Incident
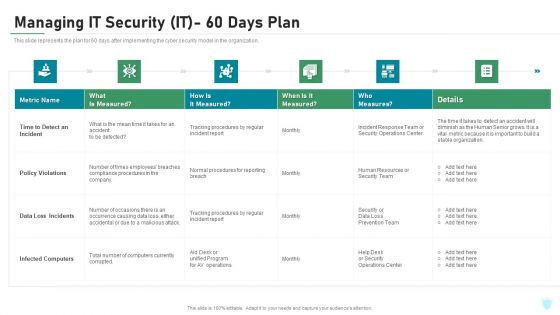
Managing IT Security IT 60 Days Plan Ppt Ideas Graphics PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative managing it security it 60 days plan ppt ideas graphics pdf bundle. Topics like policy violations, infected computers, data loss incidents, time to detect an incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
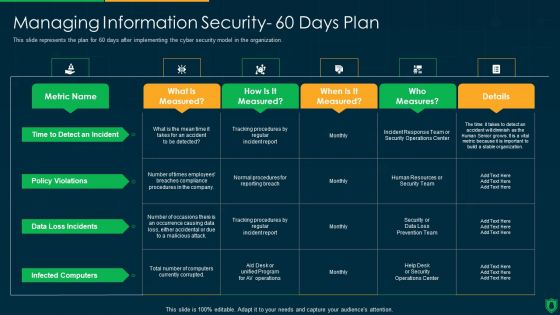
Info Security Managing Information Security 60 Days Plan Ppt PowerPoint Presentation File Graphics Example PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver and pitch your topic in the best possible manner with this info security managing information security 60 days plan ppt powerpoint presentation file graphics example pdf. Use them to share invaluable insights on policy violations, data loss incidents, infected computers, time to detect an incident and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
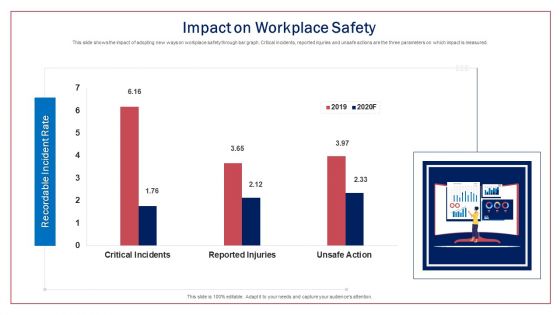
Impact On Workplace Safety Ppt Slides Infographics PDF
This slide shows the impact of adopting new ways on workplace safety through bar graph. Critical incidents, reported injuries and unsafe actions are the three parameters on which impact is measured. Deliver an awe-inspiring pitch with this creative impact on workplace safety ppt slides infographics pdf. bundle. Topics like recordable incident rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Intelligent Architecture Growing Cyber Security Issues Ppt Professional Design Templates PDF
The slide provides the major cyber security issues Unprecedented Attacks, Cyber Espionage, and Data Theft along with the split of total information security incidents by the type of incident Deliver an awe inspiring pitch with this creative intelligent architecture growing cyber security issues ppt professional design templates pdf bundle. Topics like organizations, cyber security, business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
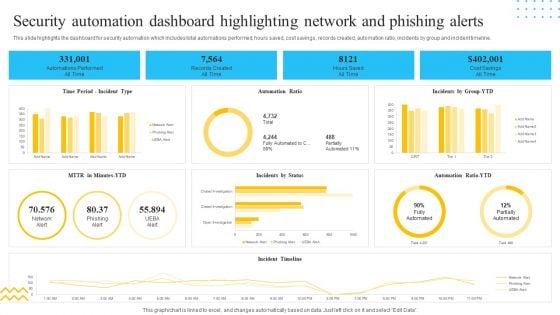
IT Security Automation Tools Integration Security Automation Dashboard Highlighting Network Portrait PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Security Automation Dashboard Highlighting Network Portrait PDF bundle. Topics like Records Created, All Time, Hours Saved, Cost Savings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
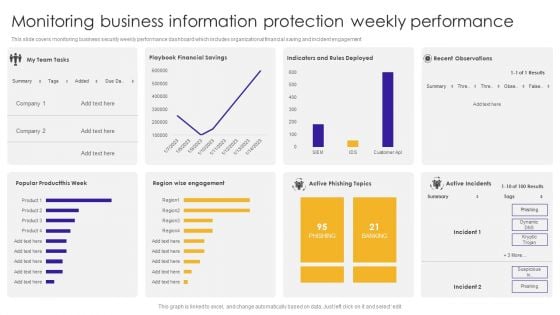
Monitoring Business Information Protection Weekly Performance Summary PDF
This slide covers monitoring business security weekly performance dashboard which includes organizational financial saving and incident engagement. Pitch your topic with ease and precision using this Monitoring Business Information Protection Weekly Performance Summary PDF. This layout presents information on Active Phishing, Active Incidents, Recent Observations. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
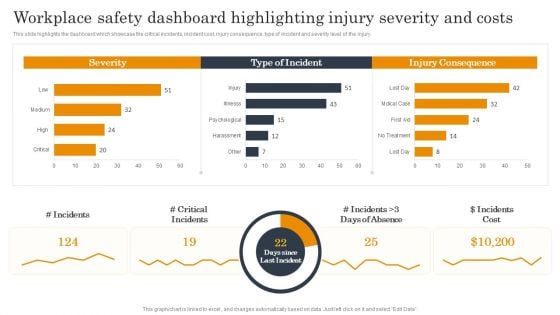
Employee Health And Safety Workplace Safety Dashboard Highlighting Injury Severity And Costs Sample PDF
This slide highlights the dashboard which showcase the critical incidents, incident cost, injury consequence, type of incident and severity level of the injury. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Employee Health And Safety Workplace Safety Dashboard Highlighting Injury Severity And Costs Sample PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Employee Health And Safety Workplace Safety Dashboard Highlighting Injury Severity And Costs Sample PDF.
