Information Security Roadmap
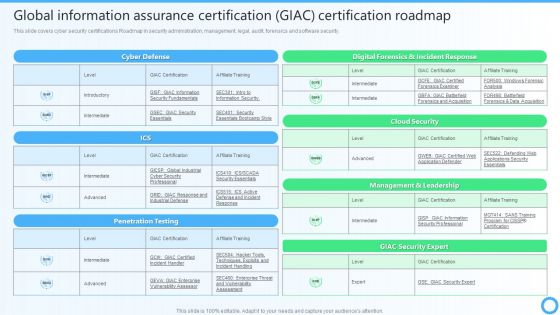
Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security.This Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
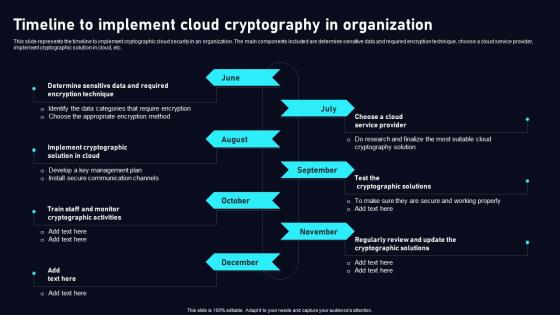
Timeline To Implement Cloud Data Security Using Cryptography Download Pdf
This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Timeline To Implement Cloud Data Security Using Cryptography Download Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.
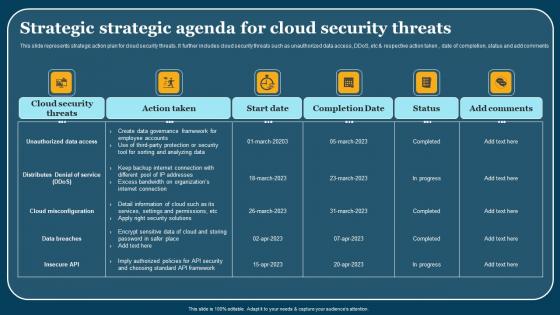
Strategic Strategic Agenda For Cloud Security Threats Ideas Pdf
This slide represents strategic action plan for cloud security threats. It further includes cloud security threats such as unauthorized data access, DDoS, etc and respective action taken , date of completion, status and add comments. Showcasing this set of slides titled Strategic Strategic Agenda For Cloud Security Threats Ideas Pdf. The topics addressed in these templates are Cloud Security Threats, Action Taken, Start Date. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents strategic action plan for cloud security threats. It further includes cloud security threats such as unauthorized data access, DDoS, etc and respective action taken , date of completion, status and add comments.

It Security Training Courses Strategic Agenda To Employees Portrait Pdf
This slide represents action plan for various training courses. It includes training courses such as complete cyber security courses, etc and their description, mode, duration, and budget. Showcasing this set of slides titled It Security Training Courses Strategic Agenda To Employees Portrait Pdf. The topics addressed in these templates are Training Courses, Description, Trainer Name. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan for various training courses. It includes training courses such as complete cyber security courses, etc and their description, mode, duration, and budget.
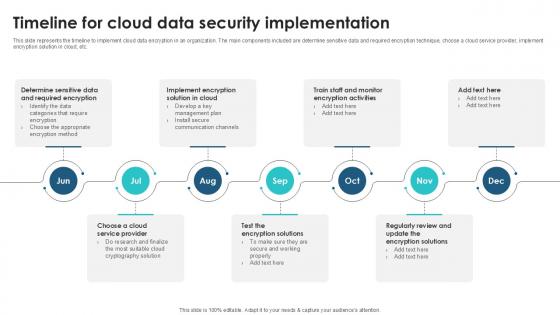
Timeline For Cloud Data Security Client Side Encryption PPT Example
This slide represents the timeline to implement cloud data encryption in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc. Slidegeeks has constructed Timeline For Cloud Data Security Client Side Encryption PPT Example after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the timeline to implement cloud data encryption in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc.
