Iot Security
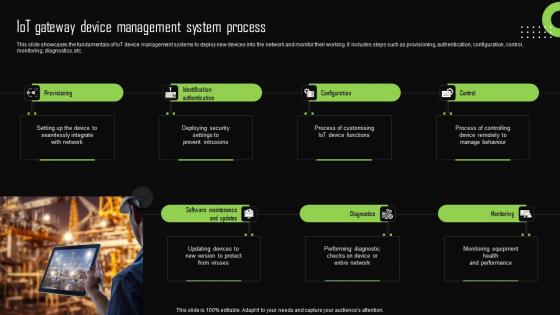
Iot Gateway Device Management System Process Iot Device Management Portrait Pdf
This slide showcases the fundamentals of IoT device management systems to deploy new devices into the network and monitor their working. It includes steps such as provisioning, authentication, configuration, control, monitoring, diagnostics, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Iot Gateway Device Management System Process Iot Device Management Portrait Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases the fundamentals of IoT device management systems to deploy new devices into the network and monitor their working. It includes steps such as provisioning, authentication, configuration, control, monitoring, diagnostics, etc.
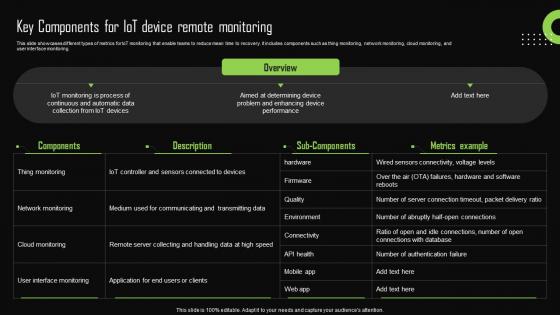
Key Components For Iot Device Remote Monitoring Iot Device Management Ideas Pdf
This slide showcases different types of metrics for IoT monitoring that enable teams to reduce mean time to recovery. It includes components such as thing monitoring, network monitoring, cloud monitoring, and user interface monitoring. Present like a pro with Key Components For Iot Device Remote Monitoring Iot Device Management Ideas Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases different types of metrics for IoT monitoring that enable teams to reduce mean time to recovery. It includes components such as thing monitoring, network monitoring, cloud monitoring, and user interface monitoring.

Hazardous Waste Management To Enhance Workers Safety IOT Applications In Smart Waste IoT SS V
This slide includes information about hazardous waste management to significantly improve workers safety and resource allocation in smart cities. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Hazardous Waste Management To Enhance Workers Safety IOT Applications In Smart Waste IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide includes information about hazardous waste management to significantly improve workers safety and resource allocation in smart cities.
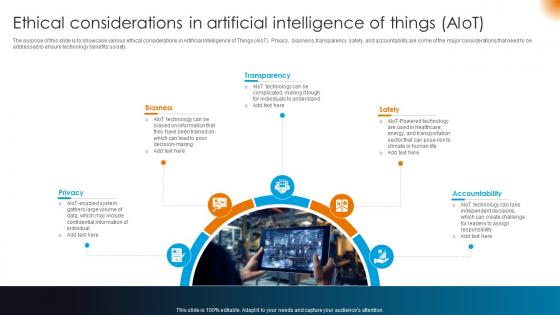
Integrating AI With IoT Ethical Considerations In Artificial Intelligence Of Things AIoT IoT SS V
The purpose of this slide is to showcase various ethical considerations in Artificial Intelligence of Things AIoT. Privacy, biasness, transparency, safety, and accountability are some of the major considerations that need to be addressed to ensure technology benefits society. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Integrating AI With IoT Ethical Considerations In Artificial Intelligence Of Things AIoT IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Integrating AI With IoT Ethical Considerations In Artificial Intelligence Of Things AIoT IoT SS V effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The purpose of this slide is to showcase various ethical considerations in Artificial Intelligence of Things AIoT. Privacy, biasness, transparency, safety, and accountability are some of the major considerations that need to be addressed to ensure technology benefits society.
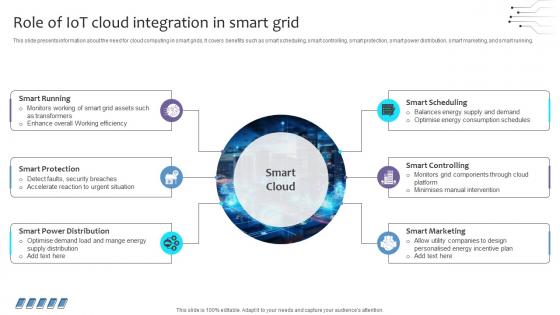
Empowering The Future Role Of IoT Cloud Integration In Smart Grid IoT SS V
This slide presents information about the need for cloud computing in smart grids. It covers benefits such as smart scheduling, smart controlling, smart protection, smart power distribution, smart marketing, and smart running. If you are looking for a format to display your unique thoughts, then the professionally designed Empowering The Future Role Of IoT Cloud Integration In Smart Grid IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Empowering The Future Role Of IoT Cloud Integration In Smart Grid IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide presents information about the need for cloud computing in smart grids. It covers benefits such as smart scheduling, smart controlling, smart protection, smart power distribution, smart marketing, and smart running.