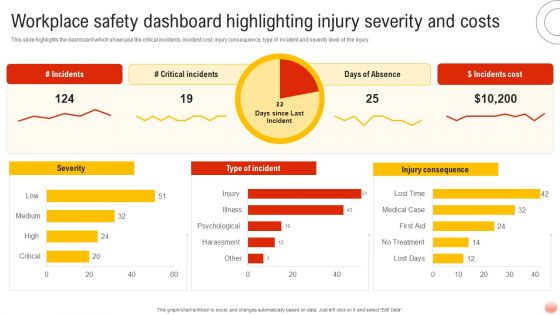
Best Practices For Occupational Health And Safety Workplace Safety Dashboard Highlighting Introduction PDF
This slide highlights the dashboard which showcase the critical incidents, incident cost, injury consequence, type of incident and severity level of the injury. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices For Occupational Health And Safety Workplace Safety Dashboard Highlighting Introduction PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Gra Best Practices For Occupational Health And Safety Workplace Safety Dashboard Highlighting Introduction PDF today and make your presentation stand out from the rest.
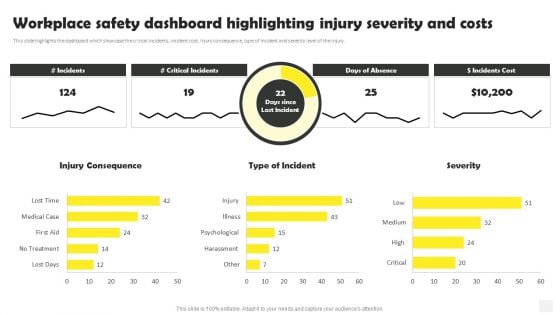
Occupational Health And Safety At Workplace Workplace Safety Dashboard Highlighting Formats PDF
This slide highlights the dashboard which showcase the critical incidents, incident cost, injury consequence, type of incident and severity level of the injury. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Occupational Health And Safety At Workplace Workplace Safety Dashboard Highlighting Formats PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Occupational Health And Safety At Workplace Workplace Safety Dashboard Highlighting Formats PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Roles And Responsibilities Of SRE Expert Ppt Icon Layouts PDF
The following slide depicts the key roles and responsibilities SRE to manage systems and metrics reporting. It constitutes software development, incident escalation, troubleshooting, documenting processes, managing load, evaluating incidents etc. Persuade your audience using this Roles And Responsibilities Of SRE Expert Ppt Icon Layouts PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Knowledge Software Development, Managin Gload, Evaluating Incidents. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
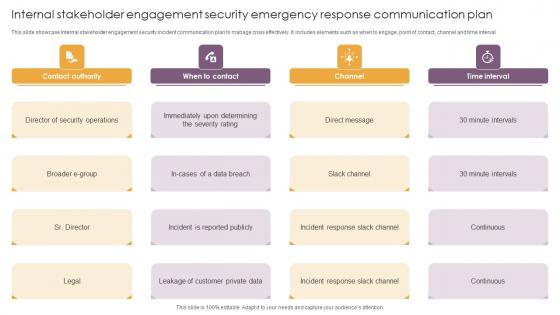
Internal Stakeholder Engagement Security Emergency Response Communication Plan Introduction Pdf
This slide showcase Internal stakeholder engagement security incident communication plan to manage crisis effectively. It includes elements such as when to engage, point of contact, channel and time interval Showcasing this set of slides titled Internal Stakeholder Engagement Security Emergency Response Communication Plan Introduction Pdf The topics addressed in these templates are Contact Authority, Time Interval, Director Of Security Operations All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase Internal stakeholder engagement security incident communication plan to manage crisis effectively. It includes elements such as when to engage, point of contact, channel and time interval
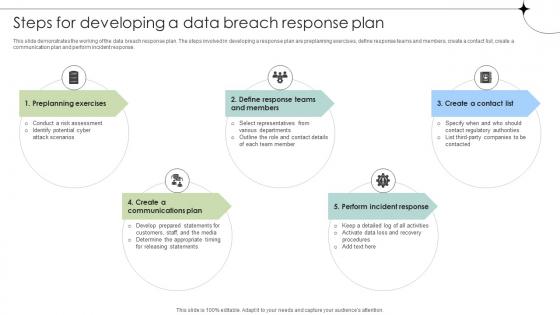
Steps For Developing A Data Breach Response Plan Data Fortification Strengthening Defenses
This slide demonstrates the working of the data breach response plan. The steps involved in developing a response plan are preplanning exercises, define response teams and members, create a contact list, create a communication plan and perform incident response. Want to ace your presentation in front of a live audience Our Steps For Developing A Data Breach Response Plan Data Fortification Strengthening Defenses can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide demonstrates the working of the data breach response plan. The steps involved in developing a response plan are preplanning exercises, define response teams and members, create a contact list, create a communication plan and perform incident response.
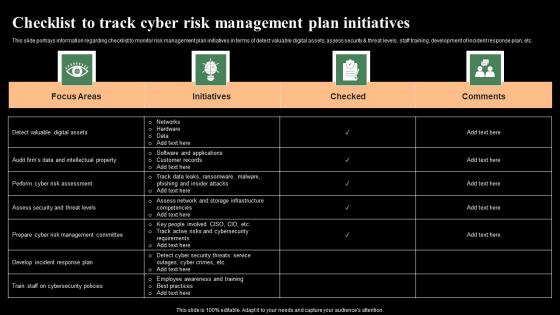
Checklist To Track Cyber Risk Management Plan Initiatives Monitoring Digital Assets Themes Pdf
This slide portrays information regarding checklist to monitor risk management plan initiatives in terms of detect valuable digital assets, assess security and threat levels, staff training, development of incident response plan, etc. Do you know about Slidesgeeks Checklist To Track Cyber Risk Management Plan Initiatives Monitoring Digital Assets Themes Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide portrays information regarding checklist to monitor risk management plan initiatives in terms of detect valuable digital assets, assess security and threat levels, staff training, development of incident response plan, etc.