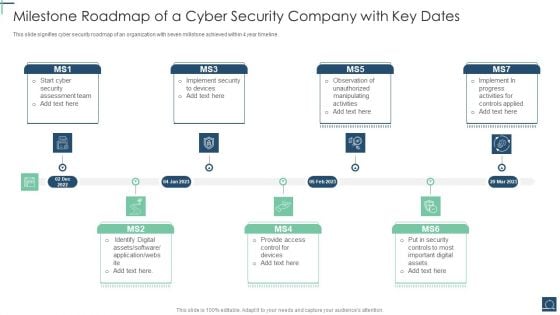
Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF
This slide signifies cyber security roadmap of an organization with seven millstone achieved within 4 year timeline. Persuade your audience using this Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Security Assessment Team, Identify Digital Assets, Provide Access Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
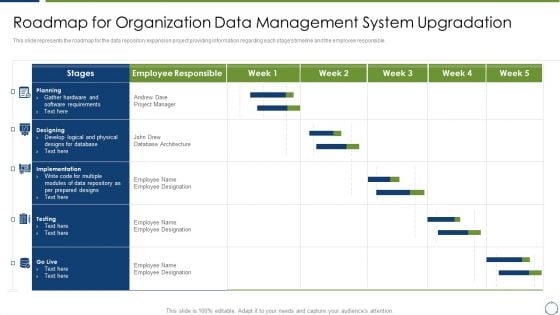
Horizontal Scaling Technique For Information Roadmap For Organization Data Management System Upgradation Rules PDF
This slide represents the roadmap for the data repository expansion project providing information regarding each stages timeline and the employee responsible. Deliver an awe inspiring pitch with this creative Horizontal Scaling Technique For Information Roadmap For Organization Data Management System Upgradation Rules PDF bundle. Topics like Requirement Analyst, Hardware Engineer, Information Security Engineer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Timeline Food Security Excellence Ppt Model Images PDF
This is a timeline food security excellence ppt model images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2018 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Risk Management Plan Timeline Portrait PDF
This is a cyber security risk management plan timeline portrait pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2016 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Developing Firm Security Strategy Plan Timeline Rules PDF
This is a developing firm security strategy plan timeline rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2017 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Organizational Network Security Awareness Staff Learning Timeline Download PDF
This is a organizational network security awareness staff learning timeline download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2018 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Financing Catalogue For Security Underwriting Agreement Timeline Ideas PDF
This is a financing catalogue for security underwriting agreement timeline ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2017 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
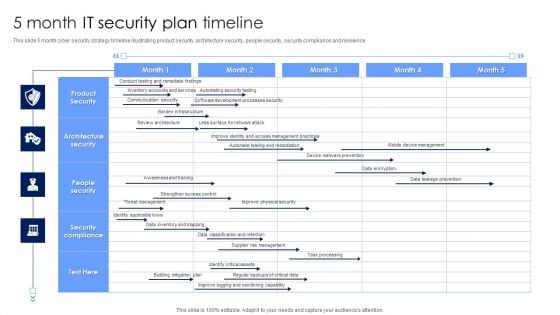
5 Month IT Security Plan Timeline Pictures PDF
This slide 5 month cyber security strategy timeline illustrating product security, architecture security, people security, security compliance and resilience. Showcasing this set of slides titled 5 Month IT Security Plan Timeline Pictures PDF. The topics addressed in these templates are Architecture Security, People Security, Security Compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Timeline Hacking Prevention Awareness Training For IT Security Brochure PDF
Presenting timeline hacking prevention awareness training for it security brochure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like timeline, 2016 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Timeline Cloud Computing Security IT Ppt Layouts Slide Portrait PDF
Presenting timeline cloud computing security it ppt layouts slide portrait pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like timeline, 2015 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Workforce Security Realization Coaching Plan Timeline Ppt Summary Templates PDF
