Information Security

Steps Of NIST Cybersecurity Risk Management Framework Mockup PDF
The slide showcases various steps of Nist RMF process which instructs in monitoring, selecting and implementing security controls. It covers identify, select, implement, assess, authorize and monitor. Persuade your audience using this Steps Of NIST Cybersecurity Risk Management Framework Mockup PDF.zip. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Identify. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
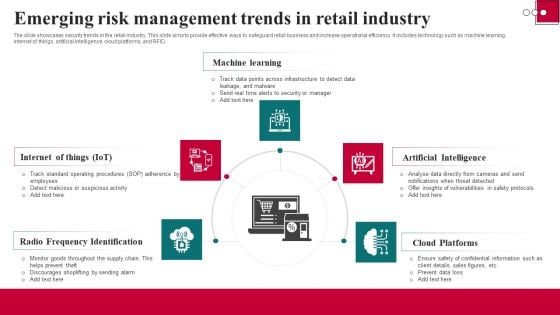
Emerging Risk Management Trends In Retail Industry Background PDF
The slide showcases security trends in the retail industry. This slide aims to provide effective ways to safeguard retail business and increase operational efficiency. It includes technology such as machine learning, internet of things, artificial intelligence, cloud platforms, and RFID. Persuade your audience using this Emerging Risk Management Trends In Retail Industry Background PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Radio Frequency Identification, Artificial Intelligence, Cloud Platforms. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
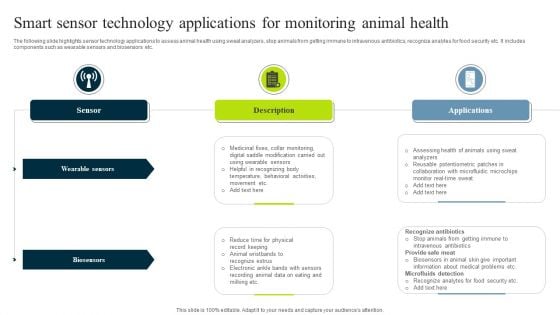
Smart Sensor Technology Applications For Monitoring Animal Health Clipart PDF
The following slide highlights sensor technology applications to assess animal health using sweat analyzers, stop animals from getting immune to intravenous antibiotics, recognize analytes for food security etc. It includes components such as wearable sensors and biosensors etc. Persuade your audience using this Smart Sensor Technology Applications For Monitoring Animal Health Clipart PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Wearable Sensors, Biosensors, Description. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
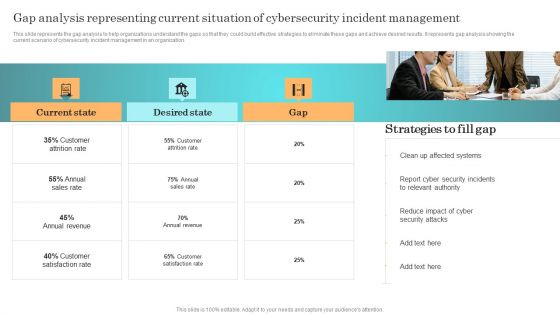
Incident Response Techniques Deployement Gap Analysis Representing Current Situation Of Cybersecurity Designs PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. There are so many reasons you need a Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
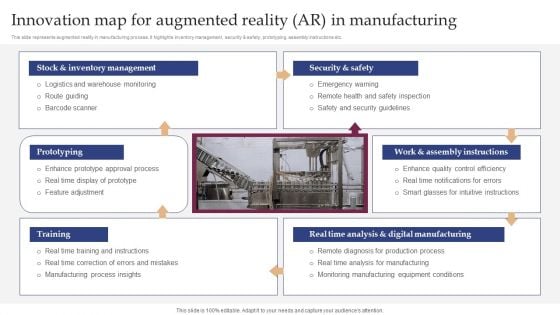
Innovation Map For Augmented Reality AR In Manufacturing Inspiration PDF
This slide represents augmented reality in manufacturing process. It highlights inventory management, security and safety, prototyping, assembly instructions etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 peracent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Innovation Map For Augmented Reality AR In Manufacturing Inspiration PD from Slidegeeks and deliver a wonderful presentation.
