It Security Roadmap
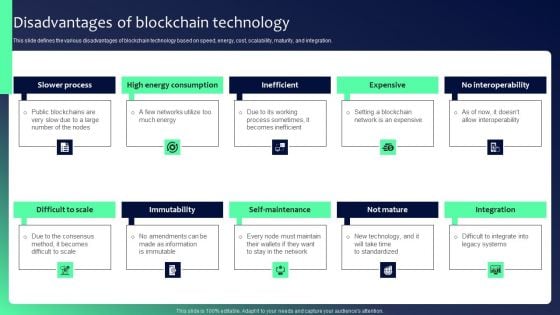
Blockchain Security Solutions Deployment Disadvantages Of Blockchain Technology Diagrams PDF
This slide defines the various disadvantages of blockchain technology based on speed, energy, cost, scalability, maturity, and integration. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Blockchain Security Solutions Deployment Disadvantages Of Blockchain Technology Diagrams PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Blockchain Security Solutions Deployment Disadvantages Of Blockchain Technology Diagrams PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
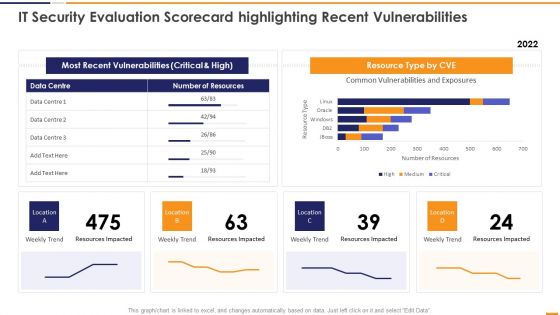
IT Security Evaluation Scorecard Highlighting Recent Vulnerabilities Introduction PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard Highlighting Recent Vulnerabilities Introduction PDF bundle. Topics like Most Recent Vulnerabilities, Resource Type CVE, Weekly Trend Location can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
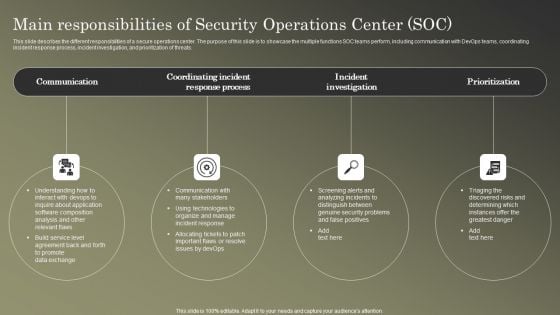
Cybersecurity Operations Cybersecops Main Responsibilities Of Security Operations Template PDF
This slide describes the different responsibilities of a secure operations center. The purpose of this slide is to showcase the multiple functions SOC teams perform, including communication with DevOps teams, coordinating incident response process, incident investigation, and prioritization of threats. There are so many reasons you need a Cybersecurity Operations Cybersecops Main Responsibilities Of Security Operations Template PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
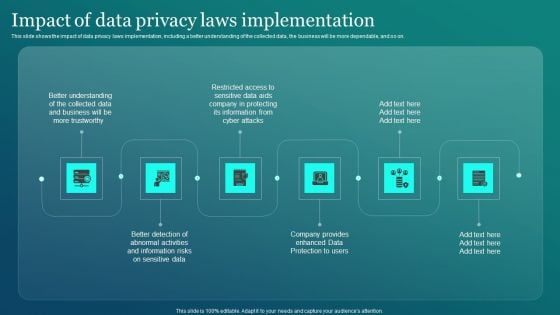
Information Security Impact Of Data Privacy Laws Implementation Slides PDF
This slide shows the impact of data privacy laws implementation, including a better understanding of the collected data, the business will be more dependable, and so on. Take your projects to the next level with our ultimate collection of Information Security Impact Of Data Privacy Laws Implementation Slides PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
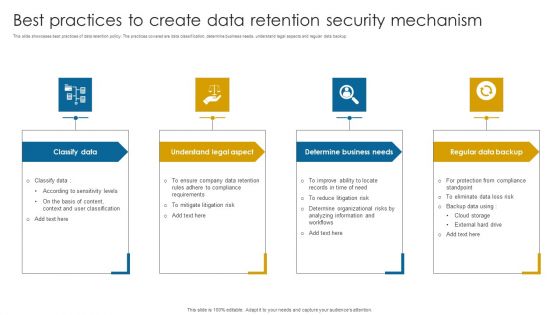
Best Practices To Create Data Retention Security Mechanism Topics PDF
This slide showcases best practices of data retention policy. The practices covered are data classification, determine business needs, understand legal aspects and regular data backup.Presenting Best Practices To Create Data Retention Security Mechanism Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Understand Legal Aspect, Determine Business Needs, Regular Data Backup . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Hacker Hacking Of Email Domain Inspiration PDF
This slide represents the hacking of the company email domain by hackers by sending spam emails to employees and stealing money from clients and customers.This is a IT Security Hacker Hacking Of Email Domain Inspiration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like After Entering, Passwords And Other, Technological Upgrades. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
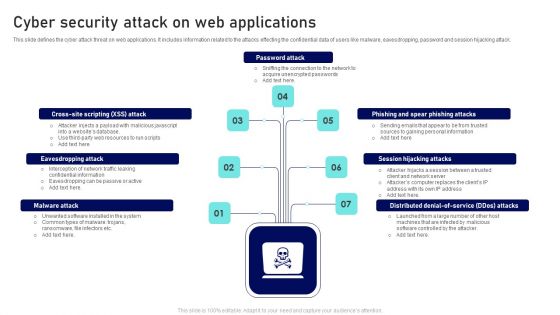
Cyber Security Attack On Web Applications Ppt Outline Files PDF
