Information Security Program
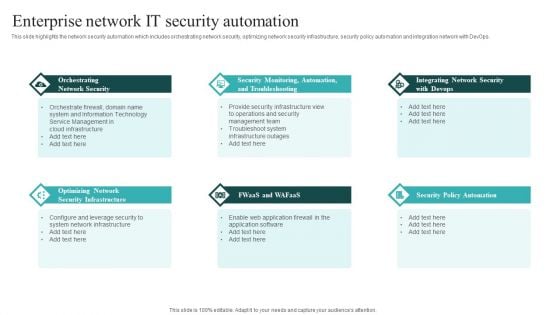
IT Security Automation Systems Guide Enterprise Network It Security Automation Sample PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT Security Automation Systems Guide Enterprise Network It Security Automation Sample PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT Security Automation Systems Guide Enterprise Network It Security Automation Sample PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
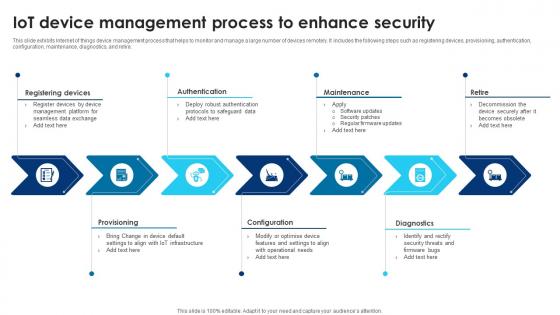
Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V
This slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely. It includes the following steps such as registering devices, provisioning, authentication, configuration, maintenance, diagnostics, and retire. Are you searching for a Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V from Slidegeeks today. This slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely. It includes the following steps such as registering devices, provisioning, authentication, configuration, maintenance, diagnostics, and retire.
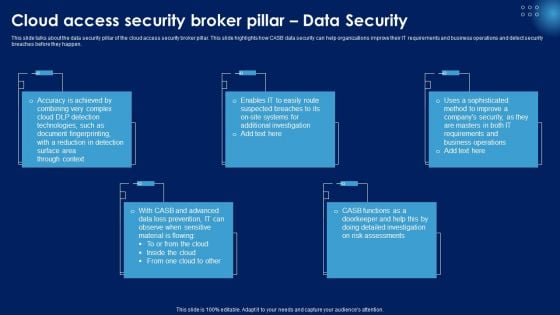
Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF
This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Slidegeeks is here to make your presentations a breeze with Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Risk Management Model For Data Security Setting Scenario For Security Control Designs PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Setting Scenario For Security Control Designs PDF bundle. Topics like Identify, Protect, Detect, Response, Recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
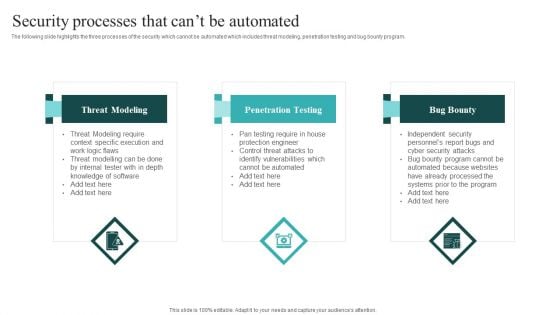
IT Security Automation Systems Guide Security Processes That Cant Be Automated Portrait PDF
The following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Find highly impressive IT Security Automation Systems Guide Security Processes That Cant Be Automated Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download IT Security Automation Systems Guide Security Processes That Cant Be Automated Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
Desktop Security Management What Is Computer Security And How Does It Work Template PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Deliver an awe inspiring pitch with this creative desktop security management what is computer security and how does it work template pdf bundle. Topics like networks, systems, protect data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
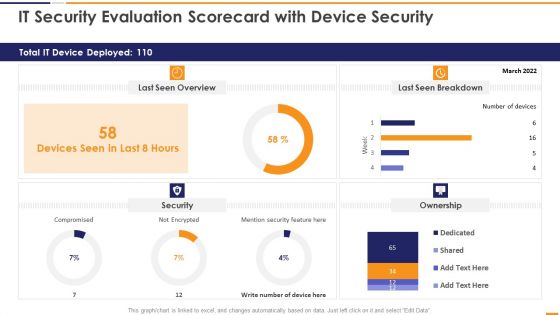
IT Security Evaluation Scorecard With Device Security Ppt Slides Good PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Device Security Ppt Slides Good PDF bundle. Topics like Total IT Device, Last Seen Overview, Last Seen Breakdown, Mention Security Feature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Best Practices Cloud Computing Security IT Ppt Portfolio Master Slide PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver an awe inspiring pitch with this creative cloud security best practices cloud computing security it ppt portfolio master slide pdf bundle. Topics like cloud protection, cloud utilization and risk, authentication process, security policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
