Network Security
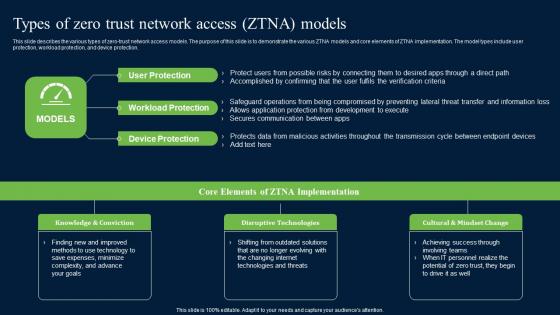
Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Boost your pitch with our creative Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.
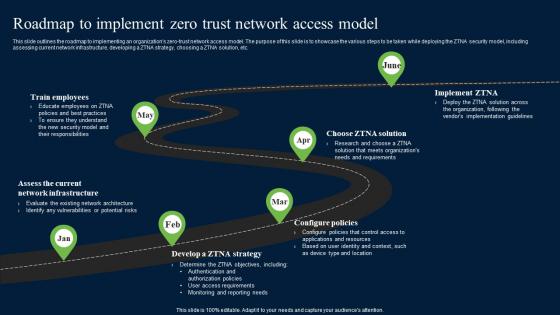
Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.

Main Pillars Of Zero Network Trust Access Zero Trust Network Security Professional Pdf
This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation. Welcome to our selection of the Main Pillars Of Zero Network Trust Access Zero Trust Network Security Professional Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation.
Securing Windows With Network Security System Ppt PowerPoint Presentation File Slides PDF
Presenting this set of slides with name securing windows with network security system ppt powerpoint presentation file slides pdf. The topics discussed in these slide is securing windows with network security system. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Wireless Network Security System Icon Of Cloud Servers To Secure Data Clipart PDF
Persuade your audience using this wireless network security system icon of cloud servers to secure data clipart pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including wireless network security system icon of cloud servers to secure data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
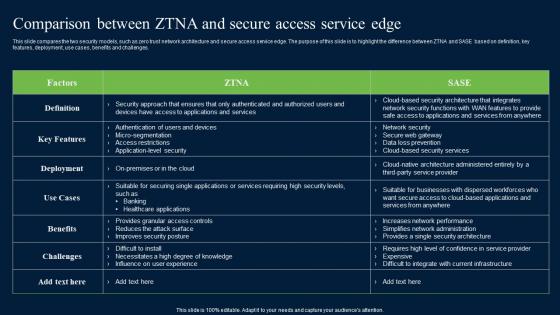
Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Slidegeeks is here to make your presentations a breeze with Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.
Wireless Network Security System To Prevent Unauthorized Access To Internet Elements PDF
Presenting wireless network security system to prevent unauthorized access to internet elements pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including wireless network security system to prevent unauthorized access to internet. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Common Network Security Threats Vector Icon Ppt PowerPoint Presentation Ideas Elements PDF
Presenting common network security threats vector icon ppt powerpoint presentation ideas elements pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including common network security threats vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Business Network Security Vector Icon Ppt PowerPoint Presentation File Layouts PDF
Presenting business network security vector icon ppt powerpoint presentation file layouts pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including business network security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Data Network Security With Lock Showing Online Safety Icon Ppt PowerPoint Presentation Infographic Template Graphics PDF
Presenting this set of slides with name data network security with lock showing online safety icon ppt powerpoint presentation infographic template graphics pdf. This is a two stage process. The stages in this process are data network security with lock showing online safety icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Business Network Security Vector Icon Ppt PowerPoint Presentation Gallery Examples PDF
Presenting this set of slides with name business network security vector icon ppt powerpoint presentation gallery examples pdf. This is a three stage process. The stages in this process are business network security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Vector Showing Wide Area Network Security Analysis Ppt PowerPoint Presentation Summary Templates PDF
Presenting this set of slides with name vector showing wide area network security analysis ppt powerpoint presentation summary templates pdf. This is a three stage process. The stages in this process are vector showing wide area network security analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
IT Network Security And Protection Vector Icon Ppt PowerPoint Presentation Gallery Slides PDF
Persuade your audience using this it network security and protection vector icon ppt powerpoint presentation gallery slides pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including it network security and protection vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icon Of Wireless Network Security System With Lock And Globe Grid Demonstration PDF
Presenting icon of wireless network security system with lock and globe grid demonstration pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including icon of wireless network security system with lock and globe grid. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