This slide defines the cyber attack threat on web applications. It includes information related to the attacks effecting the confidential data of users like malware, eavesdropping, password and session hijacking attack. Presenting Cyber Security Attack On Web Applications Ppt Outline Files PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Password Attack, Session Hijacking Attacks, Eavesdropping Attack. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
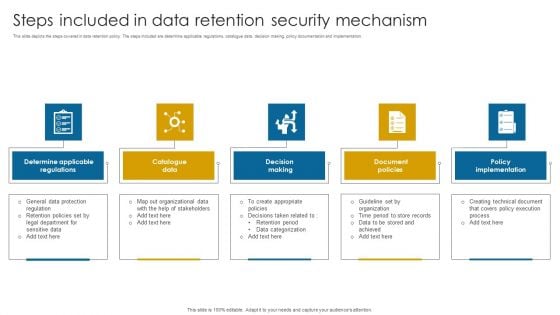
Steps Included In Data Retention Security Mechanism Introduction PDF
This slide depicts the steps covered in data retention policy. The steps included are determine applicable regulations, catalogue data, decision making, policy documentation and implementation.Persuade your audience using this Steps Included In Data Retention Security Mechanism Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Catalogue Data, Decision Making, Document Policies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Blockchain Security Technology For Healthcare Industry Icons PDF
This slide highlights the importance of blockchain technology in healthcare industry which is used to preserve data and promote workflow authenticity. Key components are supply chain, electronic health records, safety access and staff verification.Persuade your audience using this Blockchain Security Technology For Healthcare Industry Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authenticity Medicine, Electronic Health, Ensures Only Trusted. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
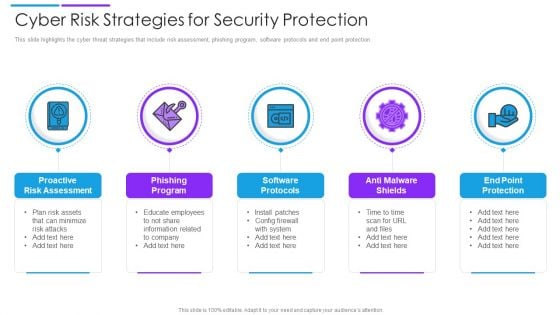
Cyber Risk Strategies For Security Protection Mockup PDF
This slide highlights the cyber threat strategies that include risk assessment, phishing program, software protocols and end point protection. Persuade your audience using this cyber risk strategies for security protection mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including proactive risk assessment, phishing program, software protocols. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
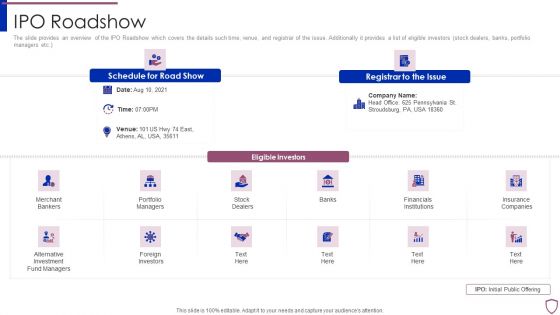
Financing Catalogue For Security Underwriting Agreement IPO Roadshow Topics PDF
The slide provides an overview of the IPO Roadshow which covers the details such time, venue, and registrar of the issue. Additionally it provides a list of eligible investors stock dealers, banks, portfolio managers etc. This is a financing catalogue for security underwriting agreement ipo roadshow topics pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like merchant bankers, portfolio managers, financials institutions, foreign investors, insurance companies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Software Company Investor Funding Elevator Pitch Deck Complete Deck
In this Security Software Company Investor Funding Elevator Pitch Deck Complete Deck, we detail the way one can plan on timelines innovation and making the best of resources. We also present to you the importance of documenting every major strategic move. In this thirty eight slide presentation template, we also include umbrella concepts to make sure your authority as a handsome business person is enhanced. As always, the editable and customizable benefit is also provided making you emerge as the business Guru. Download now to establish your superiority in both running a business, and being confident enough to present about it.
