Information Security Roadmap

Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF
The following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF
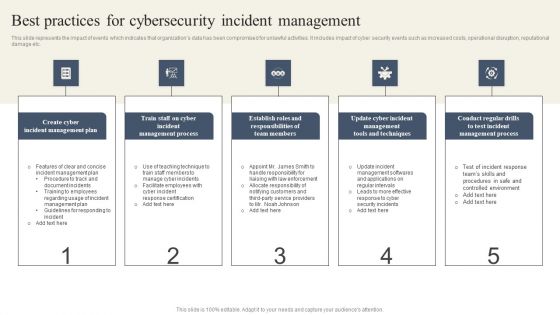
CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. The Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
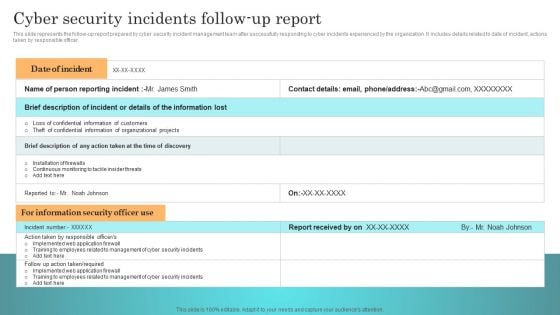
Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. The Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
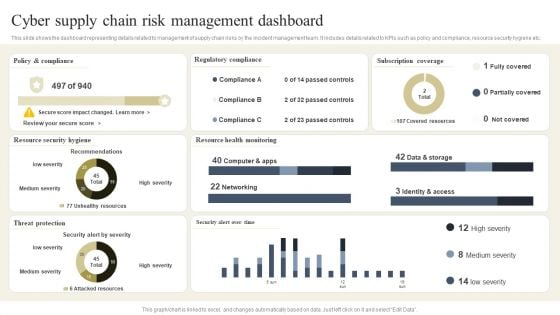
CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Incident Response Techniques Deployement Cyber Security Crisis Management Action Plan Timeline Rules PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Incident Response Techniques Deployement Cyber Security Crisis Management Action Plan Timeline Rules PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
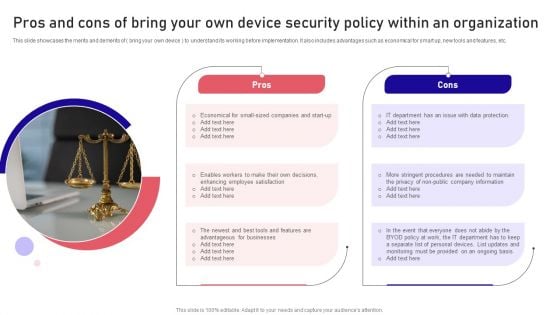
Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF
This slide showcases the merits and demerits of bring your own device to understand its working before implementation. It also includes advantages such as economical for smart up, new tools and features, etc. Presenting Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Data Protection, Organization, Company Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
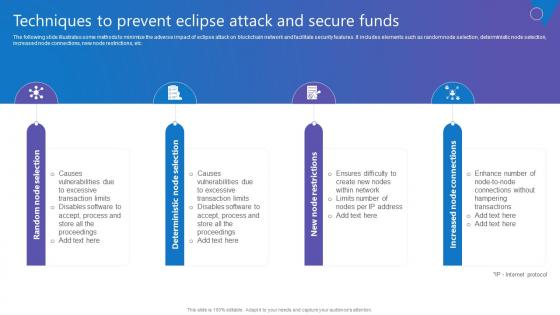
Techniques To Prevent Eclipse Comprehensive Guide To Blockchain Digital Security Formats Pdf
The following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Create an editable Techniques To Prevent Eclipse Comprehensive Guide To Blockchain Digital Security Formats Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Techniques To Prevent Eclipse Comprehensive Guide To Blockchain Digital Security Formats Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc.