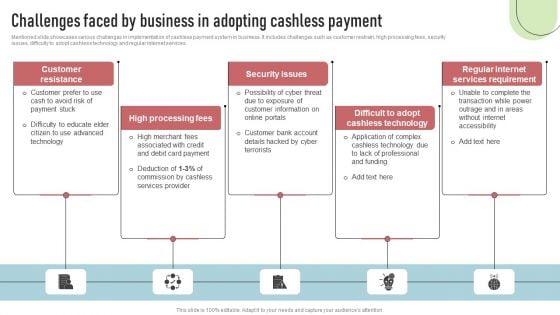
Cashless Payment Strategies To Enhance Business Performance Challenges Faced By Business In Adopting Microsoft PDF
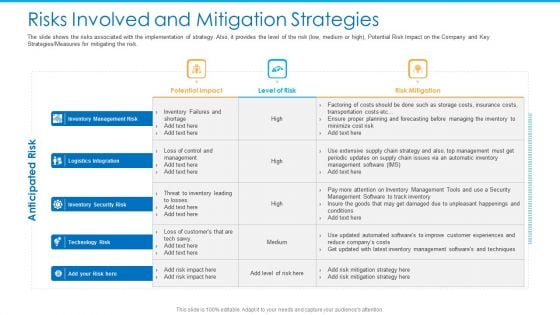
Risks Involved And Mitigation Strategies Infographics PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies or Measures for mitigating the risk.Deliver an awe inspiring pitch with this creative risks involved and mitigation strategies infographics pdf bundle. Topics like inventory management risk, logistics integration, inventory security risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
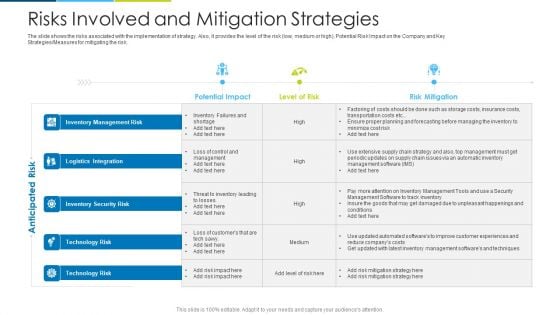
Risks Involved And Mitigation Strategies Ppt Design Templates PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies or Measures for mitigating the risk. Deliver an awe inspiring pitch with this creative risks involved and mitigation strategies ppt design templates pdf bundle. Topics like inventory management risk, inventory management risk, inventory security risk, technology risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risks Involved And Mitigation Strategies Demonstration PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies Measures for mitigating the risk.Deliver an awe-inspiring pitch with this creative risks involved and mitigation strategies demonstration pdf. bundle. Topics like inventory management risk, logistics integration, inventory security risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
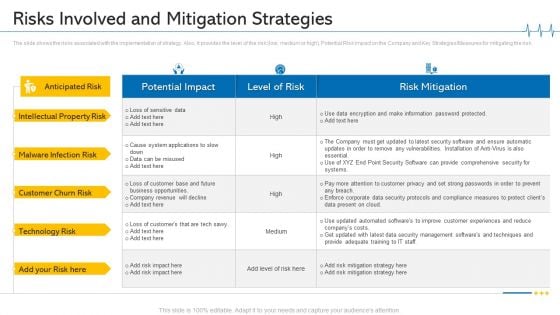
Minimize Cloud Risks Medical Care Business Case Competition Risks Involved And Mitigation Strategies Brochure PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies Measures for mitigating the risk. Deliver and pitch your topic in the best possible manner with this minimize cloud risks medical care business case competition risks involved and mitigation strategies brochure pdf. Use them to share invaluable insights on technology, customer churn risk, security software, management, business opportunities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Initiatives To Produce Effective Concept For Logistic Firm Risks Involved In Technology Formats PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high and Key Strategies or Measures for mitigating the risk. Deliver and pitch your topic in the best possible manner with this initiatives to produce effective concept for logistic firm risks involved in technology formats pdf. Use them to share invaluable insights on connectivity risk, cyber security risk, inventory management risk, technology risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
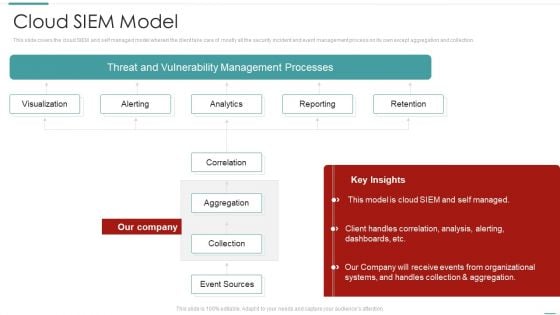
Risk Recognition Automation Cloud Siem Model Ppt Layouts Templates PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this risk recognition automation cloud siem model ppt layouts templates pdf. Use them to share invaluable insights on visualization, alerting, analytics, reporting, retention and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
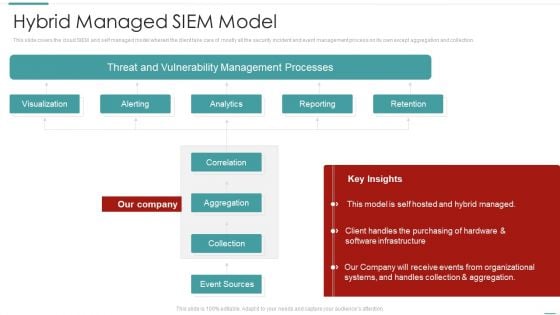
Risk Recognition Automation Hybrid Managed Siem Model Ppt Show Themes PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this risk recognition automation hybrid managed siem model ppt show themes pdf. Use them to share invaluable insights on visualization, alerting, analytics, reporting, retention and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
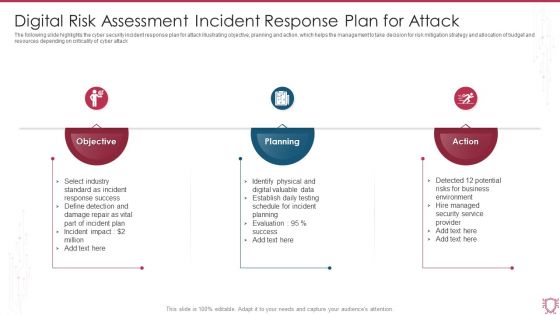
Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF
The following slide highlights the cyber security incident response plan for attack illustrating objective, planning and action, which helps the management to take decision for risk mitigation strategy and allocation of budget and resources depending on criticality of cyber attack. Persuade your audience using this Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objective, Planning, Action. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
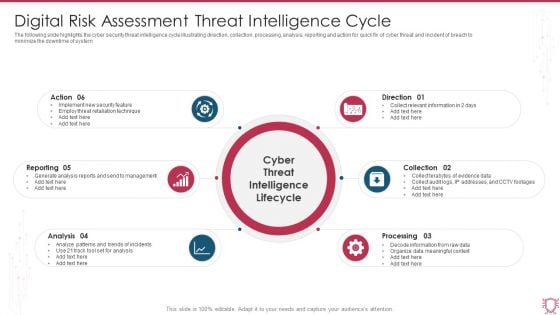
Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF
