Information Security Roadmap

Login Screen And Credit Card Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Computer PowerPoint Templates because you can Add colour to your speech with our PowerPoint Templates and Slides. Your presentation will leave your audience speechless. Use our Technology PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Present our Network Diagrams PowerPoint Templates because It can Bubble and burst with your ideas. Use our Security PowerPoint Templates because You can Stir your ideas in the cauldron of our PowerPoint Templates and Slides. Cast a magic spell on your audience. Download and present our Signs PowerPoint Templates because You can Raise a toast with our PowerPoint Templates and Slides. Spread good cheer amongst your audience.Use these PowerPoint slides for presentations relating to One notebook with a login screen and a credit card, computer, technology, network diagrams, security, signs. The prominent colors used in the PowerPoint template are Blue, Gray, White. You can be sure our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113 effectively help you save your valuable time. Use our screen PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. You can be sure our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113 are visually appealing. Customers tell us our with PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. People tell us our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113 are second to none. People tell us our credit PowerPoint templates and PPT Slides will make the presenter look like a pro even if they are not computer savvy. Evoke desires with our Login Screen And Credit Card Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Your thoughts will have them enraptured.

Laptop With Lock Folder Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Laptop With Lock Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides are Clear and concise. Use them and dispel any doubts your team may have. Download and present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides help you pinpoint your timelines. Highlight the reasons for your deadlines with their use. Use our Technology PowerPoint Templates because Watching this your Audience will Grab their eyeballs, they wont even blink. Use our Signs PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges.Use these PowerPoint slides for presentations relating to Laptop with lock folder, Security, Business, Shapes, Technology, Signs. The prominent colors used in the PowerPoint template are Yellow, Gray, Blue. PowerPoint presentation experts tell us our Laptop With Lock Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by professionals Use our lock PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. The feedback we get is that our Laptop With Lock Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113 are topically designed to provide an attractive backdrop to any subject. The feedback we get is that our Shapes PowerPoint templates and PPT Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. People tell us our Laptop With Lock Folder Security PowerPoint Templates PPT Backgrounds For Slides 0113 look good visually. Professionals tell us our Technology PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. Let them breathe in with our Laptop With Lock Folder Security PowerPoint Templates Ppt Backgrounds For Slides 0113. They will find your ideas easier to fathom.

Black Folder With Keys Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Black Folder With Keys Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan. Download our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Illuminate the road ahead to Pinpoint the important landmarks along the way. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides are created by a hardworking bunch of busybees. Always flitting around with solutions gauranteed to please.Use these PowerPoint slides for presentations relating to Black folder with keys, Security, Technology, Shapes, Business, Success. The prominent colors used in the PowerPoint template are Yellow, Blue, Black. Professionals tell us our Black Folder With Keys Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by professionals Professionals tell us our Business PowerPoint templates and PPT Slides look good visually. Use our Black Folder With Keys Security PowerPoint Templates PPT Backgrounds For Slides 0113 will impress their bosses and teams. PowerPoint presentation experts tell us our with PowerPoint templates and PPT Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Customers tell us our Black Folder With Keys Security PowerPoint Templates PPT Backgrounds For Slides 0113 will save the presenter time. Use our Success PowerPoint templates and PPT Slides will get their audience's attention. Achievestrong & sustainable performance gains with our Black Folder With Keys Security PowerPoint Templates Ppt Backgrounds For Slides 0113. They will make you look good.

Dollars Chained And Locked Crisis Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Dollars Chained And Locked Crisis Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Money PowerPoint Templates because It will Strengthen your hand with your thoughts. They have all the aces you need to win the day. Download our Chains PowerPoint Templates because You have a driving passion to excel in your field. Our PowerPoint Templates and Slides will prove ideal vehicles for your ideas. Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need. Download and present our Signs PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download and present our Americana PowerPoint Templates because It can Conjure up grand ideas with our magical PowerPoint Templates and Slides. Leave everyone awestruck by the end of your presentation.Use these PowerPoint slides for presentations relating to Roll of US dollars chained and locked, money, chains, security, signs, americana. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. PowerPoint presentation experts tell us our Dollars Chained And Locked Crisis Security PowerPoint Templates PPT Backgrounds For Slides 0113 are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. Use our money PowerPoint templates and PPT Slides are visually appealing. People tell us our Dollars Chained And Locked Crisis Security PowerPoint Templates PPT Backgrounds For Slides 0113 are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. The feedback we get is that our US PowerPoint templates and PPT Slides look good visually. Professionals tell us our Dollars Chained And Locked Crisis Security PowerPoint Templates PPT Backgrounds For Slides 0113 are the best it can get when it comes to presenting. Presenters tell us our chained PowerPoint templates and PPT Slides are designed to make your presentations professional. Analyse your inputs with our Dollars Chained And Locked Crisis Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Discover ways to increase your output.