Robotics In IoT To Gain Data Driven Insights Optimizing Inventory Management IoT SS V
This slide provides an overview of the robotics technology used to transfer data. The slide further includes applications and benefits that are it enhance automation, improve quality, ensure workplace safety and increase efficiency. Are you searching for a Robotics In IoT To Gain Data Driven Insights Optimizing Inventory Management IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Robotics In IoT To Gain Data Driven Insights Optimizing Inventory Management IoT SS V from Slidegeeks today. This slide provides an overview of the robotics technology used to transfer data. The slide further includes applications and benefits that are it enhance automation, improve quality, ensure workplace safety and increase efficiency.
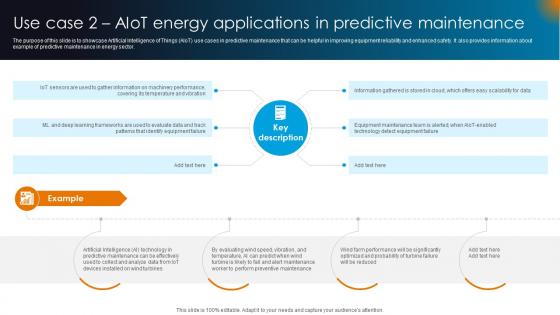
Integrating AI With IoT Use Case 2 AIoT Energy Applications In Predictive Maintenance IoT SS V
The purpose of this slide is to showcase Artificial Intelligence of Things AIoT use cases in predictive maintenance that can be helpful in improving equipment reliability and enhanced safety. It also provides information about example of predictive maintenance in energy sector. This Integrating AI With IoT Use Case 2 AIoT Energy Applications In Predictive Maintenance IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Integrating AI With IoT Use Case 2 AIoT Energy Applications In Predictive Maintenance IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The purpose of this slide is to showcase Artificial Intelligence of Things AIoT use cases in predictive maintenance that can be helpful in improving equipment reliability and enhanced safety. It also provides information about example of predictive maintenance in energy sector.
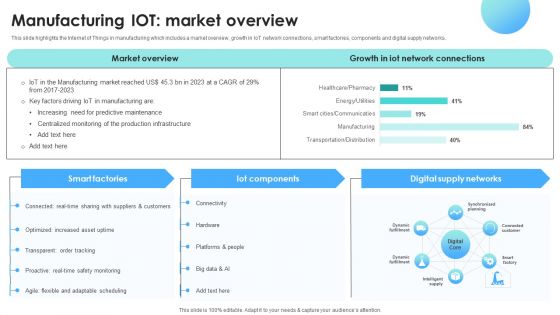
IOT Use Cases For Manufacturing Manufacturing IOT Market Overview Brochure PDF
This slide highlights the Internet of Things in manufacturing which includes a market overview, growth in IoT network connections, smart factories, components and digital supply networks. Are you searching for a IOT Use Cases For Manufacturing Manufacturing IOT Market Overview Brochure PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IOT Use Cases For Manufacturing Manufacturing IOT Market Overview Brochure PDF from Slidegeeks today.
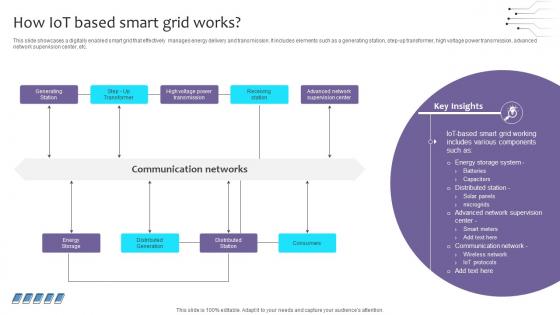
Empowering The Future How IoT Based Smart Grid Works IoT SS V
This slide showcases a digitally enabled smart grid that effectively manages energy delivery and transmission. It includes elements such as a generating station, step-up transformer, high voltage power transmission, advanced network supervision center, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Empowering The Future How IoT Based Smart Grid Works IoT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Empowering The Future How IoT Based Smart Grid Works IoT SS V. This slide showcases a digitally enabled smart grid that effectively manages energy delivery and transmission. It includes elements such as a generating station, step-up transformer, high voltage power transmission, advanced network supervision center, etc.
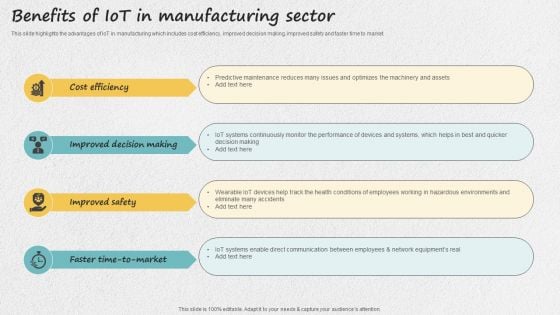
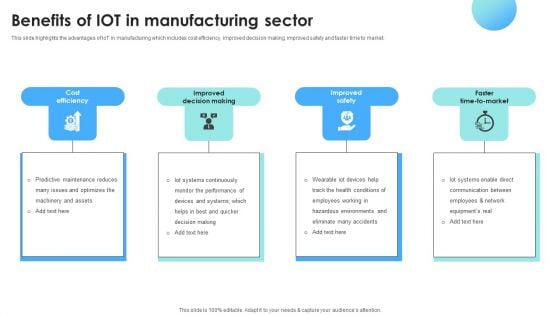
Iot Applications For Manufacturing Industry Benefits Of Iot In Manufacturing Sector Designs PDF
This slide highlights the advantages of IoT in manufacturing which includes cost efficiency, improved decision making, improved safety and faster time to market. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Iot Applications For Manufacturing Industry Benefits Of Iot In Manufacturing Sector Designs PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Iot Applications For Manufacturing Industry Benefits Of Iot In Manufacturing Sector Designs PDF
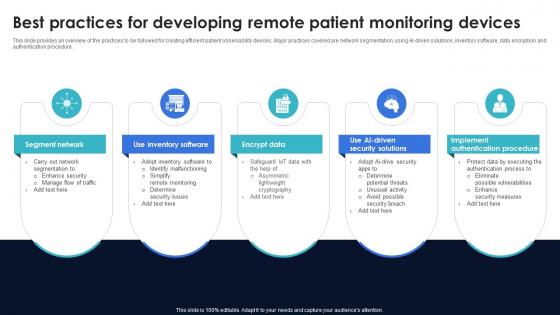
Optimization Of IoT Remote Monitoring Best Practices For Developing Remote Patient Monitoring IoT SS V
This slide provides an overview of the practices to be followed for creating efficient patient observability devices. Major practices covered are network segmentation, using AI-driven solutions, inventory software, data encryption and authentication procedure. Present like a pro with Optimization Of IoT Remote Monitoring Best Practices For Developing Remote Patient Monitoring IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide provides an overview of the practices to be followed for creating efficient patient observability devices. Major practices covered are network segmentation, using AI-driven solutions, inventory software, data encryption and authentication procedure.

