Gap Analysis Of Security

Security Metrics Dashboard In Powerpoint And Google Slides Cpb
Introducing our well designed Security Metrics Dashboard In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Metrics Dashboard. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Metrics Dashboard In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Server Security Checklist In Powerpoint And Google Slides Cpb
Introducing our well designed Server Security Checklist In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Server Security Checklist. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Server Security Checklist In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Schneider Electric Security Systems In Powerpoint And Google Slides Cpb
Introducing our well designed Schneider Electric Security Systems In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Schneider Electric Security Systems. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Schneider Electric Security Systems In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Bracketing Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well designed Bracketing Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Bracketing Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Bracketing Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Company In Powerpoint And Google Slides Cpb
Introducing our well designed Security Company In Powerpoint And Google Slides Cpb This PowerPoint design presents information on topics like Security Company Profile Presentation As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Company In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Monitoring Dashboard In Powerpoint And Google Slides Cpb
Introducing our well designed Security Monitoring Dashboard In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Monitoring Dashboard. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Monitoring Dashboard In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Sphere Security In Powerpoint And Google Slides Cpb
Introducing our well designed Sphere Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Sphere Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Sphere Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Security Pick Lines In Powerpoint And Google Slides Cpb
Introducing our well designed Cyber Security Pick Lines In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Security Pick Lines. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cyber Security Pick Lines In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Pattern Documents In Powerpoint And Google Slides Cpb
Introducing our well designed Security Pattern Documents In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Pattern Documents. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Pattern Documents In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Devsecops Security Checklist In Powerpoint And Google Slides Cpb
Introducing our well designed Devsecops Security Checklist In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Devsecops Security Checklist. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Devsecops Security Checklist In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Wireless Security Presentation In Powerpoint And Google Slides Cpb
Introducing our well designed Wireless Security Presentation In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Wireless Security Presentation. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Wireless Security Presentation In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Chip Security Flaw In Powerpoint And Google Slides Cpb
Introducing our well-designed Chip Security Flaw In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Chip Security Flaw. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Chip Security Flaw In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Computer Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Computer Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Computer Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Computer Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Smart Watch Security System In Powerpoint And Google Slides Cpb
Introducing our well designed Smart Watch Security System In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Smart Watch Security System. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Smart Watch Security System In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Information Security Policy In Powerpoint And Google Slides Cpb
Introducing our well designed Information Security Policy In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Information Security Policy. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Information Security Policy In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Facial Recognition Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Facial Recognition Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Facial Recognition Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Facial Recognition Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Best Cyber Security World In Powerpoint And Google Slides Cpb
Introducing our well designed Best Cyber Security World In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Best Cyber Security World. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Best Cyber Security World In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Complete Guide To Launch Best Practices For Website Security Management