Presenting workforce security realization coaching plan timeline ppt summary templates pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like timeline, 2017 to 2021. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Implementing Security Management Strategy To Mitigate Risk Timeline Rules PDF
Presenting implementing security management strategy to mitigate risk timeline rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like timeline. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Critical Importance Of HR Security At Workplace Demonstration PDF
Showcasing this set of slides titled Critical Importance Of HR Security At Workplace Demonstration PDF. The topics addressed in these templates are Critical Importance, HR Security Workplace. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Crisis Management Action Plan Timeline Topics PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Crisis Management Action Plan Timeline Topics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Crisis Management Action Plan Timeline Topics PDF
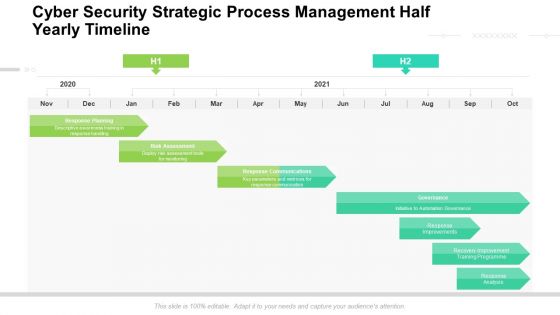
Cyber Security Strategic Process Management Half Yearly Timeline Rules
Presenting our innovatively structured cyber security strategic process management half yearly timeline rules Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
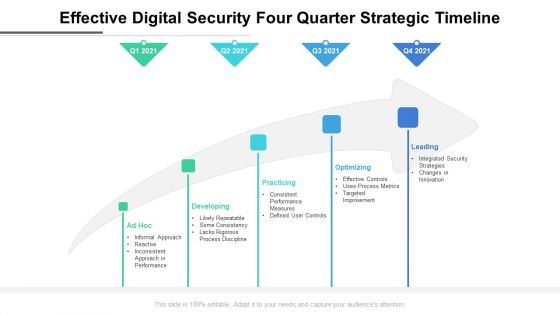
Effective Digital Security Four Quarter Strategic Timeline Elements
Presenting our innovatively structured effective digital security four quarter strategic timeline elements Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
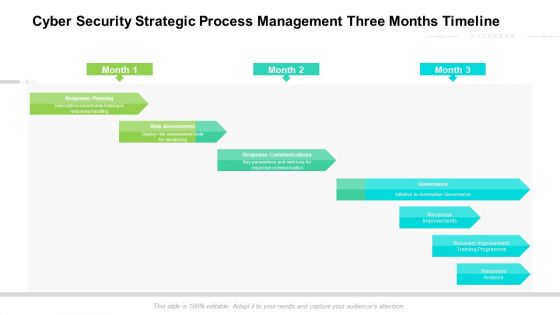
Cyber Security Strategic Process Management Three Months Timeline Introduction
Presenting the cyber security strategic process management three months timeline introduction. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
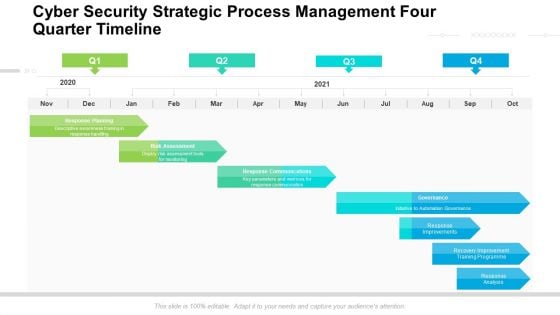
Cyber Security Strategic Process Management Four Quarter Timeline Diagrams
We present our cyber security strategic process management four quarter timeline diagrams. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security strategic process management four quarter timeline diagrams in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
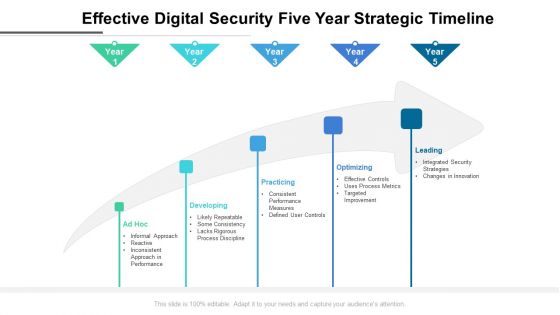
Effective Digital Security Five Year Strategic Timeline Formats
We present our effective digital security five year strategic timeline formats. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched effective digital security five year strategic timeline formats in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cyber Security Strategic Process Management Six Months Timeline Structure
Introducing our cyber security strategic process management six months timeline structure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Effective Digital Security Half Yearly Strategic Timeline Download
Introducing our effective digital security half yearly strategic timeline download. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

30 60 90 Days Plan To Implement Cloud Security In Business Cloud Computing Security IT Ppt Gallery Master Slide PDF
This slide defines the 30,60 and 90 days plan to implement cloud security in the organization and what tasks would be performed on each 30 days interval. This is a 30 60 90 days plan to implement cloud security in business cloud computing security it ppt gallery master slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like performed, analyze, cloud services, data access policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Email Security Encryption And Data Loss Prevention Timeline Template PDF