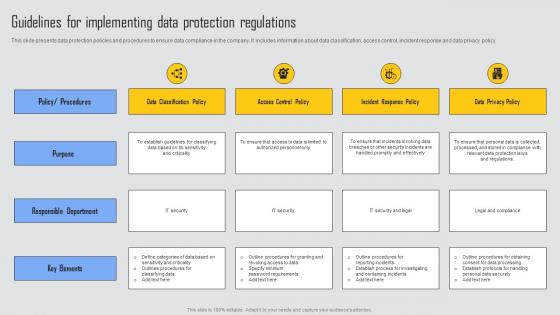
Guidelines For Implementing Managing Risks And Establishing Trust Through Efficient Formats Pdf
This slide presents data protection policies and procedures to ensure data compliance in the company. It includes information about data classification, access control, incident response and data privacy policy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Guidelines For Implementing Managing Risks And Establishing Trust Through Efficient Formats Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Guidelines For Implementing Managing Risks And Establishing Trust Through Efficient Formats Pdf today and make your presentation stand out from the rest This slide presents data protection policies and procedures to ensure data compliance in the company. It includes information about data classification, access control, incident response and data privacy policy.

Cybersecurity Operations Cybersecops Key Outcomes Manage By Security Operations Demonstration PDF
This slide outlines the critical outcomes that are handled by the security operations team. The purpose of this slide is to demonstrate the various key outcomes, their activities, responsible person and remarks. The main outcomes include incident management, incident preparation and threat intelligence. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cybersecurity Operations Cybersecops Key Outcomes Manage By Security Operations Demonstration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cybersecurity Operations Cybersecops Key Outcomes Manage By Security Operations Demonstration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
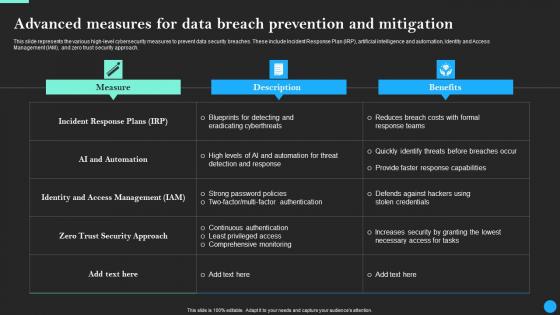
Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.
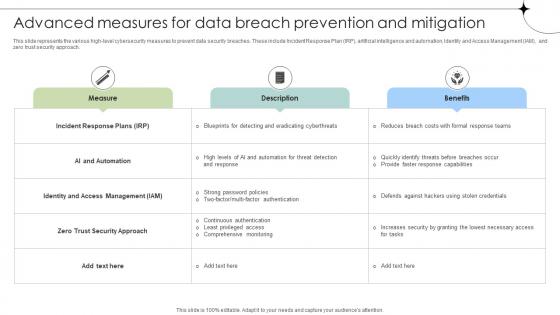
Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.

Deploying Data Governance Digital Transformation Journey PPT PowerPoint DT SS V
This slide presents strategies for ensuring data governance and compliance in a regulated energy and utilities industry. It includes data governance, access controls, audit trail and reporting, vendor management, regulatory compliance monitoring and data incident response. This modern and well-arranged Deploying Data Governance Digital Transformation Journey PPT PowerPoint DT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide presents strategies for ensuring data governance and compliance in a regulated energy and utilities industry. It includes data governance, access controls, audit trail and reporting, vendor management, regulatory compliance monitoring and data incident response.
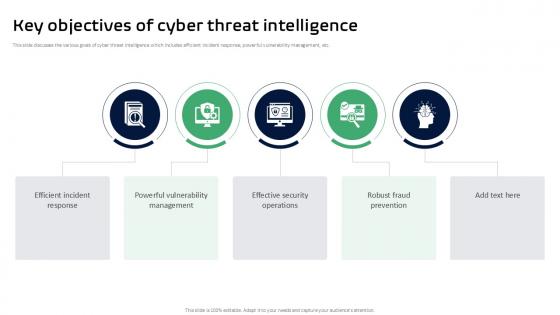
Key Objectives Of Cyber Threat Intelligence Ppt Sample
This slide discusses the various goals of cyber threat intelligence which includes efficient incident response, powerful vulnerability management, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Objectives Of Cyber Threat Intelligence Ppt Sample to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide discusses the various goals of cyber threat intelligence which includes efficient incident response, powerful vulnerability management, etc.
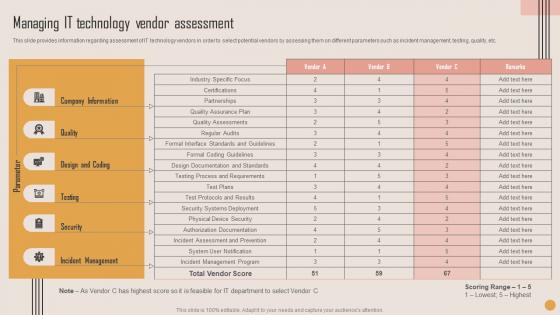
Managing IT Technology Playbook For Strategic Actions To Improve IT Performance Clipart Pdf
This slide provides information regarding assessment of IT technology vendors in order to select potential vendors by assessing them on different parameters such as incident management, testing, quality, etc. Boost your pitch with our creative Managing IT Technology Playbook For Strategic Actions To Improve IT Performance Clipart Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide provides information regarding assessment of IT technology vendors in order to select potential vendors by assessing them on different parameters such as incident management, testing, quality, etc.
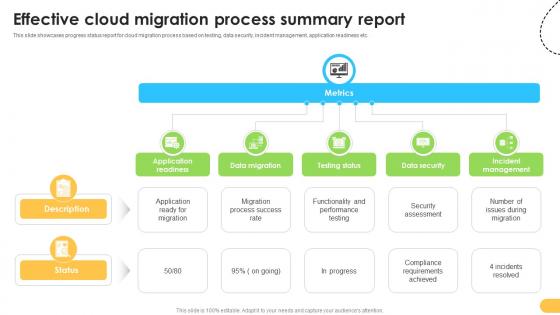
Effective Cloud Migration Process Summary Report Data Migration From On Premises
This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Effective Cloud Migration Process Summary Report Data Migration From On Premises and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc.