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Get a simple yet stunning designed Complete Guide To Launch Best Practices For Website Security Management. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Complete Guide To Launch Best Practices For Website Security Management can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc.
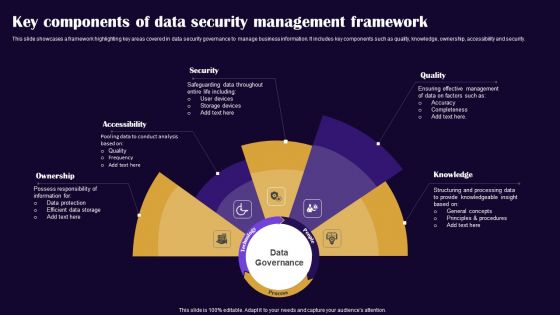
Key Components Of Data Security Management Framework Pictures PDF
This slide showcases a framework highlighting key areas covered in data security governance to manage business information. It includes key components such as quality, knowledge, ownership, accessibility and security. Presenting Key Components Of Data Security Management Framework Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Ownership, Accessibility, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
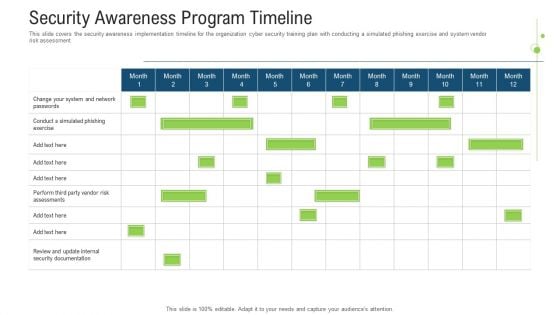
Security Awareness Program Timeline Ppt Outline Introduction PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe inspiring pitch with this creative Security Awareness Program Timeline Ppt Outline Introduction Pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Cloud Security Assessment Cont Background PDF
This is a Table Of Contents For Cloud Security Assessment Cont Background PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Security, Security Responsibilities, Security Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Cloud Security Assessment Ideas PDF
Presenting Table Of Contents For Cloud Security Assessment Ideas PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Cloud Security, Security Different, Security Is Important. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Essential Measures For Business Cyber Security Assessment Plan Rules PDF
This slide demonstrates the safety measures in a business security plan that helps in decreasing the frequency of security threats data hacks, information breaches etc. The measures include handy backups, multi layer security, protective software, and employee training. Presenting Essential Measures For Business Cyber Security Assessment Plan Rules PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comprehensive Guide To Blockchain Digital Security Risk Management Complete Deck
This Comprehensive Guide To Blockchain Digital Security Risk Management Complete Deck will give you an idea about business planning and how it helps in achievement of objectives and goals. With seventy seven slides,this complete deck aims to ensure that business planning is internalized in the audience. The 100 percent customisable template is also colour coded in a way that visually the message has a very clear impact. The presenter might not be a business expert,but the high quality PPT forces him her to rise to the ocassion. Download now to wow a roomful of people. Our Comprehensive Guide To Blockchain Digital Security Risk Management Complete Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Data Breach Prevention Recognition Security Awareness Program Timeline Inspiration PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security awareness program timeline inspiration pdf. Use them to share invaluable insights on security awareness, implementation timeline, organization, cyber security training plan, risk assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Voice Assistance Security Platform Investor Funding Presentation Complete Deck
This unique Voice Assistance Security Platform Investor Funding Presentation Complete Deck is a compendium of amazing information,actionable ideas on all business issues. The design of the presentation template ensures you have an ample opportunity to pick and choose areas you might want to emphasize. The thirty eight slides in the presentation template or all wonderfully colour coded to and ensure that you can get on with delivering your message with speed,and amazing effectiveness. Talk about management,leadership,change management,digital transformation etc with the unparalleled advantage of 100 percent customization of each and every elements of all our slides. Download now and see presentation take on a new dimension. Our Voice Assistance Security Platform Investor Funding Presentation Complete Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Exploring Investment Opportunities With Security Token Offerings Complete Deck
This seventy nine slide Exploring Investment Opportunities With Security Token Offerings Complete Deck is your content ready tool to impress the stakeholders with your business planning and its manner of execution. Showcase your ideas and how you plan to make them real in detail with this PPT Template Bundle. The slides have the conceptual bandwidth to present the crucial aspects of your plan, such as funding, marketing, resource allocation, timeline, roadmap, and more. When you present your plans with this PPT Layout, the stakeholders are sure to come on board because you will be able to present a succinct, thought-out, winning project. Download this Complete Deck now to take control into your hands. The 100 percent customizable offer is just too good to be resisted. Our Exploring Investment Opportunities With Security Token Offerings Complete Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
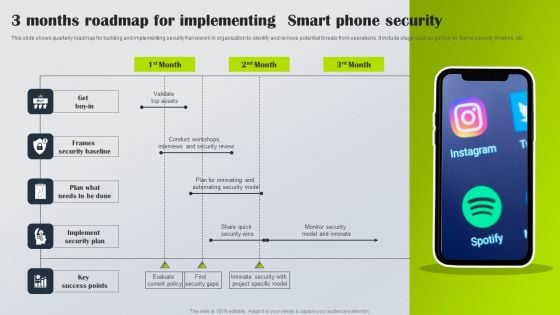
3 Months Roadmap For Implementing Smart Phone Security Information PDF