Golden Key On Keyboard Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Golden Key On Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides are innately eco-friendly. Their high recall value negate the need for paper handouts. Present our Technology PowerPoint Templates because Your audience will believe you are the cats whiskers. Download and present our Security PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides will provide weight to your words. They will bring out the depth of your thought process. Use our Business PowerPoint Templates because You have a driving passion to excel in your field. Our PowerPoint Templates and Slides will prove ideal vehicles for your ideas.Use these PowerPoint slides for presentations relating to Golden key on keyboard, technology, computer, security, success, business. The prominent colors used in the PowerPoint template are Yellow, Black, White. Achieve any feat you desire to. Our Golden Key On Keyboard Security PowerPoint Templates Ppt Backgrounds For Slides 0213 are extremely facilitating.

Padlock With Metallic Chain Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Padlock With Metallic Chain Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Security PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level. Present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides are created by a hardworking bunch of busybees. Always flitting around with solutions gauranteed to please. Download and present our Chains PowerPoint Templates because You aspire to touch the sky with glory. Let our PowerPoint Templates and Slides provide the fuel for your ascent. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence.Use these PowerPoint slides for presentations relating to Padlock with metal chain, security, signs, chains, business, success. The prominent colors used in the PowerPoint template are Yellow, Gray, White. Prepare your brigade with our Padlock With Metallic Chain Security PowerPoint Templates Ppt Backgrounds For Slides 0213. Get them ready for the battle for success.

Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF
This slide provides information about enhancing brand protection strategy by implementing anti counterfeiting measures in terms of overt security features, covert security features and serialization. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
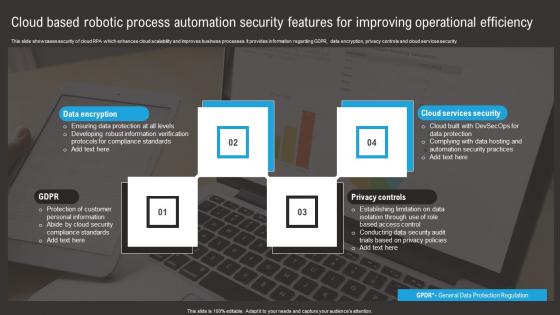
Cloud Based Robotic Process Automation Security Features For Improving Operational Efficiency Summary Pdf
This slide showcases security of cloud RPA which enhances cloud scalability and improves business processes. It provides information regarding GDPR, data encryption, privacy controls and cloud services security. Pitch your topic with ease and precision using this Cloud Based Robotic Process Automation Security Features For Improving Operational Efficiency Summary Pdf. This layout presents information on Data Encryption, Privacy Controls, Cloud Services Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases security of cloud RPA which enhances cloud scalability and improves business processes. It provides information regarding GDPR, data encryption, privacy controls and cloud services security.
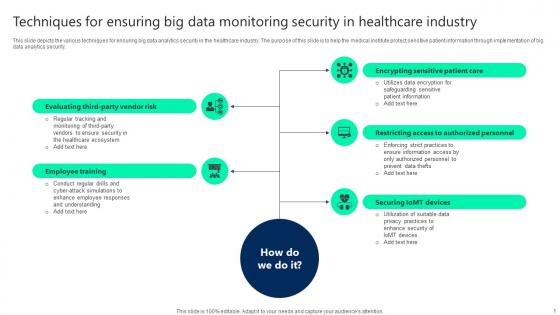
Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf
This slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security. Pitch your topic with ease and precision using this Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf. This layout presents information on Employee Training, Securing Iomt Devices, Restricting Access. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security.
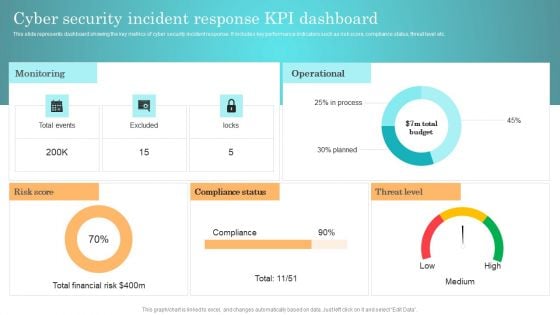
Incident Response Techniques Deployement Cyber Security Incident Response KPI Dashboard Background PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

