Information Security Program

Integrating AML And Transaction Key Members Of Financial Security Department Slides PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This Integrating AML And Transaction Key Members Of Financial Security Department Slides PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. TheIntegrating AML And Transaction Key Members Of Financial Security Department Slides PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
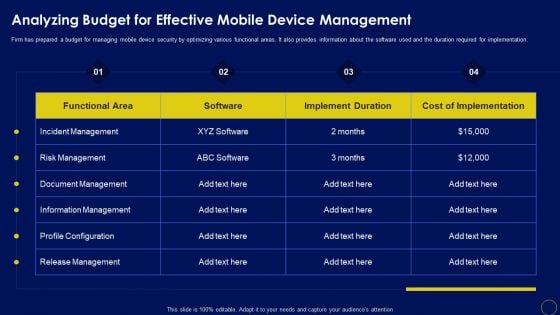
Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF
Firm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Explore a selection of the finest Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF
This slide provides information about enabling online brand protection by tracking incidents per seller, incident per platform and infringements per country. Presenting this PowerPoint presentation, titled Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
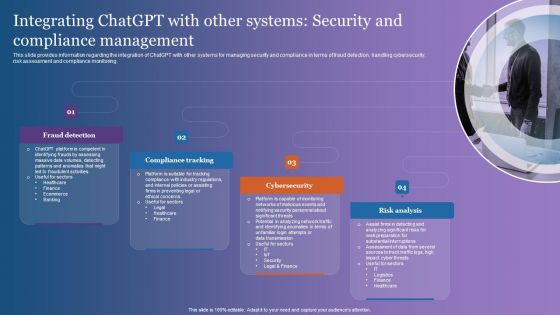
Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF
This slide provides information regarding the integration of ChatGPT with other systems for managing security and compliance in terms of fraud detection, handling cybersecurity, risk assessment and compliance monitoring. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF can be your best option for delivering a presentation. Represent everything in detail using Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Project Security Administration IT Different Modes Of Coordination For Project Management Professional PDF
This slide provides information about different ways by which the firm can coordinate with its partners about project. The coordination can be of electronic mode like through email, etc. Deliver an awe inspiring pitch with this creative project security administration it different modes of coordination for project management professional pdf bundle. Topics like group mode of coordination, individual mode of coordination, electronic mode of coordination, impersonal mode of coordination can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Info Security Define Access Control Measures For Employees Ppt PowerPoint Presentation Gallery Icon PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Presenting info security define access control measures for employees ppt powerpoint presentation gallery icon pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like access data, personnel according, duties or roles, organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
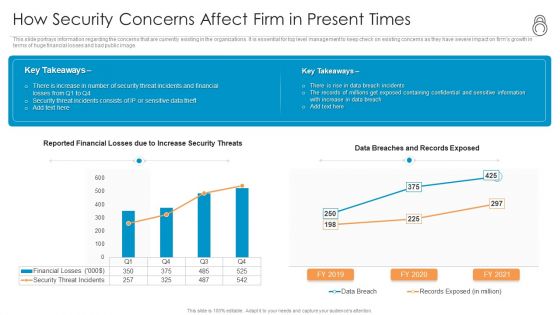
Enhanced Protection Corporate Event Administration How Security Concerns Affect Firm In Present Times Inspiration PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration how security concerns affect firm in present times inspiration pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
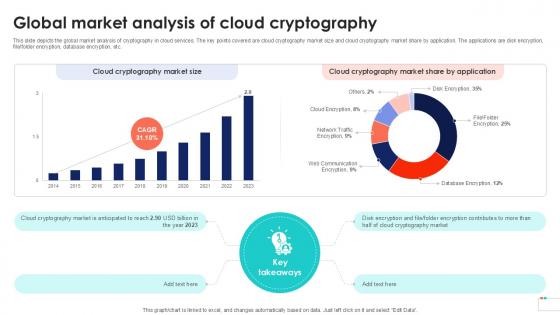
Global Market Analysis Of Cloud Data Security In Cloud Computing Ppt Powerpoint
This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file, folder encryption, database encryption, etc. Are you searching for a Global Market Analysis Of Cloud Data Security In Cloud Computing Ppt Powerpoint that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Global Market Analysis Of Cloud Data Security In Cloud Computing Ppt Powerpoint from Slidegeeks today. This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file, folder encryption, database encryption, etc.