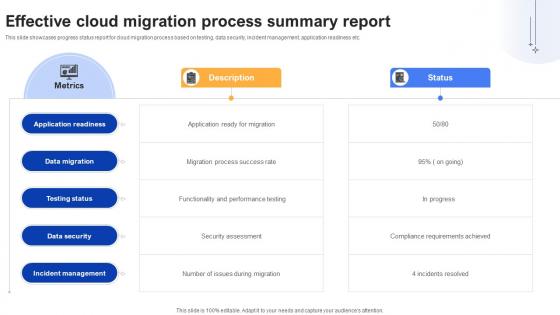
Effective Data Migration Effective Cloud Migration Process Summary Report
This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Effective Data Migration Effective Cloud Migration Process Summary Report and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc.
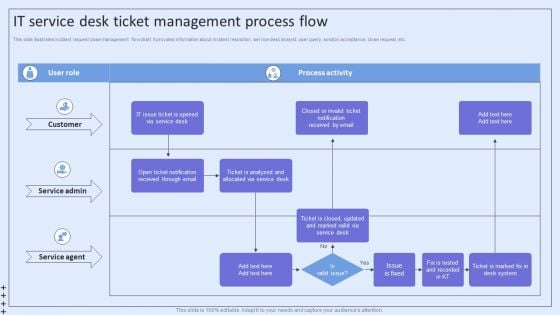
Integrating ITSM To Enhance Service IT Service Desk Ticket Management Process Flow Structure PDF
This slide illustrates incident request close management flowchart. It provides information about incident resolution, service desk analyst, user query, solution acceptance, close request, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Integrating ITSM To Enhance Service IT Service Desk Ticket Management Process Flow Structure PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
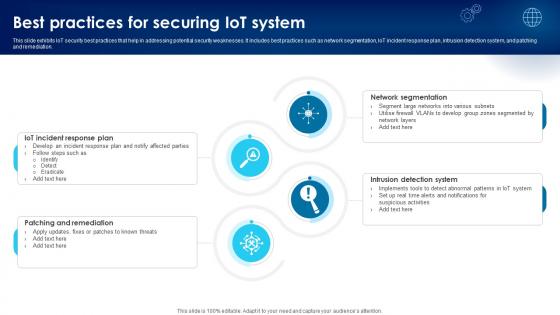
Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V
This slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation. Want to ace your presentation in front of a live audience Our Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation.
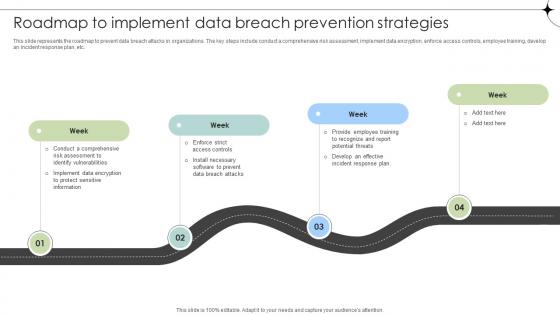
Roadmap To Implement Data Breach Prevention Strategies Data Fortification Strengthening Defenses
This slide represents the roadmap to prevent data breach attacks in organizations. The key steps include conduct a comprehensive risk assessment, implement data encryption, enforce access controls, employee training, develop an incident response plan, etc.Boost your pitch with our creative Roadmap To Implement Data Breach Prevention Strategies Data Fortification Strengthening Defenses. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the roadmap to prevent data breach attacks in organizations. The key steps include conduct a comprehensive risk assessment, implement data encryption, enforce access controls, employee training, develop an incident response plan, etc.

Information Security Program Strategic Agenda Process Microsoft Pdf
This slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc. Showcasing this set of slides titled Information Security Program Strategic Agenda Process Microsoft Pdf. The topics addressed in these templates are Assets And Inventory, Evaluate Risk, Manage Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc.
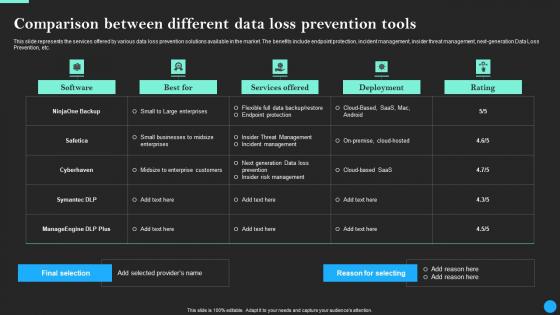
Comparison Between Different Data Loss Prevention Data Breach Prevention Themes Pdf
This slide represents the services offered by various data loss prevention solutions available in the market. The benefits include endpoint protection, incident management, insider threat management, next-generation Data Loss Prevention, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comparison Between Different Data Loss Prevention Data Breach Prevention Themes Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comparison Between Different Data Loss Prevention Data Breach Prevention Themes Pdf today and make your presentation stand out from the rest This slide represents the services offered by various data loss prevention solutions available in the market. The benefits include endpoint protection, incident management, insider threat management, next-generation Data Loss Prevention, etc.
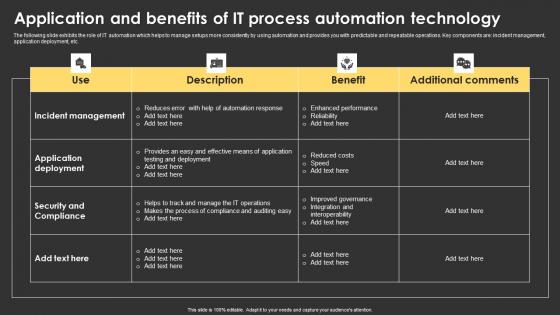
Application And Benefits Of IT Process Automation Technology Summary Pdf
The following slide exhibits the role of IT automation which helps to manage setups more consistently by using automation and provides you with predictable and repeatable operations. Key components are incident management, application deployment, etc. Showcasing this set of slides titled Application And Benefits Of IT Process Automation Technology Summary Pdf. The topics addressed in these templates are Use, Description, Benefit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide exhibits the role of IT automation which helps to manage setups more consistently by using automation and provides you with predictable and repeatable operations. Key components are incident management, application deployment, etc.