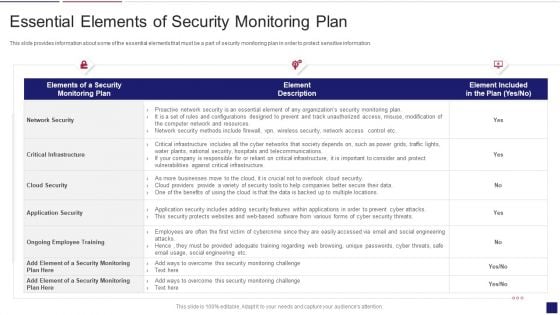
Methods To Develop Advanced Essential Elements Of Security Monitoring Plan Formats PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver and pitch your topic in the best possible manner with this methods to develop advanced essential elements of security monitoring plan formats pdf. Use them to share invaluable insights on network security, critical infrastructure, cloud security, application security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
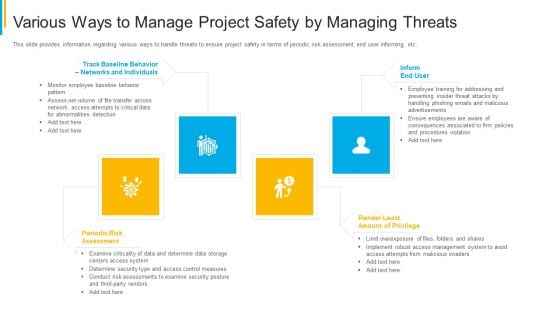
Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Designs PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Presenting project security administration it various ways to manage project safety by managing threats designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like track baseline behavior, networks and individuals, inform end user, periodic risk assessment, render least amount of privilege. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Continuous Development Evaluation Plan Eliminate Cyber Attacks Essential Elements Of Security Monitoring Elements PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks essential elements of security monitoring elements pdf bundle. Topics like network security, critical infrastructure, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
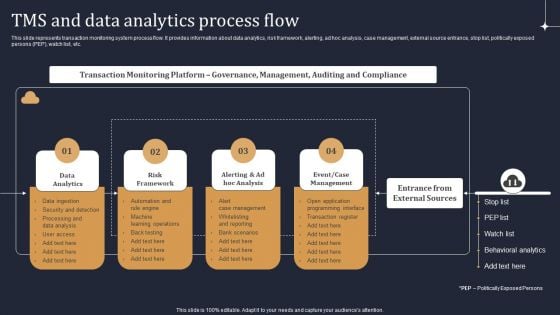
KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF
This slide represents transaction monitoring system process flow. It provides information about data analytics, risk framework, alerting, ad hoc analysis, case management, external source entrance, stop list, politically exposed persons PEP, watch list, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
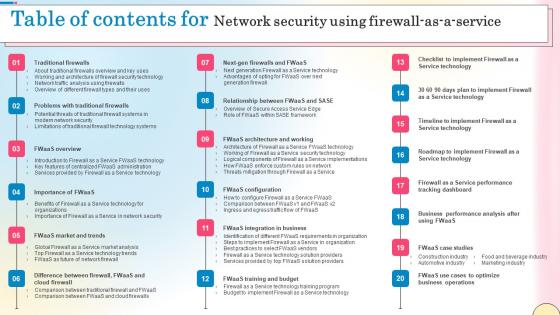
Table Of Contents For Network Security Using Firewall As A Service Guidelines Pdf
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Table Of Contents For Network Security Using Firewall As A Service Guidelines Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. Our Table Of Contents For Network Security Using Firewall As A Service Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF
This slide represents the schematic elements of software-defined networking, such as the northbound interface, SDN controller, and southbound interface. These components transmit the information throughout the SDN architecture. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

