Hacker
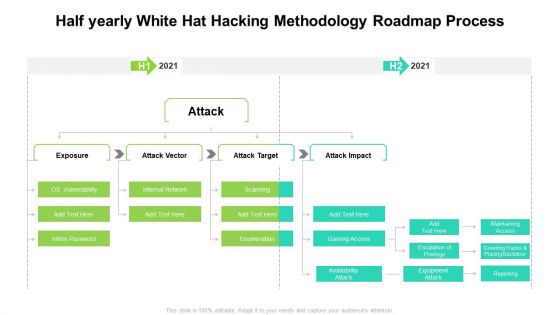
Half Yearly White Hat Hacking Methodology Roadmap Process Professional
Presenting our innovatively structured half yearly white hat hacking methodology roadmap process professional Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
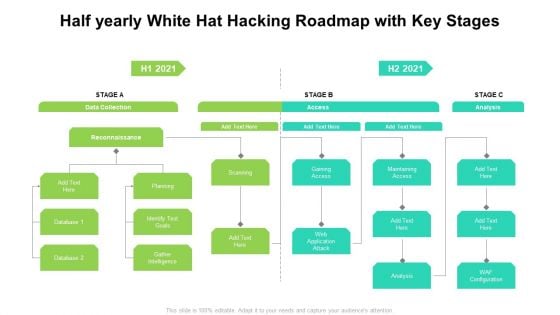
Half Yearly White Hat Hacking Roadmap With Key Stages Brochure
Introducing our half yearly white hat hacking roadmap with key stages brochure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
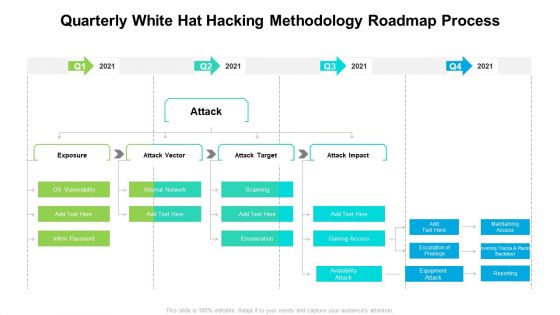
Quarterly White Hat Hacking Methodology Roadmap Process Information
Presenting our innovatively structured quarterly white hat hacking methodology roadmap process information Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
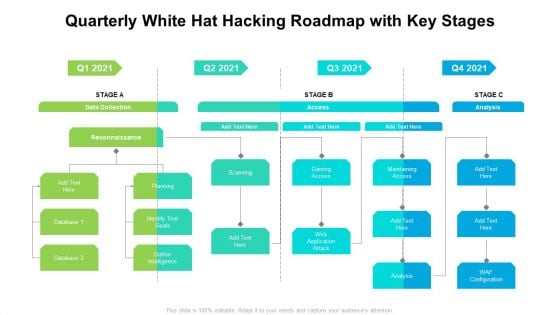
Quarterly White Hat Hacking Roadmap With Key Stages Designs
Introducing our quarterly white hat hacking roadmap with key stages designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
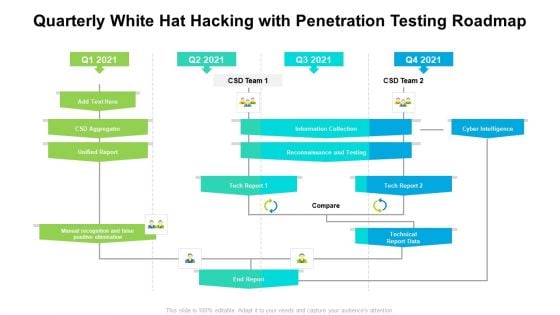
Quarterly White Hat Hacking With Penetration Testing Roadmap Rules
Presenting our jaw dropping quarterly white hat hacking with penetration testing roadmap rules. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Six Months White Hat Hacking Methodology Roadmap Process Infographics
Presenting our innovatively structured six months white hat hacking methodology roadmap process infographics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
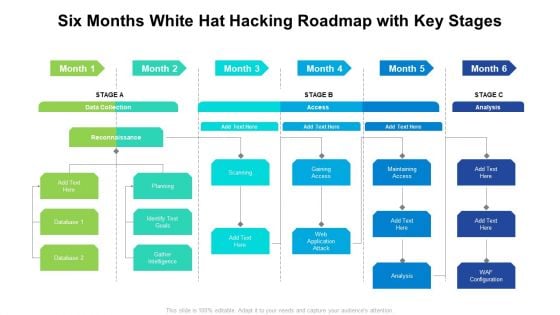
Six Months White Hat Hacking Roadmap With Key Stages Infographics
Introducing our six months white hat hacking roadmap with key stages infographics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
