Information Security Program
CYBER Security Breache Response Strategy Cyber Security Incidents Follow Up Report Icons PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. This modern and well arranged CYBER Security Breache Response Strategy Cyber Security Incidents Follow Up Report Icons PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Organizing Security Awareness KPI Dashboard To Monitor Cyber Security Performance Ideas PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. This modern and well-arranged Organizing Security Awareness KPI Dashboard To Monitor Cyber Security Performance Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

CYBER Security Breache Response Strategy Comparative Analysis Of Cyber Security Incident Mitigation Guidelines PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Want to ace your presentation in front of a live audience Our CYBER Security Breache Response Strategy Comparative Analysis Of Cyber Security Incident Mitigation Guidelines PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
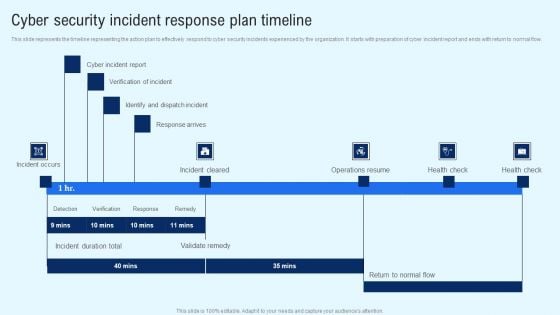
Implementing Cyber Security Incident Cyber Security Incident Response Plan Timeline Download PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Welcome to our selection of the Implementing Cyber Security Incident Cyber Security Incident Response Plan Timeline Download PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

CYBER Security Breache Response Strategy Strategies To Analyze Cyber Security Incidents Inspiration PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Do you know about Slidesgeeks CYBER Security Breache Response Strategy Strategies To Analyze Cyber Security Incidents Inspiration PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
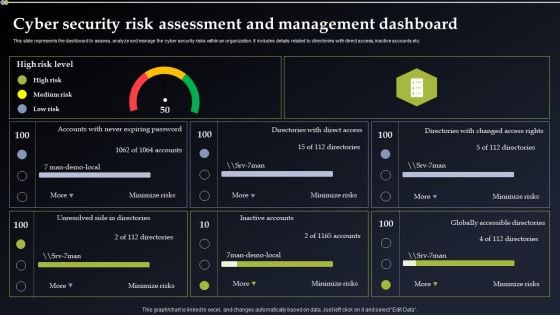
Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment Portrait PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present like a pro with Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment Portrait PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
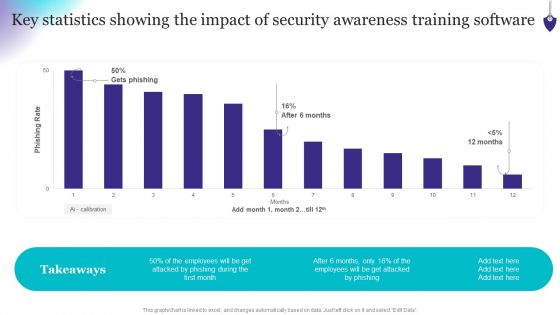