KYC Transaction Monitoring System Business Security Transaction Monitoring And Aml Training Plan Ideas PDF
The following slide represents training program for transaction monitoring and anti money laundering AML. It provides information about certification, assessment, compatibility, surveillance, operational efficiency, escalation, unusual transactions, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. KYC Transaction Monitoring System Business Security Transaction Monitoring And Aml Training Plan Ideas PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
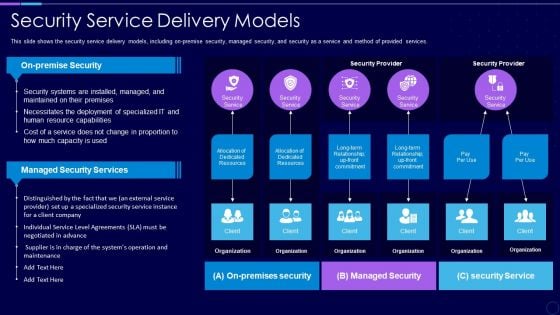
Everything As A Service Xaas For Cloud Computing IT Security Service Delivery Models Diagrams PDF
This slide shows the security service delivery models, including on-premise security, managed security, and security as a service and method of provided services. This is a everything as a service xaas for cloud computing it security service delivery models diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deployment, resource capabilities, security systems, security service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Functioning Centre Timeframe For Incident Management Ppt Slides Template PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. This is a security functioning centre timeframe for incident management ppt slides template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeframe for incident management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Market Trends Inspiration PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. This is a modern security observation plan to eradicate cybersecurity risk and data breach current market trends inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like increasing digitization of sensitive data, outsourcing, general data protection laws. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT System Risk Management Guide Security Criteria And Control Measures For IT System Vulnerabilities Icons PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. The IT System Risk Management Guide Security Criteria And Control Measures For IT System Vulnerabilities Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
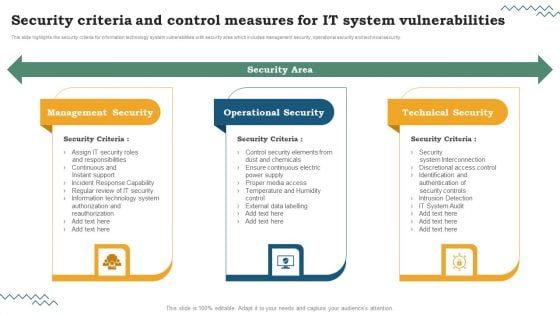
Software Development Life Cycle Planning Security Criteria And Control Measures For IT System Vulnerabilities Brochure PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. The Software Development Life Cycle Planning Security Criteria And Control Measures For IT System Vulnerabilities Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Dollar Under Protection Financial Security PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Dollar Under Protection Financial Security PowerPoint Templates PPT Backgrounds For Slides 0313.Download and present our Money PowerPoint Templates because It can Bubble and burst with your ideas. Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will definately Enhance the stature of your presentation. Adorn the beauty of your thoughts with their colourful backgrounds. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Download and present our Signs PowerPoint Templates because They will Put the wind in your sails. Skim smoothly over the choppy waters of the market. Present our Umbrellas PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues.Use these PowerPoint slides for presentations relating to Dollar under the umbrella, money, signs, business, umbrellas, security . The prominent colors used in the PowerPoint template are Blue, Red, Black. Take your thoughts that extra mile. Express your dream with our Dollar Under Protection Financial Security PowerPoint Templates Ppt Backgrounds For Slides 0313.

Security And Process Integration How Firm Handle Insider Threats Template PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a security and process integration how firm handle insider threats template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan How Firm Handle Various Insider Threats At Workplace Elements PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a developing firm security strategy plan how firm handle various insider threats at workplace elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Training And Building Role Competencies Portrait PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. This is a security management plan steps in detail training and building role competencies portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management system, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Identifying Goals And Objectives Download PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, security, management, organizational, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
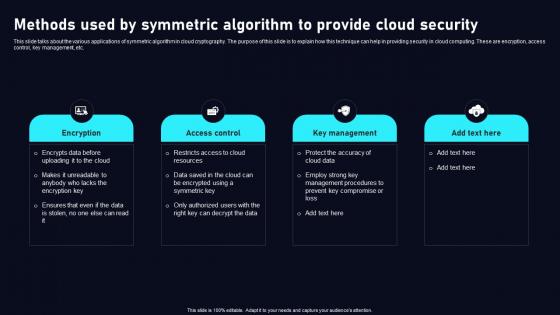
Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf
This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc.