The following slide highlights the cyber security threat intelligence cycle illustrating direction, collection, processing, analysis, reporting and action for quick fix of cyber threat and incident of breach to minimize the downtime of system. Persuade your audience using this Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Reporting, Analysis, Processing, Direction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Phases Of Digital Risk Assessment Incident Response Cycle Ppt Gallery Format Ideas PDF
The following slide highlights the phase of cyber security incident response cycle depicting preparation phase, analysis phase, response phase, and post event phase. Persuade your audience using this Phases Of Digital Risk Assessment Incident Response Cycle Ppt Gallery Format Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Post Event Phase, Response Phase, Preparation Phase, Analysis Phase. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
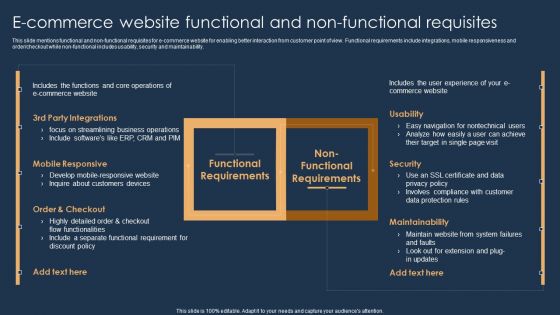
E Commerce Website Functional And Non Functional Requisites Summary PDF
This slide mentions functional and non-functional requisites for e commerce website for enabling better interaction from customer point of view. Functional requirements include integrations, mobile responsiveness and order or checkout while non functional includes usability, security and maintainability. Persuade your audience using this E Commerce Website Functional And Non Functional Requisites Summary PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Functional Requirements, Non Functional Requirements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Internal Audit Control Mechanism Implementation Risks And Mitigation Strategies Icons PDF
This slide mentions implementation risks and solutions of internal audit control system. The parameters include audit system design, management and governance, internal security controls and reporting and analytics. Persuade your audience using this Internal Audit Control Mechanism Implementation Risks And Mitigation Strategies Icons PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Parameters, Risks, Mitigation Strategies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Project Risk Optimization Strategic Approaches Formats PDF
This slide comprises different ways to assess portfolio risk in order to make asset allocation and security selection decisions. Some of the best practices include portfolio standard deviation, shortfall risk, tracking error, Sharpe ratio, and beta. Persuade your audience using this Project Risk Optimization Strategic Approaches Formats PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Portfolio Standard Deviation, Shortfall Risk, Tracking Error. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
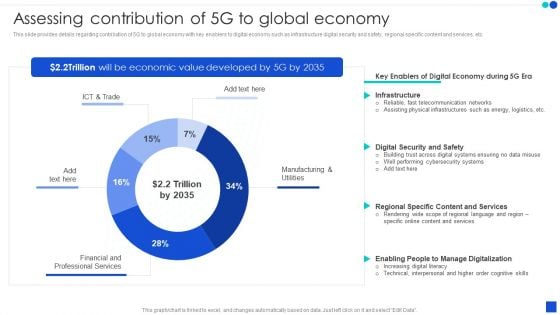
5G Technology Development For Digital Transformation Assessing Contribution Of 5G To Global Economy Graphics PDF
This slide provides details regarding contribution of 5G to global economy with key enablers to digital economy such as infrastructure digital security and safety, regional specific content and services, etc. Boost your pitch with our creative 5G Technology Development For Digital Transformation Assessing Contribution Of 5G To Global Economy Graphics PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Advantages Of Cloud Computing With Better Operational Control Ppt PowerPoint Presentation Styles Samples PDF
Presenting this set of slides with name advantages of cloud computing with better operational control ppt powerpoint presentation styles samples pdf. This is a eight stage process. The stages in this process are agility to meet volatile business cycles, reorganizes it cost structure, agile application release cycles through devops, better operational control of the platform, elasticity to support demand consumption, cost reduction and improved cost predictability, facilitate access to enhanced capabilities, increased security and controls through automation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Crisis Program Presentation Risk Management Action Plan Strategic Guidelines PDF
This slide depicts the several that are to be taken at various levels to avoid the occurrence of security breach that might lead to technological crisis in the organization. Deliver and pitch your topic in the best possible manner with this crisis program presentation risk management action plan strategic guidelines pdf. Use them to share invaluable insights on strategic, crisis response resolution, enforcement perspective, compliance, technical and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Determining Crisis Management BCP Risk Management Action Plan Actions Ppt PowerPoint Presentation File Mockup PDF
