Information Security Program
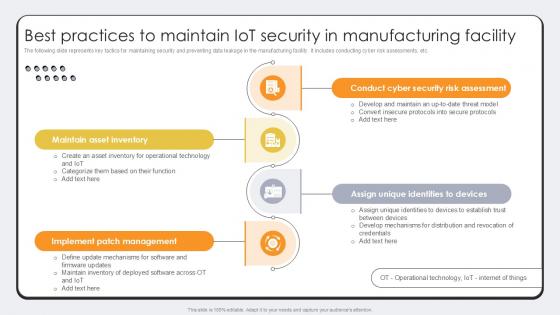
Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. There are so many reasons you need a Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc.

Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is here to make your presentations a breeze with Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Slidegeeks has constructed PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Table Of Contents For Workplace Safety Protocol And Security Practices Professional Pdf
There are so many reasons you need a Table Of Contents For Workplace Safety Protocol And Security Practices Professional Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Our Table Of Contents For Workplace Safety Protocol And Security Practices Professional Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF
This slide showcases timeline to introduce transaction monitoring system. It provides information about scenario planning, threshold setting, deployment, project management office PMO, project planning, scenario identification, data source identification, etc. Get a simple yet stunning designed KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
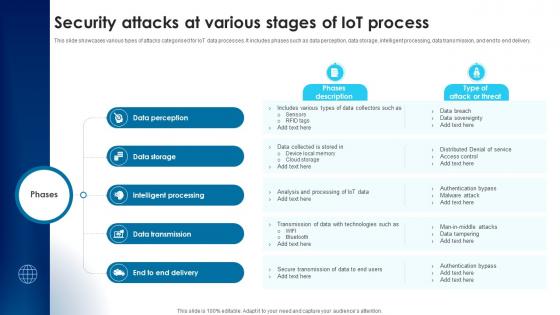
Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V
This slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery. Create an editable Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery.
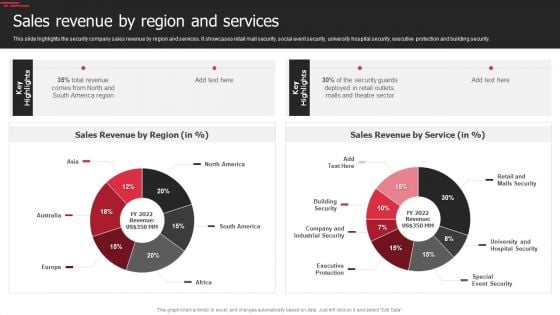
Security Agency Business Profile Sales Revenue By Region And Services Slides PDF
This slide highlights the security company sales revenue by region and services. It showcases retail mall security, social event security, university hospital security, executive protection and building security. Deliver and pitch your topic in the best possible manner with this Security Agency Business Profile Sales Revenue By Region And Services Slides PDF. Use them to share invaluable insights on Revenue, Security, Executive Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
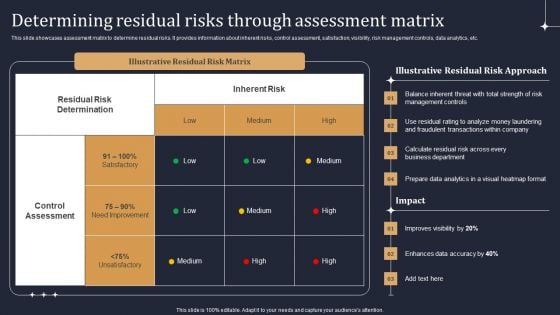
KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF
This slide showcases assessment matrix to determine residual risks. It provides information about inherent risks, control assessment, satisfaction, visibility, risk management controls, data analytics, etc. Explore a selection of the finest KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
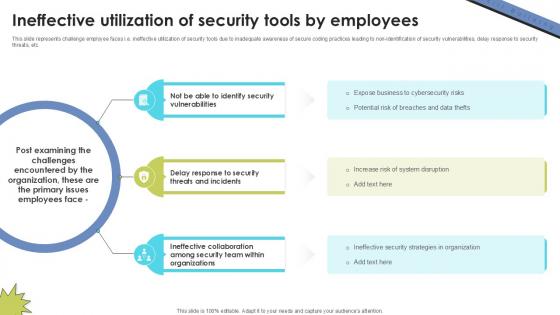
Ineffective Utilization Of Security Skill Building Plan For Application PPT Presentation DTE SS V
This slide represents challenge employee faces i.e. ineffective utilization of security tools due to inadequate awareness of secure coding practices leading to non-identification of security vulnerabilities, delay response to security threats, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Ineffective Utilization Of Security Skill Building Plan For Application PPT Presentation DTE SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents challenge employee faces i.e. ineffective utilization of security tools due to inadequate awareness of secure coding practices leading to non-identification of security vulnerabilities, delay response to security threats, etc.
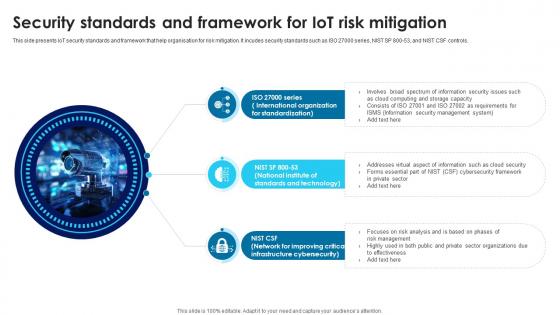
Building Trust With IoT Security Standards And Framework For IoT Risk Mitigation IoT SS V
This side presents IoT security standards and framework that help organisation for risk mitigation. It incudes security standards such as ISO 27000 series, NIST SP 800-53, and NIST CSF controls. Present like a pro with Building Trust With IoT Security Standards And Framework For IoT Risk Mitigation IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This side presents IoT security standards and framework that help organisation for risk mitigation. It incudes security standards such as ISO 27000 series, NIST SP 800-53, and NIST CSF controls.