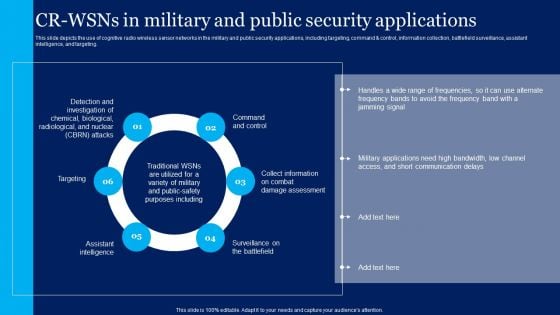
Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
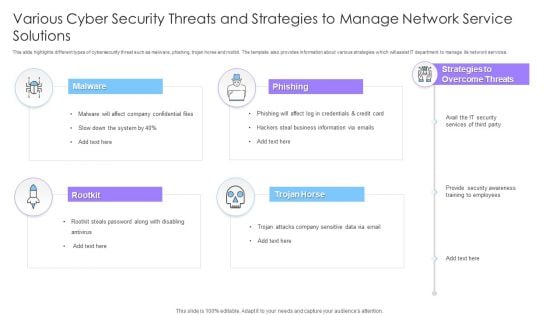
Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF
This slide highlights different types of cybersecurity threat such as malware, phishing, trojan horse and rootkit. The template also provides information about various strategies which will assist IT department to manage its network services. Persuade your audience using this Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Malware, Phishing, Rootkit, Trojan Horse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
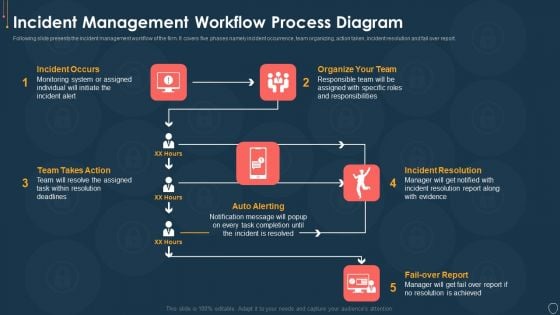
Cyber Security Risk Management Plan Incident Management Workflow Process Diagram Infographics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting cyber security risk management plan incident management workflow process diagram infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like fail over report, incident resolution, organize your team, incident occurs, team takes action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
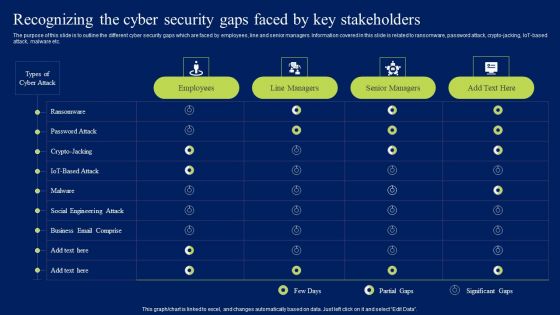
Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Get a simple yet stunning designed Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
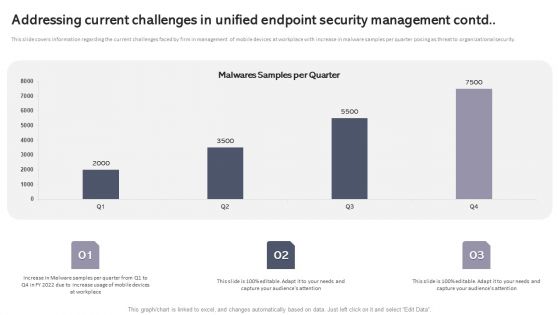
Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with increase in malware samples per quarter posing as threat to organizational security. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF.
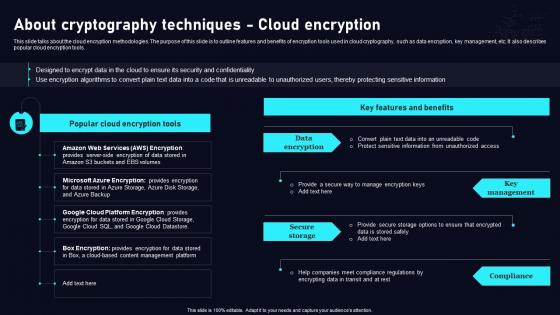
Cloud Data Security Using Cryptography About Cryptography Techniques Cloud Download Pdf
This slide talks about the cloud encryption methodologies. The purpose of this slide is to outline features and benefits of encryption tools used in cloud cryptography, such as data encryption, key management, etc. It also describes popular cloud encryption tools. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cloud Data Security Using Cryptography About Cryptography Techniques Cloud Download Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cloud Data Security Using Cryptography About Cryptography Techniques Cloud Download Pdf This slide talks about the cloud encryption methodologies. The purpose of this slide is to outline features and benefits of encryption tools used in cloud cryptography, such as data encryption, key management, etc. It also describes popular cloud encryption tools.
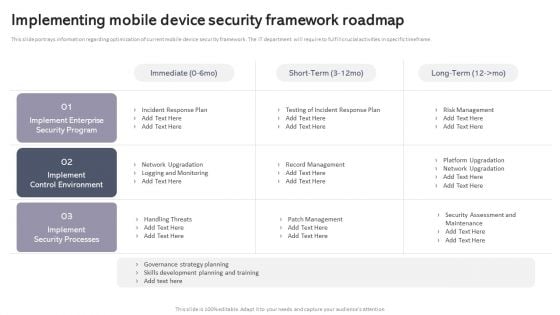
Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Explore a selection of the finest Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
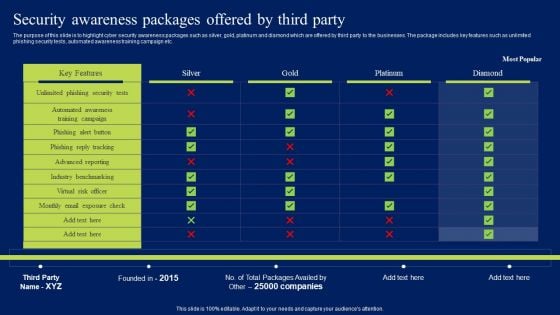
Security Awareness Packages Offered By Third Party Ppt Layouts Topics PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. This Security Awareness Packages Offered By Third Party Ppt Layouts Topics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
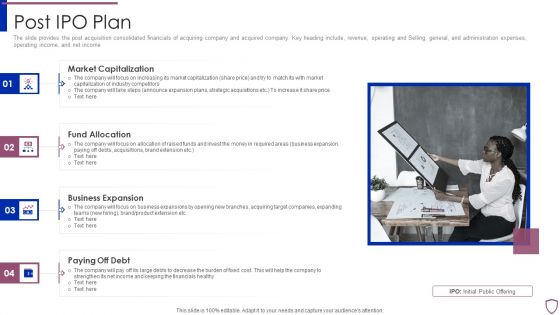
Financing Catalogue For Security Underwriting Agreement Post IPO Plan Inspiration PDF
The slide provides the post acquisition consolidated financials of acquiring company and acquired company. Key heading include, revenue, operating and Selling, general, and administration expenses, operating income, and net income. Presenting financing catalogue for security underwriting agreement post ipo plan inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like market capitalization, fund allocation, business expansion, paying off debt. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
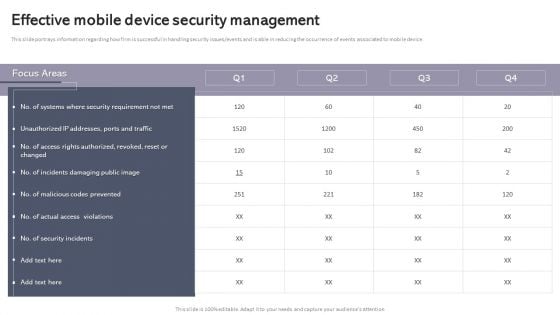
Workplace Portable Device Monitoring And Administration Effective Mobile Device Security Management Pictures PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. This Workplace Portable Device Monitoring And Administration Effective Mobile Device Security Management Pictures PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Workplace Portable Device Monitoring And Administration Effective Mobile Device Security Management Pictures PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
