yet stunning designed Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.
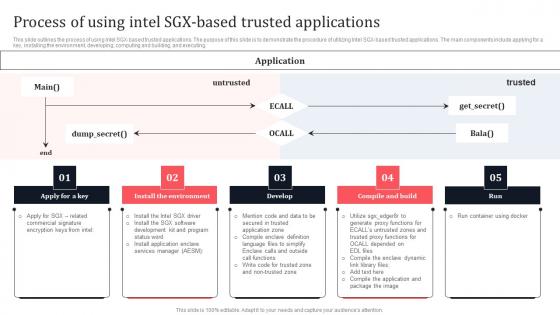
Process Of Using Intel SGX Based Trusted Applications Secure Multi Party Structure Pdf
This slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Present like a pro with Process Of Using Intel SGX Based Trusted Applications Secure Multi Party Structure Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing.
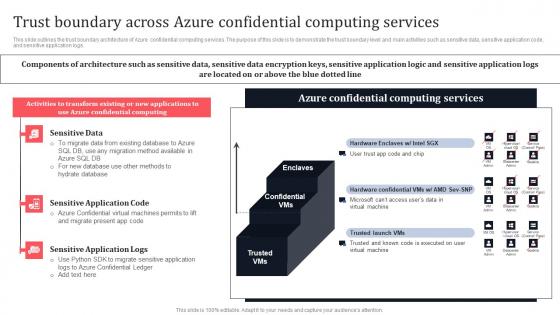
Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf
This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs.
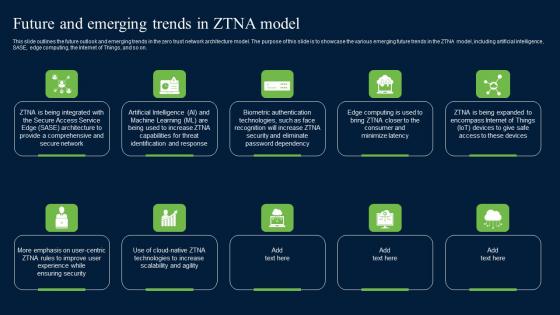
Future And Emerging Trends In ZTNA Model Zero Trust Network Security Clipart Pdf
This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Future And Emerging Trends In ZTNA Model Zero Trust Network Security Clipart Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on.
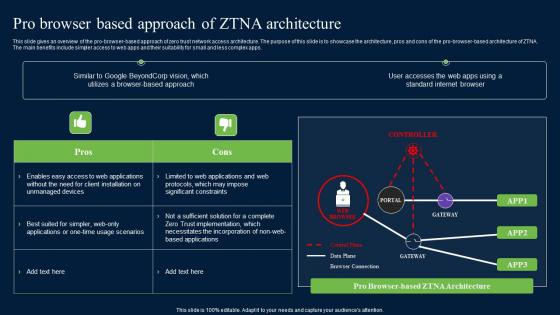
Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf
The main benefits include simpler access to web apps and their suitability for small and less complex apps. Presenting this PowerPoint presentation, titled Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The main benefits include simpler access to web apps and their suitability for small and less complex apps.