This slide depicts the several that are to be taken at various levels to avoid the occurrence of security breach that might lead to technological crisis in the organization. Deliver an awe inspiring pitch with this creative determining crisis management bcp risk management action plan actions ppt powerpoint presentation file mockup pdf. bundle. Topics like government, critical senior, professional, technical, individual, international. can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agile Model Improve Task Team Performance Agile Kanban Methodology Chart With Stories Guidelines PDF
This slide explains Kanban Methodology through a chart that shows User Story Details, Tasks to be done, Tasks in progress Product Development, Software Quality Check, Testing to be done Automation Processes, Cycle Time Analysis and the activities that are ready to be deployed. Deliver an awe inspiring pitch with this creative agile model improve task team performance agile kanban methodology chart with stories guidelines pdf bundle. Topics like security integration, product development, automation processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

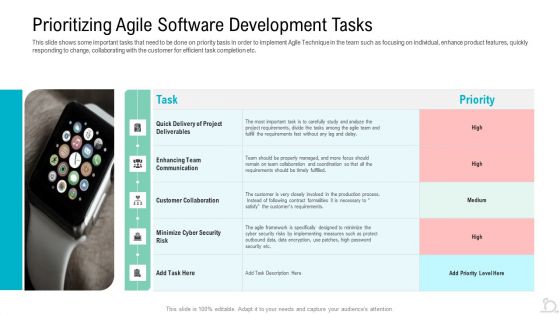
Prioritizing Agile Software Development Tasks Diagrams PDF
This slide shows some important tasks that need to be done on priority basis in order to implement Agile Technique in the team such as focusing on individual, enhanc3 product features, quickly responding to change, collaborating with the customer for efficient task completion etc. Deliver and pitch your topic in the best possible manner with this prioritizing agile software development tasks diagrams pdf. Use them to share invaluable insights on enhancing team communication, customer collaboration, minimize cyber security risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
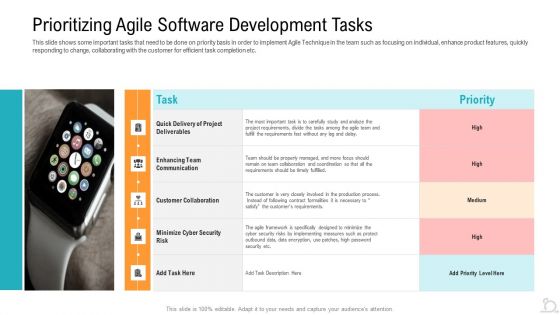
Prioritizing Agile Software Development Tasks Ppt Slides Templates PDF
This slide shows some important tasks that need to be done on priority basis in order to implement Agile Technique in the team such as focusing on individual, enhance product features, quickly responding to change, collaborating with the customer for efficient task completion etc. Deliver and pitch your topic in the best possible manner with this prioritizing agile software development tasks ppt slides templates pdf. Use them to share invaluable insights on enhancing team communication, customer collaboration, cyber security risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Prioritizing Agile Software Development Tasks Clipart PDF
This slide shows some important tasks that need to be done on priority basis in order to implement Agile Technique in the team such as focusing on individual, enhance product features, quickly responding to change, collaborating with the customer for efficient task completion etc.Deliver an awe inspiring pitch with this creative prioritizing agile software development tasks clipart pdf bundle. Topics like enhancing team communication, customer collaboration, minimize cyber security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
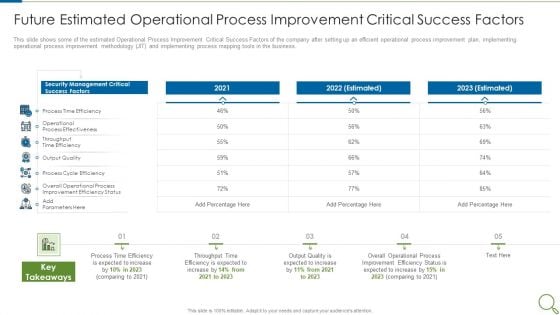
Future Estimated Operational Process Improvement Critical Success Factors Slides PDF
This slide shows some of the estimated Operational Process Improvement Critical Success Factors of the company after setting up an efficient operational process improvement plan, implementing operational process improvement methodology JIT and implementing process mapping tools in the business. Deliver an awe inspiring pitch with this creative future estimated operational process improvement critical success factors slides pdf bundle. Topics like process, output quality, security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
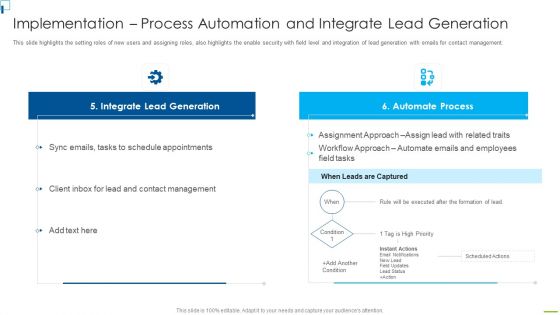
