Iot Security

Cyber Network Code Security PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with cyber security network data monitor as abstract Factor it all in with our Cyber Network Code Security PowerPoint Templates And PowerPoint Backgrounds 0511. They account for every element.
Identity Info Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with scaned hand for internet identity and security Our Identity Info Security PowerPoint Templates And PowerPoint Backgrounds 0211 make many a feat feasible. They ease out all difficulties.
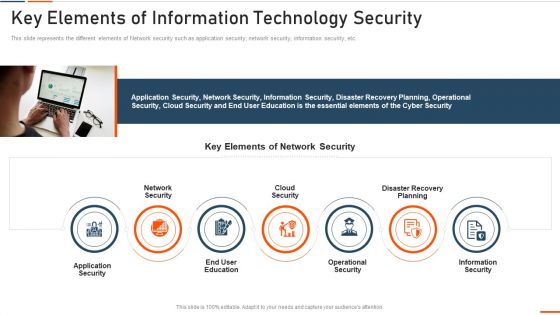
Key Elements Of Information Technology Security Ppt Styles Example PDF
This slide defines the meaning of network security and how it helps to prevent data through different methods and techniques. Presenting key elements of information technology security ppt styles example pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like approach, collective, methods, techniques, procedures, protect. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

House With Key Security PowerPoint Templates And PowerPoint Themes 1112
House With Key Security PowerPoint Templates And PowerPoint Themes 1112-Develop competitive advantage with our above template which contains a diagram of greenhouse connected with keys. This image represents the concept of security. It portrays the concept of building, chain, development, investment, mortgage, residential etc. Our PPT images are so ideally designed that it reveals the very basis of our PPT template are an effective tool to make your clients understand. The structure of our templates allows you to effectively highlight the key issues concerning the growth of your business.-House With Key Security PowerPoint Templates And PowerPoint Themes 1112-This PowerPoint template can be used for presentations relating to-House with key, Security, Design, Business, Abstract, Metaphor The audience will always evince interest. Our House With Key Security PowerPoint Templates And PowerPoint Themes 1112 will make them apply their minds.

Chain Cross Security Leadreship PowerPoint Templates And PowerPoint Themes 1012
Chain Cross Security Leadership PowerPoint Templates And PowerPoint Themes 1012-Create stunning Microsoft office PPT Presentations with our professional templates containing a graphic of red ring connected with chains. This image has been professionally designed to emphasize the concept of strong group. It also depicts the concept of security. Our stunning image makes your presentations friendly and simpler showing that you care about even the smallest details.-Chain Cross Security Leadreship PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Chain cross, security, business, chains, success, leadership Use our Chain Cross Security Leadreship PowerPoint Templates And PowerPoint Themes 1012 as an experimental tool. Try them out to get the correct effect.

Labyrinth With Key Security PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with white circle labyrinth with key No matter how far flung your clientele is. Connect with them all through our Labyrinth With Key Security PowerPoint Backgrounds And Templates 1210.

Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Cyber Security Vector Icon Ppt PowerPoint Presentation Inspiration
Presenting this set of slides with name cyber security vector icon ppt powerpoint presentation inspiration. This is a one stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Business Context Diagram 3d Man With Chain Security PowerPoint Slides
We present our business context diagram 3d man with chain security PowerPoint Slides.Download our Security PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Present our Chains PowerPoint Templates because Our PowerPoint Templates and Slides will effectively help you save your valuable time. They are readymade to fit into any presentation structure. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need. Use our Process and Flows PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download and present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time.Use these PowerPoint slides for presentations relating to 3d, Business, Chain, Connect, Connection, Heavy, Industrial, Industry, Isolated, Link, Linked, Man, Metal, Power, Powerful, Protection, Secure, Steel, Strength, Support, Symbol, Teamwork, Weak, White. The prominent colors used in the PowerPoint template are Blue, Gray, Black. Professionals tell us our business context diagram 3d man with chain security PowerPoint Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. The feedback we get is that our Industry PowerPoint templates and PPT Slides are designed to make your presentations professional. Professionals tell us our business context diagram 3d man with chain security PowerPoint Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. People tell us our Connection PowerPoint templates and PPT Slides are designed by professionals PowerPoint presentation experts tell us our business context diagram 3d man with chain security PowerPoint Slides look good visually. You can be sure our Industry PowerPoint templates and PPT Slides will make you look like a winner. You've found a treasure for presentations. Get goingwith our Business Context Diagram 3d Man With Chain Security PowerPoint Slides. You'll deliver your best presentation yet.
