Gap Analysis Of Security
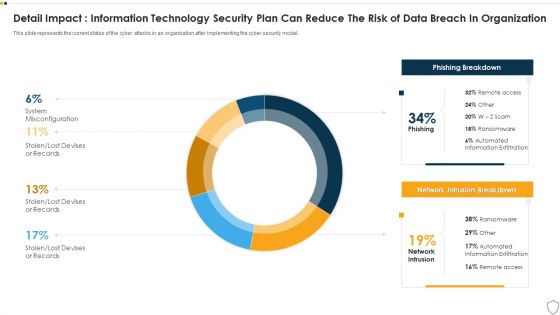
IT Security Detail Impact Information Technology Security Plan Can Reduce The Risk Of Data Breach In Organization Ppt Layouts Show PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this it security detail impact information technology security plan can reduce the risk of data breach in organization ppt layouts show pdf. Use them to share invaluable insights on detail impact information technology security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Effective Ways Of Raising It Security Awareness Communication Plan Demonstration Pdf
This slide showcases different ways to consider while planning communication to increase information security awareness which helps to create messages that match with audiences mitigates all problems. It includes information related to impact of security incidents, IT security mechanism, etc.Pitch your topic with ease and precision using this Effective Ways Of Raising It Security Awareness Communication Plan Demonstration Pdf This layout presents information on Secure Management, Prioritize Personal, Security Awareness It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases different ways to consider while planning communication to increase information security awareness which helps to create messages that match with audiences mitigates all problems. It includes information related to impact of security incidents, IT security mechanism, etc.

Comprehensive Guide For Website Different Security Threats To Be Managed By Web
Mentioned slide provides insights into various security threats to be managed by web designers. It includes key components such as SQL injection, ransomware, spyware, phishing, cross site scription, and virus and bugs. Are you searching for a Comprehensive Guide For Website Different Security Threats To Be Managed By Web that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Comprehensive Guide For Website Different Security Threats To Be Managed By Web from Slidegeeks today. Mentioned slide provides insights into various security threats to be managed by web designers. It includes key components such as SQL injection, ransomware, spyware, phishing, cross site scription, and virus and bugs.
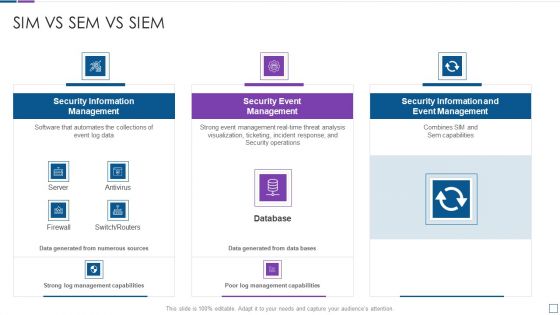
Real Time Assessment Of Security Threats Sim Vs Sem Vs SIEM Diagrams PDF
Deliver an awe inspiring pitch with this creative real time assessment of security threats sim vs sem vs siem diagrams pdf bundle. Topics like security information management, security event management, security information and event management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
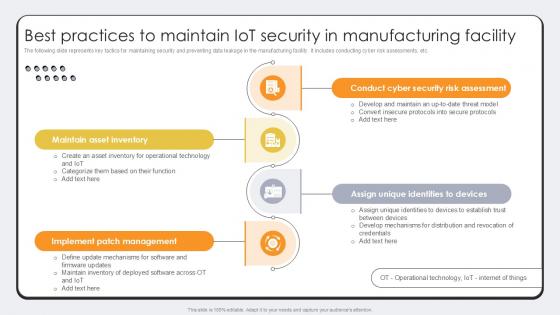
Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. There are so many reasons you need a Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc.
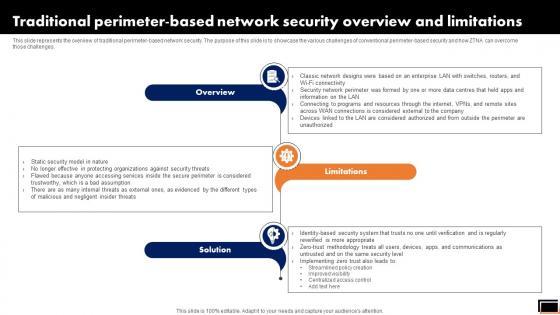
Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. If you are looking for a format to display your unique thoughts, then the professionally designed Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.
Icons Slide For Global Data Security Industry Report IR SS V
Introducing our well designed Icons Slide For Global Data Security Industry Report IR SS V set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Global Data Security Industry Report IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

IoT Security Best Practices In Banking Sector IoT In Banking For Digital Future IoT SS V
Following slide represents best practices to be followed while using IoT in banking services to ensure enhanced security and maintain client confidence. It includes pointers such as access control, network secure infrastructure, regular updates, zero trust approach, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable IoT Security Best Practices In Banking Sector IoT In Banking For Digital Future IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. Following slide represents best practices to be followed while using IoT in banking services to ensure enhanced security and maintain client confidence. It includes pointers such as access control, network secure infrastructure, regular updates, zero trust approach, etc.