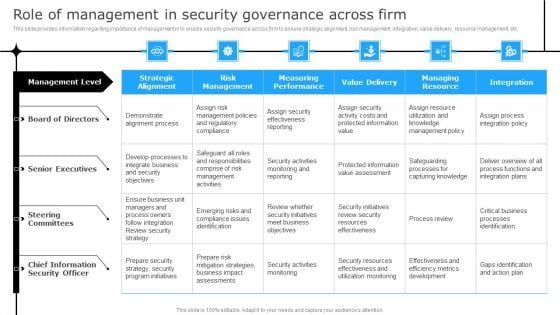
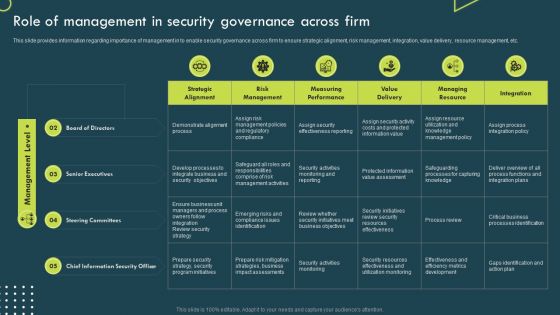
Successful Corporate Technique Enhancing Firms Performance Role Of Management In Security Governance Across Firm Background PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Get a simple yet stunning designed Successful Corporate Technique Enhancing Firms Performance Role Of Management In Security Governance Across Firm Background PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Successful Corporate Technique Enhancing Firms Performance Role Of Management In Security Governance Across Firm Background PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
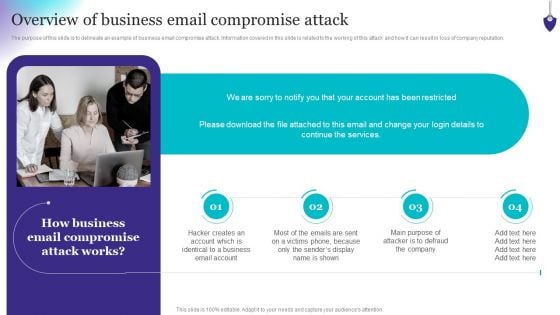
Organizing Security Awareness Overview Of Business Email Compromise Attack Portrait PDF
The purpose of this slide is to delineate an example of business email compromise attack. Information covered in this slide is related to the working of this attack and how it can result in loss of company reputation. Presenting this PowerPoint presentation, titled Organizing Security Awareness Overview Of Business Email Compromise Attack Portrait PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Organizing Security Awareness Overview Of Business Email Compromise Attack Portrait PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Organizing Security Awareness Overview Of Business Email Compromise Attack Portrait PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
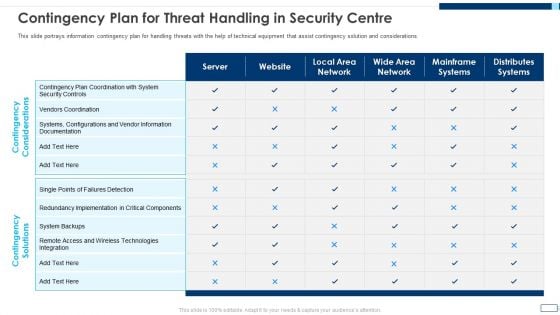
Evolving BI Infrastructure Contingency Plan For Threat Handling In Security Centre Pictures PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver and pitch your topic in the best possible manner with this evolving bi infrastructure contingency plan for threat handling in security centre pictures pdf. Use them to share invaluable insights on server, website, local area network, wide area network, mainframe systems, distributes systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents Security And Human Resource Services Business Profile Slides PDF
This Table Of Contents Security And Human Resource Services Business Profile Slides PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Table Of Contents Global Security Industry Report PPT Sample IR SS V
Presenting this PowerPoint presentation, titled Table Of Contents Global Security Industry Report PPT Sample IR SS V, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Table Of Contents Global Security Industry Report PPT Sample IR SS V. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Table Of Contents Global Security Industry Report PPT Sample IR SS V that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. Our Table Of Contents Global Security Industry Report PPT Sample IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
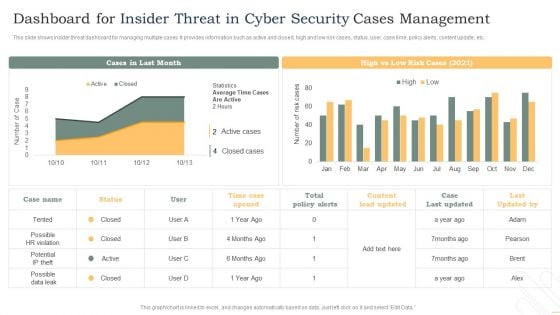
Dashboard For Insider Threat In Cyber Security Cases Management Background PDF
This slide shows insider threat dashboard for managing multiple cases. It provides information such as active and closed, high and low risk cases, status, user, case time, policy alerts, content update, etc. Showcasing this set of slides titled Dashboard For Insider Threat In Cyber Security Cases Management Background PDF. The topics addressed in these templates are Total Policy Alerts, High, Low, Time Case Opened. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
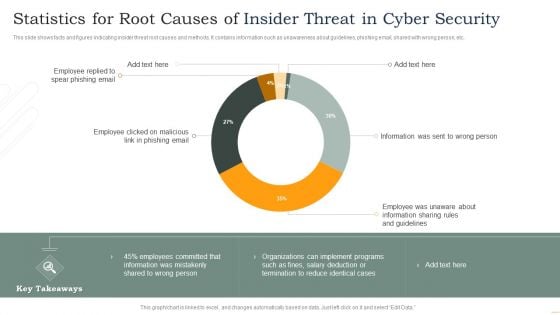
Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF
This slide shows facts and figures indicating insider threat root causes and methods. It contains information such as unawareness about guidelines, phishing email, shared with wrong person, etc. Showcasing this set of slides titled Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF. The topics addressed in these templates are Employee Replied, Spear Phishing Email, Employee Clicked, Phishing Email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Strategic Corporate Planning To Attain Role Of Management In Security Governance Across Firm Guidelines PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Strategic Corporate Planning To Attain Role Of Management In Security Governance Across Firm Guidelines PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Strategic Corporate Planning To Attain Role Of Management In Security Governance Across Firm Guidelines PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
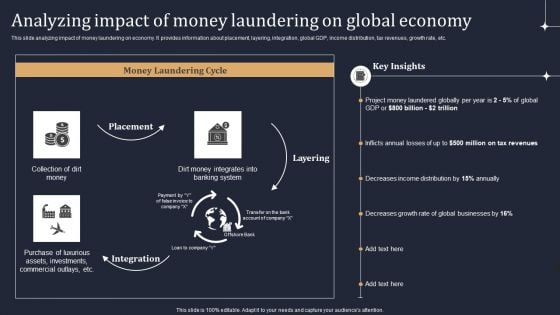
KYC Transaction Monitoring System Business Security Analyzing Impact Of Money Laundering Guidelines PDF
This slide analyzing impact of money laundering on economy. It provides information about placement, layering, integration, global GDP, income distribution, tax revenues, growth rate, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable KYC Transaction Monitoring System Business Security Analyzing Impact Of Money Laundering Guidelines PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Formulating Money Laundering Key Members Of Financial Security Department Structure PDF
This Formulating Money Laundering Key Members Of Financial Security Department Structure PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
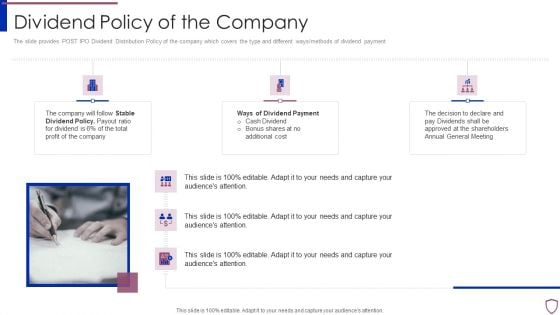
Financing Catalogue For Security Underwriting Agreement Dividend Policy Of The Company Elements PDF
The slide provides POST IPO Dividend Distribution Policy of the company which covers the type and different ways or methods of dividend payment. Presenting financing catalogue for security underwriting agreement dividend policy of the company elements pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like stable dividend policy, ways of dividend payment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
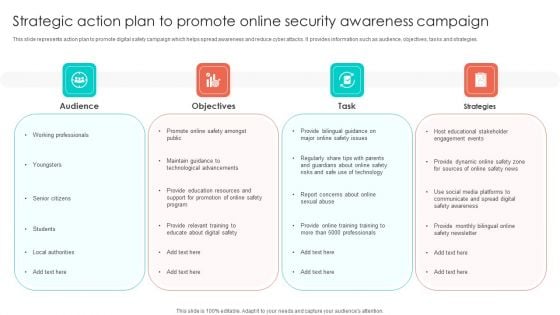
Strategic Action Plan To Promote Online Security Awareness Campaign Portrait PDF
This slide represents action plan to promote digital safety campaign which helps spread awareness and reduce cyber attacks. It provides information such as audience, objectives, tasks and strategies. Persuade your audience using this Strategic Action Plan To Promote Online Security Awareness Campaign Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Objectives, Task, Strategies, Audience. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
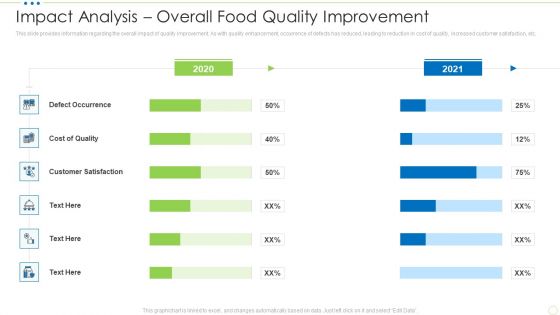
Impact Analysis Overall Food Quality Improvement Food Security Excellence Ppt Gallery Graphics Template PDF
This slide provides information regarding the overall impact of quality improvement. As with quality enhancement, occurrence of defects has reduced, leading to reduction in cost of quality, increased customer satisfaction, etc. Deliver an awe inspiring pitch with this creative impact analysis overall food quality improvement food security excellence ppt gallery graphics template pdf bundle. Topics like cost, customer satisfaction, defect occurrence can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
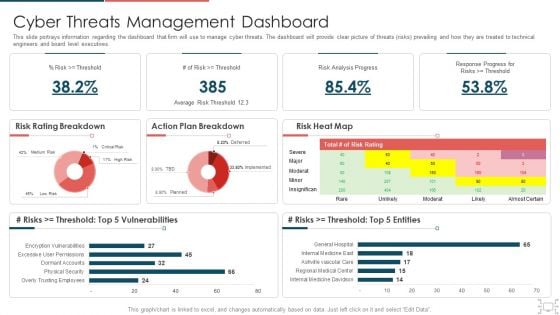
Cyber Security Administration In Organization Cyber Threats Management Dashboard Formats PDF
This slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver an awe inspiring pitch with this creative cyber security administration in organization cyber threats management dashboard formats pdf bundle. Topics like cyber threats management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Cyber Threats Management Dashboard Ideas PDF
This slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver and pitch your topic in the best possible manner with this corporate security and risk management cyber threats management dashboard ideas pdf. Use them to share invaluable insights on cyber threats management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
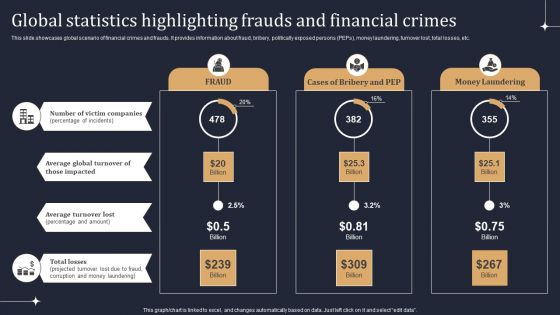
KYC Transaction Monitoring System Business Security Global Statistics Highlighting Frauds Diagrams PDF
This slide showcases global scenario of financial crimes and frauds. It provides information about fraud, bribery, politically exposed persons PEPs, money laundering, turnover lost, total losses, etc. Take your projects to the next level with our ultimate collection of KYC Transaction Monitoring System Business Security Global Statistics Highlighting Frauds Diagrams PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
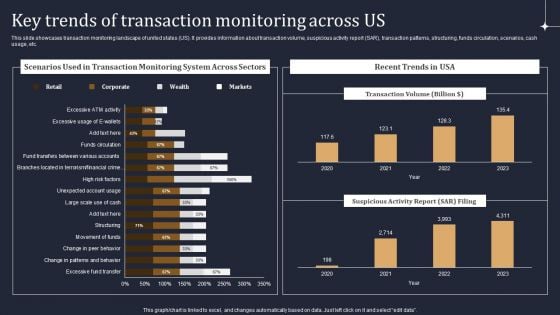
KYC Transaction Monitoring System Business Security Key Trends Of Transaction Monitoring Across Us Diagrams PDF
This slide showcases transaction monitoring landscape of united states US. It provides information about transaction volume, suspicious activity report SAR, transaction patterns, structuring, funds circulation, scenarios, cash usage, etc. There are so many reasons you need a KYC Transaction Monitoring System Business Security Key Trends Of Transaction Monitoring Across Us Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
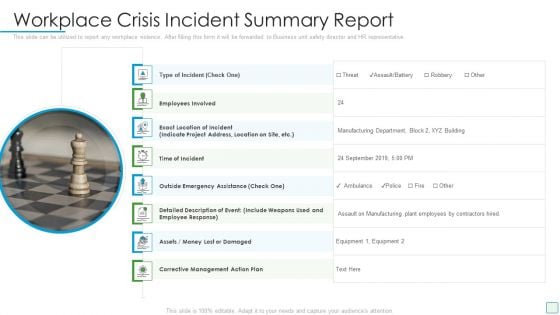
Developing Firm Security Strategy Plan Workplace Crisis Incident Summary Report Professional PDF
This slide can be utilized to report any workplace violence. After filling this form it will be forwarded to Business unit safety director and HR representative. Presenting developing firm security strategy plan workplace crisis incident summary report professional pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like management action plan, time of incident, employees involved, outside emergency assistance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Assets Security Management Strategy Addressing Risk Response Plan For Firms Demonstration PDF
This slide provides information regarding risk response plan for firms in terms of employee safety, development of cross functional team, ensuring liquidity and developing contingency plan, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Organizational Assets Security Management Strategy Addressing Risk Response Plan For Firms Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cyber Security Risk Management Plan Threat Identification And Vulnerability Impact Assessment Brochure PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat identification and vulnerability impact assessment brochure pdf. Use them to share invaluable insights on threat agent, affected assets, potential vulnerability, vulnerability ranking, threats to firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Global Data Security Industry Report Covid 19 Impact Assessment On Cybersecurity Industry IR SS V
The slide represents a comprehensive analysis of the covid-19 impact on the cybersecurity industry The purpose is to understand how the pandemic has shaped cybersecurity adoption and the significance of adapting cybersecurity technologies responsibly amidst global challenges. It covers both positive and negative impacts. Get a simple yet stunning designed Global Data Security Industry Report Covid 19 Impact Assessment On Cybersecurity Industry IR SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Global Data Security Industry Report Covid 19 Impact Assessment On Cybersecurity Industry IR SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The slide represents a comprehensive analysis of the covid-19 impact on the cybersecurity industry The purpose is to understand how the pandemic has shaped cybersecurity adoption and the significance of adapting cybersecurity technologies responsibly amidst global challenges. It covers both positive and negative impacts.

