Information Security Roadmap
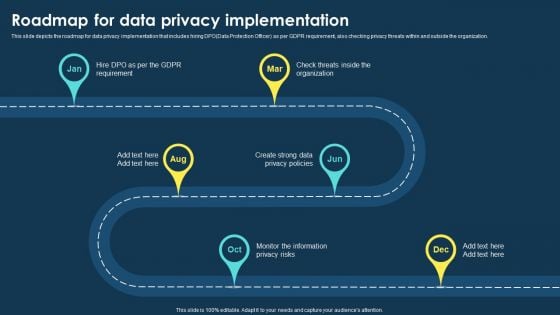
Integrating Data Privacy System Roadmap For Data Privacy Implementation Background PDF
This slide depicts the roadmap for data privacy implementation that includes hiring DPO Data Protection Officer as per GDPR requirement, also checking privacy threats within and outside the organization. Create an editable Integrating Data Privacy System Roadmap For Data Privacy Implementation Background PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Integrating Data Privacy System Roadmap For Data Privacy Implementation Background PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Annual Timeline Roadmap Visual For Data Mining Privacy Issues Ppt PowerPoint Presentation Icon Files PDF
Presenting annual timeline roadmap visual for data mining privacy issues ppt powerpoint presentation icon files pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including annual timeline roadmap visual for data mining privacy issues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
5 Stage Roadmap Visual For Data Mining Privacy Issues Ppt PowerPoint Presentation Icon Outline PDF
Persuade your audience using this 5 stage roadmap visual for data mining privacy issues ppt powerpoint presentation icon outline pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including 5 stage roadmap visual for data mining privacy issues. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
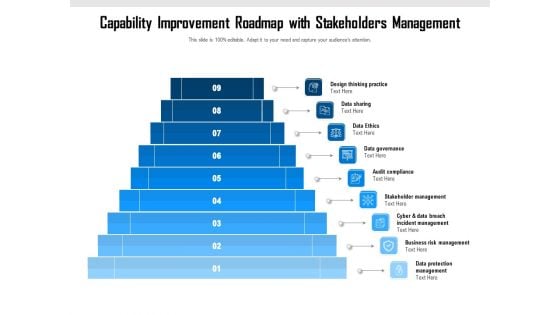
Capability Improvement Roadmap With Stakeholders Management Ppt PowerPoint Presentation File Templates PDF
Presenting capability improvement roadmap with stakeholders management ppt powerpoint presentation file templates pdf to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including management, business, data protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
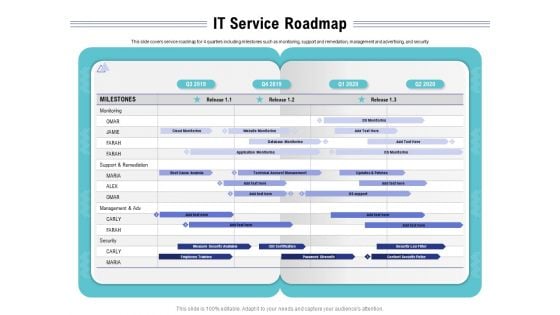
Cloud Managed Services Pricing Guide IT Service Roadmap Ppt Outline Guidelines PDF
Presenting this set of slides with name cloud managed services pricing guide it service roadmap ppt outline guidelines pdf. The topics discussed in these slides are monitoring, management, security, analysis, training. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Project Roadmap Of Product Delivery Ppt PowerPoint Presentation Summary Graphics Design PDF
Presenting this set of slides with name it project roadmap of product delivery ppt powerpoint presentation summary graphics design pdf. The topics discussed in these slides are delivery, security, inception, promotion stream, continuous improvement, low risk, medium risk, high risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
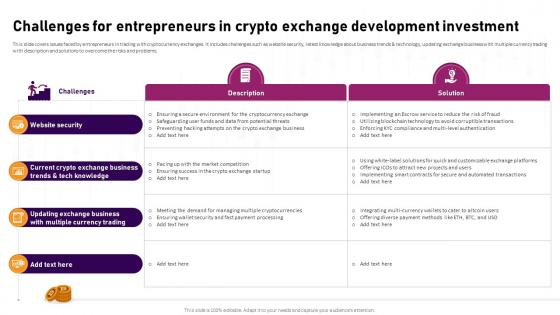
Challenges For Entrepreneurs In Crypto Exchange Complete Roadmap To Blockchain BCT SS V
This slide covers issues faced by entrepreneurs in trading with cryptocurrency exchanges. It includes challenges such as website security, latest knowledge about business trends and technology, updating exchange business with multiple currency trading with description and solutions to overcome the risks and problems. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Challenges For Entrepreneurs In Crypto Exchange Complete Roadmap To Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers issues faced by entrepreneurs in trading with cryptocurrency exchanges. It includes challenges such as website security, latest knowledge about business trends and technology, updating exchange business with multiple currency trading with description and solutions to overcome the risks and problems.