Future Of Digital Wallet Security And Safety In Depth Guide To Digital Wallets Fin SS V
This slide exhibits the future of digital wallet security using various technologies and regulations that help to promote the seamless working of online transactions. The major components are biometric authorization, government regulations, artificial intelligence, etc. Welcome to our selection of the Future Of Digital Wallet Security And Safety In Depth Guide To Digital Wallets Fin SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide exhibits the future of digital wallet security using various technologies and regulations that help to promote the seamless working of online transactions. The major components are biometric authorization, government regulations, artificial intelligence, etc.
Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V
If you are looking for a format to display your unique thoughts, then the professionally designed Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Our Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
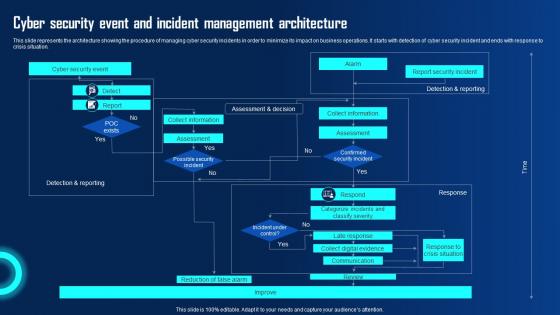
Cyber Security Event And Incident Management Ppt Powerpoint Presentation Diagram Graph Charts Pdf
This slide represents the architecture showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cyber Security Event And Incident Management Ppt Powerpoint Presentation Diagram Graph Charts Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the architecture showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation.

Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks.
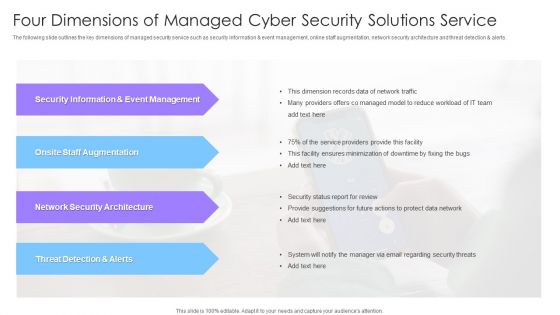
Four Dimensions Of Managed Cyber Security Solutions Service Ppt Pictures Model PDF
The following slide outlines the key dimensions of managed security service such as security information and event management, online staff augmentation, network security architecture and threat detection and alerts. Pitch your topic with ease and precision using this Four Dimensions Of Managed Cyber Security Solutions Service Ppt Pictures Model PDF. This layout presents information on Security Information, Event Management, Staff Augmentation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V
This slide exhibits key activities and tools for monitoring and diagnostics of IoT device security. It includes activities such as continuous monitoring, anomaly detection, vulnerability scanning, auditing and reporting, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide exhibits key activities and tools for monitoring and diagnostics of IoT device security. It includes activities such as continuous monitoring, anomaly detection, vulnerability scanning, auditing and reporting, etc.
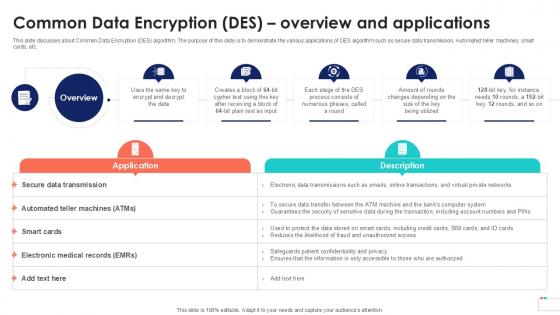
Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample
This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc.
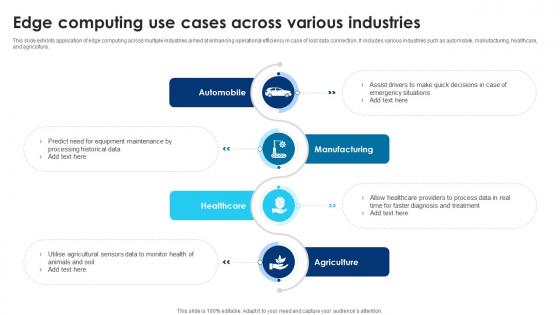
Building Trust With IoT Security Edge Computing Use Cases AcroSS Various Industries IoT SS V
This slide exhibits application of edge computing across multiple industries aimed at enhancing operational efficiency in case of lost data connection. It includes various industries such as automobile, manufacturing, healthcare, and agriculture. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Building Trust With IoT Security Edge Computing Use Cases AcroSS Various Industries IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Building Trust With IoT Security Edge Computing Use Cases AcroSS Various Industries IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide exhibits application of edge computing across multiple industries aimed at enhancing operational efficiency in case of lost data connection. It includes various industries such as automobile, manufacturing, healthcare, and agriculture.