Multiple Device Based Internet Of Things Security Icon Formats Pdf
Showcasing this set of slides titled Multiple Device Based Internet Of Things Security Icon Formats Pdf The topics addressed in these templates are Multiple Device Based, Internet Of Things, Security Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Multiple Device Based Internet Of Things Security Icon Formats Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Importance Of 5G Network Security Policies Portrait Pdf
This slide highlights importance for 5G network security policies for Network stabilization. It further includes security EU, access network security , core network security etc. Showcasing this set of slides titled Importance Of 5G Network Security Policies Portrait Pdf. The topics addressed in these templates are Access Network Security, Core Network Security, Security Enablers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights importance for 5G network security policies for Network stabilization. It further includes security EU, access network security , core network security etc.
Internet Of Things Security Icon For Home Safety Background Pdf
Pitch your topic with ease and precision using this Internet Of Things Security Icon For Home Safety Background Pdf This layout presents information on Internet Of Things Security, Icon For Home Safety It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Internet Of Things Security Icon For Home Safety Background Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
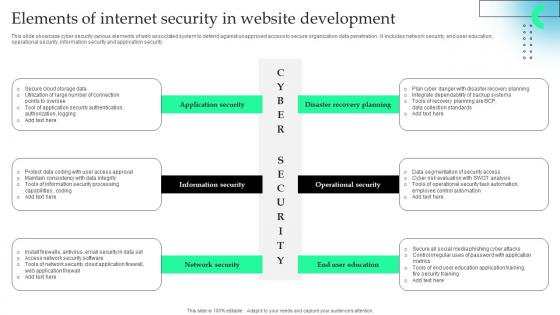
Elements Of Internet Security In Website Development Formats Pdf
This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.Pitch your topic with ease and precision using this Elements Of Internet Security In Website Development Formats Pdf This layout presents information on Information Security, Network Security, Operational Security It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.
Internet Of Things Security Icon For Software Management Template Pdf
Showcasing this set of slides titled Internet Of Things Security Icon For Software Management Template Pdf The topics addressed in these templates are Internet Of Things Security, Icon For Software, Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Internet Of Things Security Icon For Software Management Template Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

4 Steps For Building Internet Security Strategy Clipart Pdf
This slide showcase developing and implementation of cyber security strategy for streamline the data security and organization vision and mission. It includes cyber threat landscape, assess cybersecurity maturity, determine security program and document cybersecurity strategy.Showcasing this set of slides titled 4 Steps For Building Internet Security Strategy Clipart Pdf The topics addressed in these templates are Cyber Security Maturity, Cyber Security Program, Document Cybersecurity Strategy All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase developing and implementation of cyber security strategy for streamline the data security and organization vision and mission. It includes cyber threat landscape, assess cybersecurity maturity, determine security program and document cybersecurity strategy.

Global 5G Network Security Market Dynamics Designs Pdf
This slide shows 5g security market dynamics globally to understand market scenario . It further includes dynamics such as increasing cyber attacks , Emergence of IoT, AI, Machine Learning, and Blockchain Technologies etc. Showcasing this set of slides titled Global 5G Network Security Market Dynamics Designs Pdf. The topics addressed in these templates are Market Dynamics, Description. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows 5g security market dynamics globally to understand market scenario . It further includes dynamics such as increasing cyber attacks , Emergence of IoT, AI, Machine Learning, and Blockchain Technologies etc.