Roadmap To Identify And Launch Devops Initiatives Ppt Professional Slide Download PDF
This template covers DevOps implementation roadmaps starting from organizing devOps initiative, then building, containerizing, integrating, test automation and monitoring etc. Deliver and pitch your topic in the best possible manner with this roadmap to identify and launch devops initiatives ppt professional slide download pdf. Use them to share invaluable insights on process, security, strategy, opportunities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
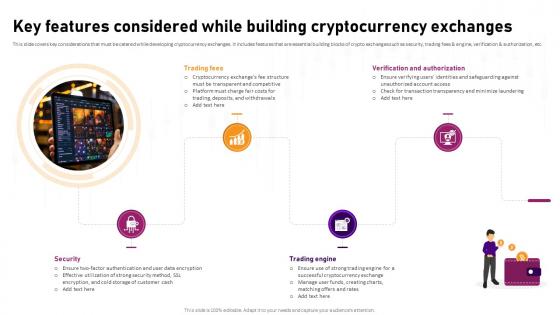
Key Features Considered While Building Complete Roadmap To Blockchain BCT SS V
This slide covers key considerations that must be catered while developing cryptocurrency exchanges. It includes features that are essential building blocks of crypto exchanges such as security, trading fees and engine, verification and authorization, etc. Take your projects to the next level with our ultimate collection of Key Features Considered While Building Complete Roadmap To Blockchain BCT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide covers key considerations that must be catered while developing cryptocurrency exchanges. It includes features that are essential building blocks of crypto exchanges such as security, trading fees and engine, verification and authorization, etc.

