It Security Roadmap

Video Meeting Internet Security Threat Analysis Measures Brochure PDF
Following slide showcase video meeting security breach control tasks and actions. It includes multiple actions such as- run the recent version of application, utilizing corporate mails to send meeting links and so on. Persuade your audience using this video meeting internet security threat analysis measures brochure pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including video meeting internet security threat analysis measures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
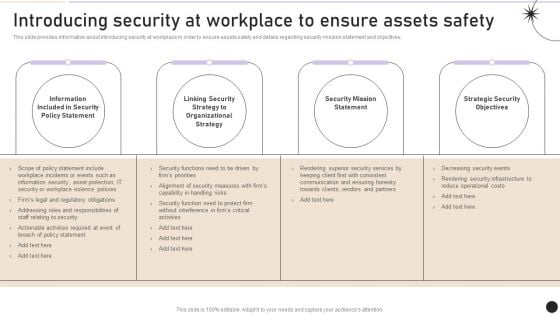
Introducing Security At Workplace To Ensure Assets Safety Graphics PDF
This slide provides information about introducing security at workplace in order to ensure assets safety and details regarding security mission statement and objectives. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Introducing Security At Workplace To Ensure Assets Safety Graphics PDF can be your best option for delivering a presentation. Represent everything in detail using Introducing Security At Workplace To Ensure Assets Safety Graphics PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
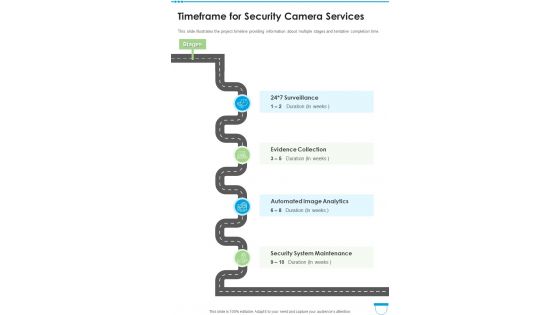
Timeframe For Security Camera Services One Pager Sample Example Document
This slide illustrates the project timeline providing information about multiple stages and tentative completion time. Presenting you an exemplary Timeframe For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Timeframe For Security Camera Services One Pager Sample Example Document brilliant piece now.
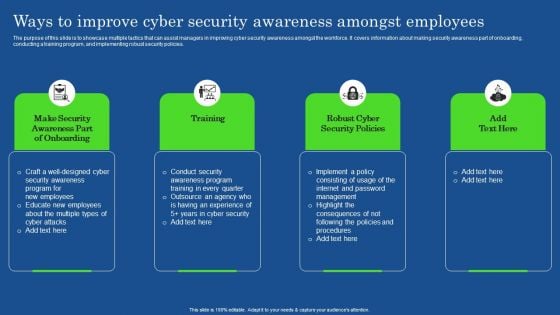
Ways To Improve Cyber Security Awareness Amongst Employees Elements PDF
The purpose of this slide is to showcase multiple tactics that can assist managers in improving cyber security awareness amongst the workforce. It covers information about making security awareness part of onboarding, conducting a training program, and implementing robust security policies. The Ways To Improve Cyber Security Awareness Amongst Employees Elements PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
IT Divisional Strategy To Improve Cyber Security Measures Icons PDF
This slide signifies information technology department to enhance cyber security measures. It also includes stages like identify, plan, execute and control. Presenting IT Divisional Strategy To Improve Cyber Security Measures Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Identify, Plan, Execute, Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Trends Ppt PowerPoint Presentation Show Structure Cpb
Presenting this set of slides with name cyber security trends ppt powerpoint presentation show structure cpb. This is an editable Powerpoint five stages graphic that deals with topics like cyber security trends to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
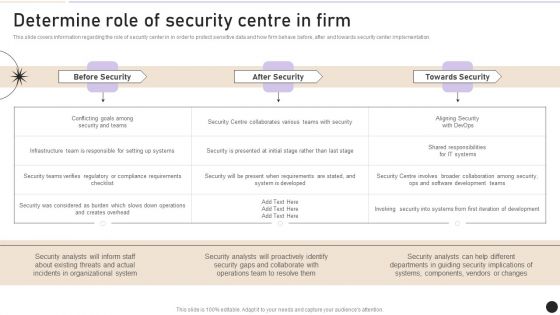