Deploying AML Transaction Monitoring Key Members Of Financial Security Department Ideas PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. Welcome to our selection of the Deploying AML Transaction Monitoring Key Members Of Financial Security Department Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
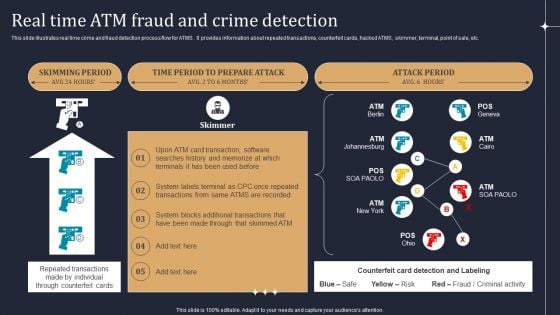
KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
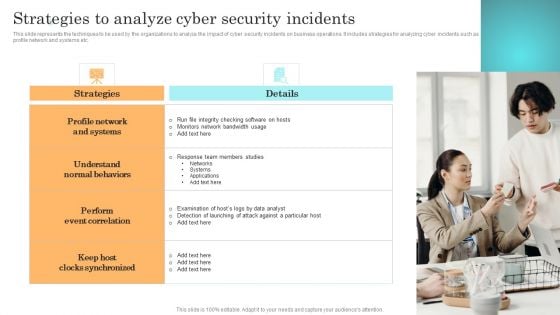
Incident Response Techniques Deployement Strategies To Analyze Cyber Security Incidents Sample PDF

KYC Transaction Monitoring System Business Security Identifying Inherent Risk Factors And Measures Portrait PDF
This slide showcases identifying inherent risk factors and measures. It provides information about customer base, products, services, delivery channels, jurisdictions, qualitative factors, location, customer risk rating, transparency, fund transfer, etc. Create an editable KYC Transaction Monitoring System Business Security Identifying Inherent Risk Factors And Measures Portrait PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. KYC Transaction Monitoring System Business Security Identifying Inherent Risk Factors And Measures Portrait PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
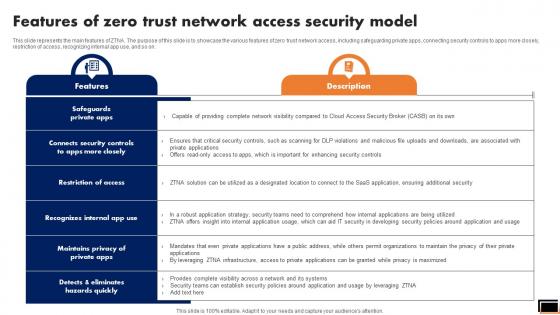
Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.
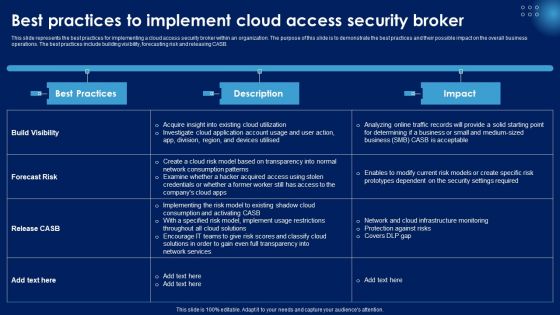
Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. This Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Various CSR Initiatives Taken Global Security Industry PPT Presentation IR SS V
The slide highlights csr initiatives taken in Defense sector. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes financial education and literacy, supporting vulnerable communities, disaster relief and preparedness. This Various CSR Initiatives Taken Global Security Industry PPT Presentation IR SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The slide highlights csr initiatives taken in Defense sector. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes financial education and literacy, supporting vulnerable communities, disaster relief and preparedness.

