Hacker
Hacked Dating Profiles In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Hacked Dating Profiles In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Hacked Dating Profiles that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Hacked Dating Profiles In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Hacks Website Optimization In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Hacks Website Optimization In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Hacks Website Optimization that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Hacks Website Optimization In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
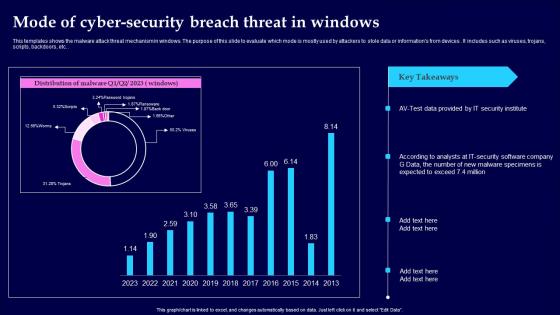
Mode Of Cyber Security Breach Threat In Windows Clipart Pdf
This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc. Showcasing this set of slides titled Mode Of Cyber Security Breach Threat In Windows Clipart Pdf The topics addressed in these templates are Mode Of Cyber Security, Threat In Windows All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc.
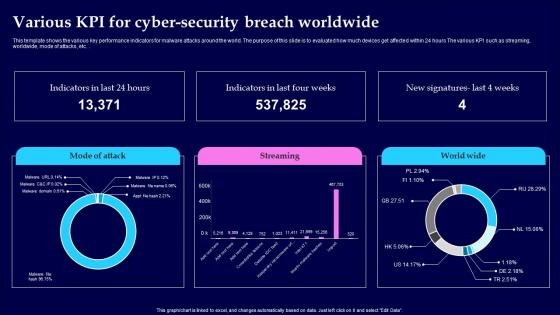
Various KPI For Cyber Security Breach Worldwide Pictures Pdf
This template shows the various key performance indicators for malware attacks around the world. The purpose of this slide is to evaluated how much devices get affected within 24 hours The various KPI such as streaming, worldwide, mode of attacks, etc. Showcasing this set of slides titled Various KPI For Cyber Security Breach Worldwide Pictures Pdf The topics addressed in these templates are Cyber Security Breach, Worldwide All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This template shows the various key performance indicators for malware attacks around the world. The purpose of this slide is to evaluated how much devices get affected within 24 hours The various KPI such as streaming, worldwide, mode of attacks, etc.
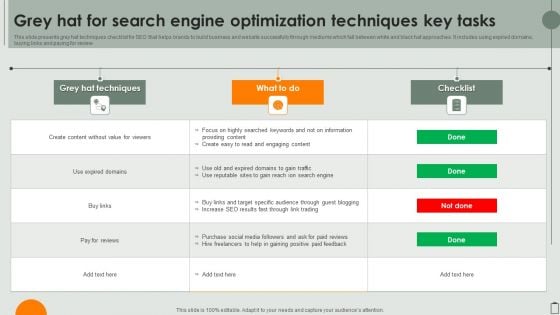
Grey Hat For Search Engine Optimization Techniques Key Tasks Elements PDF
This slide presents grey hat techniques checklist for SEO that helps brands to build business and website successfully through mediums which fall between white and black hat approaches. It includes using expired domains, buying links and paying for review. Showcasing this set of slides titled Grey Hat For Search Engine Optimization Techniques Key Tasks Elements PDF. The topics addressed in these templates are Information Providing Content, Expired Domains Gain Traffic, Target Specific Audience. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

White Hat SEO With Techniques Advantages And Limitations Training Ppt
The purpose of the following slide is to provide an overview of white hat SEO. It also includes information regarding the major white hat techniques, advantages, and limitations.