Laptop Under Umbrella Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Laptop Under Umbrella Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Umbrellas PowerPoint Templates because You can Double your output with our PowerPoint Templates and Slides. They make beating deadlines a piece of cake. Present our Security PowerPoint Templates because You can Channelise the thoughts of your team with our PowerPoint Templates and Slides. Urge them to focus on the goals you have set. Download our Computer PowerPoint Templates because you can Set pulses racing with our PowerPoint Templates and Slides. They will raise the expectations of your team. Download and present our Network Diagrams PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium. Download and present our Signs PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time.Use these PowerPoint slides for presentations relating to Laptop computer under umbrella, umbrellas, security, computer, network diagrams, signs. The prominent colors used in the PowerPoint template are Red, Blue, Gray. Use our Laptop Under Umbrella Security PowerPoint Templates PPT Backgrounds For Slides 0113 have awesome images to get your point across. The feedback we get is that our security PowerPoint templates and PPT Slides are incredible easy to use. Customers tell us our Laptop Under Umbrella Security PowerPoint Templates PPT Backgrounds For Slides 0113 will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Customers tell us our network PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Presenters tell us our Laptop Under Umbrella Security PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Presenters tell us our computer PowerPoint templates and PPT Slides are designed by professionals Book you place at the top with our Laptop Under Umbrella Security PowerPoint Templates Ppt Backgrounds For Slides 0113. You will come out on top.
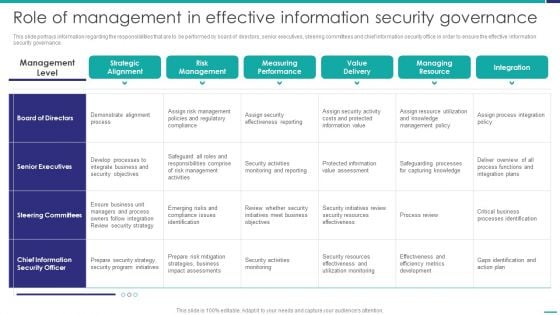
Role Of Management In Effective Governance Mobile Device Security Management Background PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Deliver and pitch your topic in the best possible manner with this Role Of Management In Effective Governance Mobile Device Security Management Background PDF. Use them to share invaluable insights on Senior Executives, Steering Committees, Effectiveness Reporting and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
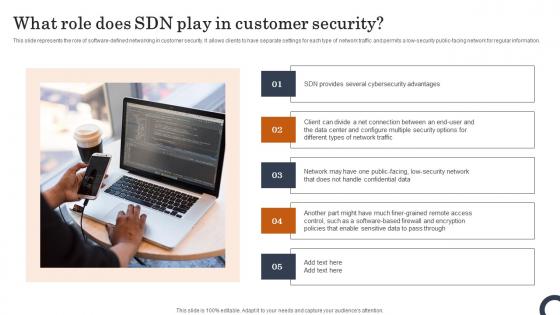
What Role Does SDN Play In Customer Security Evolution Of SDN Controllers Mockup Pdf
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. What Role Does SDN Play In Customer Security Evolution Of SDN Controllers Mockup Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information.