Organizing Security Awareness Key Statistics Showing The Impact Of Security Awareness Clipart PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Organizing Security Awareness Key Statistics Showing The Impact Of Security Awareness Clipart PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
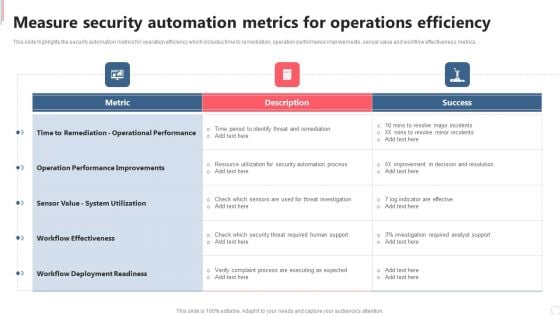
Cyber Security Automation Framework Measure Security Automation Metrics For Operations Efficiency Formats PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Automation Framework Measure Security Automation Metrics For Operations Efficiency Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
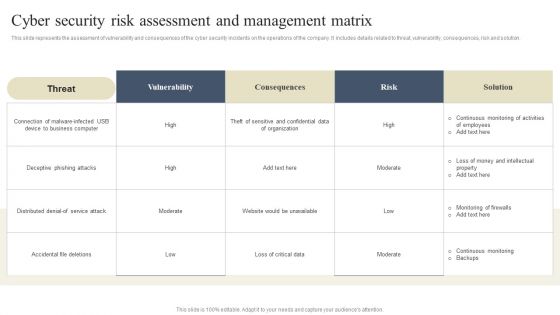
CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Welcome to our selection of the CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
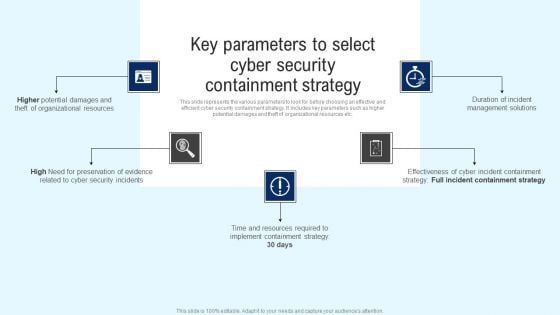
Implementing Cyber Security Incident Key Parameters To Select Cyber Security Containment Formats PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Slidegeeks is here to make your presentations a breeze with Implementing Cyber Security Incident Key Parameters To Select Cyber Security Containment Formats PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
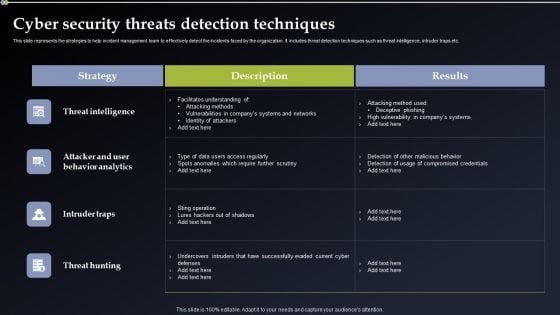
Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Want to ace your presentation in front of a live audience Our Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF from Slidegeeks and deliver a wonderful presentation.
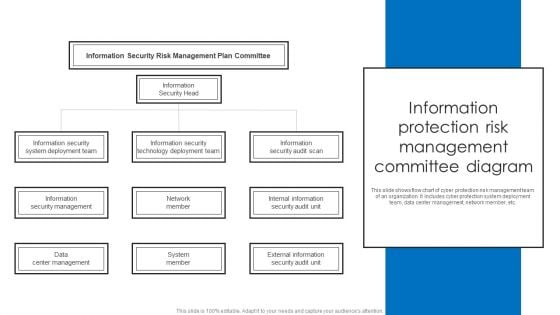
Information Protection Risk Management Committee Diagram Information PDF
This slide shows flow chart of cyber protection risk management team of an organization. It includes cyber protection system deployment team, data center management, network member, etc. Persuade your audience using this Information Protection Risk Management Committee Diagram Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security Head, Information Security Audit Scan, Network Member. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Safety Lock Cyber Security Global Security Ppt PowerPoint Presentation Complete Deck
Boost your confidence and team morale with this well-structured safety lock cyber security global security ppt powerpoint presentation complete deck. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of fourteen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.
