Ethical Values
Factors Affecting Employee Morale Motivation Ppt PowerPoint Presentation Summary Example
Presenting this set of slides with name factors affecting employee morale motivation ppt powerpoint presentation summary example. This is an editable Powerpoint six stages graphic that deals with topics like factors affecting employee morale motivation to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
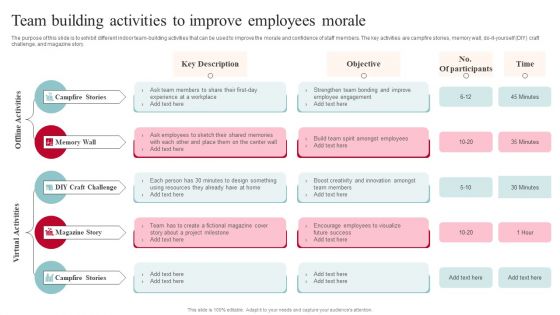
Team Building Activities To Improve Employees Morale Brochure PDF
The purpose of this slide is to exhibit different indoor team-building activities that can be used to improve the morale and confidence of staff members. The key activities are campfire stories, memory wall, do-it-yourself DIY craft challenge, and magazine story. Are you searching for a Team Building Activities To Improve Employees Morale Brochure PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Team Building Activities To Improve Employees Morale Brochure PDF from Slidegeeks today.
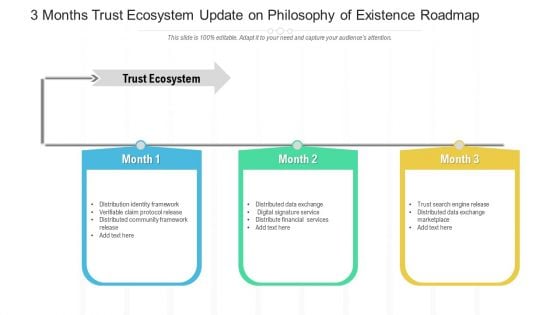
3 Months Trust Ecosystem Update On Philosophy Of Existence Roadmap Formats
Introducing our 3 months trust ecosystem update on philosophy of existence roadmap formats. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
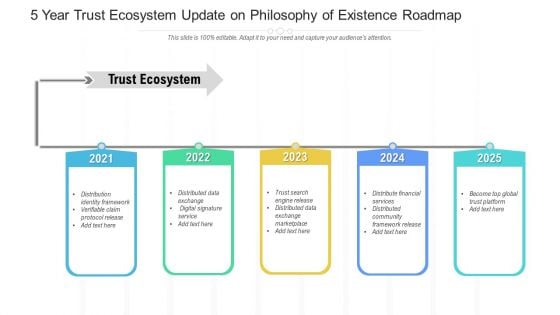
5 Year Trust Ecosystem Update On Philosophy Of Existence Roadmap Template
Introducing our 5 year trust ecosystem update on philosophy of existence roadmap template. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
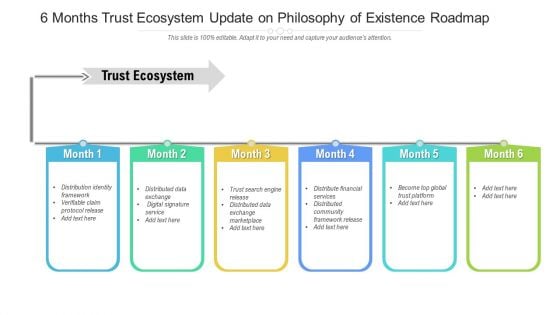
6 Months Trust Ecosystem Update On Philosophy Of Existence Roadmap Inspiration
Introducing our 6 months trust ecosystem update on philosophy of existence roadmap inspiration. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
Half Yearly Trust Ecosystem Update On Philosophy Of Existence Roadmap Icons
Introducing our half yearly trust ecosystem update on philosophy of existence roadmap icons. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
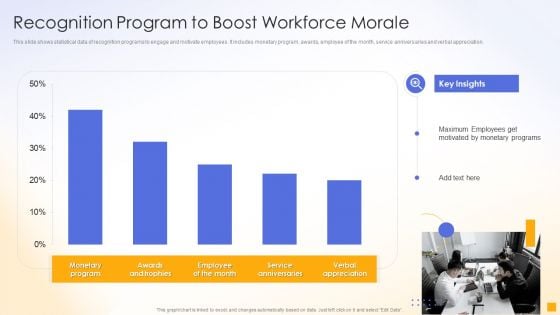
Recognition Program To Boost Workforce Morale Ppt Gallery Information PDF
This slide shows statistical data of recognition programs to engage and motivate employees. It includes monetary program, awards, employee of the month, service anniversaries and verbal appreciation. Pitch your topic with ease and precision using this Recognition Program To Boost Workforce Morale Ppt Gallery Information PDF. This layout presents information on Monetary Program, Awards And Trophies, Employee Month, Service Anniversaries. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Understanding Workforce Morale Through Feedback Form Ppt Styles Template PDF
This slide shows feedback form with ratings from employee to know how satisfied he is with firm. Legends included are never, rarely, sometimes, often and always. Presenting Understanding Workforce Morale Through Feedback Form Ppt Styles Template PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Organizations Support, Sufficient Responsibility, Provided Adequate Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Virtuous Moral Development Business Ppt PowerPoint Presentation Complete Deck
This virtuous moral development business ppt powerpoint presentation complete deck acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twelve slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this virtuous moral development business ppt powerpoint presentation complete deck PPT slideshow.