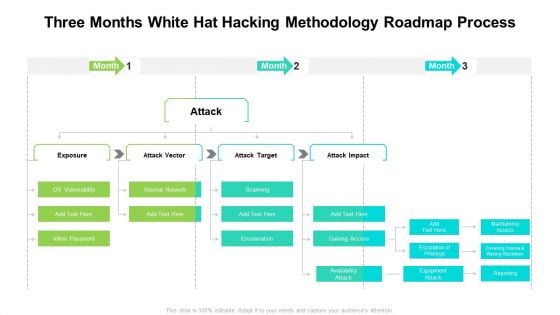
Three Months White Hat Hacking Methodology Roadmap Process Professional
Presenting our innovatively structured three months white hat hacking methodology roadmap process professional Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
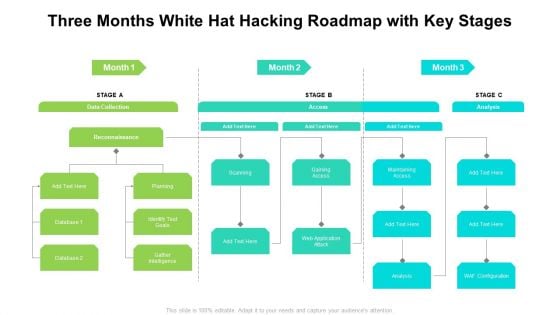
Three Months White Hat Hacking Roadmap With Key Stages Guidelines
Introducing our three months white hat hacking roadmap with key stages guidelines. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
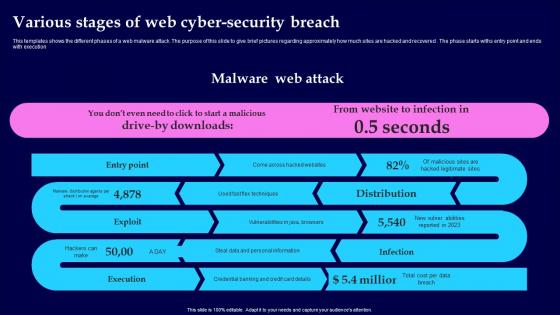
Various Stages Of Web Cyber Security Breach Introduction Pdf
This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution Pitch your topic with ease and precision using this Various Stages Of Web Cyber Security Breach Introduction Pdf This layout presents information on Malware Web Attack, Various Stages, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution

Different Types Of Vishing Cyber Attacks Man In The Middle Phishing IT
This slide talks about the various types of vishing cyber attacks. The purpose of this slide is to briefly explain different techniques of vishing scams used by the attackers to scam users. These are caller ID spoofing, dumpster diving, wardialing, etc. This modern and well-arranged Different Types Of Vishing Cyber Attacks Man In The Middle Phishing IT provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide talks about the various types of vishing cyber attacks. The purpose of this slide is to briefly explain different techniques of vishing scams used by the attackers to scam users. These are caller ID spoofing, dumpster diving, wardialing, etc.