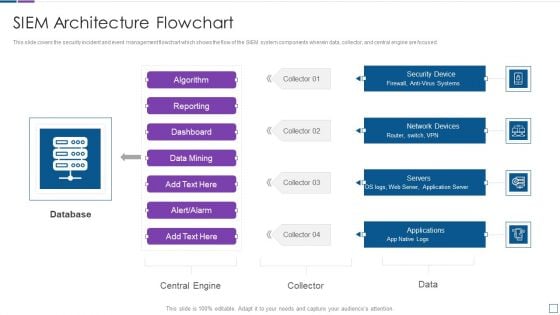
Real Time Assessment Of Security Threats SIEM Architecture Flowchart Sample PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Deliver an awe inspiring pitch with this creative real time assessment of security threats siem architecture flowchart sample pdf bundle. Topics like database, network devices, security device, servers, applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
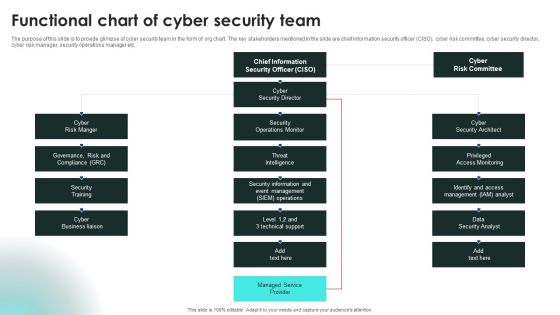
Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
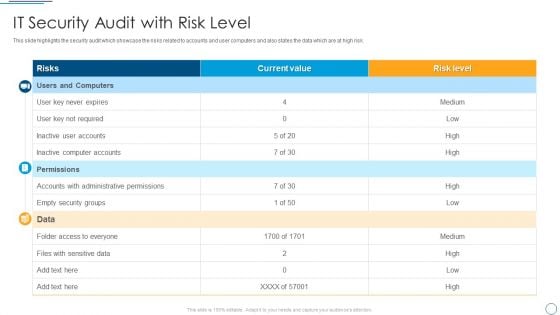
Digital Assessment To Analyze Social Media Brand Presence IT Security Audit With Risk Level Designs PDF
This slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk.Deliver an awe inspiring pitch with this creative Digital Assessment To Analyze Social Media Brand Presence IT Security Audit With Risk Level Designs PDF bundle. Topics like Administrative Permissions, Empty Security, Computer Accounts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
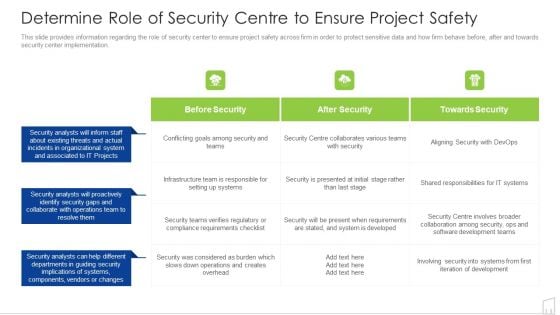
Determine Role Of Security Centre To Ensure Project Safety Ppt Professional Example PDF
This slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an awe inspiring pitch with this creative determine role of security centre to ensure project safety ppt professional example pdf bundle. Topics like security, system, developed, requirements, teams can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
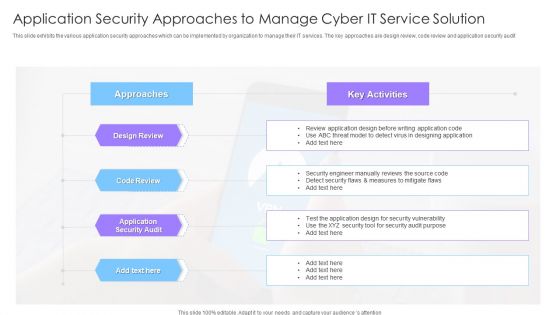
Application Security Approaches To Manage Cyber It Service Solution Ppt Styles Slide Portrait PDF
This slide exhibits the various application security approaches which can be implemented by organization to manage their IT services. The key approaches are design review, code review and application security audit Showcasing this set of slides titled Application Security Approaches To Manage Cyber It Service Solution Ppt Styles Slide Portrait PDF. The topics addressed in these templates are Design Review, Code Review, Approaches, Application Security Audit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Corporate Data Management For Network Security Vector Icon Ppt PowerPoint Presentation Icon Portfolio PDF
Pitch your topic with ease and precision using this corporate data management for network security vector icon ppt powerpoint presentation icon portfolio pdf. This layout presents information on corporate data management for network security vector icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Building Trust With IoT Security Essential Data Privacy Regulations For Ensuring Connected Devices IoT SS V
This slide exhibits personal data handling regulations for organisations across various regions. It includes data regulations such as general data protection regulation, the California consumer privacy act, and personal data protection act in Singapore. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Building Trust With IoT Security Essential Data Privacy Regulations For Ensuring Connected Devices IoT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Building Trust With IoT Security Essential Data Privacy Regulations For Ensuring Connected Devices IoT SS V. This slide exhibits personal data handling regulations for organisations across various regions. It includes data regulations such as general data protection regulation, the California consumer privacy act, and personal data protection act in Singapore.