Workforce Morale Ppt PowerPoint Presentation Complete Deck With Slides
This Workforce Morale Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twelve slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Workforce Morale Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.

Lean Stock Management Core Principles Clipart Pdf
This slide illustrate principle to manage lean inventory by taking measures to reduce wastage. It includes elements such as value, flow, pull responsiveness, perfection. Showcasing this set of slides titled Lean Stock Management Core Principles Clipart Pdf. The topics addressed in these templates are Lean Stock, Management Core Principles, Pull Responsiveness, Perfection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrate principle to manage lean inventory by taking measures to reduce wastage. It includes elements such as value, flow, pull responsiveness, perfection.

Company Moral Principle Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Company Moral Principle Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twenty three slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

A50 Zero Trust Network Access Architecture Workflow
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate A50 Zero Trust Network Access Architecture Workflow for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Zero Trust Model Microsegmentation Overview And Working
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Are you searching for a Zero Trust Model Microsegmentation Overview And Working that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Model Microsegmentation Overview And Working from Slidegeeks today. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.
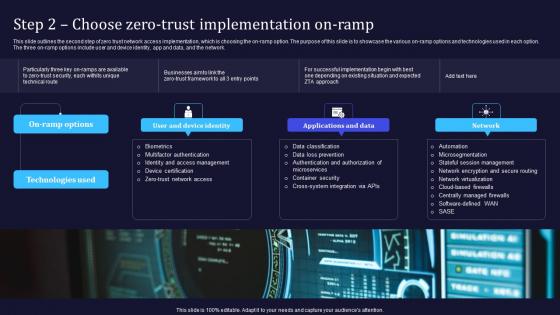
Zero Trust Model Step 2 Choose Zero Trust Implementation On Ramp
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Step 2 Choose Zero Trust Implementation On Ramp a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Step 2 Choose Zero Trust Implementation On Ramp. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.
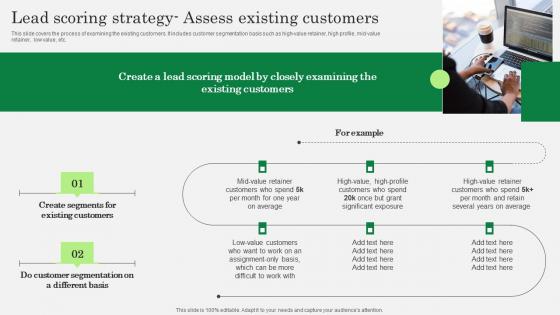
Optimizing Client Lead Handling Lead Scoring Strategy Assess Existing Customers Clipart Pdf
This slide covers the process of examining the existing customers. It includes customer segmentation basis such as high-value retainer, high profile, mid-value retainer,low value, etc. Do you know about Slidesgeeks Optimizing Client Lead Handling Lead Scoring Strategy Assess Existing Customers Clipart Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide covers the process of examining the existing customers. It includes customer segmentation basis such as high-value retainer, high profile, mid-value retainer,low value, etc.

Zero Trust Network Access External Components Of Zero Trust Network Architecture
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Retrieve professionally designed Zero Trust Network Access External Components Of Zero Trust Network Architecture to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.
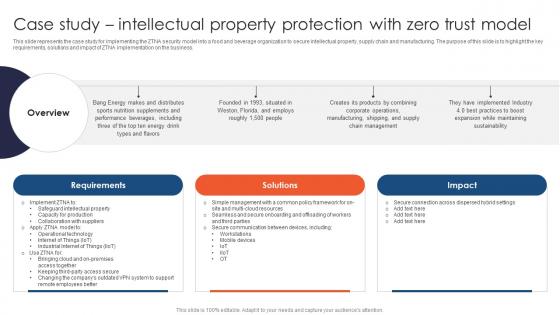
Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.