Determine Role Of Security Centre In Firm Designs PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security center implementation. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Determine Role Of Security Centre In Firm Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Determine Role Of Security Centre In Firm Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
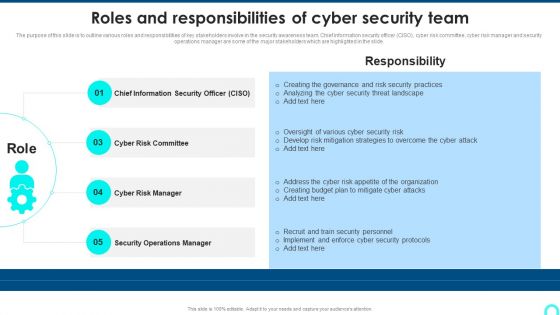
Roles And Responsibilities Of Cyber Security Team Designs PDF
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide.This is a Roles And Responsibilities Of Cyber Security Team Designs PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Chief Information, Operations Manager, Risk Manager . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
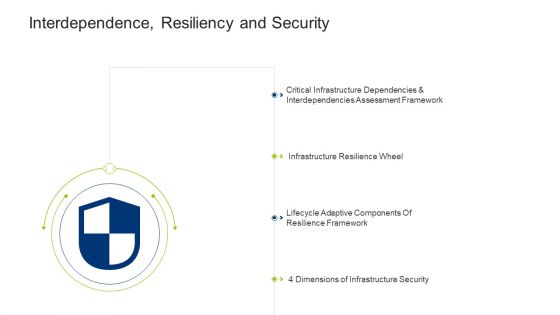
Infrastructure Building Administration Interdependence Resiliency And Security Microsoft PDF
This is a infrastructure building administration interdependence resiliency and security microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure resilience wheel, lifecycle adaptive components of resilience framework, 4 dimensions of infrastructure security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
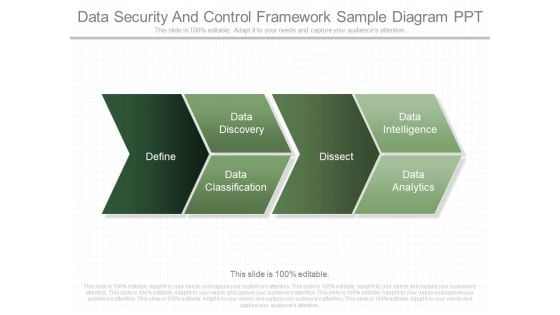
Data Security And Control Framework Sample Diagram Ppt
This is a data security and control framework sample diagram ppt. This is a four stage process. The stages in this process are define, data classification, data discovery, dissect, data intelligence, data analytics.
Key Security Considerations For 5G For Threat Handling Icons PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling Icons PDF. Use them to share invaluable insights on Denial Of Service, Information Interception, Application Plane Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
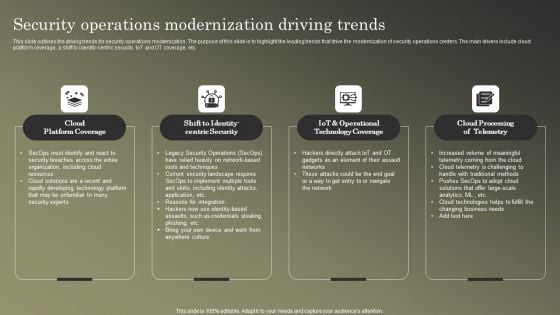
Cybersecurity Operations Cybersecops Security Operations Modernization Driving Slides PDF
This slide outlines the driving trends for security operations modernization. The purpose of this slide is to highlight the leading trends that drive the modernization of security operations centers. The main drivers include cloud platform coverage, a shift to identify-centric security, IoT and OT coverage, etc. Present like a pro with Cybersecurity Operations Cybersecops Security Operations Modernization Driving Slides PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Ensure Security And Access Controls Ppt PowerPoint Presentation Slides Information
This is a ensure security and access controls ppt powerpoint presentation slides information. This is a two stage process. The stages in this process are business, management, planning, strategy, marketing.
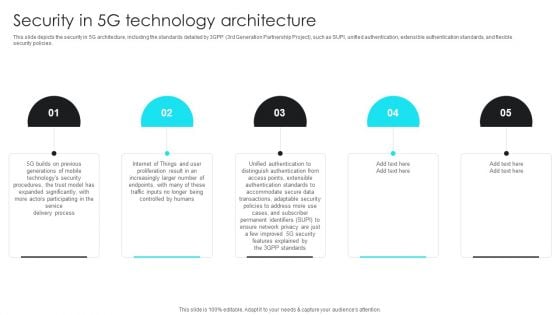
5G Network Operations Security In 5G Technology Architecture Template PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download 5G Network Operations Security In 5G Technology Architecture Template PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the 5G Network Operations Security In 5G Technology Architecture Template PDF.