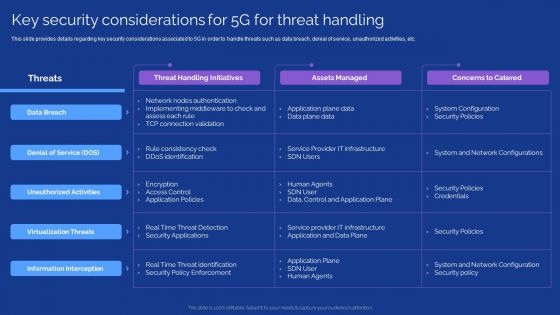
Development Guide For 5G World Key Security Considerations For 5G For Threat Handling Slides PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. This modern and well arranged Development Guide For 5G World Key Security Considerations For 5G For Threat Handling Slides PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Find highly impressive Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
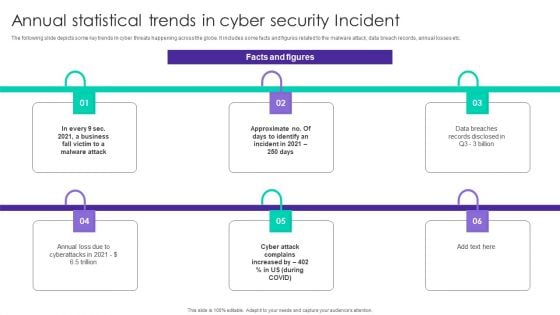
Annual Statistical Trends In Cyber Security Incident Ppt Outline Shapes PDF
The following slide depicts some key trends in cyber threats happening across the globe. It includes some facts and figures related to the malware attack, data breach records, annual losses etc. Presenting Annual Statistical Trends In Cyber Security Incident Ppt Outline Shapes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Malware Attack, Business Fall, Data Breaches. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Software Development Life Cycle Planning Prioritized Cyber Security Threats With Risk Mitigation Plan Template PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Explore a selection of the finest Software Development Life Cycle Planning Prioritized Cyber Security Threats With Risk Mitigation Plan Template PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Software Development Life Cycle Planning Prioritized Cyber Security Threats With Risk Mitigation Plan Template PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Investment Banking Security Underwriting Pitchbook IPO Timeline Pre IPO To Post IPO Pictures PDF
The slide provides the timeline of IPO issue and covers the five steps i.e. Pre-IPO planning, Preparation for Filing, SEC Review, Road Show, and Post IPODeliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook IPO Timeline Pre IPO To Post IPO Pictures PDF bundle. Topics like Organizational Meeting, Preparation Filling, Internal Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Overview And Working Process Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide illustrates brief introduction of distributed denial of service DDoS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. The Overview And Working Process Comprehensive Guide To Blockchain Digital Security Template Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The following slide illustrates brief introduction of distributed denial of service DDoS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc.
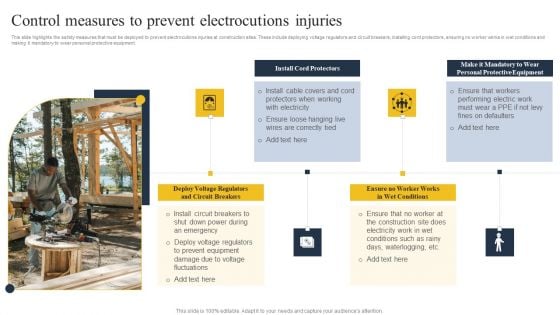
Security Control Techniques For Real Estate Project Control Measures To Prevent Electrocutions Injuries Ideas PDF
Explore a selection of the finest Security Control Techniques For Real Estate Project Control Measures To Prevent Electrocutions Injuries Ideas PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Security Control Techniques For Real Estate Project Control Measures To Prevent Electrocutions Injuries Ideas PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Monthly IT Security Awareness Training Program Timeline Ppt Model Demonstration PDF
This slide covers monthly cybersecurity awareness training program timeline. It involves activities such as passwords training, phishing exercise, remote access testing and conduct internal tabletop exercises. Showcasing this set of slides titled Monthly IT Security Awareness Training Program Timeline Ppt Model Demonstration PDF. The topics addressed in these templates are Authentication And Passwords, Conduct Phishing Exercise, Remote Access Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
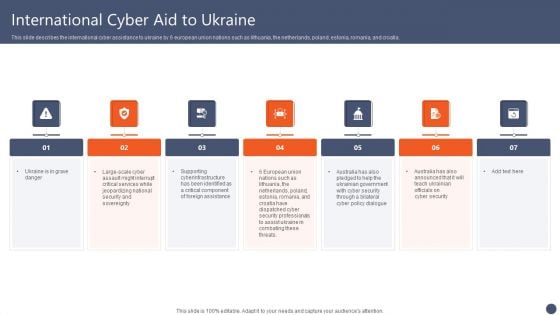
Series Of Cyber Security Attacks Against Ukraine 2022 International Cyber Aid To Ukraine Graphics PDF
This slide describes the international cyber assistance to ukraine by 6 european union nations such as lithuania, the netherlands, poland, estonia, romania, and croatia. Get a simple yet stunning designed Series Of Cyber Security Attacks Against Ukraine 2022 International Cyber Aid To Ukraine Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Series Of Cyber Security Attacks Against Ukraine 2022 International Cyber Aid To Ukraine Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Operational Safety Guidelines Air Workplace Safety Protocol And Security Practices Icons Pdf
This slides highlights the operational safety guidelines to minimize air compressor hazards. It showcases different protective gears with pre operation, operation and post operation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Operational Safety Guidelines Air Workplace Safety Protocol And Security Practices Icons Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Operational Safety Guidelines Air Workplace Safety Protocol And Security Practices Icons Pdf. This slides highlights the operational safety guidelines to minimize air compressor hazards. It showcases different protective gears with pre operation, operation and post operation.