Comparing Decentralized And Centralized Complete Roadmap To Blockchain BCT SS V
This slide covers comparison between two cryptocurrencies based on different factors. It includes factors such as range of crypto offerings, supporting fiat currencies, user friendliness and funds custodian, privacy, security, liquidity and adoption rates for centralized and decentralized crypto exchanges. Find highly impressive Comparing Decentralized And Centralized Complete Roadmap To Blockchain BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Comparing Decentralized And Centralized Complete Roadmap To Blockchain BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide covers comparison between two cryptocurrencies based on different factors. It includes factors such as range of crypto offerings, supporting fiat currencies, user friendliness and funds custodian, privacy, security, liquidity and adoption rates for centralized and decentralized crypto exchanges.
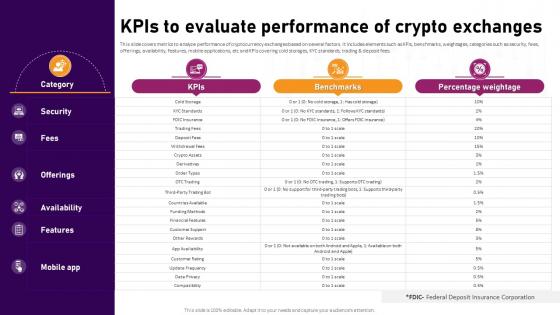
KPIs To Evaluate Performance Of Crypto Exchanges Complete Roadmap To Blockchain BCT SS V
This slide covers metrics to analyze performance of cryptocurrency exchanges based on several factors. It includes elements such as KPIs, benchmarks, weightages, categories such as security, fees, offerings, availability, features, mobile applications, etc and KPIs covering cold storages, KYC standards, trading and deposit fees. Do you know about Slidesgeeks KPIs To Evaluate Performance Of Crypto Exchanges Complete Roadmap To Blockchain BCT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide covers metrics to analyze performance of cryptocurrency exchanges based on several factors. It includes elements such as KPIs, benchmarks, weightages, categories such as security, fees, offerings, availability, features, mobile applications, etc and KPIs covering cold storages, KYC standards, trading and deposit fees.
Curved Roadmap Graphics To Protect Personal Assets From Business Ppt PowerPoint Presentation File Gallery PDF
Presenting curved roadmap graphics to protect personal assets from business ppt powerpoint presentation file gallery pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including curved roadmap graphics to protect personal assets from business. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Overview Of Decentralized Cryptocurrency Exchanges Complete Roadmap To Blockchain BCT SS V
This slide covers brief summary of decentralized crypto exchanges with ways to operate by users. It also includes benefits such as faster and cheaper transactions, secure, integration with hardware wallets, users control funds, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Overview Of Decentralized Cryptocurrency Exchanges Complete Roadmap To Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers brief summary of decentralized crypto exchanges with ways to operate by users. It also includes benefits such as faster and cheaper transactions, secure, integration with hardware wallets, users control funds, etc.
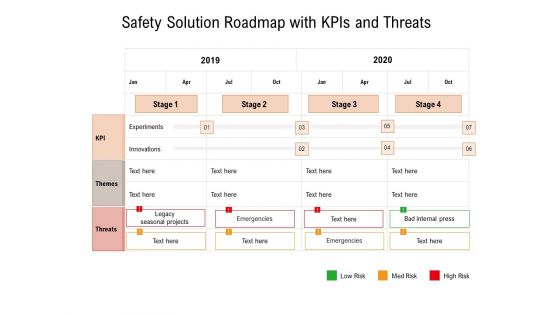
Safety Solution Roadmap With Kpis And Threats Ppt PowerPoint Presentation File Outline PDF
Showcasing this set of slides titled safety solution roadmap with kpis and threats ppt powerpoint presentation file outline pdf. The topics addressed in these templates are experiments, innovations, 2019, 2020, bad internal press. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Internet Defence Protection Roadmap Ppt PowerPoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Internet Defence Protection Roadmap Ppt PowerPoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising fivteen this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.
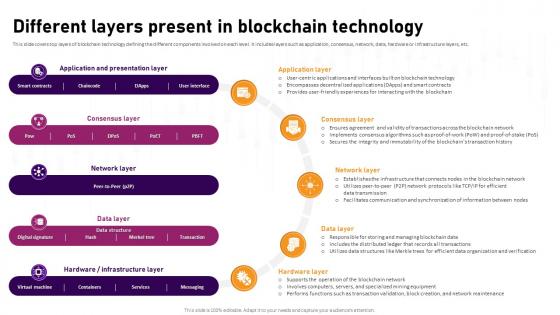
Different Layers Present In Blockchain Technology Complete Roadmap To Blockchain BCT SS V
This slide covers top layers of blockchain technology defining the different components involved on each level. It includes layers such as application, consensus, network, data, hardware or infrastructure layers, etc. This modern and well-arranged NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide covers top layers of blockchain technology defining the different components involved on each level. It includes layers such as application, consensus, network, data, hardware or infrastructure layers, etc.
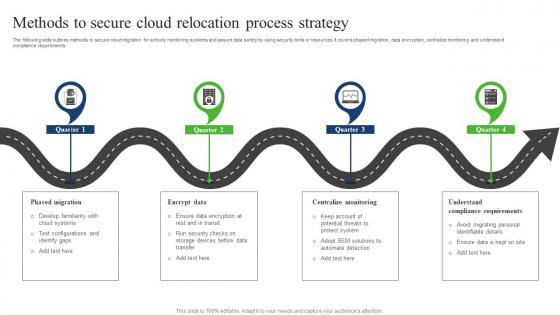
Methods To Secure Cloud Relocation Process Strategy Sample Pdf
The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements. Showcasing this set of slides titled Methods To Secure Cloud Relocation Process Strategy Sample Pdf. The topics addressed in these templates are Centralize Monitoring, Understand Compliance Requirements, Phased Migration, Encrypt Data . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements.
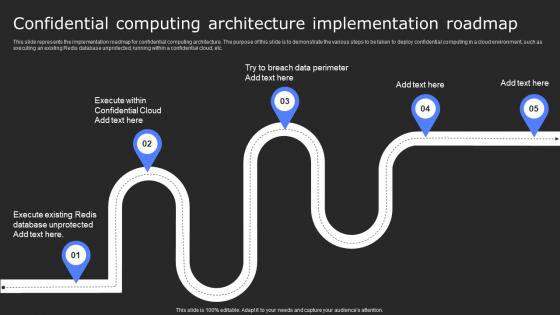
Confidential Computing Architecture Secure Computing Framework Themes Pdf
This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Confidential Computing Architecture Secure Computing Framework Themes Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.
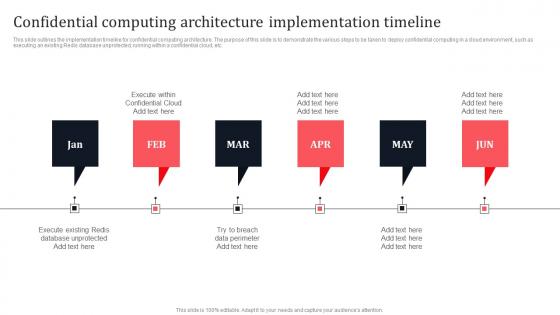
Confidential Computing Architecture Implementation Timeline Secure Multi Party Demonstration Pdf
This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Find highly impressive Confidential Computing Architecture Implementation Timeline Secure Multi Party Demonstration Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Confidential Computing Architecture Implementation Timeline Secure Multi Party Demonstration Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.

Nanorobotics In Healthcare And Medicine Timeline For Effective Nanorobot Utilization In Organization
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Nanorobotics In Healthcare And Medicine Timeline For Effective Nanorobot Utilization In Organization. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Nanorobotics In Healthcare And Medicine Timeline For Effective Nanorobot Utilization In Organization today and make your presentation stand out from the rest This slide defines an all-inclusive timeline of steps in the execution of nanorobotics in healthcare and medicine by incorporating effective use of nanorobots within an organization. This ranges from preparation and research and eventually to the inclusion of nanorobotics with the existing healthcare systems. The timeline also identifies critical factors including security, regulatory compliance, testing, and safety procedures, where nanorobots would be applied safely and effectively.This slide is perfect for advanced medical technology presentations to help the stakeholders understand the systematic process of how nanorobotics could be introduced in healthcare solutions and paved their way for smooth adoption and use.