Cloud Based Email Security Market Report Industry Trends Ppt Styles Diagrams PDF
Major trends of the E mail security industry are shown in this slide. This is a cloud based email security market report industry trends ppt styles diagrams pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security system, artificial intelligence, supply chain security, security adaptive approach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
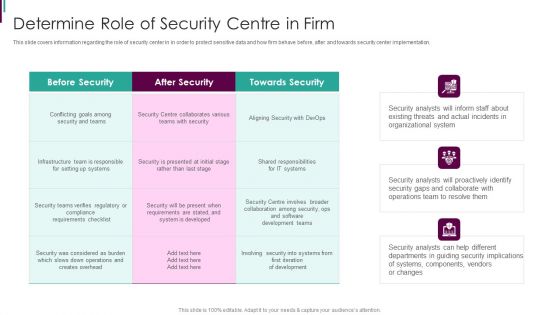
Developing Business Analytics Framework Determine Role Of Security Centre In Firm Brochure PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an awe inspiring pitch with this creative Developing Business Analytics Framework Determine Role Of Security Centre In Firm Brochure PDF bundle. Topics like Before Security, After Security, Towards Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Development Company Pitch Deck Problems Faced By Companies Security Introduction PDF
This is a it development company pitch deck problems faced by companies security introduction pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like poor network security, backup issues, software concerns, qualified experience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
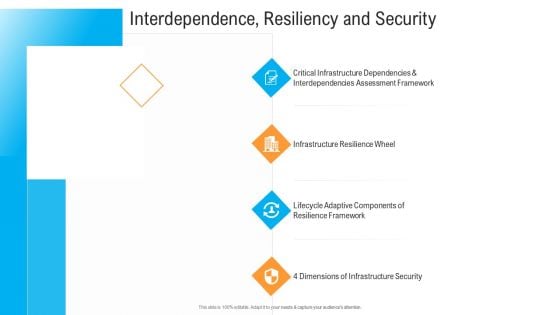
Civil Infrastructure Designing Services Management Interdependence Resiliency And Security Background PDF
This is a civil infrastructure designing services management interdependence resiliency and security background pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interdependence, resiliency and security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
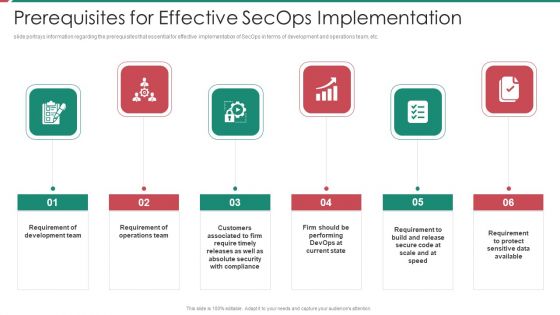
Security And Process Integration Prerequisites For Effective Secops Implementation Microsoft PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a security and process integration prerequisites for effective secops implementation microsoft pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Risk Assessment And Analysis Template PDF
This is a security management plan steps in detail risk assessment and analysis template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential consequence, security risks or liabilities, management to educate You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
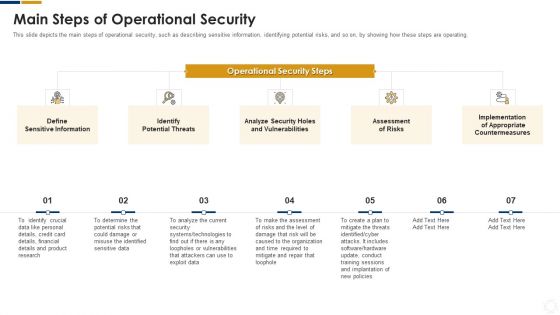
Cybersecurity Main Steps Of Operational Security Ppt Infographic Template Topics PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. This is a cybersecurity main steps of operational security ppt infographic template topics pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine, potential, risks, technologies, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
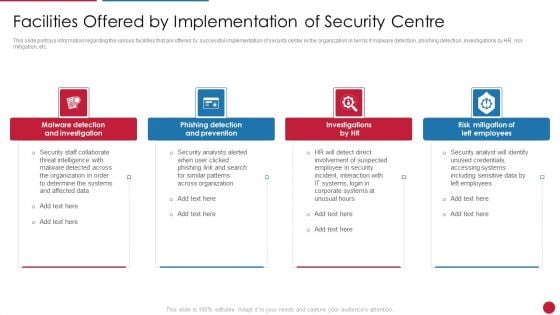
Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Phishing Detection And Prevention, Risk Mitigation Of Left You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security Functioning Centre Various Metrics To Measure Secops System Performance Icons PDF
This slide portrays information regarding the various metrics that considered in order to assess SecOps system performance such as mean time to detection, mean time to resolution, total cases per month, etc. This is a security functioning centre various metrics to measure secops system performance icons pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security analysts productivity, escalation breakdown, average time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
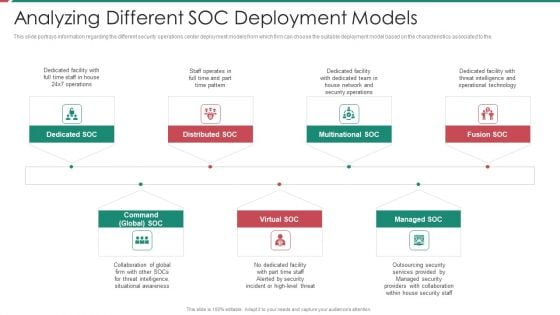