This is a email security encryption and data loss prevention timeline template pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2013 to 2020. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
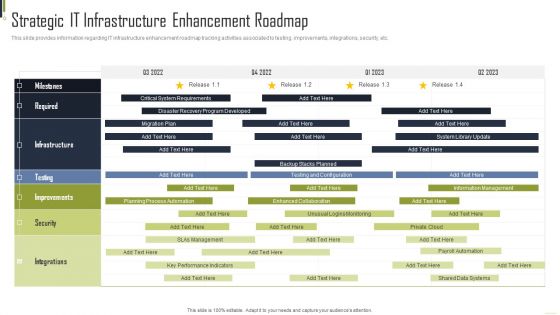
Strategic IT Infrastructure Enhancement Roadmap Playbook For Information Technology Download PDF
This slide provides information regarding IT infrastructure enhancement roadmap tracking activities associated to testing, improvements, integrations, security, etc. Deliver an awe inspiring pitch with this creative Strategic IT Infrastructure Enhancement Roadmap Playbook For Information Technology Download PDF bundle. Topics like Planning Process, Improvements, Integrations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Playbook For Managing Information Strategic IT Infrastructure Enhancement Roadmap Microsoft PDF
This slide provides information regarding IT infrastructure enhancement roadmap tracking activities associated to testing, improvements, integrations, security, etc. Deliver and pitch your topic in the best possible manner with this Playbook For Managing Information Strategic IT Infrastructure Enhancement Roadmap Microsoft PDF. Use them to share invaluable insights on Critical System Requirements, Planning Process, System Library and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Damage Security Insurance Proposal Timeline Ppt Summary Vector PDF
Presenting damage security insurance proposal timeline ppt summary vector pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like timeline, 2016 to 2020. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Workforce Security Realization Coaching Plan Location Ppt Diagram Lists PDF
Presenting workforce security realization coaching plan location ppt diagram lists pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topic like location. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Best Data Security Software 30 60 90 Days Plan For Company Online Database Security Proposal Sample PDF
Presenting this set of slides with name best data security software 30 60 90 days plan for company online database security proposal sample pdf. This is a three stage process. The stages in this process are 30 60 90 days plan, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
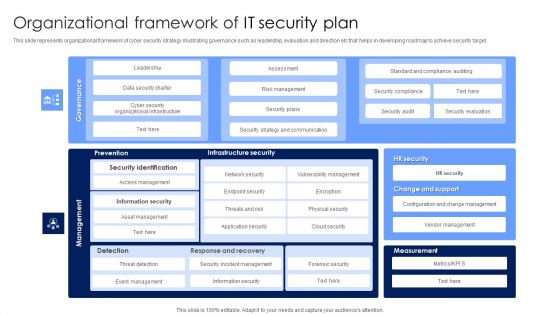
Organizational Framework Of IT Security Plan Microsoft PDF
This slide represents organizational framework of cyber security strategy illustrating governance such as leadership, evaluation and direction etc that helps in developing roadmap to achieve security target. Showcasing this set of slides titled Organizational Framework Of IT Security Plan Microsoft PDF. The topics addressed in these templates are Infrastructure Security, Management, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
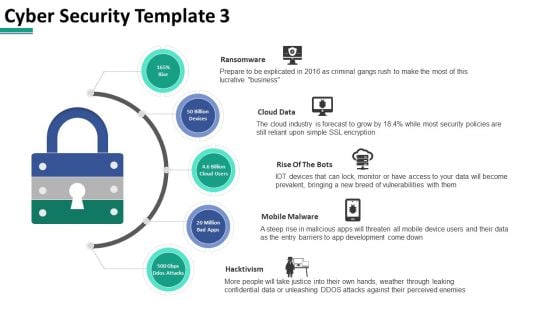
Cyber Security Cloud Data Ppt PowerPoint Presentation Summary Graphics Download
This is a cyber security cloud data ppt powerpoint presentation summary graphics download. This is a five stage process. The stages in this process are business, lock, planning, strategy, marketing, security.