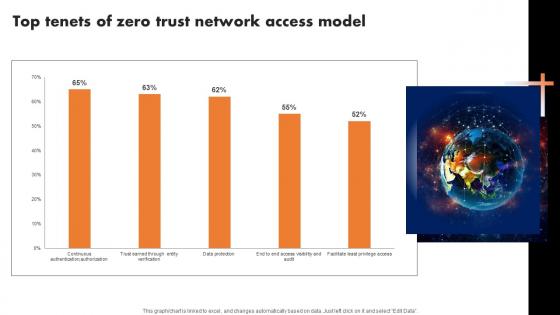
Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP
Find highly impressive Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now Our Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Contents For Zero Trust Network Access Ppt Diagram Lists
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Table Of Contents For Zero Trust Network Access Ppt Diagram Lists can be your best option for delivering a presentation. Represent everything in detail using Table Of Contents For Zero Trust Network Access Ppt Diagram Lists and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. Our Table Of Contents For Zero Trust Network Access Ppt Diagram Lists are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
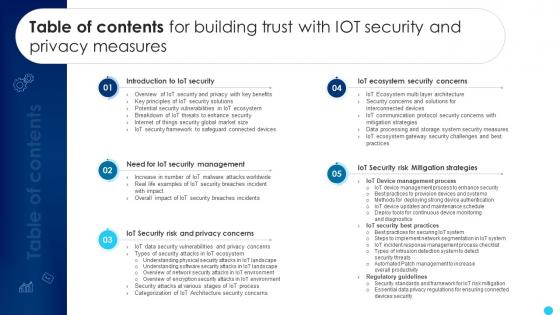
Table Of Contents For Building Trust With IoT Security And Privacy Measures IoT SS V
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Table Of Contents For Building Trust With IoT Security And Privacy Measures IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Table Of Contents For Building Trust With IoT Security And Privacy Measures IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Our Table Of Contents For Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Agenda For Building Trust With IoT Security And Privacy Measures IoT SS V
Find a pre-designed and impeccable Agenda For Building Trust With IoT Security And Privacy Measures IoT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda For Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
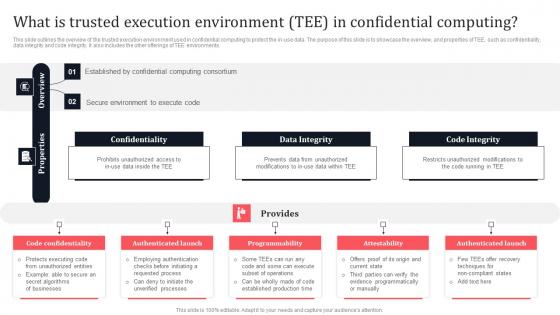
What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments.

Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf
This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment.
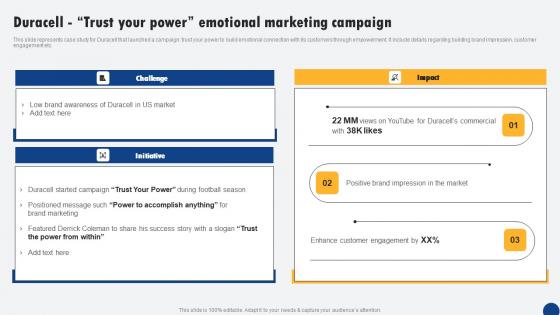
Duracell Trust Your Power Emotional Marketing Driven Digital Marketing Professional Pdf
This slide represents case study for Duracell that launched a campaign trust your power to build emotional connection with its customers through empowerment. It include details regarding building brand impression, customer engagement etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Duracell Trust Your Power Emotional Marketing Driven Digital Marketing Professional Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Duracell Trust Your Power Emotional Marketing Driven Digital Marketing Professional Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents case study for Duracell that launched a campaign trust your power to build emotional connection with its customers through empowerment. It include details regarding building brand impression, customer engagement etc.
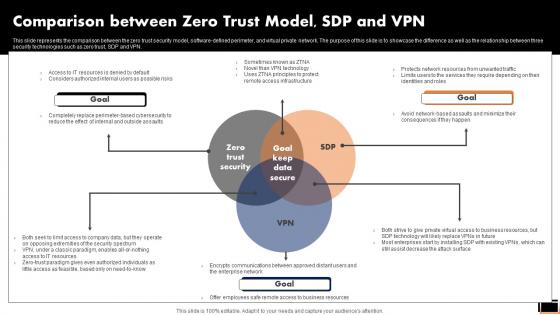
Comparison Between Zero Trust ModelSDP And Vpn Software Defined Perimeter SDP
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Present like a pro with Comparative Assessment Of Ztna Version 1 0 And 2 0 Software Defined Perimeter SDP. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
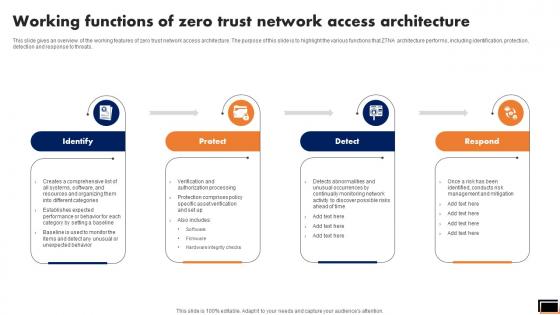
Working Functions Of Zero Trust Network Access Architecture Software Defined Perimeter SDP
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Working Functions Of Zero Trust Network Access Architecture Software Defined Perimeter SDP was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Working Functions Of Zero Trust Network Access Architecture Software Defined Perimeter SDP. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.