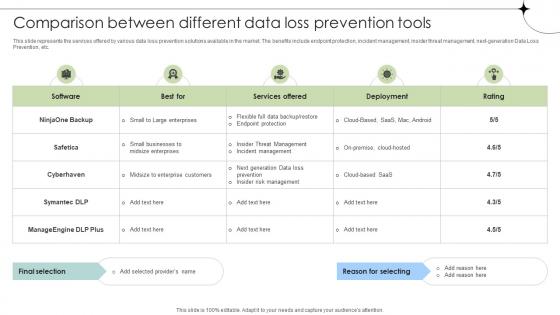
Comparison Between Different Data Loss Prevention Tools Data Fortification Strengthening Defenses
This slide represents the services offered by various data loss prevention solutions available in the market. The benefits include endpoint protection, incident management, insider threat management, next-generation Data Loss Prevention, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comparison Between Different Data Loss Prevention Tools Data Fortification Strengthening Defenses. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comparison Between Different Data Loss Prevention Tools Data Fortification Strengthening Defenses today and make your presentation stand out from the rest This slide represents the services offered by various data loss prevention solutions available in the market. The benefits include endpoint protection, incident management, insider threat management, next-generation Data Loss Prevention, etc.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Plan Slides PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring plan slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Topics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan topics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
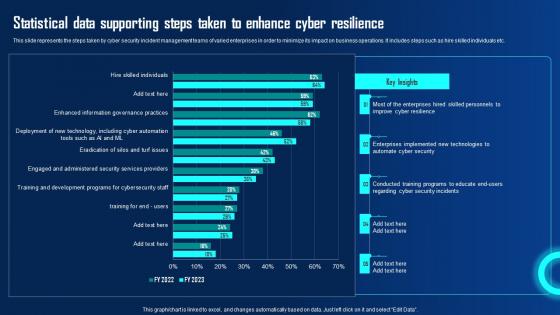
Statistical Data Supporting Steps Taken To Enhance Cyber Ppt Powerpoint Presentation File Outline Pdf
This slide represents the steps taken by cyber security incident management teams of varied enterprises in order to minimize its impact on business operations. It includes steps such as hire skilled individuals etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Statistical Data Supporting Steps Taken To Enhance Cyber Ppt Powerpoint Presentation File Outline Pdf from Slidegeeks and deliver a wonderful presentation. This slide represents the steps taken by cyber security incident management teams of varied enterprises in order to minimize its impact on business operations. It includes steps such as hire skilled individuals etc.
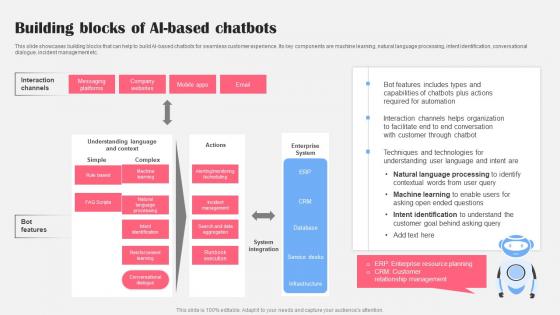
Building Blocks Of Ai Based Chatbots AI Bot Application For Various Industries Slides Pdf
This slide showcases building blocks that can help to build AI based chatbots for seamless customer experience. Its key components are machine learning, natural language processing, intent identification, conversational dialogue, incident management etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Building Blocks Of Ai Based Chatbots AI Bot Application For Various Industries Slides Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide showcases building blocks that can help to build AI based chatbots for seamless customer experience. Its key components are machine learning, natural language processing, intent identification, conversational dialogue, incident management etc.
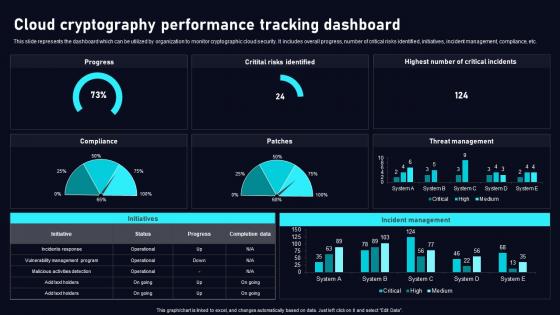
Cloud Cryptography Performance Cloud Data Security Using Cryptography Sample Pdf
This slide represents the dashboard which can be utilized by organization to monitor cryptographic cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Cloud Cryptography Performance Cloud Data Security Using Cryptography Sample Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the dashboard which can be utilized by organization to monitor cryptographic cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, etc.

Use Case Of Splunk Big Data For Security Intelligence Elements Pdf
Following slide showcases uses of splunk big data for security management. The purpose of this slide is to help businesses in investigating threats and improving compliance. It includes elements such as security monitoring, incident reporting, etc. Showcasing this set of slides titled Use Case Of Splunk Big Data For Security Intelligence Elements Pdf The topics addressed in these templates are Security Monitoring, Compliance, Threat Intelligence All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide showcases uses of splunk big data for security management. The purpose of this slide is to help businesses in investigating threats and improving compliance. It includes elements such as security monitoring, incident reporting, etc.