Designing And Deployment Implementation Process Automation And Integrate Themes PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management. Deliver and pitch your topic in the best possible manner with this designing and deployment implementation process automation and integrate themes pdf. Use them to share invaluable insights on integrate lead generation, automate process, schedule appointments, contact management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver an awe inspiring pitch with this creative Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF bundle. Topics like Ransomware, Reduce Ransomware, Cybersecurity Awareness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Hedge Funds Trading And Investing Strategies Hedge Fund Investor And Manager Tool Kit Themes PDF
This slide highlights the tool kit for investor and manager for investing in hedge funds which includes short selling, active hedging, leverage, dynamic risk management, concentration and litigation techniques. Deliver and pitch your topic in the best possible manner with this Hedge Funds Trading And Investing Strategies Hedge Fund Investor And Manager Tool Kit Themes PDF. Use them to share invaluable insights on Dynamic Risk Management, Application, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Summary PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver and pitch your topic in the best possible manner with this Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Summary PDF. Use them to share invaluable insights on Reduce Ransomware, Reduce Distributed, Approaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
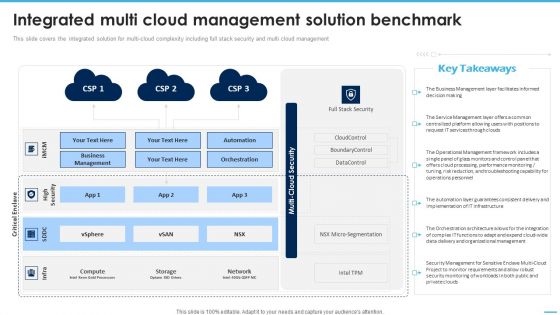
Integrated Multi Cloud Management Solution Benchmark Managing Complexity Of Multiple Cloud Platforms Rules PDF
This slide covers the integrated solution for multi-cloud complexity including full stack security and multi cloud management.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Integrated Multi Cloud Management Solution Benchmark Managing Complexity Of Multiple Cloud Platforms Rules PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
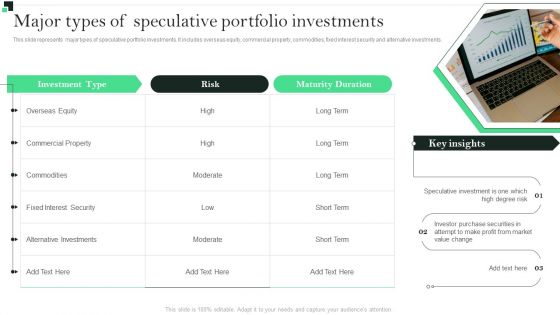
Major Types Of Speculative Portfolio Investments Strategies To Enhance Portfolio Management Portrait PDF
This slide represents major types of speculative portfolio investments. It includes overseas equity, commercial property, commodities, fixed interest security and alternative investments.Create an editable Major Types Of Speculative Portfolio Investments Strategies To Enhance Portfolio Management Portrait PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Major Types Of Speculative Portfolio Investments Strategies To Enhance Portfolio Management Portrait PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Website Audit To Increase Conversion Rate Different Areas Of Website SEO Audit Demonstration PDF
This slide highlights the areas of website audit which includes security audit, performance audit, code audit, website theme audit, UX or UI audit and website architecture audit. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Website Audit To Increase Conversion Rate Different Areas Of Website SEO Audit Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Cloud Computing Scalability Integrated Multi Cloud Management Solution Benchmark Icons PDF
This slide covers the integrated solution for multi-cloud complexity including full stack security and multi cloud management. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Computing Scalability Integrated Multi Cloud Management Solution Benchmark Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Computing Scalability Integrated Multi Cloud Management Solution Benchmark Icons PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
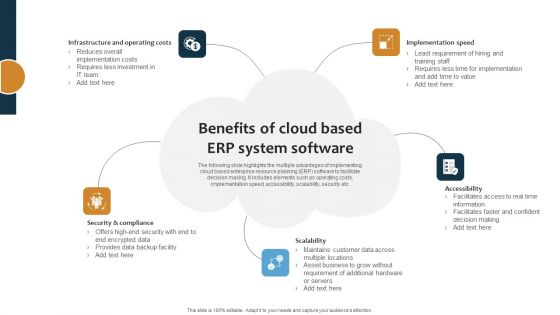
Improving Business Procedures Enterprise Resource Planning System Benefits Of Cloud Based Erp Inspiration PDF
The following slide highlights the multiple advantages of implementing cloud based enterprise resource planning ERP software to facilitate decision making. It includes elements such as operating costs, implementation speed, accessibility, scalability, security etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Improving Business Procedures Enterprise Resource Planning System Benefits Of Cloud Based Erp Inspiration PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