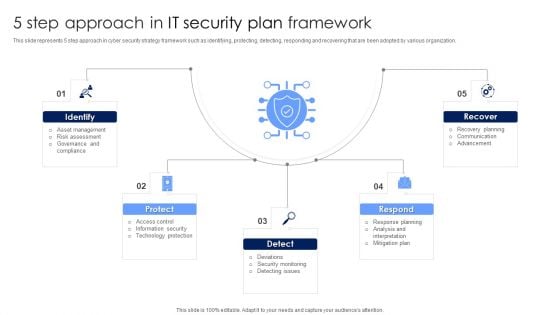
5 Step Approach In IT Security Plan Framework Designs PDF
This slide represents 5 step approach in cyber security strategy framework such as identifying, protecting, detecting, responding and recovering that are been adopted by various organization. Presenting 5 Step Approach In IT Security Plan Framework Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Protect, Detect, Respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
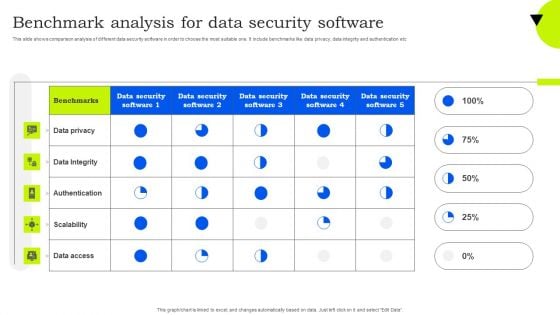
Benchmark Analysis For Data Security Software Mockup PDF
This slide shows comparison analysis of different data security software in order to choose the most suitable one. It include benchmarks like data privacy, data integrity and authentication etc. Showcasing this set of slides titled Benchmark Analysis For Data Security Software Mockup PDF. The topics addressed in these templates are Data Privacy, Data Integrity, Authentication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
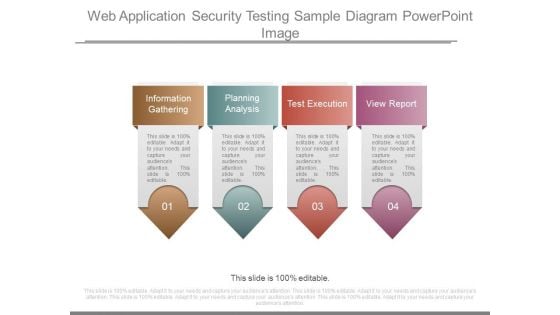
Web Application Security Testing Sample Diagram Powerpoint Image
This is a web application security testing sample diagram powerpoint image. This is a four stage process. The stages in this process are information gathering, planning analysis, test execution, view report.
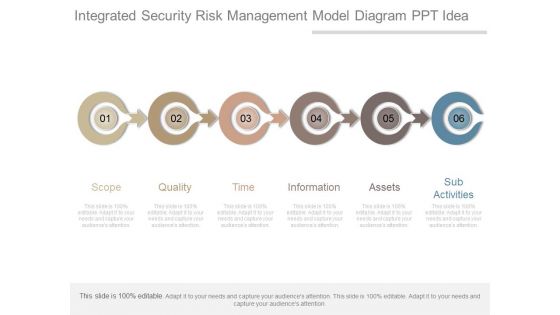
Integrated Security Risk Management Model Diagram Ppt Idea
This is a integrated security risk management model diagram ppt idea. This is a six stage process. The stages in this process are scope, quality, time, information, assets, sub activities.
Threats Affecting Infra Cyber Security In Market Icons PDF
The following slide showcases threats in infrastructure security which can cause electrical blackouts, breaches of national secrets, etc. It presents information related to phishing, ransomware, botnets, etc. Presenting Threats Affecting Infra Cyber Security In Market Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Phishing, Ransomware, Botnets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
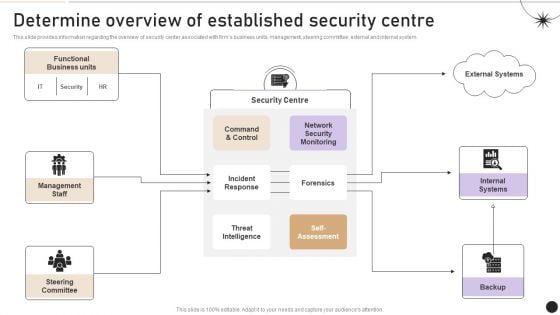
Determine Overview Of Established Security Centre Themes PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. There are so many reasons you need a Determine Overview Of Established Security Centre Themes PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
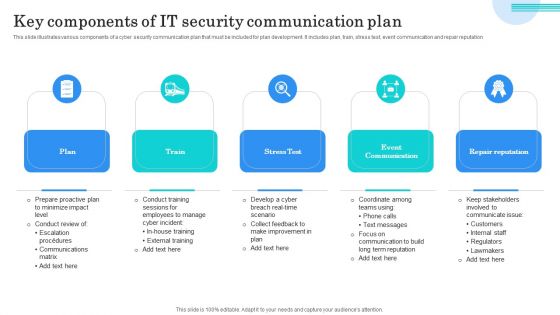
Key Components Of IT Security Communication Plan Mockup PDF
This slide illustrates various components of a cyber security communication plan that must be included for plan development. It includes plan, train, stress test, event communication and repair reputation. Presenting Key Components Of IT Security Communication Plan Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Plan, Train, Stress Test. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
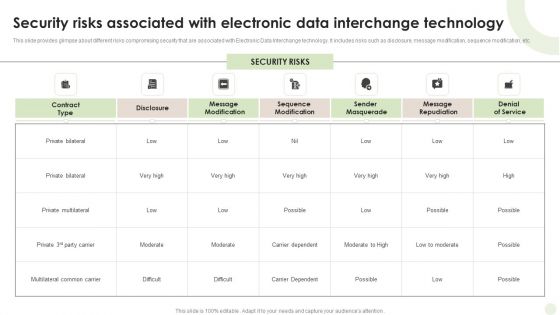
Security Risks Associated With Electronic Data Interchange Technology Guidelines PDF