Organizational Assets Security Management Strategy How To Handle Financial Crisis At Workplace Formats PDF
This slide covers information regarding how firm can handle financial crisis by safeguarding financial stability in terms of abundant cash requirements, overhead analysis, currency hedging, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Organizational Assets Security Management Strategy How To Handle Financial Crisis At Workplace Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Organizational Assets Security Management Strategy How To Handle Financial Crisis At Workplace Formats PDF today and make your presentation stand out from the rest.
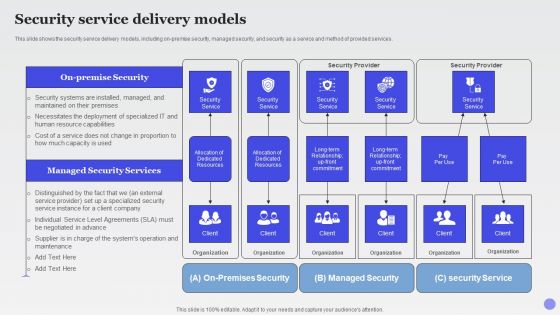
Security Service Delivery Models Xaas Cloud Computing Models Ppt PowerPoint Presentation Infographic Template Graphics PDF
This slide shows the security service delivery models, including on premise security, managed security, and security as a service and method of provided services.Deliver an awe inspiring pitch with this creative Security Service Delivery Models Xaas Cloud Computing Models Ppt PowerPoint Presentation Infographic Template Graphics PDF bundle. Topics like Dedicated Resources, Security Service, Managed Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF
This slide showcases risks identified during transaction monitoring. It provides information about anti money laundering fines, staff productivity, motivation, organizational profitability, compliance, fees, false positive, workload, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
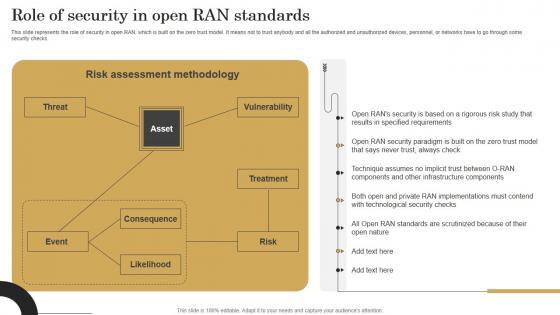
Role Of Security In Open Ran Standards Revolutionizing Mobile Networks Ideas PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Role Of Security In Open Ran Standards Revolutionizing Mobile Networks Ideas PDF from Slidegeeks and deliver a wonderful presentation. This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks.

Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V
The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks. Slidegeeks is here to make your presentations a breeze with Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks.

Cyber Security Business Threats Landscape With Potential Outcomes Ppt Outline Ideas PDF
This slide showcases cyber security risk landscape which can benefit various users around the world to be proactive of potential outcomes. It includes information about target, purpose, possible outcome, social media phishing, system viruses, configuration and passcodes, allocated service denial, hacking devices and structured query language. Persuade your audience using this Cyber Security Business Threats Landscape With Potential Outcomes Ppt Outline Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Landscape, Target, Purpose, Possible Outcome. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Roles And Responsibilities Of Digitization Of Security Systems Team Graphics PDF
The following slide highlights key responsibilities of the digitization of security systems team with the position level and requirements. The various positions mentioned in the slide are security engineer, senior security engineer, distinguished security engineer and digitization of security systems manager. Showcasing this set of slides titled Roles And Responsibilities Of Digitization Of Security Systems Team Graphics PDF. The topics addressed in these templates are Security Engineer, Senior Security Engineer, Security Automation Manager. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
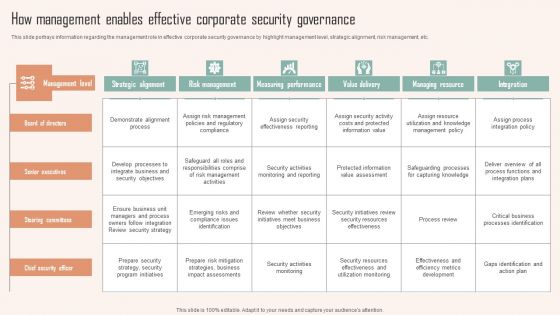
How Management Enables Effective Corporate Security Governance Ppt PowerPoint Presentation File Pictures PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download How Management Enables Effective Corporate Security Governance Ppt PowerPoint Presentation File Pictures PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Building Trust With IoT Security Essential Data Privacy Regulations For Ensuring Connected Devices IoT SS V
This slide exhibits personal data handling regulations for organisations across various regions. It includes data regulations such as general data protection regulation, the California consumer privacy act, and personal data protection act in Singapore. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Building Trust With IoT Security Essential Data Privacy Regulations For Ensuring Connected Devices IoT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Building Trust With IoT Security Essential Data Privacy Regulations For Ensuring Connected Devices IoT SS V. This slide exhibits personal data handling regulations for organisations across various regions. It includes data regulations such as general data protection regulation, the California consumer privacy act, and personal data protection act in Singapore.

