Executive Summary Security

Common Use Cases Of Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc. Slidegeeks is here to make your presentations a breeze with Common Use Cases Of Tokenization In Data Security Securing Your Data Ppt Sample With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc.
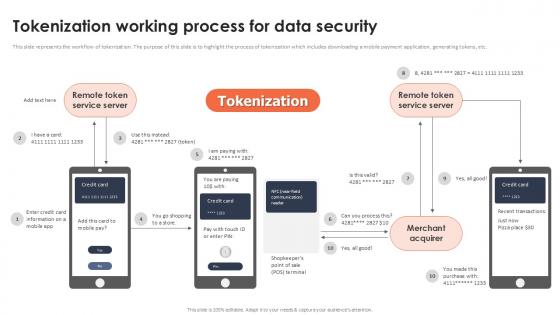
Tokenization Working Process For Data Security Securing Your Data Ppt Presentation
This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Find highly impressive Tokenization Working Process For Data Security Securing Your Data Ppt Presentation on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Tokenization Working Process For Data Security Securing Your Data Ppt Presentation for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc.
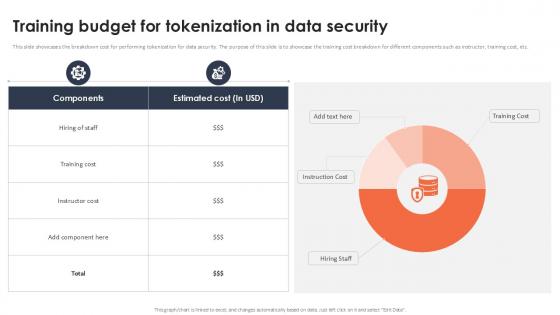
Training Budget For Tokenization In Data Security Securing Your Data Ppt Slide
This slide showcases the breakdown cost for performing tokenization for data security. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor, training cost, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Training Budget For Tokenization In Data Security Securing Your Data Ppt Slide and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases the breakdown cost for performing tokenization for data security. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor, training cost, etc.

Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example
This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client. Slidegeeks is here to make your presentations a breeze with Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client.

CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway. This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment.
Securing Windows With Network Security System Ppt PowerPoint Presentation File Slides PDF
Presenting this set of slides with name securing windows with network security system ppt powerpoint presentation file slides pdf. The topics discussed in these slide is securing windows with network security system. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
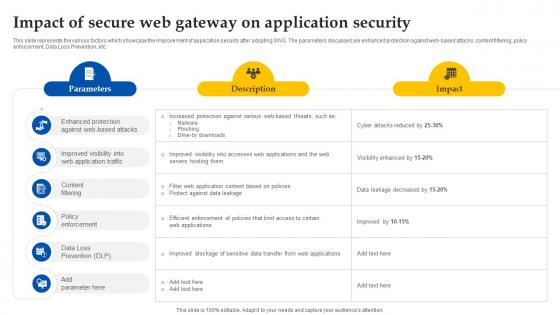
Web Access Control Solution Impact Of Secure Web Gateway On Application Security
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Welcome to our selection of the Web Access Control Solution Impact Of Secure Web Gateway On Application Security. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc.

Data Security Benefits Of Adopting Tokenization Securing Your Data Ppt Presentation
This slide discusses the cons of tokenization. The purpose of this slide is to showcase the advantages of tokenization such as utilizing less resources, decreases risk, stimulates innovation, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Data Security Benefits Of Adopting Tokenization Securing Your Data Ppt Presentation and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide discusses the cons of tokenization. The purpose of this slide is to showcase the advantages of tokenization such as utilizing less resources, decreases risk, stimulates innovation, etc.
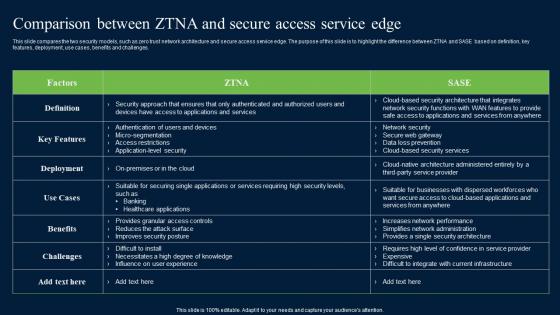
Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Slidegeeks is here to make your presentations a breeze with Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.