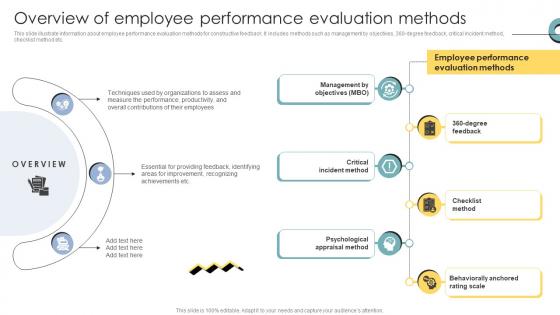
Skill Enhancement Performance Overview Of Employee Performance Evaluation Methods
This slide illustrate information about employee performance evaluation methods for constructive feedback. It includes methods such as management by objectives, 360-degree feedback, critical incident method, checklist method etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Skill Enhancement Performance Overview Of Employee Performance Evaluation Methods and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide illustrate information about employee performance evaluation methods for constructive feedback. It includes methods such as management by objectives, 360-degree feedback, critical incident method, checklist method etc.
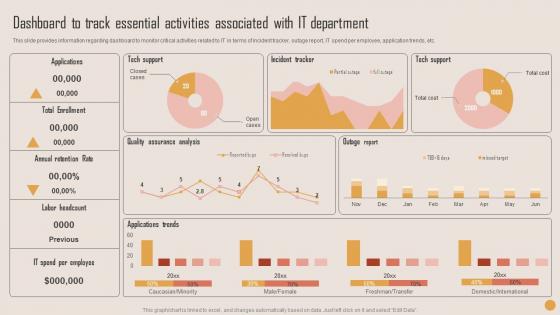
Dashboard To Track Essential Playbook For Strategic Actions To Improve IT Performance Guidelines Pdf
This slide provides information regarding dashboard to monitor critical activities related to IT in terms of incident tracker, outage report, IT spend per employee, application trends, etc. Find highly impressive Dashboard To Track Essential Playbook For Strategic Actions To Improve IT Performance Guidelines Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Dashboard To Track Essential Playbook For Strategic Actions To Improve IT Performance Guidelines Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide provides information regarding dashboard to monitor critical activities related to IT in terms of incident tracker, outage report, IT spend per employee, application trends, etc.
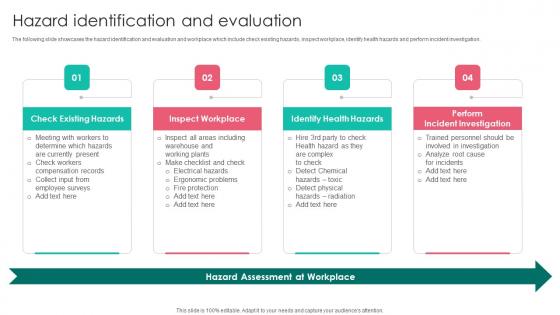
Hazard Identification Workplace Safety Protocol And Security Practices Background Pdf
The following slide showcases the hazard identification and evaluation and workplace which include check existing hazards, inspect workplace, identify health hazards and perform incident investigation. This modern and well arranged Hazard Identification Workplace Safety Protocol And Security Practices Background Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The following slide showcases the hazard identification and evaluation and workplace which include check existing hazards, inspect workplace, identify health hazards and perform incident investigation.

Phishing Awareness Training Program For Man In The Middle Phishing IT
This slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan. There are so many reasons you need a Phishing Awareness Training Program For Man In The Middle Phishing IT. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan.

Inclusive Workplace Training Program Development Of Anti Discrimination Policies DTE SS V
Purpose of this slides to develop anti discrimination policies for employees and establish transparent process for incident reporting. Slidegeeks is here to make your presentations a breeze with Inclusive Workplace Training Program Development Of Anti Discrimination Policies DTE SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first Purpose of this slides to develop anti discrimination policies for employees and establish transparent process for incident reporting.
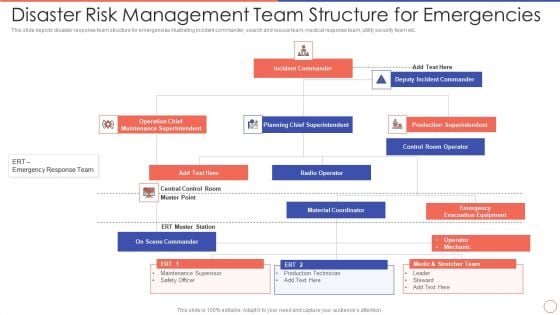
Disaster Risk Management Team Structure For Emergencies Mockup PDF
This slide depicts disaster response team structure for emergencies illustrating incident commander, search and rescue team, medical response team, utility security team etc. Pitch your topic with ease and precision using this disaster risk management team structure for emergencies mockup pdf. This layout presents information on disaster risk management team structure for emergencies. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
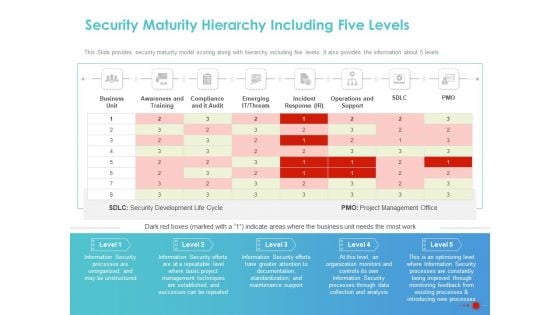
COVID 19 Mitigating Impact On High Tech Industry Security Maturity Hierarchy Including Five Levels Brochure PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry security maturity hierarchy including five levels brochure pdf. The topics discussed in these slides are business unit, awareness and training, compliance and it audit, emerging it threats, incident response ir, operations and support. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Integration Of ITIL With Agile Service Management IT Roles And Responsibilities Within ITSM Team Themes PDF