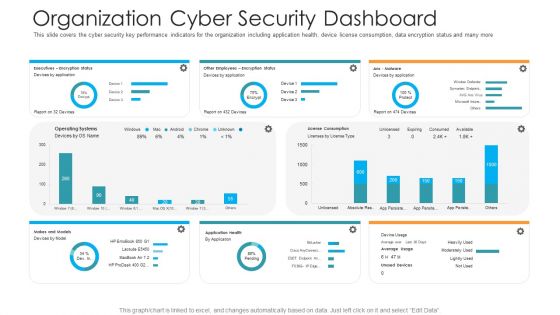
Organization Cyber Security Dashboard Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this organization cyber security dashboard hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on executives, license consumption, operating systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management It Infrastructure Computer Security Budget For Fy2022 Slides PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative desktop security management it infrastructure computer security budget for fy2022 slides pdf bundle. Topics like it infrastructure computer security budget for fy2022 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
The Roi Of Security Awareness Training Hacking Prevention Awareness Training For IT Security Icons PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this the roi of security awareness training hacking prevention awareness training for it security icons pdf. Use them to share invaluable insights on organizations, training, security, costs and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Uniformed Security Our Equipments Used For Security Guard Services Proposal Template PDF
Deliver an awe inspiring pitch with this creative uniformed security our equipments used for security guard services proposal template pdf bundle. Topics like surveillance technology and software, security trailers, vehicles, cameras, mobile phones can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
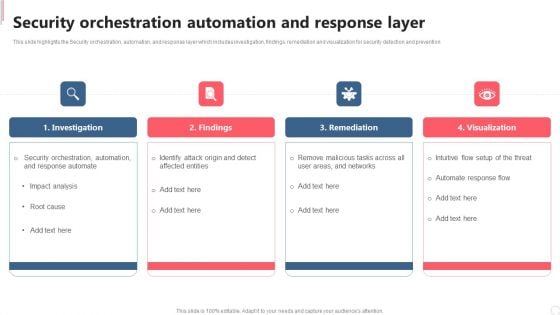
Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. Get a simple yet stunning designed Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Best Data Security Software Why Us For Company Online Database Security Proposal Themes PDF
Presenting this set of slides with name best data security software why us for company online database security proposal themes pdf. This is a four stage process. The stages in this process are our team includes elite software engineers and cyber security experts to keep our culture fresh, innovative and energetic. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security And Surveillance Company Profile Security Company Strategic Partnerships Graphics PDF
This slide highlights the strategic partnership of the security company. It covers the major services such as voice control, mobile security application, and CCTV installation.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Security Company Strategic Partnerships Graphics PDF. Use them to share invaluable insights on Technology Partner, Installation Centres, Partnership Type and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
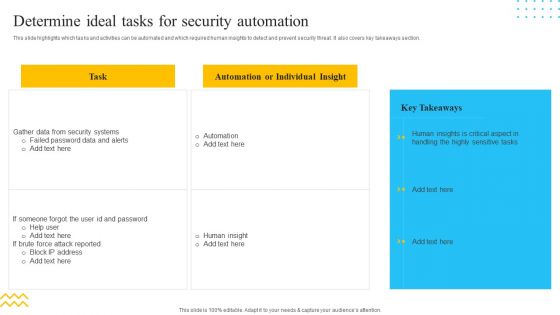
IT Security Automation Tools Integration Determine Ideal Tasks For Security Automation Template PDF
This slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Determine Ideal Tasks For Security Automation Template PDF bundle. Topics like Automation, Individual Insight, Gather Data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Security Risk Management Plan Current Security Infrastructure Performance Analysis Icons PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative cyber security risk management plan current security infrastructure performance analysis icons pdf bundle. Topics like technology, target, plan, vulnerability intelligence, security infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