Secure Email Technology PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Secure Email Technology PowerPoint Templates PPT Backgrounds For Slides 0413.Download our Technology PowerPoint Templates because Your audience will believe you are the cats whiskers. Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Present our Communication PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download and present our Signs PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium.Use these PowerPoint slides for presentations relating to Illustration of envelope and email sign protect with padloc, security, communication, technology, business, signs. The prominent colors used in the PowerPoint template are Red, Gray, Yellow. Deal a decisive blow with our Secure Email Technology PowerPoint Templates Ppt Backgrounds For Slides 0413. Get clearlyahead in a critical event.
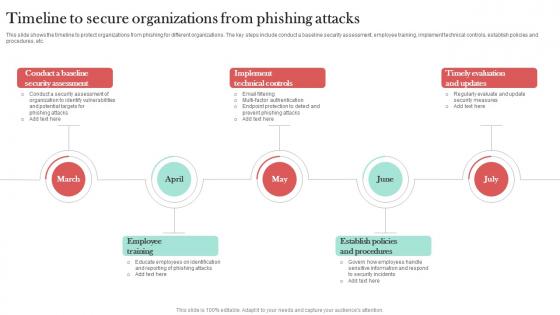
Timeline To Secure Organizations From Man In The Middle Phishing IT
This slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. This Timeline To Secure Organizations From Man In The Middle Phishing IT is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Timeline To Secure Organizations From Man In The Middle Phishing IT features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc.

Secure Web Gateway SWG Functional Components Ppt Infographics Picture PDF
This slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Secure Web Gateway SWG Functional Components Ppt Infographics Picture PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
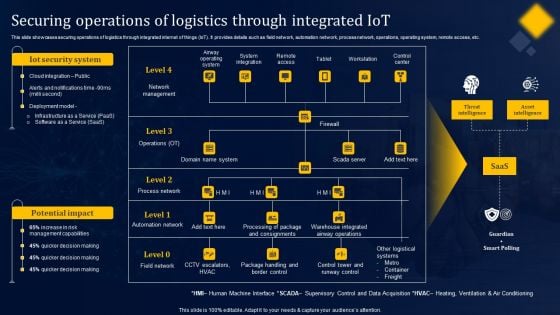
Securing Operations Of Logistics Through Integrated Iot Structure PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Securing Operations Of Logistics Through Integrated Iot Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
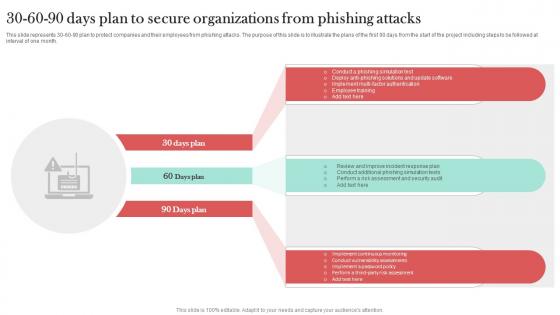
30 60 90 Days Plan To Secure Organizations Man In The Middle Phishing IT
This slide represents 30-60-90 plan to protect companies and their employees from phishing attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Organizations Man In The Middle Phishing IT. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to protect companies and their employees from phishing attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.
Cloud Secure Data Lifecycle In Powerpoint And Google Slides Cpb
Introducing our well designed Cloud Secure Data Lifecycle In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cloud Secure Data Lifecycle. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cloud Secure Data Lifecycle In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Browser Secure Market In Powerpoint And Google Slides Cpb
Introducing our well designed Browser Secure Market In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Browser Secure Market. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Browser Secure Market In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Business Continuity Securing In Powerpoint And Google Slides Cpb
Introducing our well designed Business Continuity Securing In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Business Continuity Securing. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Business Continuity Securing In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
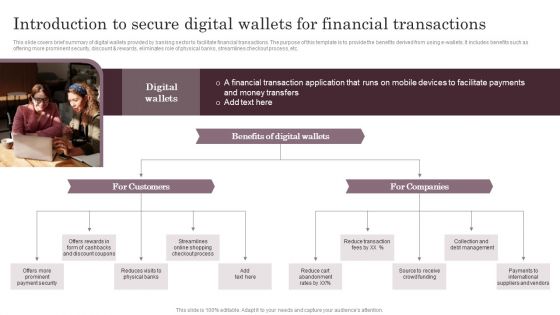
Introduction To Secure Digital Wallets For Financial Transactions Themes PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e-wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Introduction To Secure Digital Wallets For Financial Transactions Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Securing Your Data with Tokenization Powerpoint Presentation Slides PPT Example
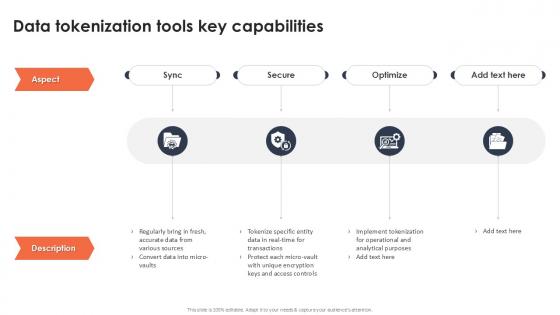
Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint
If you are looking for a format to display your unique thoughts, then the professionally designed Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Our Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
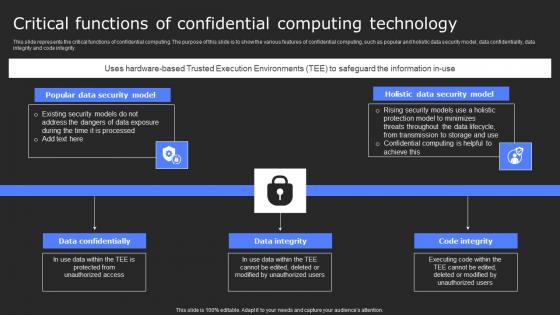
Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Are you searching for a Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf from Slidegeeks today. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.