This slide shows quarterly roadmap for building and implementing security framework in organization to identify and remove potential threats from operations. It include stage such as get buy-in, frame security timeline, etc. Presenting 3 Months Roadmap For Implementing Smart Phone Security Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Get Buy In, Frames Security Baseline, Implement Security Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
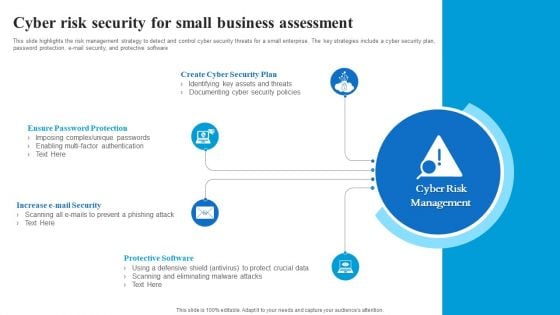
Cyber Risk Security For Small Business Assessment Brochure PDF
This slide highlights the risk management strategy to detect and control cyber security threats for a small enterprise. The key strategies include a cyber security plan, password protection, e-mail security, and protective software. Presenting Cyber Risk Security For Small Business Assessment Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Create Cyber Security Plan, Ensure Password Protection, Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
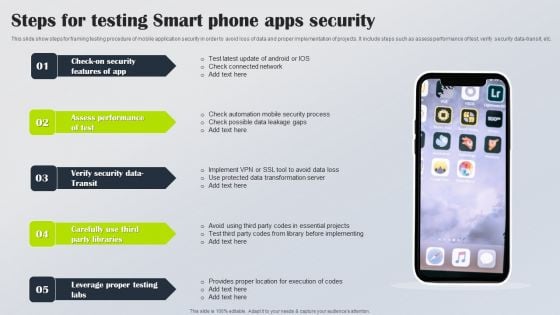
Steps For Testing Smart Phone Apps Security Inspiration PDF
This slide show steps for framing testing procedure of mobile application security in order to avoid loss of data and proper implementation of projects. It include steps such as assess performance of test, verify security data transit, etc. Presenting Steps For Testing Smart Phone Apps Security Inspiration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Check Security Features App, Assess Performance Test, Verify Security Data Transit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Checklist Ppt Powerpoint Presentation Complete Deck With Slides
This Security Checklist Ppt Powerpoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing thirteen slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Security Checklist Ppt Powerpoint Presentation Complete Deck With Slides PPT slideshow. Our Security Checklist Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Distributed Ledger Security Ppt Powerpoint Presentation Complete Deck With Slides
This Distributed Ledger Security Ppt Powerpoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twenty slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Distributed Ledger Security Ppt Powerpoint Presentation Complete Deck With Slides PPT slideshow. Our Distributed Ledger Security Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Digital Security Metrics Ppt Powerpoint Presentation Complete Deck With Slides
This Digital Security Metrics Ppt Powerpoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing seventeen slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Digital Security Metrics Ppt Powerpoint Presentation Complete Deck With Slides PPT slideshow. Our Digital Security Metrics Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Virtual Security Hazards Ppt PowerPoint Presentation Complete Deck With Slides
This Virtual Security Hazards Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas,vision,thoughts,etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in house and outside presentations depending upon your needs and business demands. Entailing seventeen slides with a consistent design and theme,this template will make a solid use case. As it is intuitively designed,it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color,design,shapes,and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well thought and crafted presentation can be delivered with ease and precision by downloading this Virtual Security Hazards Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow. Our Virtual Security Hazards Ppt PowerPoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Develop Security Token Offering Plan Exploring Investment Opportunities Brochure Pdf
The following slide depicts sample security token offering STO plan to enable fundraising and crowd funding activities. It includes elements such as number of tokens, percentage allocated to public, private investors, pre-sale participants, project teams, reserve funds, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Develop Security Token Offering Plan Exploring Investment Opportunities Brochure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide depicts sample security token offering STO plan to enable fundraising and crowd funding activities. It includes elements such as number of tokens, percentage allocated to public, private investors, pre-sale participants, project teams, reserve funds, etc.

Email Security Industry Report In Powerpoint And Google Slides Cpb
Introducing our well-designed Email Security Industry Report In Powerpoint And Google Slides Cpb This PowerPoint design presents information on topics like Email Security Industry Report As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Email Security Industry Report In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
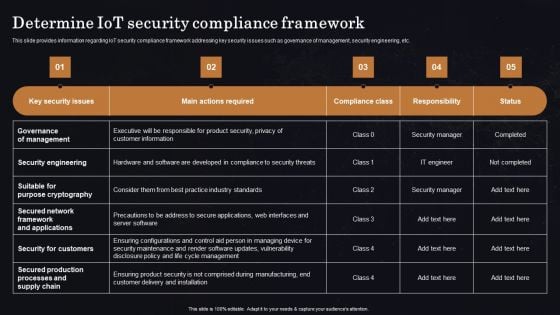
Determine Iot Security Compliance Framework Ppt Professional Vector PDF
This slide provides information regarding IoT security compliance framework addressing key security issues such as governance of management, security engineering, etc. Get a simple yet stunning designed Determine Iot Security Compliance Framework Ppt Professional Vector PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Determine Iot Security Compliance Framework Ppt Professional Vector PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide
This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc. Find highly impressive Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc.

