Information Security

Malware Assessment Prevention Strategies From Infection Topics PDF
This slide demonstrates malware analysis approaches which assist businesses to protect and secure their system from attacks and threats. Up to date systems, being cautious of social engineering attacks, performing regular scans, etc. are few of the key approaches included in this slide. Presenting Malware Assessment Prevention Strategies From Infection Topics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Perform Regular Scans, Employ Best Security Practices, Create Backups. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
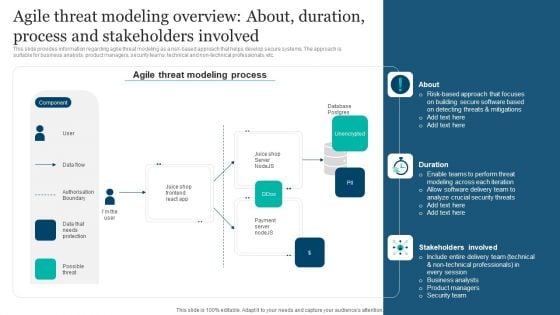
Responsible Technology Playbook Agile Threat Modeling Overview About Duration Process Elements PDF
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. This modern and well-arranged Responsible Technology Playbook Agile Threat Modeling Overview About Duration Process Elements PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
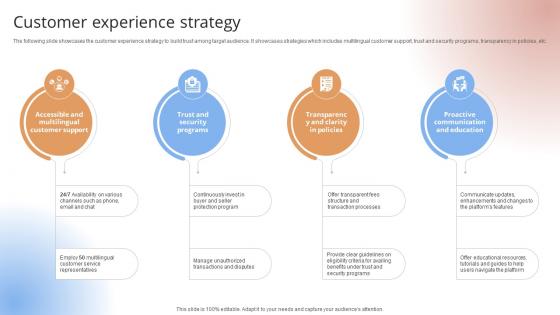
Customer Experience Strategy Payment Gateway Provider Startup GTM Strategy GTM SS V
The following slide showcases the customer experience strategy to build trust among target audience. It showcases strategies which includes multilingual customer support, trust and security programs, transparency in policies, etc.The following slide showcases the customer experience strategy to build trust among target audience. It showcases strategies which includes multilingual customer support, trust and security programs, transparency in policies, etc.Get a simple yet stunning designed Customer Experience Strategy Payment Gateway Provider Startup GTM Strategy GTM SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Customer Experience Strategy Payment Gateway Provider Startup GTM Strategy GTM SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide showcases the customer experience strategy to build trust among target audience. It showcases strategies which includes multilingual customer support, trust and security programs, transparency in policies, etc.