Prominent Users Of Secure Web Gateway Web Threat Protection System
This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc. Retrieve professionally designed Prominent Users Of Secure Web Gateway Web Threat Protection System to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc.

Future Of Confidential Computing Technology Secure Multi Party Rules Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Slidegeeks has constructed Future Of Confidential Computing Technology Secure Multi Party Rules Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment.
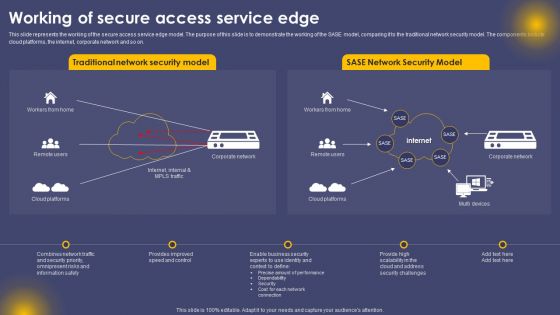
Working Of Secure Access Service Edge Ppt Summary Ideas PDF
This slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. The Working Of Secure Access Service Edge Ppt Summary Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
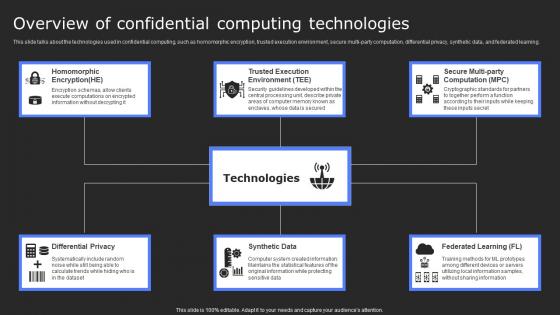
Overview Of Confidential Computing Technologies Secure Computing Framework Slides Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Present like a pro with Overview Of Confidential Computing Technologies Secure Computing Framework Slides Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.
Design Secure Network In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Design Secure Network In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Design Secure Network that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Design Secure Network In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Web Access Control Solution Secure Web Gateway Performance Tracking Dashboard
This slide represents a dashboard to maintain the record of various functions of Secure Web Gateway. The main components are top blocked web malware, web usage trend, top web application categories, risky web isolations, etc. Get a simple yet stunning designed Web Access Control Solution Secure Web Gateway Performance Tracking Dashboard. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Web Access Control Solution Secure Web Gateway Performance Tracking Dashboard can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents a dashboard to maintain the record of various functions of Secure Web Gateway. The main components are top blocked web malware, web usage trend, top web application categories, risky web isolations, etc.
Secure Copy Protocolreport Template In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Secure Copy Protocolreport Template In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Secure Copy Protocolreport Template that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Secure Copy Protocolreport Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Secure Web Gateway Implementation Methodology Transparent Web Access Control Solution
This slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Secure Web Gateway Implementation Methodology Transparent Web Access Control Solution for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.
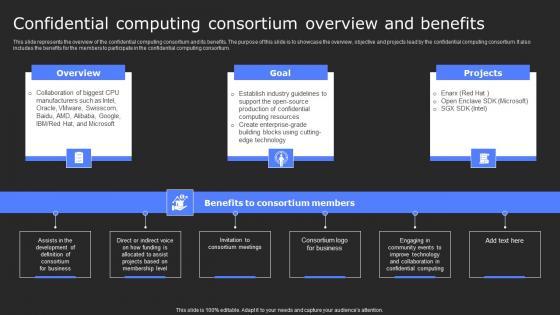
Confidential Computing Consortium Overview And Secure Computing Framework Inspiration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. Make sure to capture your audiences attention in your business displays with our gratis customizable Confidential Computing Consortium Overview And Secure Computing Framework Inspiration Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium.
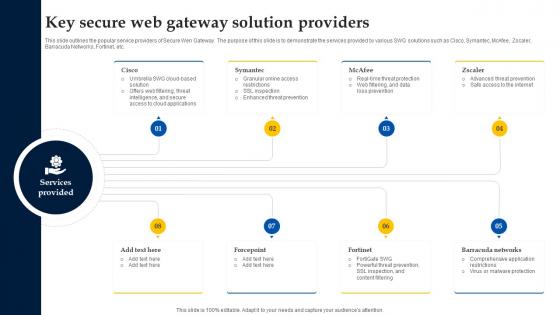
Web Access Control Solution Key Secure Web Gateway Solution Providers
This slide outlines the popular service providers of Secure Wen Gateway. The purpose of this slide is to demonstrate the services provided by various SWG solutions such as Cisco, Symantec, McAfee, Zscaler, Barracuda Networks, Fortinet, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Web Access Control Solution Key Secure Web Gateway Solution Providers to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Web Access Control Solution Key Secure Web Gateway Solution Providers. This slide outlines the popular service providers of Secure Wen Gateway. The purpose of this slide is to demonstrate the services provided by various SWG solutions such as Cisco, Symantec, McAfee, Zscaler, Barracuda Networks, Fortinet, etc.
Timeline Secure Network Construction Proposal One Pager Sample Example Document
Presenting you an exemplary Timeline Secure Network Construction Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Timeline Secure Network Construction Proposal One Pager Sample Example Document brilliant piece now.