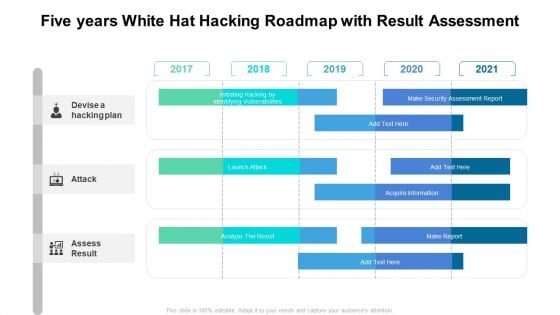
Five Years White Hat Hacking Roadmap With Result Assessment Guidelines
Presenting the five years white hat hacking roadmap with result assessment guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
Five Years White Hat Hacking With Penetration Testing Roadmap Icons
Presenting our jaw dropping five years white hat hacking with penetration testing roadmap icons. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
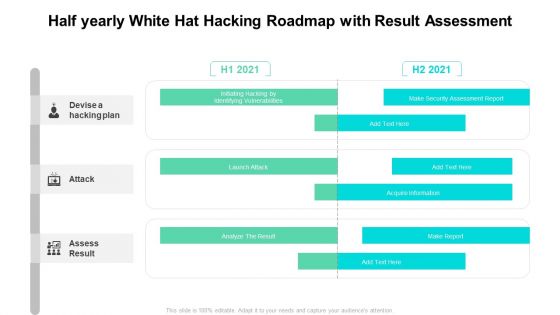
Half Yearly White Hat Hacking Roadmap With Result Assessment Graphics
Presenting the half yearly white hat hacking roadmap with result assessment graphics. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
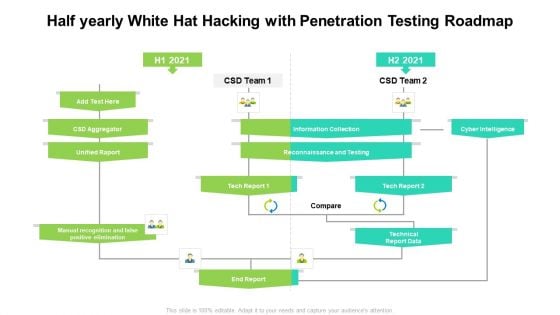
Half Yearly White Hat Hacking With Penetration Testing Roadmap Designs
Presenting our jaw dropping half yearly white hat hacking with penetration testing roadmap designs. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
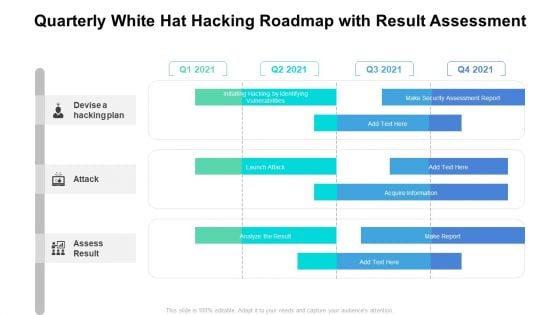
Quarterly White Hat Hacking Roadmap With Result Assessment Microsoft
Presenting the quarterly white hat hacking roadmap with result assessment microsoft. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
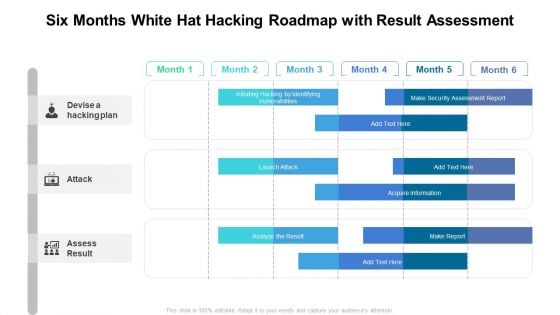
Six Months White Hat Hacking Roadmap With Result Assessment Rules
Presenting the six months white hat hacking roadmap with result assessment rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
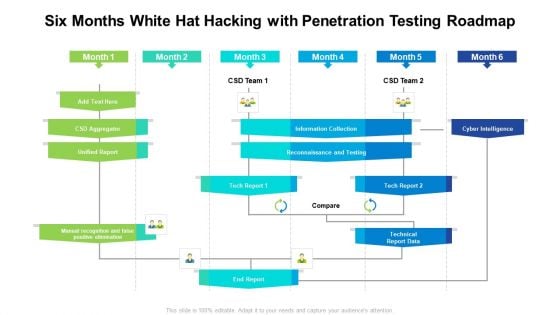
Six Months White Hat Hacking With Penetration Testing Roadmap Infographics
Presenting our jaw dropping six months white hat hacking with penetration testing roadmap infographics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
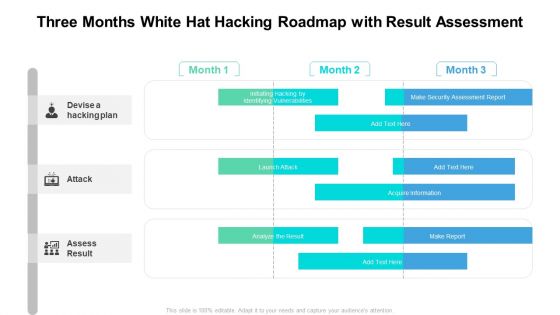
Three Months White Hat Hacking Roadmap With Result Assessment Mockup
Presenting the three months white hat hacking roadmap with result assessment mockup. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
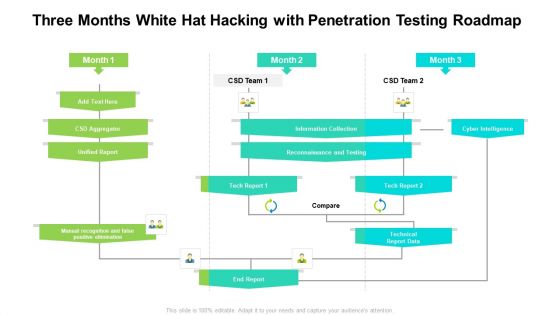
Three Months White Hat Hacking With Penetration Testing Roadmap Professional
Presenting our jaw dropping three months white hat hacking with penetration testing roadmap professional. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Major Consequences Of Data Breach Cyber Attack Data Fortification Strengthening Defenses
This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss. Slidegeeks has constructed Major Consequences Of Data Breach Cyber Attack Data Fortification Strengthening Defenses after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss.
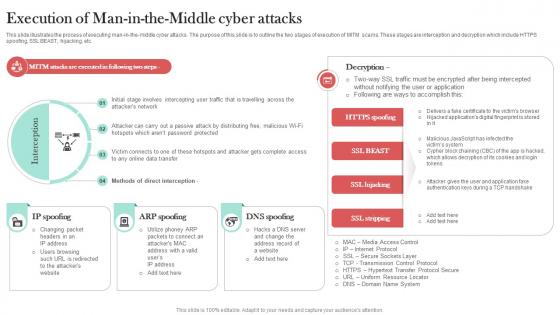