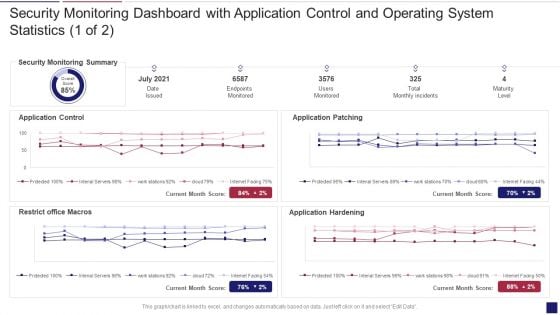
Continuous Development Evaluation Plan Eliminate Cyber Attacks Security Monitoring Dashboard Security Brochure PDF
Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks security monitoring dashboard security brochure pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
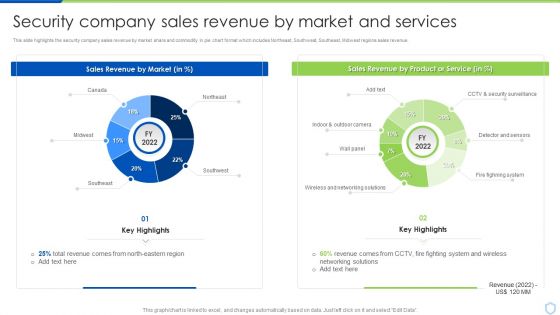
Security And Surveillance Company Profile Security Company Sales Revenue Clipart PDF
This slide highlights the security company sales revenue by market share and commodity in pie chart format which includes Northeast, Southwest, Southeast, Midwest regions sales revenue.Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Security Company Sales Revenue Clipart PDF bundle. Topics like Sales Revenue, Security Surveillance, Networking Solutions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
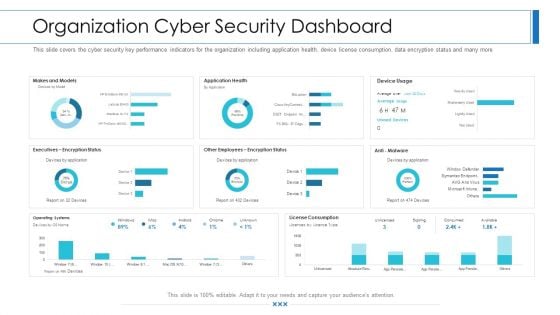
Workforce Security Realization Coaching Plan Organization Cyber Security Dashboard Template PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan organization cyber security dashboard template pdf bundle. Topics like makes and models, operating systems, encryption status, application health, license consumption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
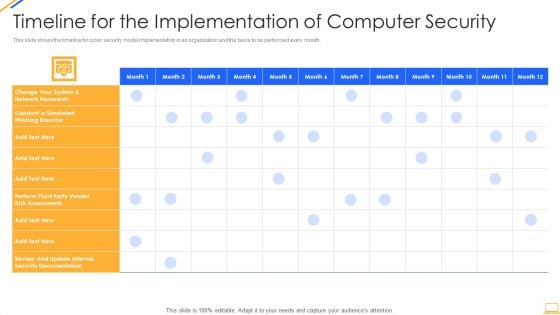
Desktop Security Management Timeline For The Implementation Of Computer Security Sample PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver and pitch your topic in the best possible manner with this desktop security management timeline for the implementation of computer security sample pdf. Use them to share invaluable insights on security documentation, system and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Uniformed Security Our Services For The Security Guard Services Proposal Icons PDF
Deliver and pitch your topic in the best possible manner with this uniformed security our services for the security guard services proposal icons pdf. Use them to share invaluable insights on security, monitoring, planning, corporate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Automation Tools Integration Criteria To Automate Security Analysis And Response Portrait PDF
This slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Criteria To Automate Security Analysis And Response Portrait PDF bundle. Topics like Responses, Criteria, Activities Repeatable can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
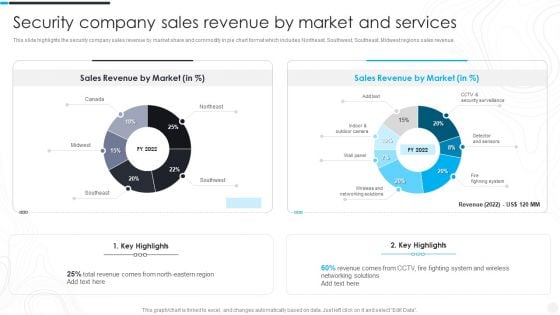
Security Camera System Company Profile Security Company Sales Revenue Template PDF
This slide highlights the security company sales revenue by market share and commodity in pie chart format which includes Northeast, Southwest, Southeast, Midwest regions sales revenue.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Security Company Sales Revenue Template PDF bundle. Topics like Detector And Sensors, Fighning System, Security Surveillance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Type Security Testing Identify Security Vulnerabilities Ppt PowerPoint Presentation Inspiration Themes Cpb