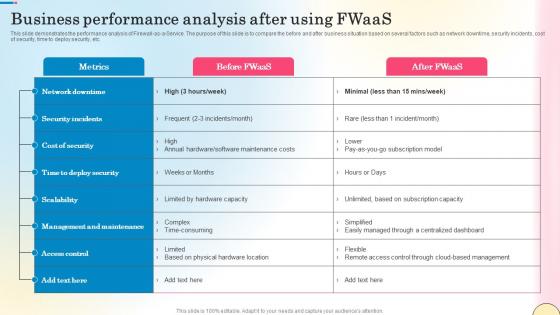
Business Performance Analysis After Using Fwaas Network Security Sample Pdf
This slide demonstrates the performance analysis of Firewall-as-a-Service. The purpose of this slide is to compare the before and after business situation based on several factors such as network downtime, security incidents, cost of security, time to deploy security, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Business Performance Analysis After Using Fwaas Network Security Sample Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide demonstrates the performance analysis of Firewall-as-a-Service. The purpose of this slide is to compare the before and after business situation based on several factors such as network downtime, security incidents, cost of security, time to deploy security, etc.
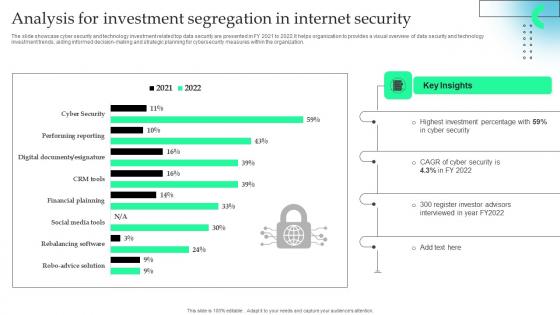
Analysis For Investment Segregation In Internet Security Formats Pdf
The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.Pitch your topic with ease and precision using this Analysis For Investment Segregation In Internet Security Formats Pdf This layout presents information on Highest Investment, Register Investor Advisors, Key Insights It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.

Key Aspects Of 5G Network Security Topics Pdf
This slide highlights 5G security policies for various domains. It further includes network, user equipment, management, access network and applications. Pitch your topic with ease and precision using this Key Aspects Of 5G Network Security Topics Pdf. This layout presents information on Security Domains, Description, Importance Level. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights 5G security policies for various domains. It further includes network, user equipment, management, access network and applications.
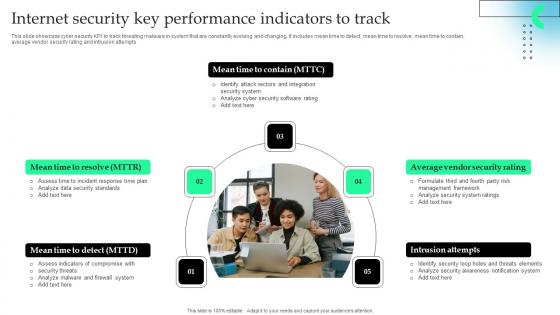
Internet Security Key Performance Indicators To Track Microsoft Pdf
This slide showcase cyber security KPI to track threating malware in system that are constantly evolving and changing. It includes mean time to detect, mean time to resolve, mean time to contain, average vendor security rating and intrusion attempts.Showcasing this set of slides titled Internet Security Key Performance Indicators To Track Microsoft Pdf The topics addressed in these templates are Firewall System, Security Standards, Identify Attack All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security KPI to track threating malware in system that are constantly evolving and changing. It includes mean time to detect, mean time to resolve, mean time to contain, average vendor security rating and intrusion attempts.
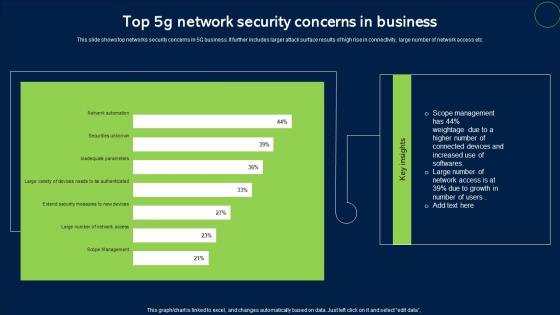
Top 5G Network Security Concerns In Business Sample Pdf
This slide shows top networks security concerns in 5G business. It further includes larger attack surface results of high rise in connectivity, large number of network access etc. Pitch your topic with ease and precision using this Top 5G Network Security Concerns In Business Sample Pdf. This layout presents information on Network Security, Concerns In Business. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows top networks security concerns in 5G business. It further includes larger attack surface results of high rise in connectivity, large number of network access etc.