KYC Transaction Monitoring System Business Security Cryptocurrency Transaction Monitoring Guidelines PDF
This slide showcases cryptocurrency transaction monitoring with alert status. It provides information about address, risk level, currencies, bitcoin, Ethereum, date added, deposits, case status, alerts, deposits, darknet, etc. This KYC Transaction Monitoring System Business Security Cryptocurrency Transaction Monitoring Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The KYC Transaction Monitoring System Business Security Cryptocurrency Transaction Monitoring Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Retrieve professionally designed Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Strategies To Develop Effective Cyber Security Plan Ppt Powerpoint Presentation File Icon Pdf
This slide represents the techniques to be adopted by administration to effectively manage cyber security incidents in order to reduce their impact on business operations. It includes strategies to develop cyber security plan such as establish IR team, conduct threat analysis etc. The Strategies To Develop Effective Cyber Security Plan Ppt Powerpoint Presentation File Icon Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the techniques to be adopted by administration to effectively manage cyber security incidents in order to reduce their impact on business operations. It includes strategies to develop cyber security plan such as establish IR team, conduct threat analysis etc.
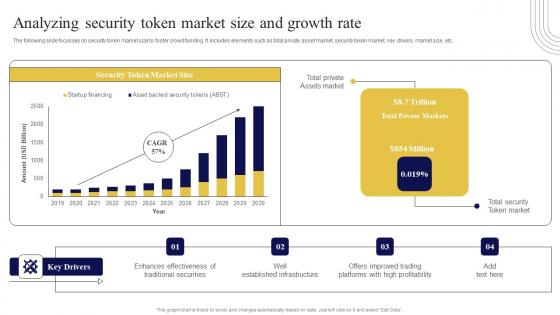
Analyzing Security Token Market Size And Exploring Investment Opportunities Structure Pdf
The following slide focusses on security token market size to foster crowd funding. It includes elements such as total private asset market, security token market, key drivers, market size, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Analyzing Security Token Market Size And Exploring Investment Opportunities Structure Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide focusses on security token market size to foster crowd funding. It includes elements such as total private asset market, security token market, key drivers, market size, etc.

Optimization Of IoT Remote Monitoring Smart Locks Used To Increase Safety And Security IoT SS V
This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings. This Optimization Of IoT Remote Monitoring Smart Locks Used To Increase Safety And Security IoT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings.
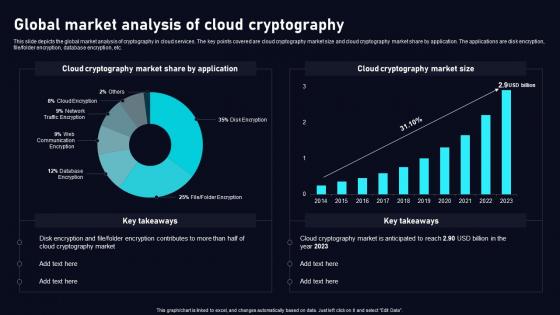
Global Market Analysis Of Cloud Data Security Using Cryptography Portrait Pdf
This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file folder encryption, database encryption, etc. Do you know about Slidesgeeks Global Market Analysis Of Cloud Data Security Using Cryptography Portrait Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file folder encryption, database encryption, etc.
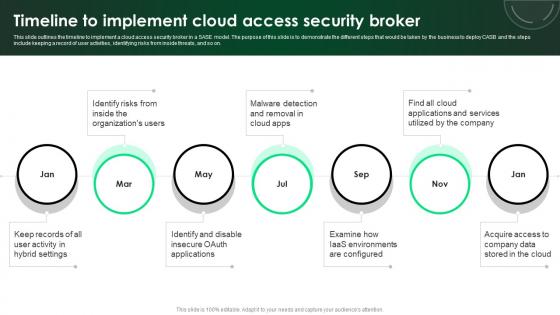
CASB 2 0 IT Timeline To Implement Cloud Access Security Broker
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable CASB 2 0 IT Timeline To Implement Cloud Access Security Broker. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on.