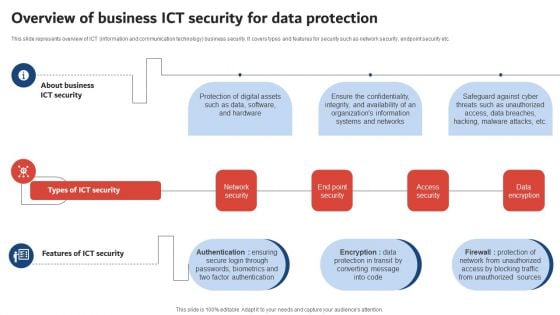
Execution Of ICT Strategic Plan Overview Of Business ICT Security For Data Protection Sample PDF
This slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Welcome to our selection of the Execution Of ICT Strategic Plan Overview Of Business ICT Security For Data Protection Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
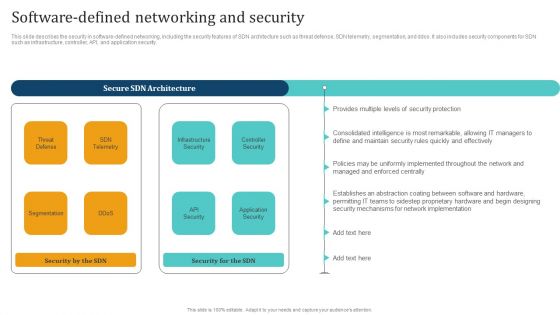
Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF
This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Welcome to our selection of the Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
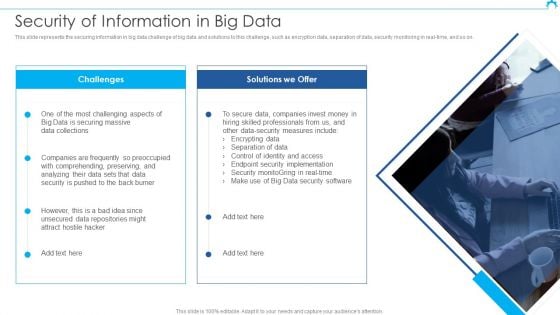
Big Data Architect Security Of Information In Big Data Graphics PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Big Data Architect Security Of Information In Big Data Graphics PDF bundle. Topics like Most Challenging, Securing Massive, Data Collections can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
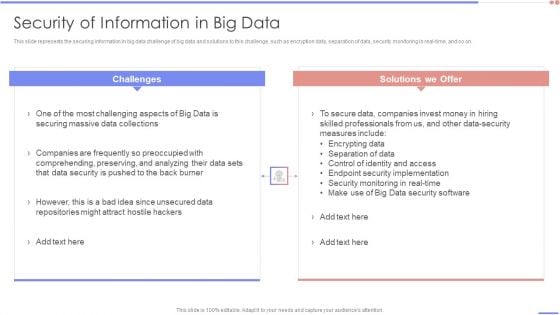
Data Analytics Management Security Of Information In Big Data Summary PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Data Analytics Management Security Of Information In Big Data Summary PDF bundle. Topics like Securing Massive, Companies Frequently, Comprehending Preserving can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
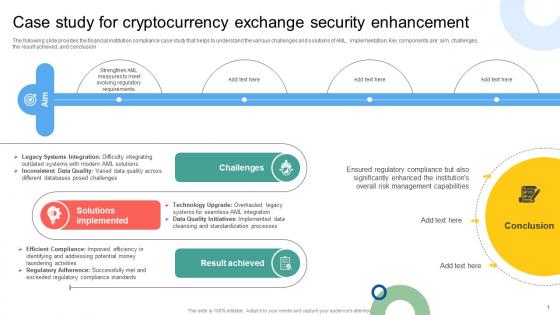
Case Study For Cryptocurrency Exchange Security Mapping Out The Anti Money Fin SS V
The following slide provides the financial institution compliance case study that helps to understand the various challenges and solutions of AML implementation. Key components are aim, challenges, the result achieved, and conclusion. Find highly impressive Case Study For Cryptocurrency Exchange Security Mapping Out The Anti Money Fin SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Case Study For Cryptocurrency Exchange Security Mapping Out The Anti Money Fin SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The following slide provides the financial institution compliance case study that helps to understand the various challenges and solutions of AML implementation. Key components are aim, challenges, the result achieved, and conclusion.
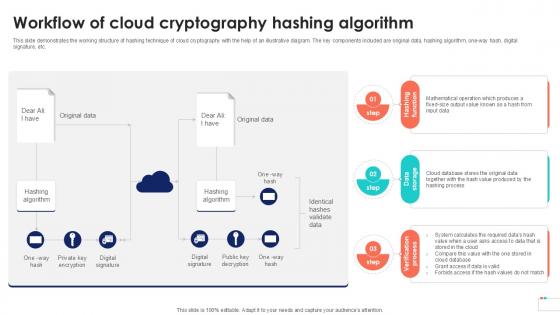
Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example
This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one-way hash, digital signature, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one-way hash, digital signature, etc.

Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V
This slide provides a glimpse of key highlights of the cybersecurity industry, enabling executives to grasp the main findings quickly. It serves as a snapshot highlighting revenue, CAGR, fastest growing region, segments, regional breakdown, and key market players. If you are looking for a format to display your unique thoughts, then the professionally designed Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide provides a glimpse of key highlights of the cybersecurity industry, enabling executives to grasp the main findings quickly. It serves as a snapshot highlighting revenue, CAGR, fastest growing region, segments, regional breakdown, and key market players.
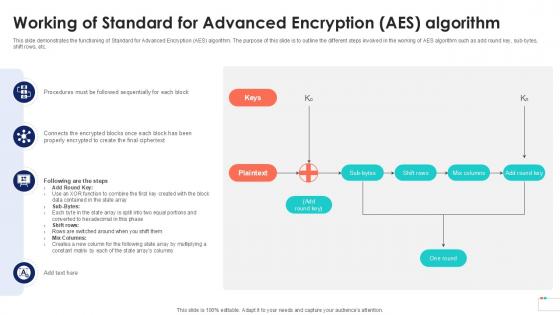
Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc.
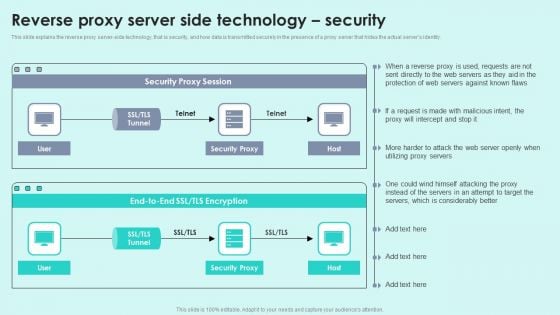
Reverse Proxy Server Side Technology Security Reverse Proxy For Load Balancing Portrait PDF
This slide explains the reverse proxy server-side technology, that is security, and how data is transmitted securely in the presence of a proxy server that hides the actual servers identity.Deliver and pitch your topic in the best possible manner with this Reverse Proxy Server Side Technology Security Reverse Proxy For Load Balancing Portrait PDF. Use them to share invaluable insights on Security Proxy, Protection Servers, Considerably Better and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
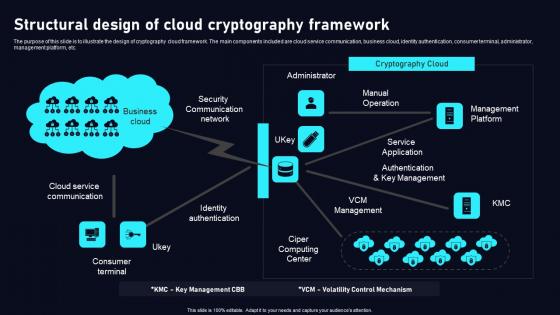
Structural Design Of Cloud Cryptography Cloud Data Security Using Cryptography Themes Pdf
The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Structural Design Of Cloud Cryptography Cloud Data Security Using Cryptography Themes Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc.
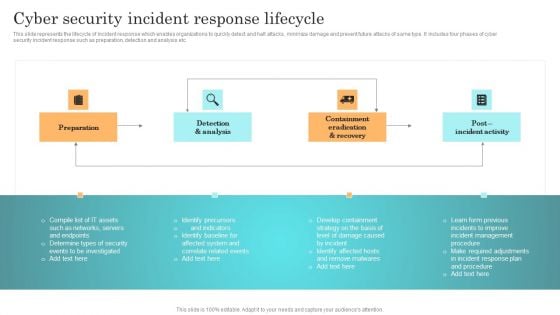
Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Welcome to our selection of the Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
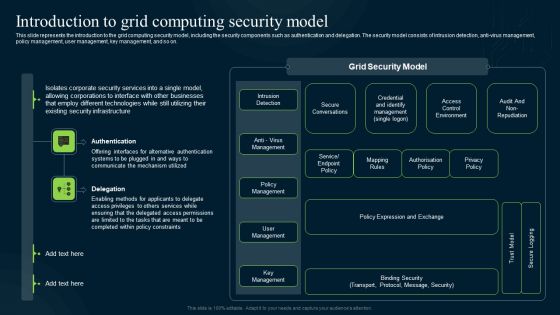
Grid Computing Infrastructure Introduction To Grid Computing Security Model Background PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. This modern and well-arranged Grid Computing Infrastructure Introduction To Grid Computing Security Model Background PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
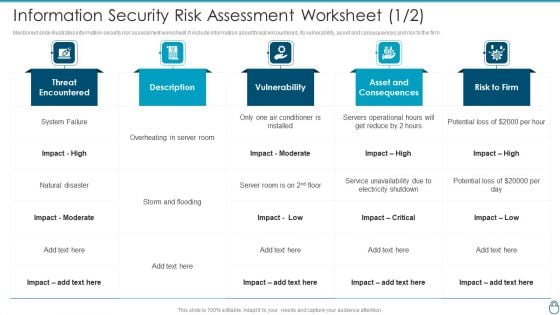
Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF bundle. Topics like Conditioner Is Installed, Asset And Consequences, Electricity Shutdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
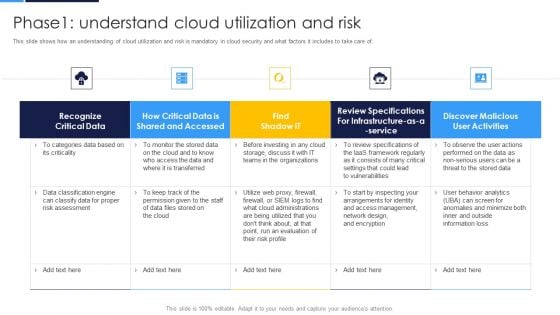