This slide provides glimpse about different risks compromising security that are associated with Electronic Data Interchange technology. It includes risks such as disclosure, message modification, sequence modification, etc.Showcasing this set of slides titled Security Risks Associated With Electronic Data Interchange Technology Guidelines PDF. The topics addressed in these templates are Private Multilateral, Multilateral Common, Carrier Dependent. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Network Security Training Programs Timeline Download PDF
The slide showcases training programs to improve individuals level of awareness about security measures designed to protect cloud based infrastructure and data. The elements are SANS, infosec, ISC, edX with their completion timeline and pricing package . Showcasing this set of slides titled Cloud Network Security Training Programs Timeline Download PDF. The topics addressed in these templates are Training Programs, Models Controls, Offense Defense Operations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Differentiating 2 Items Illustration For Free Internet Security Clipart PDF
Presenting differentiating 2 items illustration for free internet security clipart pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like differentiating 2 items illustration for free internet security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
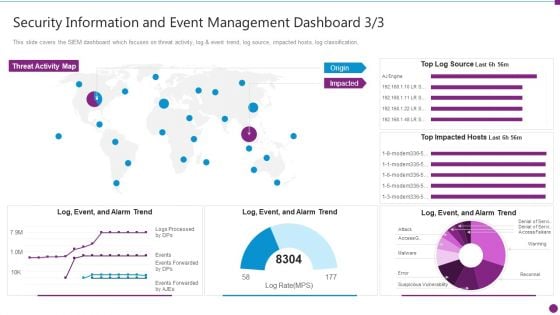
Security Information And Event Management Dashboard Source Ideas PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification. Deliver an awe inspiring pitch with this creative security information and event management dashboard source ideas pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
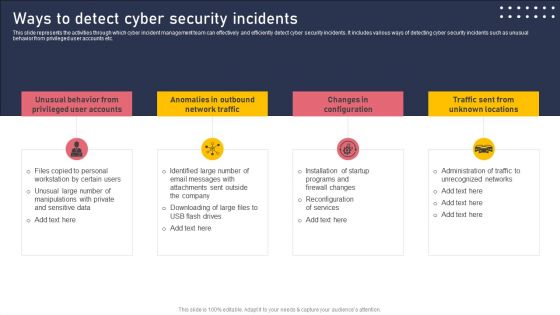
Ways To Detect Cyber Security Incidents Template PDF
This slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Ways To Detect Cyber Security Incidents Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Ways To Detect Cyber Security Incidents Template PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

International Security Market Highlights Ppt PowerPoint Presentation Pictures Graphics Example
This is a international security market highlights ppt powerpoint presentation pictures graphics example. This is a three stage process. The stages in this process are management, marketing, business, strategy, process.
Ensure Security And Access Controls Ppt PowerPoint Presentation Pictures Examples
This is a ensure security and access controls ppt powerpoint presentation pictures examples. This is a two stage process. The stages in this process are business, planning, strategy, marketing, management.
Cyber Security Process Compliance Ppt PowerPoint Presentation Ideas Inspiration Cpb
Presenting this set of slides with name cyber security process compliance ppt powerpoint presentation ideas inspiration cpb. This is an editable Powerpoint four stages graphic that deals with topics like cyber security process compliance to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
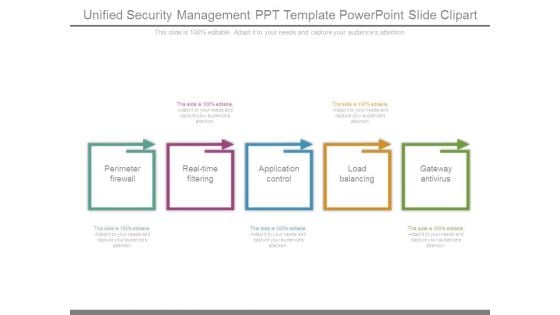
Unified Security Management Ppt Template Powerpoint Slide Clipart
This is a unified security management ppt template powerpoint slide clipart. This is a five stage process. The stages in this process are perimeter firewall, real time filtering, application control, load balancing, gateway antivirus.