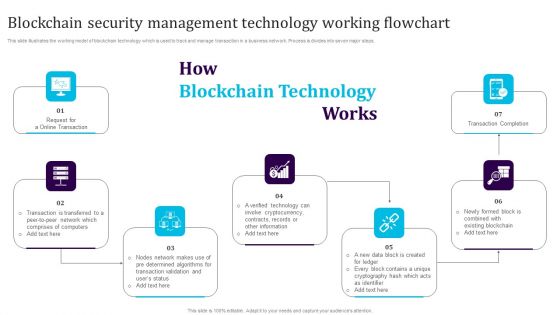
Blockchain Security Management Technology Working Flowchart Download PDF
This slide illustrates the working model of blockchain technology which is used to track and manage transaction in a business network. Process is divides into seven major steps. Persuade your audience using this Blockchain Security Management Technology Working Flowchart Download PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Transaction Completion, Cryptocurrency, Blockchain. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
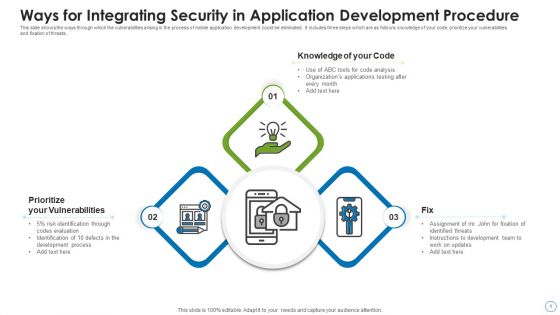
Ways For Integrating Security In Application Development Procedure Structure PDF
This slide shows the ways through which the vulnerabilities arising in the process of mobile application development could be eliminated. It includes three steps which are as follows knowledge of your code, prioritize your vulnerabilities and fixation of threats. Persuade your audience using this ways for integrating security in application development procedure structure pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including prioritize your vulnerabilities, knowledge of your code, fix. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Cyber Security Risk Assessment Process Inspiration PDF
The slide shows cyber threat detection and protection measures in order to eliminate the potential risks to the business. The steps include identifying, detecting, responding, protecting, and recovering. Persuade your audience using this Business Cyber Security Risk Assessment Process Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Detect, Respond, Protect, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
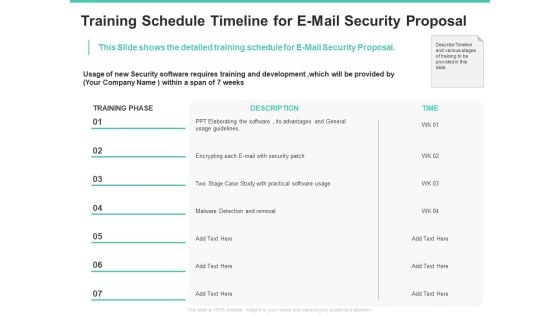
Email Security Encryption And Data Loss Prevention Training Schedule Timeline For E Mail Security Proposal Diagrams PDF
This Slide shows the detailed training schedule for E-Mail Security Proposal. Deliver an awe-inspiring pitch with this creative email security encryption and data loss prevention training schedule timeline for e mail security proposal diagrams pdf bundle. Topics like case study, security, development, timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps In Detail Remote Summary PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks security management plan steps in detail remote summary pdf bundle. Topics like requirement for additional, remote access control, control security status can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Essential Elements Of Security Monitoring Plan Sample PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach essential elements of security monitoring plan sample pdf bundle. Topics like critical infrastructure, cloud security, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
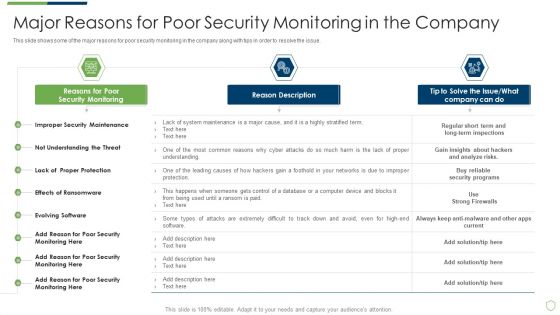
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Major Reasons For Poor Security Elements PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach major reasons for poor security elements pdf bundle. Topics like major reasons for poor security monitoring in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
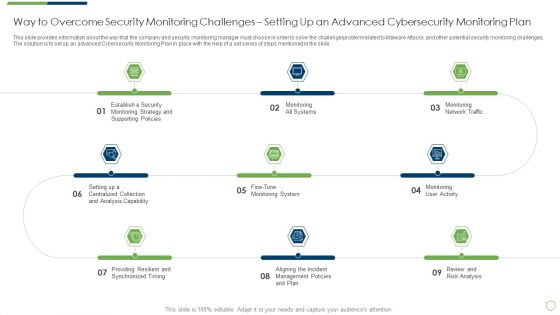
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Way To Overcome Security Introduction PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a modern security observation plan to eradicate cybersecurity risk and data breach way to overcome security introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost.