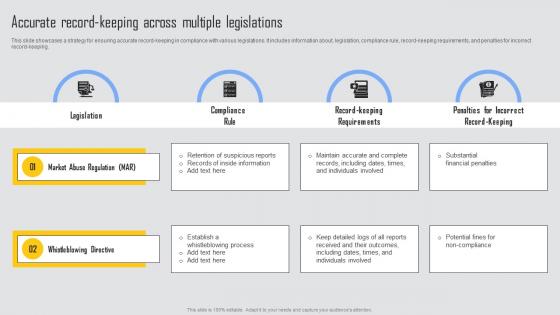
Accurate Record Keeping Managing Risks And Establishing Trust Through Efficient Ideas Pdf
This slide showcases a strategy for ensuring accurate record keeping in compliance with various legislations. It includes information about, legislation, compliance rule, record keeping requirements, and penalties for incorrect record keeping. Find highly impressive Accurate Record Keeping Managing Risks And Establishing Trust Through Efficient Ideas Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Accurate Record Keeping Managing Risks And Establishing Trust Through Efficient Ideas Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases a strategy for ensuring accurate record keeping in compliance with various legislations. It includes information about, legislation, compliance rule, record keeping requirements, and penalties for incorrect record keeping.
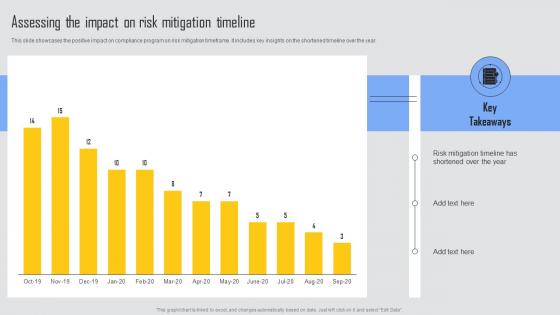
Assessing The Impact Risk Managing Risks And Establishing Trust Through Efficient Professional Pdf
This slide showcases the positive impact on compliance program on risk mitigation timeframe. It includes key insights on the shortened timeline over the year. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Assessing The Impact Risk Managing Risks And Establishing Trust Through Efficient Professional Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Assessing The Impact Risk Managing Risks And Establishing Trust Through Efficient Professional Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide showcases the positive impact on compliance program on risk mitigation timeframe. It includes key insights on the shortened timeline over the year.
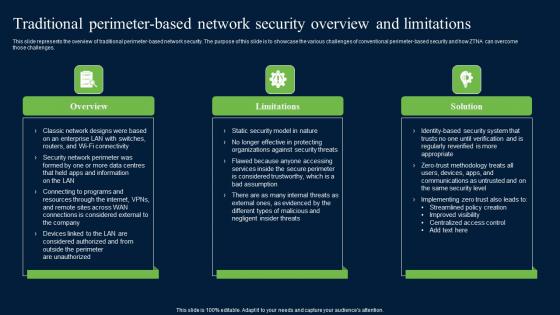
Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. Find highly impressive Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.

Table Of Contents For Zero Trust Model Ppt Powerpoint Presentation Show
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Table Of Contents For Zero Trust Model Ppt Powerpoint Presentation Show for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Our Table Of Contents For Zero Trust Model Ppt Powerpoint Presentation Show are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Zero Trust Network Access Traditional Perimeter Based Network Security Overview And Limitations
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges. This Zero Trust Network Access Traditional Perimeter Based Network Security Overview And Limitations is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Traditional Perimeter Based Network Security Overview And Limitations features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges.