Zero Trust Network Access Service Initiated Zero Trust Network Topology Model
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access Service Initiated Zero Trust Network Topology Model With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.
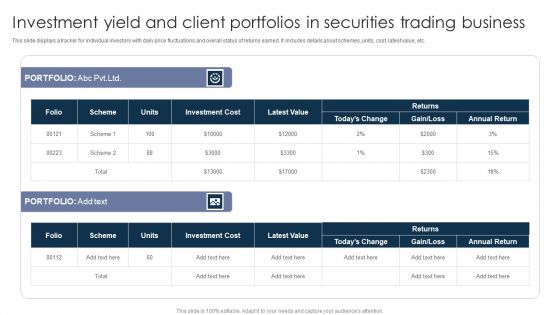
Investment Yield And Client Portfolios In Securities Trading Business Ppt PowerPoint Presentation Gallery Format Ideas PDF
This slide displays a tracker for individual investors with daily price fluctuations and overall status of returns earned. It includes details about schemes, units, cost, latest value, etc. Showcasing this set of slides titled Investment Yield And Client Portfolios In Securities Trading Business Ppt PowerPoint Presentation Gallery Format Ideas PDF. The topics addressed in these templates are Investment Cost, Latest Value, Annual Return. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Zero Trust Model Client Based Approach Of ZTNA Architecture
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Model Client Based Approach Of ZTNA Architecture. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Model Client Based Approach Of ZTNA Architecture today and make your presentation stand out from the rest This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.
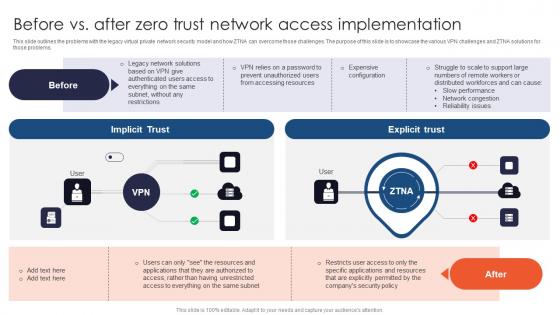
Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Customer Oriented Marketing Strategy Powerpoint Slide Rules
This is a customer oriented marketing strategy powerpoint slide rules. This is a six stage process. The stages in this process are meet expectations, meet desires, meet unexpected needs, clarity of value, consistency, credibility, trust, loyalty, customer interactions over time, emotional connection.
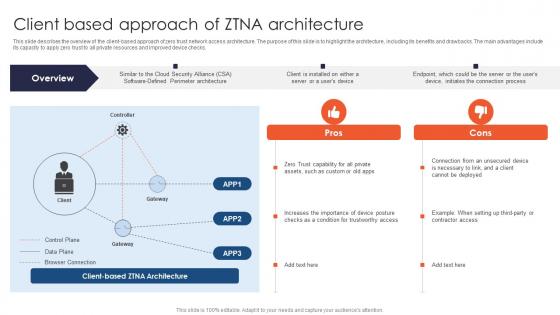
Zero Trust Network Access Client Based Approach Of ZTNA Architecture
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. This modern and well-arranged Zero Trust Network Access Client Based Approach Of ZTNA Architecture provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.

Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.
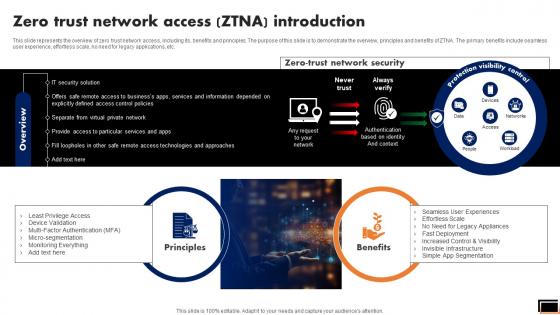
Zero Trust Network Access Ztna Introduction Software Defined Perimeter SDP
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Network Access Ztna Introduction Software Defined Perimeter SDP to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Network Access Ztna Introduction Software Defined Perimeter SDP. This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.
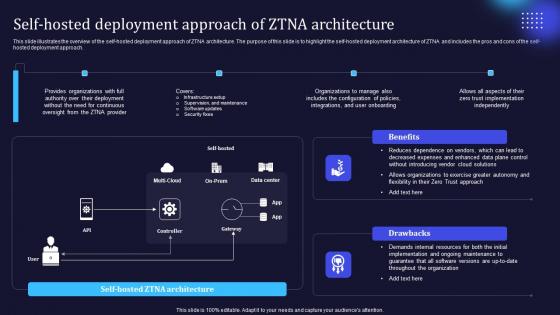
Zero Trust Model Self Hosted Deployment Approach Of ZTNA Architecture
This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach. Create an editable Zero Trust Model Self Hosted Deployment Approach Of ZTNA Architecture that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Zero Trust Model Self Hosted Deployment Approach Of ZTNA Architecture is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach.