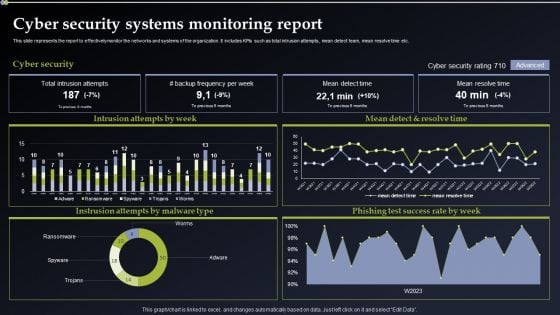
Deploying Cyber Security Incident Response Administration Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Slidegeeks is here to make your presentations a breeze with Deploying Cyber Security Incident Response Administration Cyber Security Systems Monitoring Report Microsoft PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Present like a pro with Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
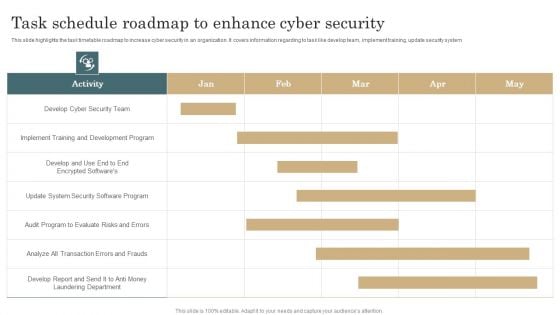
Task Schedule Roadmap To Enhance Cyber Security Template PDF
This slide highlights the task timetable roadmap to increase cyber security in an organization. It covers information regarding to task like develop team, implement training, update security system. Pitch your topic with ease and precision using this Task Schedule Roadmap To Enhance Cyber Security Template PDF. This layout presents information on Development Program, Implement Training, Evaluate Risks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Uniformed Security Proposal For Security Guard Services Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of twenty three slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.
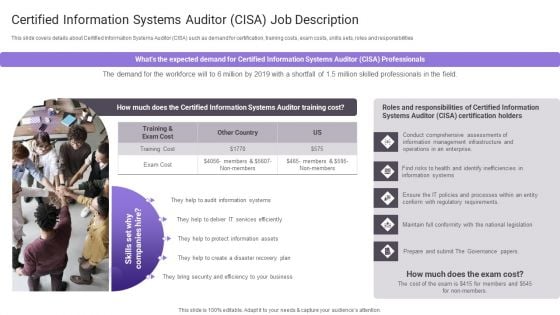
Certified Information Systems Auditor Cisa Job Description Information PDF
This slide covers details about Certified Information Systems Auditor CISA such as demand for certification, training costs, exam costs, skills sets, roles and responsibilities.Deliver an awe inspiring pitch with this creative Certified Information Systems Auditor Cisa Job Description Information PDF bundle. Topics like Certified Information, Security Efficiency, Skilled Professionals can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
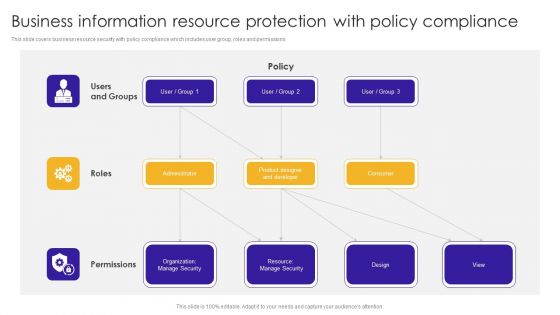
Business Information Resource Protection With Policy Compliance Information PDF
This slide covers business resource security with policy compliance which includes user group, roles and permissions. Showcasing this set of slides titled Business Information Resource Protection With Policy Compliance Information PDF. The topics addressed in these templates are Product Designer, Organization Manage, Resource Manage. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents For Secure Computing Framework Information Pdf
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Table Of Contents For Secure Computing Framework Information Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Our Table Of Contents For Secure Computing Framework Information Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
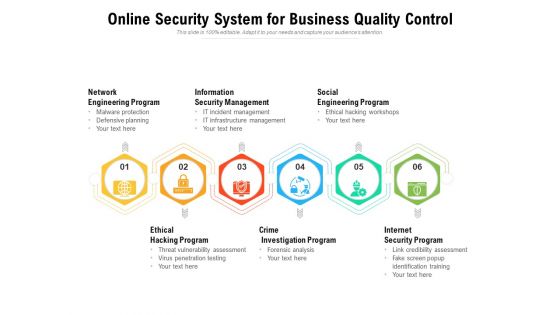
Online Security System For Business Quality Control Ppt PowerPoint Presentation Gallery Templates PDF
Presenting this set of slides with name online security system for business quality control ppt powerpoint presentation gallery templates pdf. This is a six stage process. The stages in this process are network engineering program, information security management, social engineering program, ethical hacking program, crime investigation program, internet security program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Technical Stack For Evaluating Confidential Secure Computing Framework Information Pdf
This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks. Want to ace your presentation in front of a live audience Our Technical Stack For Evaluating Confidential Secure Computing Framework Information Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks.