Cloud Security Assessment Phase1 Understand Cloud Utilization And Risk Professional PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Phase1 Understand Cloud Utilization And Risk Professional PDF bundle. Topics like Shared And Accessed, Risk Assessment, Review Specifications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ISO 27001 Certification Procedure Current Security Management Capabilities Overview Diagrams PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver and pitch your topic in the best possible manner with this ISO 27001 Certification Procedure Current Security Management Capabilities Overview Diagrams PDF. Use them to share invaluable insights on Assessing Information, Occurrence Identification, Communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IoT Device Management Fundamentals IoT Device Authentication Methods To Ensure Data Security IoT Ss V
This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys. Slidegeeks has constructed IoT Device Management Fundamentals IoT Device Authentication Methods To Ensure Data Security IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys.

Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V
The slide highlights the future outlook and potential for the cybersecurity industry. The purpose of the slide is to inform stakeholders regarding growth opportunities, creating a compelling case for investment and collaboration. It covers drivers, trends, and the revolutionary impact of the industry. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The slide highlights the future outlook and potential for the cybersecurity industry. The purpose of the slide is to inform stakeholders regarding growth opportunities, creating a compelling case for investment and collaboration. It covers drivers, trends, and the revolutionary impact of the industry.

Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc.
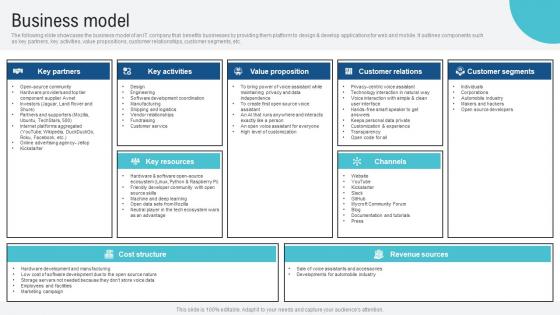
Business Model Voice Assistance Security Platform Investor Funding Presentation Guidelines Pdf
The following slide showcases the business model of an IT company that benefits businesses by providing them platform to design and develop applications for web and mobile. It outlines components such as key partners, key activities, value propositions, customer relationships, customer segments, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Business Model Voice Assistance Security Platform Investor Funding Presentation Guidelines Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide showcases the business model of an IT company that benefits businesses by providing them platform to design and develop applications for web and mobile. It outlines components such as key partners, key activities, value propositions, customer relationships, customer segments, etc.