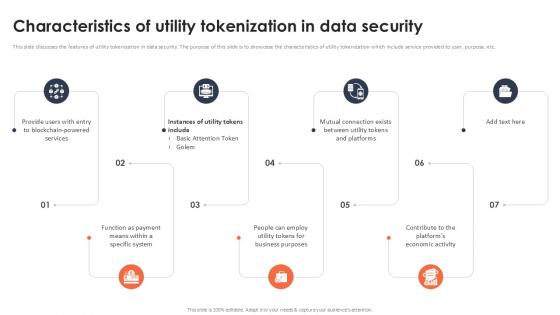
Characteristics Of Utility Tokenization In Data Security Securing Your Data Ppt Slide
This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Characteristics Of Utility Tokenization In Data Security Securing Your Data Ppt Slide will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc.
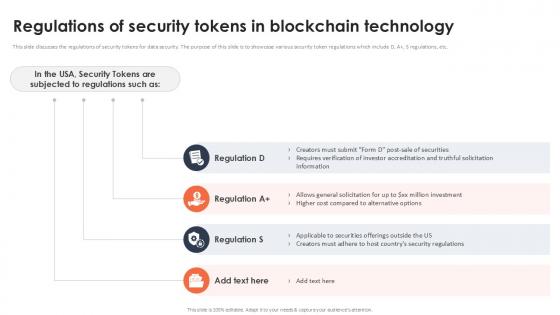
Regulations Of Security Tokens In Blockchain Technology Securing Your Data Ppt Slide
This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc. Find a pre-designed and impeccable Regulations Of Security Tokens In Blockchain Technology Securing Your Data Ppt Slide The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc.
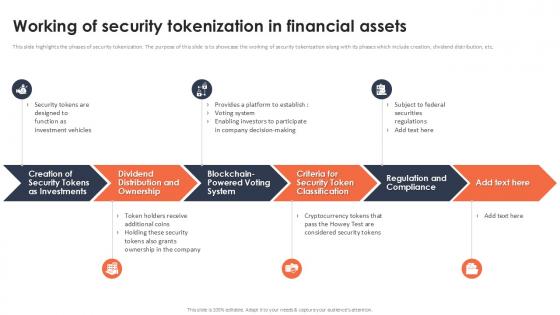
Working Of Security Tokenization In Financial Assets Securing Your Data Ppt Powerpoint
This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Working Of Security Tokenization In Financial Assets Securing Your Data Ppt Powerpoint These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc.

Best Practices For Tokenization In Data Security Securing Your Data Ppt Example
The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. There are so many reasons you need a Best Practices For Tokenization In Data Security Securing Your Data Ppt Example The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc.
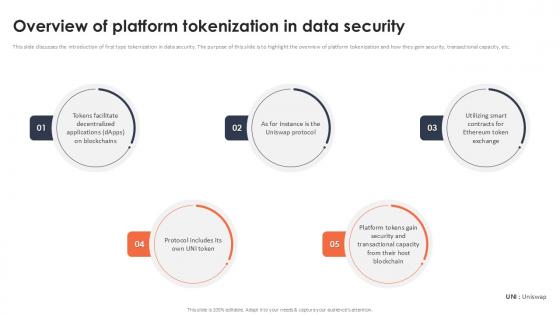
Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation
This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc.
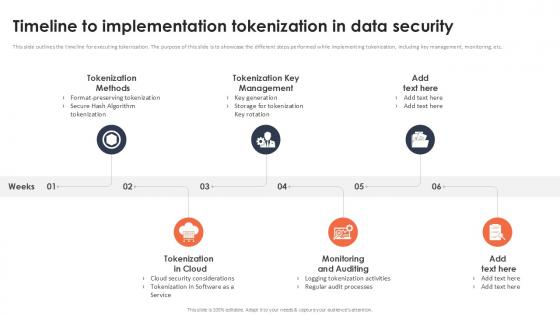
Timeline To Implementation Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the timeline for executing tokenization. The purpose of this slide is to showcase the different steps performed while implementing tokenization, including key management, monitoring, etc. Get a simple yet stunning designed Timeline To Implementation Tokenization In Data Security Securing Your Data Ppt Sample It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Timeline To Implementation Tokenization In Data Security Securing Your Data Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the timeline for executing tokenization. The purpose of this slide is to showcase the different steps performed while implementing tokenization, including key management, monitoring, etc.
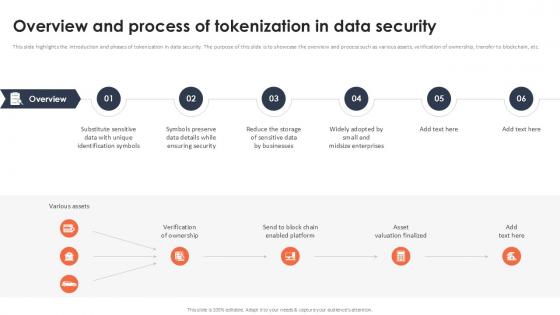
Overview And Process Of Tokenization In Data Security Securing Your Data Ppt Presentation
This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc. Slidegeeks has constructed Overview And Process Of Tokenization In Data Security Securing Your Data Ppt Presentation after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc.