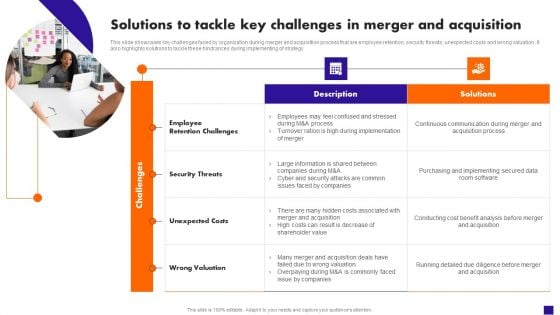
Solutions To Tackle Key Challenges In Merger And Acquisition Portrait PDF
This slide showcases key challenges faced by organization during merger and acquisition process that are employee retention, security threats, unexpected costs and wrong valuation. It also highlights solutions to tackle these hindrances during implementing of strategy. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Solutions To Tackle Key Challenges In Merger And Acquisition Portrait PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
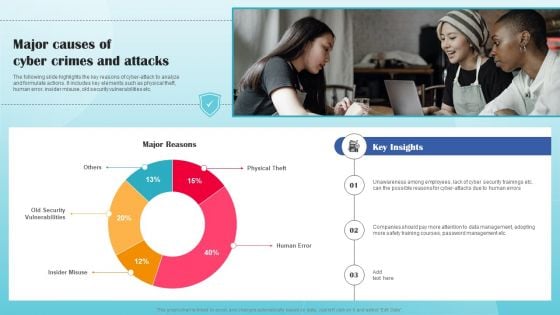
Major Causes Of Cyber Crimes And Attacks Ppt PowerPoint Presentation File Outline PDF
The following slide highlights the key reasons of cyber-attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Find a pre designed and impeccable Major Causes Of Cyber Crimes And Attacks Ppt PowerPoint Presentation File Outline PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
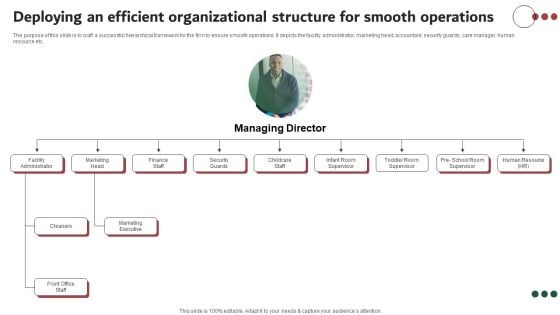
Deploying An Efficient Organizational Structure For Smooth Operations Summary PDF
The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc. Find a pre-designed and impeccable Deploying An Efficient Organizational Structure For Smooth Operations Summary PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Major Milestones Achieved Conglomerate Company Fund Raising Rules Pdf
If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Major Milestones Achieved Conglomerate Company Fund Raising Rules Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents major awards and recognition achieved by diversified manufacturers and technology company. It includes awards such as reddot design award, top 100 internship programs winner, security sales and integration award, the world most admired company, etc.

BYOD Policy Challenges And Mitigation Tips
If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit BYOD Policy Challenges And Mitigation Tips and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide highlights challenges in implementing a Bring Your Own Device BYOD policy, including challenges like device loss, malicious apps, and insecure cloud storage. It also provides practical solutions to mitigate these risks and enhance security in the workplace.
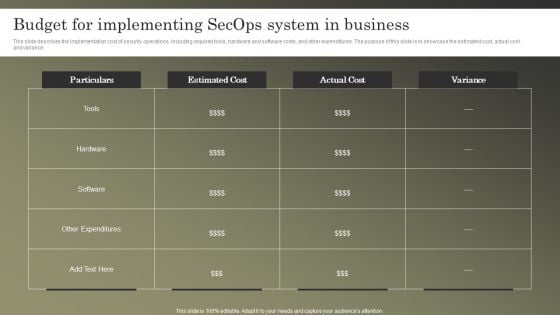
Cybersecurity Operations Cybersecops Budget For Implementing Secops System Elements PDF
This slide describes the implementation cost of security operations, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Boost your pitch with our creative Cybersecurity Operations Cybersecops Budget For Implementing Secops System Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

CASB 2 0 IT CASB Deployment With Optional Components Pricing
This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CASB 2 0 IT CASB Deployment With Optional Components Pricing. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CASB 2 0 IT CASB Deployment With Optional Components Pricing today and make your presentation stand out from the rest This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on.

Cyber Strategies For KPMG For Client Data Protection Pictures PDF
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Boost your pitch with our creative Cyber Strategies For KPMG For Client Data Protection Pictures PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

CASB 2 0 IT Future Use Of Emerging Technologies In CASB Model
This slide gives an overview of the technologies that can be used in the cloud access security broker model in the future. The purpose of this slide is to showcase the various emerging technologies that can help CASB to grow in the future. The technologies include AI, ML, CSPM, data privacy and protection, etc. Want to ace your presentation in front of a live audience Our CASB 2 0 IT Future Use Of Emerging Technologies In CASB Model can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide gives an overview of the technologies that can be used in the cloud access security broker model in the future. The purpose of this slide is to showcase the various emerging technologies that can help CASB to grow in the future. The technologies include AI, ML, CSPM, data privacy and protection, etc.