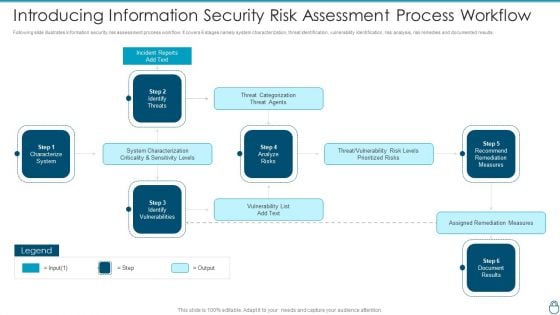
Cybersecurity Risk Administration Plan Introducing Information Security Risk Assessment Process Workflow Slides PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Introducing Information Security Risk Assessment Process Workflow Slides PDF Use them to share invaluable insights on System Characterization, Threat Categorization, Recommend Remediation Measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
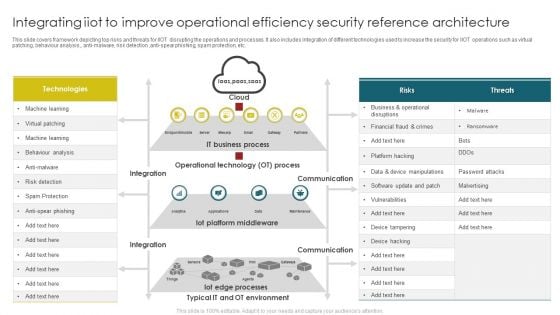
Integrating Iiot To Improve Operational Efficiency Security Reference Architecture Themes PDF
This slide covers framework depicting top risks and threats for IIOT disrupting the operations and processes. It also includes integration of different technologies used to increase the security for IIOT operations such as virtual patching, behaviour analysis, anti malware, risk detection, anti spear phishing, spam protection, etc. Pitch your topic with ease and precision using this Integrating Iiot To Improve Operational Efficiency Security Reference Architecture Themes PDF. This layout presents information on Operational Technology, IT Business Process, Iot Platform Middleware . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
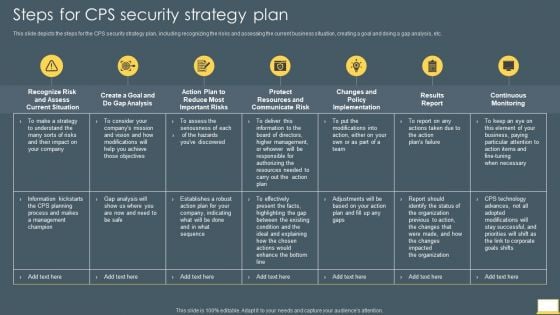
Cyber Intelligent Computing System Steps For CPS Security Strategy Plan Mockup PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Deliver and pitch your topic in the best possible manner with this Cyber Intelligent Computing System Steps For CPS Security Strategy Plan Mockup PDF. Use them to share invaluable insights on Gap Analysis, Protect Resources, Communicate Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
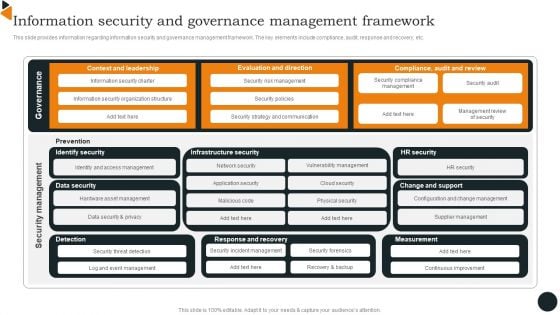
Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
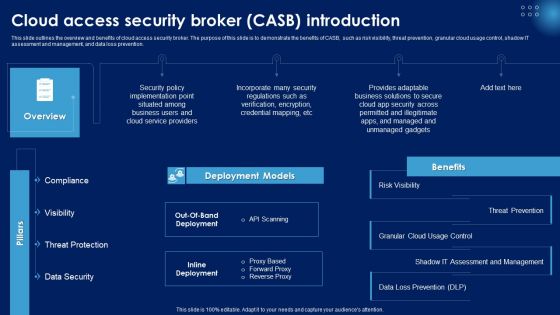
Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF.
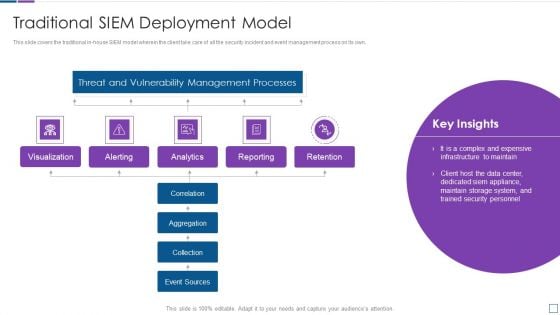
Real Time Assessment Of Security Threats Traditional SIEM Deployment Model Background PDF
This slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats traditional siem deployment model background pdf. Use them to share invaluable insights on threat and vulnerability management processes, visualization, retention, analytics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Real Time Assessment Of Security Threats Cloud SIEM Model Icons PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats cloud siem model icons pdf. Use them to share invaluable insights on threat and vulnerability management processes, aggregation, collection, correlation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Icons Slide For Security Guard Services Proposal Ppt Summary Design Inspiration PDF
Introducing our well-designed icons slide for security guard services proposal ppt summary design inspiration pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Workforce Security Realization Coaching Plan Icons Slide Ppt Ideas Topics PDF
Introducing our well-designed workforce security realization coaching plan icons slide ppt ideas topics pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Comprehensive Guide For Ensuring IT Infrastructure Security Inspiration PDF
Introducing our well designed Icons Slide For Comprehensive Guide For Ensuring IT Infrastructure Security Inspiration PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Investment Banking Security Underwriting Pitchbook IPO Timeline Pre IPO To Post IPO Pictures PDF
The slide provides the timeline of IPO issue and covers the five steps i.e. Pre-IPO planning, Preparation for Filing, SEC Review, Road Show, and Post IPODeliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook IPO Timeline Pre IPO To Post IPO Pictures PDF bundle. Topics like Organizational Meeting, Preparation Filling, Internal Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