Security And Performance Digital Marketing Create Content Strategy That Resonates With Targets Clipart PDF
This template covers account based marketing strategy such as create content that provide value to the customers. It also depicts that Different types of target accounts require additional content focuses.Presenting Security And Performance Digital Marketing Create Content Strategy That Resonates With Targets Clipart PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Competitors Customers, Strategic Importance, Different. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
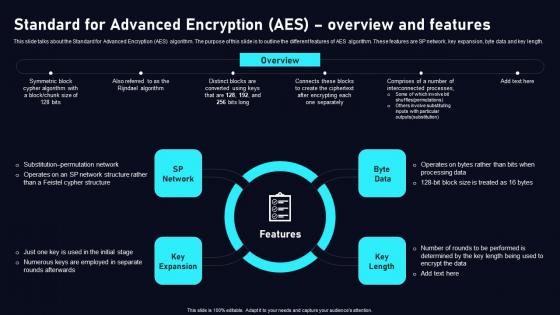
Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf
This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf can be your best option for delivering a presentation. Represent everything in detail using Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length.
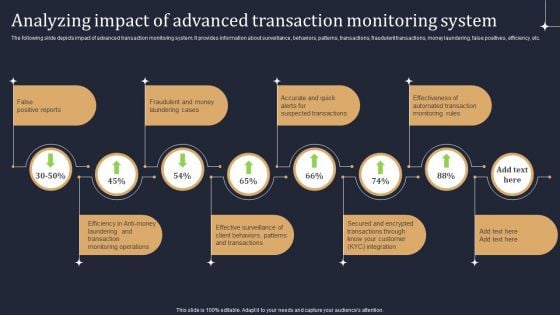
KYC Transaction Monitoring System Business Security Analyzing Impact Of Advanced Transaction Guidelines PDF
The following slide depicts impact of advanced transaction monitoring system. It provides information about surveillance, behaviors, patterns, transactions, fraudulent transactions, money laundering, false positives, efficiency, etc. Boost your pitch with our creative KYC Transaction Monitoring System Business Security Analyzing Impact Of Advanced Transaction Guidelines PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cyber Security Administration In Organization Evaluating Financial Practices In Firm Rules PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Presenting cyber security administration in organization evaluating financial practices in firm rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like evaluating financial practices in firm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
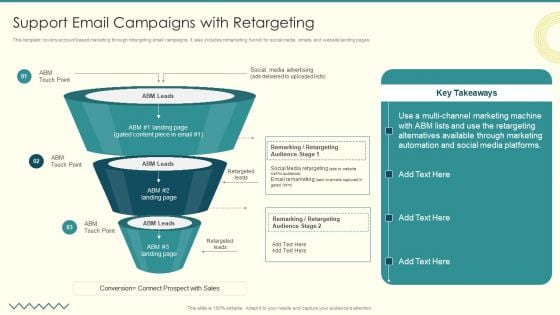
Security And Performance Digital Marketing Support Email Campaigns With Retargeting Elements PDF
This template covers account based marketing through retargeting email campaigns. It also includes remarketing funnel for social media, emails and website landing pages.Presenting Security And Performance Digital Marketing Support Email Campaigns With Retargeting Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Alternatives Available, Remarking Retargeting, Media Advertising. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Data Security Industry Report Comprehensive Swot Analysis For Cybersecurity Industry IR SS V
The slide covers the cybersecurity industrys strengths, weaknesses, opportunities, and threats. The slide aims to identify internal and external factors impacting the industrys functioning. It will help stakeholders to develop strategies to achieve their objectives and improve efficiency. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Global Data Security Industry Report Comprehensive Swot Analysis For Cybersecurity Industry IR SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Global Data Security Industry Report Comprehensive Swot Analysis For Cybersecurity Industry IR SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The slide covers the cybersecurity industrys strengths, weaknesses, opportunities, and threats. The slide aims to identify internal and external factors impacting the industrys functioning. It will help stakeholders to develop strategies to achieve their objectives and improve efficiency.