This slide provides information regarding roles and responsibilities that are assigned to ITSM team as incident manager, problem manager, change manager, release manager and configuration manager. Deliver an awe inspiring pitch with this creative Integration Of ITIL With Agile Service Management IT Roles And Responsibilities Within ITSM Team Themes PDF bundle. Topics like Problem Manager, Release Manager, Configuration Manager can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Adopting Information Technology Infrastructure Roles And Responsibilities Within ITSM Inspiration PDF
This slide provides information regarding roles and responsibilities that are assigned to ITSM team as incident manager, problem manager, change manager, release manager and configuration manager. Deliver an awe inspiring pitch with this creative Adopting Information Technology Infrastructure Roles And Responsibilities Within ITSM Inspiration PDF bundle. Topics like Problem Manager Develops, temporary Problem Manager, Configuration Manager IT can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
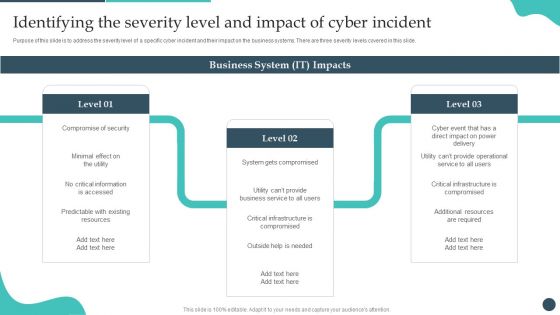
Safety Breach Response Playbook Identifying The Severity Level And Impact Pictures PDF
Purpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide. There are so many reasons you need a Safety Breach Response Playbook Identifying The Severity Level And Impact Pictures PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Essential Roles And Responsibilities Involved In Secops Elements PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure.Deliver an awe inspiring pitch with this creative essential roles and responsibilities involved in secops elements pdf bundle. Topics like security incident responder, security alert investigator, security engineers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
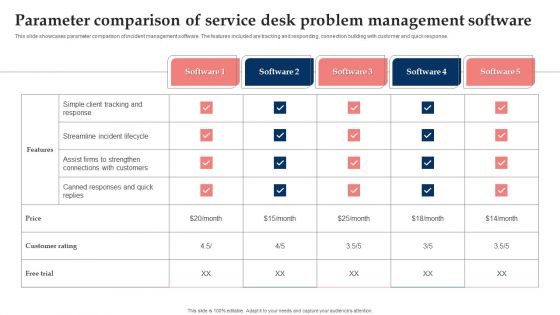
Parameter Comparison Of Service Desk Problem Management Software Slides PDF
This slide showcases parameter comparison of incident management software. The features included are tracking and responding, connection building with customer and quick response. Showcasing this set of slides titled Parameter Comparison Of Service Desk Problem Management Software Slides PDF. The topics addressed in these templates are Customers, Parameter Comparison Service, Desk Problem Management Software. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
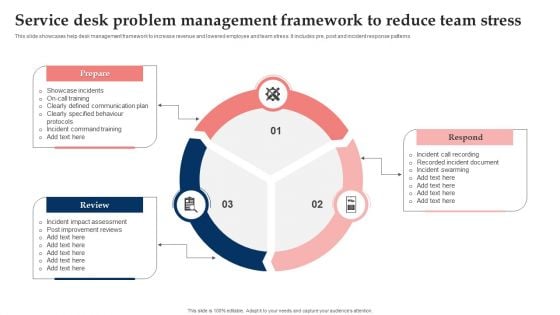
Service Desk Problem Management Framework To Reduce Team Stress Guidelines PDF
This slide showcases help desk management framework to increase revenue and lowered employee and team stress. It includes pre, post and incident response patterns. Presenting Service Desk Problem Management Framework To Reduce Team Stress Guidelines PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Review, Prepare, Respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

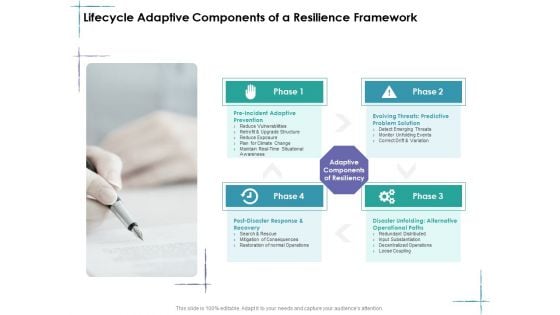
Managing IT Operating System Lifecycle Adaptive Components Of A Resilience Framework Elements PDF
Presenting this set of slides with name managing it operating system lifecycle adaptive components of a resilience framework elements pdf. This is a four stage process. The stages in this process are post disaster response and recovery, pre incident adaptive prevention, evolving threats predictive problem solution. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Facility Management Lifecycle Adaptive Components Of A Resilience Framework Ppt Ideas Show PDF
This is a facility management lifecycle adaptive components of a resilience framework ppt ideas show pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like pre incident adaptive prevention, evolving threats predictive problem solution. post-disaster response and recovery, disaster unfolding alternative operational paths. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
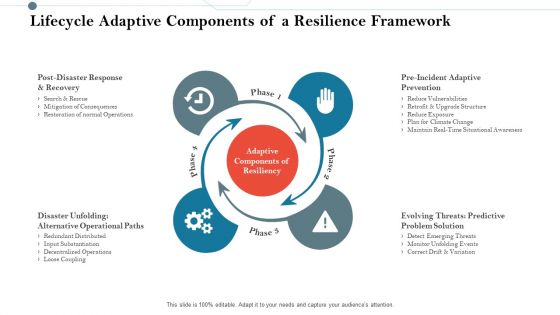
Construction Management Services And Action Plan Lifecycle Adaptive Components Of A Resilience Framework Template PDF
Presenting construction management services and action plan lifecycle adaptive components of a resilience framework template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like post disaster response and recovery, disaster unfolding alternative operational paths, pre incident adaptive prevention. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
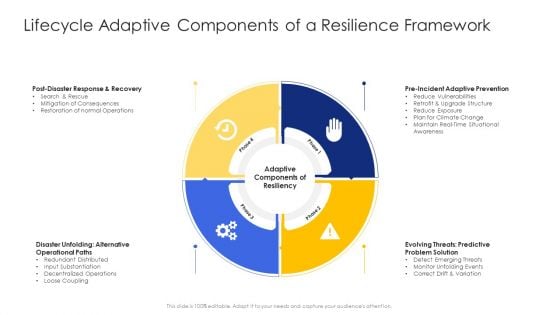