Table Of Content Cyber Security And Phishing Awareness Training Hacking Prevention Awareness Training For IT Security Elements PDF
Deliver an awe inspiring pitch with this creative table of content cyber security and phishing awareness training hacking prevention awareness training for it security elements pdf bundle. Topics like training, awareness, strategies, communication, plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
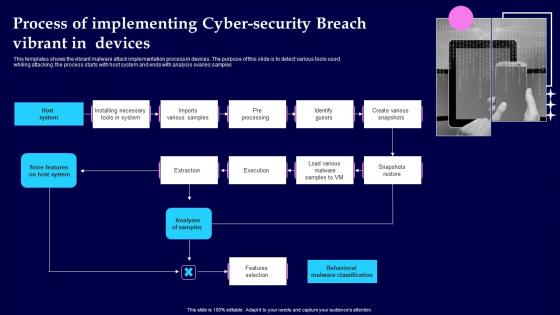
Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf
This templates shows the vibrant malware attack implementation process in devices. The purpose of this slide is to detect various tools used whiling attacking .the process starts with host system and ends with analysis ovaries samples Pitch your topic with ease and precision using this Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf This layout presents information on Analyses Of Samples, Features Selection, Pre Processing It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the vibrant malware attack implementation process in devices. The purpose of this slide is to detect various tools used whiling attacking .the process starts with host system and ends with analysis ovaries samples
Coder Checking Business Internet Security Threats Ppt PowerPoint Presentation Gallery Model PDF
Persuade your audience using this coder checking business internet security threats ppt powerpoint presentation gallery model pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including coder checking business internet security threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Coders Guide To Web Design Development Project Strategy Icon Slides PDF
Persuade your audience using this Coders Guide To Web Design Development Project Strategy Icon Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Coders Guide Web Design, Development Project Strategy Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
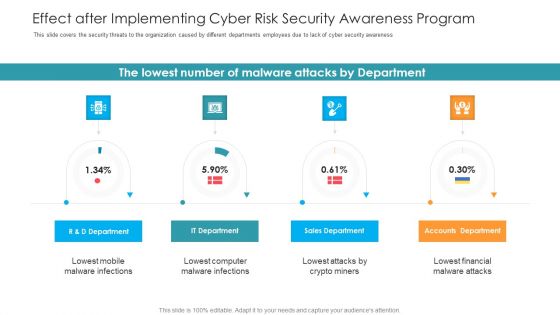
Effect After Implementing Cyber Risk Security Awareness Program Hacking Prevention Awareness Training For IT Security Information PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative effect after implementing cyber risk security awareness program hacking prevention awareness training for it security information pdf bundle. Topics like accounts department, sales department, it department, r and d department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda For Cyber Security And Phishing Awareness Training Hacking Prevention Awareness Training For IT Security Sample PDF
Presenting agenda for cyber security and phishing awareness training hacking prevention awareness training for it security sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like safeguard, integrity, cybersecurity, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
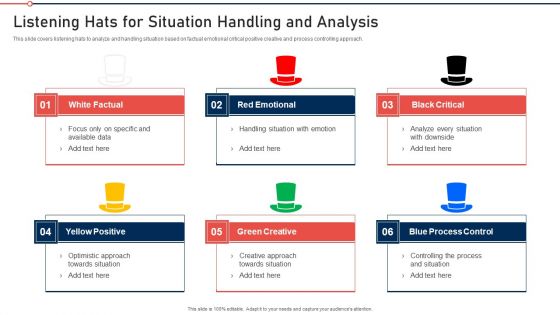
Modernization And Product Listening Hats For Situation Handling And Analysis Formats PDF
This slide covers listening hats to analyze and handling situation based on factual emotional critical positive creative and process controlling approach. This is a modernization and product listening hats for situation handling and analysis formats pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like white factual, red emotional, black critical, yellow positive, green creative, blue process control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Russian Cyber Attacks On Ukraine IT Cyber Attacks On Ukraine Information PDF
This slide represents the conspicuous Russian cyber attacks on Ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. Presenting russian cyber attacks on ukraine it cyber attacks on ukraine information pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like social media, systems, networks, services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
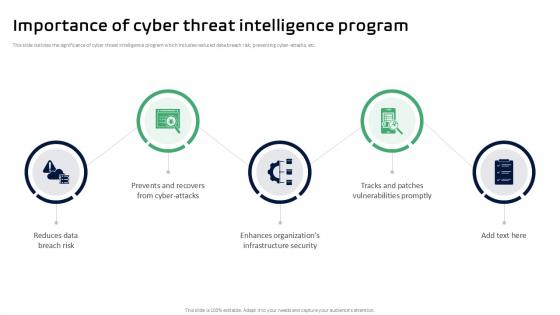
Importance Of Cyber Threat Intelligence Program Threat Intelligence Ppt Slides
This slide outlines the significance of cyber threat intelligence program which includes reduced data breach risk, preventing cyber attacks, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Importance Of Cyber Threat Intelligence Program Threat Intelligence Ppt Slides. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the significance of cyber threat intelligence program which includes reduced data breach risk, preventing cyber attacks, etc.
Stock Photo White Hat For Patrick Day PowerPoint Slide
We have added colors in the celebration of Patrick's Day. To show our joy we have designed this beautiful image . This image contains the graphic of white hat which is a traditional hat of this festival. Display the colors of this festival in your creativity by using this exclusive image.

Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf
This slide represents the emerging trends in cyber attacks faced by the enterprises. It includes details related to cyber attacks experienced by enterprises, top global fraud types and volume of cyber security incidents by sector. Explore a selection of the finest Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents the emerging trends in cyber attacks faced by the enterprises. It includes details related to cyber attacks experienced by enterprises, top global fraud types and volume of cyber security incidents by sector.
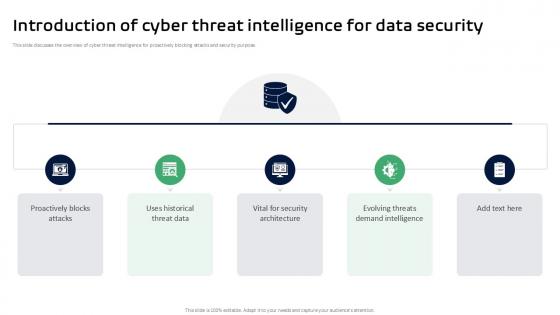
Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template
This slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template This slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose.
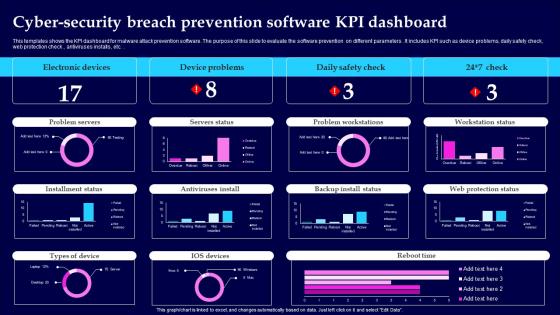
Cyber Security Breach Prevention Software KPI Dashboard Information Pdf
This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc. Showcasing this set of slides titled Cyber Security Breach Prevention Software KPI Dashboard Information Pdf The topics addressed in these templates are Electronic Devices, Device Problems, Daily Safety Check All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc.