Presenting this set of slides with name type security testing identify security vulnerabilities ppt powerpoint presentation inspiration themes cpb. This is an editable Powerpoint five stages graphic that deals with topics like type security testing identify security vulnerabilities to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
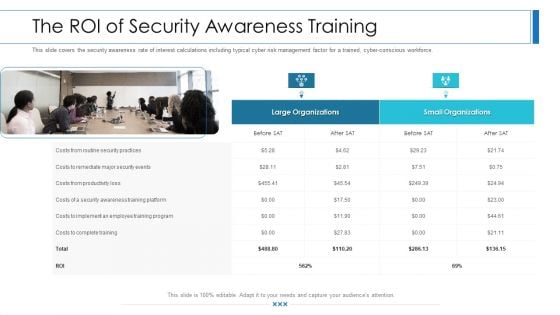
Workforce Security Realization Coaching Plan The ROI Of Security Awareness Training Pictures PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan the roi of security awareness training pictures pdf. Use them to share invaluable insights on security awareness training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
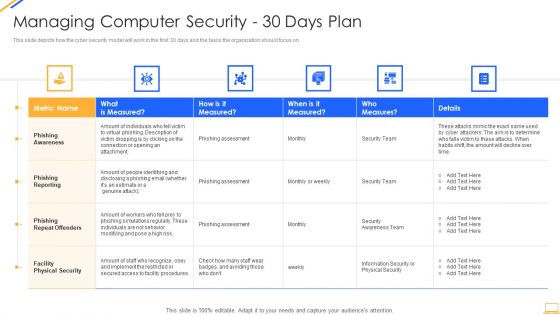
Desktop Security Management Managing Computer Security 30 Days Plan Designs PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative desktop security management managing computer security 30 days plan designs pdf bundle. Topics like awareness, measured, risk, security, team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
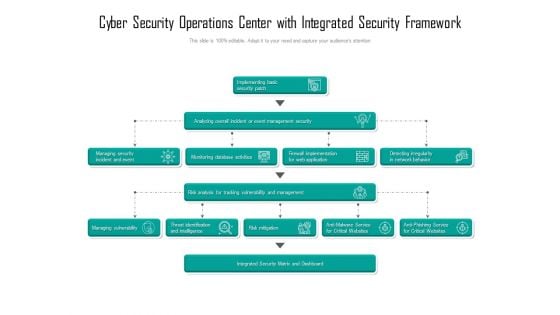
Cyber Security Operations Center With Integrated Security Framework Ppt Gallery Graphics Design PDF
Showcasing this set of slides titled cyber security operations center with integrated security framework ppt gallery graphics design pdf. The topics addressed in these templates are security, framework, management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
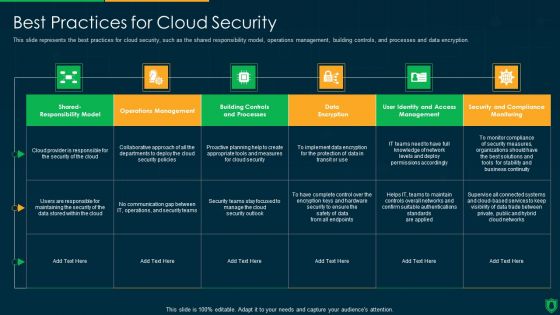
Info Security Best Practices For Cloud Security Ppt PowerPoint Presentation Gallery Visual Aids PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver and pitch your topic in the best possible manner with this info security best practices for cloud security ppt powerpoint presentation gallery visual aids pdf. Use them to share invaluable insights on communication gap, data encryption, operations management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Best Data Security Software Case Study For Company Online Database Security Proposal Template PDF
Presenting this set of slides with name best data security software case study for company online database security proposal template pdf. This is a three stage process. The stages in this process are problem, our solution, results. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
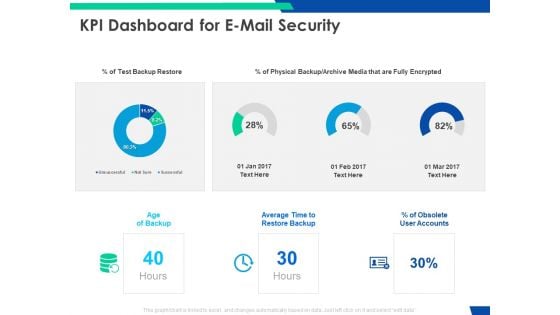
Cloud Based Email Security Market Report KPI Dashboard For E Mail Security Ppt Slides Microsoft PDF
Deliver an awe inspiring pitch with this creative cloud based email security market report kpi dashboard for e mail security ppt slides microsoft pdf bundle. Topics like kpi dashboard for e mail security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
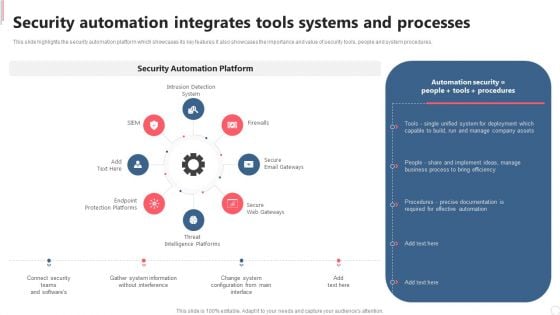
Cyber Security Automation Framework Security Automation Integrates Tools Systems And Processes Formats PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. There are so many reasons you need a Cyber Security Automation Framework Security Automation Integrates Tools Systems And Processes Formats PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