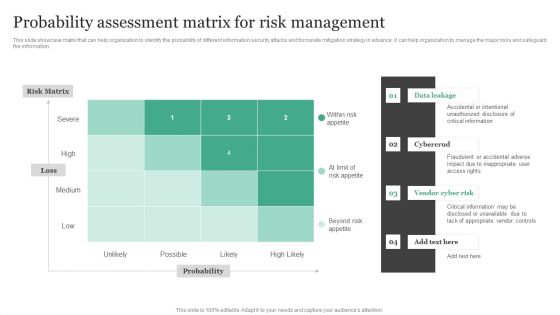
Probability Assessment Matrix For Risk Management Information Security Risk Administration Pictures PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information.This Probability Assessment Matrix For Risk Management Information Security Risk Administration Pictures PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
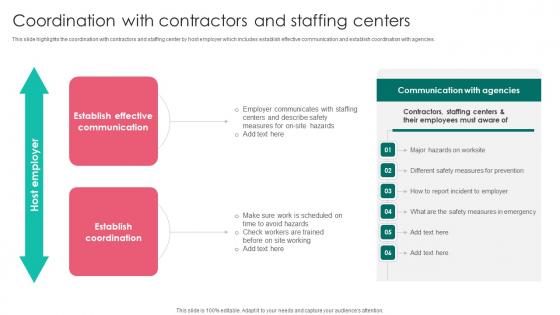
Coordination With Contractors Workplace Safety Protocol And Security Practices Ideas Pdf
This slide highlights the coordination with contractors and staffing center by host employer which includes establish effective communication and establish coordination with agencies. If you are looking for a format to display your unique thoughts, then the professionally designed Coordination With Contractors Workplace Safety Protocol And Security Practices Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Coordination With Contractors Workplace Safety Protocol And Security Practices Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide highlights the coordination with contractors and staffing center by host employer which includes establish effective communication and establish coordination with agencies.

Incident Response Techniques Deployement Cyber Security Crisis Management Action Plan Timeline Rules PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Incident Response Techniques Deployement Cyber Security Crisis Management Action Plan Timeline Rules PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
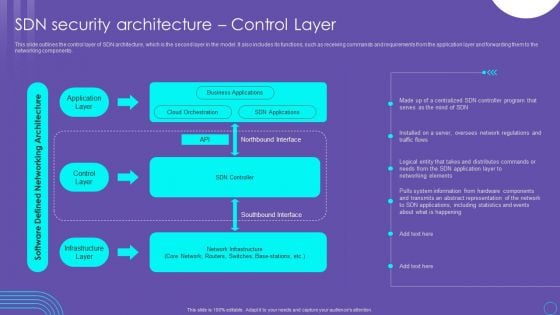
SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF
This slide outlines the control layer of SDN architecture, which is the second layer in the model. It also includes its functions, such as receiving commands and requirements from the application layer and forwarding them to the networking components. If you are looking for a format to display your unique thoughts, then the professionally designed SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Real Time Assessment Of Security Threats Estimating Total Cost Of Ownership Of SIEM Icons PDF
This slide covers the total cost of ownership incurred by SIEM services which focuses on the costs of hardware, software, infrastructure, and support.Deliver an awe inspiring pitch with this creative real time assessment of security threats estimating total cost of ownership of siem icons pdf bundle. Topics like hardware, infrastructure, software, support can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
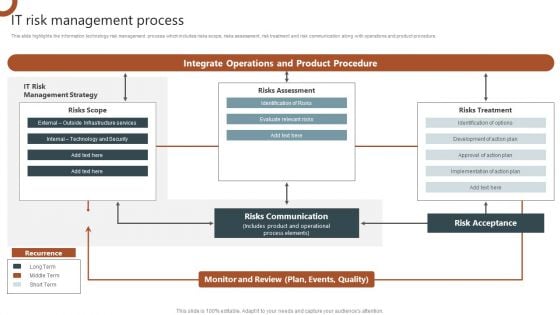
IT Risk Management Process Organizations Risk Management And IT Security Slides PDF
This slide highlights the information technology risk management process which includes risks scope, risks assessment, risk treatment and risk communication along with operations and product procedure. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT Risk Management Process Organizations Risk Management And IT Security Slides PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT Risk Management Process Organizations Risk Management And IT Security Slides PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
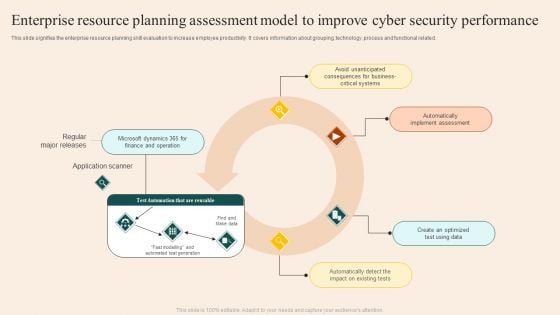
Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF
This slide signifies the enterprise resource planning skill evaluation to increase employee productivity. It covers information about grouping, technology ,process and functional related. Showcasing this set of slides titled Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF. The topics addressed in these templates are Regular Major Releases, Application Scanner, Implement Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