Snowman With Hat On Winter Background PowerPoint Templates Ppt Backgrounds For Slides 1112
We present our Snowman With Hat On Winter Background PowerPoint Templates PPT Backgrounds For Slides 1112.Download and present our Christmas PowerPoint Templates because this slide depicts the festive and holy season to remind your team of your commitment to your faith. Download our Shapes PowerPoint Templates because this will helps you to explore the minutest detail of each concept and follow the trail to its conclusion. Download and present our Spheres PowerPoint Templates because you have analysed the illness and know the need. Present our Festival PowerPoint Templates because educate your staff on the means to provide the required support for speedy recovery. Present our Holidays PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines.Use these PowerPoint slides for presentations relating to Snowman wearing hat, spheres, shapes, christmas, festival, holidays . The prominent colors used in the PowerPoint template are Red, Black, White. Presenters tell us our Snowman With Hat On Winter Background PowerPoint Templates PPT Backgrounds For Slides 1112 are designed by professionals Professionals tell us our spheres PowerPoint templates and PPT Slides are Luxurious. Presenters tell us our Snowman With Hat On Winter Background PowerPoint Templates PPT Backgrounds For Slides 1112 are Detailed. Presenters tell us our festival PowerPoint templates and PPT Slides are Tranquil. Use our Snowman With Hat On Winter Background PowerPoint Templates PPT Backgrounds For Slides 1112 are Youthful. PowerPoint presentation experts tell us our hat PowerPoint templates and PPT Slides are Elegant. Imagine your audience applauding with our Snowman With Hat On Winter Background PowerPoint Templates Ppt Backgrounds For Slides 1112. Make sure your presentation gets the attention it deserves.

Snowman Wearing Hat Christmas Events PowerPoint Templates Ppt Backgrounds For Slides 1112
We present our Snowman Wearing Hat Christmas Events PowerPoint Templates PPT Backgrounds For Slides 1112.Use our Spheres PowerPoint Templates because,This diagram provides multiple options for taking in and making sense of information. Use our Shapes PowerPoint Templates because,There are so many different pieces to the puzzle. Use our Christmas PowerPoint Templates because,The evergreen fir is the tree of choice in this season. Use our Festival PowerPoint Templates because,Forward thinking is the way to go. Use our Holidays PowerPoint Templates because,You can spread the fruits of your efforts and elaborate your ideas on the prevention, diagnosis, control and cure of prevalent diseases.Use these PowerPoint slides for presentations relating to Snowman wearing hat, spheres, shapes, christmas, festival, holidays . The prominent colors used in the PowerPoint template are Red, Black, White. Customers tell us our Snowman Wearing Hat Christmas Events PowerPoint Templates PPT Backgrounds For Slides 1112 will help them to explain complicated concepts. Professionals tell us our festival PowerPoint templates and PPT Slides are Exuberant. PowerPoint presentation experts tell us our Snowman Wearing Hat Christmas Events PowerPoint Templates PPT Backgrounds For Slides 1112 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. PowerPoint presentation experts tell us our spheres PowerPoint templates and PPT Slides are Sparkling. Presenters tell us our Snowman Wearing Hat Christmas Events PowerPoint Templates PPT Backgrounds For Slides 1112 are Wistful. Professionals tell us our shapes PowerPoint templates and PPT Slides are Colorful. Expedite growth with our Snowman Wearing Hat Christmas Events PowerPoint Templates Ppt Backgrounds For Slides 1112. Download without worries with our money back guaranteee.

Clock With Christmas Hat New Year PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Clock With Christmas Hat New Year PowerPoint Templates PPT Backgrounds For Slides 1212.Present our Christmas PowerPoint Templates because you can Embrace the overwhelming mood of the season. Present our Time Planning PowerPoint Templates because it helps to prove the viability of your ideas to help your organisation to achieve the quality and success required. Download and present our New year PowerPoint Templates because different personalities, different abilities but formidable together. Download and present our Clocks PowerPoint Templates because you can Refine them all as you take them through the numerous filtering stages of the funnel of your quality control process. Use our Christmas PowerPoint Templates because the Christmas season brings with it cheer and goodwill.Use these PowerPoint slides for presentations relating to New year clock in red hat, time planning, christmas, new year, christmas, clocks. The prominent colors used in the PowerPoint template are Red, White, Black. Customers tell us our Clock With Christmas Hat New Year PowerPoint Templates PPT Backgrounds For Slides 1212 are Breathtaking. Presenters tell us our time PowerPoint templates and PPT Slides are Flirty. Presenters tell us our Clock With Christmas Hat New Year PowerPoint Templates PPT Backgrounds For Slides 1212 are Efficient. The feedback we get is that our clock PowerPoint templates and PPT Slides are Charming. Use our Clock With Christmas Hat New Year PowerPoint Templates PPT Backgrounds For Slides 1212 are designed to make your presentations professional. You can be sure our red PowerPoint templates and PPT Slides are One-of-a-kind. Our Clock With Christmas Hat New Year PowerPoint Templates Ppt Backgrounds For Slides 1212 are definitely new age. Ring in overdue changes with your ideas.

Alarm Clock Christmas Hat Welcome New Year PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Alarm Clock Christmas Hat Welcome New Year PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Clocks PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need. Download and present our Christmas PowerPoint Templates because you can Embrace the overwhelming mood of the season. Download and present our Festival PowerPoint Templates because you have developed a vision of where you want to be a few years from now. Download and present our Holidays PowerPoint Templates because business ethics is an essential element in your growth. Present our Shapes PowerPoint Templates because your team and you always raise a toast.Use these PowerPoint slides for presentations relating to Clock with christmas hat, christmas, clocks, festival, holidays, shapes. The prominent colors used in the PowerPoint template are Red, Black, White. Professionals tell us our Alarm Clock Christmas Hat Welcome New Year PowerPoint Templates PPT Backgrounds For Slides 1212 are Whimsical. Use our shapes PowerPoint templates and PPT Slides look good visually. Presenters tell us our Alarm Clock Christmas Hat Welcome New Year PowerPoint Templates PPT Backgrounds For Slides 1212 are Dazzling. Professionals tell us our shapes PowerPoint templates and PPT Slides are Wonderful. Presenters tell us our Alarm Clock Christmas Hat Welcome New Year PowerPoint Templates PPT Backgrounds For Slides 1212 are Magical. The feedback we get is that our christmas PowerPoint templates and PPT Slides are the best it can get when it comes to presenting. Increase the output of your factory. Explore avenues available with our Alarm Clock Christmas Hat Welcome New Year PowerPoint Templates Ppt Backgrounds For Slides 1212.