Problem Solution Payment Gateway Provider Startup GTM Strategy GTM SS V
The following slide showcases various gaps addressed in market along with desired state through the launch of ABC digital payment provider startup. It includes gaps such as security concerns and fraud risks, lacks responsive support team, etc.The following slide showcases various gaps addressed in market along with desired state through the launch of ABC digital payment provider startup. It includes gaps such as security concerns and fraud risks, lacks responsive support team, etc.This Problem Solution Payment Gateway Provider Startup GTM Strategy GTM SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Problem Solution Payment Gateway Provider Startup GTM Strategy GTM SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The following slide showcases various gaps addressed in market along with desired state through the launch of ABC digital payment provider startup. It includes gaps such as security concerns and fraud risks, lacks responsive support team, etc.
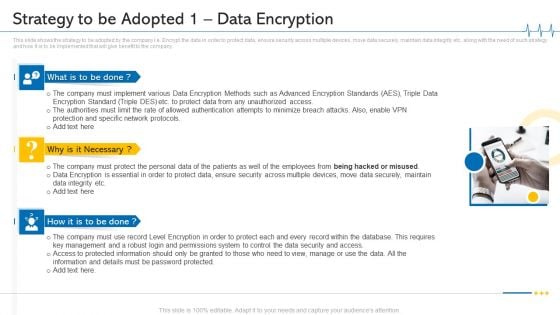
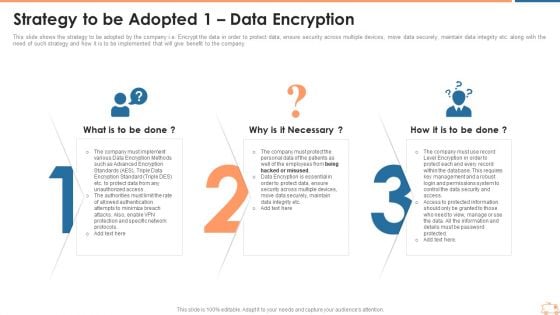
Minimize Cloud Risks Medical Care Business Case Competition Strategy To Be Adopted 1 Data Encryption Microsoft PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting minimize cloud risks medical care business case competition strategy to be adopted 1 data encryption microsoft pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Protection And Specific Network Protocols, Protect Data, Permissions System, Key Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
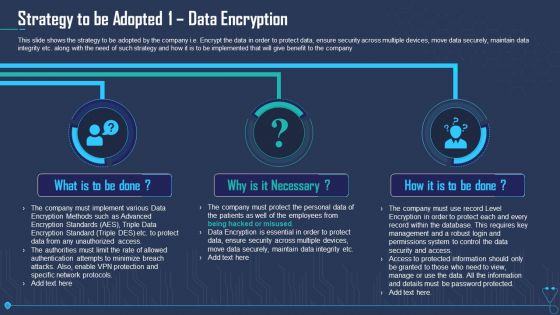
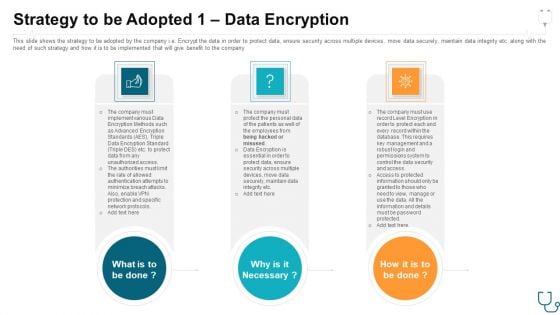
Strategy To Be Adopted 1 Data Encryption Ppt Outline PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 1 data encryption ppt outline pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 1 data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
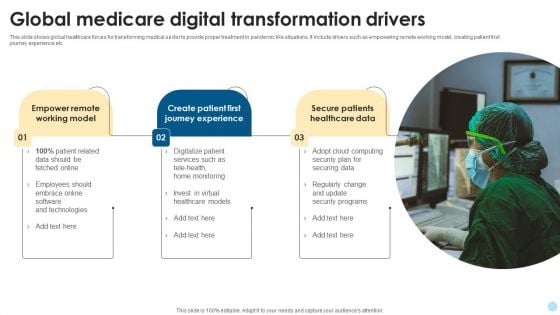
Global Medicare Digital Transformation Drivers Mockup PDF
This slide shows global healthcare forces for transforming medical sector to provide proper treatment in pandemic like situations. It include drivers such as empowering remote working model, creating patient first journey experience etc. Showcasing this set of slides titled Global Medicare Digital Transformation Drivers Mockup PDF. The topics addressed in these templates are Digitalize Patient Services, Security Programs, Securing Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Strategy To Be Adopted 1 Data Encryption Ppt Gallery Skills PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 1 data encryption ppt gallery skills pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 1 data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Strategy To Be Adopted 1 Data Encryption Ppt Model Deck PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 1 data encryption ppt model deck pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 1 data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agile Threat Modeling Overview About Duration Process And Stakeholders Involved Ppt Pictures Structure PDF
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Boost your pitch with our creative Agile Threat Modeling Overview About Duration Process And Stakeholders Involved Ppt Pictures Structure PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Agile Threat Modeling Overview About Duration Process And Stakeholders Involved Ppt Pictures Graphics Template PDF
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Boost your pitch with our creative Agile Threat Modeling Overview About Duration Process And Stakeholders Involved Ppt Pictures Graphics Template PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
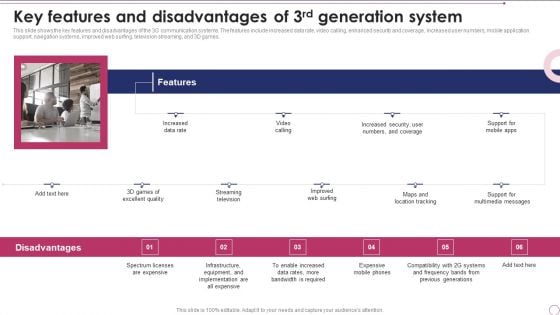
1G To 5G Wireless Communication System IT Key Features And Disadvantages Of 3Rd Generation System Download PDF
This slide shows the key features and disadvantages of the 3G communication systems. The features include increased data rate, video calling, enhanced security and coverage, increased user numbers, mobile application support, navigation systems, improved web surfing, television streaming, and 3D games. This is a 1G To 5G Wireless Communication System IT Key Features And Disadvantages Of 3Rd Generation System Download PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Equipment, And Implementation, Data Rates, Expensive Mobile Phones. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major Techniques For Project Safety IT Determine Project Safety Management Team Structure Pictures PDF
This slide provides information regarding project safety management team generally comprise of senior management personnel that have authority and resources to accelerate IT projects incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting major techniques for project safety it determine project safety management team structure pictures pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like public affair advisor, legal advisor, security manager, crisis management advisor, medical advisor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
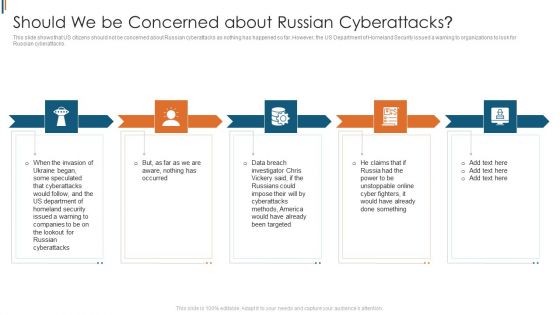