Timeline To Implement Secure Access Service Edge Ppt Infographics Display PDF
This slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Find highly impressive Timeline To Implement Secure Access Service Edge Ppt Infographics Display PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Timeline To Implement Secure Access Service Edge Ppt Infographics Display PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Online PR Techniques To Boost Brands Online Visibility Budget Securing Tips For Public Relations Introduction PDF
This slide shows various tips which can be used by organizations to while developing marketing budget. It includes aligning marketing outcome with organizational goals, strategic insights and highlight impacts. Make sure to capture your audiences attention in your business displays with our gratis customizable Online PR Techniques To Boost Brands Online Visibility Budget Securing Tips For Public Relations Introduction PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Piggy Bank Locked Secure Money Future PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Piggy Bank Locked Secure Money Future PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Illuminate the road ahead to Pinpoint the important landmarks along the way. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are created by a hardworking bunch of busybees. Always flitting around with solutions gauranteed to please. Use our Finance PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Download our Technology PowerPoint Templates because Our PowerPoint Templates and Slides are created with admirable insight. Use them and give your group a sense of your logical mind.Use these PowerPoint slides for presentations relating to Financial insurance, Security, Business, Shapes, Finance, Technology. The prominent colors used in the PowerPoint template are Gray, Red, Black. PowerPoint presentation experts tell us our Piggy Bank Locked Secure Money Future PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Use our Technology PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. The feedback we get is that our Piggy Bank Locked Secure Money Future PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. The feedback we get is that our Security PowerPoint templates and PPT Slides will help them to explain complicated concepts. People tell us our Piggy Bank Locked Secure Money Future PowerPoint Templates PPT Backgrounds For Slides 0113 have awesome images to get your point across. Professionals tell us our Technology PowerPoint templates and PPT Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Transition to a better presentation with our Piggy Bank Locked Secure Money Future PowerPoint Templates Ppt Backgrounds For Slides 0113. Download without worries with our money back guaranteee.

Secured Piggy Bank With Chains PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Secured Piggy Bank With Chains PowerPoint Templates PPT Backgrounds For Slides 0313.Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Download and present our Success PowerPoint Templates because Our PowerPoint Templates and Slides are Clear and concise. Use them and dispel any doubts your team may have. Download our services PowerPoint Templates because Our PowerPoint Templates and Slides will embellish your thoughts. See them provide the desired motivation to your team. Use our Chains PowerPoint Templates because It will get your audience in sync.Use these PowerPoint slides for presentations relating to Piggy bank secured with padlock and chains, business, security, success, services, chains. The prominent colors used in the PowerPoint template are Blue, Orange, Gray. Address the conference with elan. Our Secured Piggy Bank With Chains PowerPoint Templates Ppt Backgrounds For Slides 0313 will give your confidence a boost.

Secure Internet Browser Internet PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Secure Internet Browser Internet PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Technology PowerPoint Templates because You have gained great respect for your brilliant ideas. Use our PowerPoint Templates and Slides to strengthen and enhance your reputation. Use our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Present our Security PowerPoint Templates because Watching this your Audience will Grab their eyeballs, they wont even blink. Download our Business PowerPoint Templates because You have the co-ordinates for your destination of success. Let our PowerPoint Templates and Slides map out your journey. Present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time.Use these PowerPoint slides for presentations relating to Secure Internet Browser, technology, arrows, security, business, success. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. Professionals tell us our Secure Internet Browser Internet PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides are the best it can get when it comes to presenting. You can be sure our Secure Internet Browser Internet PowerPoint Templates PPT Backgrounds For Slides 0113 are topically designed to provide an attractive backdrop to any subject. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. We assure you our Secure Internet Browser Internet PowerPoint Templates PPT Backgrounds For Slides 0113 are the best it can get when it comes to presenting. PowerPoint presentation experts tell us our Browser PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. Make your audience feel exclusive with our Secure Internet Browser Internet PowerPoint Templates Ppt Backgrounds For Slides 0113. Give them special attention with your thoughts.