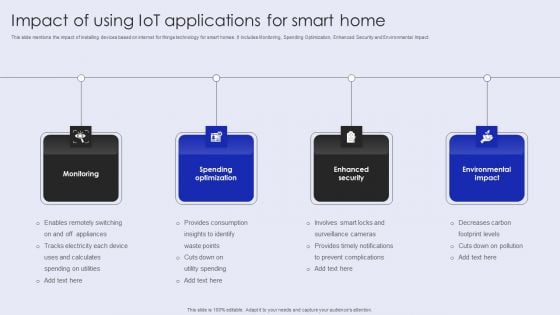
Impact Of Using Iot Applications For Smart Home Template PDF
This slide mentions the impact of installing devices based on internet for things technology for smart homes. It includes Monitoring, Spending Optimization, Enhanced Security and Environmental Impact. Persuade your audience using this Impact Of Using Iot Applications For Smart Home Template PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Spending Optimization, Enhanced Security, Environmental Impact. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
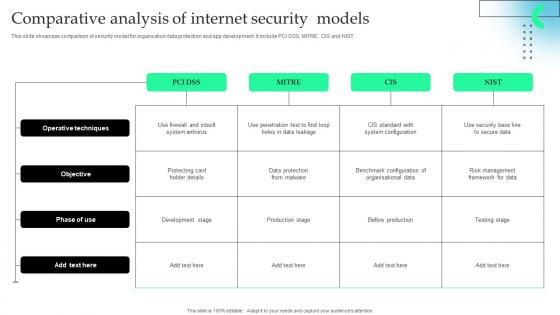
Comparative Analysis Of Internet Security Models Slides Pdf
This slide showcase comparison of security model for organsation data protection and app development. It include PCI DSS, MITRE, CIS and NIST Pitch your topic with ease and precision using this Comparative Analysis Of Internet Security Models Slides Pdf This layout presents information on Operative Techniques, Development Stage, Benchmark Configuration It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase comparison of security model for organsation data protection and app development. It include PCI DSS, MITRE, CIS and NIST
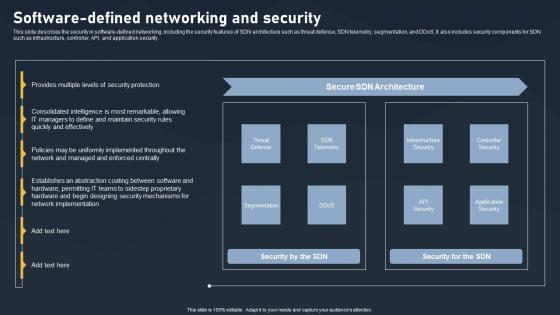
Software Defined Networking And Security SDN Building Blocks Portrait Pdf
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Software Defined Networking And Security SDN Building Blocks Portrait Pdf can be your best option for delivering a presentation. Represent everything in detail using Software Defined Networking And Security SDN Building Blocks Portrait Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security.
Virtual Security Hazards And Network Hacking Icon Diagrams Pdf
Pitch your topic with ease and precision using this Virtual Security Hazards And Network Hacking Icon Diagrams Pdf. This layout presents information on Virtual Security, Hazards, Network Hacking. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Virtual Security Hazards And Network Hacking Icon Diagrams Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
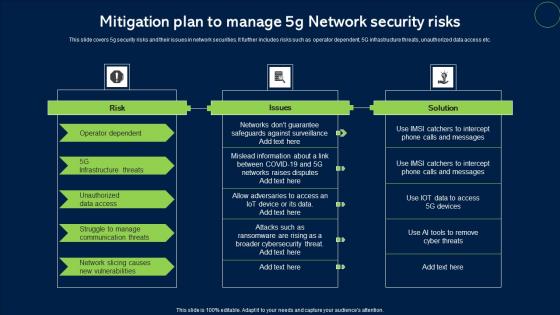
Mitigation Plan To Manage 5G Network Security Risks Microsoft Pdf
This slide covers 5g security risks and their issues in network securities. It further includes risks such as operator dependent, 5G infrastructure threats, unauthorized data access etc. Showcasing this set of slides titled Mitigation Plan To Manage 5G Network Security Risks Microsoft Pdf. The topics addressed in these templates are Risk, Issues, Solution. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide covers 5g security risks and their issues in network securities. It further includes risks such as operator dependent, 5G infrastructure threats, unauthorized data access etc.