Security And Process Integration Analyzing Different SOC Deployment Models Diagrams PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a security and process integration analyzing different soc deployment models diagrams pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Implementing Safety Administration Initiative For Risk Mitigation Way To Overcome Security Demonstration PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide. This is a implementing safety administration initiative for risk mitigation way to overcome security demonstration pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like goals, information, risk, analysis, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc.
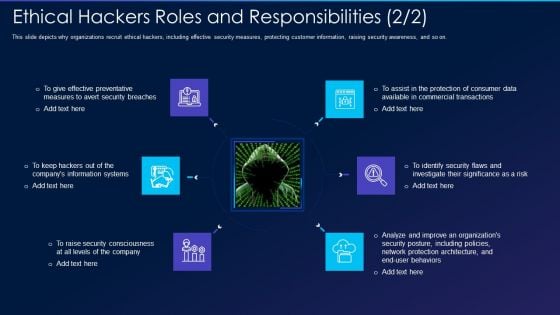
Cyber Exploitation IT Ethical Hackers Roles And Responsibilities Security Inspiration PDF
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on. Presenting cyber exploitation it ethical hackers roles and responsibilities security inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, organizations, analyze, measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Website Designing And Development Service Security Web Development Technique Themes PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Website Designing And Development Service Security Web Development Technique Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security, Content Security, Loopholes Or Shortcomings You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
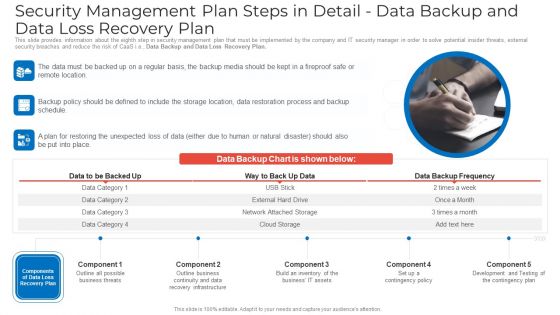
Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Ideas PDF
This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Data Backup and Data Loss Recovery Plan. This is a security management plan steps in detail data backup and data loss recovery plan ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail data backup and data loss recovery plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
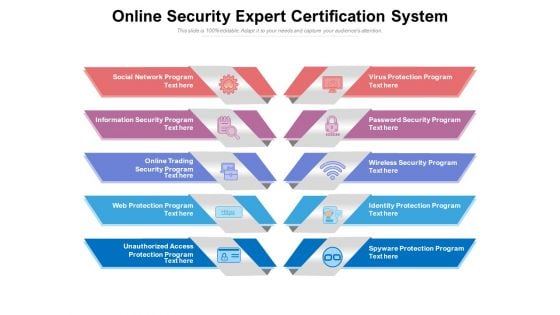
Online Security Expert Certification System Ppt PowerPoint Presentation Professional Themes PDF
Presenting this set of slides with name online security expert certification system ppt powerpoint presentation professional themes pdf. This is a ten stage process. The stages in this process are social network program, information security program, online trading security program, web protection program, unauthorized access protection program, virus protection program, password security program, wireless security program, identity protection program, spyware protection program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
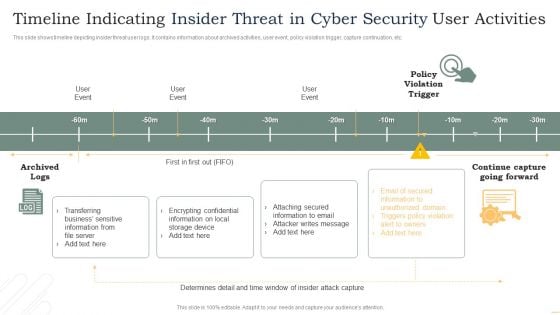
Timeline Indicating Insider Threat In Cyber Security User Activities Microsoft PDF
This slide shows timeline depicting insider threat user logs. It contains information about archived activities, user event, policy violation trigger, capture continuation, etc. Pitch your topic with ease and precision using this Timeline Indicating Insider Threat In Cyber Security User Activities Microsoft PDF. This layout presents information on User Event, Policy Violation Trigger, Archived Logs. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Management Plan Steps In Detail Risk Assessment And Analysis Introduction PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis. Deliver an awe inspiring pitch with this creative security management plan steps in detail risk assessment and analysis introduction pdf bundle. Topics like information, system, risks, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
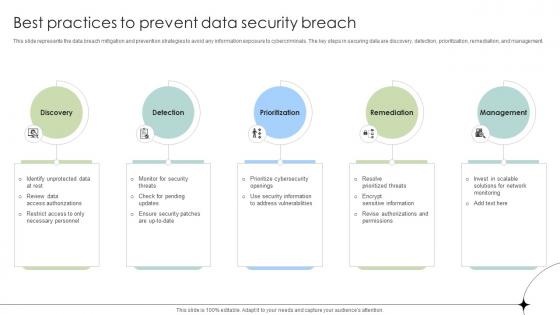
Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses
This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management.