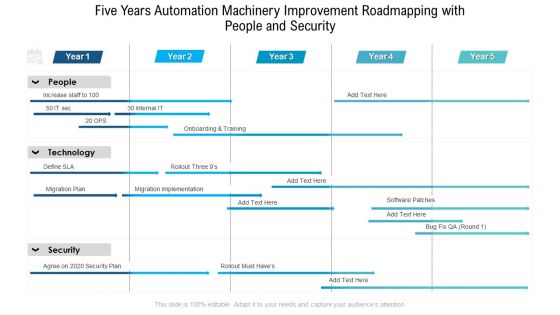
Five Years Automation Machinery Improvement Roadmapping With People And Security Download
Presenting our innovatively structured five years automation machinery improvement roadmapping with people and security download Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
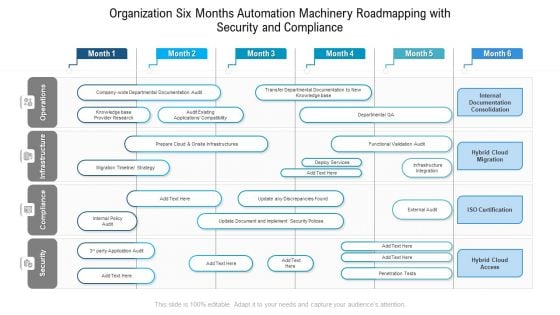
Organization Six Months Automation Machinery Roadmapping With Security And Compliance Summary
Presenting our innovatively structured organization six months automation machinery roadmapping with security and compliance summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
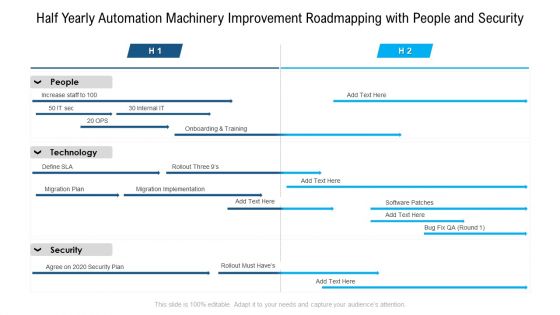
Half Yearly Automation Machinery Improvement Roadmapping With People And Security Topics
We present our half yearly automation machinery improvement roadmapping with people and security topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly automation machinery improvement roadmapping with people and security topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
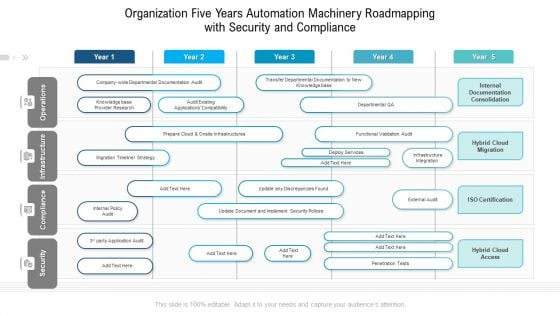
Organization Five Years Automation Machinery Roadmapping With Security And Compliance Diagrams
Presenting the organization five years automation machinery roadmapping with security and compliance diagrams. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
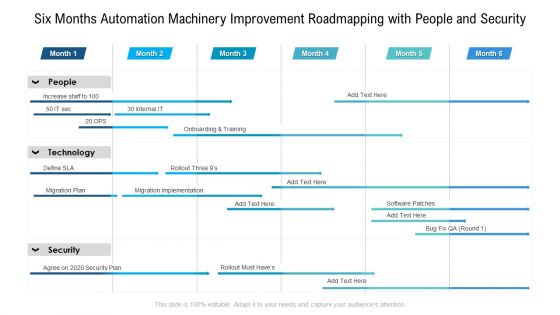
Six Months Automation Machinery Improvement Roadmapping With People And Security Brochure
Presenting the six months automation machinery improvement roadmapping with people and security brochure. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
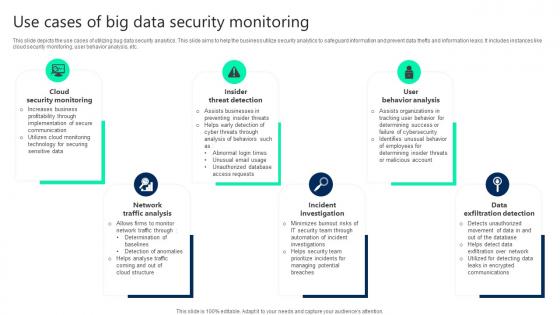
Use Cases Of Big Data Security Monitoring Clipart pdf
This slide depicts the use cases of utilizing bug data security analytics. This slide aims to help the business utilize security analytics to safeguard information and prevent data thefts and information leaks. It includes instances like cloud security monitoring, user behavior analysis, etc. Pitch your topic with ease and precision using this Use Cases Of Big Data Security Monitoring Clipart pdf. This layout presents information on Cloud Security Monitoring, Insider Threat Detection, User Behavior Analysis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the use cases of utilizing bug data security analytics. This slide aims to help the business utilize security analytics to safeguard information and prevent data thefts and information leaks. It includes instances like cloud security monitoring, user behavior analysis, etc.