Ukraine Cyberwarfare Should We Be Concerned About Russian Cyberattacks Sample Pdf
This slide shows that US citizens should not be concerned about Russian cyberattacks as nothing has happened so far. However, the US Department of Homeland Security issued a warning to organizations to look for Russian cyberattacks. This is a ukraine cyberwarfare should we be concerned about russian cyberattacks sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like but, as far as we are aware, nothing has occurred, he claims that if russia had the power to be unstoppable online cyber fighters, data breach investigator chris vickery said, if the russians could impose their will by cyberattacks methods. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
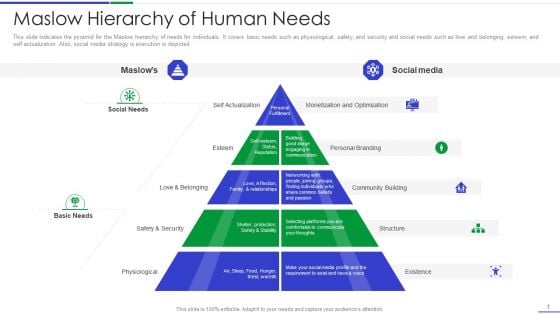
Ultimate Guide To Effective Change Management Process Maslow Hierarchy Of Human Needs Pictures PDF
This slide indicates the pyramid for the Maslow hierarchy of needs for individuals. It covers basic needs such as physiological, safety, and security and social needs such as love and belonging, esteem, and self actualization. Also, social media strategy is execution is depicted. This is a ultimate guide to effective change management process maslow hierarchy of human needs pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like existence, structure, community building, personal branding, monetization and optimization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Program Presentation Crisis Management Team Structure Advisor Designs PDF
This slide depicts the CMT structure designed to support management through crisis level issues. It comprise of senior management that have authority and resources to accelerate the firms internal incident response and are responsible in managing human impacts, company reputation, share values, and corporate assets. This is a program presentation crisis management team structure advisor designs pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like provide participate, aspects crisis communication, maintain current, accessible, security manager . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
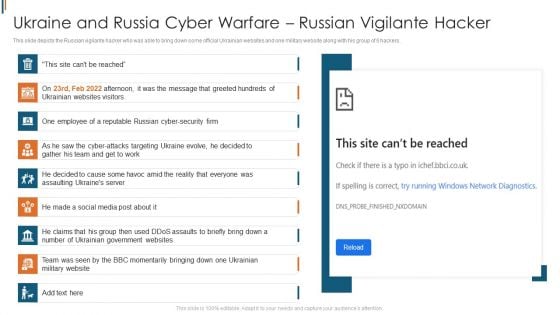
Ukraine Cyberwarfare Ukraine And Russia Cyber Warfare Russian Vigilante Hacker Inspiration Pdf
This slide depicts the Russian vigilante hacker who was able to bring down some official Ukrainian websites and one military website along with his group of 6 hackers. This is a ukraine cyberwarfare ukraine and russia cyber warfare russian vigilante hacker inspiration pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like he made a social media post about it, one employee of a reputable russian cyber security firm, team was seen by the bbc momentarily bringing down one ukrainian military website. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Team Performance Improvement Functional Optimization Through Agile Methodologies Prioritizing Agile Software Development Tasks Sample PDF
This slide shows some important tasks that need to be done on priority basis in order to implement Agile Technique in the team such as focusing on individual, enhance product features, quickly responding to change, collaborating with the customer for efficient task completion etc. This is a team performance improvement functional optimization through agile methodologies prioritizing agile software development tasks sample pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project deliverables, enhancing team communication, customer collaboration, minimize cyber security risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
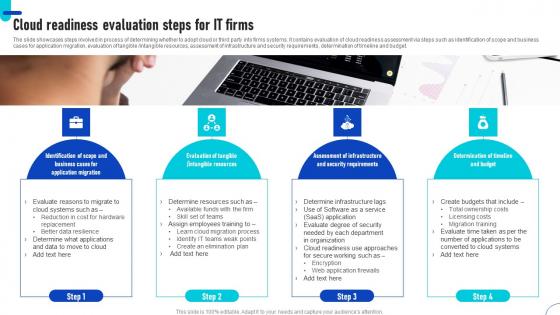
Cloud Readiness Evaluation Steps For IT Firms Ppt Outline Files Pdf
The slide showcases steps involved in process of determining whether to adopt cloud or third party into firms systems. It contains evaluation of cloud readiness assessment via steps such as identification of scope and business cases for application migration, evaluation of tangible intangible resources, assessment of infrastructure and security requirements, determination of timeline and budget. Pitch your topic with ease and precision using this Cloud Readiness Evaluation Steps For IT Firms Ppt Outline Files Pdf. This layout presents information on Determine Resources, Assign Employees Training, Determine Applications. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcases steps involved in process of determining whether to adopt cloud or third party into firms systems. It contains evaluation of cloud readiness assessment via steps such as identification of scope and business cases for application migration, evaluation of tangible intangible resources, assessment of infrastructure and security requirements, determination of timeline and budget.
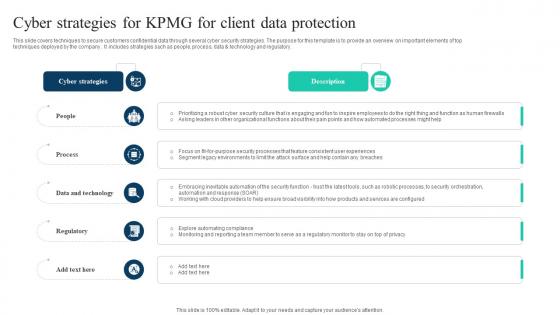
The Ultimate Guide To KPMG Cyber Strategies For KPMG For Client Data Protection Strategy SS V
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward The Ultimate Guide To KPMG Cyber Strategies For KPMG For Client Data Protection Strategy SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal The Ultimate Guide To KPMG Cyber Strategies For KPMG For Client Data Protection Strategy SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory.

Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.

CASB 2 0 IT Advantages And Disadvantages Of Proxy Based Deployment
This slide represents the benefits and drawbacks of proxy-based CASB deployment. The purpose of this slide is to showcase the various pros and cons of proxy-based cloud access security brokers and the advantages cover flexibility, secure SaaS applications, and so on. Create an editable CASB 2 0 IT Advantages And Disadvantages Of Proxy Based Deployment that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. CASB 2 0 IT Advantages And Disadvantages Of Proxy Based Deployment is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the benefits and drawbacks of proxy-based CASB deployment. The purpose of this slide is to showcase the various pros and cons of proxy-based cloud access security brokers and the advantages cover flexibility, secure SaaS applications, and so on.

Iot Device Update Management Process Iot Device Management Background Pdf
This slide exhibits IoT device management and maintenance process in order to avoid security threats. It includes steps such as analyse IoT fleet, Create backup, Test updates, schedule plan, divide fleet into groups, execute updates, and collect feedback. This Iot Device Update Management Process Iot Device Management Background Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide exhibits IoT device management and maintenance process in order to avoid security threats. It includes steps such as analyse IoT fleet, Create backup, Test updates, schedule plan, divide fleet into groups, execute updates, and collect feedback.

The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory.

Solutions To Protect Bitcoin Against Everything About Bitcoin PPT Sample Fin SS V
This slide shows solutions to various types of threats associated with Bitcoin s security which can be used by individuals to secure their digital currencies. It incudes protection against frauds such as malware attacks, fake wallets, SIM swapping, etc. Explore a selection of the finest Solutions To Protect Bitcoin Against Everything About Bitcoin PPT Sample Fin SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Solutions To Protect Bitcoin Against Everything About Bitcoin PPT Sample Fin SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide shows solutions to various types of threats associated with Bitcoin s security which can be used by individuals to secure their digital currencies. It incudes protection against frauds such as malware attacks, fake wallets, SIM swapping, etc.

Technologies To Ensure Data Protection And Privacy Background PDF
The following slide showcases some technologies to administer organizational data privacy and security concerns. It includes elements such as data encryption, change management and auditing, user and behavior analytics UEBA, backup and recovery etc. Presenting Technologies To Ensure Data Protection And Privacy Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Encryption, Change Management And Auditing, Backup And Recovery. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
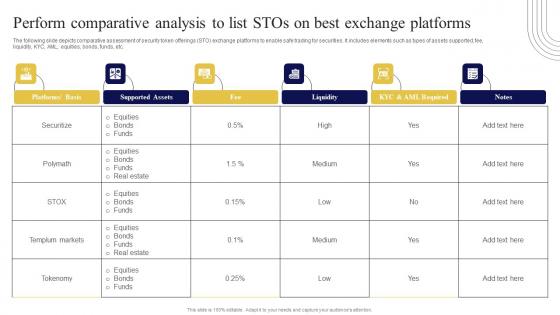
Perform Comparative Analysis To Exploring Investment Opportunities Topics Pdf
The following slide depicts comparative assessment of security token offerings STO exchange platforms to enable safe trading for securities. It includes elements such as types of assets supported, fee, liquidity, KYC, AML, equities, bonds, funds, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Perform Comparative Analysis To Exploring Investment Opportunities Topics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Perform Comparative Analysis To Exploring Investment Opportunities Topics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide depicts comparative assessment of security token offerings STO exchange platforms to enable safe trading for securities. It includes elements such as types of assets supported, fee, liquidity, KYC, AML, equities, bonds, funds, etc.