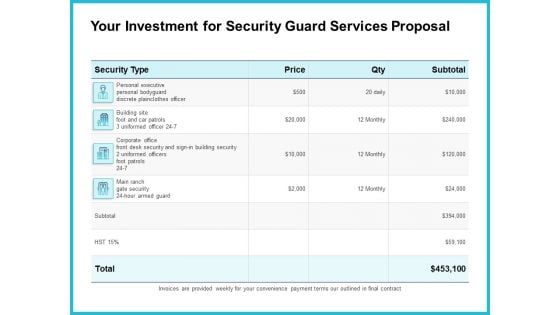
Uniformed Security Your Investment For Security Guard Services Proposal Graphics PDF
Deliver an awe inspiring pitch with this creative uniformed security your investment for security guard services proposal graphics pdf bundle. Topics like executive, security, corporate, price can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
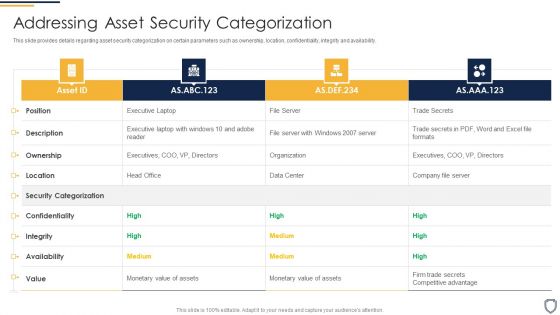
Corporate Security And Risk Management Addressing Asset Security Categorization Guidelines PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Deliver an awe inspiring pitch with this creative corporate security and risk management addressing asset security categorization guidelines pdf bundle. Topics like addressing asset security categorization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Best Data Security Software Project Context And Objectives For Cyber Security Services Pictures PDF
Presenting this set of slides with name best data security software project context and objectives for cyber security services pictures pdf. This is a six stage process. The stages in this process are project context, project objectives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
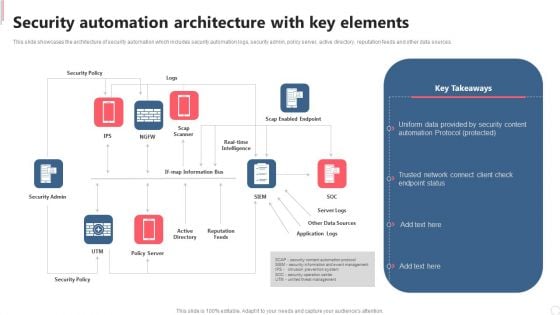
Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. This modern and well arranged Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
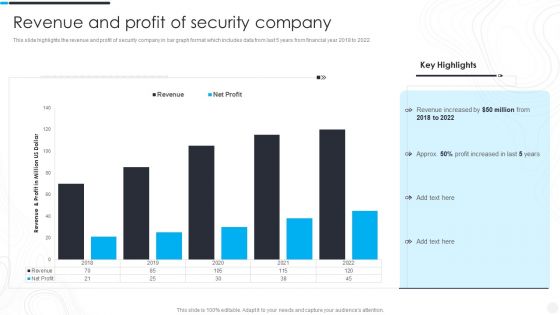
Security Camera System Company Profile Revenue And Profit Of Security Company Clipart PDF
This slide highlights the revenue and profit of security company in bar graph format which includes data from last 5 years from financial year 2018 to 2022.Deliver and pitch your topic in the best possible manner with this Security Camera System Company Profile Revenue And Profit Of Security Company Clipart PDF. Use them to share invaluable insights on Revenue Increased, Profit Increased, Key Highlights and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Best Data Security Software Our Expertise For Company Online Database Security Proposal Formats PDF
Presenting this set of slides with name best data security software our expertise for company online database security proposal formats pdf. This is a three stage process. The stages in this process are mobile app development, onsite developer, business intelligence analytics. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
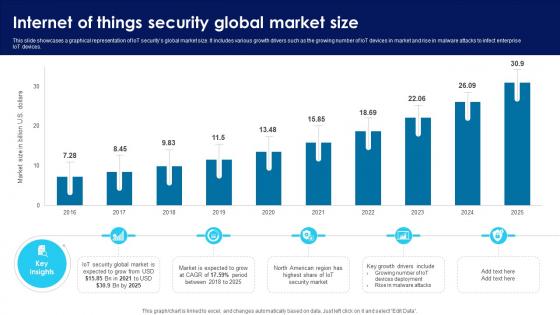
Building Trust With IoT Security Internet Of Things Security Global Market Size IoT SS V
This slide showcases a graphical representation of IoT securitys global market size. It includes various growth drivers such as the growing number of IoT devices in market and rise in malware attacks to infect enterprise IoT devices. This modern and well-arranged Building Trust With IoT Security Internet Of Things Security Global Market Size IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide showcases a graphical representation of IoT securitys global market size. It includes various growth drivers such as the growing number of IoT devices in market and rise in malware attacks to infect enterprise IoT devices.