Estimated Security Management Plan Critical Success Factors Microsoft PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this estimated security management plan critical success factors microsoft pdf. Use them to share invaluable insights on estimated security management plan critical success factors and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Estimated Security Management Plan Critical Success Factors Designs PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this estimated security management plan critical success factors designs pdf. Use them to share invaluable insights on security, management, implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
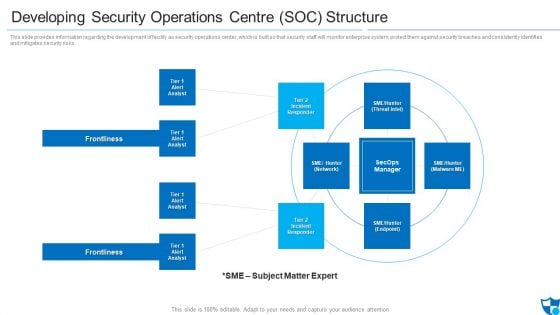
Developing Security Operations Centre SOC Structure Microsoft PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting developing security operations centre soc structure microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident responder, tier 2 incident responder, frontlines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
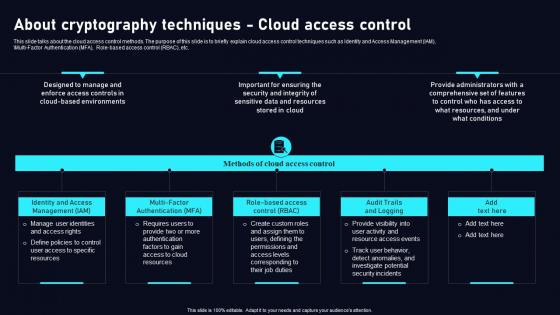
About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf
This slide talks about the cloud access control methods. The purpose of this slide is to briefly explain cloud access control techniques such as Identity and Access Management IAM, Multi Factor Authentication MFA, Role based access control RBAC, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf today and make your presentation stand out from the rest This slide talks about the cloud access control methods. The purpose of this slide is to briefly explain cloud access control techniques such as Identity and Access Management IAM, Multi Factor Authentication MFA, Role based access control RBAC, etc.

Comparison Of Various Security Awareness Training Software Elements PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver and pitch your topic in the best possible manner with this Comparison Of Various Security Awareness Training Software Elements PDF. Use them to share invaluable insights on Individualized Security, Industry Specific, Deployment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Steps For Internet Security Risk Assessment And Evaluation Microsoft Pdf
This slide showcase cyber risk assessment with standard risk identification to align organizational objective . It includes context establishment, risk identification, risk assessment and risk evaluation. Showcasing this set of slides titled Steps For Internet Security Risk Assessment And Evaluation Microsoft Pdf The topics addressed in these templates are Risk Identification, Risk Assessment, Risk Evaluation All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber risk assessment with standard risk identification to align organizational objective . It includes context establishment, risk identification, risk assessment and risk evaluation.
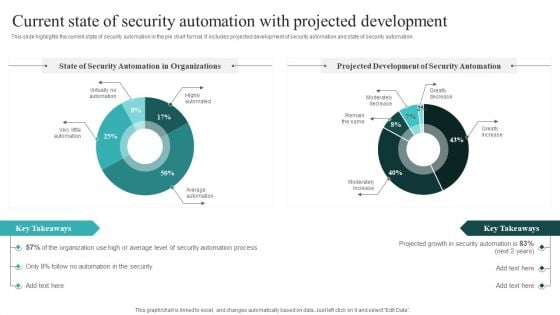
Current State Of Security Automation With Projected Development Slides PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. If you are looking for a format to display your unique thoughts, then the professionally designed IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
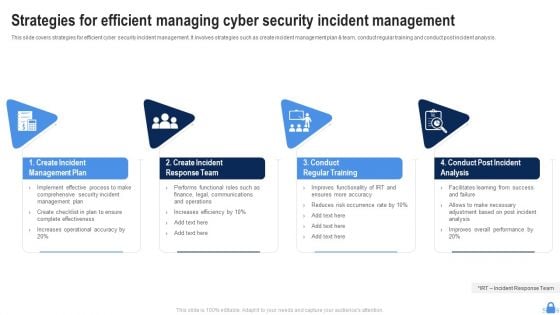
Strategies For Efficient Managing Cyber Security Incident Management Portrait PDF
This slide covers strategies for efficient cyber security incident management. It involves strategies such as create incident management plan and team, conduct regular training and conduct post incident analysis. Presenting Strategies For Efficient Managing Cyber Security Incident Management Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Create Incident Management Plan, Create Incident, Response Team, Conduct Regular Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
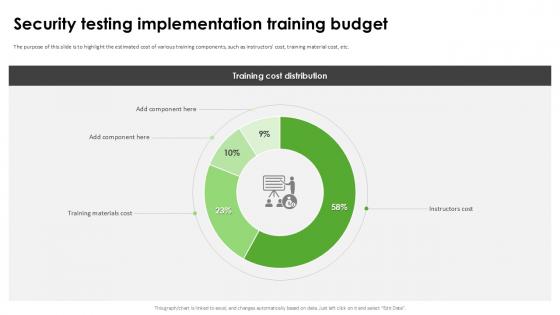
Security Testing Implementation Harnessing The World Of Ethical Ppt Presentation
The purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc. Explore a selection of the finest Security Testing Implementation Harnessing The World Of Ethical Ppt Presentation here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Security Testing Implementation Harnessing The World Of Ethical Ppt Presentation to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc.