Construction Engineering And Industrial Facility Management Lifecycle Adaptive Components Of A Resilience Framework Ideas PDF
This is a construction engineering and industrial facility management lifecycle adaptive components of a resilience framework ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post disaster response and recovery, pre incident adaptive prevention, disaster unfolding alternative operational paths. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
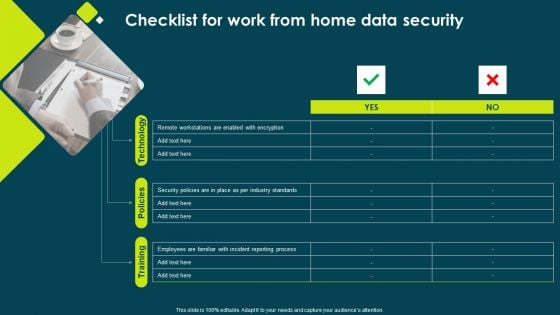
IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF
This is a IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policies, Incident Reporting, Remote Workstations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
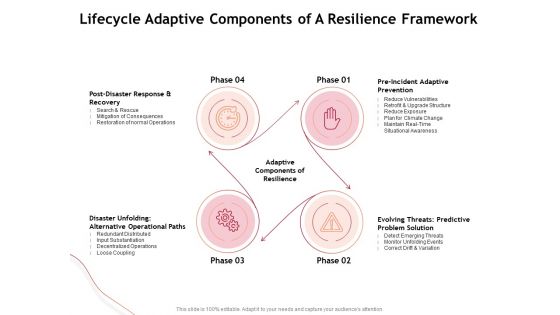
Performance Measuement Of Infrastructure Project Lifecycle Adaptive Components Of A Resilience Framework Diagrams PDF
Presenting this set of slides with name performance measuement of infrastructure project lifecycle adaptive components of a resilience framework diagrams pdf. This is a four stage process. The stages in this process are post disaster response and recovery, disaster unfolding alternative operational paths, pre incident adaptive prevention, evolving threats predictive problem solution. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
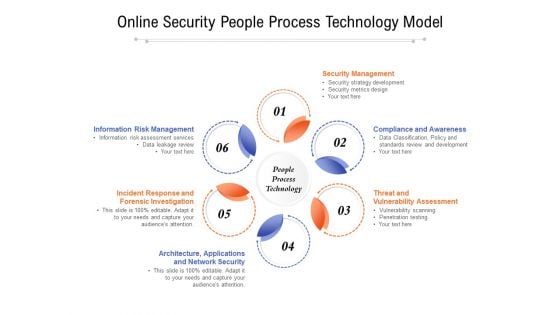
Online Security People Process Technology Model Ppt PowerPoint Presentation Slides Example Introduction PDF
Presenting online security people process technology model ppt powerpoint presentation slides example introduction pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including security management, compliance and awareness, threat and vulnerability assessment, architecture, applications, incident response and forensic investigation, information risk management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Coronavirus Impact Assessment And Mitigation Strategies In Technology Sector Themes PDF
Presenting this set of slides with name table of contents for coronavirus impact assessment and mitigation strategies in technology sector themes pdf. The topics discussed in these slides are risk management plans, business continuity plans, policy management, incident management, risk maturity model scoring and survey results, risk readiness assessments, business impact analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
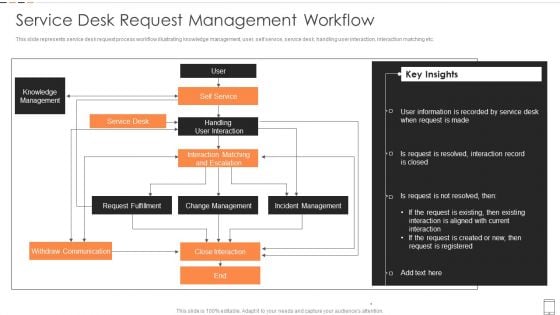
Service Desk Request Management Workflow Demonstration PDF
This slide represents service desk request process workflow illustrating knowledge management, user, self service, service desk, handling user interaction, interaction matching etc.Pitch your topic with ease and precision using this Service Desk Request Management Workflow Demonstration PDF This layout presents information on Request Fulfillment, Incident Management, Knowledge Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
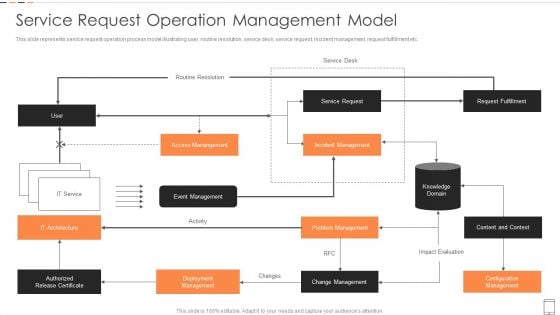
Service Request Operation Management Model Diagrams PDF
This slide represents service request operation process model illustrating user, routine resolution, service desk, service request, incident management, request fulfillment etc.Pitch your topic with ease and precision using this Service Request Operation Management Model Diagrams PDF This layout presents information on Access Manangement, Request Fulfillment, Deployment Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

ITMS Policy And Procedure Management Ppt PowerPoint Presentation Layouts Aids
Presenting this set of slides with name itms policy and procedure management ppt powerpoint presentation layou. This is a eight stage process. The stages in this process are service desk, incident management, problem management, change management, project management, asset management, policy and procedure management, service catalog. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

ITIL Service Operation Overview Infographics PDF
This slide represents the overview of ITIL service operation, including service monitoring, incident resolution, request fulfillment, operational responsibilities, process, functions, and so on.Presenting ITIL Service Operation Overview Infographics PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Comprises Monitoring, Operational Responsibilities, Level Agreements. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