Email Phishing And Internet Security Icon Microsoft Pdf
Showcasing this set of slides titled Email Phishing And Internet Security Icon Microsoft Pdf The topics addressed in these templates are Email Phishing, Internet Security Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Email Phishing And Internet Security Icon Microsoft Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Internet Security And Data Audit Icon Pictures Pdf
Pitch your topic with ease and precision using this Internet Security And Data Audit Icon Pictures Pdf This layout presents information on Internet Security, Data Audit Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Internet Security And Data Audit Icon Pictures Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Internet Security Kpi Icon With Monitor Summary Pdf
Pitch your topic with ease and precision using this Internet Security Kpi Icon With Monitor Summary Pdf This layout presents information on Internet Security KPI, Icon Monitor It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Internet Security Kpi Icon With Monitor Summary Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Zero Trust Model Traditional Perimeter Based Network Security Overview
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Model Traditional Perimeter Based Network Security Overview is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Model Traditional Perimeter Based Network Security Overview and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.
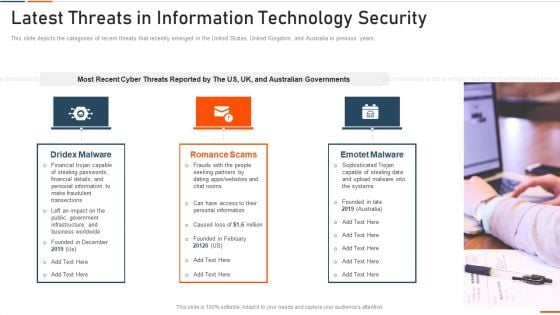
Latest Threats In Information Technology Security Ppt Pictures Designs PDF
This slide represents the different elements of Network security such as application security, network security, information security, etc. This is a latest threats in information technology security ppt pictures designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network security, cloud security, application security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Internet Security Challenges And Solutions In Banking Industry Download Pdf
This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.Showcasing this set of slides titled Internet Security Challenges And Solutions In Banking Industry Download Pdf The topics addressed in these templates are Installing Intergraded, Introducing Firewall, Learning Algorisms All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.
5G Network Security Icon For Device Safety Sample Pdf
Pitch your topic with ease and precision using this 5G Network Security Icon For Device Safety Sample Pdf. This layout presents information on 5G Network Security, Device Safety. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our 5G Network Security Icon For Device Safety Sample Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Green Computing Improving Security By Green Computing Technology
This slide outlineshow green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. The Green Computing Improving Security By Green Computing Technology is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide outlineshow green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.

Internet Security Management In Powerpoint And Google Slides Cpb
Introducing our well designed Internet Security Management In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Internet Security Management. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Internet Security Management In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
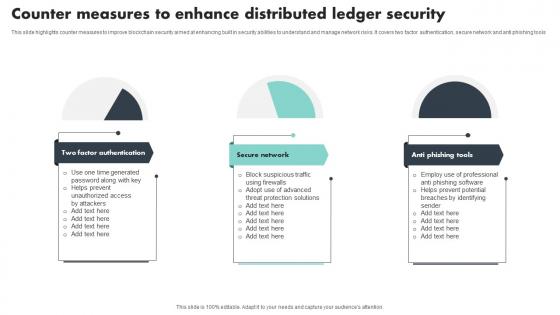
Counter Measures To Enhance Distributed Ledger Security Mockup Pdf
This slide highlights counter measures to improve blockchain security aimed at enhancing built in security abilities to understand and manage network risks. It covers two factor authentication, secure network and anti phishing tools Showcasing this set of slides titled Counter Measures To Enhance Distributed Ledger Security Mockup Pdf The topics addressed in these templates are Factor Authentication, Secure Network, Anti Phishing Tools All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights counter measures to improve blockchain security aimed at enhancing built in security abilities to understand and manage network risks. It covers two factor authentication, secure network and anti phishing tools
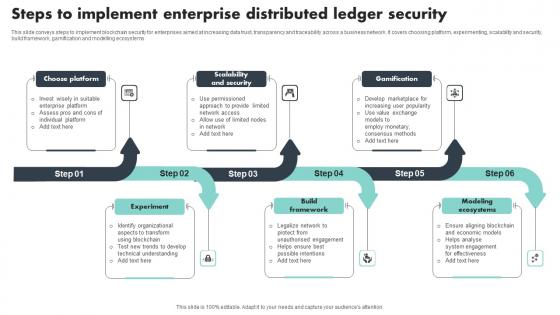
Steps To Implement Enterprise Distributed Ledger Security Download Pdf
This slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems Pitch your topic with ease and precision using this Steps To Implement Enterprise Distributed Ledger Security Download Pdf This layout presents information on Choose Platform, Scalability And Security, Gamification It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems

Improving Security By Green Computing Technology Eco Friendly Computing IT
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.Are you searching for a Improving Security By Green Computing Technology Eco Friendly Computing IT that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Improving Security By Green Computing Technology Eco Friendly Computing IT from Slidegeeks today. This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.