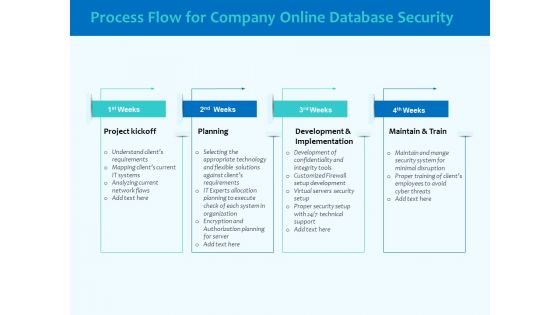
Best Data Security Software Process Flow For Company Online Database Security Elements PDF
Presenting this set of slides with name best data security software process flow for company online database security elements pdf. This is a four stage process. The stages in this process are project kickoff, planning, development and implementation, maintain and train. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Timeframe For Company Online Database Security Proposal Topics PDF
Presenting this set of slides with name best data security software timeframe for company online database security proposal topics pdf. This is a four stage process. The stages in this process are project kickoff, planning, development and implementation, result. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
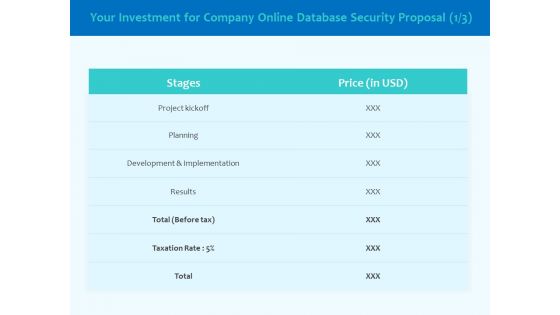
Best Data Security Software Your Investment For Company Online Database Security Proposal Slides PDF
Presenting this set of slides with name best data security software your investment for company online database security proposal slides pdf. The topics discussed in these slides are project kickoff, planning, development and implementation, result. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Smart Home Security Solutions Company Profile Security Company Strategic Partnerships Ideas PDF
This slide highlights the strategic partnership of the security company. It covers the major services such as voice control, mobile security application, and CCTV installation. Deliver and pitch your topic in the best possible manner with this Smart Home Security Solutions Company Profile Security Company Strategic Partnerships Ideas PDF. Use them to share invaluable insights on Mobile Security Application, CCTV Installation Centres, Technology Partner Partnership and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Best Data Security Software Mode Of Communication For Company Online Database Security Proposal Inspiration PDF
Presenting this set of slides with name best data security software mode of communication for company online database security proposal inspiration pdf. The topics discussed in these slides are communicate medium, description. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
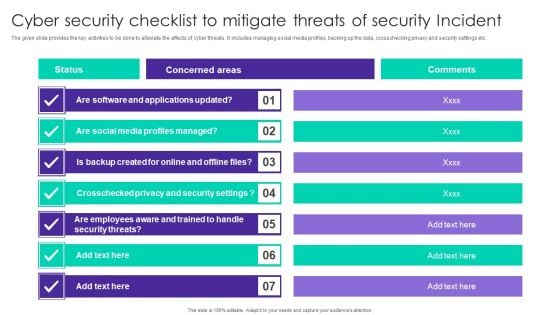
Cyber Security Checklist To Mitigate Threats Of Security Incident Ppt Model Example PDF
The given slide provides the key activities to be done to alleviate the effects of cyber threats. It includes managing social media profiles, backing up the data, crosschecking privacy and security settings etc. Showcasing this set of slides titled Cyber Security Checklist To Mitigate Threats Of Security Incident Ppt Model Example PDF. The topics addressed in these templates are Concerned Areas, Social Media Profiles, Security Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
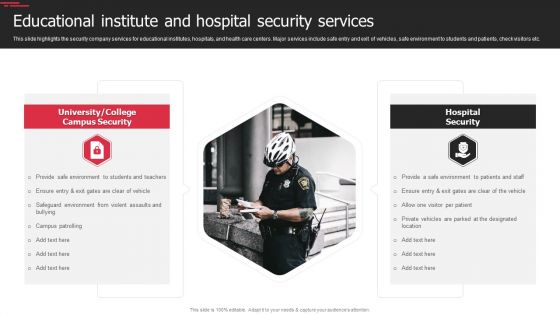
Manpower Corporate Security Business Profile Educational Institute And Hospital Security Services Icons PDF