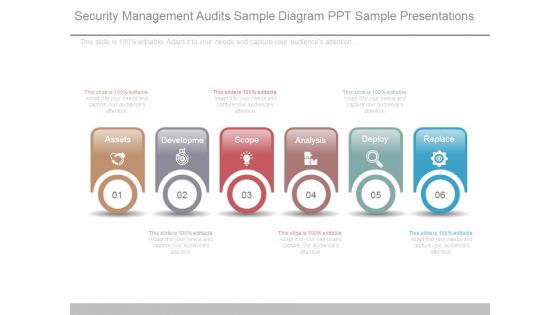
Security Management Audits Sample Diagram Ppt Sample Presentations
This is a security management audits sample diagram ppt sample presentations. This is a six stage process. The stages in this process are assets, development, scope, analysis, deploy, replace.
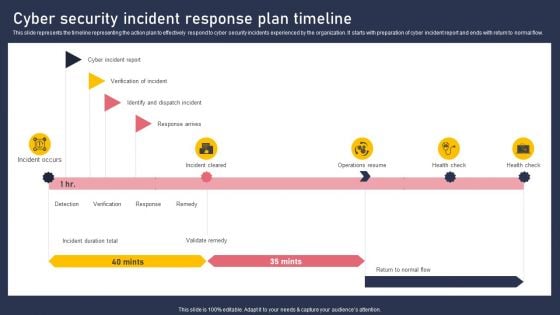
Cyber Security Incident Response Plan Timeline Inspiration PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Cyber Security Incident Response Plan Timeline Inspiration PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Cyber Security Incident Response Plan Timeline Inspiration PDF.
Web Services Security Ppt PowerPoint Presentation Styles Gallery Cpb
Presenting this set of slides with name web services security ppt powerpoint presentation styles gallery cpb. This is an editable Powerpoint five stages graphic that deals with topics like web services security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Vendor Application Security Testing Ppt Example Ppt Presentation

Security Incident Response Plan Template Ppt Design Templates
This is a security incident response plan template ppt design templates. This is a three stage process. The stages in this process are prepare, detection and analysis, post incident activity.
Ensure Security And Access Controls Ppt PowerPoint Presentation Inspiration Portfolio
This is a ensure security and access controls ppt powerpoint presentation inspiration portfolio. This is a two stage process. The stages in this process are marketing, management, strategy, business, planning.
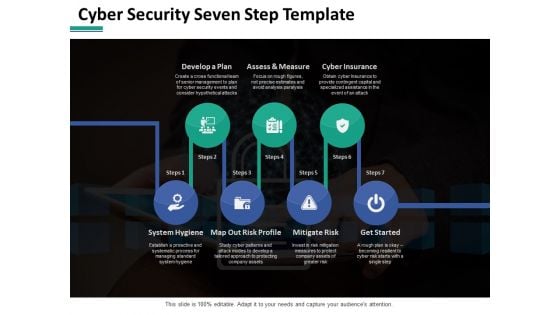
Cyber Security Seven Step Ppt PowerPoint Presentation Infographic Template Maker
This is a cyber security seven step ppt powerpoint presentation infographic template maker. This is a seven stage process. The stages in this process are business, management, planning, strategy, marketing.

Employee Benefits Social Security Ppt PowerPoint Presentation Outline Brochure
This is a employee benefits social security ppt powerpoint presentation outline brochure. This is a eight stage process. The stages in this process are business, management, perks and bonuses, achievement award, health insurance.
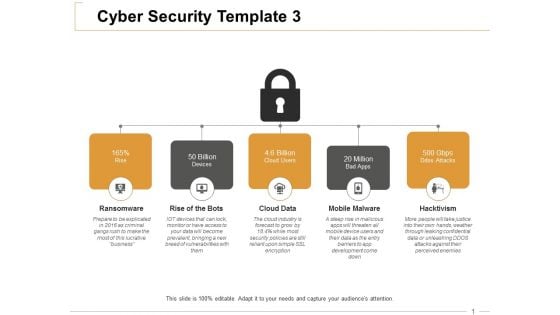
Cyber Security Ransomware Ppt PowerPoint Presentation Summary Graphics Design
This is a cyber security ransomware ppt powerpoint presentation summary graphics design. This is a five stage process. The stages in this process are business, management, planning, strategy, marketing.