Zero Trust Model Pro Browser Based Approach Of ZTNA Architecture
This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps. Take your projects to the next level with our ultimate collection of Zero Trust Model Pro Browser Based Approach Of ZTNA Architecture. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps.
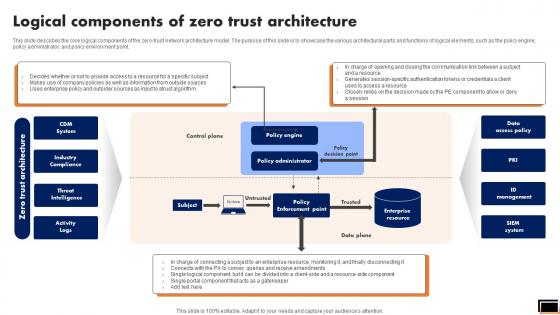
Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. This Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point.

Comparison Of Crm And Customer Relationship Management With Core Objective Guidelines PDF
This slide focuses on the comparison of customer relationship and experience management that covers focus, core objective, data type and uses with buying behavior analysis, determine customer value, reducing churn, improve customer experience, etc. Showcasing this set of slides titled Comparison Of Crm And Customer Relationship Management With Core Objective Guidelines PDF. The topics addressed in these templates are Increasing Customer Value, Organization, Market Research. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
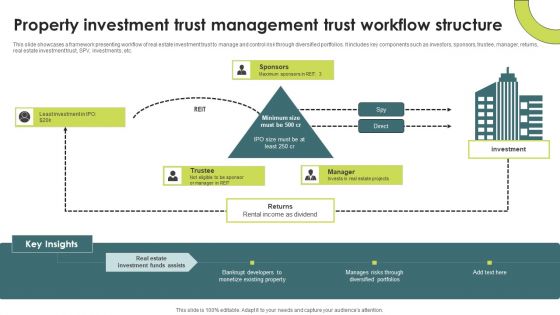
Property Investment Trust Management Trust Workflow Structure Summary PDF
This slide showcases a framework presenting workflow of real estate investment trust to manage and control risk through diversified portfolios. It includes key components such as investors, sponsors, trustee, manager, returns, real estate investment trust, SPV, investments, etc.Showcasing this set of slides titled Property Investment Trust Management Trust Workflow Structure Summary PDF. The topics addressed in these templates are Minimum Size, Rental Income As Dividend. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Zero Trust Model As A Service Deployment Approach Of ZTNA
This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. There are so many reasons you need a Zero Trust Model As A Service Deployment Approach Of ZTNA. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software.
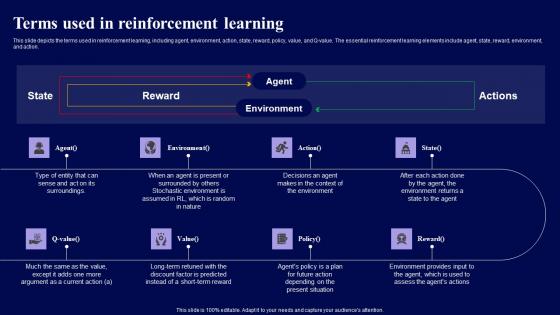
Terms Used In Reinforcement Learning Role Of Reinforcement Clipart Pdf
This slide depicts the terms used in reinforcement learning, including agent, environment, action, state, reward, policy, value, and Q-value. The essential reinforcement learning elements include agent, state, reward, environment, and action. Create an editable Terms Used In Reinforcement Learning Role Of Reinforcement Clipart Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Terms Used In Reinforcement Learning Role Of Reinforcement Clipart Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide depicts the terms used in reinforcement learning, including agent, environment, action, state, reward, policy, value, and Q-value. The essential reinforcement learning elements include agent, state, reward, environment, and action.
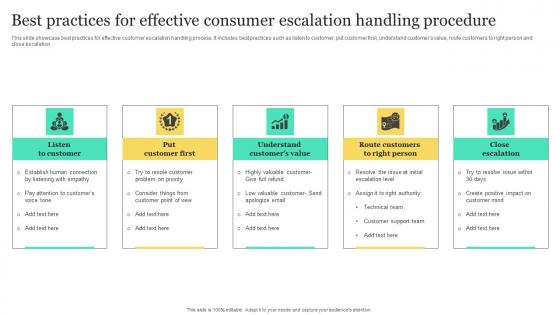
Best Practices For Effective Consumer Escalation Handling Procedure Rules Pdf
This slide showcase best practices for effective customer escalation handling process. It includes best practices such as listen to customer, put customer first, understand customers value, route customers to right person and close escalation. Showcasing this set of slides titled Best Practices For Effective Consumer Escalation Handling Procedure Rules Pdf. The topics addressed in these templates are Listen To Customer, Understand Customers Value, Route Customers Right Person, Close Escalation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase best practices for effective customer escalation handling process. It includes best practices such as listen to customer, put customer first, understand customers value, route customers to right person and close escalation.