Financing Catalogue For Security Underwriting Agreement Major Investment Banking Deals In Last Summary PDF
The slide provides the top five deals by profit amount of the company in last five years. It comprises, year, client name, deal type and brief information about all the five deals. Deliver an awe inspiring pitch with this creative financing catalogue for security underwriting agreement major investment banking deals in last summary pdf bundle. Topics like automobile, financials services, healthcare, construction can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
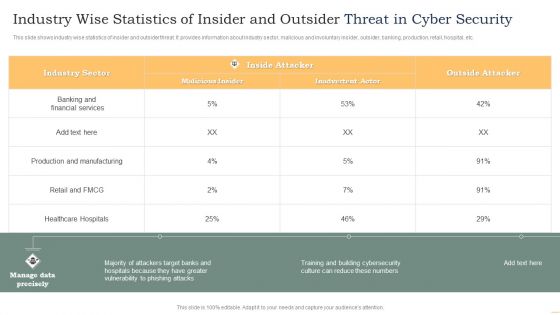
Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF
This slide shows industry wise statistics of insider and outsider threat. It provides information about industry sector, malicious and involuntary insider, outsider, banking, production, retail, hospital, etc. Showcasing this set of slides titled Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF. The topics addressed in these templates are Industry Sector, Malicious Insider, Inside Attacker. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
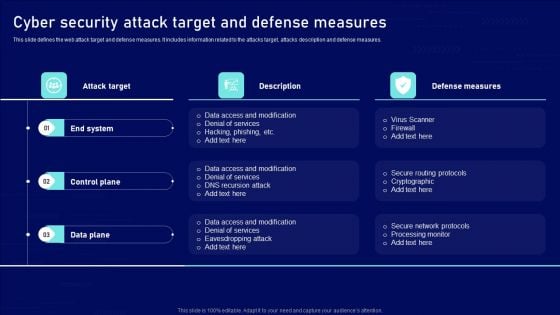
Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF
This slide defines the web attack target and defense measures. It includes information related to the attacks target, attacks description and defense measures. Showcasing this set of slides titled Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF. The topics addressed in these templates are Attack Target, Defense Measures, End System, Control Plane. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
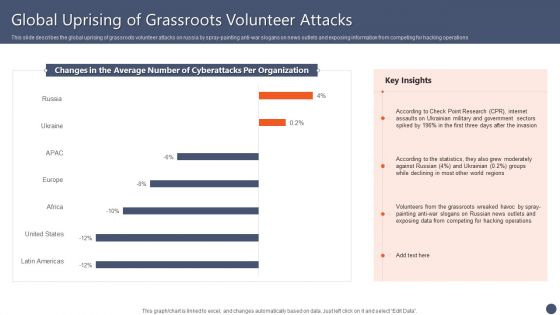
Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF
This slide describes the global uprising of grassroots volunteer attacks on russia by spray-painting anti-war slogans on news outlets and exposing information from competing for hacking operations. Boost your pitch with our creative Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
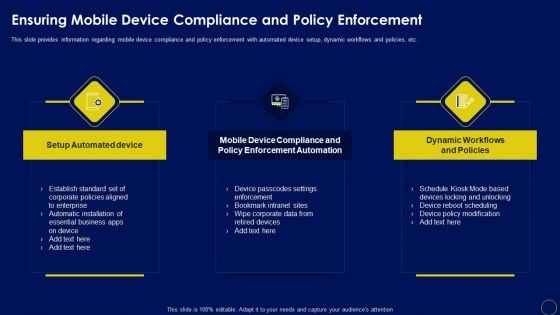
Ensuring Mobile Device Compliance And Policy Enforcement Business Mobile Device Security Formats PDF
This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc.Want to ace your presentation in front of a live audience Our Ensuring Mobile Device Compliance And Policy Enforcement Business Mobile Device Security Formats PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
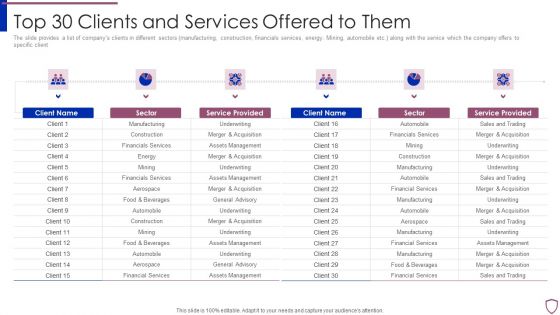
Financing Catalogue For Security Underwriting Agreement Top 30 Clients And Services Offered Structure PDF
The slide provides a list of companys clients in different sectors manufacturing, construction, financials services, energy. Mining, automobile etc. along with the service which the company offers to specific client. Presenting financing catalogue for security underwriting agreement top 30 clients and services offered structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like manufacturing, financials services, construction, automobile. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
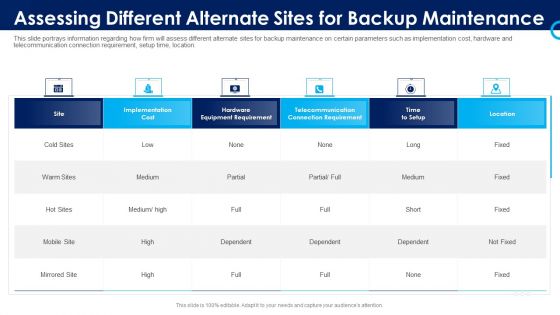
Organizational Security Solutions Assessing Different Alternate Sites For Backup Maintenance Infographics PDF
This slide portrays information regarding how firm will assess different alternate sites for backup maintenance on certain parameters such as implementation cost, hardware and telecommunication connection requirement, setup time, location. Deliver and pitch your topic in the best possible manner with this organizational security solutions assessing different alternate sites for backup maintenance infographics pdf. Use them to share invaluable insights on implementation, cost, location, telecommunication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Functioning Centre Assessing Different Alternate Sites For Backup Maintenance Icons PDF
This slide portrays information regarding how firm will assess different alternate sites for backup maintenance on certain parameters such as implementation cost, hardware and telecommunication connection requirement, setup time, location. Deliver and pitch your topic in the best possible manner with this security functioning centre assessing different alternate sites for backup maintenance icons pdf. Use them to share invaluable insights on telecommunication, location, equipment requirement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Process Integration Analysing Various Threats Faced By Firm Download PDF