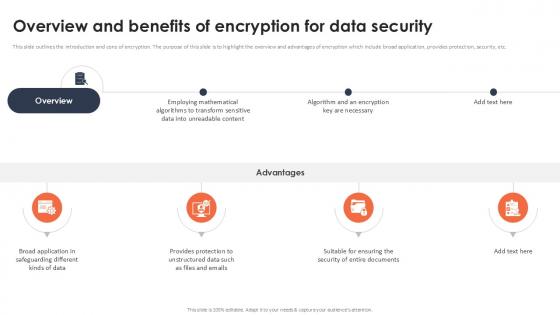
Overview And Benefits Of Encryption For Data Security Securing Your Data Ppt Powerpoint
This slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc. Retrieve professionally designed Overview And Benefits Of Encryption For Data Security Securing Your Data Ppt Powerpoint to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc.
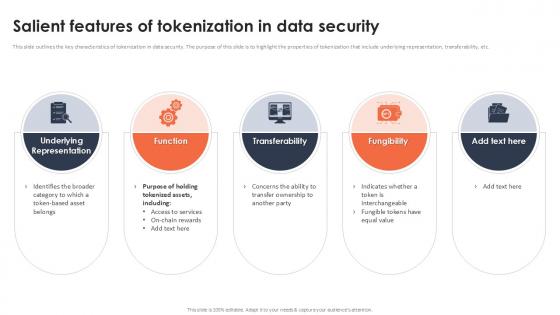
Salient Features Of Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the key characteristics of tokenization in data security. The purpose of this slide is to highlight the properties of tokenization that include underlying representation, transferability, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Salient Features Of Tokenization In Data Security Securing Your Data Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the key characteristics of tokenization in data security. The purpose of this slide is to highlight the properties of tokenization that include underlying representation, transferability, etc.
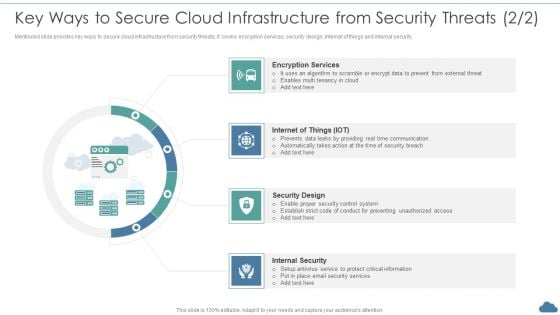
Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF
Mentioned slide provides key ways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Encryption Services, Security Design, Internal Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Timeline To Implement Cloud Data Security In Cloud Computing Ppt Sample
This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Timeline To Implement Cloud Data Security In Cloud Computing Ppt Sample. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Timeline To Implement Cloud Data Security In Cloud Computing Ppt Sample today and make your presentation stand out from the rest This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.
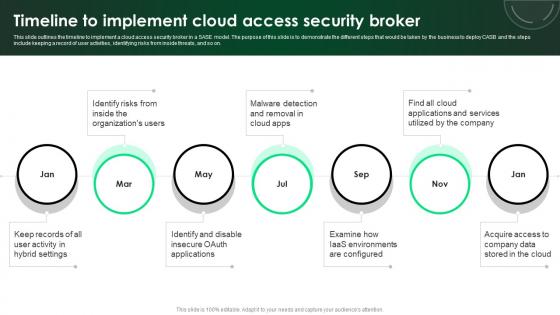
CASB 2 0 IT Timeline To Implement Cloud Access Security Broker
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable CASB 2 0 IT Timeline To Implement Cloud Access Security Broker. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on.
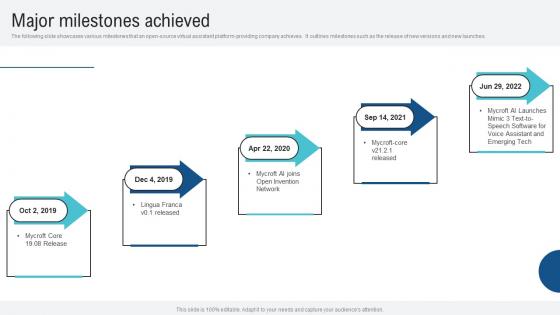
Major Milestones Achieved Voice Assistance Security Platform Investor Funding Presentation Slides Pdf
The following slide showcases various milestones that an open source virtual assistant platform providing company achieves. It outlines milestones such as the release of new versions and new launches. Slidegeeks has constructed Major Milestones Achieved Voice Assistance Security Platform Investor Funding Presentation Slides Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. The following slide showcases various milestones that an open source virtual assistant platform providing company achieves. It outlines milestones such as the release of new versions and new launches.