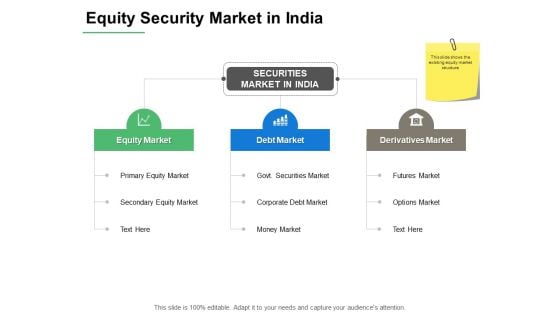
Equity Security Market In India Ppt PowerPoint Presentation Pictures Infographics
This is a equity security market in india ppt powerpoint presentation pictures infographics. This is a three stage process. The stages in this process are marketing, business, management, planning, strategy.
Overview Security Management Ppt PowerPoint Presentation Model Structure Cpb
Presenting this set of slides with name overview security management ppt powerpoint presentation model structure cpb. This is an editable Powerpoint three stages graphic that deals with topics like overview security management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Computer Security Plan Ppt PowerPoint Presentation Visual Aids Show Cpb
Presenting this set of slides with name computer security plan ppt powerpoint presentation visual aids show cpb. This is an editable Powerpoint four stages graphic that deals with topics like computer security plan to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
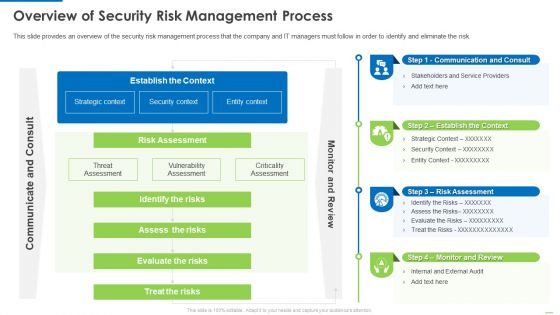
Overview Of Security Risk Management Process Demonstration PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver and pitch your topic in the best possible manner with this Overview of security risk management process demonstration pdf. Use them to share invaluable insights on identify the risks, assess the risks, evaluate the risks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
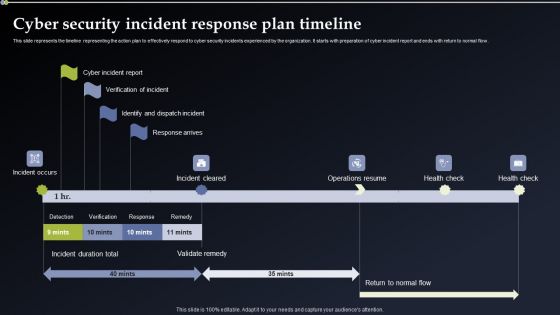
Cyber Security Incident Response Plan Timeline Mockup PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Security Incident Response Plan Timeline Mockup PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Information Technology Security Data Breach And Trend Analysis Professional PDF
The following slide reflects some trends in information technology security to assess financial loss occurred to companies due to data breach. It includes average cost and average number of days to determine and report data breach, number of new malware detected per day etc. Presenting Information Technology Security Data Breach And Trend Analysis Professional PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Data Breach, Average Cost, Determine. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
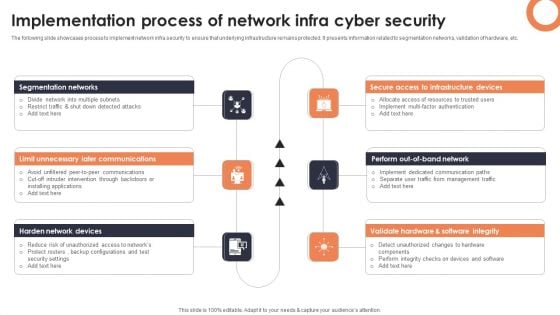
Implementation Process Of Network Infra Cyber Security Introduction PDF
The following slide showcases process to implement network infra security to ensure that underlying infrastructure remains protected. It presents information related to segmentation networks, validation of hardware, etc. Presenting Implementation Process Of Network Infra Cyber Security Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Segmentation Networks, Secure Access Infrastructure, Validate Hardware. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
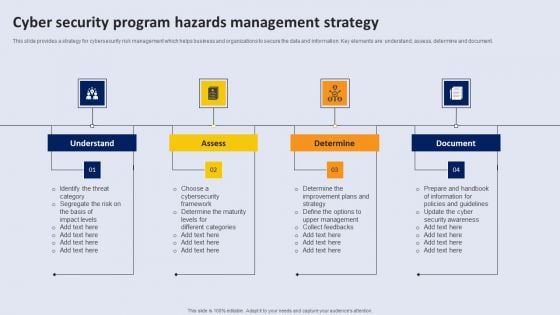
Cyber Security Program Hazards Management Strategy Topics PDF
This slide provides a strategy for cyber security risk management which helps business and organizations to secure the data and information. Key elements are understand, assess, determine and document.Persuade your audience using this Cyber Security Program Hazards Management Strategy Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Understand, Determine. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
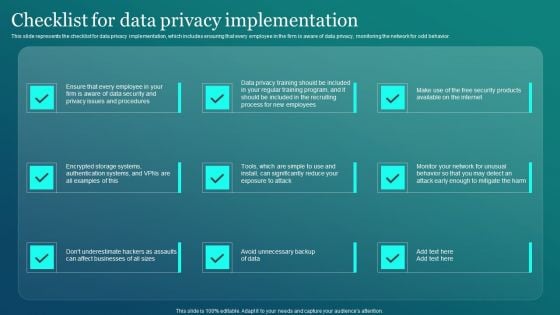
Information Security Checklist For Data Privacy Implementation Elements PDF