This slide portrays information regarding the various threats that are faced by firm at present times with their cause of threat, risks associated to threats, occurrence of threats, and monetary loss to firm. Deliver an awe inspiring pitch with this creative security and process integration analysing various threats faced by firm download pdf bundle. Topics like threats, negligent, occurrence, compromised, malicious can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
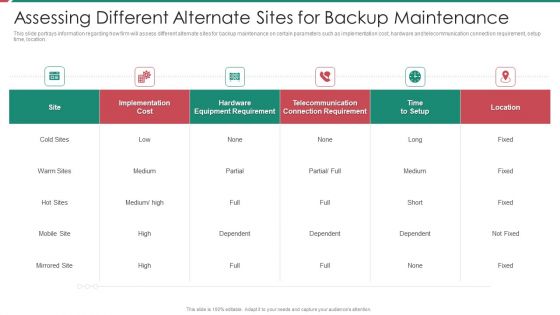
Security And Process Integration Assessing Different Alternate Sites For Backup Maintenance Formats PDF
This slide portrays information regarding how firm will assess different alternate sites for backup maintenance on certain parameters such as implementation cost, hardware and telecommunication connection requirement, setup time, location. Deliver and pitch your topic in the best possible manner with this security and process integration assessing different alternate sites for backup maintenance formats pdf. Use them to share invaluable insights on implementation, cost, location, telecommunication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Addressing Hazard Analysis In Different Focus Areas Contd Food Security Excellence Ppt Inspiration Example PDF
This slide provides information regarding addressing hazard analysis in different focus areas such as sanitation, intended use, storage scenario, employee health and hygiene, etc. Deliver and pitch your topic in the best possible manner with this addressing hazard analysis in different focus areas contd food security excellence ppt inspiration example pdf. Use them to share invaluable insights on hygiene and education, sanitation, storage scenario, intended use, intended consumer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Addressing Various Food Processing System Food Security Excellence Ppt Infographic Template Templates PDF
This slide provides information regarding various food handling and processing systems such as drying and curing, fermentation, etc. on various parameters such as longer shelf life, micro organism inactivation, etc. Deliver an awe inspiring pitch with this creative addressing various food processing system food security excellence ppt infographic template templates pdf bundle. Topics like mechanical handling, extrudation, irradiation, fermentation, organisms inactivation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Financing Catalogue For Security Underwriting Agreement IPO Deal Overview Key Points Background PDF
The slide provides the overview of IPO deals. It cover the points such as Application Date, Issue Price, of shares, Amount to be raised, key reasons behind the IPO issue etc. Presenting financing catalogue for security underwriting agreement ipo deal overview key points background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like industry overview, reason behind ipo issue. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
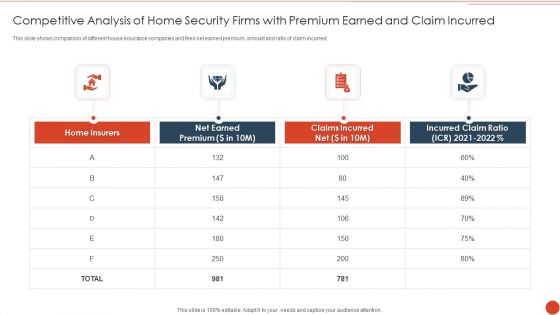
Competitive Analysis Of Home Security Firms With Premium Earned And Claim Incurred Microsoft PDF
This slide shows comparison of different house insurance companies and their net earned premium, amount and ratio of claim incurred. Pitch your topic with ease and precision using this Competitive Analysis Of Home Security Firms With Premium Earned And Claim Incurred Microsoft PDF. This layout presents information on Incurred Claim Ratio, Claims Incurred Net, Net Earned Premium. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
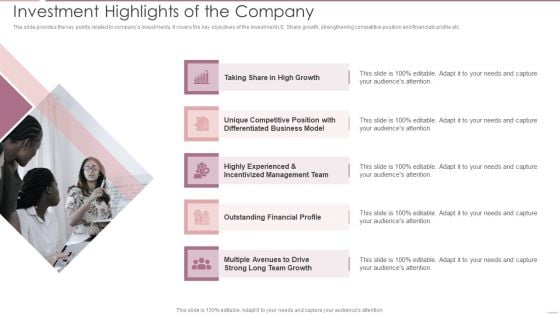
Investment Banking Security Underwriting Pitchbook Investment Highlights Of The Company Elements PDF
The slide provides the key points related to companys investments. It covers the key objectives of the investment i.E. Share growth, strengthening competitive position and financials profile etc.Presenting Investment Banking Security Underwriting Pitchbook Investment Highlights Of The Company Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Unique Competitive, Differentiated Business, Incentivized Management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