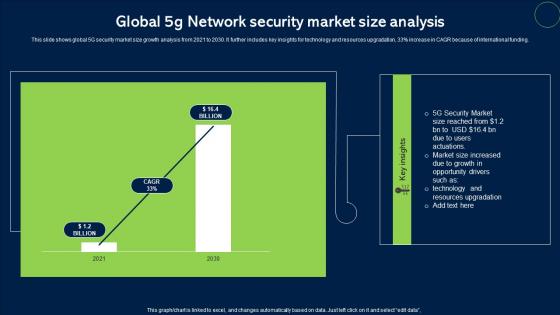
Global 5G Network Security Market Size Analysis Topics Pdf
This slide shows global 5G security market size growth analysis from 2021 to 2030. It further includes key insights for technology and resources upgradation, 33percent increase in CAGR because of international funding. Pitch your topic with ease and precision using this Global 5G Network Security Market Size Analysis Topics Pdf. This layout presents information on Network Security, Market Size. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows global 5G security market size growth analysis from 2021 to 2030. It further includes key insights for technology and resources upgradation, 33percent increase in CAGR because of international funding.

Network Security Checklist Template In Powerpoint And Google Slides Cpb
Introducing our well designed Network Security Checklist Template In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Network Security Checklist Template. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Network Security Checklist Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
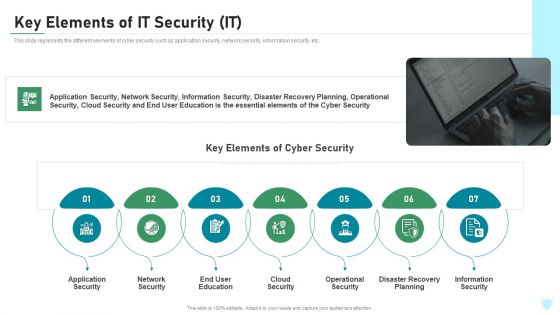
Key Elements Of IT Security IT Ppt Pictures Inspiration PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a key elements of it security it ppt pictures inspiration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, end user education, cloud security, operational security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Zero Trust Network Security Pictures Pdf
Find a pre-designed and impeccable Agenda For Zero Trust Network Security Pictures Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda For Zero Trust Network Security Pictures Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Contents For Zero Trust Network Security Introduction Pdf
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Table Of Contents For Zero Trust Network Security Introduction Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. Our Table Of Contents For Zero Trust Network Security Introduction Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Example Of Security Testing Services Ppt Powerpoint Guide
This is a example of security testing services ppt powerpoint guide. This is a eight stage process. The stages in this process are security management, access security, application security, networking security, test delivery, results and analysis, technology enablement, test development and publishing.
5G Network Security Technologies To Overcome Threats Icons Pdf
This slide shows 5G network technologies to overcome threats in network. It further includes dos attacks, hijacking attacks, user identity theft, scanning attacks, timings attacks and boundary attacks. Showcasing this set of slides titled 5G Network Security Technologies To Overcome Threats Icons Pdf. The topics addressed in these templates are Security Threat, Impact, Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows 5G network technologies to overcome threats in network. It further includes dos attacks, hijacking attacks, user identity theft, scanning attacks, timings attacks and boundary attacks.