Security Management Plan Steps In Detail System Maintenance And Monitoring Portrait PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. System Maintenance and Monitoring. This is a security management plan steps in detail system maintenance and monitoring portrait pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail system maintenance and monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
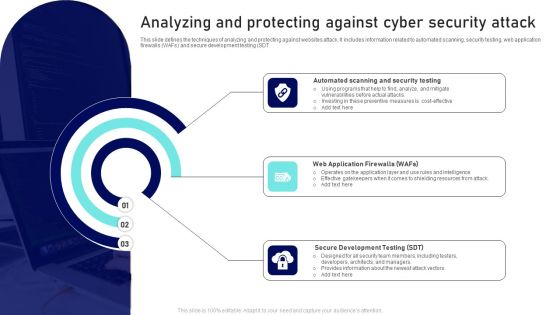
Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF
This slide defines the techniques of analyzing and protecting against websites attack. It includes information related to automated scanning, security testing, web application firewalls WAFs and secure development testing SDT. Presenting Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Web Application Firewalls, Secure Development Testing, Automated Scanning, Security Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Management Plan Steps In Detail Identifying Goals And Objectives Graphics PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives graphics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail identifying goals and objectives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf
This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc.
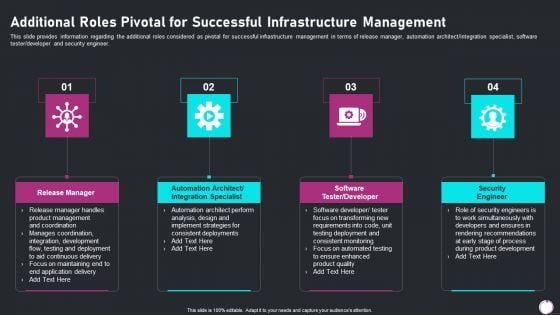
Information Technology Transformation Playbook Additional Roles Pivotal Infographics PDF
This slide provides information regarding the additional roles considered as pivotal for successful infrastructure management in terms of release manager, automation architect integration specialist, software tester developer and security engineer. This is a information technology transformation playbook additional roles pivotal infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like release manager, security engineer, software tester developer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Contd Sample PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a project security administration it various ways to manage project safety by managing threats contd sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deactivate orphaned user accounts, develop strict access management policies, implement active remediation, investigate remote access policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
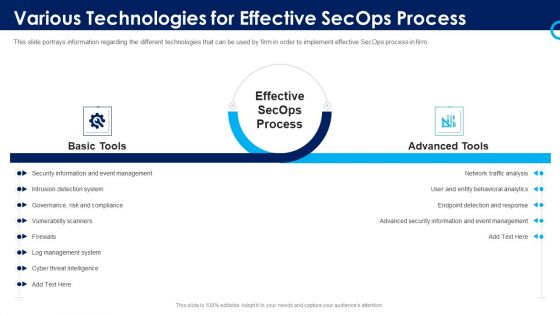
Organizational Security Solutions Various Technologies For Effective Secops Process Designs PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. This is a organizational security solutions various technologies for effective secops process designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like basic tools, advanced tools. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
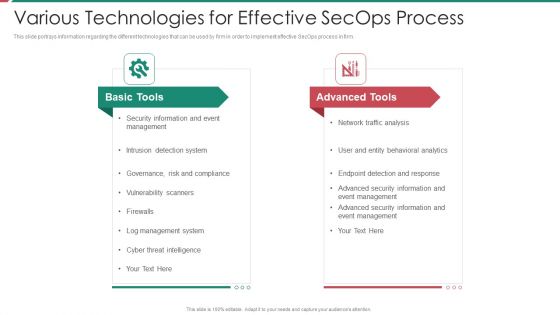
Security And Process Integration Various Technologies For Effective Secops Process Clipart PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. This is a security and process integration various technologies for effective secops process clipart pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like basic tools, advanced tools. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
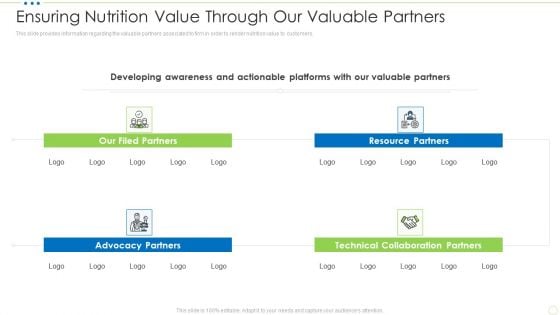
Ensuring Nutrition Value Through Our Valuable Partners Food Security Excellence Ppt Layouts Visuals PDF
This slide provides information regarding the valuable partners associated to firm in order to render nutrition value to customers. This is a ensuring nutrition value through our valuable partners food security excellence ppt layouts visuals pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our filed partners, resource partners, advocacy partners, technical collaboration partners. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks.


 Continue with Email
Continue with Email

 Home
Home


