Timeline To Implement Devsecops Process In Organization Role Of Devsecops Ppt Example
This slide shows the timeline for implementing the DevSecOps process. The key steps include defining the project objective, identifying key stakeholders, sharing basic guidelines on secure coding, basic compliance checks, regularly reviewing and updating security tools, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Timeline To Implement Devsecops Process In Organization Role Of Devsecops Ppt Example With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Timeline To Implement Devsecops Process In Organization Role Of Devsecops Ppt Example today and make your presentation stand out from the rest This slide shows the timeline for implementing the DevSecOps process. The key steps include defining the project objective, identifying key stakeholders, sharing basic guidelines on secure coding, basic compliance checks, regularly reviewing and updating security tools, etc.
Strategies To Optimize Data Center Management Technology Operations Icons PDF
This slide highlights strategies to optimize datacentre with the purpose of improving infrastructural efficiency to make datacentre central hub for all technologies. It covers hiring data security officer, utilizing cloud computing, upgrading hardware, virtualization, management transparency and automation. Presenting Strategies To Optimize Data Center Management Technology Operations Icons PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Utilize Cloud Computing, Upgrade Hardware, Virtualization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Warehouse Implementation Why We Need Data Warehouse Portrait PDF
This slide represents the need for a data warehouse in the organization, such as data quality, single point for all data for all users, and the complicated problems that can be solved through a data warehouse.Deliver and pitch your topic in the best possible manner with this Data Warehouse Implementation Why We Need Data Warehouse Portrait PDF. Use them to share invaluable insights on Systems Individually, Range Of Complicated, Security Considerations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Financial Enterprise Data Governance Plan Ppt Icon Visuals PDF
This slide showcases an ideal structure to utilize data within the organization to ensure security and reliability of data in enterprises according to the data usage policies and standards. The key strategies include identify data source, define data, standardize data and data handling. Persuade your audience using this Financial Enterprise Data Governance Plan Ppt Icon Visuals PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Identify Data Source, Define Data, Standardize Data, Data Handling. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution. If you are looking for a format to display your unique thoughts, then the professionally designed Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution.
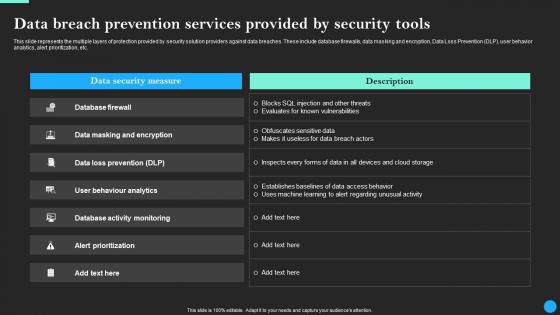
Data Breach Prevention Services Provided Data Breach Prevention Graphics Pdf
This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Data Breach Prevention Services Provided Data Breach Prevention Graphics Pdfand observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc.
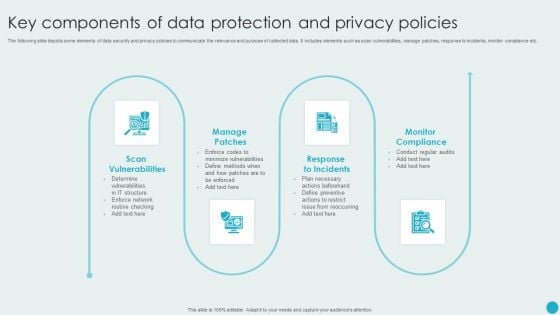
Key Components Of Data Protection And Privacy Policies Graphics PDF
The following slide depicts some elements of data security and privacy policies to communicate the relevance and purpose of collected data. It includes elements such as scan vulnerabilities, manage patches, response to incidents, monitor compliance etc. Presenting Key Components Of Data Protection And Privacy Policies Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Patches, Response To Incidents, Monitor Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Integration Implementation Challenges And Solutions Data Integration Strategies For Business
This slide highlights various limitations of data integration. The purpose of this slide is to discuss the solutions to different challenges associated with data integration. These include security risks, delays in data delivery, resource-constrained, and their solutions. If you are looking for a format to display your unique thoughts, then the professionally designed Data Integration Implementation Challenges And Solutions Data Integration Strategies For Business is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Integration Implementation Challenges And Solutions Data Integration Strategies For Business and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide highlights various limitations of data integration. The purpose of this slide is to discuss the solutions to different challenges associated with data integration. These include security risks, delays in data delivery, resource-constrained, and their solutions.
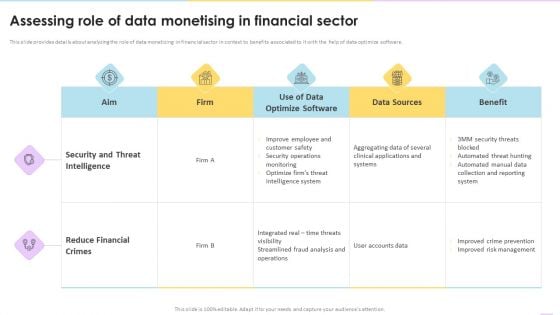
Data Valuation And Monetization Assessing Role Of Data Monetising In Financial Sector Themes PDF
This slide provides details about analyzing the role of data monetizing in financial sector in context to benefits associated to it with the help of data optimize software.Deliver and pitch your topic in the best possible manner with this Data Valuation And Monetization Assessing Role Of Data Monetising In Financial Sector Themes PDF. Use them to share invaluable insights on Improve Employee, Security Operations, Automated Threat and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