3d Snowman With Hat Holiday PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our 3d Snowman With Hat Holiday PowerPoint Templates PPT Backgrounds For Slides 1212.Present our Holidays PowerPoint Templates because it helps your team to align their arrows to consistently be accurate. Download and present our New year PowerPoint Templates because another year is coming to a close. Download our Festival PowerPoint Templates because spreading the light of knowledge around you will clear the doubts and enlighten the questioning minds with your brilliance and ability. Download our Christmas PowerPoint Templates because you can Set out the goals and your plan of action for teamwork. Present our Shapes PowerPoint Templates because the basic stages are in place, you need to build upon them with our PowerPoint templates.Use these PowerPoint slides for presentations relating to Holiday snowman in a top hat, new year, holidays, festival, christmas, shapes. The prominent colors used in the PowerPoint template are White, Red, Black. Professionals tell us our 3d Snowman With Hat Holiday PowerPoint Templates PPT Backgrounds For Slides 1212 will make you look like a winner. We assure you our top PowerPoint templates and PPT Slides are Precious. PowerPoint presentation experts tell us our 3d Snowman With Hat Holiday PowerPoint Templates PPT Backgrounds For Slides 1212 are Awesome. Presenters tell us our year PowerPoint templates and PPT Slides are Dynamic. The feedback we get is that our 3d Snowman With Hat Holiday PowerPoint Templates PPT Backgrounds For Slides 1212 are Elevated. You can be sure our holidays PowerPoint templates and PPT Slides are Nifty. Optimize your business cyclewith our 3d Snowman With Hat Holiday PowerPoint Templates Ppt Backgrounds For Slides 1212. You'll deliver your best presentation yet.

3d Snowman With Hat Background Christmas PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our 3d Snowman With Hat Background Christmas PowerPoint Templates PPT Backgrounds For Slides 0113.Present our Christmas PowerPoint Templates because It is Aesthetically crafted by artistic young minds. Our PowerPoint Templates and Slides are designed to display your dexterity. Download and present our Nature PowerPoint Templates because Our PowerPoint Templates and Slides are innately eco-friendly. Their high recall value negate the need for paper handouts. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will let you Clearly mark the path for others to follow. Use our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words. Present our Children PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time.Use these PowerPoint slides for presentations relating to 3d render of snowman character, christmas, nature, shapes, signs, children. The prominent colors used in the PowerPoint template are Red, Black, White. People tell us our 3d Snowman With Hat Background Christmas PowerPoint Templates PPT Backgrounds For Slides 0113 will get their audience's attention. You can be sure our character PowerPoint templates and PPT Slides will make the presenter look like a pro even if they are not computer savvy. Customers tell us our 3d Snowman With Hat Background Christmas PowerPoint Templates PPT Backgrounds For Slides 0113 will impress their bosses and teams. Use our character PowerPoint templates and PPT Slides will impress their bosses and teams. PowerPoint presentation experts tell us our 3d Snowman With Hat Background Christmas PowerPoint Templates PPT Backgrounds For Slides 0113 are visually appealing. Customers tell us our character PowerPoint templates and PPT Slides look good visually. Capitalise on the benefits our 3d Snowman With Hat Background Christmas PowerPoint Templates Ppt Backgrounds For Slides 0113 offer. They make the entire process a simpler one.
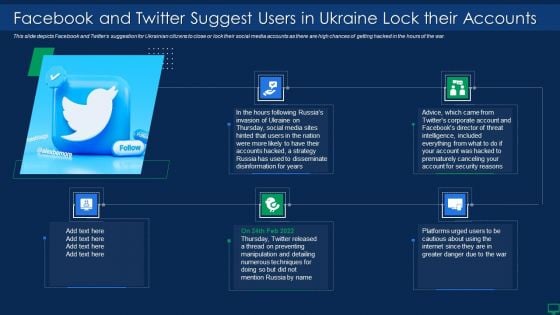
Russian Cyber Attacks On Ukraine IT Facebook And Twitter Suggest Rules PDF
This slide depicts Facebook and Twitters suggestion for Ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. This is a russian cyber attacks on ukraine it facebook and twitter suggest rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like social media, accounts, strategy, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
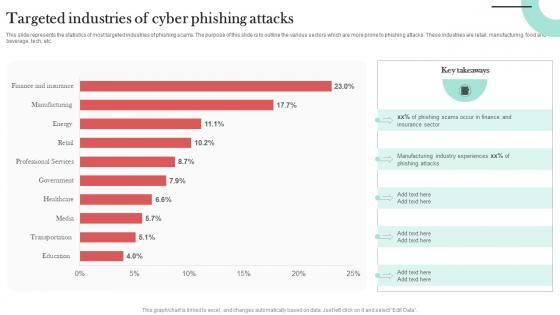
Targeted Industries Of Cyber Phishing Man In The Middle Phishing IT
This slide represents the statistics of most targeted industries of phishing scams. The purpose of this slide is to outline the various sectors which are more prone to phishing attacks. These industries are retail, manufacturing, food and beverage, tech, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Targeted Industries Of Cyber Phishing Man In The Middle Phishing IT to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the statistics of most targeted industries of phishing scams. The purpose of this slide is to outline the various sectors which are more prone to phishing attacks. These industries are retail, manufacturing, food and beverage, tech, etc.