Icons Slide For Secure Access Service Edge Cloud Security Model Ppt Gallery Layout PDF
Help your business to create an attention-grabbing presentation using our Icons Slide For Secure Access Service Edge Cloud Security Model Ppt Gallery Layout PDF set of slides. The slide contains innovative icons that can be flexibly edited. Choose this Icons Slide For Secure Access Service Edge Cloud Security Model Ppt Gallery Layout PDF template to create a satisfactory experience for your customers. Go ahead and click the download button.
Wireless Network Security System Icon Of Cloud Servers To Secure Data Clipart PDF
Persuade your audience using this wireless network security system icon of cloud servers to secure data clipart pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including wireless network security system icon of cloud servers to secure data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
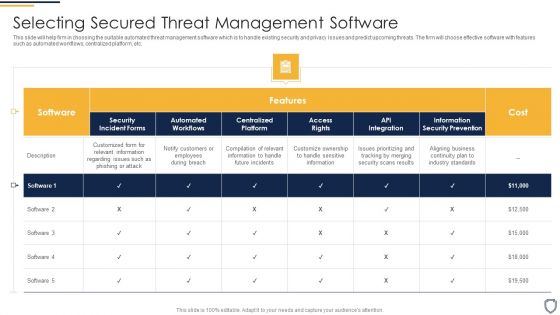
Corporate Security And Risk Management Selecting Secured Threat Management Software Introduction PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative corporate security and risk management selecting secured threat management software introduction pdf bundle. Topics like selecting secured threat management software can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF today and make your presentation stand out from the rest.
Agenda For Secure Access Service Edge Cloud Security Model Ppt Outline Maker PDF
Find a pre designed and impeccable Agenda For Secure Access Service Edge Cloud Security Model Ppt Outline Maker PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF.
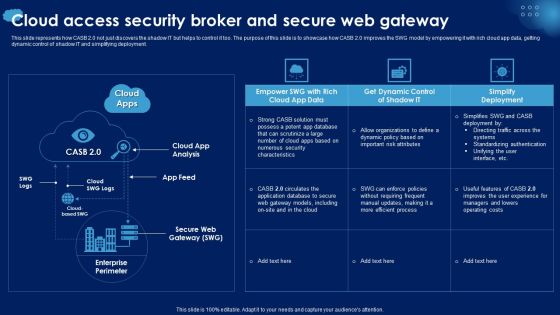
Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

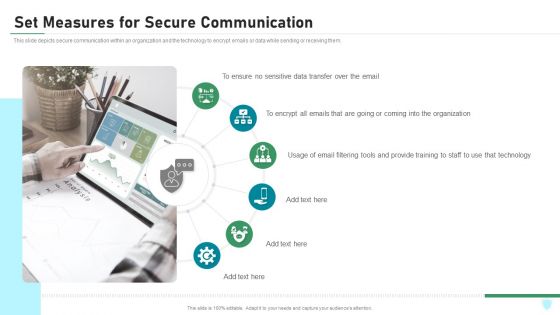
Info Security Set Measures For Secure Communication Ppt PowerPoint Presentation Gallery Graphics Design PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a info security set measures for secure communication ppt powerpoint presentation gallery graphics design pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sensitive data, organization, email filtering tools, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Set Measures For Secure Communication IT Security IT Ppt Styles Background Designs PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. Presenting set measures for secure communication it security it ppt styles background designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data transfer, organization, technology, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
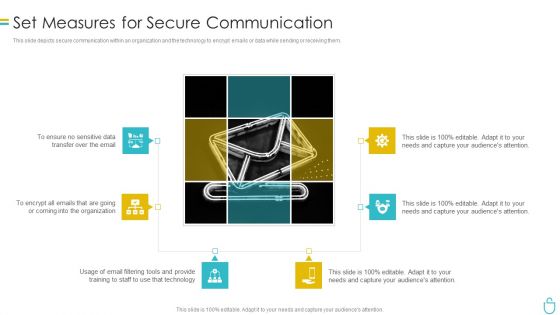
Information Security Set Measures For Secure Communication Ppt Outline Slide Download PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a information security set measures for secure communication ppt outline slide download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
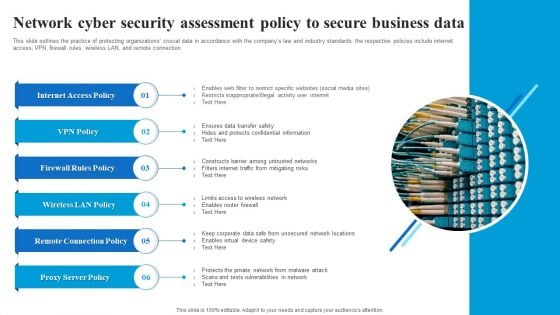
Network Cyber Security Assessment Policy To Secure Business Data Microsoft PDF
This slide outlines the practice of protecting organizations crucial data in accordance with the companys law and industry standards. the respective policies include internet access, VPN, firewall rules, wireless LAN, and remote connection. Showcasing this set of slides titled Network Cyber Security Assessment Policy To Secure Business Data Microsoft PDF. The topics addressed in these templates are Internet Access Policy, Firewall Rules Policy, Wireless LAN Policy, Remote Connection Policy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.