This slide represents the checklist for data privacy implementation, which includes ensuring that every employee in the firm is aware of data privacy, monitoring the network for odd behavior. Presenting this PowerPoint presentation, titled Information Security Checklist For Data Privacy Implementation Elements PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Information Security Checklist For Data Privacy Implementation Elements PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Information Security Checklist For Data Privacy Implementation Elements PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Data Protection And Information Security Policy And Procedure Guidelines PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Protection And Information Security Policy And Procedure Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Protection And Information Security Policy And Procedure Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Digital Banking Security Management Technology Trends Introduction PDF
The following slide provides the integration of security technology with banking which helps to provide improved and enhanced customer experience. Key components are login protection, artificial intelligence and cloud computing. Presenting Digital Banking Security Management Technology Trends Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Login Protection, Ai, Cloud Computing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
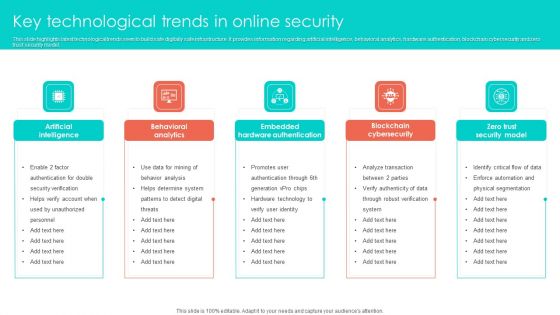
Key Technological Trends In Online Security Clipart PDF
This slide highlights latest technological trends seen to build safe digitally safe infrastructure. It provides information regarding artificial intelligence, behavioral analytics, hardware authentication, blockchain cybersecurity and zero trust security model. Persuade your audience using this Key Technological Trends In Online Security Clipart PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Behavioral Analytics, Artificial Intelligence, Embedded Hardware Authentication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Risk Management Plan Implementation Stages Summary PDF
This slide explains various steps for implementation of cybersecurity risk management plan in the organization to ensure time and budget compliance. It includes elements such as current state analysis, assessment, target state, etc. Presenting IT Security Risk Management Plan Implementation Stages Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State Analysis, Assessment, Target State, Roadmap. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
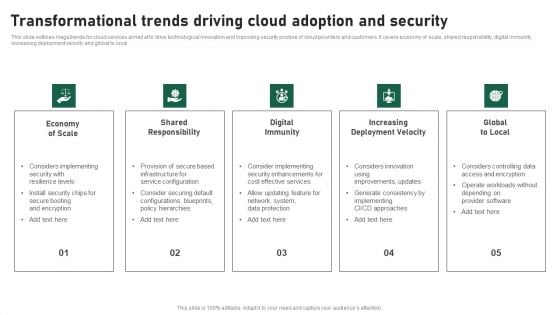
Transformational Trends Driving Cloud Adoption And Security Clipart PDF
This slide outlines mega trends for cloud services aimed at to drive technological innovation and improving security posture of cloud providers and customers. It covers economy of scale, shared responsibility, digital immunity, increasing deployment velocity and global to local. Presenting Transformational Trends Driving Cloud Adoption And Security Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Economy Of Scale, Shared Responsibility, Digital Immunity, Increasing Deployment Velocity, Global To Local. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Security Event And Incident Flow Diagram Icons PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Event And Incident Flow Diagram Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
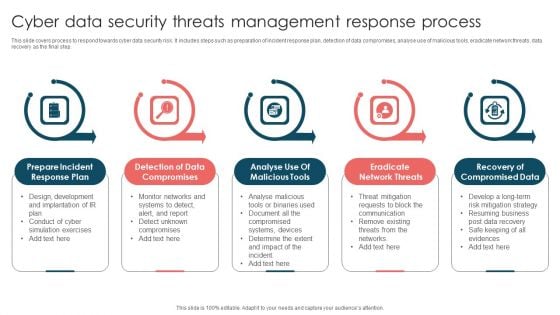
Cyber Data Security Threats Management Response Process Infographics PDF