Vishing Attacks Prevention Email Signing Man In The Middle Phishing IT
This slide talks about the techniques which can help in protecting organizations from phishing and vishing attacks. The purpose of this slide is to explain two important methods of preventing cyber scams. These techniques are email signing and code signing. The Vishing Attacks Prevention Email Signing Man In The Middle Phishing IT is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide talks about the techniques which can help in protecting organizations from phishing and vishing attacks. The purpose of this slide is to explain two important methods of preventing cyber scams. These techniques are email signing and code signing.

Cyber Terrorism Assault Peroration Of Cyber Terrorism Attacks Sample PDF
This slide explains the conclusion or peroration of cyber terrorism and how it is different from information warfare as it targets civilians rather than operations. This is a cyber terrorism assault peroration of cyber terrorism attacks sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitored closely, implemented and every aspect, ideological gain oriented You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Global Cyber War Attacks Icon Ideas PDF
Presenting Global Cyber War Attacks Icon Ideas PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Global Cyber, War Attacks Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Series Of Cyber Security Attacks Against Ukraine 2022 Facebook And Twitter Suggest Users In Ukraine Lock Their Accounts Professional PDF
This slide depicts facebook and twitters suggestion for ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. Present like a pro with Series Of Cyber Security Attacks Against Ukraine 2022 Facebook And Twitter Suggest Users In Ukraine Lock Their Accounts Professional PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
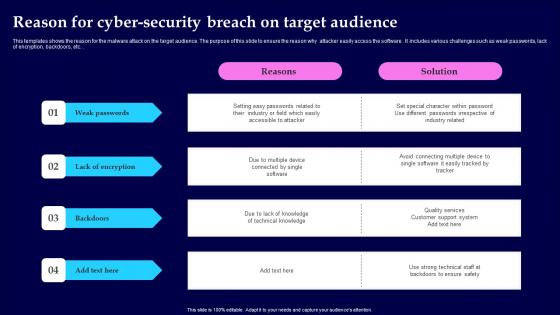
Reason For Cyber Security Breach On Target Audience Microsoft Pdf
This templates shows the reason for the malware attack on the target audience. The purpose of this slide to ensure the reason why attacker easily access the software . It includes various challenges such as weak passwords, lack of encryption, backdoors, etc. Showcasing this set of slides titled Reason For Cyber Security Breach On Target Audience Microsoft Pdf The topics addressed in these templates are Weak Passwords, Lack Of Encryption, Backdoors All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the reason for the malware attack on the target audience. The purpose of this slide to ensure the reason why attacker easily access the software . It includes various challenges such as weak passwords, lack of encryption, backdoors, etc.
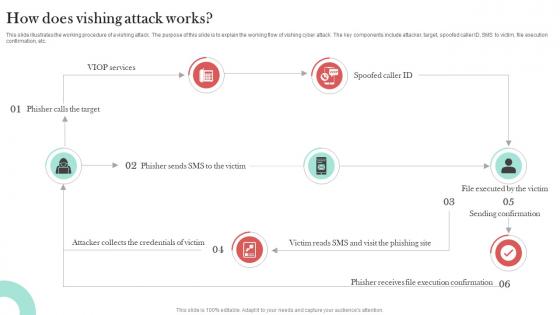
How Does Vishing Attack Works Man In The Middle Phishing IT
This slide illustrates the working procedure of a vishing attack. The purpose of this slide is to explain the working flow of vishing cyber attack. The key components include attacker, target, spoofed caller ID, SMS to victim, file execution confirmation, etc. The How Does Vishing Attack Works Man In The Middle Phishing IT is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide illustrates the working procedure of a vishing attack. The purpose of this slide is to explain the working flow of vishing cyber attack. The key components include attacker, target, spoofed caller ID, SMS to victim, file execution confirmation, etc.
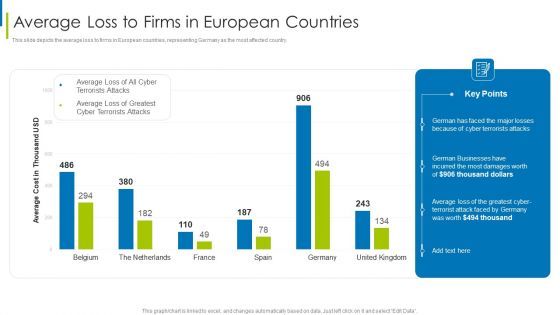
Cyber Terrorism Assault Average Loss To Firms In European Countries Slides PDF
This slide depicts the average loss to firms in European countries, representing Germany as the most affected country. Deliver and pitch your topic in the best possible manner with this cyber terrorism assault average loss to firms in european countries slides pdf Use them to share invaluable insights on German businesses, average loss , cyber terrorist attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