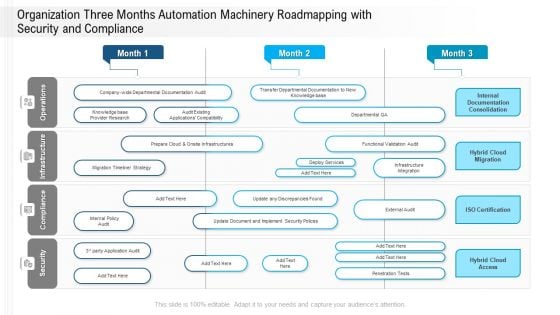
Organization Three Months Automation Machinery Roadmapping With Security And Compliance Rules
Introducing our organization three months automation machinery roadmapping with security and compliance rules. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
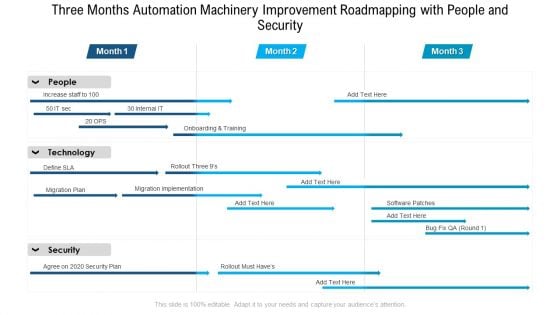
Three Months Automation Machinery Improvement Roadmapping With People And Security Designs
Introducing our three months automation machinery improvement roadmapping with people and security designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

National Security France PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our National Security France PowerPoint Templates PPT Backgrounds For Slides 0113.Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Download and present our Business PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there. Use our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides help you meet the demand of the Market. Just browse and pick the slides that appeal to your intuitive senses. Present our Signs PowerPoint Templates because They will Put your wonderful verbal artistry on display. Our PowerPoint Templates and Slides will provide you the necessary glam and glitter.Use these PowerPoint slides for presentations relating to Key with french flag, security, success, business, shapes, signs. The prominent colors used in the PowerPoint template are Blue navy, White, Red. We assure you our National Security France PowerPoint Templates PPT Backgrounds For Slides 0113 will make the presenter successul in his career/life. Professionals tell us our security PowerPoint templates and PPT Slides will save the presenter time. We assure you our National Security France PowerPoint Templates PPT Backgrounds For Slides 0113 look good visually. The feedback we get is that our security PowerPoint templates and PPT Slides are incredible easy to use. Customers tell us our National Security France PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. Customers tell us our french PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. Say farewell to uncertainties with our National Security France PowerPoint Templates Ppt Backgrounds For Slides 0113. They help ensure desired results.

Running Cyber Security Awareness Campaign For Employees Background PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Running Cyber Security Awareness Campaign For Employees Background PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
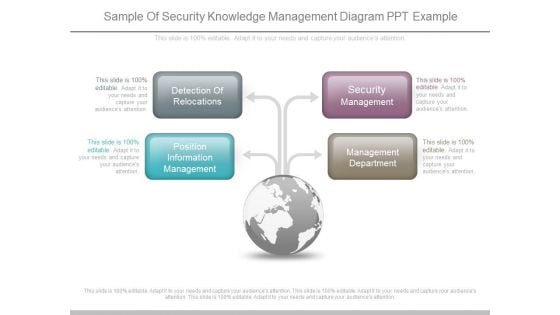
Sample Of Security Knowledge Management Diagram Ppt Example
This is a sample of security knowledge management diagram ppt example. This is a four stage process. The stages in this process are detection of relocations, position information management, security management, management department.
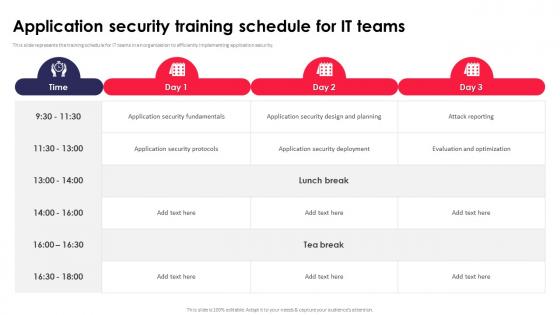
Application Security Training Schedule For IT Teams Ppt Powerpoint Portrait
This slide represents the training schedule for IT teams in an organization to efficiently implementing application security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Application Security Training Schedule For IT Teams Ppt Powerpoint Portrait will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the training schedule for IT teams in an organization to efficiently implementing application security.
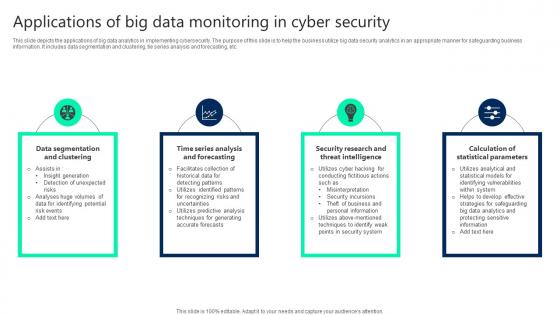
Applications Of Big Data Monitoring In Cyber Security Themes pdf
This slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc. Pitch your topic with ease and precision using this Applications Of Big Data Monitoring In Cyber Security Themes pdf. This layout presents information on Data Segmentation, Security Research, Threat Intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc.