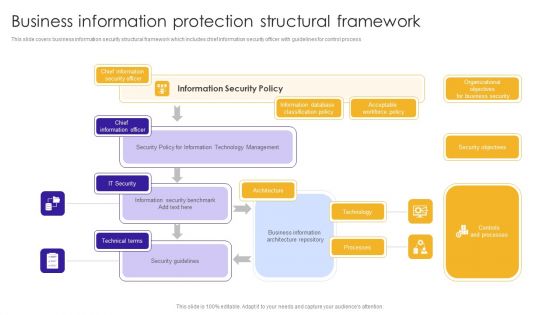
Business Information Protection Structural Framework Summary PDF
This slide covers business information security structural framework which includes chief information security officer with guidelines for control process.Showcasing this set of slides titled Business Information Protection Structural Framework Summary PDF. The topics addressed in these templates are Information Database, Classification Policy, Architecture Repository. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Execution Of ICT Strategic Plan Selection For Cloud Management Platform Tools Summary PDF
This slide represents selection for cloud management tools. It covers asset inventory management, workflow automation, security, access control etc. Want to ace your presentation in front of a live audience Our Execution Of ICT Strategic Plan Selection For Cloud Management Platform Tools Summary PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Offer Selection Procedure From CPA Networks Executing Cost Per Action Marketing Summary Pdf
This slide showcase the process of selection of CPA network on the bases on various categories. It compare offers on the basis of price, model type, category, network, and offer timeline. Welcome to our selection of the Offer Selection Procedure From CPA Networks Executing Cost Per Action Marketing Summary Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide showcase the process of selection of CPA network on the bases on various categories. It compare offers on the basis of price, model type, category, network, and offer timeline.

Security Officer Service Company Profile Table Of Contents Ppt PowerPoint Presentation Gallery Influencers PDF
Deliver an awe inspiring pitch with this creative Security Officer Service Company Profile Table Of Contents Ppt PowerPoint Presentation Gallery Influencers PDF bundle. Topics like Executive Summary, Business Model, Management Team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
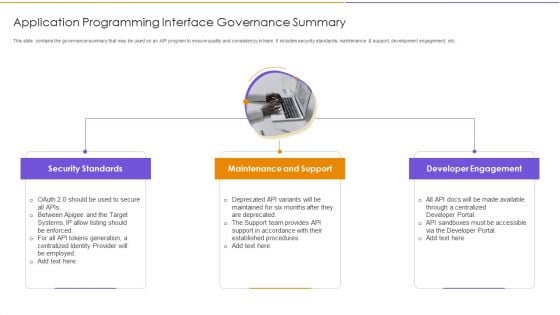
Application Programming Interface Governance Summary Pictures PDF
This slide contains the governance summary that may be used on an API program to ensure quality and consistency in team. It includes security standards, maintenance and support, development engagement, etc. Persuade your audience using this Application Programming Interface Governance Summary Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Maintenance And Support, Developer Engagement, Security Standards. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Compliance Management Procedure Key Challenges Summary PDF
This slide presents compliance management process key challenges faced by organisations, helpful in determining focus areas for improvement. It includes issues such as distributed teams, third parties, volatile security an unclear language Presenting Compliance Management Procedure Key Challenges Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Distributed Teams, Third Parties, Volatile Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Implementation Framework Cybersecurity Maintenance Checklist Ppt Inspiration Grid PDF
Presenting this set of slides with name cyber security implementation framework cybersecurity maintenance checklist ppt inspiration grid pdf. The topics discussed in these slides are activities, daily, weekly, monthly, quarterly, executive reporting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
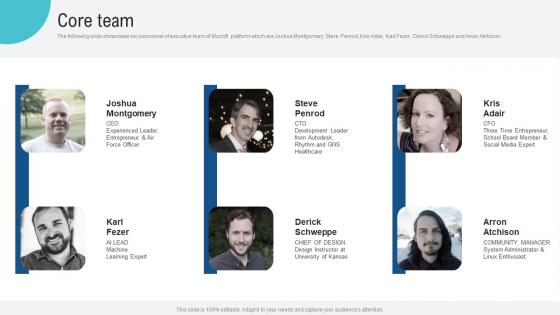
Core Team Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf