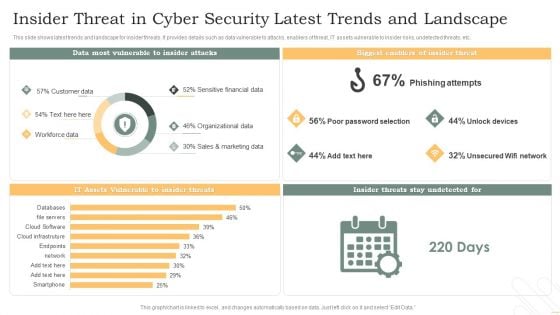
Insider Threat In Cyber Security Latest Trends And Landscape Pictures PDF
This slide shows latest trends and landscape for insider threats. It provides details such as data vulnerable to attacks, enablers of threat, IT assets vulnerable to insider risks, undetected threats, etc. Showcasing this set of slides titled Insider Threat In Cyber Security Latest Trends And Landscape Pictures PDF. The topics addressed in these templates are Phishing Attempts, Unlock Devices, Unsecured Wifi Network. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
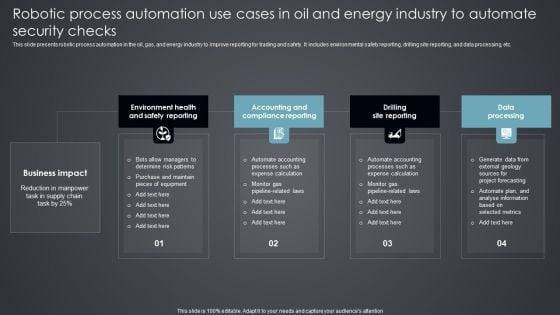
Robotic Process Automation Use Cases In Oil And Energy Industry To Automate Security Checks Introduction PDF
This slide presents robotic process automation in the oil, gas, and energy industry to improve reporting for trading and safety. It includes environmental safety reporting, drilling site reporting, and data processing, etc. Presenting Robotic Process Automation Use Cases In Oil And Energy Industry To Automate Security Checks Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Environment Health, Accounting Compliance Reporting, Drilling Site Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
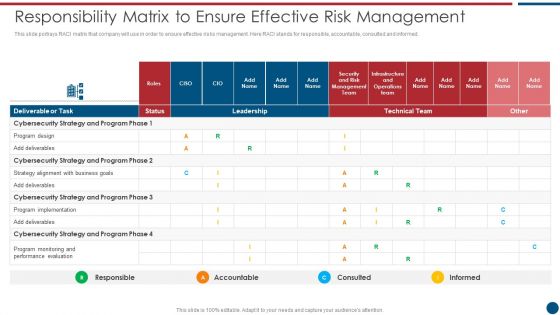
Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF bundle. Topics like Technical Team, Cybersecurity Strategy, Program Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF bundle. Topics like Program Design, Cybersecurity Strategy, Performance Evaluation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
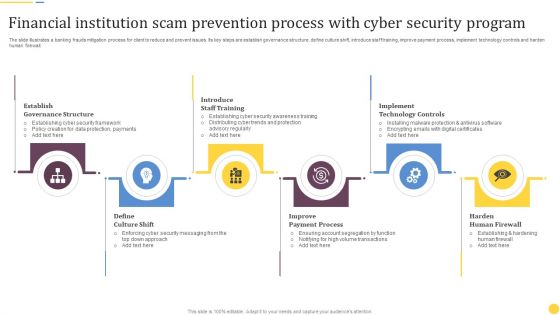
Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF
The slide illustrates a banking frauds mitigation process for client to reduce and prevent issues. Its key steps are establish governance structure, define culture shift, introduce staff training, improve payment process, implement technology controls and harden human firewall. Presenting Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Establish Governance Structure, Introduce Staff Training, Implement Technology Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
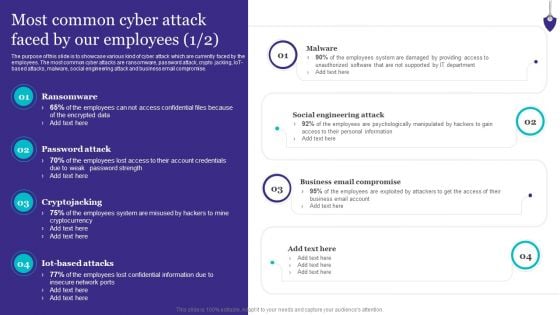
Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF
The Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF
The Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
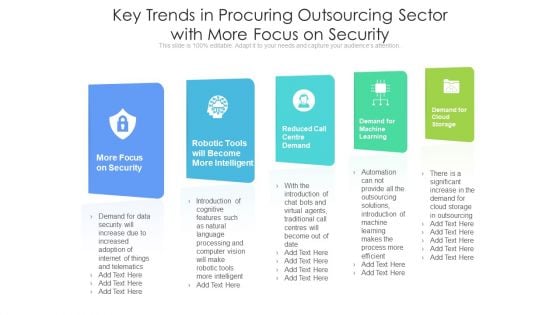
Key Trends In Procuring Outsourcing Sector With More Focus On Security Ppt Gallery Smartart PDF