Blue Piggy With Lock Financially Secure PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Blue Piggy With Lock Financially Secure PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Finance PowerPoint Templates because It will get your audience in sync. Download and present our Security PowerPoint Templates because You can Stir your ideas in the cauldron of our PowerPoint Templates and Slides. Cast a magic spell on your audience. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Present our Future PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home.Use these PowerPoint slides for presentations relating to A blue piggy with lock, Finance, Security, Business, Future, Shapes. The prominent colors used in the PowerPoint template are Blue, Gray, Yellow. PowerPoint presentation experts tell us our Blue Piggy With Lock Financially Secure PowerPoint Templates PPT Backgrounds For Slides 0113 will help them to explain complicated concepts. Use our piggy PowerPoint templates and PPT Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. The feedback we get is that our Blue Piggy With Lock Financially Secure PowerPoint Templates PPT Backgrounds For Slides 0113 have awesome images to get your point across. The feedback we get is that our Future PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. People tell us our Blue Piggy With Lock Financially Secure PowerPoint Templates PPT Backgrounds For Slides 0113 will help you be quick off the draw. Just enter your specific text and see your points hit home. Professionals tell us our Business PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. Influence teams with our Blue Piggy With Lock Financially Secure PowerPoint Templates Ppt Backgrounds For Slides 0113. Download without worries with our money back guaranteee.