The following slide showcases key personnel of executive team of Mycroft platform which are Joshua Montgomery, Steve Penrod, Kris Adair, Karl Fezer, Derick Schweppe and Arron Atchison. This modern and well arranged Core Team Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The following slide showcases key personnel of executive team of Mycroft platform which are Joshua Montgomery, Steve Penrod, Kris Adair, Karl Fezer, Derick Schweppe and Arron Atchison.
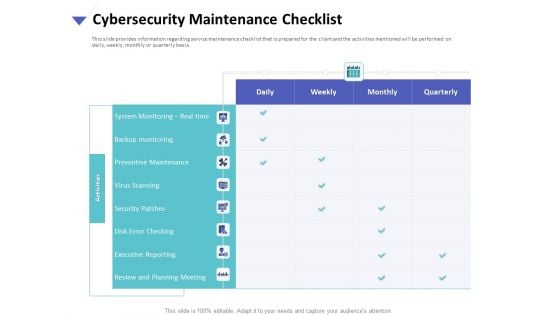
Strategies To Mitigate Cyber Security Risks Cybersecurity Maintenance Checklist Ppt Slides Graphics Tutorials PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity maintenance checklist ppt slides graphics tutorials pdf. The topics discussed in these slides are system monitoring, real time, backup monitoring, preventive maintenance, virus scanning, security patches, disk error checking, executive reporting, review and planning meeting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

SIEM Integrations Ppt Summary Templates PDF
This is a siem integrations ppt summary templates pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Events, Network Logs, Applications and Devices, IT Infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cyber Security For Your Organization Business Impact Assessment Ppt Icon Designs PDF
Presenting this set of slides with name cyber security for your organization business impact assessment ppt icon designs pdf. This is a three stage process. The stages in this process are department function, executive dexter hastings, employees, bcp representative, primary business function, strengths, weaknesses, loss impact. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
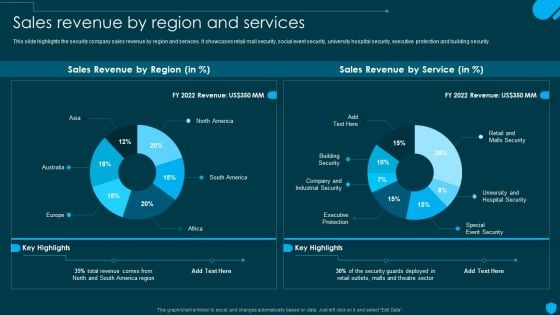
Security And Human Resource Services Business Profile Sales Revenue By Region Brochure PDF
This slide highlights the security company sales revenue by region and services. It showcases retail mall security, social event security, university hospital security, executive protection and building security. The Security And Human Resource Services Business Profile Sales Revenue By Region Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Benefits Of ISO 27001 Certification Summary PDF
This slide displays various organizational benefits after getting ISO 27001 certification. Benefits included are information confidentiality, low operational cost, increase in the trust of valuable partners and customers and competitive advantage.Presenting Benefits Of ISO 27001 Certification Summary PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Security Breaches, Competitive Advantage, Recognized Standard. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
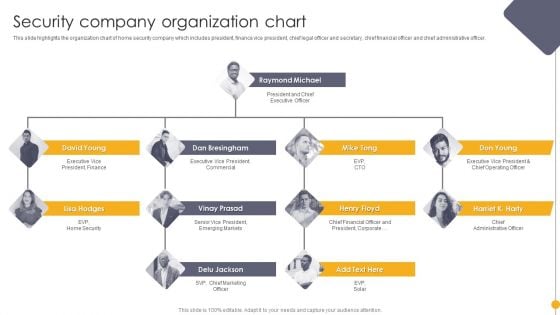
Portable Home Safety Systems Company Profile Security Company Organization Chart Demonstration PDF
This slide highlights the organization chart of home security company which includes president, finance vice president, chief legal officer and secretary, chief financial officer and chief administrative officer. Presenting Portable Home Safety Systems Company Profile Security Company Organization Chart Demonstration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Chief Financial, Executive Vice President, Chief Operating Officer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Lock Red Heart Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Key Lock Red Heart Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will let you Leave a lasting impression to your audiences. They possess an inherent longstanding recall factor. Use our Curves and Lines PowerPoint Templates because It can Leverage your style with our PowerPoint Templates and Slides. Charm your audience with your ability. Present our Festival PowerPoint Templates because It is Aesthetically crafted by artistic young minds. Our PowerPoint Templates and Slides are designed to display your dexterity. Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Download and present our Stars PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need.Use these PowerPoint slides for presentations relating to Locked red heart security, security, shapes, festival, stars, curves and lines. The prominent colors used in the PowerPoint template are Red, Yellow, Black. Be the executive with our Key Lock Red Heart Security PowerPoint Templates Ppt Backgrounds For Slides 0213. They will project your authority.
Information Mapping Process Ppt PowerPoint Presentation Summary Microsoft Cpb
This is a information mapping process ppt powerpoint presentation summary microsoft cpb. This is a four stage process. The stages in this process are information mapping process.

As A Service Deployment Approach Zero Trust Network Security Microsoft Pdf
This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. Boost your pitch with our creative As A Service Deployment Approach Zero Trust Network Security Microsoft Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software.

Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF
The following slide showcases key personnel of executive team of IT company which are CEO, chief architect, VP marketing, sales, product, engineering, chief data scientist, chief scientist, etc. Get a simple yet stunning designed Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Global Data Security Industry Report Geographical Analysis For Cybersecurity Industry IR SS V
The slide highlights the geographical summary of current state of cybersecurity industry. The purpose of the slide is to provide insights on cybersecurity landscape, trends, development at regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Global Data Security Industry Report Geographical Analysis For Cybersecurity Industry IR SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The slide highlights the geographical summary of current state of cybersecurity industry. The purpose of the slide is to provide insights on cybersecurity landscape, trends, development at regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities.
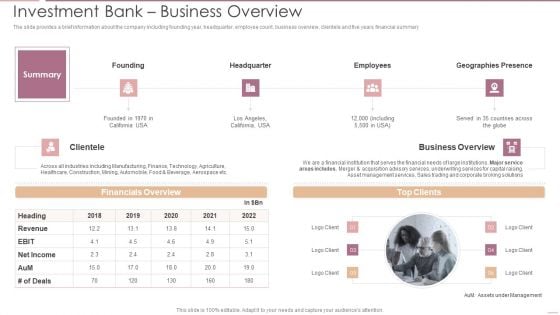
Investment Banking Security Underwriting Pitchbook Investment Bank Business Overview Themes PDF
The slide provides a brief information about the company including founding year, headquarter, employee count, business overview, clientele and five years financial summary .Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook Investment Bank Business Overview Themes PDF bundle. Topics like Financials Overview, Business Overview, Geographies Presence can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
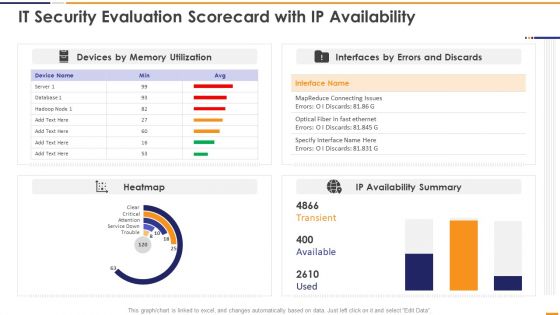
IT Security Evaluation Scorecard With Ip Availability Ppt Pictures Portrait PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Ip Availability Ppt Pictures Portrait PDF. Use them to share invaluable insights on Devices Memory Utilization, Interfaces Errors Discards, IP Availability Summary and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
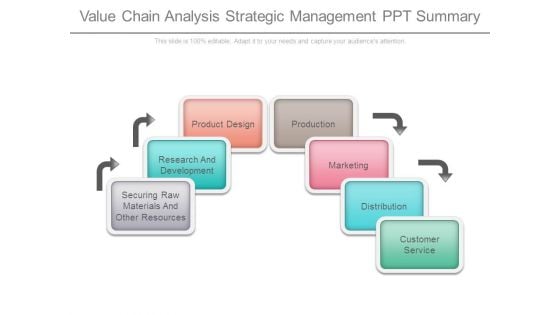
Value Chain Analysis Strategic Management Ppt Summary
This is a value chain analysis strategic management ppt summary. This is a seven stage process. The stages in this process are securing raw materials and other resources, research and development, product design, production, marketing, distribution, customer service.