Persuade your audience using this key trends in procuring outsourcing sector with more focus on security ppt gallery smartart pdf.This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including demand for machine learning, demand for cloud storage. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
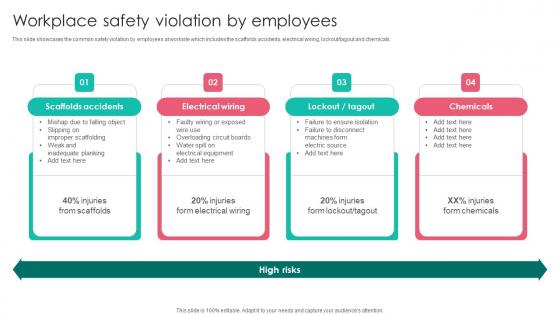
Workplace Safety Violation By Employees Workplace Safety Protocol And Security Practices Demonstration Pdf
This slide showcases the common safety violation by employees at worksite which includes the scaffolds accidents, electrical wiring, lockout tagout and chemicals. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Workplace Safety Violation By Employees Workplace Safety Protocol And Security Practices Demonstration Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Workplace Safety Violation By Employees Workplace Safety Protocol And Security Practices Demonstration Pdf today and make your presentation stand out from the rest This slide showcases the common safety violation by employees at worksite which includes the scaffolds accidents, electrical wiring, lockout tagout and chemicals.
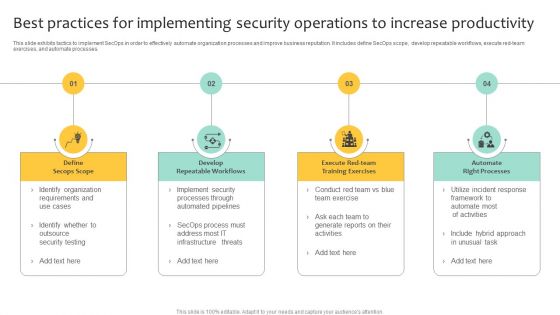
Best Practices For Implementing Security Operations To Increase Productivity Clipart PDF
This slide exhibits tactics to implement SecOps in order to effectively automate organization processes and improve business reputation. It includes define SecOps scope, develop repeatable workflows, execute red-team exercises, and automate processes. Presenting Best Practices For Implementing Security Operations To Increase Productivity Clipart PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Develop Repeatable Workflows, Automate Right Processes, Define Secops Scope. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
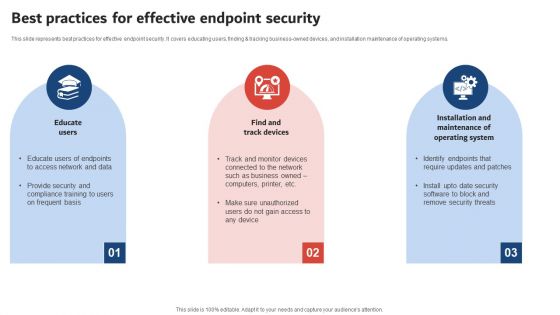
Execution Of ICT Strategic Plan Best Practices For Effective Endpoint Security Demonstration PDF
This slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business owned devices, and installation maintenance of operating systems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Execution Of ICT Strategic Plan Best Practices For Effective Endpoint Security Demonstration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Implementing Cyber Security Incident Best Practices For Cybersecurity Incident Guidelines PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Implementing Cyber Security Incident Best Practices For Cybersecurity Incident Guidelines PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Key Elements Of IT Security Awareness Training Program Ppt Model Example PDF