IT Security Risk Management Plan Implementation Stages Summary PDF
This slide explains various steps for implementation of cybersecurity risk management plan in the organization to ensure time and budget compliance. It includes elements such as current state analysis, assessment, target state, etc. Presenting IT Security Risk Management Plan Implementation Stages Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State Analysis, Assessment, Target State, Roadmap. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Top Countries Effect By Cyber Security Breach Background Pdf
This templates shows the top countries impacted by malware attacks. The purpose of this slide which country is most effected by malware attack what precaution they should take to reduce the numbers of attacks in futures. it includes various countries such as sweden, japan , china, etc. Pitch your topic with ease and precision using this Top Countries Effect By Cyber Security Breach Background Pdf This layout presents information on Malware Attack, Countries Effect, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the top countries impacted by malware attacks. The purpose of this slide which country is most effected by malware attack what precaution they should take to reduce the numbers of attacks in futures. it includes various countries such as sweden, japan , china, etc.
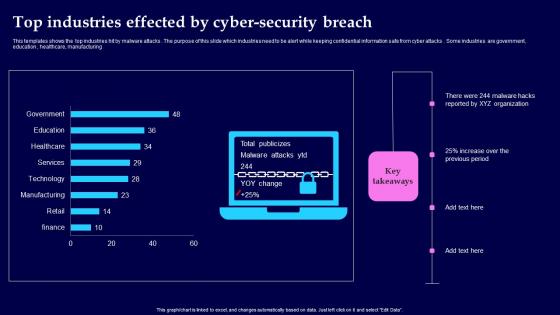
Top Industries Effected By Cyber Security Breach Background Pdf
This templates shows the top industries hit by malware attacks. The purpose of this slide which industries need to be alert while keeping confidential information safe from cyber attacks. Some industries are government, education, healthcare, manufacturing Showcasing this set of slides titled Top Industries Effected By Cyber Security Breach Background Pdf The topics addressed in these templates are Top Industries Effected, Cyber Security Breach All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the top industries hit by malware attacks. The purpose of this slide which industries need to be alert while keeping confidential information safe from cyber attacks. Some industries are government, education, healthcare, manufacturing

Checklist For Online Security Threat And Risk Assessment Designs PDF
This slide represents digital safety threat and assessment checklist which ensure risk management in cost effective manner. It provides information regarding conducting assessment, perform threat analysis, risk mitigation and process completion. Showcasing this set of slides titled Checklist For Online Security Threat And Risk Assessment Designs PDF. The topics addressed in these templates are Perform Threat Analysis, Conduct Assessment, Risk Mitigation And Recommendations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

5G Network Security Ppt Powerpoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this 5G Network Security Ppt Powerpoint Presentation Complete Deck With Slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set. Our 5G Network Security Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
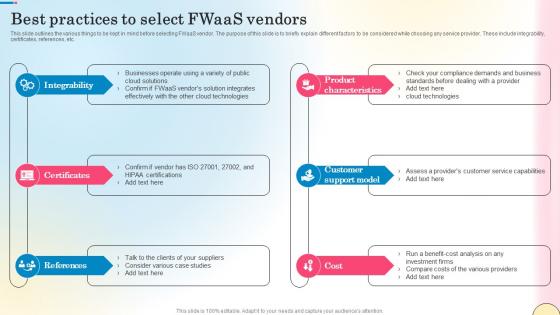
Best Practices To Select Fwaas Vendors Network Security Ideas Pdf
This slide outlines the various things to be kept in mind before selecting FWaaS vendor. The purpose of this slide is to briefly explain different factors to be considered while choosing any service provider. These include integrability, certificates, references, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Select Fwaas Vendors Network Security Ideas Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Select Fwaas Vendors Network Security Ideas Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the various things to be kept in mind before selecting FWaaS vendor. The purpose of this slide is to briefly explain different factors to be considered while choosing any service provider. These include integrability, certificates, references, etc.