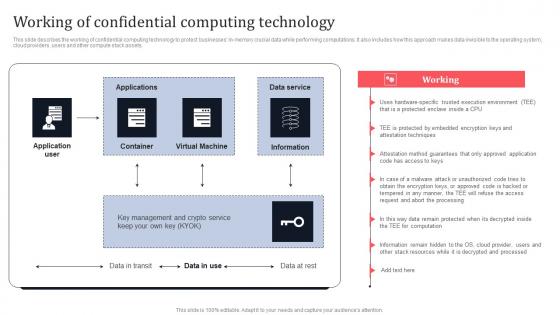
Working Of Confidential Computing Technology Secure Multi Party Information Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Confidential Computing Technology Secure Multi Party Information Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
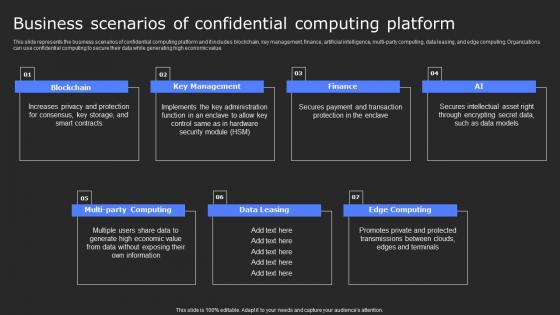
Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. There are so many reasons you need a Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
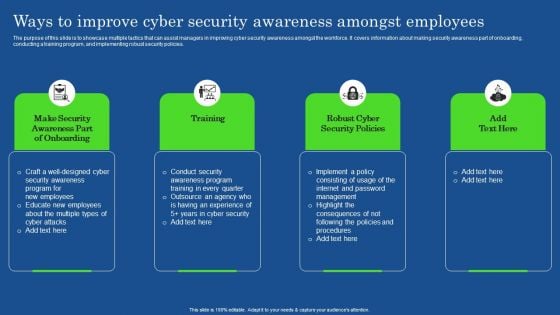
Ways To Improve Cyber Security Awareness Amongst Employees Elements PDF
The purpose of this slide is to showcase multiple tactics that can assist managers in improving cyber security awareness amongst the workforce. It covers information about making security awareness part of onboarding, conducting a training program, and implementing robust security policies. The Ways To Improve Cyber Security Awareness Amongst Employees Elements PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
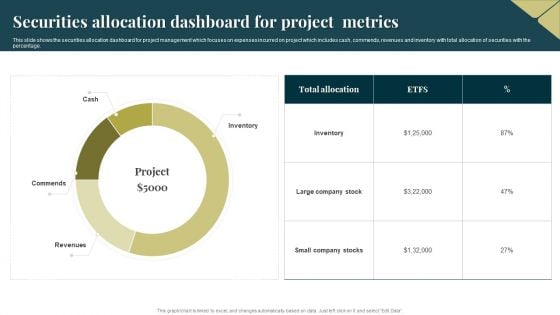
Securities Allocation Dashboard For Project Metrics Information PDF
This slide shows the securities allocation dashboard for project management which focuses on expenses incurred on project which includes cash, commends, revenues and inventory with total allocation of securities with the percentage. Showcasing this set of slides titled Securities Allocation Dashboard For Project Metrics Information PDF. The topics addressed in these templates are Inventory, Project, Revenues. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Information Technology Protection Icon To Reduce Threats Information PDF
Presenting Information Technology Protection Icon To Reduce Threats Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Information Technology Protection Icon, Reduce Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Privacy IT Data Privacy In Financial Institutions Information PDF
This slide represents the data privacy in financial institutions which decreases the possibility of fines and reputational damage as a result of unlawful disclosure. This is a information privacy it data privacy in financial institutions information pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data privacy in financial institutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Steps To Manage Electronic Footprint Information Information PDF
This slide mentions steps for maintaining digital footprint information for individuals. It includes searching name on search engines, having different email address, setting up privacy settings and exercising caution. Persuade your audience using this Steps To Manage Electronic Footprint Information Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Exercise Caution, Social Profiles, Have Different Email Addresses. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
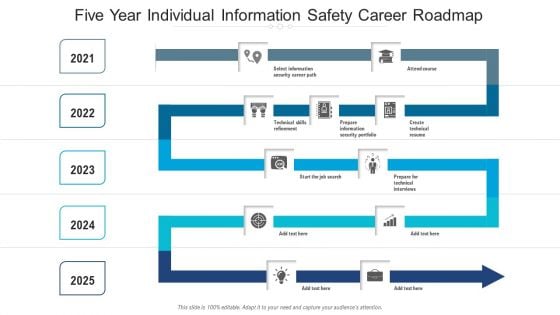
Five Year Individual Information Safety Career Roadmap Information
Presenting our innovatively structured five year individual information safety career roadmap information Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
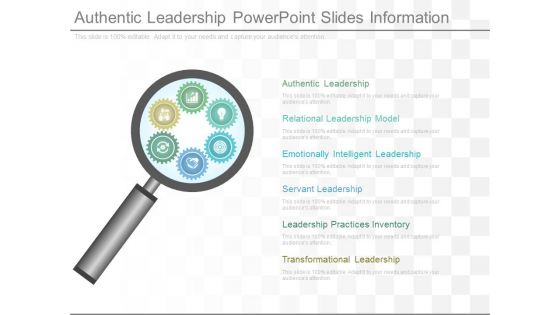
Authentic Leadership Powerpoint Slides Information
This is a authentic leadership powerpoint slides information. This is a six stage process. The stages in this process are authentic leadership, relational leadership model, emotionally intelligent leadership, servant leadership, leadership practices inventory, transformational leadership.