Iot Device Management Architecture For Real Time Iot Device Management Introduction Pdf
This slide exhibits architecture showcasing automated irrigation in agriculture with various technologies. It includes elements such as irrigation controller, sensors, software gateway, cellular network, vendors, device management servers, etc. Find a pre-designed and impeccable Iot Device Management Architecture For Real Time Iot Device Management Introduction Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide exhibits architecture showcasing automated irrigation in agriculture with various technologies. It includes elements such as irrigation controller, sensors, software gateway, cellular network, vendors, device management servers, etc.
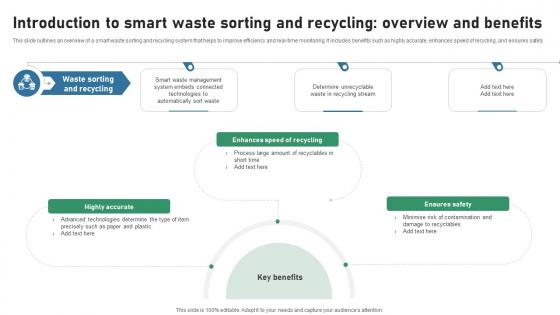
Introduction To Smart Waste Sorting And Recycling Overview IOT Applications In Smart Waste IoT SS V
This slide outlines an overview of a smart waste sorting and recycling system that helps to improve efficiency and real-time monitoring. It includes benefits such as highly accurate, enhances speed of recycling, and ensures safety. Welcome to our selection of the Introduction To Smart Waste Sorting And Recycling Overview IOT Applications In Smart Waste IoT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines an overview of a smart waste sorting and recycling system that helps to improve efficiency and real-time monitoring. It includes benefits such as highly accurate, enhances speed of recycling, and ensures safety.

IoT Solutions For Oil Case Study On Remote Pipeline Monitoring System IoT SS V
This slide exhibits a comprehensive case study of pipeline monitoring, enhancing safety and operations. It includes elements such as company, industry, goals, challenges faced, solutions implemented, and benefits to business. Slidegeeks is here to make your presentations a breeze with IoT Solutions For Oil Case Study On Remote Pipeline Monitoring System IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide exhibits a comprehensive case study of pipeline monitoring, enhancing safety and operations. It includes elements such as company, industry, goals, challenges faced, solutions implemented, and benefits to business.