Execution Of Man In The Middle Cyber Attacks Man In The Middle Phishing IT
This slide illustrates the process of executing man-in-the-middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption which include HTTPS spoofing, SSL BEAST, hijacking, etc. Welcome to our selection of the Execution Of Man In The Middle Cyber Attacks Man In The Middle Phishing IT. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide illustrates the process of executing man-in-the-middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption which include HTTPS spoofing, SSL BEAST, hijacking, etc.
Business Diagram Three Circles With Lock For Safety Presentation Template
Three air balloons with text boxes are used to craft this power point template slide. This PPT slide contains the concept of business text representation. This slide is usable for business and marketing related presentations.

Brainstorming Session Six Thinking Hats Presentation Images
This is a brainstorming session six thinking hats presentation images. This is a six stage process. The stages in this process are focus, white hat data driven inputs, green hat outside the box thinkers, yellow hat focused on the positives, black hat opposing viewpoints, red hat feelings and intuitions, blue hat idea collector leader.

White Hat Hacking Ppt PowerPoint Presentation Complete With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the eighty seven slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Highest Number Of Malware Attacks On Departments Hacking Prevention Awareness Training For IT Security Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this highest number of malware attacks on departments hacking prevention awareness training for it security themes pdf. Use them to share invaluable insights on r and d department, it department, accounts department, sales department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
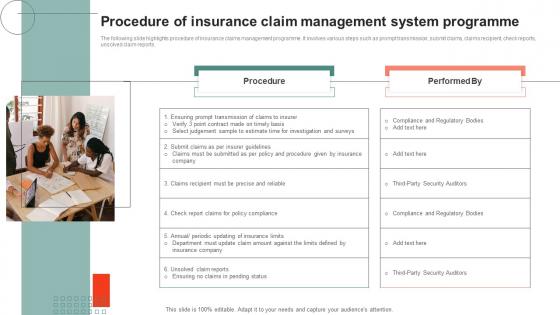
Procedure Of Insurance Claim Management System Programme Demonstration Pdf
The following slide highlights procedure of insurance claims management programme. It involves various steps such as prompt transmission, submit claims, claims recipient, check reports, unsolved claim reports. Showcasing this set of slides titled Procedure Of Insurance Claim Management System Programme Demonstration Pdf The topics addressed in these templates are Procedure, Claim Management System, Programme All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide highlights procedure of insurance claims management programme. It involves various steps such as prompt transmission, submit claims, claims recipient, check reports, unsolved claim reports.