This slide covers key elements of cybersecurity awareness training program. It involves elements such as make message relevant, use real world examples, common language, present small messages and use continued reinforcement. Presenting Key Elements Of IT Security Awareness Training Program Ppt Model Example PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Make Message Relevant, Use Examples, Use Common Language. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
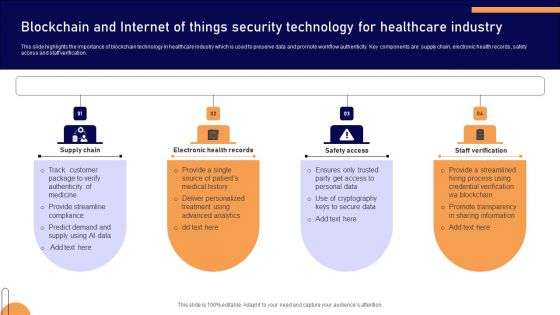
Blockchain And Internet Of Things Security Technology For Healthcare Industry Mockup PDF
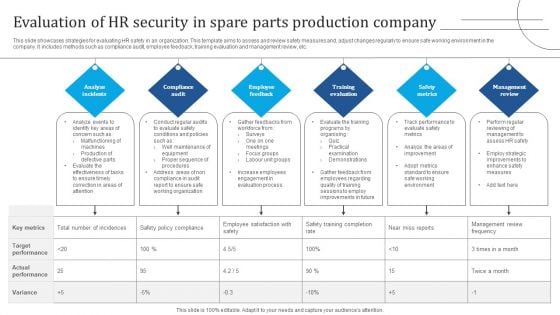
Evaluation Of HR Security In Spare Parts Production Company Demonstration PDF
This slide showcases strategies for evaluating HR safety in an organization. This template aims to assess and review safety measures and, adjust changes regularly to ensure safe working environment in the company. It includes methods such as compliance audit, employee feedback, training evaluation and management review, etc. Presenting Evaluation Of HR Security In Spare Parts Production Company Demonstration PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Analyze Incidents, Compliance Audit, Employee Feedback. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
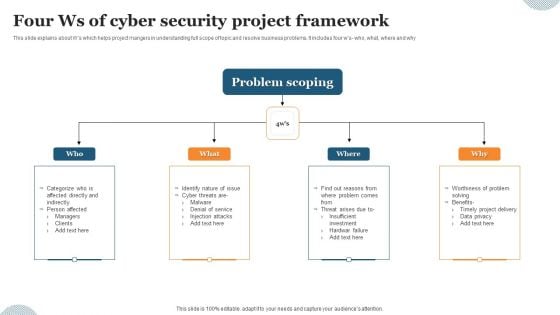
Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF
This slide explains about Ws which helps project mangers in understanding full scope of topic and resolve business problems. It includes four ws- who, what, where and why. Presenting Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Problem Scoping, Denial Service, Injection Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF
This slide describes how SDN can help with intent based networking, which comprises many components, and it gives network managers the freedom to explain their expectations from the network. IBN SDN aims to attain even higher levels of functional clarity, computerized intelligence, and closed loop functionality. Explore a selection of the finest SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
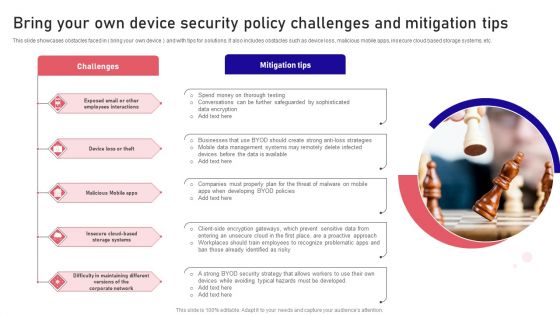
Bring Your Own Device Security Policy Challenges And Mitigation Tips Designs PDF
This slide showcases obstacles faced in bring your own device and with tips for solutions. It also includes obstacles such as device loss, malicious mobile apps, insecure cloud based storage systems, etc. Presenting Bring Your Own Device Security Policy Challenges And Mitigation Tips Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Challenges, Mitigation Tips, Malicious Mobile. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