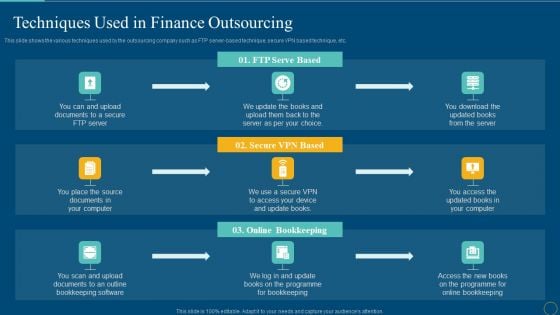
Techniques Used In Finance Outsourcing Summary PDF
This slide shows the various techniques used by the outsourcing company such as FTP server-based technique, secure VPN based technique, etc.This is a techniques used in finance outsourcing summary pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like documents to a secure, programme for bookkeeping, bookkeeping software You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
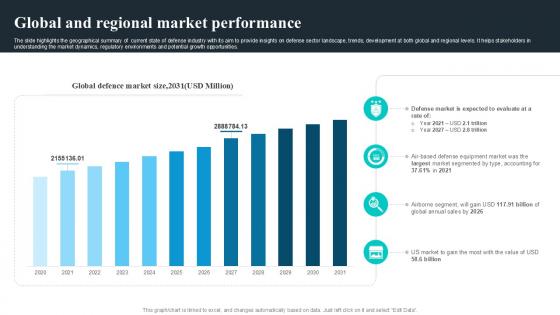
Global And Regional Market Performance Global Security Industry PPT Slide IR SS V
The slide highlights the geographical summary of current state of defense industry with its aim to provide insights on defense sector landscape, trends, development at both global and regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities. If you are looking for a format to display your unique thoughts, then the professionally designed Global And Regional Market Performance Global Security Industry PPT Slide IR SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global And Regional Market Performance Global Security Industry PPT Slide IR SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The slide highlights the geographical summary of current state of defense industry with its aim to provide insights on defense sector landscape, trends, development at both global and regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities.
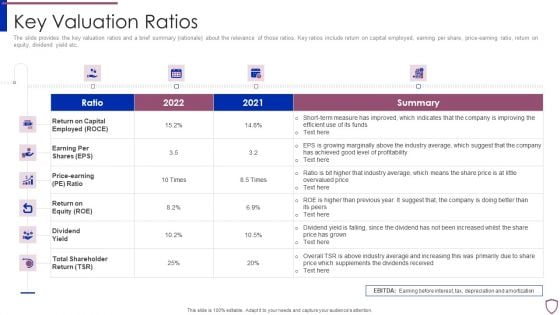
Financing Catalogue For Security Underwriting Agreement Key Valuation Ratios Clipart PDF
The slide provides the key valuation ratios and a brief summary rationale about the relevance of those ratios. Key ratios include return on capital employed, earning per share, price-earning ratio, return on equity, dividend yield etc. Deliver and pitch your topic in the best possible manner with this financing catalogue for security underwriting agreement key valuation ratios clipart pdf. Use them to share invaluable insights on return on capital employed, earning per shares, price earning, return on equity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112
Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112-Use this awesome PowerPoint template for property and ownership concept. This template features golden key with welcome home text. It portrays the concept of home, happiness, investment, mortgage, ownership, property, residence, security etc. This image has been conceived to enable you to emphatically communicate your ideas in your Real Estate PPT presentations. Our PPT images are so ideally designed that it reveals the very basis of our PPT template are an effective tool to make your clients understand.-Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112-This PowerPoint template can be used for presentations relating to-Gold Key With Welcome Home, Security, Business, Technology, Design, Metaphor Flood your audience with great slides with our Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112. Try us out and see what a difference our templates make.