Programmable Logic In Powerpoint And Google Slides Cpb
Introducing our well designed Programmable Logic In Powerpoint And Google Slides Cpb This PowerPoint design presents information on topics like Programmable Logic As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Programmable Logic In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Managing Successful Programmes Templates In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Managing Successful Programmes Templates In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Managing Successful Programmes Templates that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Managing Successful Programmes Templates In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
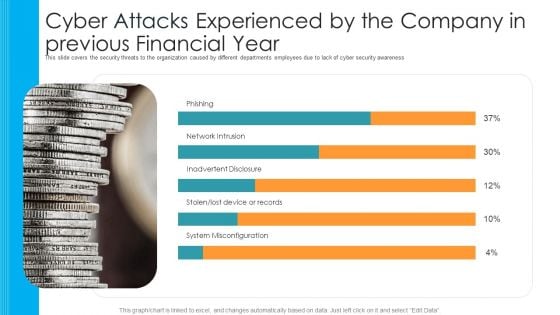
Cyber Attacks Experienced By The Company In Previous Financial Year Hacking Prevention Awareness Training For IT Security Template PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year hacking prevention awareness training for it security template pdf bundle. Topics like phishing, network intrusion, inadvertent disclosure, stolen or lost device or records, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Internet Security And Electronic Payment System Ppt Slides
This is a internet security and electronic payment system ppt slides. This is a six stage process. The stages in this process are internet security and electronic payment system, eviction of eco implementation, eco site life cycle, promotion and marketing, net readiness evaluation, eco investment and opportunity.

Business Diagram Lock Graphics For Secure Internet Access Presentation Template
This power point template has been crafted with graphic of 3d world map and lock. This PPT contains the concept of security. Use this PPT for your business and marketing related presentations.
Business Diagram Secure Connections To The Public Cloud With Folders And Lock Ppt Slide
This technical slide has been designed with graphic of folders and cloud with lock. This PPT slide depicts the concept of secure connections. It focuses on the data safety in cloud technology. Use this diagram for data safety related presentations.
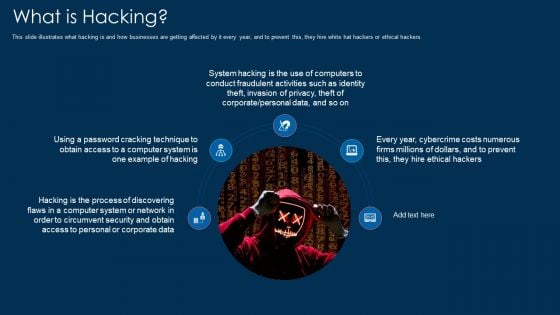
What Is Hacking Ppt Gallery Layouts PDF
Presenting what is hacking ppt gallery layouts pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like system, technique, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
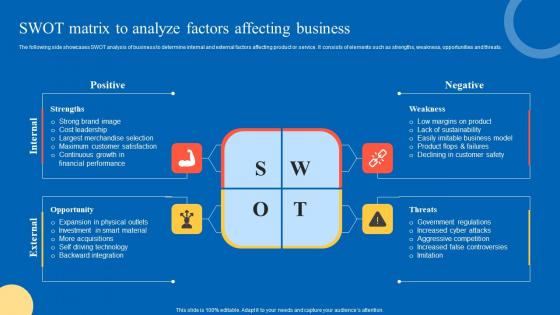
SWOT Matrix To Analyze Strategic Guide For Marketing Program Microsoft Pdf
The following side showcases SWOT analysis of business to determine internal and external factors affecting product or service. It consists of elements such as strengths, weakness, opportunities and threats. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download SWOT Matrix To Analyze Strategic Guide For Marketing Program Microsoft Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following side showcases SWOT analysis of business to determine internal and external factors affecting product or service. It consists of elements such as strengths, weakness, opportunities and threats.