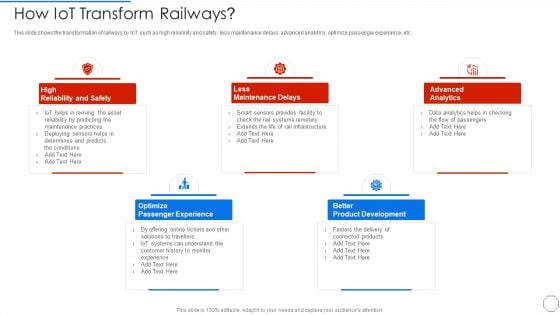
Iot And Digital Twin To Reduce Costs Post Covid How Iot Transform Railways Formats PDF
This slide shows the transformation of railways by IoT such as high reliability and safety, less maintenance delays, advanced analytics, optimize passenger experience, etc. Presenting iot and digital twin to reduce costs post covid how iot transform railways formats pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like high reliability and safety, less maintenance delays, advanced analytics, optimize passenger experience, better product development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Iot Digital Twin Technology Post Covid Expenditure Management How Iot Transform Railways Designs PDF
This slide shows the transformation of railways by IoT such as high reliability and safety, less maintenance delays, advanced analytics, optimize passenger experience, etc. Presenting iot digital twin technology post covid expenditure management how iot transform railways designs pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like maintenance, experience, development, reliability . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Minimizing Operational Cost Through Iot Virtual Twins Implementation How Iot Transform Mockup PDF
This slide shows the transformation of railways by IoT such as high reliability and safety, less maintenance delays, advanced analytics, optimize passenger experience, etc. This is a minimizing operational cost through iot virtual twins implementation how iot transform mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, data, development, product. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IOT Use Cases For Manufacturing Benefits Of IOT In Manufacturing Sector Background PDF
This slide highlights the advantages of IoT in manufacturing which includes cost efficiency, improved decision making, improved safety and faster time to market. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate IOT Use Cases For Manufacturing Benefits Of IOT In Manufacturing Sector Background PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
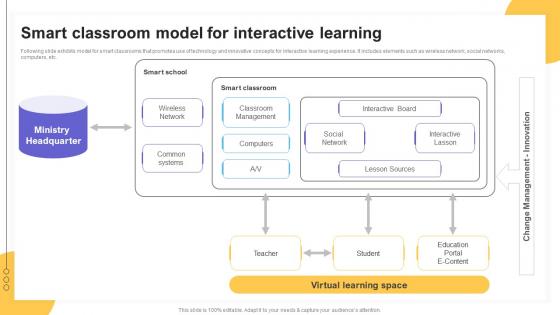
Smart Classroom Model For Interactive Learning Impact Of IoT Technology On Education IoT SS V
Following slide exhibits model for smart classrooms that promotes use of technology and innovative concepts for interactive learning experience. It includes elements such as wireless network, social networks, computers, etc. There are so many reasons you need a Smart Classroom Model For Interactive Learning Impact Of IoT Technology On Education IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide exhibits model for smart classrooms that promotes use of technology and innovative concepts for interactive learning experience. It includes elements such as wireless network, social networks, computers, etc.
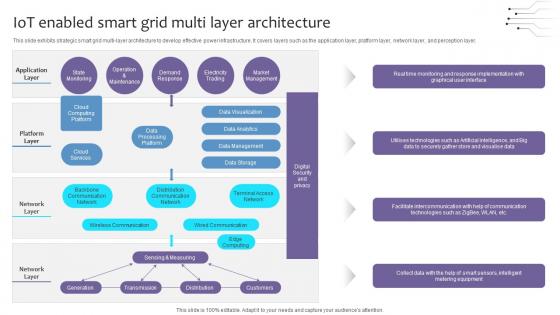
Empowering The Future IoT Enabled Smart Grid Multi Layer Architecture IoT SS V
This slide exhibits strategic smart grid multi-layer architecture to develop effective power infrastructure. It covers layers such as the application layer, platform layer, network layer, and perception layer. Boost your pitch with our creative Empowering The Future IoT Enabled Smart Grid Multi Layer Architecture IoT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide exhibits strategic smart grid multi-layer architecture to develop effective power infrastructure. It covers layers such as the application layer, platform layer, network layer, and perception layer.
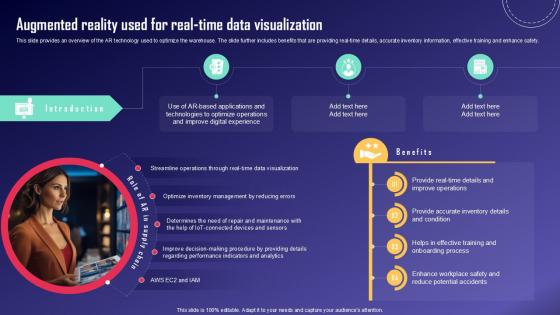
Augmented Reality Used For IoT Fleet Monitoring Ppt PowerPoint IoT SS V
This slide provides an overview of the AR technology used to optimize the warehouse. The slide further includes benefits that are providing real-time details, accurate inventory information, effective training and enhance safety. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Augmented Reality Used For IoT Fleet Monitoring Ppt PowerPoint IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides an overview of the AR technology used to optimize the warehouse. The slide further includes benefits that are providing real-time details, accurate inventory information, effective training and enhance safety.
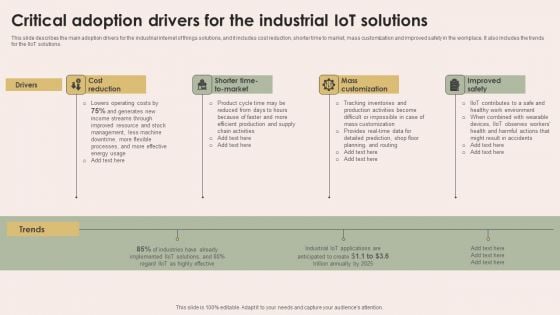
Iot Integration In Manufacturing Critical Adoption Drivers For The Industrial Iot Solutions Icons PDF
This slide describes the main adoption drivers for the industrial internet of things solutions, and it includes cost reduction, shorter time to market, mass customization and improved safety in the workplace. It also includes the trends for the IIoT solutions. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Iot Integration In Manufacturing Critical Adoption Drivers For The Industrial Iot Solutions Icons PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Iot Integration In Manufacturing Critical Adoption Drivers For The Industrial Iot Solutions Icons PDF today and make your presentation stand out from the rest