Vector Showing Safe And Secure Intranet Of Company Ppt PowerPoint Presentation Summary Icons PDF
Persuade your audience using this vector showing safe and secure intranet of company ppt powerpoint presentation summary icons pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including vector showing safe and secure intranet of company. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Network Threat Prevention And Security Vector Icon Ppt PowerPoint Presentation Outline Example Introduction PDF
Presenting network threat prevention and security vector icon ppt powerpoint presentation outline example introduction pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including network threat prevention and security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Yellow Computer Folder With Golden Key Security PowerPoint Templates And PowerPoint Themes 1112
We present our Yellow Computer Folder With Golden Key Security PowerPoint Templates And PowerPoint Themes 1112.Use our Computer PowerPoint Templates because, Tachometer:- You have a good idea of the roadmap to your desired destination. Use our Internet PowerPoint Templates because, Display your ideas and highlight thei ability to accelerate the the growth of your company and you. Use our Communication PowerPoint Templates because,Explain the process by which you intend to right it. Use our Security PowerPoint Templates because, Build on your foundation or prepare for change ahead to enhance the future. Use our Symbol PowerPoint Templates because, You have the plans to increase the strength of your business relationships.Use these PowerPoint slides for presentations relating to Yellow computer folder with key Internet Security Computer Symbol Communication. The prominent colors used in the PowerPoint template are Yellow, White, Orange Soak in the energy our Yellow Computer Folder With Golden Key Security PowerPoint Templates And PowerPoint Themes 1112 emit. Your thoughts will find them exhilirating.

Laptop With Lock Internet Security PowerPoint Templates Ppt Backgrounds For Slides 1112
We present our Laptop With Lock Internet Security PowerPoint Templates PPT Backgrounds For Slides 1112.Download and present our Technology PowerPoint Templates because we provide the means to project your views. Download and present our Business PowerPoint Templates because this template can project the path to sucess that you have charted. Use our Security PowerPoint Templates because you can Explore the various hues and layers existing in your in your plans and processes using this slide. Use our Computer PowerPoint Templates because it demonstrates the seeds of many of our successes. Download and present our Shapes PowerPoint Templates because the Gear train is a basic element of living and daily business.Use these PowerPoint slides for presentations relating to Lock laptop keyboard safety security on the internet, technology, Security, business, shapes, computer. The prominent colors used in the PowerPoint template are Blue, Gray, Yellow. People tell us our Laptop With Lock Internet Security PowerPoint Templates PPT Backgrounds For Slides 1112 are Flirty. Presenters tell us our technology PowerPoint templates and PPT Slides are Pretty. PowerPoint presentation experts tell us our Laptop With Lock Internet Security PowerPoint Templates PPT Backgrounds For Slides 1112 provide great value for your money. Be assured of finding the best projection to highlight your words. Customers tell us our on PowerPoint templates and PPT Slides are Reminiscent. Customers tell us our Laptop With Lock Internet Security PowerPoint Templates PPT Backgrounds For Slides 1112 are Fantastic. Customers tell us our security PowerPoint templates and PPT Slides are Stunning. Develop their craving for your creativity. Become a brand name with our Laptop With Lock Internet Security PowerPoint Templates Ppt Backgrounds For Slides 1112.