Procedure To Conduct Fund Investment Assessment Formats Pdf
This slide illustrate process to conduct capital investment analysis to choose best project. It includes steps such as decide total amount of investment, determine cash flows, determine residual value, calculate annual cash flows etc. Pitch your topic with ease and precision using this Procedure To Conduct Fund Investment Assessment Formats Pdf. This layout presents information on Determine Cash Flows, Determine Residual Value, Run Sensitivity Analysis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrate process to conduct capital investment analysis to choose best project. It includes steps such as decide total amount of investment, determine cash flows, determine residual value, calculate annual cash flows etc.

Key Approaches For Optimizing Budget For Acquiring New Customers Structure Pdf
This slide highlights various approaches which can be adopted to calculate customer acquisition costs which help measure overall sales generated. It provides information regarding develop product value, boost on site conversions, improve pricing strategy and use effective marketing techniques. Pitch your topic with ease and precision using this Key Approaches For Optimizing Budget For Acquiring New Customers Structure Pdf. This layout presents information on Develop Product Value, Boost On Site Conversions, Improve Pricing Strategy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights various approaches which can be adopted to calculate customer acquisition costs which help measure overall sales generated. It provides information regarding develop product value, boost on site conversions, improve pricing strategy and use effective marketing techniques.

Business Kpis To Plan Subscription Strategic Pictures Pdf
The following slide highlights business key performance indicators to plan subscription strategy. It includes various metrics such as monthly recurring revenue, customer lifetime value, churn rate and average revenue per user. Showcasing this set of slides titled Business Kpis To Plan Subscription Strategic Pictures Pdf. The topics addressed in these templates are Monthly Recurring Revenue, Customer Lifetime Value, Churn Rate. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide highlights business key performance indicators to plan subscription strategy. It includes various metrics such as monthly recurring revenue, customer lifetime value, churn rate and average revenue per user.
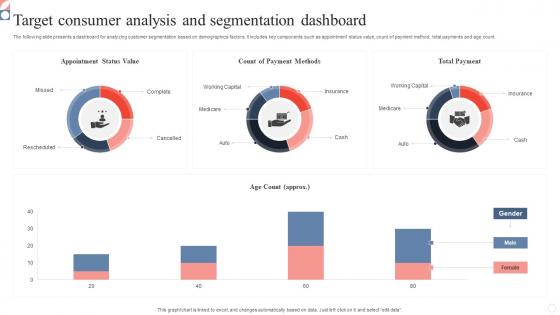
Target Consumer Analysis And Segmentation Dashboard Inspiration Pdf
The following slide presents a dashboard for analyzing customer segmentation based on demographics factors. It includes key components such as appointment status value, count of payment method, total payments and age count. Pitch your topic with ease and precision using this Target Consumer Analysis And Segmentation Dashboard Inspiration Pdf. This layout presents information on Target Consumer Analysis, Segmentation Dashboard, Appointment Status Value. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide presents a dashboard for analyzing customer segmentation based on demographics factors. It includes key components such as appointment status value, count of payment method, total payments and age count.
Dashboard For DEI Maturity Framework Icons Pdf
This slide illustrates facts and figures related to D and I that can help a business organization to track D and I maturity levels. It includes number of qualified leads, percent of supplier satisfaction value, etc. Pitch your topic with ease and precision using this Dashboard For DEI Maturity Framework Icons Pdf. This layout presents information on Dashboard For DEI, Maturity Framework, Supplier Satisfaction Value. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrates facts and figures related to D and I that can help a business organization to track D and I maturity levels. It includes number of qualified leads, percent of supplier satisfaction value, etc.

Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Software Defined Perimeter SDP
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Software Defined Perimeter SDP a try. Our experts have put a lot of knowledge and effort into creating this impeccable Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Software Defined Perimeter SDP. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.
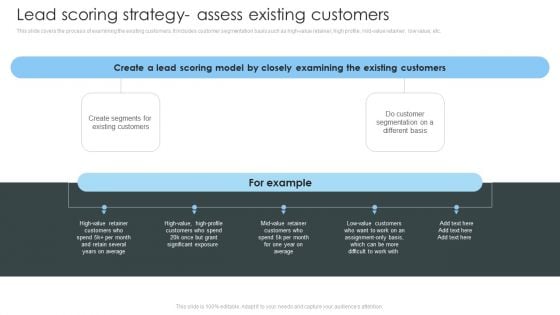
Consumer Lead Generation Process Lead Scoring Strategy Assess Existing Customers Summary PDF
This slide covers the process of examining the existing customers. It includes customer segmentation basis such as high-value retainer, high profile, mid-value retainer, low value, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Consumer Lead Generation Process Lead Scoring Strategy Assess Existing Customers Summary PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
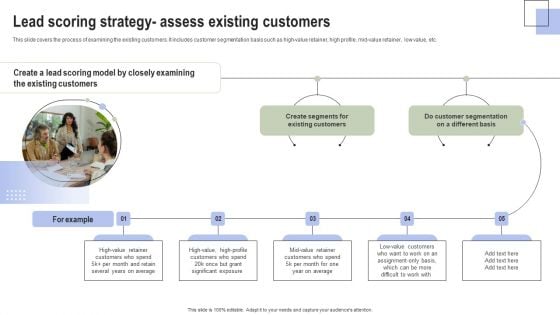
Optimizing Consumer Lead Nurturing Procedure Lead Scoring Strategy Assess Existing Customers Inspiration PDF
This slide covers the process of examining the existing customers. It includes customer segmentation basis such as high-value retainer, high profile, mid-value retainer, low value, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Optimizing Consumer Lead Nurturing Procedure Lead Scoring Strategy Assess Existing Customers Inspiration PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
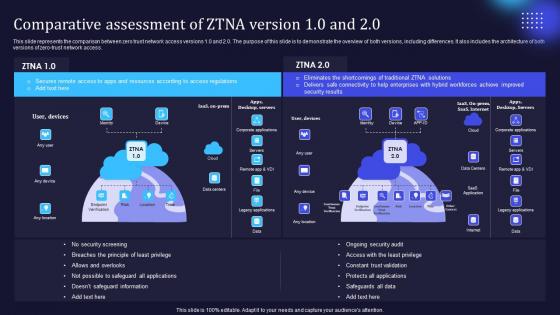
Zero Trust Model Comparative Assessment Of ZTNA Version 1 0 And 2 0
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Model Comparative Assessment Of ZTNA Version 1 0 And 2 0 can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Model Comparative Assessment Of ZTNA Version 1 0 And 2 0 and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.

Online Reviews Strategy To Increase Trust On Innovative Tactics For Revving Up Strategy SS
This slide showcases online reviews technique to enhance trust on brand. It includes strategies such as monitor online reviews, respond to reviews, positive feedback and remove fake reviews. Presenting this PowerPoint presentation, titled Online Reviews Strategy To Increase Trust On Innovative Tactics For Revving Up Strategy SS, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Online Reviews Strategy To Increase Trust On Innovative Tactics For Revving Up Strategy SS. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Online Reviews Strategy To Increase Trust On Innovative Tactics For Revving Up Strategy SS that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide showcases online reviews technique to enhance trust on brand. It includes strategies such as monitor online reviews, respond to reviews, positive feedback and remove fake reviews.
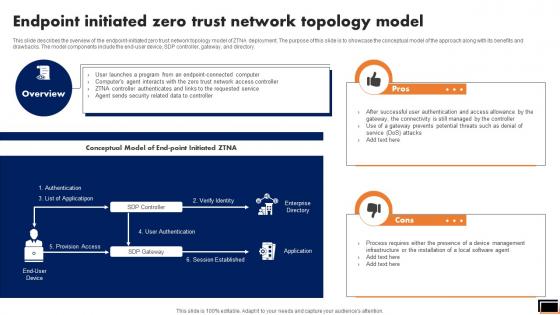
Endpoint Initiated Zero Trust Network Topology Model Software Defined Perimeter SDP
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Endpoint Initiated Zero Trust Network Topology Model Software Defined Perimeter SDP and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.
Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.
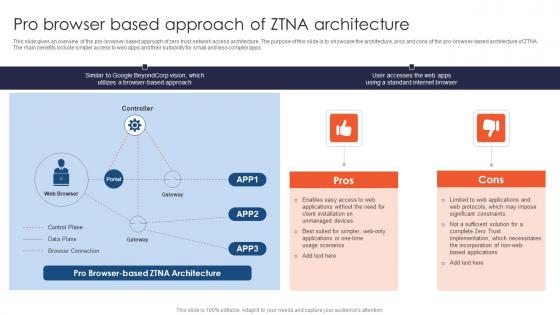
Zero Trust Network Access Pro Browser Based Approach Of ZTNA Architecture
This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps. There are so many reasons you need a Zero Trust Network Access Pro Browser Based Approach Of ZTNA Architecture. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps.