Website Programming IT What Is The Cyber Security Ppt PowerPoint Presentation Gallery Example File PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks. This is a website programming it what is the cyber security ppt powerpoint presentation gallery example file pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect information, digital assets, computers, servers, mobile devices, networks, and resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
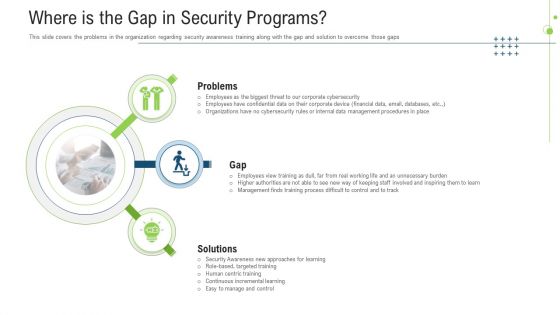
Where Is The Gap In Security Programs Ppt File Examples PDF
This is a where is the gap in security programs ppt file examples pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, gap, solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
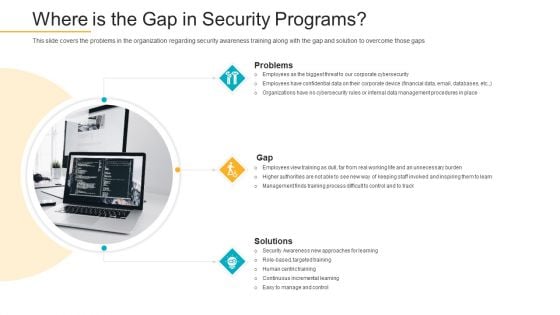
Data Breach Prevention Recognition Where Is The Gap In Security Programs Summary PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a data breach prevention recognition where is the gap in security programs summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, solutions, gap. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Companys Data Safety Recognition Where Is The Gap In Security Programs Infographics PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a companys data safety recognition where is the gap in security programs infographics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, gap, solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Safety Initiatives Employee Upskilling Training Program Portrait PDF
Mentioned slide displays a five-day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. Deliver and pitch your topic in the best possible manner with this data safety initiatives employee upskilling training program portrait pdf. Use them to share invaluable insights on assess security requirements, perform gap analysis, develop gap initiatives, plan transition, communicate and implement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Where Is The Gap In Security Programs Ppt Icon Layout Ideas PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps Presenting where is the gap in security programs ppt icon layout ideas pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like problems, gap, solution. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF
This slide showcases distinguish between bring your own device and choose your own device policies and programs for mobile devices. It also includes differentiation on basis such as benefits , challenges, etc. Pitch your topic with ease and precision using this Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF. This layout presents information on Basis, Benefits, Best Practices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business IT Cyber Security Assessment Framework With Safety Programs Diagrams PDF
This slide outlines the strategic security framework created by an organization to overcome potential external or internal threats along with security programs. Risks include hacking and accidental data disclosure with certain protective programs like anti-spyware software and cloud security. Presenting Business IT Cyber Security Assessment Framework With Safety Programs Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Program, Threats And Risks, Protected Assets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