This slide highlights the security company services for educational institutes, hospitals, and health care centers. Major services include safe entry and exit of vehicles, safe environment to students and patients, check visitors etc. Deliver and pitch your topic in the best possible manner with this Manpower Corporate Security Business Profile Educational Institute And Hospital Security Services Icons PDF. Use them to share invaluable insights on College Campus Security, Hospital Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Agency Business Profile Educational Institute And Hospital Security Services Guidelines PDF
This slide highlights the security company services for educational institutes, hospitals, and health care centers. Major services include safe entry and exit of vehicles, safe environment to students and patients, check visitors etc. Deliver and pitch your topic in the best possible manner with this Security Agency Business Profile Educational Institute And Hospital Security Services Guidelines PDF. Use them to share invaluable insights on Campus Security, Hospital Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
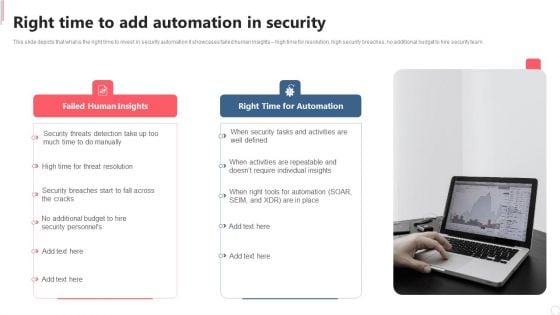
Cyber Security Automation Framework Right Time To Add Automation In Security Microsoft PDF
This slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Want to ace your presentation in front of a live audience Our Cyber Security Automation Framework Right Time To Add Automation In Security Microsoft PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Organizational Network Security Awareness Staff Learning IT Infrastructure Security Budget Slides PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning it infrastructure security budget slides pdf. Use them to share invaluable insights on it infrastructure security budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
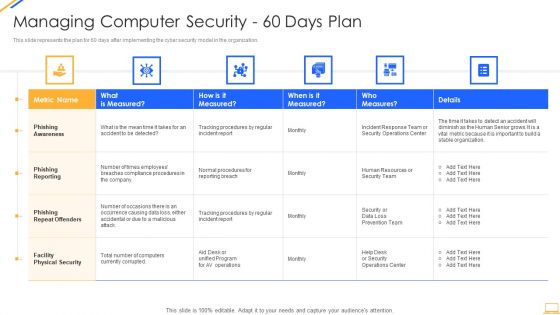
Desktop Security Management Managing Computer Security 60 Days Plan Ideas PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver and pitch your topic in the best possible manner with this desktop security management managing computer security 60 days plan ideas pdf. Use them to share invaluable insights on security, team, organization, awareness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
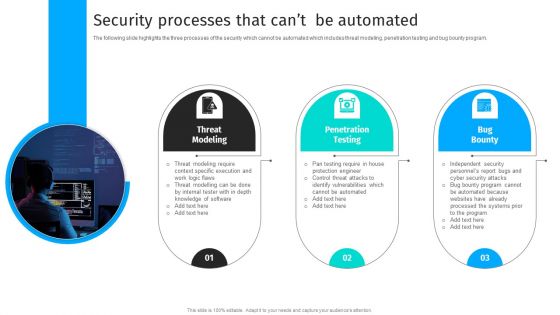
Security Automation To Analyze And Mitigate Cyberthreats Security Processes That Cant Clipart PDF
The following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program.Explore a selection of the finest Security Automation To Analyze And Mitigate Cyberthreats Security Processes That Cant Clipart PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Security Automation To Analyze And Mitigate Cyberthreats Security Processes That Cant Clipart PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
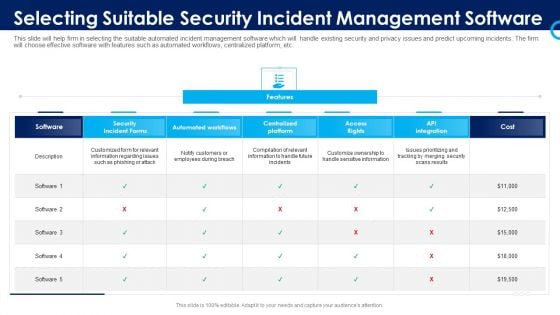
Organizational Security Solutions Selecting Suitable Security Incident Management Software Pictures PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative organizational security solutions selecting suitable security incident management software pictures pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
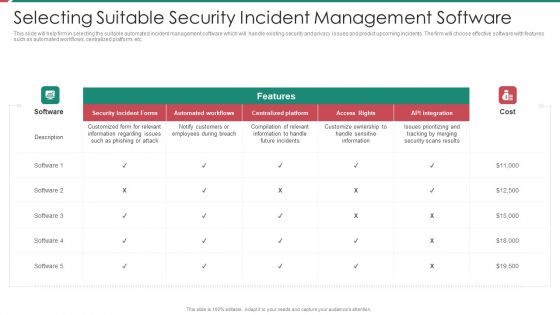
Security And Process Integration Selecting Suitable Security Incident Management Software Brochure PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative security and process integration selecting suitable security incident management software brochure pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
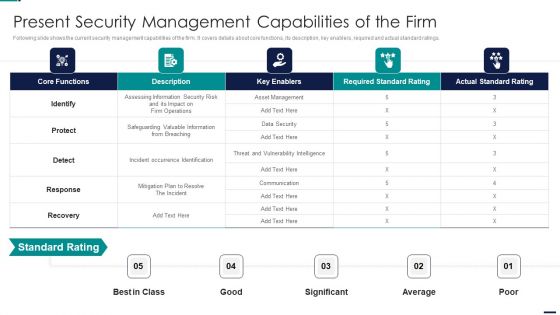