Laptop With Lock And Key Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Internet PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Download and present our Computer PowerPoint Templates because It can Conjure up grand ideas with our magical PowerPoint Templates and Slides. Leave everyone awestruck by the end of your presentation. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Use our Technology PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas.Use these PowerPoint slides for presentations relating to Computer security concept, computer, internet, success, technology, security. The prominent colors used in the PowerPoint template are Brown, Black, Gray. People tell us our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. People tell us our security PowerPoint templates and PPT Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. PowerPoint presentation experts tell us our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 are incredible easy to use. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. Presenters tell us our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. The feedback we get is that our technology PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. Examine the causes with our Laptop With Lock And Key Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Let everyone know what's behind it all.

Safety First Concept Business Security PowerPoint Templates And PowerPoint Themes 1112
We present our Safety First Concept Business Security PowerPoint Templates And PowerPoint Themes 1112.Use our Computer PowerPoint Templates because, Emphasise on any critical or key factors within them. Use our Technology PowerPoint Templates because,And watch them strenthen your companys sinews. Use our Business PowerPoint Templates because,Show them how you can save the day. Use our Internet PowerPoint Templates because, Set out the goals and your plan of action for them. Use our Security PowerPoint Templates because, Clarity of thought has been the key to your growth.Use these PowerPoint slides for presentations relating to Safety first concept, computer, technology, business, internet, security . The prominent colors used in the PowerPoint template are Red, White, Black Index your ascent with our Safety First Concept Business Security PowerPoint Templates And PowerPoint Themes 1112. Illustrate every step of the way.
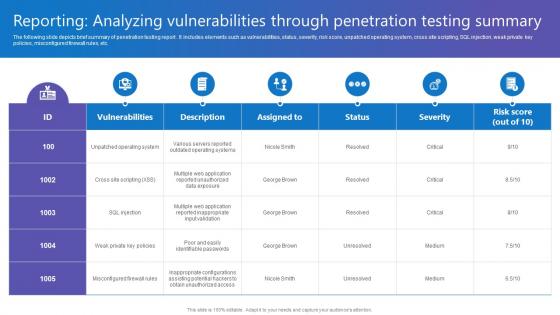
Reporting Analyzing Vulnerabilities Comprehensive Guide To Blockchain Digital Security Inspiration Pdf
The following slide depicts brief summary of penetration testing report . It includes elements such as vulnerabilities, status, severity, risk score, unpatched operating system, cross site scripting, SQL injection, weak private key policies, misconfigured firewall rules, etc. Do you know about Slidesgeeks Reporting Analyzing Vulnerabilities Comprehensive Guide To Blockchain Digital Security Inspiration Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The following slide depicts brief summary of penetration testing report . It includes elements such as vulnerabilities, status, severity, risk score, unpatched operating system, cross site scripting, SQL injection, weak private key policies, misconfigured firewall rules, etc.
VPN Privacy And Security Vector Icon Ppt PowerPoint Presentation Model Slides PDF
Presenting vpn privacy and security vector icon ppt powerpoint presentation model slides pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including vpn privacy and security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Vector Illustration Of IT Security Measures For Strong Protection Ppt PowerPoint Presentation File Outline PDF
Persuade your audience using this vector illustration of it security measures for strong protection ppt powerpoint presentation file outline pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including vector illustration of it security measures for strong protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
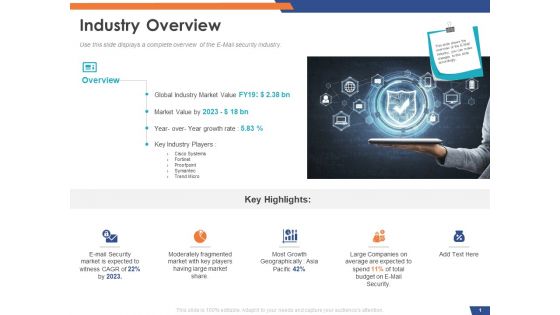
Email Security Market Research Report Industry Overview Ppt Outline Graphic Images PDF
Presenting this set of slides with name email security market research report industry overview ppt outline graphic images pdf. This is a two stage process. The stages in this process are moderately fragmented market with key players having large market share, global industry market value, key industry players. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Vector Showing Computer Security Threats Ppt PowerPoint Presentation Ideas Introduction PDF
Persuade your audience using this vector showing computer security threats ppt powerpoint presentation ideas introduction pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including vector showing computer security threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