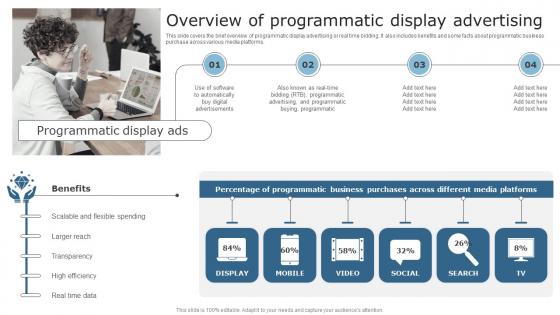
Techniques To Optimize Business Performance Overview Of Programmatic Display Demonstration Pdf
This slide covers the brief overview of programmatic display advertising or real time bidding. It also includes benefits and some facts about programmatic business purchase across various media platforms. Presenting this PowerPoint presentation, titled Techniques To Optimize Business Performance Overview Of Programmatic Display Demonstration Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Techniques To Optimize Business Performance Overview Of Programmatic Display Demonstration Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Techniques To Optimize Business Performance Overview Of Programmatic Display Demonstration Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide covers the brief overview of programmatic display advertising or real time bidding. It also includes benefits and some facts about programmatic business purchase across various media platforms.

IT Infrastructure Security Budget Hacking Prevention Awareness Training For IT Security Graphics PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver an awe inspiring pitch with this creative it infrastructure security budget hacking prevention awareness training for it security graphics pdf bundle. Topics like security, services, costs, cloud security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
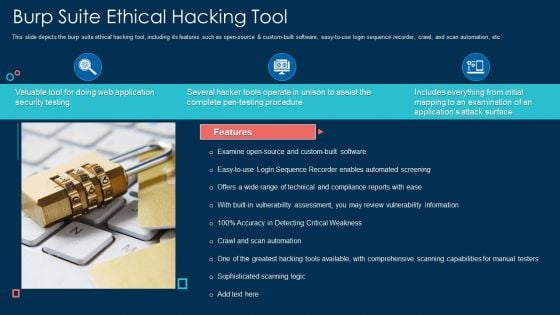
Burp Suite Ethical Hacking Tool Ppt Portfolio Skills PDF
This slide depicts the burp suite ethical hacking tool, including its features such as open source and custom built software, easy to use login sequence recorder, crawl, and scan automation, etc. Presenting burp suite ethical hacking tool ppt portfolio skills pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security, application, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Hacking Prevention Awareness Training For IT Security Icons Slide Hacking Prevention Awareness Training For IT Security Information PDF
Introducing our well designed hacking prevention awareness training for it security icons slide hacking prevention awareness training for it security information pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Roadmap Hacking Prevention Awareness Training For IT Security Brochure PDF
This is a roadmap hacking prevention awareness training for it security brochure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like roadmap. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Timeline Hacking Prevention Awareness Training For IT Security Brochure PDF
Presenting timeline hacking prevention awareness training for it security brochure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like timeline, 2016 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Mental Health Hacks Reddit In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Mental Health Hacks Reddit In Powerpoint And Google Slides Cpb This completely editable PowerPoint graphic exhibits Mental Health Hacks Reddit that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Mental Health Hacks Reddit In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Quizlet Match Hack In Powerpoint And Google Slides Cpb
Introducing our well designed Quizlet Match Hack In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Quizlet Match Hack. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Quizlet Match Hack In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Credit Card Point Hacking In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Credit Card Point Hacking In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Credit Card Point Hacking that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Credit Card Point Hacking In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Hacking Case In Powerpoint And Google Slides Cpb
Introducing our well-designed Hacking Case In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Hacking Case. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Hacking Case In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Tips Get Hacked In Powerpoint And Google Slides Cpb
Introducing our well designed Tips Get Hacked In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Tips Get Hacked. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Tips Get Hacked In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Traffic Light Hacking In Powerpoint And Google Slides Cpb
Introducing our well designed Traffic Light Hacking In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Traffic Light Hacking. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Traffic Light Hacking In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Expressvpn Hacked Accounts In Powerpoint And Google Slides Cpb