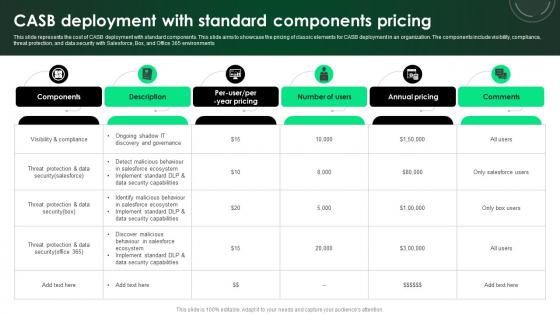
CASB 2 0 IT CASB Deployment With Standard Components Pricing
This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. Whether you have daily or monthly meetings, a brilliant presentation is necessary. CASB 2 0 IT CASB Deployment With Standard Components Pricing can be your best option for delivering a presentation. Represent everything in detail using CASB 2 0 IT CASB Deployment With Standard Components Pricing and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments
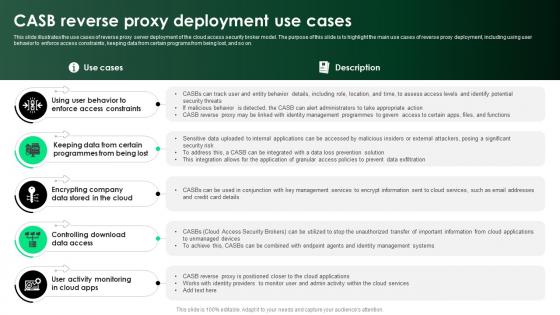
CASB 2 0 IT CASB Reverse Proxy Deployment Use Cases
This slide illustrates the use cases of reverse proxy server deployment of the cloud access security broker model. The purpose of this slide is to highlight the main use cases of reverse proxy deployment, including using user behavior to enforce access constraints, keeping data from certain programs from being lost, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed CASB 2 0 IT CASB Reverse Proxy Deployment Use Cases is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CASB 2 0 IT CASB Reverse Proxy Deployment Use Cases and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide illustrates the use cases of reverse proxy server deployment of the cloud access security broker model. The purpose of this slide is to highlight the main use cases of reverse proxy deployment, including using user behavior to enforce access constraints, keeping data from certain programs from being lost, and so on.
Applications Of Photonics In Safety Silicon Photonics SiPh It Ppt PowerPoint
This slide depicts how photonics helps in peoples safety and security by developing contactless sensors and visual apps, avoiding pollution, detecting structural faults, biometrics and border safety, video surveillance, and detecting illegal goods.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Applications Of Photonics In Safety Silicon Photonics SiPh It Ppt PowerPoint a try. Our experts have put a lot of knowledge and effort into creating this impeccable Applications Of Photonics In Safety Silicon Photonics SiPh It Ppt PowerPoint. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide depicts how photonics helps in peoples safety and security by developing contactless sensors and visual apps, avoiding pollution, detecting structural faults, biometrics and border safety, video surveillance, and detecting illegal goods.

CASB 2 0 IT Pros And Cons Of API Scanning CASB Deployment
This slide outlines the advantages and disadvantages of the API scanning cloud access security broker deployment model. This slide aims to highlight the pros and cons of the API scanning deployment model and the benefits include no impact on user experience, taking only a few hours to configure, etc. Slidegeeks is here to make your presentations a breeze with CASB 2 0 IT Pros And Cons Of API Scanning CASB Deployment With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the advantages and disadvantages of the API scanning cloud access security broker deployment model. This slide aims to highlight the pros and cons of the API scanning deployment model and the benefits include no impact on user experience, taking only a few hours to configure, etc.

The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V
This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. Take your projects to the next level with our ultimate collection of The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc.

CASB 2 0 IT Overview Of CASB Deployment Models
This slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give CASB 2 0 IT Overview Of CASB Deployment Models a try. Our experts have put a lot of knowledge and effort into creating this impeccable CASB 2 0 IT Overview Of CASB Deployment Models. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy.
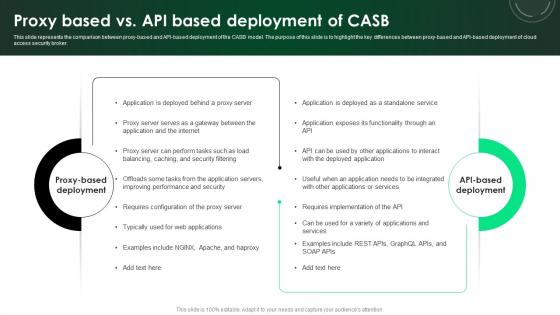
CASB 2 0 IT Proxy Based Vs API Based Deployment Of CASB
This slide represents the comparison between proxy-based and API-based deployment of the CASB model. The purpose of this slide is to highlight the key differences between proxy-based and API-based deployment of cloud access security broker. Whether you have daily or monthly meetings, a brilliant presentation is necessary. CASB 2 0 IT Proxy Based Vs API Based Deployment Of CASB can be your best option for delivering a presentation. Represent everything in detail using CASB 2 0 IT Proxy Based Vs API Based Deployment Of CASB and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the comparison between proxy-based and API-based deployment of the CASB model. The purpose of this slide is to highlight the key differences between proxy-based and API-based deployment of cloud access security broker.

Characteristics Of Strong Devsecops Program In It Role Of Devsecops Ppt Slide
This slide discusses the features adopted for a strong DevSecOps program. The purpose of this slide is to explain the various characteristics these are security awareness and ownership, automated operations, wide scope, shift-left and shift-right, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Characteristics Of Strong Devsecops Program In It Role Of Devsecops Ppt Slide a try. Our experts have put a lot of knowledge and effort into creating this impeccable Characteristics Of Strong Devsecops Program In It Role Of Devsecops Ppt Slide You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide discusses the features adopted for a strong DevSecOps program. The purpose of this slide is to explain the various characteristics these are security awareness and ownership, automated operations, wide scope, shift-left and shift-right, etc.