This slide covers process to respond towards cyber data security risk. It includes steps such as preparation of incident response plan, detection of data compromises, analyse use of malicious tools, eradicate network threats, data recovery as the final step. Presenting Cyber Data Security Threats Management Response Process Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Prepare Incident, Response Plan, Detection Data Compromises, Eradicate Network Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
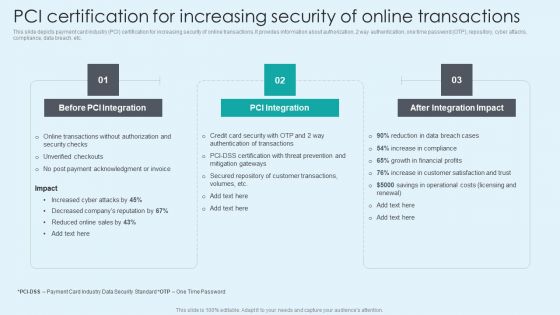
PCI Certification For Increasing Security Of Online Transactions Background PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Explore a selection of the finest PCI Certification For Increasing Security Of Online Transactions Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our PCI Certification For Increasing Security Of Online Transactions Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
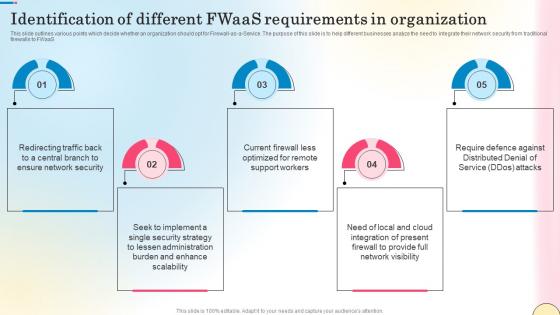
Identification Of Different Fwaas Requirements In Network Security Template Pdf
This slide outlines various points which decide whether an organization should opt for Firewall-as-a-Service. The purpose of this slide is to help different businesses analyze the need to integrate their network security from traditional firewalls to FWaaS. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Identification Of Different Fwaas Requirements In Network Security Template Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines various points which decide whether an organization should opt for Firewall-as-a-Service. The purpose of this slide is to help different businesses analyze the need to integrate their network security from traditional firewalls to FWaaS.
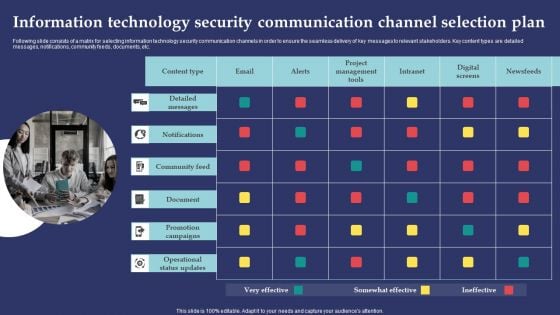
Information Technology Security Communication Channel Selection Plan Template PDF
Following slide consists of a matrix for selecting information technology security communication channels in order to ensure the seamless delivery of key messages to relevant stakeholders. Key content types are detailed messages, notifications, community feeds, documents, etc. Presenting Information Technology Security Communication Channel Selection Plan Template PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Detailed Message, Notifications, Community Feed. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Network Security Threats And Solutions Infographics PDF
The slide showcases threats occurred due to data flowing between cloud service providers and organizations with their solutions. It includes lack of cloud security architecture and tactics, account hijacking , weak control plane , inadequate of identity, credentials, etc. Presenting Cloud Network Security Threats And Solutions Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats, Description, Solutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
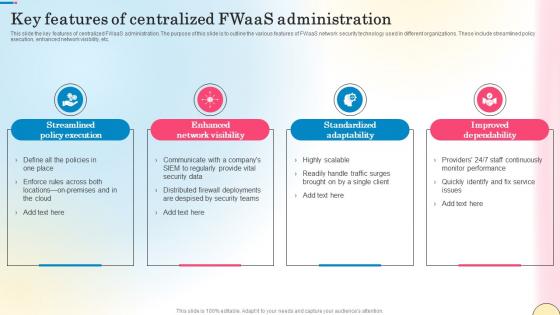
Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf
This slide the key features of centralized FWaaS administration. The purpose of this slide is to outline the various features of FWaaS network security technology used in different organizations. These include streamlined policy execution, enhanced network visibility, etc. Slidegeeks has constructed Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide the key features of centralized FWaaS administration. The purpose of this slide is to outline the various features of FWaaS network security technology used in different organizations. These include streamlined policy execution, enhanced network visibility, etc.


 Continue with Email
Continue with Email

 Home
Home


