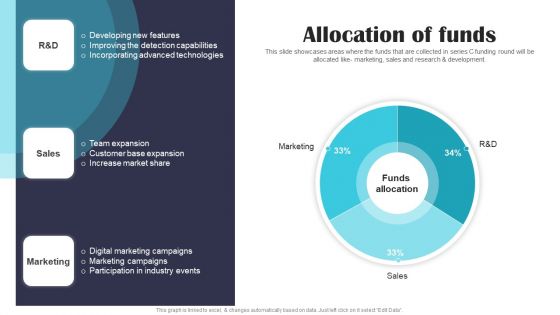
Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF
This slide showcases areas where the funds that are collected in series C funding round will be allocated like- marketing, sales and research and development. If you are looking for a format to display your unique thoughts, then the professionally designed Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
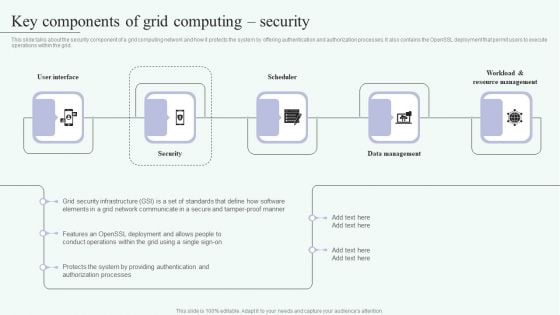
Grid Computing For High Performance Solutions Key Components Of Grid Computing Security Clipart PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Grid Computing For High Performance Solutions Key Components Of Grid Computing Security Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
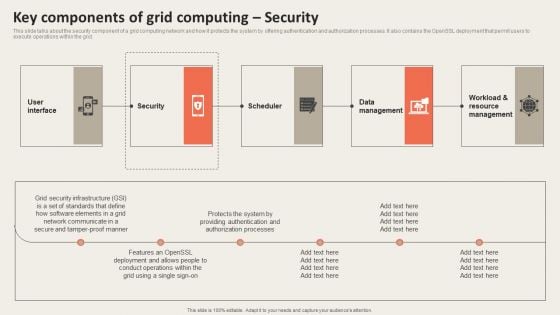
Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. This modern and well arranged Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
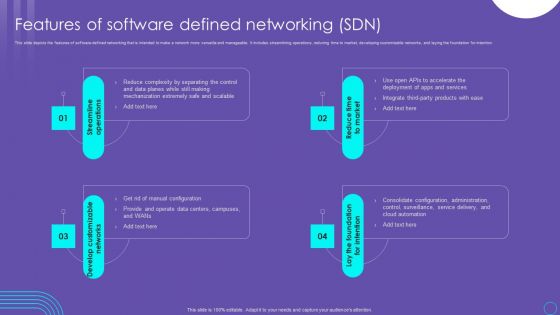
SDN Security Architecture Features Of Software Defined Networking SDN Infographics PDF
This slide depicts the features of software defined networking that is intended to make a network more versatile and manageable. It includes streamlining operations, reducing time to market, developing customizable networks, and laying the foundation for intention. This SDN Security Architecture Features Of Software Defined Networking SDN Infographics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The SDN Security Architecture Features Of Software Defined Networking SDN Infographics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
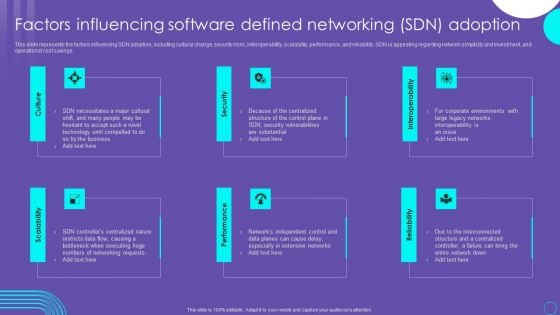
SDN Security Architecture Factors Influencing Software Defined Networking SDN Adoption Summary PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. This modern and well arranged SDN Security Architecture Factors Influencing Software Defined Networking SDN Adoption Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
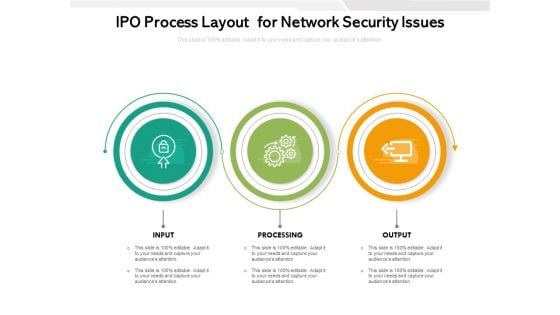
IPO Process Layout For Network Security Issues Ppt PowerPoint Presentation Outline Graphics Template PDF
Persuade your audience using this ipo process layout for network security issues ppt powerpoint presentation outline graphics template pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including processing, output, input. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides
Use this Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy eight slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.