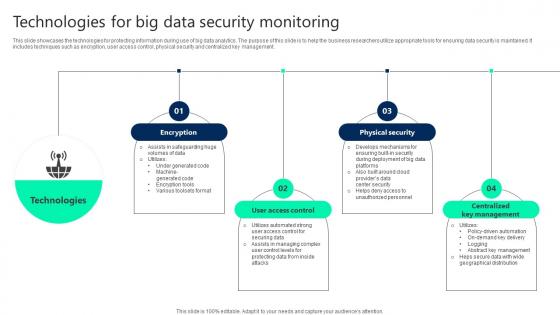
Technologies For Big Data Security Monitoring Summary pdf
This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management. Showcasing this set of slides titled Technologies For Big Data Security Monitoring Summary pdf. The topics addressed in these templates are User Access Control, Physical Security, Centralized Key Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management.

Table Of Contents For Zero Trust Network Security Introduction Pdf
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Table Of Contents For Zero Trust Network Security Introduction Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. Our Table Of Contents For Zero Trust Network Security Introduction Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
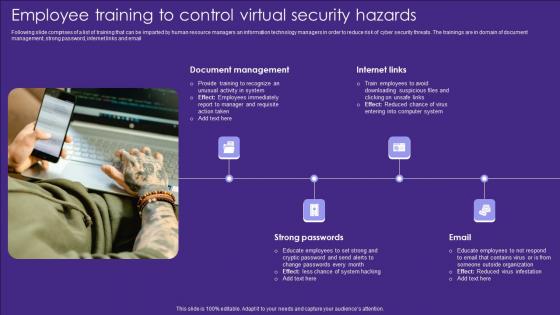
Employee Training To Control Virtual Security Hazards Designs Pdf
Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email Pitch your topic with ease and precision using this Employee Training To Control Virtual Security Hazards Designs Pdf. This layout presents information on Internet Links, Email, Strong Passwords. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email
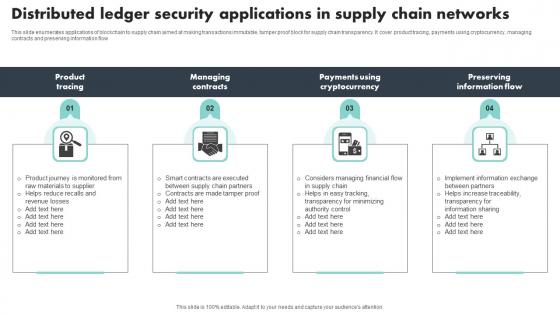
Distributed Ledger Security Applications In Supply Chain Networks Themes Pdf
This slide enumerates applications of blockchain to supply chain aimed at making transactions immutable, tamper proof block for supply chain transparency. It cover product tracing, payments using cryptocurrency, managing contracts and preserving information flow Pitch your topic with ease and precision using this Distributed Ledger Security Applications In Supply Chain Networks Themes Pdf This layout presents information on Product Tracing, Managing Contracts, Preserving Information Flow It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide enumerates applications of blockchain to supply chain aimed at making transactions immutable, tamper proof block for supply chain transparency. It cover product tracing, payments using cryptocurrency, managing contracts and preserving information flow

Security Measures To Prevent Phishing Attacks Ppt Gallery Deck PDF
This slide represents the security measures to prevent phishing attacks, such as using the spam filter, updating security software regularly, utilization of multi factor authentication, and so on. This is a security measures to prevent phishing attacks ppt gallery deck pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, organization, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
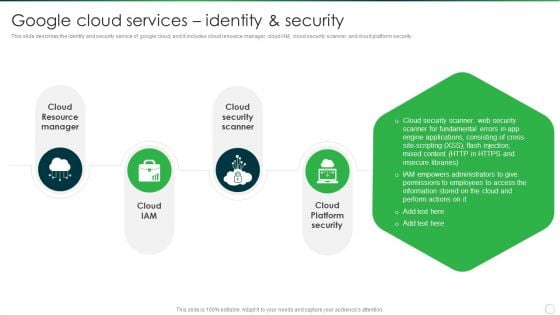
Google Cloud Services Identity And Security Graphics PDF
This slide describes the identity and security service of google cloud, and it includes cloud resource manager, cloud IAM, cloud security scanner, and cloud platform security. This is a Google Cloud Services Identity And Security Graphics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Resource Manager, Cloud Security Scanner, Cloud Platform Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
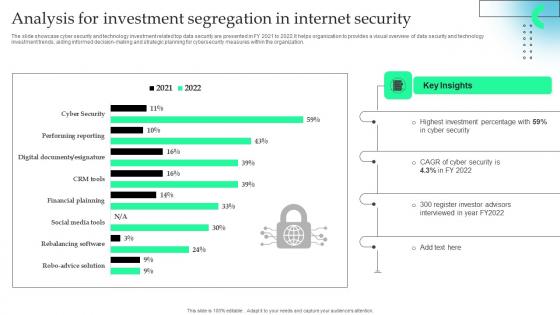
Analysis For Investment Segregation In Internet Security Formats Pdf
The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.Pitch your topic with ease and precision using this Analysis For Investment Segregation In Internet Security Formats Pdf This layout presents information on Highest Investment, Register Investor Advisors, Key Insights It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.