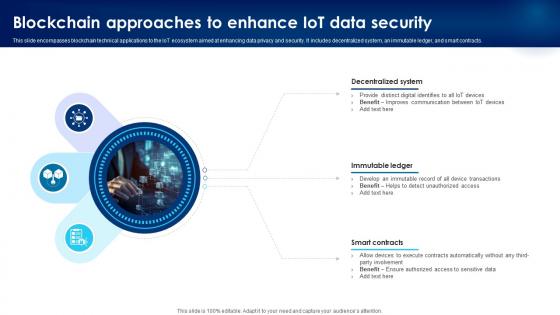
Building Trust With IoT Security Blockchain Approaches To Enhance IoT Data Security IoT SS V
This slide encompasses blockchain technical applications to the IoT ecosystem aimed at enhancing data privacy and security. It includes decentralized system, an immutable ledger, and smart contracts. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Building Trust With IoT Security Blockchain Approaches To Enhance IoT Data Security IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Building Trust With IoT Security Blockchain Approaches To Enhance IoT Data Security IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide encompasses blockchain technical applications to the IoT ecosystem aimed at enhancing data privacy and security. It includes decentralized system, an immutable ledger, and smart contracts.

Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. Our Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
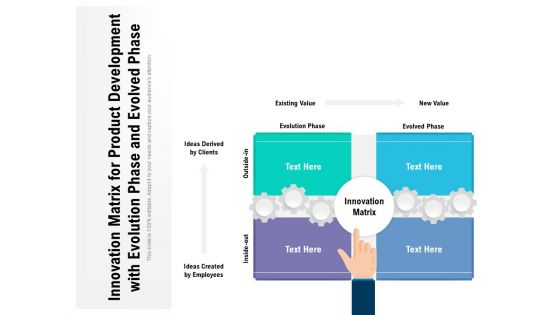
Innovation Matrix For Product Development With Evolution Phase And Evolved Phase Ppt PowerPoint Presentation Outline Model PDF
Presenting this set of slides with name innovation matrix for product development with evolution phase and evolved phase ppt powerpoint presentation outline model pdf. This is a four stage process. The stages in this process are innovation matrix, evolved phase, evolution phase, existing value, new value, ideas derived by clients, ideas created by employees, inside out, outside in. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.

What Is Trusted Execution Environment Tee In Secure Computing Framework Mockup Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Present like a pro with What Is Trusted Execution Environment Tee In Secure Computing Framework Mockup Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments.

Step 2 Choose Zero Trust Implementation On Ramp Software Defined Perimeter SDP
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Want to ace your presentation in front of a live audience Our Step 2 Choose Zero Trust Implementation On Ramp Software Defined Perimeter SDP can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.
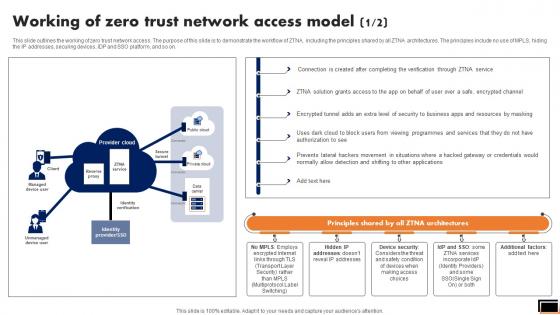
Working Of Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Zero Trust Network Access Model Software Defined Perimeter SDP to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Zero Trust Network Access System Use Cases Software Defined Perimeter SDP
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Are you searching for a Zero Trust Network Access System Use Cases Software Defined Perimeter SDP that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access System Use Cases Software Defined Perimeter SDP from Slidegeeks today. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.