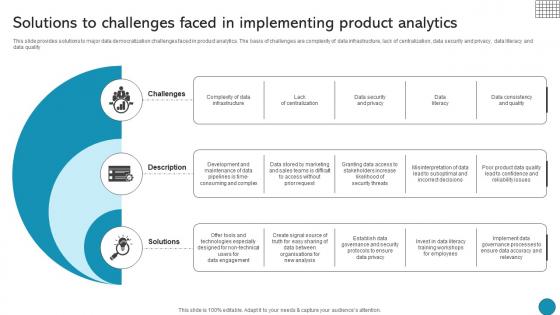
Solutions To Challenges Faced In Implementing Product Driving Business Success Integrating Product
This slide provides solutions to major data democratization challenges faced in product analytics. The basis of challenges are complexity of data infrastructure, lack of centralization, data security and privacy, data literacy and data quality If you are looking for a format to display your unique thoughts, then the professionally designed Solutions To Challenges Faced In Implementing Product Driving Business Success Integrating Product is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Solutions To Challenges Faced In Implementing Product Driving Business Success Integrating Product and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide provides solutions to major data democratization challenges faced in product analytics. The basis of challenges are complexity of data infrastructure, lack of centralization, data security and privacy, data literacy and data quality
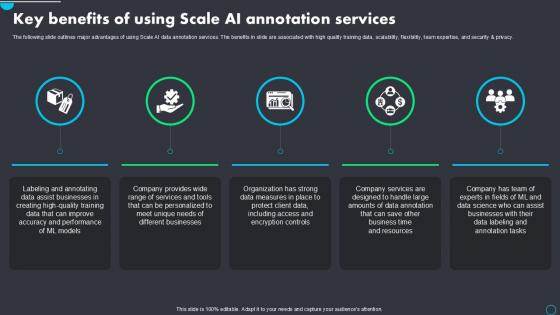
Key Benefits Of Using Implementing Scale AI PPT Presentation AI SS V
The following slide outlines major advantages of using Scale AI data annotation services. The benefits in slide are associated with high quality training data, scalability, flexibility, team expertise, and security and privacy. If you are looking for a format to display your unique thoughts, then the professionally designed Key Benefits Of Using Implementing Scale AI PPT Presentation AI SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Benefits Of Using Implementing Scale AI PPT Presentation AI SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The following slide outlines major advantages of using Scale AI data annotation services. The benefits in slide are associated with high quality training data, scalability, flexibility, team expertise, and security and privacy.
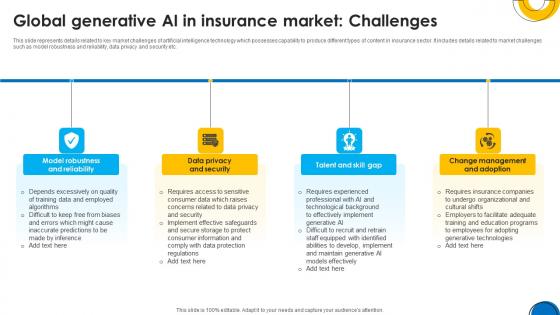
Implementing ChatGpt In Insurance Global Generative AI In Insurance Market ChatGpt SS V
This slide represents details related to key market challenges of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market challenges such as model robustness and reliability, data privacy and security etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing ChatGpt In Insurance Global Generative AI In Insurance Market ChatGpt SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing ChatGpt In Insurance Global Generative AI In Insurance Market ChatGpt SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents details related to key market challenges of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market challenges such as model robustness and reliability, data privacy and security etc.
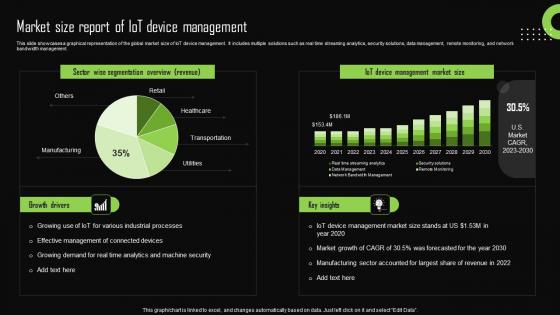
Market Size Report Of Iot Device Management Iot Device Management Demonstration Pdf
This slide showcases a graphical representation of the global market size of IoT device management. It includes multiple solutions such as real time streaming analytics, security solutions, data management, remote monitoring, and network bandwidth management. If you are looking for a format to display your unique thoughts, then the professionally designed Market Size Report Of Iot Device Management Iot Device Management Demonstration Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Market Size Report Of Iot Device Management Iot Device Management Demonstration Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases a graphical representation of the global market size of IoT device management. It includes multiple solutions such as real time streaming analytics, security solutions, data management, remote monitoring, and network bandwidth management.

Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.


 Continue with Email
Continue with Email

 Home
Home


