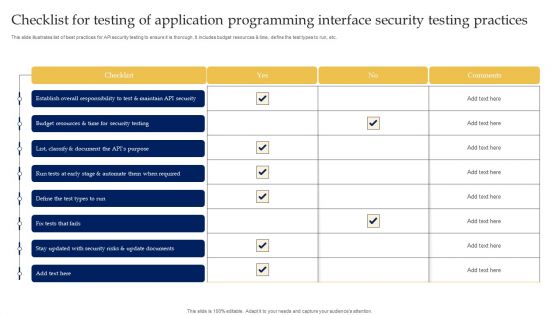
Checklist For Testing Of Application Programming Interface Security Testing Practices Microsoft PDF
This slide illustrates list of best practices for API security testing to ensure it is thorough. It includes budget resources and time, define the test types to run, etc. Showcasing this set of slides titled Checklist For Testing Of Application Programming Interface Security Testing Practices Microsoft PDF. The topics addressed in these templates are Application Programming, Interface Security, Testing Practices. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Agenda Of Data Safety Initiatives For Effective IT Security Threats Administration Professional PDF
This is a agenda of data safety initiatives for effective it security threats administration professional pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security program keeping, threat drivers, cybersecurity attacks resulting, business agility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

4 Steps For Building Internet Security Strategy Clipart Pdf
This slide showcase developing and implementation of cyber security strategy for streamline the data security and organization vision and mission. It includes cyber threat landscape, assess cybersecurity maturity, determine security program and document cybersecurity strategy.Showcasing this set of slides titled 4 Steps For Building Internet Security Strategy Clipart Pdf The topics addressed in these templates are Cyber Security Maturity, Cyber Security Program, Document Cybersecurity Strategy All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase developing and implementation of cyber security strategy for streamline the data security and organization vision and mission. It includes cyber threat landscape, assess cybersecurity maturity, determine security program and document cybersecurity strategy.

Holding A Lock Security PowerPoint Templates And PowerPoint Backgrounds 0711
Microsoft PowerPoint Template and Background with holding a lock security concept File it with our Holding A Lock Security PowerPoint Templates And PowerPoint Backgrounds 0711. Get all the information together.

Data Security Internet PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with internet data security with fiber optical background Our Data Security Internet PowerPoint Templates And PowerPoint Backgrounds 0511 have just about everything. Just think of it and you'll find it in them.

Data Security Internet PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with internet data security with fiber optical Slide Create a flow with our Data Security Internet PowerPoint Themes And PowerPoint Slides 0511. Your thoughts will be coasting along.
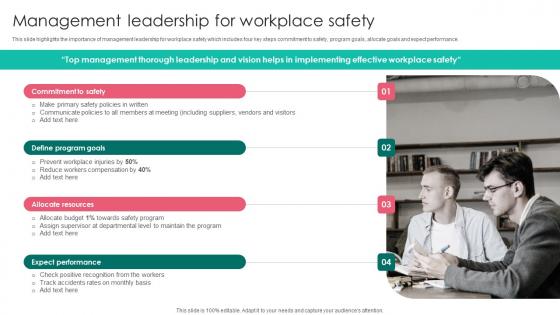
Management Leadership Workplace Safety Protocol And Security Practices Sample Pdf
This slide highlights the importance of management leadership for workplace safety which includes four key steps commitment to safety, program goals, allocate goals and expect performance. The Management Leadership Workplace Safety Protocol And Security Practices Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide highlights the importance of management leadership for workplace safety which includes four key steps commitment to safety, program goals, allocate goals and expect performance.