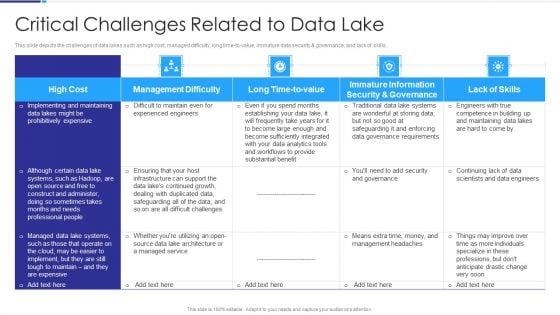
Data Lake Architecture Critical Challenges Related To Data Lake Slides PDF
This slide depicts the challenges of data lakes such as high cost, managed difficulty, long time-to-value, immature data security And governance, and lack of skills. Deliver and pitch your topic in the best possible manner with this Data Lake Architecture Critical Challenges Related To Data Lake Slides PDF. Use them to share invaluable insights on High Cost, Management Difficulty, Long Time To Value, Lack Skills and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
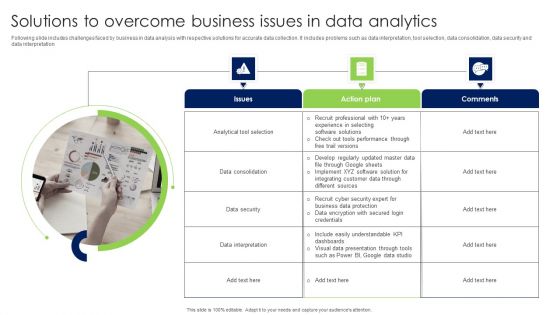
Solutions To Overcome Business Issues In Data Analytics Infographics PDF
Following slide includes challenges faced by business in data analysis with respective solutions for accurate data collection. It includes problems such as data interpretation, tool selection, data consolidation, data security and data interpretation Presenting Solutions To Overcome Business Issues In Data Analytics Infographics PDF to dispense important information. This template comprises Three stages. It also presents valuable insights into the topics including Issues, Action Plan, Comments. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Common Drawbacks Of Electronic Data Interchange Document Transport Icons PDF
This slide provides glimpse about key challenges of using Electronic Data Interchange EDI system. It includes drawbacks such as for a complex B2B network, growing electronic data interchange volumes, etc.Showcasing this set of slides titled Common Drawbacks Of Electronic Data Interchange Document Transport Icons PDF. The topics addressed in these templates are More Transparency, Security Concerns, Skyrocketing Costs. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
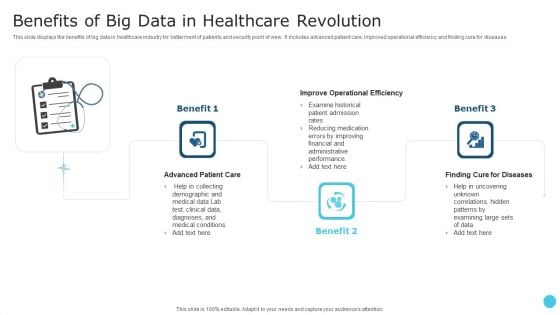
Benefits Of Big Data In Healthcare Revolution Sample PDF
This slide displays the benefits of big data in healthcare industry for betterment of patients and security point of view. It includes advanced patient care, improved operational efficiency and finding cure for diseases. Presenting Benefits Of Big Data In Healthcare Revolution Sample PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Advanced Patient Care, Improve Operational Efficiency, Benefit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
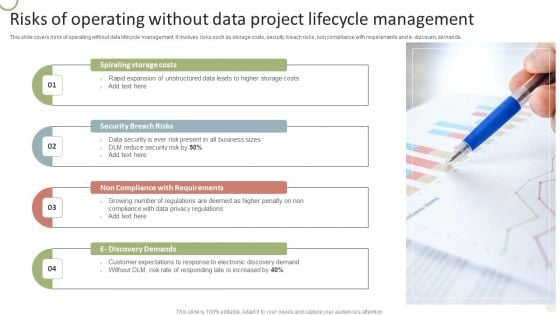
Risks Of Operating Without Data Project Lifecycle Management Ideas PDF
This slide covers risks of operating without data lifecycle management. It involves risks such as storage costs, security breach risks, non compliance with requirements and e- discovery demands.Presenting Risks Of Operating Without Data Project Lifecycle Management Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Rapid Expansion, Present Business, Discovery Demands. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
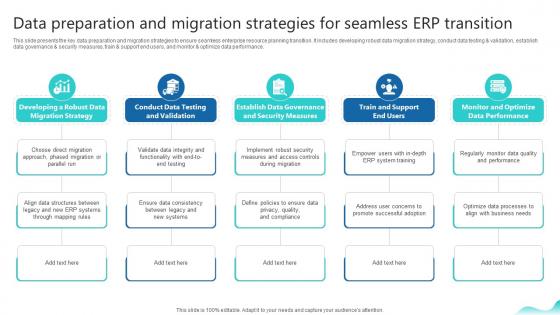
Data Preparation And Migration Strategies For Seamless Erp And Digital Transformation For Maximizing DT SS V
This slide presents the key data preparation and migration strategies to ensure seamless enterprise resource planning transition. It includes developing robust data migration strategy, conduct data testing and validation, establish data governance and security measures, train and support end users, and monitor and optimize data performance. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Preparation And Migration Strategies For Seamless Erp And Digital Transformation For Maximizing DT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Preparation And Migration Strategies For Seamless Erp And Digital Transformation For Maximizing DT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide presents the key data preparation and migration strategies to ensure seamless enterprise resource planning transition. It includes developing robust data migration strategy, conduct data testing and validation, establish data governance and security measures, train and support end users, and monitor and optimize data performance.
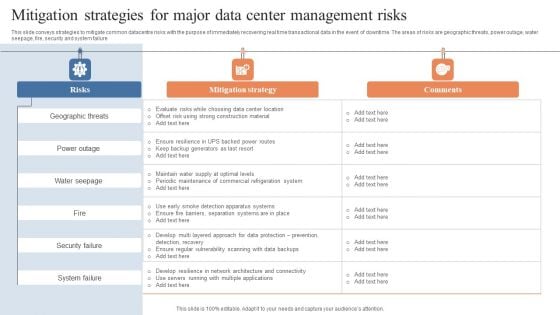
Mitigation Strategies For Major Data Center Management Risks Designs PDF
This slide conveys strategies to mitigate common datacentre risks with the purpose of immediately recovering real time transactional data in the event of downtime. The areas of risks are geographic threats, power outage, water seepage, fire, security and system failure. Showcasing this set of slides titled Mitigation Strategies For Major Data Center Management Risks Designs PDF. The topics addressed in these templates are Geographic Threats, Power Outage, Water Seepage . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Breach Awareness Training Program Data Breach Prevention Professional Pdf
This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs. Find highly impressive Data Breach Awareness Training Program Data Breach Prevention Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Breach Awareness Training Program Data Breach Prevention Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.