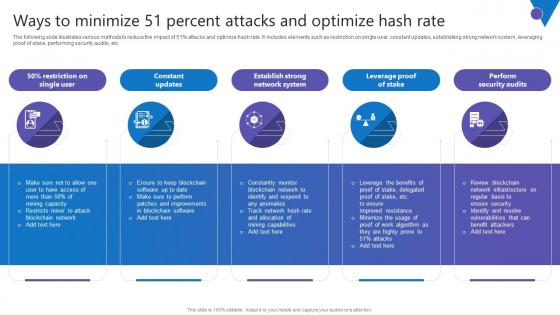
Ways To Minimize 51 Percent Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates various methods to reduce the impact of 51percent attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc. Present like a pro with Ways To Minimize 51 Percent Comprehensive Guide To Blockchain Digital Security Ideas Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The following slide illustrates various methods to reduce the impact of 51percent attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc.

Intelligent Manufacturing Role Of Cyber Security In Manufacturing Automation Ideas PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. This modern and well arranged Intelligent Manufacturing Role Of Cyber Security In Manufacturing Automation Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
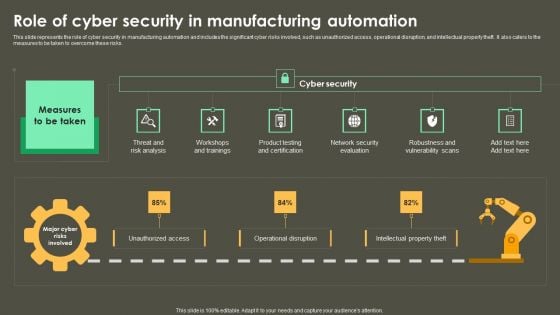
Iot Integration In Manufacturing Role Of Cyber Security In Manufacturing Automation Elements PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. This modern and well-arranged Iot Integration In Manufacturing Role Of Cyber Security In Manufacturing Automation Elements PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
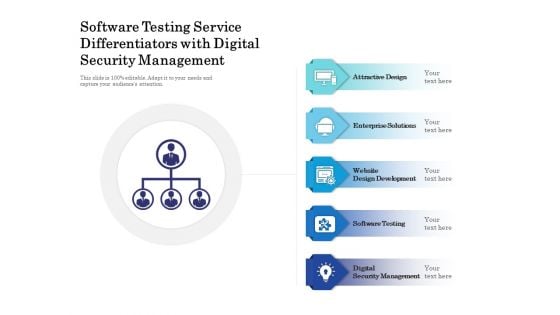
Software Testing Service Differentiators With Digital Security Management Ppt PowerPoint Presentation File Graphics Download PDF
Persuade your audience using this software testing service differentiators with digital security management ppt powerpoint presentation file graphics download pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including attractive design, enterprise solutions, software testing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
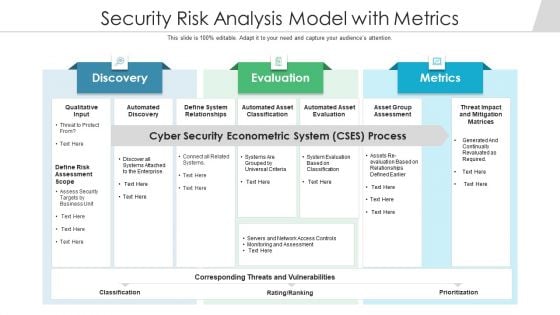
Security Risk Analysis Model With Metrics Ppt PowerPoint Presentation Outline Designs PDF
Persuade your audience using this security risk analysis model with metrics ppt powerpoint presentation outline designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including automated discovery, define system relationships, automated asset classification. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
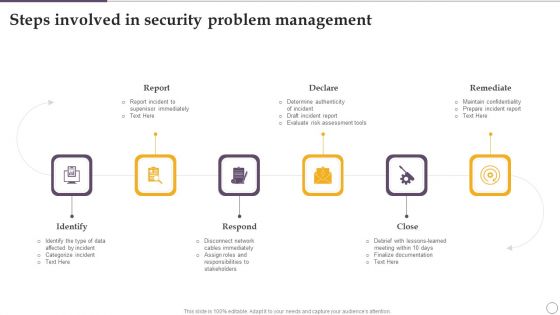
Steps Involved In Security Problem Management Ppt Inspiration Graphics Example PDF
Persuade your audience using this Steps Involved In Security Problem Management Ppt Inspiration Graphics Example PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Report, Declare, Remediate, Close, Respond, Identify. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
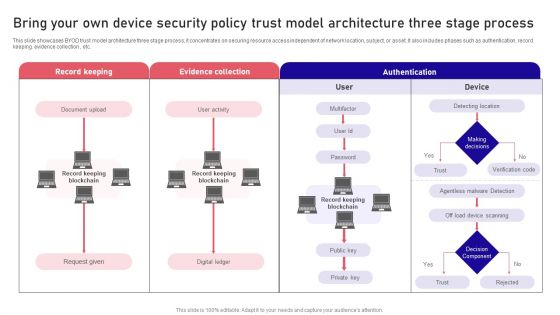
Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Corporate Security And Risk Management Financial Performance Tracking Dashboard Introduction PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver an awe inspiring pitch with this creative corporate security and risk management financial performance tracking dashboard introduction pdf bundle. Topics like revenue and expense trends, receivables analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Strategies To Mitigate Cyber Security Risks Cybersecurity Contingency Plan Business Impact Analysis Brochure PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity contingency plan business impact analysis brochure pdf. This is a three stage process. The stages in this process are determining vital it resources, determining issues impacts and acceptable outage time, assign recovery priorities, settlement agreements, litigation files, department file cabinets. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Developing Firm Security Strategy Plan Evaluating Financial Practices In Firm Icons PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Deliver an awe inspiring pitch with this creative developing firm security strategy plan evaluating financial practices in firm icons pdf bundle. Topics like evaluating financial practices in firm can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Security Administration In Organization Financial Performance Tracking Dashboard Microsoft PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization financial performance tracking dashboard microsoft pdf. Use them to share invaluable insights on financial performance tracking dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
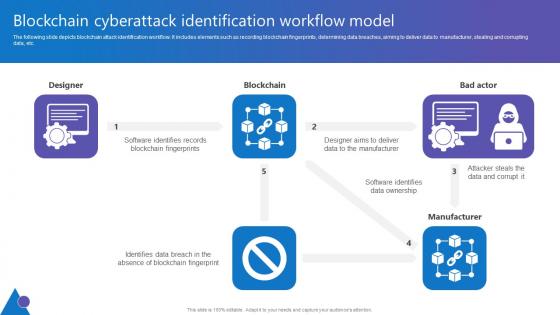
Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf
The following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Take your projects to the next level with our ultimate collection of Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc.

Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF
Slidegeeks has constructed Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Table Of Contents For Series Of Cyber Security Attacks Against Ukraine 2022 Website Template PDF
Retrieve professionally designed Table Of Contents For Series Of Cyber Security Attacks Against Ukraine 2022 Website Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
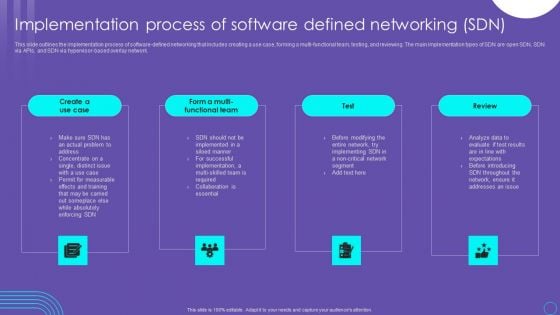
SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF
This slide outlines the implementation process of software defined networking that includes creating a use case, forming a multi functional team, testing, and reviewing. The main implementation types of SDN are open SDN, SDN via APIs, and SDN via hypervisor based overlay network. The SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Key Statistics Associated Comprehensive Guide To Blockchain Digital Security Topics Pdf
The following slide depicts key facts related with blockchain frauds to ensure secure transactions. It includes elements such as hacking of decentralized finance, stolen funds, fraudulent schemes, cryptocurrency scams, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Key Statistics Associated Comprehensive Guide To Blockchain Digital Security Topics Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide depicts key facts related with blockchain frauds to ensure secure transactions. It includes elements such as hacking of decentralized finance, stolen funds, fraudulent schemes, cryptocurrency scams, etc.

Series Of Cyber Security Attacks Against Ukraine 2022 Ppt PowerPoint Presentation Complete With Slides
People are consistently online to look for new ways to start a business or make money. What better than impressing that target audience with your Series Of Cyber Security Attacks Against Ukraine 2022 Ppt PowerPoint Presentation Complete With Slides, with its relatable and valuable content. This sixty one slide complete deck will turn a mundane session into a power-packed wow level presentation that your prospects will love to revisit over and over. This actionable preset will cover the nuances of all business slides. You can populate the slides in this template with your content and share the file with the presentation attendees as well.


 Continue with Email
Continue with Email

 Home
Home


