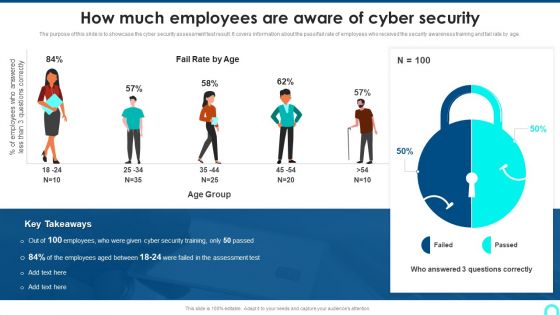
How Much Employees Are Aware Of Cyber Security Introduction PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass fail rate of employees who received the security awareness training and fail rate by age.This is a How Much Employees Are Aware Of Cyber Security Introduction PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Questions Correctly, Employees Answered, Employees Between. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
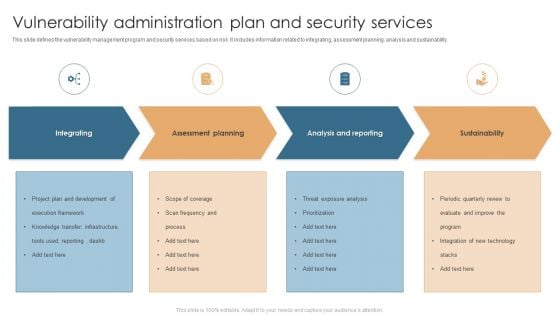
Vulnerability Administration Plan And Security Services Topics PDF
This slide defines the vulnerability management program and security services based on risk. It includes information related to integrating, assessment planning, analysis and sustainability. Persuade your audience using this Vulnerability Administration Plan And Security Services Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Integrating, Assessment Planning, Analysis And Reporting, Sustainability. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Internet Security And Electronic Payment System Ppt Slides
This is a internet security and electronic payment system ppt slides. This is a six stage process. The stages in this process are internet security and electronic payment system, eviction of eco implementation, eco site life cycle, promotion and marketing, net readiness evaluation, eco investment and opportunity.
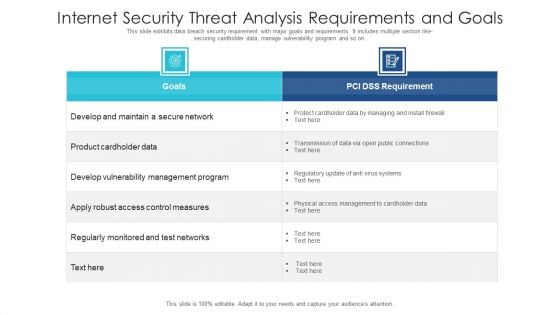
Internet Security Threat Analysis Requirements And Goals Ideas PDF
This slide exhibits data breach security requirement with major goals and requirements. It includes multiple section like- securing cardholder data, manage vulnerability program and so on. Showcasing this set of slides titled internet security threat analysis requirements and goals ideas pdf. The topics addressed in these templates are internet security threat analysis requirements and goals. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Lock Minded Security PowerPoint Templates And PowerPoint Backgrounds 0711
Microsoft PowerPoint Template and Background with security minded digital collage of human profile with key Make your presentations helpful with our Lock Minded Security PowerPoint Templates And PowerPoint Backgrounds 0711. Dont waste time struggling with PowerPoint. Let us do it for you.