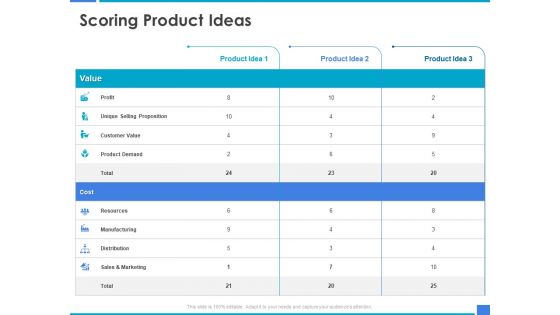
Product Strategy And Product Management Implementation Scoring Product Ideas Ppt Styles Design Inspiration PDF
Presenting this set of slides with name product strategy and product management implementation scoring product ideas ppt styles design inspiration pdf. The topics discussed in these slides are value, profit, unique selling proposition, customer value, product demand, resources, cost, product idea, sales and marketing, manufacturing, distribution. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
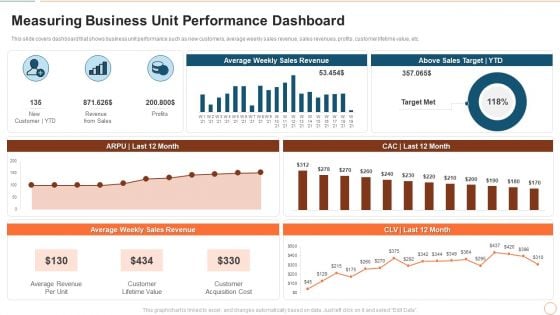
Illustrating Product Leadership Plan Incorporating Innovative Techniques Measuring Business Unit Professional PDF
This slide covers dashboard that shows business unit performance such as new customers, average weekly sales revenue, sales revenues, profits, customer lifetime value, etc. Deliver an awe inspiring pitch with this creative illustrating product leadership plan incorporating innovative techniques measuring business unit professional pdf bundle. Topics like average revenue per unit, customer lifetime value, customer acquisition cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
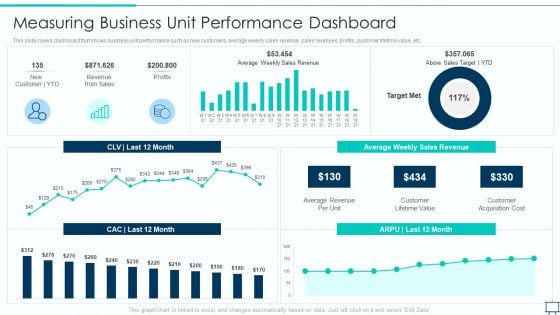
Formulating Competitive Plan Of Action For Effective Product Leadership Measuring Business Unit Slides PDF
This slide covers dashboard that shows business unit performance such as new customers, average weekly sales revenue, sales revenues, profits, customer lifetime value, etc. Deliver an awe inspiring pitch with this creative formulating competitive plan of action for effective product leadership measuring business unit slides pdf bundle. Topics like average revenue per unit, customer lifetime value, customer acquisition cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
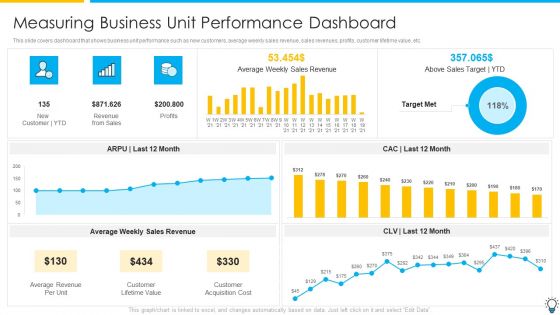
Assuring Management In Product Innovation To Enhance Processes Measuring Business Unit Performance Dashboard Inspiration PDF
This slide covers dashboard that shows business unit performance such as new customers, average weekly sales revenue, sales revenues, profits, customer lifetime value, etc.Deliver an awe inspiring pitch with this creative assuring management in product innovation to enhance processes measuring business unit performance dashboard inspiration pdf bundle. Topics like average weekly sales revenue, customer lifetime value, customer acquisition cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
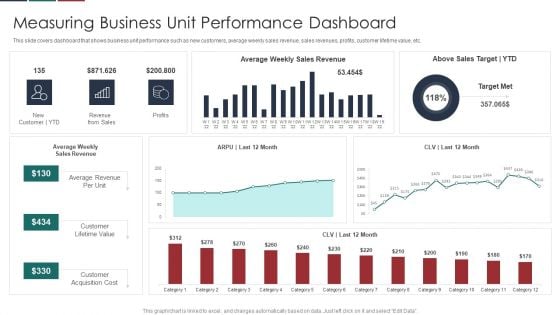
Deliver Efficiency Innovation Measuring Business Unit Performance Dashboard Background PDF