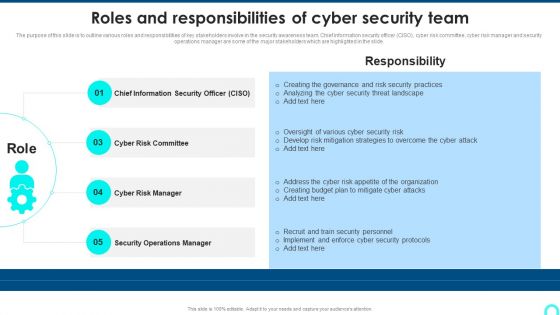
Roles And Responsibilities Of Cyber Security Team Designs PDF
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide.This is a Roles And Responsibilities Of Cyber Security Team Designs PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Chief Information, Operations Manager, Risk Manager . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Divisional Strategy To Improve Cyber Security Measures Icons PDF
This slide signifies information technology department to enhance cyber security measures. It also includes stages like identify, plan, execute and control. Presenting IT Divisional Strategy To Improve Cyber Security Measures Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Identify, Plan, Execute, Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Distributed Ledger Technology Impact On Data Security Infographics Pdf
This slide highlights impact on blockchain on data security aimed at reducing costs, increasing transparency, enhancing security and efficiency. It covers encryption and validation, decentralized data security with difficulties in hacking Pitch your topic with ease and precision using this Distributed Ledger Technology Impact On Data Security Infographics Pdf This layout presents information on Encryption And Validation, Decentralized Data Security, Difficulties In Hacking It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights impact on blockchain on data security aimed at reducing costs, increasing transparency, enhancing security and efficiency. It covers encryption and validation, decentralized data security with difficulties in hacking
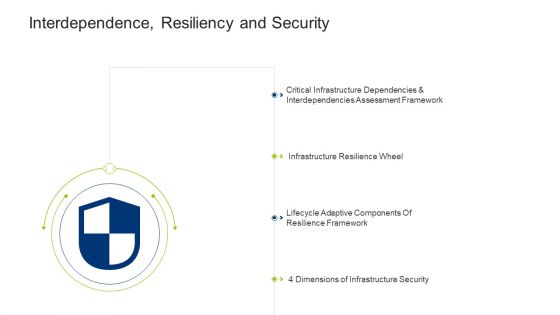
Infrastructure Building Administration Interdependence Resiliency And Security Microsoft PDF
This is a infrastructure building administration interdependence resiliency and security microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure resilience wheel, lifecycle adaptive components of resilience framework, 4 dimensions of infrastructure security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
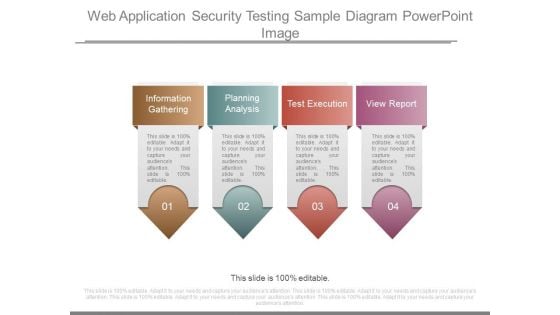
Web Application Security Testing Sample Diagram Powerpoint Image
This is a web application security testing sample diagram powerpoint image. This is a four stage process. The stages in this process are information gathering, planning analysis, test execution, view report.


 Continue with Email
Continue with Email

 Home
Home


