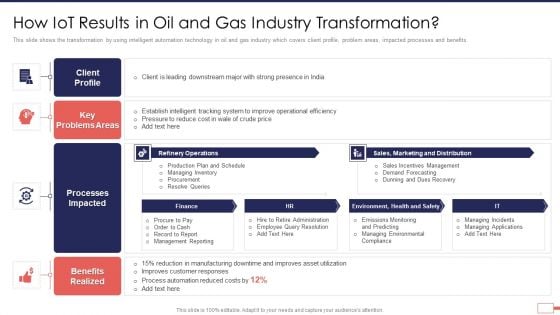
Iot Digital Twin Technology Post Covid Expenditure Management How Iot Results Ideas PDF
This slide shows the transformation by using intelligent automation technology in oil and gas industry which covers client profile, problem areas, impacted processes and benefits. Deliver and pitch your topic in the best possible manner with this iot digital twin technology post covid expenditure management how iot results ideas pdf Use them to share invaluable insights on downstream, intelligent, operational, marketing, environment, safety and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IoT Application In Global Retail IoT Solutions Offered By At And T Guidelines PDF
The following slide highlights the technology solutions provided by ATandT for enabling retailers to implement internet of things in retail sector. It shows personalized offers solution, multi access edge computing and wait time management. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created IoT Application In Global Retail IoT Solutions Offered By At And T Guidelines PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The following slide highlights the technology solutions provided by ATandT for enabling retailers to implement internet of things in retail sector. It shows personalized offers solution, multi access edge computing and wait time management.
Smart Manufacturing With Iot Critical Adoption Drivers For The Industrial Iot Solutions Elements PDF
This slide describes the main adoption drivers for the industrial internet of things solutions, and it includes cost reduction, shorter time to market, mass customization and improved safety in the workplace. It also includes the trends for the IIoT solutions. Make sure to capture your audiences attention in your business displays with our gratis customizable Smart Manufacturing With Iot Critical Adoption Drivers For The Industrial Iot Solutions Elements PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Smart Manufacturing With Iot Monitoring Safety Of Workers With Iot And Sensors Themes PDF
This slide describes monitoring workers safety through the internet of things and wearable sensors to prevent accidents or falls. The tags track workers location and wearable sensors monitor their heartbeat, temperature, galvanic skin reactions. The Smart Manufacturing With Iot Monitoring Safety Of Workers With Iot And Sensors Themes PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
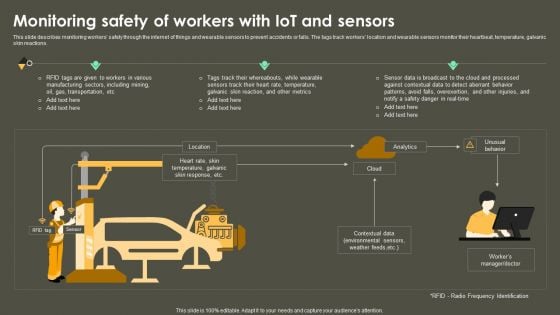
Iot Integration In Manufacturing Monitoring Safety Of Workers With Iot And Sensors Template PDF
This slide describes monitoring workers safety through the internet of things and wearable sensors to prevent accidents or falls. The tags track workers location and wearable sensors monitor their heartbeat, temperature, galvanic skin reactions. Slidegeeks is here to make your presentations a breeze with Iot Integration In Manufacturing Monitoring Safety Of Workers With Iot And Sensors Template PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
Solid Waste Handling And Vehicle Tracking System Architecture IOT Applications In Smart Waste IoT SS V
This slide showcases the architecture of the solid waste monitoring and garbage vehicle tracking system that helps in enhancing route planning. It includes four key components such as smart bins, vehicle with sensors, GSM network, and monitoring station. Want to ace your presentation in front of a live audience Our Solid Waste Handling And Vehicle Tracking System Architecture IOT Applications In Smart Waste IoT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases the architecture of the solid waste monitoring and garbage vehicle tracking system that helps in enhancing route planning. It includes four key components such as smart bins, vehicle with sensors, GSM network, and monitoring station.
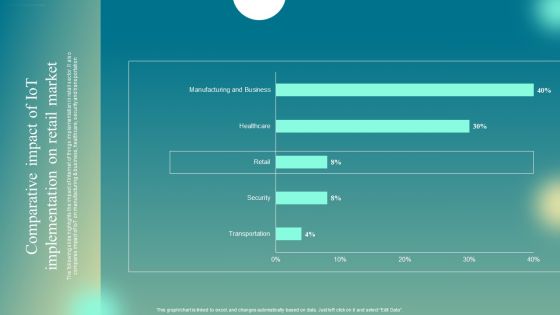
Comparative Impact Of Iot Implementation On Retail Market Clipart PDF
The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation. Welcome to our selection of the Comparative Impact Of Iot Implementation On Retail Market Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
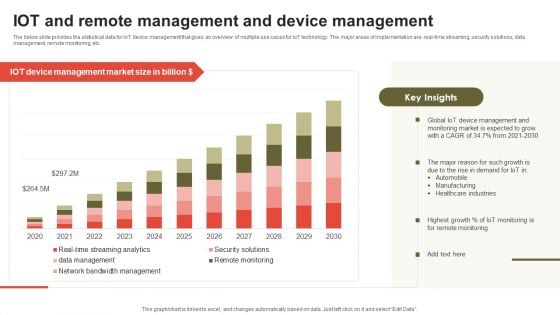
IOT And Remote Management And Device Management Brochure PDF