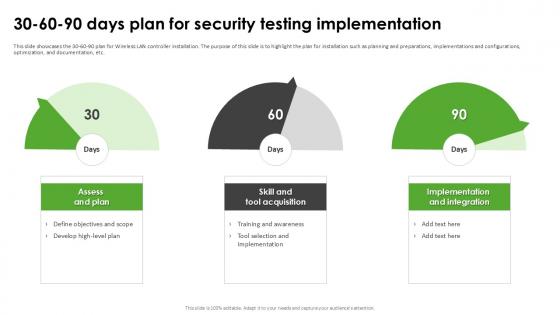
30 60 90 Days Plan For Security Harnessing The World Of Ethical Ppt Sample
This slide showcases the 30-60-90 plan for Wireless LAN controller installation. The purpose of this slide is to highlight the plan for installation such as planning and preparations, implementations and configurations, optimization, and documentation, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate 30 60 90 Days Plan For Security Harnessing The World Of Ethical Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases the 30-60-90 plan for Wireless LAN controller installation. The purpose of this slide is to highlight the plan for installation such as planning and preparations, implementations and configurations, optimization, and documentation, etc.
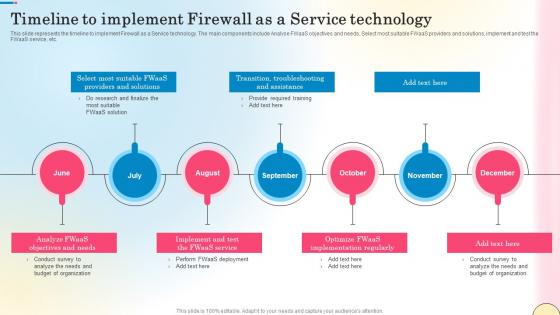
Timeline To Implement Firewall As A Service Technology Network Security Template Pdf
This slide represents the timeline to implement Firewall as a Service technology. The main components include Analyse FWaaS objectives and needs, Select most suitable FWaaS providers and solutions, implement and test the FWaaS service, etc. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Firewall As A Service Technology Network Security Template Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents the timeline to implement Firewall as a Service technology. The main components include Analyse FWaaS objectives and needs, Select most suitable FWaaS providers and solutions, implement and test the FWaaS service, etc.
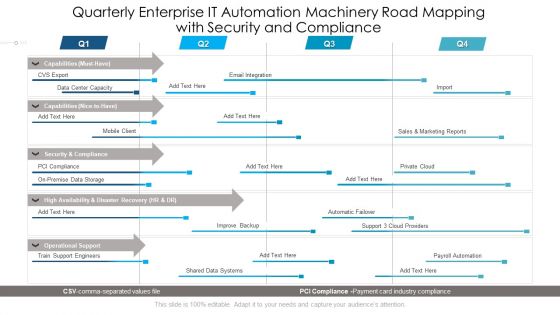
Quarterly Enterprise IT Automation Machinery Road Mapping With Security And Compliance Diagrams
Presenting our innovatively structured quarterly enterprise it automation machinery road mapping with security and compliance diagrams Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
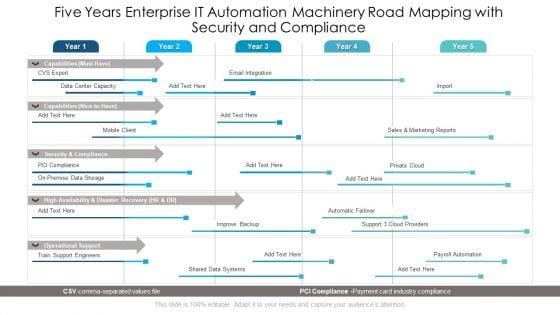
Five Years Enterprise IT Automation Machinery Road Mapping With Security And Compliance Ideas
Presenting the five years enterprise it automation machinery road mapping with security and compliance ideas. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
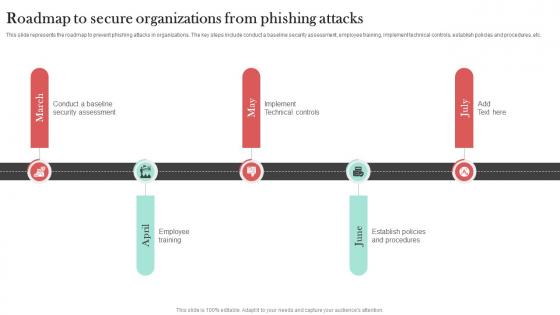
Roadmap To Secure Organizations Man In The Middle Phishing IT
This slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Roadmap To Secure Organizations Man In The Middle Phishing IT and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc.