Building Trust With IoT Security Methods For Deploying Strong Device Authentication IoT SS V
This slide exhibits several IoT device authentication models for secure communication between machines. It includes methods such as digital certificates, hardware security module, trusted platform module and symmetric keys. Boost your pitch with our creative Building Trust With IoT Security Methods For Deploying Strong Device Authentication IoT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide exhibits several IoT device authentication models for secure communication between machines. It includes methods such as digital certificates, hardware security module, trusted platform module and symmetric keys.
Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V
If you are looking for a format to display your unique thoughts, then the professionally designed Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Our Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
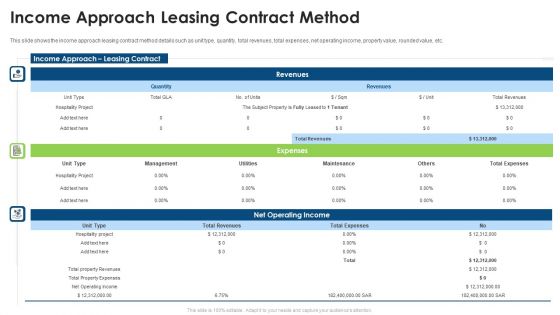
Commercial Property Evaluation Techniques Income Approach Leasing Contract Method Summary PDF
This slide shows the income approach leasing contract method details such as unit type, quantity, total revenues, total expenses, net operating income, property value, rounded value, etc. Deliver and pitch your topic in the best possible manner with this commercial property evaluation techniques income approach leasing contract method summary pdf. Use them to share invaluable insights on management, total revenues, total expenses, net operating income and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
ITIL Seven Guiding Fundamentals For Organization Icons PDF
This slide explains seven principles framework for information technology infrastructure library to help company improve business capabilities. It includes elements such as focus on value, current status analysis, holistic working, etc. Presenting ITIL Seven Guiding Fundamentals For Organization Icons PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Focus Value, Current Status Analysis, Progress Iteratively Feedback. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Service Initiated Zero Trust Network Topology Model Software Defined Perimeter SDP
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Find a pre-designed and impeccable Service Initiated Zero Trust Network Topology Model Software Defined Perimeter SDP. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.
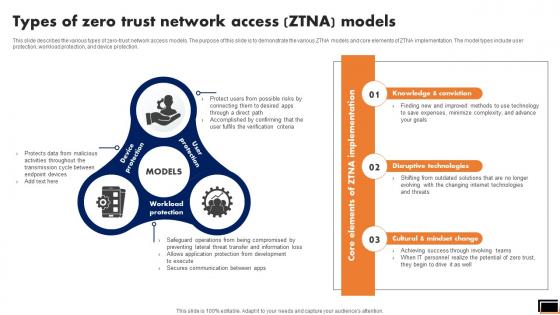
Types Of Zero Trust Network Access Ztna Models Software Defined Perimeter SDP
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Make sure to capture your audiences attention in your business displays with our gratis customizable Types Of Zero Trust Network Access Ztna Models Software Defined Perimeter SDP. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.
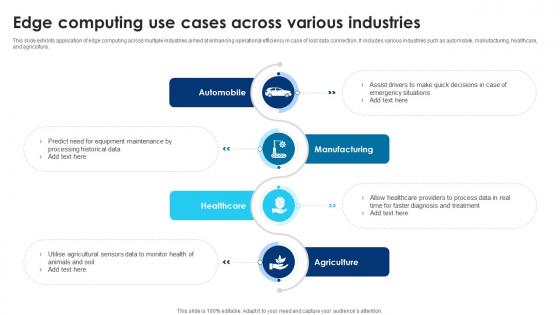
Building Trust With IoT Security Edge Computing Use Cases AcroSS Various Industries IoT SS V
This slide exhibits application of edge computing across multiple industries aimed at enhancing operational efficiency in case of lost data connection. It includes various industries such as automobile, manufacturing, healthcare, and agriculture. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Building Trust With IoT Security Edge Computing Use Cases AcroSS Various Industries IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Building Trust With IoT Security Edge Computing Use Cases AcroSS Various Industries IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide exhibits application of edge computing across multiple industries aimed at enhancing operational efficiency in case of lost data connection. It includes various industries such as automobile, manufacturing, healthcare, and agriculture.