Complete Beginners Guide To Checklist To Ensure Security Of Bitcoin Wallets Fin SS V
This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Get a simple yet stunning designed Complete Beginners Guide To Checklist To Ensure Security Of Bitcoin Wallets Fin SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Complete Beginners Guide To Checklist To Ensure Security Of Bitcoin Wallets Fin SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks.
Security Testing Tracking And Monitoring Harnessing The World Of Ethical Ppt Slide
This slide showcases the security testing tracking and monitoring dashboard components such as planning, design, development, testing, project budget, etc. The Security Testing Tracking And Monitoring Harnessing The World Of Ethical Ppt Slide is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide showcases the security testing tracking and monitoring dashboard components such as planning, design, development, testing, project budget, etc.

Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template
This slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, codecommit, build test, deploy, and monitor. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template can be your best option for delivering a presentation. Represent everything in detail using Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, codecommit, build test, deploy, and monitor.
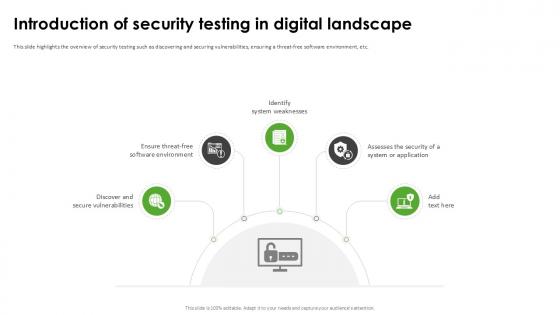
Introduction Of Security Testing Harnessing The World Of Ethical Ppt Powerpoint
This slide highlights the overview of security testing such as discovering and securing vulnerabilities, ensuring a threat-free software environment, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Introduction Of Security Testing Harnessing The World Of Ethical Ppt Powerpoint is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Introduction Of Security Testing Harnessing The World Of Ethical Ppt Powerpoint and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide highlights the overview of security testing such as discovering and securing vulnerabilities, ensuring a threat-free software environment, etc.

Building Trust With IoT Security Concerns And Solutions For Interconnected Devices IoT SS V
This slide exhibits security solution to safeguard interconnected devices against security attacks in order to enhance overall productivity. It includes devices such as smart cameras, RFID tags, Smart GPS systems, and smart home devices, smart meters. Find highly impressive Building Trust With IoT Security Concerns And Solutions For Interconnected Devices IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Building Trust With IoT Security Concerns And Solutions For Interconnected Devices IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide exhibits security solution to safeguard interconnected devices against security attacks in order to enhance overall productivity. It includes devices such as smart cameras, RFID tags, Smart GPS systems, and smart home devices, smart meters.
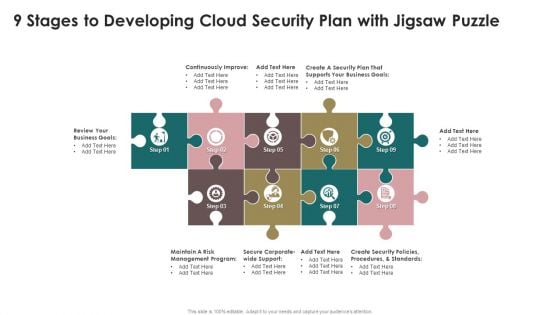
9 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Microsoft PDF
Presenting 9 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Microsoft PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Management Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
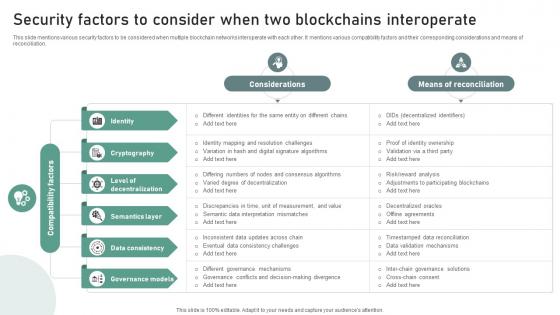
Bridging Blockchains A Deep Security Factors To Consider When Two Blockchains BCT SS V
This slide mentions various security factors to be considered when multiple blockchain networks interoperate with each other. It mentions various compatibility factors and their corresponding considerations and means of reconciliation. Create an editable Bridging Blockchains A Deep Security Factors To Consider When Two Blockchains BCT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Bridging Blockchains A Deep Security Factors To Consider When Two Blockchains BCT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide mentions various security factors to be considered when multiple blockchain networks interoperate with each other. It mentions various compatibility factors and their corresponding considerations and means of reconciliation.