Six Months Enterprise IT Automation Machinery Road Mapping With Security And Compliance Professional
We present our six months enterprise it automation machinery road mapping with security and compliance professional. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months enterprise it automation machinery road mapping with security and compliance professional in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
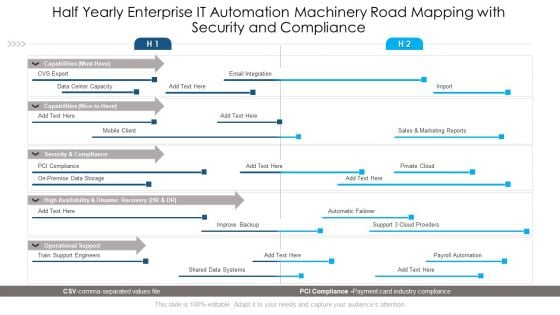
Half Yearly Enterprise IT Automation Machinery Road Mapping With Security And Compliance Inspiration
Introducing our half yearly enterprise it automation machinery road mapping with security and compliance inspiration. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Three Months Enterprise IT Automation Machinery Road Mapping With Security And Compliance Sample
Presenting our jaw dropping three months enterprise it automation machinery road mapping with security and compliance sample. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
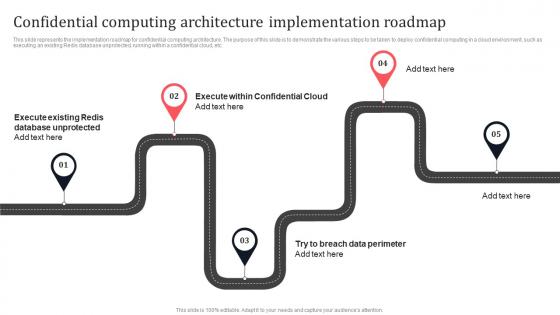
Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf
This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.
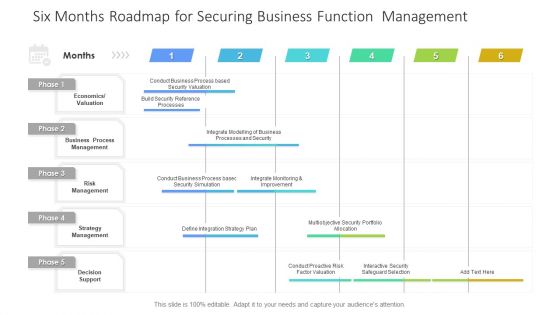
Six Months Roadmap For Securing Business Function Management Topics PDF
Presenting the six months roadmap for securing business function management topics pdf. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
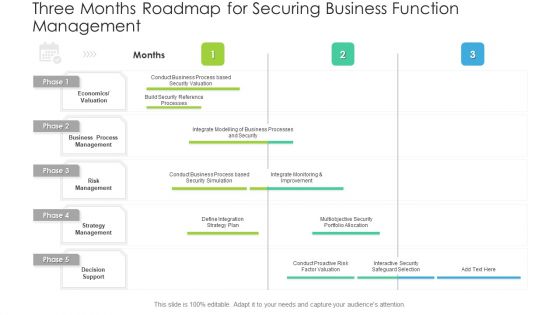
Three Months Roadmap For Securing Business Function Management Inspiration PDF
Presenting the three months roadmap for securing business function management inspiration pdf. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
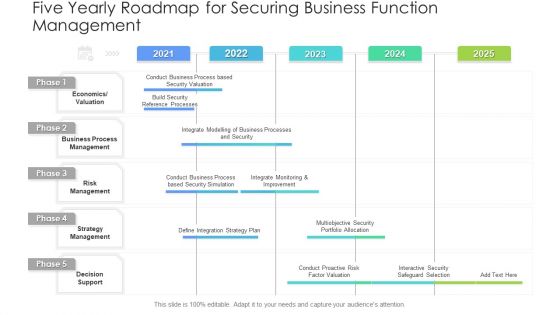
Five Yearly Roadmap For Securing Business Function Management Graphics PDF
Presenting the five yearly roadmap for securing business function management graphics pdf. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
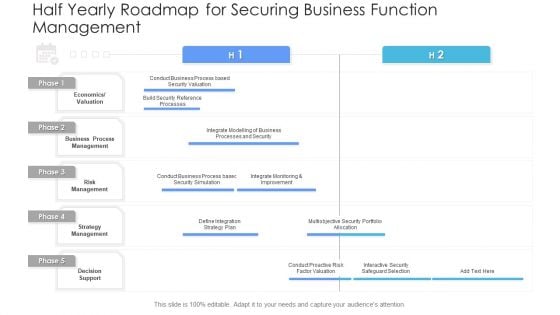
Half Yearly Roadmap For Securing Business Function Management Guidelines PDF
Presenting the half yearly roadmap for securing business function management guidelines pdf. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
Quarterly Roadmap For Securing Business Function Management Clipart PDF
Presenting the quarterly roadmap for securing business function management clipart pdf. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
Secured Digital Currency Transaction Four Quarter Roadmap Slides
Presenting our innovatively structured secured digital currency transaction four quarter roadmap slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Investment Planning Five Year Process Roadmap For Secured Future Graphics
Presenting our innovatively structured investment planning five year process roadmap for secured future graphics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