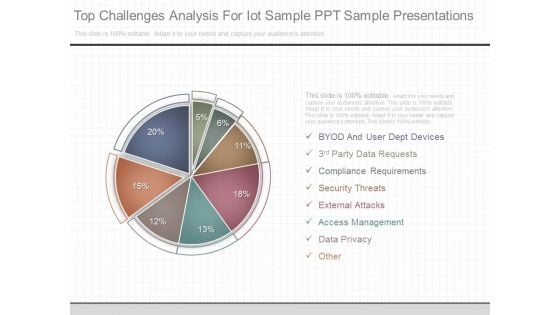
Top Challenges Analysis For Iot Sample Ppt Sample Presentations
This is a top challenges analysis for iot sample ppt sample presentations. This is a eight stage process. The stages in this process are byod and user dept devices, 3rd party data requests, compliance requirements, security threats, external attacks, access management, data privacy, other.

Levels Of Security Concerns In Cloud Network Download PDF
The slide showcases levels of security concerns that measure user and device authentication. The elements are virtual machine security , network security , interface security , privacy concerns etc. Presenting Levels Of Security Concerns In Cloud Network Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Virtual Machine Security, Interface Security, Network Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Network Security Enterprise Ppt Powerpoint Presentation Infographics Templates Cpb
This is a network security enterprise ppt powerpoint presentation infographics templates cpb. This is a five stage process. The stages in this process are network security enterprise.

Application Of Internet Security In Operational Technology Pictures Pdf
This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.Showcasing this set of slides titled Application Of Internet Security In Operational Technology Pictures Pdf The topics addressed in these templates are Consequence Driven Scenarios, Execute Prioritized, Risk Identified All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.
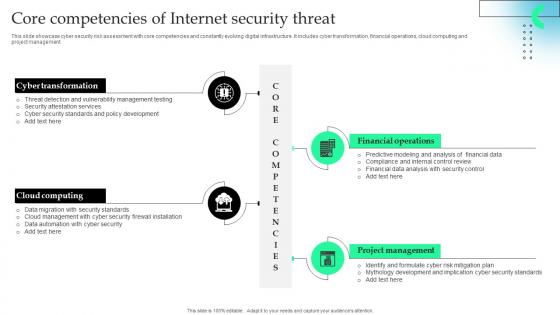
Core Competencies Of Internet Security Threat Portrait Pdf
This slide showcase cyber security risk assessment with core competencies and constantly evolving digital infrastructure. It includes cyber transformation, financial operations, cloud computing and project management.Showcasing this set of slides titled Core Competencies Of Internet Security Threat Portrait Pdf The topics addressed in these templates are Cyber Transformation, Cloud Computing, Financial Operations All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security risk assessment with core competencies and constantly evolving digital infrastructure. It includes cyber transformation, financial operations, cloud computing and project management.

Features Of Zero Trust Network Access Security Model Background Pdf
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Background Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Background Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.
5G Wi Fi Signal Icon For Network Security Inspiration Pdf
Pitch your topic with ease and precision using this 5G Wi Fi Signal Icon For Network Security Inspiration Pdf. This layout presents information on 5G Wi Fi Signal, Network Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our 5G Wi Fi Signal Icon For Network Security Inspiration Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Default Network Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Default Network Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Default Network Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Default Network Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Solar Computing IT Improving Security By Green Computing Technology
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Are you searching for a Solar Computing IT Improving Security By Green Computing Technology that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Solar Computing IT Improving Security By Green Computing Technology from Slidegeeks today. This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.