The below slide provides the statistical data for IoT device management that gives an overview of multiple use cases for IoT technology. The major areas of implementation are real-time streaming, security solutions, data management, remote monitoring, etc. Showcasing this set of slides titled IOT And Remote Management And Device Management Brochure PDF. The topics addressed in these templates are Automobile, Manufacturing, Healthcare Industries. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
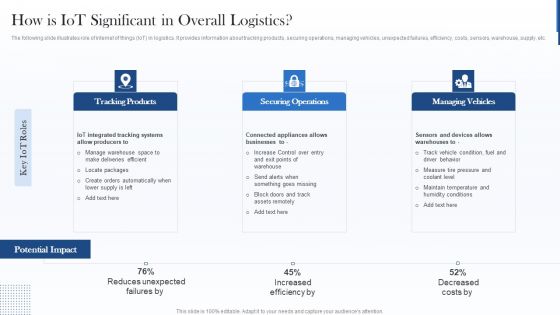
How Is Iot Significant In Overall Logistics Sample PDF
The following slide illustrates role of internet of things IoT in logistics. It provides information about tracking products, securing operations, managing vehicles, unexpected failures, efficiency, costs, sensors, warehouse, supply, etc. This is a How Is Iot Significant In Overall Logistics Sample PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Tracking Products, Securing Operations, Managing Vehicles. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
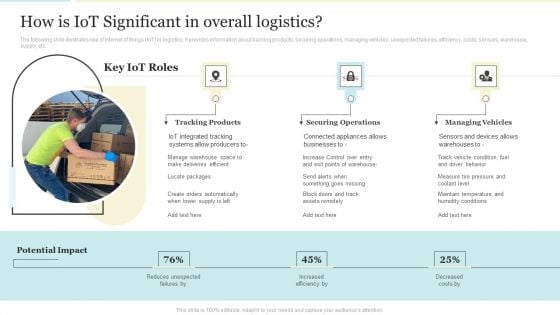
How Is Iot Significant In Overall Logistics Formats PDF
The following slide illustrates role of internet of things IoT in logistics. It provides information about tracking products, securing operations, managing vehicles, unexpected failures, efficiency, costs, sensors, warehouse, supply, etc. This is a How Is Iot Significant In Overall Logistics Formats PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Tracking Products, Securing Operations, Managing Vehicles. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Analyzing Impact Of Blockchain Iot On Major Kpis Icons PDF
This slide showcases impact analysis of blockchain internet of things IoT on key performance indicators KPIs. It provides information about efficiency, security, risk, costs, business models, revenue resources, etc. Deliver an awe inspiring pitch with this creative Analyzing Impact Of Blockchain Iot On Major Kpis Icons PDF bundle. Topics like Blockchain Integration, Business Model, Revenue Sources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
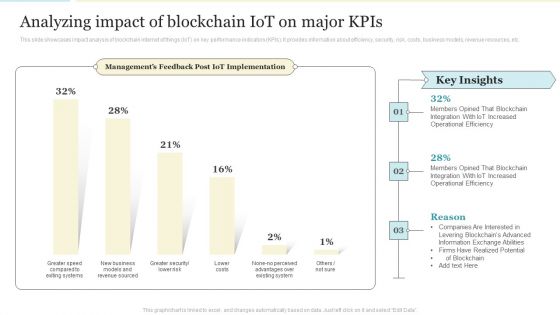
Analyzing Impact Of Blockchain Iot On Major Kpis Formats PDF
This slide showcases impact analysis of blockchain internet of things IoT on key performance indicators KPIs. It provides information about efficiency, security, risk, costs, business models, revenue resources, etc. Deliver an awe inspiring pitch with this creative Analyzing Impact Of Blockchain Iot On Major Kpis Formats PDF bundle. Topics like Operational Efficiency, Information, Existing System can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
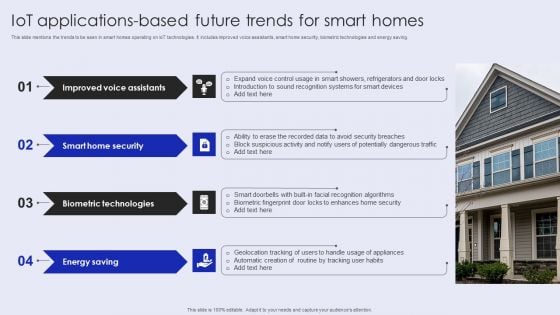
Iot Applications Based Future Trends For Smart Homes Inspiration PDF
This slide mentions the trends to be seen in smart homes operating on IoT technologies. It includes improved voice assistants, smart home security, biometric technologies and energy saving. Showcasing this set of slides titled Iot Applications Based Future Trends For Smart Homes Inspiration PDF. The topics addressed in these templates are Biometric Technologies, Smart Home Security, Improved Voice Assistants. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Implementing Essential Iot Value Drivers Ppt Inspiration Design Templates PDF
This slide provides information regarding essential implementing IoT value drivers such as simplified proximity triggers, automated product security, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Essential Iot Value Drivers Ppt Inspiration Design Templates PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Email Security Market Research Report Industry Challenges Ppt Ideas PDF
Presenting this set of slides with name email security market research report industry challenges ppt ideas pdf. This is a five stage process. The stages in this process are threat of ransomware, threat of serverless apps, iot threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
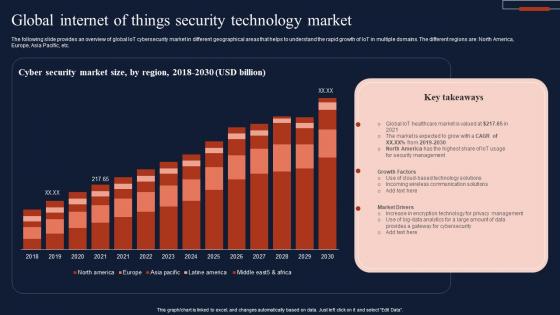
Global Internet Of Things Security Technology Market Infographics Pdf
The following slide provides an overview of global IoT cybersecurity market in different geographical areas that helps to understand the rapid growth of IoT in multiple domains. The different regions are North America, Europe, Asia Pacific, etc. Showcasing this set of slides titled Global Internet Of Things Security Technology Market Infographics Pdf The topics addressed in these templates are Cyber Security, Market Size, Technology Market All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide provides an overview of global IoT cybersecurity market in different geographical areas that helps to understand the rapid growth of IoT in multiple domains. The different regions are North America, Europe, Asia Pacific, etc.
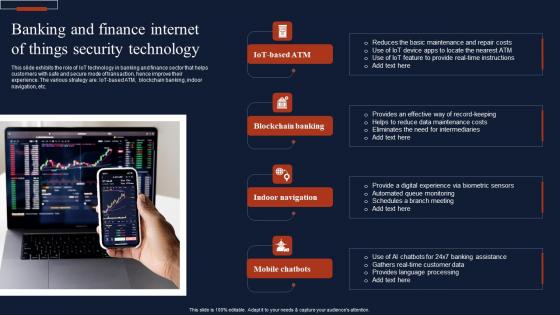
Banking And Finance Internet Of Things Security Technology Information Pdf