This slide covers dashboard that shows business unit performance such as new customers, average weekly sales revenue, sales revenues, profits, customer lifetime value, etc. Deliver an awe inspiring pitch with this creative Deliver Efficiency Innovation Measuring Business Unit Performance Dashboard Background PDF bundle. Topics like Customer Lifetime Value, Customer Acquisition Cost, Average Revenue Per Unit, Above Sales Target YTD can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
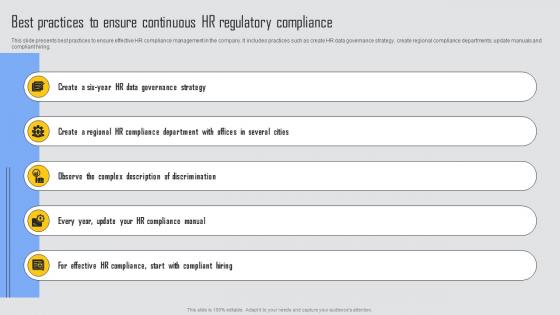
Best Practices To Ensure Managing Risks And Establishing Trust Through Efficient Introduction Pdf
This slide presents best practices to ensure effective HR compliance management in the company. It includes practices such as create HR data governance strategy, create regional compliance departments, update manuals and compliant hiring. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Best Practices To Ensure Managing Risks And Establishing Trust Through Efficient Introduction Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Best Practices To Ensure Managing Risks And Establishing Trust Through Efficient Introduction Pdf This slide presents best practices to ensure effective HR compliance management in the company. It includes practices such as create HR data governance strategy, create regional compliance departments, update manuals and compliant hiring.
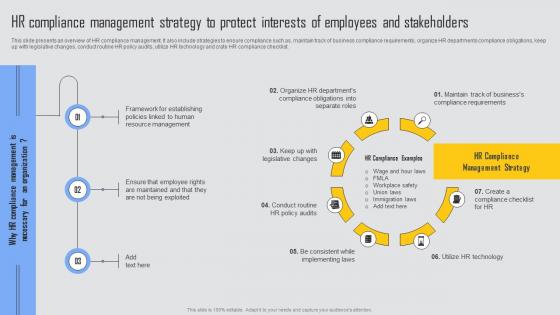
HR Compliance Management Managing Risks And Establishing Trust Through Efficient Template Pdf
This slide presents an overview of HR compliance management. It also include strategies to ensure compliance such as, maintain track of business compliance requirements, organize HR departments compliance obligations, keep up with legislative changes, conduct routine HR policy audits, utilize HR technology and crate HR compliance checklist. Find highly impressive HR Compliance Management Managing Risks And Establishing Trust Through Efficient Template Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download HR Compliance Management Managing Risks And Establishing Trust Through Efficient Template Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide presents an overview of HR compliance management. It also include strategies to ensure compliance such as, maintain track of business compliance requirements, organize HR departments compliance obligations, keep up with legislative changes, conduct routine HR policy audits, utilize HR technology and crate HR compliance checklist.
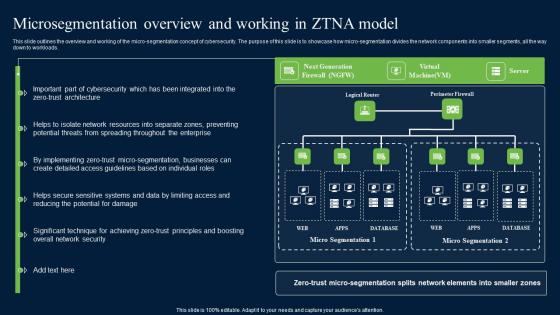
Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.
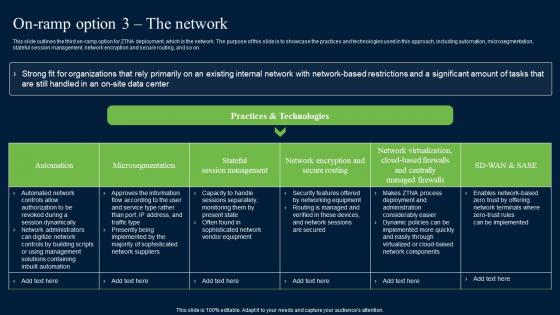
On Ramp Option 3 The Network Zero Trust Network Security Information Pdf
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Zero Trust Network Security Information Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Zero Trust Network Security Information Pdf from Slidegeeks today. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.


 Continue with Email
Continue with Email

 Home
Home


