Security Of Cloud Storage Ppt PowerPoint Presentation File Deck PDF
This slide depicts cloud storage security by describing the various security measures taken by the company to prevent information from malicious attacks while storing, transferring, and receiving it. Retrieve professionally designed Security Of Cloud Storage Ppt PowerPoint Presentation File Deck PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF. Use them to share invaluable insights on Project Managers, Senior Executives, Security Introduction and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Business Diagram Key With Security Icons Presentation Template
This diagram contains graphics of key with security icons. Download this diagram slide to display concepts of safety and security. This diagram provides an effective way of displaying information you can edit text, color, shade and style as per you need.

Links Of Chain Security PowerPoint Templates And PowerPoint Themes 1012
Links Of Chain Security PowerPoint Templates And PowerPoint Themes 1012-Use this Template to elaborate the concept of security using this chain. Security in one's life is essential whether it Get on the boat with our Links Of Chain Security PowerPoint Templates And PowerPoint Themes 1012. Set sail for the port of success.
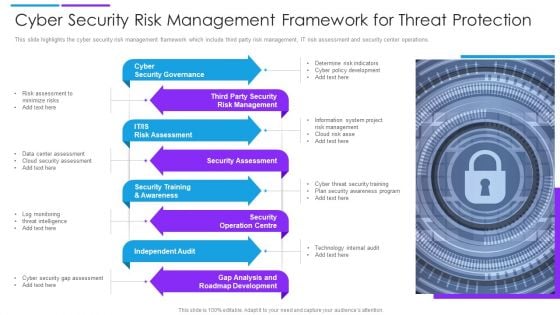
Cyber Security Risk Management Framework For Threat Protection Demonstration PDF
This slide highlights the cyber security risk management framework which include third party risk management, IT risk assessment and security center operations. Presenting cyber security risk management framework for threat protection demonstration pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including cyber security governance, security assessment, independent audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
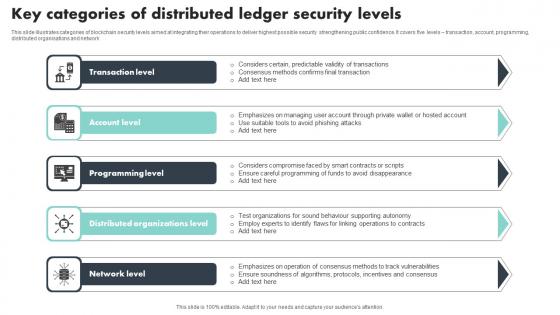
Key Categories Of Distributed Ledger Security Levels Portrait Pdf
This slide illustrates categories of blockchain security levels aimed at integrating their operations to deliver highest possible security strengthening public confidence. It covers five levels transaction, account, programming, distributed organisations and network Pitch your topic with ease and precision using this Key Categories Of Distributed Ledger Security Levels Portrait Pdf This layout presents information on Transaction Level, Account Level, Programming Level It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrates categories of blockchain security levels aimed at integrating their operations to deliver highest possible security strengthening public confidence. It covers five levels transaction, account, programming, distributed organisations and network
Encrypted Business Data Cyber Security Assessment Icon Professional PDF
Presenting Encrypted Business Data Cyber Security Assessment Icon Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
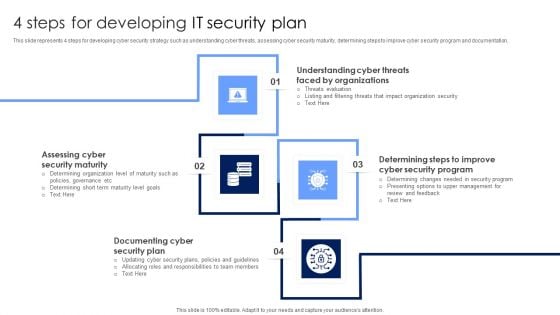
4 Steps For Developing IT Security Plan Professional PDF
This slide represents 4 steps for developing cyber security strategy such as understanding cyber threats, assessing cyber security maturity, determining steps to improve cyber security program and documentation. Presenting 4 Steps For Developing IT Security Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Documenting Cyber Security Plan, Assessing Cyber Security Maturity, Organizations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