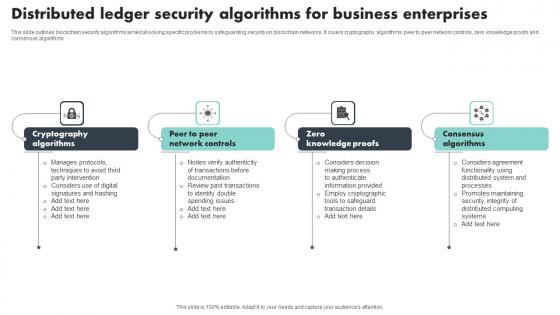
Distributed Ledger Security Algorithms For Business Enterprises Structure Pdf
This slide outlines blockchain security algorithms aimed at solving specific problems by safeguarding security on blockchain networks. It covers cryptography algorithms, peer to peer network controls, zero knowledge proofs and consensus algorithms Showcasing this set of slides titled Distributed Ledger Security Algorithms For Business Enterprises Structure Pdf The topics addressed in these templates are Cryptography Algorithms, Knowledge Proofs, Consensus Algorithms All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide outlines blockchain security algorithms aimed at solving specific problems by safeguarding security on blockchain networks. It covers cryptography algorithms, peer to peer network controls, zero knowledge proofs and consensus algorithms
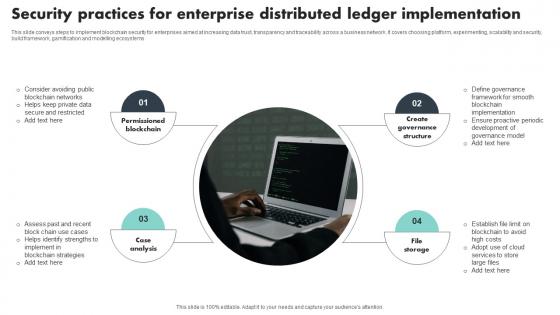
Security Practices For Enterprise Distributed Ledger Implementation Template Pdf
This slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems Showcasing this set of slides titled Security Practices For Enterprise Distributed Ledger Implementation Template Pdf The topics addressed in these templates are Permissioned Blockchain, Case Analysis, Create Governance Structure All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems
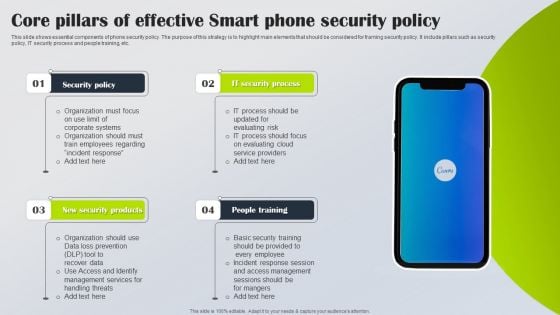
Core Pillars Of Effective Smart Phone Security Policy Slides PDF
This slide shows essential components of phone security policy. The purpose of this strategy is to highlight main elements that should be considered for framing security policy. It include pillars such as security policy, IT security process and people training, etc. Persuade your audience using this Core Pillars Of Effective Smart Phone Security Policy Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Policy, IT Security Process, New Security Products. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
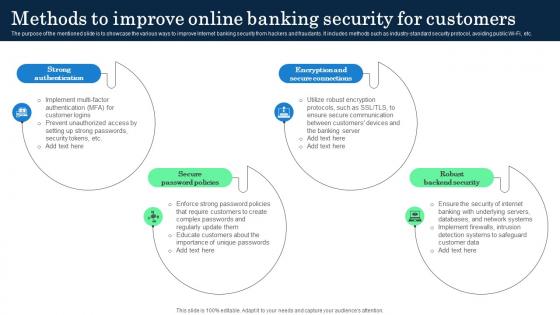
Methods To Improve Online Banking Security Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc. Do you know about Slidesgeeks Methods To Improve Online Banking Security Incorporating Banking Operational Growth These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc.
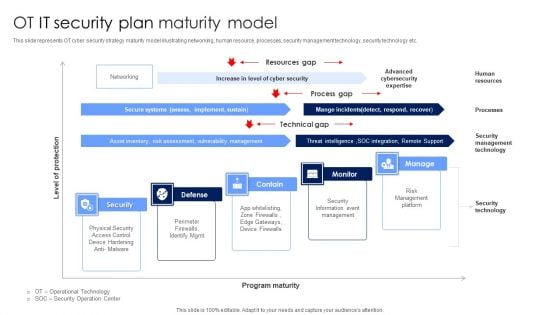
OT IT Security Plan Maturity Model Designs PDF
This slide represents OT cyber security strategy maturity model illustrating networking, human resource, processes, security management technology, security technology etc. Showcasing this set of slides titled OT IT Security Plan Maturity Model Designs PDF. The topics addressed in these templates are Security Information Event Management, Risk Management Platform, Security Technology. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Network Security Dark Overlord In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Network Security Dark Overlord In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Network Security Dark Overlord that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Network Security Dark Overlord In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