Potential Technologies Deployed To Secure Vulnerable Monitoring Digital Assets Summary Pdf
This slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Potential Technologies Deployed To Secure Vulnerable Monitoring Digital Assets Summary Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc.
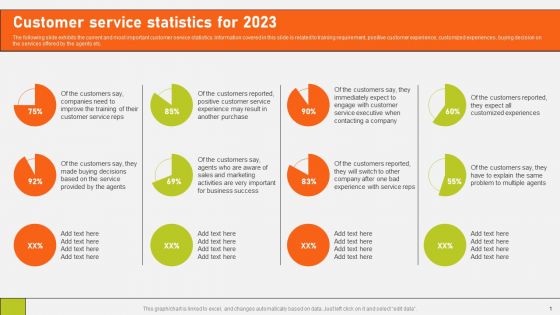
Securing Market Leadership Through Competitive Excellence Customer Service Statistics For 2023 Infographics PDF
The following slide exhibits the current and most important customer service statistics. Information covered in this slide is related to training requirement, positive customer experience, customized experiences, buying decision on the services offered by the agents etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Securing Market Leadership Through Competitive Excellence Customer Service Statistics For 2023 Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Digitized Record Book Technology Is Digital Ledger Technology Secure Sample PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. Presenting digitized record book technology is digital ledger technology secure sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like information, data, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
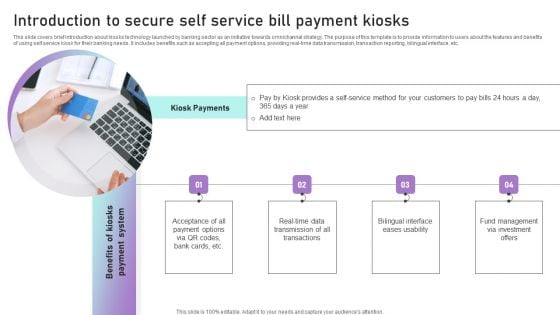
Introduction To Secure Self Service Bill Payment Kiosks Ppt Outline Grid PDF
This slide covers brief introduction about kiosks technology launched by banking sector as an initiative towards omnichannel strategy. The purpose of this template is to provide information to users about the features and benefits of using self service kiosk for their banking needs. It includes benefits such as accepting all payment options, providing real-time data transmission, transaction reporting, bilingual interface, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Introduction To Secure Self Service Bill Payment Kiosks Ppt Outline Grid PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
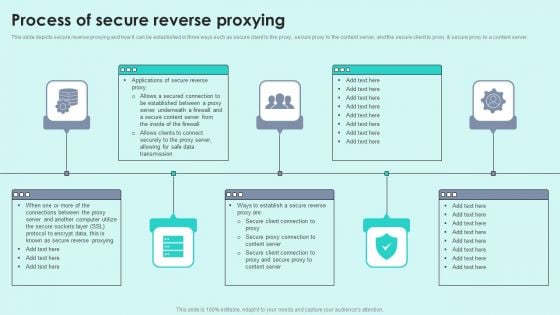
Process Of Secure Reverse Proxying Reverse Proxy For Load Balancing Microsoft PDF
This slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy secure proxy to a content server.This is a Process Of Secure Reverse Proxying Reverse Proxy For Load Balancing Microsoft PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Secured Connection, Established Between, Underneath Firewall. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
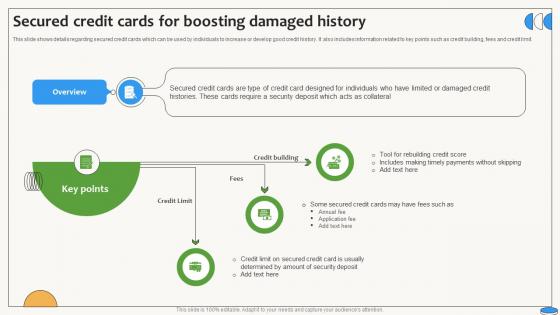
Secured Credit Cards For Boosting Damaged History Swipe Smartly A Practical Guide Fin SS V
This slide shows details regarding secured credit cards which can be used by individuals to increase or develop good credit history. It also includes information related to key points such as credit building, fees and credit limit. There are so many reasons you need a Secured Credit Cards For Boosting Damaged History Swipe Smartly A Practical Guide Fin SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide shows details regarding secured credit cards which can be used by individuals to increase or develop good credit history. It also includes information related to key points such as credit building, fees and credit limit.
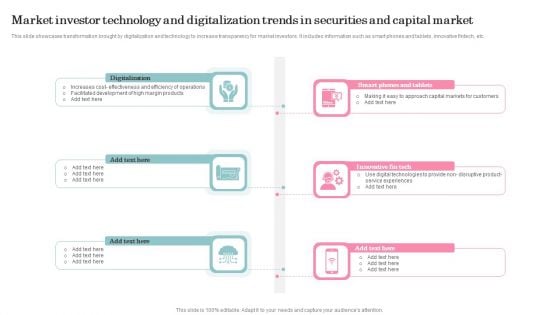
Market Investor Technology And Digitalization Trends In Securities And Capital Market Structure PDF
This slide showcases transformation brought by digitalization and technology to increase transparency for market investors. It includes information such as smart phones and tablets, innovative fintech, etc. Presenting Market Investor Technology And Digitalization Trends In Securities And Capital Market Structure PDF to dispense important information. This template comprises Six stages. It also presents valuable insights into the topics including Digitalization, Innovative Fin Tech. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
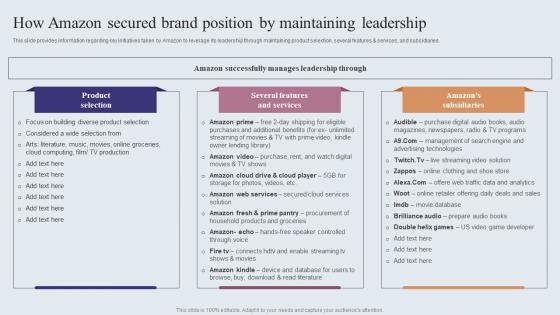
How Amazon Secured Brand Position By Maintaining Amazons Journey For Becoming Themes PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our How Amazon Secured Brand Position By Maintaining Amazons Journey For Becoming Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into How Amazon Secured Brand Position By Maintaining Amazons Journey For Becoming Themes PDF. This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries.
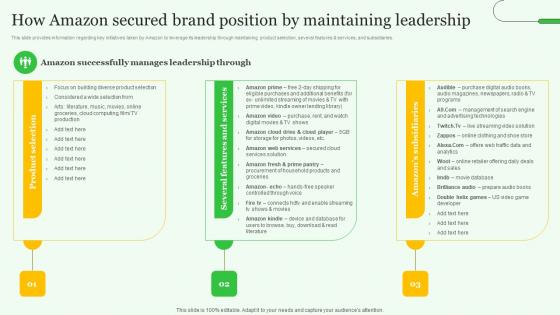
How Amazon Secured Brand Exploring Amazons Global Business Model Growth Topics Pdf
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. This How Amazon Secured Brand Exploring Amazons Global Business Model Growth Topics Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The How Amazon Secured Brand Exploring Amazons Global Business Model Growth Topics Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries.
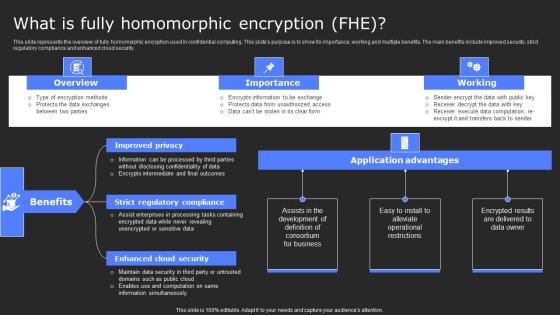
What Is Fully Homomorphic Encryption Fhe Secure Computing Framework Topics Pdf
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. What Is Fully Homomorphic Encryption Fhe Secure Computing Framework Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security.

Secure Retirement Planning With Key Activities Strategic Wealth Management And Financial Fin SS V
This slide shows information which can be utilized to know basics of retirement planning. It also includes details about key activities included in retirement planning which are lifestyle assessment, income projection, etc. Get a simple yet stunning designed Secure Retirement Planning With Key Activities Strategic Wealth Management And Financial Fin SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Secure Retirement Planning With Key Activities Strategic Wealth Management And Financial Fin SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for. Grab this template today. This slide shows information which can be utilized to know basics of retirement planning. It also includes details about key activities included in retirement planning which are lifestyle assessment, income projection, etc.


 Continue with Email
Continue with Email

 Home
Home


