Data Breach Awareness Training Program Data Fortification Strengthening Defenses
This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.Find highly impressive Data Breach Awareness Training Program Data Fortification Strengthening Defenses on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Breach Awareness Training Program Data Fortification Strengthening Defenses for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.

Customer Data Platform Safety And Privacy Usability Of CDP Software Tool Professional Pdf
The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc. If you are looking for a format to display your unique thoughts, then the professionally designed Customer Data Platform Safety And Privacy Usability Of CDP Software Tool Professional Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Customer Data Platform Safety And Privacy Usability Of CDP Software Tool Professional Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc.

Data Lake Implementation Critical Challenges Related To Data Lake Mockup PDF
This slide depicts the challenges of data lakes such as high cost, managed difficulty, long time-to-value, immature data security and governance, and lack of skills. Present like a pro with Data Lake Implementation Critical Challenges Related To Data Lake Mockup PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
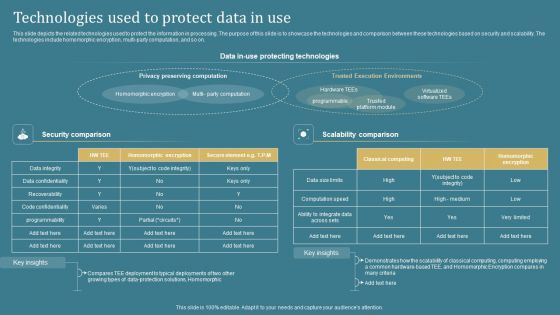
Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Organizational Data Accuracy Issues With Solutions Elements PDF
The slide highlights various data integrity challenges and solutions to overcome such issues. Various problems included are lack of data integration, manual data collection, data security issues and dependence on legacy systems.Persuade your audience using this Organizational Data Accuracy Issues With Solutions Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Integration, Manual Data Collection, Dependence Legacy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
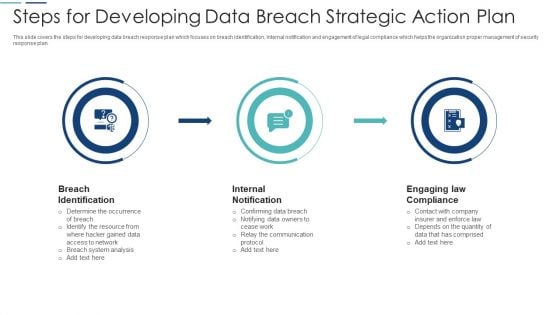
Steps For Developing Data Breach Strategic Action Plan Professional PDF
This slide covers the steps for developing data breach response plan which focuses on breach identification, internal notification and engagement of legal compliance which helps the organization proper management of security response plan. Persuade your audience using this steps for developing data breach strategic action plan professional pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including breach identification, internal notification, engaging law compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
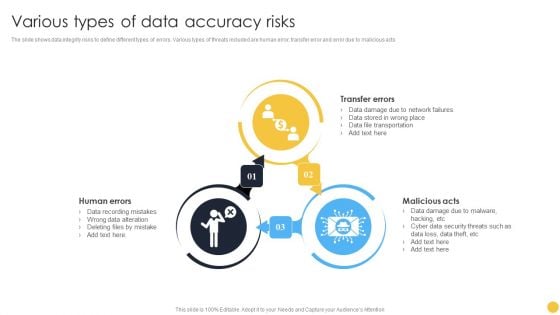
Various Types Of Data Accuracy Risks Guidelines PDF
The slide shows data integrity risks to define different types of errors. Various types of threats included are human error, transfer error and error due to malicious acts.Persuade your audience using this Various Types Of Data Accuracy Risks Guidelines PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Recording Mistakes, File Transportation, Security Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
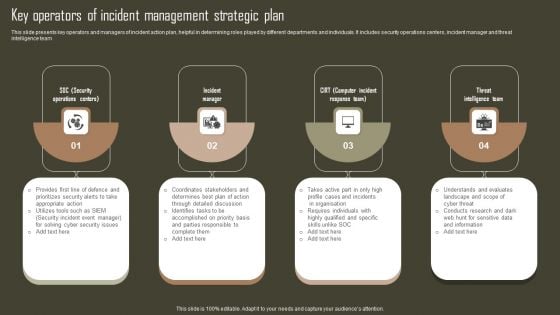
Key Operators Of Incident Management Strategic Plan Professional PDF
This slide presents key operators and managers of incident action plan, helpful in determining roles played by different departments and individuals. It includes security operations centers, incident manager and threat intelligence team. Presenting Key Operators Of Incident Management Strategic Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Incident Manager, Threat Intelligence Team, Sensitive Data And Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Predictive Data Model Outliers Model For Predictive Analytics Introduction PDF