About Phishing Attacks Overview And Impact Man In The Middle Phishing IT
This slide demonstrates the overview of cyber phishing attacks. The purpose of this slide is to talk about the effectiveness of phishing scams. This slide also outlines the issues which can be caused by phishing attacks such as disclosure of private data, etc. Get a simple yet stunning designed About Phishing Attacks Overview And Impact Man In The Middle Phishing IT. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit About Phishing Attacks Overview And Impact Man In The Middle Phishing IT can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide demonstrates the overview of cyber phishing attacks. The purpose of this slide is to talk about the effectiveness of phishing scams. This slide also outlines the issues which can be caused by phishing attacks such as disclosure of private data, etc.
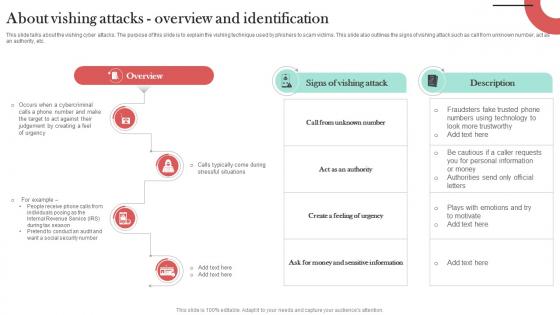
About Vishing Attacks Overview And Identification Man In The Middle Phishing IT
This slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. About Vishing Attacks Overview And Identification Man In The Middle Phishing IT can be your best option for delivering a presentation. Represent everything in detail using About Vishing Attacks Overview And Identification Man In The Middle Phishing IT and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc.
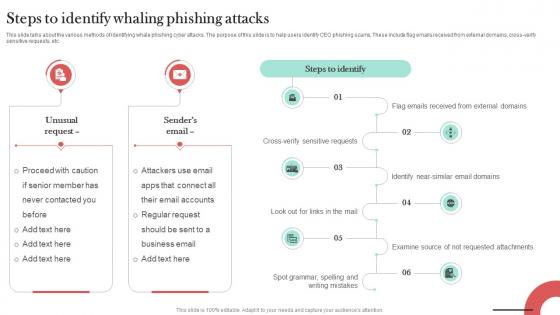
Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT
This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc.
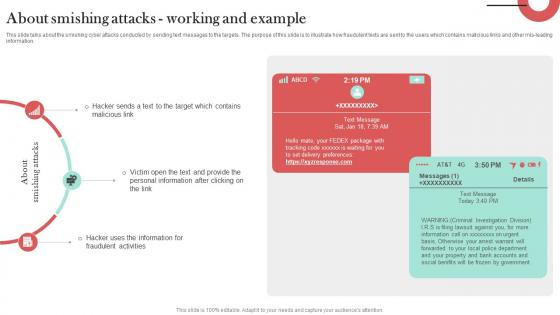
About Smishing Attacks Working And Example Man In The Middle Phishing IT
This slide talks about the smishing cyber attacks conducted by sending text messages to the targets. The purpose of this slide is to illustrate how fraudulent texts are sent to the users which contains malicious links and other mis-leading information. Slidegeeks is here to make your presentations a breeze with About Smishing Attacks Working And Example Man In The Middle Phishing IT With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the smishing cyber attacks conducted by sending text messages to the targets. The purpose of this slide is to illustrate how fraudulent texts are sent to the users which contains malicious links and other mis-leading information.

Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V
The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks. Slidegeeks is here to make your presentations a breeze with Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks.
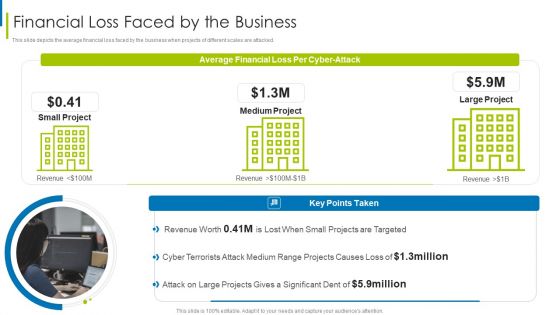
Cyber Terrorism Assault Financial Loss Faced By The Business Summary PDF
This slide depicts the average financial loss faced by the business when projects of different scales are attacked.This is a cyber terrorism assault financial loss faced by the business summary pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like projects are targeted, cyber terrorists, attack on large You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
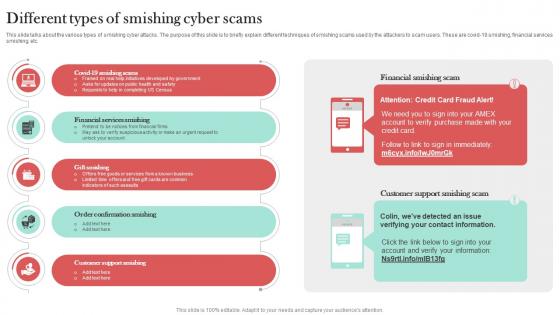
Different Types Of Smishing Cyber Scams Man In The Middle Phishing IT
This slide talks about the various types of smishing cyber attacks. The purpose of this slide is to briefly explain different techniques of smishing scams used by the attackers to scam users. These are covid-19 smishing, financial services smishing, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Different Types Of Smishing Cyber Scams Man In The Middle Phishing IT to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the various types of smishing cyber attacks. The purpose of this slide is to briefly explain different techniques of smishing scams used by the attackers to scam users. These are covid-19 smishing, financial services smishing, etc.
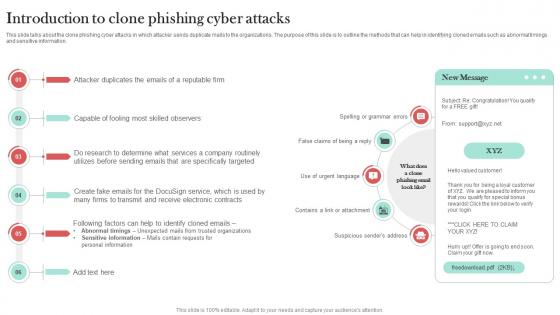
Introduction To Clone Phishing Cyber Man In The Middle Phishing IT
This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information. This Introduction To Clone Phishing Cyber Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on system misconfiguration, network intrusion breakdown, phishing breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
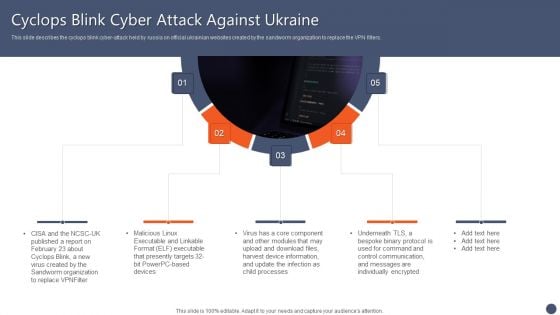
Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF
This slide describes the cyclops blink cyber attack held by russia on official ukrainian websites created by the sandworm organization to replace the VPN filters. Get a simple yet stunning designed Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
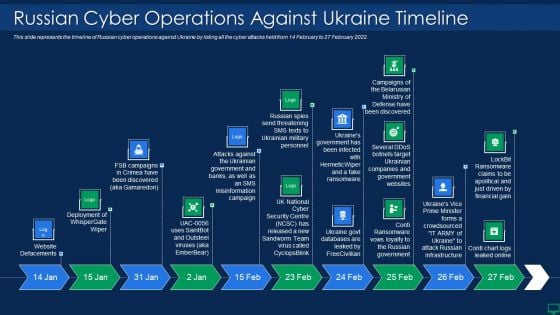
Russian Cyber Attacks On Ukraine IT Russian Cyber Operations Against Themes PDF
This slide represents the timeline of Russian cyber operations against Ukraine by listing all the cyber attacks held from 14 February to 27 February 2022. This is a russian cyber attacks on ukraine it russian cyber operations against themes pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like russian cyber operations against ukraine timeline. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Students Wearing Black Hats During Graduation Event Ppt PowerPoint Presentation Gallery Rules PDF
Presenting this set of slides with name students wearing black hats during graduation event ppt powerpoint presentation gallery rules pdf. The topics discussed in these slide is students wearing black hats during graduation event. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Vector Illustration Of Black Hat With Bird Icon Ppt PowerPoint Presentation File Slide PDF
Pitch your topic with ease and precision using this vector illustration of black hat with bird icon ppt powerpoint presentation file slide pdf. This layout presents information on vector illustration of black hat with bird icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Graduation Degree With Black Hat Vector Icon Ppt PowerPoint Presentation Gallery Graphics Design PDF
Showcasing this set of slides titled graduation degree with black hat vector icon ppt powerpoint presentation gallery graphics design pdf. The topics addressed in these templates are graduation degree with black hat vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
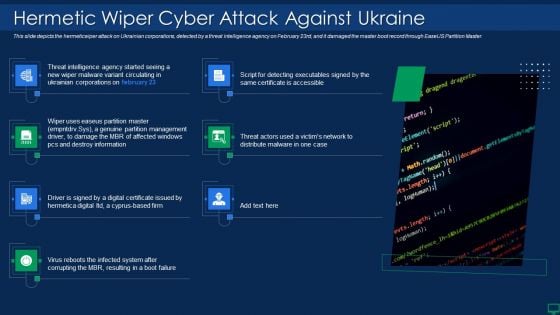
Russian Cyber Attacks On Ukraine IT Hermetic Wiper Cyber Attack Infographics PDF
Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it hermetic wiper cyber attack infographics pdf bundle. Topics like information, management, system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Series Of Cyber Security Attacks Against Ukraine 2022 Hermetic Wiper Cyber Attack Against Ukraine Icons PDF
This slide depicts the hermetic wiper attack on ukrainian corporations, detected by a threat intelligence agency on february 23rd, and it damaged the master boot record through eases partition master. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Hermetic Wiper Cyber Attack Against Ukraine Icons PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
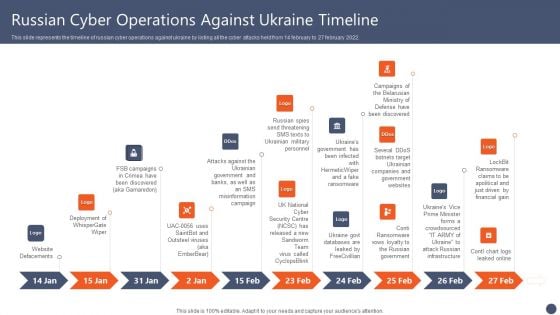
Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF
This slide represents the timeline of russian cyber operations against ukraine by listing all the cyber attacks held from 14 february to 27 february 2022. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
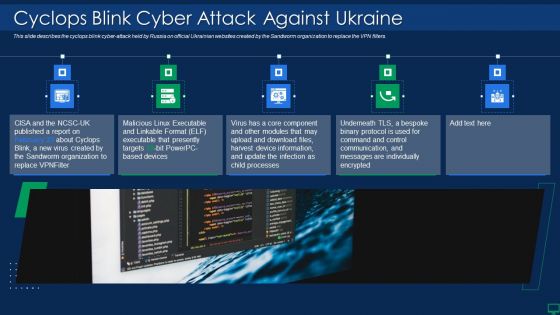
Russian Cyber Attacks On Ukraine IT Cyclops Blink Cyber Attack Mockup PDF
This slide describes the cyclops blink cyber attack held by Russia on official Ukrainian websites created by the Sandworm organization to replace the VPN filters. This is a russian cyber attacks on ukraine it cyclops blink cyber attack mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like device, processes, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
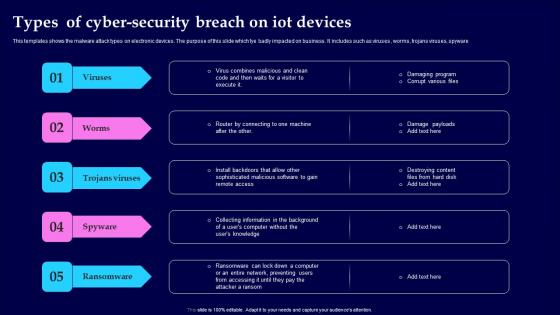
Types Of Cyber Security Breach On IOT Devices Themes Pdf
This templates shows the malware attack types on electronic devices. The purpose of this slide which tye badly impacted on business. It includes such as viruses, worms, trojans viruses, spyware Pitch your topic with ease and precision using this Types Of Cyber Security Breach On IOT Devices Themes Pdf This layout presents information on Viruses, Trojans Viruses, Spyware, Ransomware It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the malware attack types on electronic devices. The purpose of this slide which tye badly impacted on business. It includes such as viruses, worms, trojans viruses, spyware
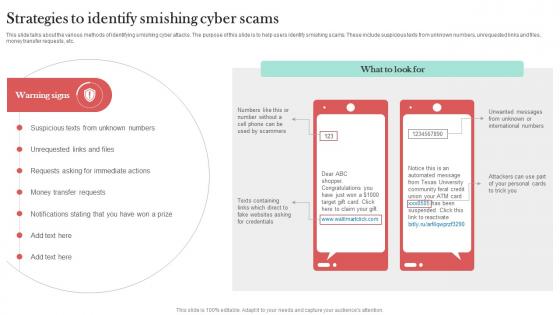
Strategies To Identify Smishing Cyber Scams Man In The Middle Phishing IT
This slide talks about the various methods of identifying smishing cyber attacks. The purpose of this slide is to help users identify smishing scams. These include suspicious texts from unknown numbers, unrequested links and files, money transfer requests, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Strategies To Identify Smishing Cyber Scams Man In The Middle Phishing IT template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Strategies To Identify Smishing Cyber Scams Man In The Middle Phishing IT that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide talks about the various methods of identifying smishing cyber attacks. The purpose of this slide is to help users identify smishing scams. These include suspicious texts from unknown numbers, unrequested links and files, money transfer requests, etc.
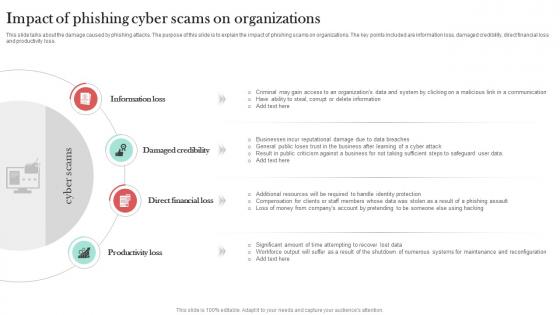
Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT
This slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations. The key points included are information loss, damaged credibility, direct financial loss and productivity loss. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT. This slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations. The key points included are information loss, damaged credibility, direct financial loss and productivity loss.
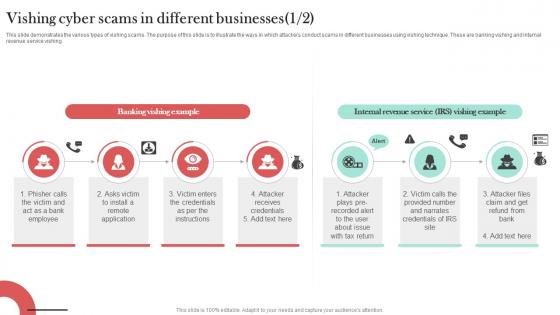
Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT
This slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing. Are you searching for a Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT from Slidegeeks today. This slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing.
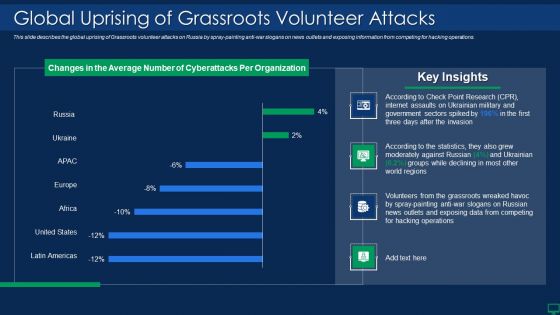
Russian Cyber Attacks On Ukraine IT Global Uprising Of Grassroots Microsoft PDF
This slide describes the global uprising of Grassroots volunteer attacks on Russia by spray painting anti war slogans on news outlets and exposing information from competing for hacking operations. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it global uprising of grassroots microsoft pdf bundle. Topics like internet, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