Secured Digital Currency Transaction Five Year Roadmap Themes
We present our secured digital currency transaction five year roadmap themes. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched secured digital currency transaction five year roadmap themes in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Secured Digital Currency Transaction Six Months Roadmap Guidelines
Presenting the secured digital currency transaction six months roadmap guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
Investment Planning Half Yearly Process Roadmap For Secured Future Topics
Presenting the investment planning half yearly process roadmap for secured future topics. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
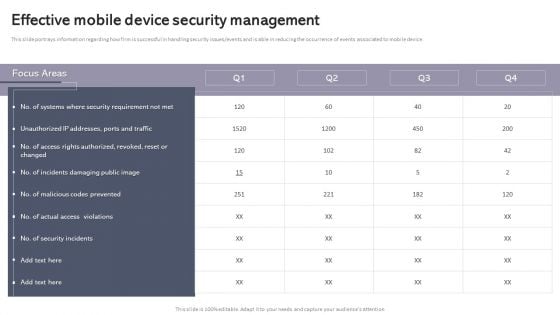
Workplace Portable Device Monitoring And Administration Effective Mobile Device Security Management Pictures PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. This Workplace Portable Device Monitoring And Administration Effective Mobile Device Security Management Pictures PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Workplace Portable Device Monitoring And Administration Effective Mobile Device Security Management Pictures PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
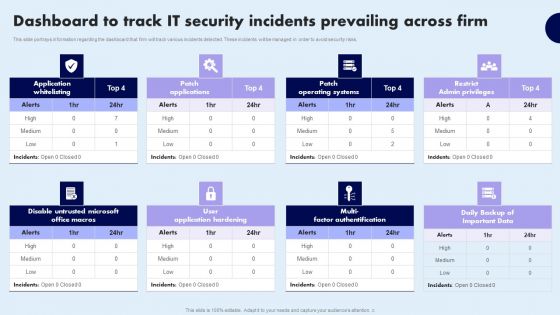
Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF today and make your presentation stand out from the rest
Secured Digital Currency Transaction Half Yearly Roadmap Portrait
Introducing our secured digital currency transaction half yearly roadmap portrait. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
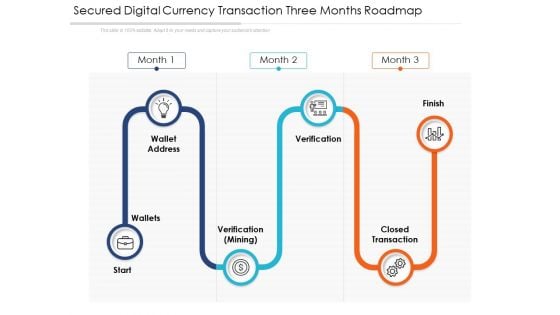
Secured Digital Currency Transaction Three Months Roadmap Graphics
Presenting our jaw dropping secured digital currency transaction three months roadmap graphics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
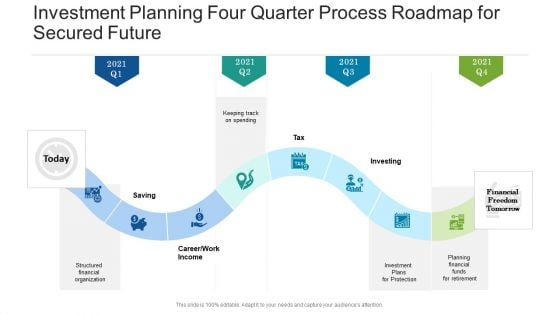
Investment Planning Four Quarter Process Roadmap For Secured Future Demonstration
Introducing our investment planning four quarter process roadmap for secured future demonstration. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
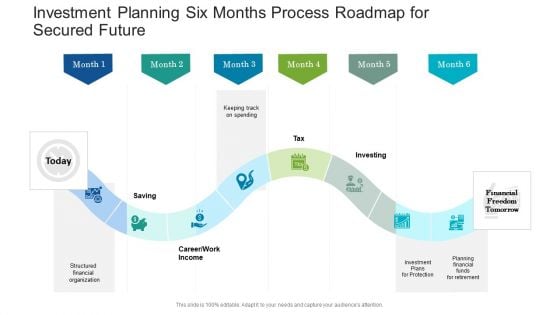
Investment Planning Six Months Process Roadmap For Secured Future Download
Introducing our investment planning six months process roadmap for secured future download. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Developing Firm Security Strategy Plan Weekly Timeline With Task Name Clipart PDF
Deliver an awe inspiring pitch with this creative developing firm security strategy plan weekly timeline with task name clipart pdf bundle. Topics like weekly timeline with task name can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