Checklist To Implement Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Checklist To Implement Cloud Data Security Using Cryptography Brochure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.
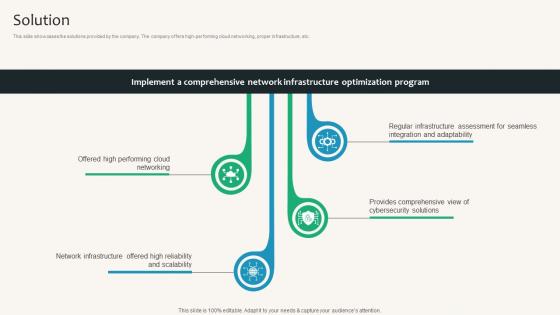
Solution Security Service Provider Business Model BMC SS V
This slide showcases the solutions provided by the company. The company offers high-performing cloud networking, proper infrastructure, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Security Service Provider Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases the solutions provided by the company. The company offers high-performing cloud networking, proper infrastructure, etc.

Stages Involved In Data IT Security Management Program Diagrams PDF
This slide shows the stages involved in data security management program which also includes initiatives and activities such as develop data security team, analyze requirements, monitor policies periodically.Pitch your topic with ease and precision using this Stages Involved In Data IT Security Management Program Diagrams PDF This layout presents information on Identify Stakeholders, Security Requirements, Execute Maintain It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
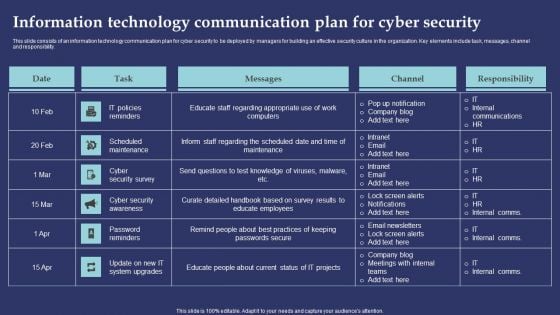
Information Technology Communication Plan For Cyber Security Information PDF
This slide consists of an information technology communication plan for cyber security to be deployed by managers for building an effective security culture in the organization. Key elements include task, messages, channel and responsibility. Showcasing this set of slides titled Information Technology Communication Plan For Cyber Security Information PDF. The topics addressed in these templates are IT Policies Reminders, Scheduled Maintenance, Cyber Security Survey. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
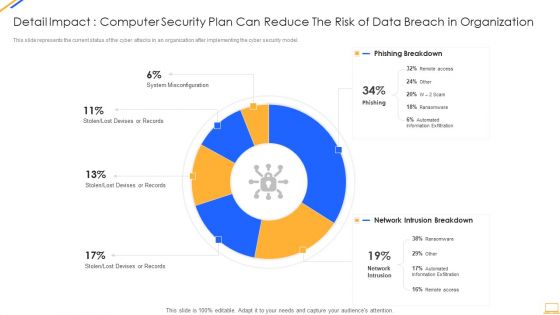
Desktop Security Management Detail Impact Computer Designs PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this desktop security management detail impact computer designs pdf. Use them to share invaluable insights on detail impact computer security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Steps To Deploy People Centric Work Culture Security Background PDF
The following slide showcases steps to enforce human centric security system to empower employees in handling useful information. It includes elements such as establishing environment for people centric security PCS, promoting culture of cyber security, etc. Presenting Steps To Deploy People Centric Work Culture Security Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Converting Cybersecurity, Punishment System, Protection Practices. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Security Considerations For 5G For Threat Handling Elements PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Key Security Considerations For 5G For Threat Handling Elements PDF bundle. Topics like System Configuration, Security Policies, Information Interception can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