Building Trust With IoT Security Overall Impact Of IoT Security Breaches Incidents IoT SS V
This slide includes IoT security breaches impact on an organisations operational capabilities, hindering the ability to function properly. It includes impacts such as financial burden, operations disruptions, and reputational damage. Create an editable Building Trust With IoT Security Overall Impact Of IoT Security Breaches Incidents IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Building Trust With IoT Security Overall Impact Of IoT Security Breaches Incidents IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide includes IoT security breaches impact on an organisations operational capabilities, hindering the ability to function properly. It includes impacts such as financial burden, operations disruptions, and reputational damage.
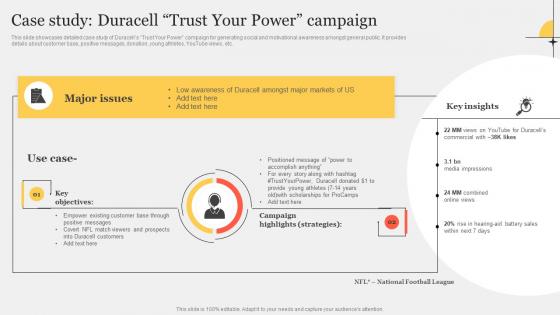
Case Study Duracell Trust Your Power Campaign Improving Customer Interaction Through Clipart Pdf
This slide showcases detailed case study of Duracells Trust Your Power campaign for generating social and motivational awareness amongst general public. It provides details about customer base, positive messages, donation, young athletes, YouTube views, etc.Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Case Study Duracell Trust Your Power Campaign Improving Customer Interaction Through Clipart Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases detailed case study of Duracells Trust Your Power campaign for generating social and motivational awareness amongst general public. It provides details about customer base, positive messages, donation, young athletes, YouTube views, etc.

Reasons To Adopt Zero Trust Network Access Model Software Defined Perimeter SDP
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Reasons To Adopt Zero Trust Network Access Model Software Defined Perimeter SDP to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Reasons To Adopt Zero Trust Network Access Model Software Defined Perimeter SDP. This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on.

Zero Trust Network Access Vs Virtual Private Network Software Defined Perimeter SDP
This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Slidegeeks has constructed Zero Trust Network Access Vs Virtual Private Network Software Defined Perimeter SDP after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access.
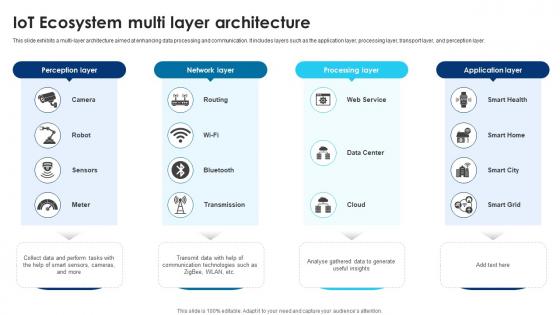
Building Trust With IoT Security IoT Ecosystem Multi Layer Architecture IoT SS V
This slide exhibits a multi-layer architecture aimed at enhancing data processing and communication. It includes layers such as the application layer, processing layer, transport layer, and perception layer. Presenting this PowerPoint presentation, titled Building Trust With IoT Security IoT Ecosystem Multi Layer Architecture IoT SS V, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Building Trust With IoT Security IoT Ecosystem Multi Layer Architecture IoT SS V. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Building Trust With IoT Security IoT Ecosystem Multi Layer Architecture IoT SS V that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide exhibits a multi-layer architecture aimed at enhancing data processing and communication. It includes layers such as the application layer, processing layer, transport layer, and perception layer.


 Continue with Email
Continue with Email

 Home
Home


