This slide exhibits the role of IoT technology in banking and finance sector that helps customers with safe and secure mode of transaction, hence improve their experience. The various strategy are IoT-based ATM, blockchain banking, indoor navigation, etc. Pitch your topic with ease and precision using this Banking And Finance Internet Of Things Security Technology Information Pdf This layout presents information on Blockchain Banking, Ndoor Navigation, Mobile Chatbots It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide exhibits the role of IoT technology in banking and finance sector that helps customers with safe and secure mode of transaction, hence improve their experience. The various strategy are IoT-based ATM, blockchain banking, indoor navigation, etc.
Home Security System Vector Icon Ppt PowerPoint Presentation File Influencers
Presenting this set of slides with name home security system vector icon ppt powerpoint presentation file influencers. This is a four stage process. The stages in this process are iot icon, smartphone vector, headphones. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Top Rising Virtual Security Hazards In 2023 Elements Pdf
This slide illustrates top threats which are emerging in the field of cyber security from the year 2023 onwards. The cyber security risks as covered in this template are crypto jacking, IoT attacks, smart medical devices, connected cars and third party attacks Showcasing this set of slides titled Top Rising Virtual Security Hazards In 2023 Elements Pdf. The topics addressed in these templates are Crypto Jacking, Attacks, Medical Devices. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates top threats which are emerging in the field of cyber security from the year 2023 onwards. The cyber security risks as covered in this template are crypto jacking, IoT attacks, smart medical devices, connected cars and third party attacks
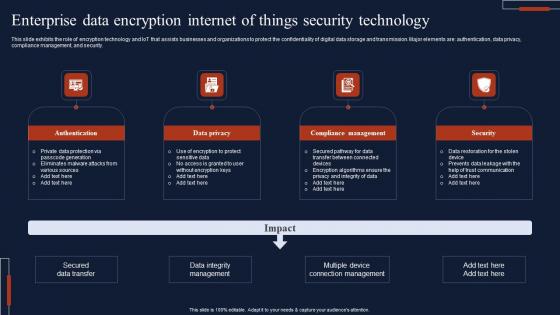
Enterprise Data Encryption Internet Of Things Security Technology Summary Pdf
This slide exhibits the role of encryption technology and IoT that assists businesses and organizations to protect the confidentiality of digital data storage and transmission. Major elements are authentication, data privacy, compliance management, and security. Showcasing this set of slides titled Enterprise Data Encryption Internet Of Things Security Technology Summary Pdf The topics addressed in these templates are Authentication, Data Privacy, Compliance Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide exhibits the role of encryption technology and IoT that assists businesses and organizations to protect the confidentiality of digital data storage and transmission. Major elements are authentication, data privacy, compliance management, and security.
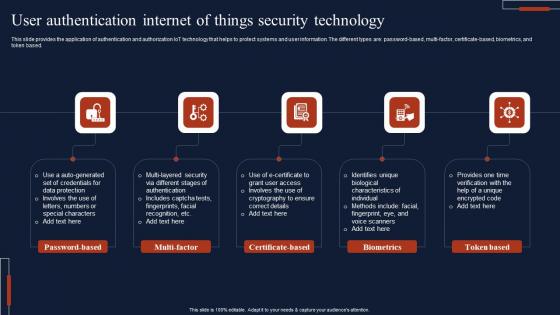
User Authentication Internet Of Things Security Technology Microsoft Pdf
This slide provides the application of authentication and authorization IoT technology that helps to protect systems and user information. The different types are password based, multi-factor, certificate-based, biometrics, and token based. Pitch your topic with ease and precision using this User Authentication Internet Of Things Security Technology Microsoft Pdf This layout presents information on Password Based, Multi Factor, Certificate Based It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide provides the application of authentication and authorization IoT technology that helps to protect systems and user information. The different types are password based, multi-factor, certificate-based, biometrics, and token based.
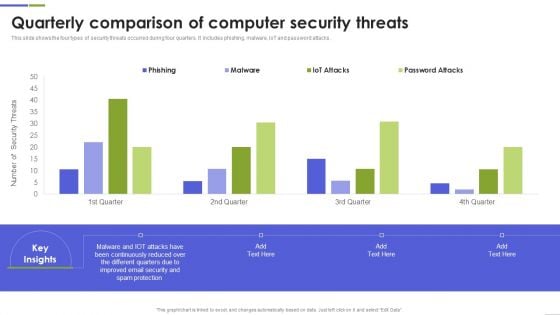
Quarterly Comparison Of Computer Security Threats Mockup PDF
This slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Computer Security Threats Mockup PDF This layout presents information on Continuously Reduced, Different Quarters, Spam Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
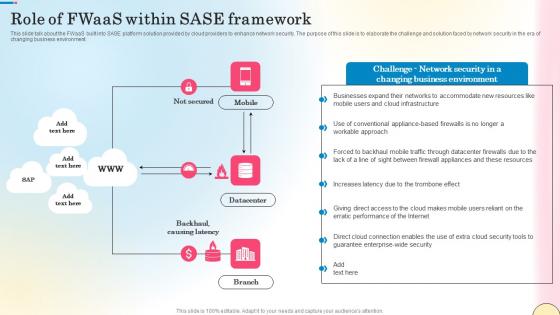
Role Of Fwaas Within Sase Framework Network Security Elements Pdf
This slide talk about the FWaaS built into SASE platform solution provided by cloud providers to enhance network security. The purpose of this slide is to elaborate the challenge and solution faced by network security in the era of changing business environment. Want to ace your presentation in front of a live audience Our Role Of Fwaas Within Sase Framework Network Security Elements Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talk about the FWaaS built into SASE platform solution provided by cloud providers to enhance network security. The purpose of this slide is to elaborate the challenge and solution faced by network security in the era of changing business environment.