Introducing our well designed Expressvpn Hacked Accounts In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Expressvpn Hacked Accounts. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Expressvpn Hacked Accounts In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Agenda For Harnessing The World Of Ethical Hacking Ppt Sample
Want to ace your presentation in front of a live audience Our Agenda For Harnessing The World Of Ethical Hacking Ppt Sample can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. Our Agenda For Harnessing The World Of Ethical Hacking Ppt Sample are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Harnessing The World of Ethical Hacking PPT Presentation

Table Of Contents For Harnessing The World Of Ethical Hacking Ppt Example
Presenting this PowerPoint presentation, titled Table Of Contents For Harnessing The World Of Ethical Hacking Ppt Example with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Table Of Contents For Harnessing The World Of Ethical Hacking Ppt Example Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Table Of Contents For Harnessing The World Of Ethical Hacking Ppt Example that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. Our Table Of Contents For Harnessing The World Of Ethical Hacking Ppt Example are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icons Slide For Harnessing The World Of Ethical Hacking Ppt Slide
Download our innovative and attention grabbing Icons Slide For Harnessing The World Of Ethical Hacking Ppt Slide template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele. Our Icons Slide For Harnessing The World Of Ethical Hacking Ppt Slide are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels
Explore a selection of the finest Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents Cybersecurity Risk Assessment Program Dashboard to effectively track cyber security risk levels. This will provide a structured approach for organizations to review and mitigate cyber threats. It includes multiple threat agents, attack methods, and preventive controls implemented with detailed insights, and it shows critical metrics including risk scores, the number of infected systems, and detected vulnerabilities.
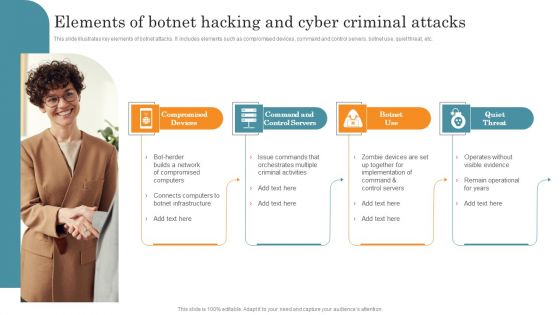
Elements Of Botnet Hacking And Cyber Criminal Attacks Brochure PDF
This slide illustrates key elements of botnet attacks. It includes elements such as compromised devices, command and control servers, botnet use, quiet threat, etc. Persuade your audience using this Elements Of Botnet Hacking And Cyber Criminal Attacks Brochure PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Compromised Devices, Command Control Servers, Botnet Use, Quiet Threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Table Of Contents Harnessing The World Of Ethical Hacking Ppt Slide
Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Table Of Contents Harnessing The World Of Ethical Hacking Ppt Slide to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Table Of Contents Harnessing The World Of Ethical Hacking Ppt Slide Our Table Of Contents Harnessing The World Of Ethical Hacking Ppt Slide are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

A Comprehensive Approach To Growth Hacking For Small Businesses MKT CD V

Agenda For A Comprehensive Approach To Growth Hacking For Small Businesses MKT SS V
This Agenda For A Comprehensive Approach To Growth Hacking For Small Businesses MKT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. Our Agenda For A Comprehensive Approach To Growth Hacking For Small Businesses MKT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icons Slide A Comprehensive Approach To Growth Hacking For Small Businesses MKT SS V
Take your projects to the next level with our ultimate collection of Icons Slide A Comprehensive Approach To Growth Hacking For Small Businesses MKT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest Our Icons Slide A Comprehensive Approach To Growth Hacking For Small Businesses MKT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Contents For White Hat Hacking Program Ppt Gallery Images PDF
Deliver an awe inspiring pitch with this creative table of contents for white hat hacking program ppt gallery images pdf bundle. Topics like fundamental, organizations, requirement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

White Hat Hacking What Is Phishing Attack Ppt Outline Design Inspiration PDF
This is a white hat hacking what is phishing attack ppt outline design inspiration pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, purchasing, required, source. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