SEO Types Based On Techniques And Ethical Practices Training Ppt
The purpose of this slide is to showcase the classification of SEO based on techniques and ethical practices. The major SEO types that come under techniques classification are on-page, off-page, technical, and local SEO. In contrast, white hat, grey hat, and black hat fall under the ethical practices category.

Distributed Ledger Technology Impact On Data Security Infographics Pdf
This slide highlights impact on blockchain on data security aimed at reducing costs, increasing transparency, enhancing security and efficiency. It covers encryption and validation, decentralized data security with difficulties in hacking Pitch your topic with ease and precision using this Distributed Ledger Technology Impact On Data Security Infographics Pdf This layout presents information on Encryption And Validation, Decentralized Data Security, Difficulties In Hacking It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights impact on blockchain on data security aimed at reducing costs, increasing transparency, enhancing security and efficiency. It covers encryption and validation, decentralized data security with difficulties in hacking
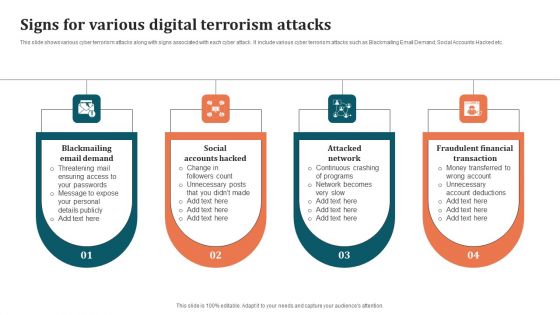
Signs For Various Digital Terrorism Attacks Brochure PDF
This slide shows various cyber terrorism attacks along with signs associated with each cyber attack. It include various cyber terrorism attacks such as Blackmailing Email Demand, Social Accounts Hacked etc. Presenting Signs For Various Digital Terrorism Attacks Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Attacked Network, Fraudulent Financial Transaction, Social Accounts Hacked. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