Specific Security Tool Common To All Devsecops Design Role Of Devsecops Ppt Sample
This slide discusses the specific security tool common to DevSecOps design. The purpose of this slide is to explain the various tools, including runtime defense, vulnerability, CVE service host, artifact repository, and zero trust. Get a simple yet stunning designed Specific Security Tool Common To All Devsecops Design Role Of Devsecops Ppt Sample It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Specific Security Tool Common To All Devsecops Design Role Of Devsecops Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide discusses the specific security tool common to DevSecOps design. The purpose of this slide is to explain the various tools, including runtime defense, vulnerability, CVE service host, artifact repository, and zero trust.

Global Data Security Industry Report Blueprint Of The Global Cybersecurity Industry Report IR SS V
The slide shows the overview of the cybersecurity industry report. It sets the stage for subsequent content by introducing the key topics covered in the report to capture the readers attention. It covers a detailed scope, research methodology, and objectives. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Global Data Security Industry Report Blueprint Of The Global Cybersecurity Industry Report IR SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The slide shows the overview of the cybersecurity industry report. It sets the stage for subsequent content by introducing the key topics covered in the report to capture the readers attention. It covers a detailed scope, research methodology, and objectives.
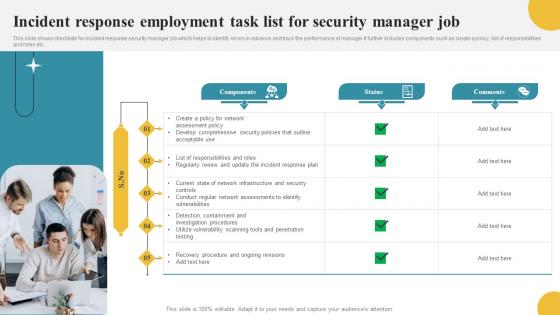
Incident Response Employment Task List For Security Manager Job Themes Pdf
This slide shows checklists for incident response security manager job which helps to identify errors in advance and track the performance of manager It further includes components such as create a policy, list of responsibilities and roles etc. Showcasing this set of slides titled Incident Response Employment Task List For Security Manager Job Themes Pdf The topics addressed in these templates are Components, Responsibilities And Roles, Response Plan All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows checklists for incident response security manager job which helps to identify errors in advance and track the performance of manager It further includes components such as create a policy, list of responsibilities and roles etc.
Five Step Roadmap To Implement Application Security Testing Ppt Powerpoint Icons
This slide outlines the steps to deploy application security in organization such as defining objectives, planning, monitoring, etc. This Five Step Roadmap To Implement Application Security Testing Ppt Powerpoint Icons is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Five Step Roadmap To Implement Application Security Testing Ppt Powerpoint Icons features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the steps to deploy application security in organization such as defining objectives, planning, monitoring, etc.
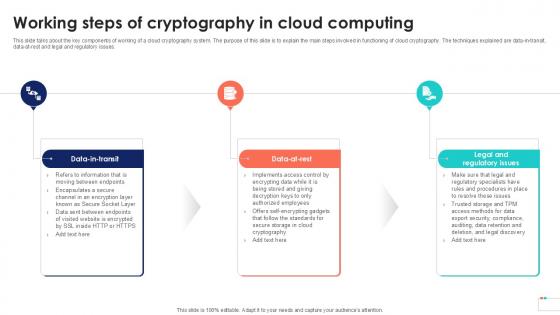
Working Steps Of Cryptography Data Security In Cloud Computing Ppt Slide
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Steps Of Cryptography Data Security In Cloud Computing Ppt Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues.
Mobile Banking Application Security Testing Tools Comprehensive Smartphone Banking Icons Pdf
This slide shows various tools which can be used to evaluate or analyze the security level of mobile banking apps. It includes features and ratings of applications. It also contains various tools such as ImmuniWeb MobileSuite, CodifiedSecurity, QARK, etc.Create an editable Mobile Banking Application Security Testing Tools Comprehensive Smartphone Banking Icons Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Mobile Banking Application Security Testing Tools Comprehensive Smartphone Banking Icons Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide shows various tools which can be used to evaluate or analyze the security level of mobile banking apps. It includes features and ratings of applications. It also contains various tools such as ImmuniWeb MobileSuite, CodifiedSecurity, QARK, etc.
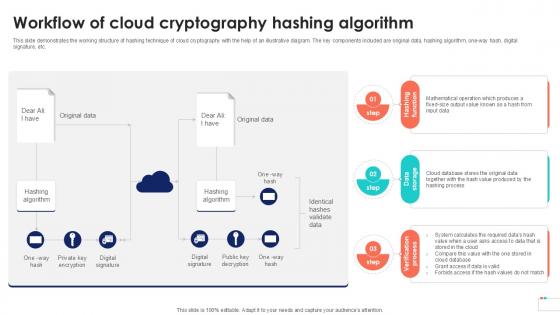
Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example
This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one-way hash, digital signature, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one-way hash, digital signature, etc.

Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V
This slide provides a glimpse of key highlights of the cybersecurity industry, enabling executives to grasp the main findings quickly. It serves as a snapshot highlighting revenue, CAGR, fastest growing region, segments, regional breakdown, and key market players. If you are looking for a format to display your unique thoughts, then the professionally designed Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide provides a glimpse of key highlights of the cybersecurity industry, enabling executives to grasp the main findings quickly. It serves as a snapshot highlighting revenue, CAGR, fastest growing region, segments, regional breakdown, and key market players.

Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V
The slide highlights Porters framework and its implications in the cybersecurity industry. Evaluating the five forces can assist businesses in anticipating changes in the competition, influencing the evolution of industry structure, and finding more beneficial strategic positions. It covers the threat of new entrants and substitutes, competitive rivalry, and the bargaining power of suppliers and buyers. Welcome to our selection of the Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. The slide highlights Porters framework and its implications in the cybersecurity industry. Evaluating the five forces can assist businesses in anticipating changes in the competition, influencing the evolution of industry structure, and finding more beneficial strategic positions. It covers the threat of new entrants and substitutes, competitive rivalry, and the bargaining power of suppliers and buyers.
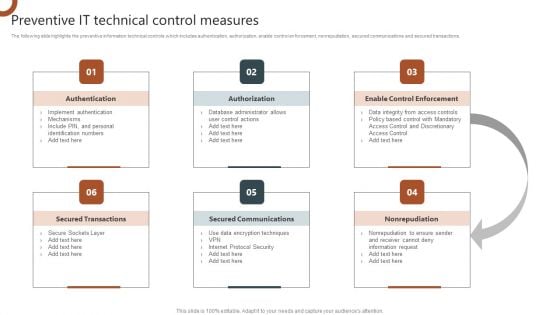
Organizations Risk Management And IT Security Preventive IT Technical Control Measures Topics PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Slidegeeks is here to make your presentations a breeze with Organizations Risk Management And IT Security Preventive IT Technical Control Measures Topics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
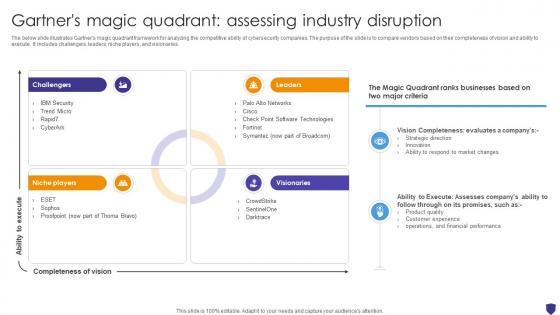
Global Data Security Industry Report Gartners Magic Quadrant Assessing Industry Disruption IR SS V
The below slide illustrates Gartners magic quadrant framework for analyzing the competitive ability of cybersecurity companies. The purpose of the slide is to compare vendors based on their completeness of vision and ability to execute. It includes challengers, leaders, niche players, and visionaries. Find highly impressive Global Data Security Industry Report Gartners Magic Quadrant Assessing Industry Disruption IR SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Global Data Security Industry Report Gartners Magic Quadrant Assessing Industry Disruption IR SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The below slide illustrates Gartners magic quadrant framework for analyzing the competitive ability of cybersecurity companies. The purpose of the slide is to compare vendors based on their completeness of vision and ability to execute. It includes challengers, leaders, niche players, and visionaries.
Image For Blockchain Internet Of Things Security Technology For Business Professional Pdf
Showcasing this set of slides titled Image For Blockchain Internet Of Things Security Technology For Business Professional Pdf The topics addressed in these templates are Blockchain Internet, Things Security, Technology For Business All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Image For Blockchain Internet Of Things Security Technology For Business Professional Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
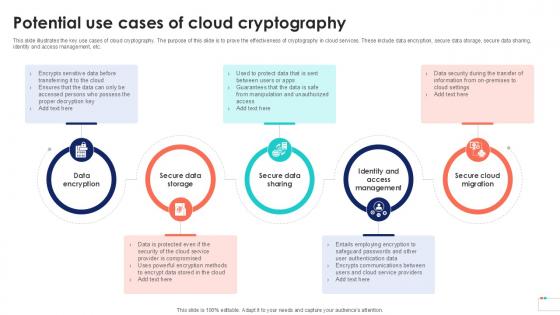
Potential Use Cases Of Cloud Data Security In Cloud Computing Ppt Sample
This slide illustrates the key use cases of cloud cryptography. The purpose of this slide is to prove the effectiveness of cryptography in cloud services. These include data encryption, secure data storage, secure data sharing, identity and access management, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Potential Use Cases Of Cloud Data Security In Cloud Computing Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide illustrates the key use cases of cloud cryptography. The purpose of this slide is to prove the effectiveness of cryptography in cloud services. These include data encryption, secure data storage, secure data sharing, identity and access management, etc.