Risk Management Model For Data Security Present Security Management Capabilities Of The Firm Elements PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Present Security Management Capabilities Of The Firm Elements PDF. Use them to share invaluable insights on Core Functions, Key Enablers, Required Standard Rating, Actual Standard Rating and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
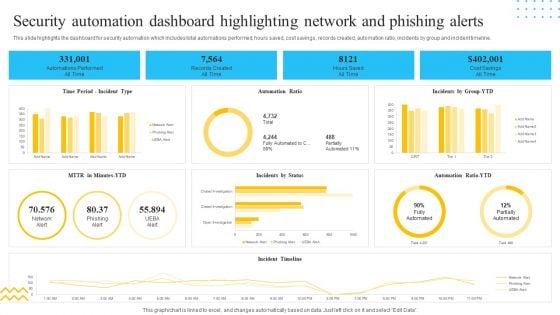
IT Security Automation Tools Integration Security Automation Dashboard Highlighting Network Portrait PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Security Automation Dashboard Highlighting Network Portrait PDF bundle. Topics like Records Created, All Time, Hours Saved, Cost Savings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
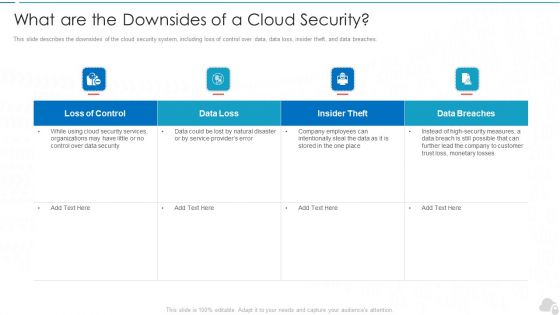
What Are The Downsides Of A Cloud Security Cloud Computing Security IT Ppt Summary Structure PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Deliver and pitch your topic in the best possible manner with this what are the downsides of a cloud security cloud computing security it ppt summary structure pdf. Use them to share invaluable insights on loss of control, data loss, insider theft, data breaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
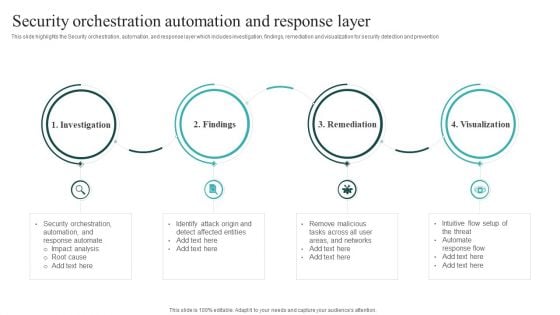
IT Security Automation Systems Guide Security Orchestration Automation And Response Layer Themes PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. Whether you have daily or monthly meetings, a brilliant presentation is necessary. IT Security Automation Systems Guide Security Orchestration Automation And Response Layer Themes PDF can be your best option for delivering a presentation. Represent everything in detail using IT Security Automation Systems Guide Security Orchestration Automation And Response Layer Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
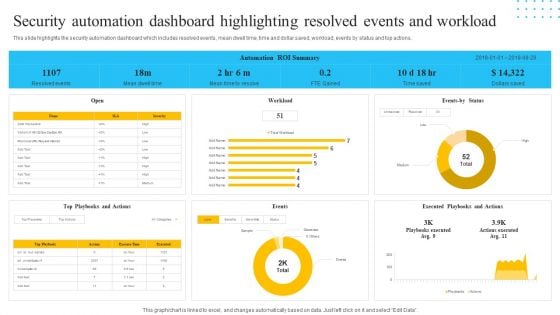
IT Security Automation Tools Integration Security Automation Dashboard Highlighting Resolved Inspiration PDF
This slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Security Automation Dashboard Highlighting Resolved Inspiration PDF bundle. Topics like Events Status, Workload, Events, Open can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
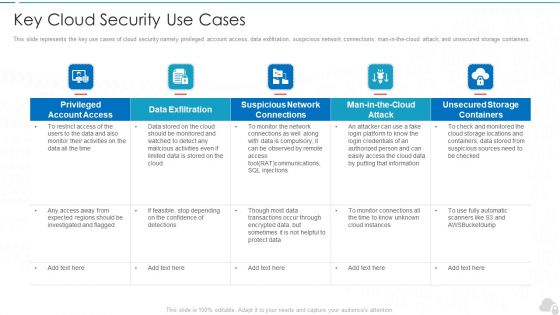
Key Cloud Security Use Cases Cloud Computing Security IT Ppt Visual Aids Ideas PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man-in-the-cloud attack, and unsecured storage containe. Deliver an awe inspiring pitch with this creative key cloud security use cases cloud computing security it ppt visual aids ideas pdf bundle. Topics like privileged account access, data exfiltration, suspicious network connections, man in the cloud attack, unsecured storage containers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
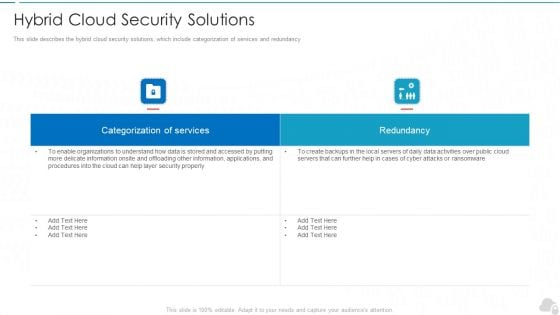
Hybrid Cloud Security Solutions Cloud Computing Security IT Ppt Layouts Slide Portrait PDF
This slide describes the hybrid cloud security solutions, which include categorization of services and redundancy. Deliver an awe inspiring pitch with this creative hybrid cloud security solutions cloud computing security it ppt layouts slide portrait pdf bundle. Topics like categorization of services, redundancy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