Threat Security Before And After Artificial Intelligence Formats PDF
This slide describes the four main cyber risks that currently threaten our digital world, as well as the difference between traditional methods and newer, AI based methods. It includes cyber threats such as malware, DDoS, IOT and endpoints and social engineering. Showcasing this set of slides titled Threat Security Before And After Artificial Intelligence Formats PDF. The topics addressed in these templates are Malware, Distributed Denial Service, Social Engineering. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Security Internet PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with internet data security with fiber optical background Our Data Security Internet PowerPoint Templates And PowerPoint Backgrounds 0511 have just about everything. Just think of it and you'll find it in them.

Data Security Internet PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with internet data security with fiber optical Slide Create a flow with our Data Security Internet PowerPoint Themes And PowerPoint Slides 0511. Your thoughts will be coasting along.

Internet Security And Electronic Payment System Ppt Slides
This is a internet security and electronic payment system ppt slides. This is a six stage process. The stages in this process are internet security and electronic payment system, eviction of eco implementation, eco site life cycle, promotion and marketing, net readiness evaluation, eco investment and opportunity.

Laptop Internet Security PowerPoint Templates And PowerPoint Themes 0812
Laptop Internet Security PowerPoint Templates And PowerPoint Themes 0812-Microsoft Powerpoint Templates and Background with computer internet security concept Excite your audience with our Laptop Internet Security PowerPoint Templates And PowerPoint Themes 0812. You will come out on top.
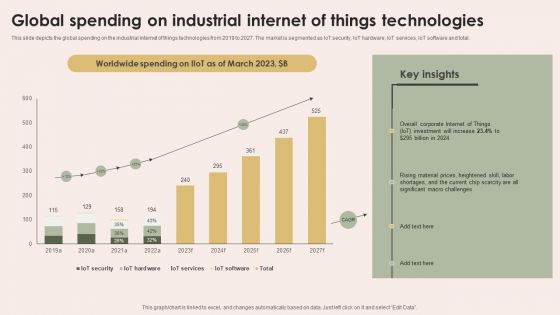
Smart Manufacturing With Iot Global Spending On Industrial Internet Of Things Technologies Designs PDF
This slide depicts the global spending on the industrial internet of things technologies from 2019 to 2027. The market is segmented as IoT security, IoT hardware, IoT services, IoT software and total. This modern and well-arranged Smart Manufacturing With Iot Global Spending On Industrial Internet Of Things Technologies Designs PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
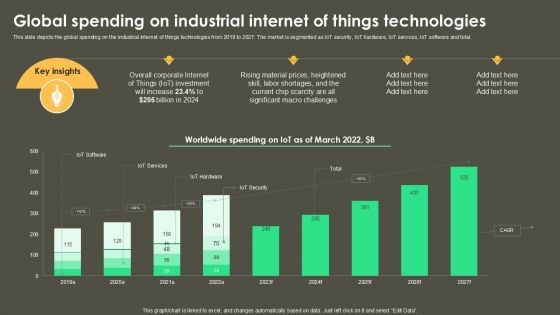
Iot Integration In Manufacturing Global Spending On Industrial Internet Of Things Technologies Topics PDF

Connectivity And Security Global PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with globe with wire around it conveying worldwide online security They consider you their father figure. Deliver on their expectations with our Connectivity And Security Global PowerPoint Backgrounds And Templates 1210.

Concept Of Internet Security PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with concept of internet security Drive to success with our Concept Of Internet Security PowerPoint Templates And PowerPoint Backgrounds 0511. You will come out on top.

Concept Of Internet Security PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with concept of internet security Our Concept Of Internet Security PowerPoint Themes And PowerPoint Slides 0511 have a chrismatic effect. The audience will attest to your brilliance.
Computer Security PowerPoint Templates And PowerPoint Themes 1012
Computer Security PowerPoint Templates And PowerPoint Themes 1012-With the move to high speed internet connection comes the greater possibility of your business being the target of an attack. One use of the term computer security refers to technology to implement a secure operating system. The Above Template will help you and your partners to understand the importance of Computer Security. Deliver amazing presentations to mesmerize your audience with our Security Template.-Computer Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Protect your computer, security, communication, computer, technology, background Bolster the excitement with our Computer Security PowerPoint Templates And PowerPoint Themes 1012. They will not let the enthusiasm fade.

Chain Security PowerPoint Templates And PowerPoint Themes 1012
Chain Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template consists of an image of many linked chains connected to one circular green chain. This image represents the concept of security or steps of business strategies. This template also emphasize strong group between family, business etc. Present your views using our innovative slides and be assured of leaving a lasting impression. -Chain Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Chains of design, communication, security, business, teamwork, industrial Set a good example with our Chain Security PowerPoint Templates And PowerPoint Themes 1012. Be the benchmark for others to follow.

Password Protection Internet Security PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with Cybernetic hand inserting user name and password Create the right environment for prosperity. Fashion the right conditions with our Password Protection Internet Security PowerPoint Backgrounds And Templates 1210.

Browsing Security Internet PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with 3d illustration of a floating/transparent internet browser with a lock padlock intersecting it Examine every deatail with our Browsing Security Internet PowerPoint Backgrounds And Templates 1210. Put each element to the test.

Laptop Under Protection Security PowerPoint Templates And PowerPoint Themes 1112
We present our Laptop Under Protection Security PowerPoint Templates And PowerPoint Themes 1112.Use our Technology PowerPoint Templates because, Activities which in themselves have many inherent business oppurtunities. Use our Computer PowerPoint Templates because,And watch them strenthen your companys sinews. Use our Business PowerPoint Templates because, Emphasise on any critical or key factors within them. Use our Internet PowerPoint Templates because,Now use this slide to bullet point your views. Use our Security PowerPoint Templates because,Demonstrate how you think out of the box.Use these PowerPoint slides for presentations relating to Computer under protection of umbrella, internet, security, business, technology, computer. The prominent colors used in the PowerPoint template are Green, Black, Blue Cross the chasm with our Laptop Under Protection Security PowerPoint Templates And PowerPoint Themes 1112. You will come out on top.


 Continue with Email
Continue with Email

 Home
Home


