Overview Cybersecurity And Data Protection In Digital Transformation DT SS V
This slide presents an overview into the landscape of cybersecurity and data protection with its advantages. It also presents a survey analysis on share of SMEs that have implemented essential and basic IT security initiatives.Find highly impressive Overview Cybersecurity And Data Protection In Digital Transformation DT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Overview Cybersecurity And Data Protection In Digital Transformation DT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide presents an overview into the landscape of cybersecurity and data protection with its advantages. It also presents a survey analysis on share of SMEs that have implemented essential and basic IT security initiatives.
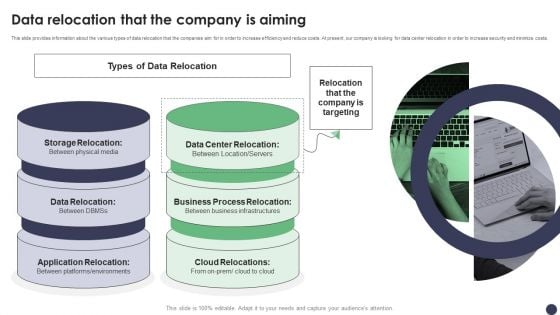
Data Relocation That The Company Is Aiming Ppt PowerPoint Presentation Diagram Lists PDF
This slide provides information about the various types of data relocation that the companies aim for in order to increase efficiency and reduce costs. At present, our company is looking for data center relocation in order to increase security and minimize costs. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Data Relocation That The Company Is Aiming Ppt PowerPoint Presentation Diagram Lists PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Data Relocation That The Company Is Aiming Ppt PowerPoint Presentation Diagram Lists PDF today and make your presentation stand out from the rest.
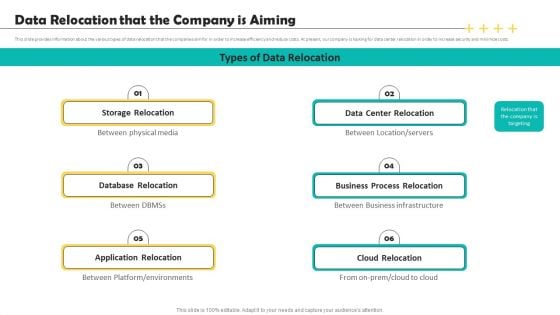
Deploying Data Center Data Relocation That The Company Is Aiming Rules PDF
This slide provides information about the various types of data relocation that the companies aim for in order to increase efficiency and reduce costs. At present, our company is looking for data center relocation in order to increase security and minimize costs. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Deploying Data Center Data Relocation That The Company Is Aiming Rules PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
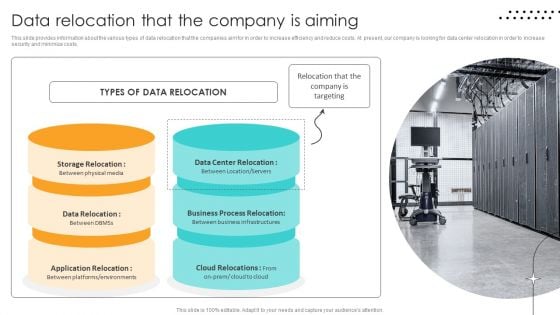
Cost Saving Benefits Of Implementing Data Center Data Relocation That The Company Is Aiming Ideas PDF
This slide provides information about the various types of data relocation that the companies aim for in order to increase efficiency and reduce costs. At present, our company is looking for data center relocation in order to increase security and minimize costs. Get a simple yet stunning designed Cost Saving Benefits Of Implementing Data Center Data Relocation That The Company Is Aiming Ideas PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cost Saving Benefits Of Implementing Data Center Data Relocation That The Company Is Aiming Ideas PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Deploying Data Center Risks And Mitigation Strategies For Data Center Relocation Template PDF
The following slide provides information about the risks involved in data center relocation process and the strategies that must be implemented in order to mitigate the risks. Major risks are unwanted downtime, data loss, data security and added latency. This modern and well-arranged Deploying Data Center Risks And Mitigation Strategies For Data Center Relocation Template PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
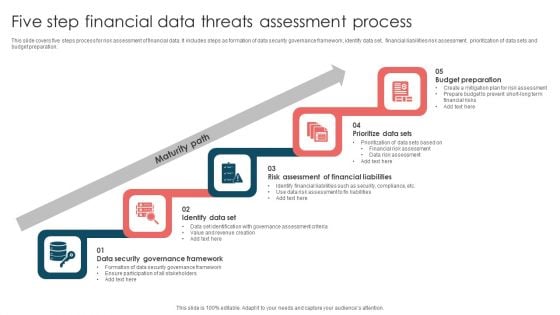
Five Step Financial Data Threats Assessment Process Ppt Infographic Template File Formats PDF
This slide covers five steps process for risk assessment of financial data. It includes steps as formation of data security governance framework, identify data set, financial liabilities risk assessment, prioritization of data sets and budget preparation. Presenting Five Step Financial Data Threats Assessment Process Ppt Infographic Template File Formats PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Maturity Path, Budget Preparation, Prioritize Data Sets, Identify Data Set. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cost Saving Benefits Of Implementing Data Center Risks And Mitigation Strategies For Data Center Relocation Brochure PDF
The following slide provides information about the risks involved in data center relocation process and the strategies that must be implemented in order to mitigate the risks. Major risks are unwanted downtime, data loss, data security and added latency. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cost Saving Benefits Of Implementing Data Center Risks And Mitigation Strategies For Data Center Relocation Brochure PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.


 Continue with Email
Continue with Email

 Home
Home


