Best Practices For Website Security Management Step By Step Guide Ideas PDF
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices For Website Security Management Step By Step Guide Ideas PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc.
Image For Personal Biometrics Internet Of Things Security Technology Summary Pdf
Showcasing this set of slides titled Image For Personal Biometrics Internet Of Things Security Technology Summary Pdf The topics addressed in these templates are Image For Personal, Biometrics Internet, Security Technology All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Image For Personal Biometrics Internet Of Things Security Technology Summary Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Wireless Network Security System Smart Lock Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this wireless network security system smart lock ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.
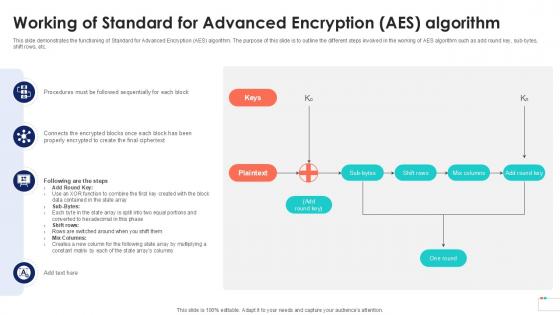
Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc.
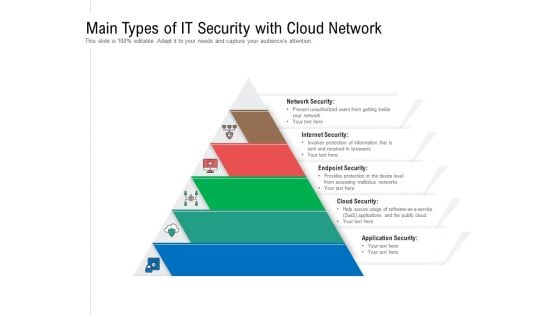
Main Types Of IT Security With Cloud Network Ppt PowerPoint Presentation Gallery Design Ideas PDF
Persuade your audience using this main types of it security with cloud network ppt powerpoint presentation gallery design ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including network security, internet security, endpoint security, cloud security, application security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
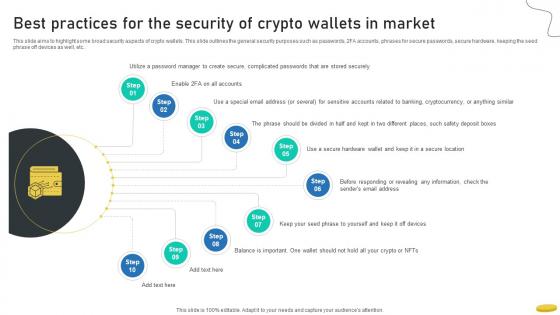
Best Practices For The Security Of Crypto Wallets In Market Cryptocurrency Management With Blockchain
This slide aims to highlight some broad security aspects of crypto wallets. This slide outlines the general security purposes such as passwords, 2FA accounts, phrases for secure passwords, secure hardware, keeping the seed phrase off devices as well, etc.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices For The Security Of Crypto Wallets In Market Cryptocurrency Management With Blockchain. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices For The Security Of Crypto Wallets In Market Cryptocurrency Management With Blockchain today and make your presentation stand out from the rest This slide aims to highlight some broad security aspects of crypto wallets. This slide outlines the general security purposes such as passwords, 2FA accounts, phrases for secure passwords, secure hardware, keeping the seed phrase off devices as well, etc.

Strategic Tips To Improve Physical Data Center Management Security Download PDF
This slide highlights tips to improve security of physical datacentre by having a thorough understanding of security measures and service level agreements. It covers secure location, physical access controls with building management security. Presenting Strategic Tips To Improve Physical Data Center Management Security Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Location, Physical Access Controls, Secure Building Management Systems. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