As A Service Deployment Approach Zero Trust Network Security Microsoft Pdf
This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. Boost your pitch with our creative As A Service Deployment Approach Zero Trust Network Security Microsoft Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software.
Corporate Data Management For Network Security Vector Icon Ppt PowerPoint Presentation Icon Portfolio PDF
Pitch your topic with ease and precision using this corporate data management for network security vector icon ppt powerpoint presentation icon portfolio pdf. This layout presents information on corporate data management for network security vector icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Wireless Network Security System Camera Connected With Computer System Portrait PDF
Presenting wireless network security system camera connected with computer system portrait pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including wireless network security system camera connected with computer system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon Of Wireless Network Security System Camera Via Internet Diagrams PDF
Presenting icon of wireless network security system camera via internet diagrams pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including icon of wireless network security system camera via internet. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Importance Of Firewall Network Security In Business Vector Icon Ppt PowerPoint Presentation File Aids PDF
Presenting this set of slides with name importance of firewall network security in business vector icon ppt powerpoint presentation file aids pdf. This is a three stage process. The stages in this process are importance of firewall network security in business vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Assessment For IT Network Security Ppt PowerPoint Presentation Gallery Example PDF
Presenting this set of slides with name threat assessment for it network security ppt powerpoint presentation gallery example pdf. This is a three stage process. The stages in this process are threat assessment for it network security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Network Security Protection Ensuring Safety From Online Threat Ppt PowerPoint Presentation Portfolio Influencers PDF
Persuade your audience using this network security protection ensuring safety from online threat ppt powerpoint presentation portfolio influencers pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including network security protection ensuring safety from online threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Online Network Security Against Hackers And Internet Threats Ppt PowerPoint Presentation File Show PDF
Persuade your audience using this online network security against hackers and internet threats ppt powerpoint presentation file show pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including online network security against hackers and internet threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Network Security Vs Firewall Ppt PowerPoint Presentation Infographic Template Gridlines Cpb
Presenting this set of slides with name network security vs firewall ppt powerpoint presentation infographic template gridlines cpb. This is an editable Powerpoint five stages graphic that deals with topics like network security vs firewall to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Computer Network Security Training Ppt PowerPoint Presentation Slides Portfolio Cpb Pdf
Presenting this set of slides with name computer network security training ppt powerpoint presentation slides portfolio cpb pdf. This is an editable Powerpoint six stages graphic that deals with topics like computer network security training to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Smart Phone With Wireless Network Security Alarm Icon Ppt Pictures Graphics Tutorials PDF
Persuade your audience using this smart phone with wireless network security alarm icon ppt pictures graphics tutorials pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including smart phone with wireless network security alarm icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Firewall Network Security Communication PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Firewall Network Security Communication PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime. Use our Technology PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination. Download our Communication PowerPoint Templates because Our PowerPoint Templates and Slides help you meet the demand of the Market. Just browse and pick the slides that appeal to your intuitive senses. Download and present our Business PowerPoint Templates because It will Strengthen your hand with your thoughts. They have all the aces you need to win the day. Present our Signs PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination.Use these PowerPoint slides for presentations relating to firewall, security, business, signs, communication, technology. The prominent colors used in the PowerPoint template are Green, Red, White. Our Firewall Network Security Communication PowerPoint Templates Ppt Backgrounds For Slides 0313 ensure the audience is never fed up. They will continue asking for more.
Icons Slide For Network Security Using Firewall As A Service Clipart Pdf
Introducing our well designed Icons Slide For Network Security Using Firewall As A Service Clipart Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Network Security Using Firewall As A Service Clipart Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
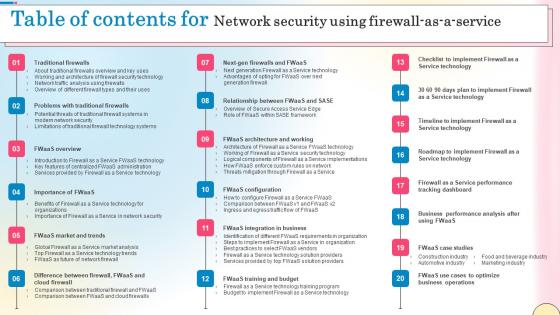
Table Of Contents For Network Security Using Firewall As A Service Guidelines Pdf
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Table Of Contents For Network Security Using Firewall As A Service Guidelines Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. Our Table Of Contents For Network Security Using Firewall As A Service Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
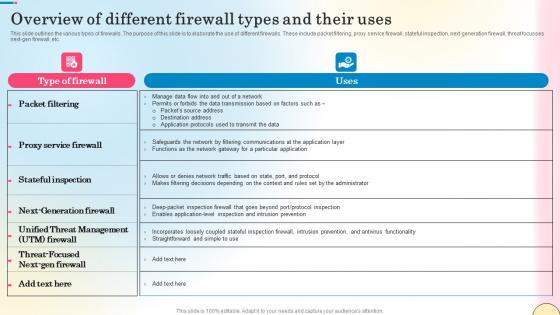
Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf
This slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc. Find a pre-designed and impeccable Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc.

Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF
This slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Get a simple yet stunning designed Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
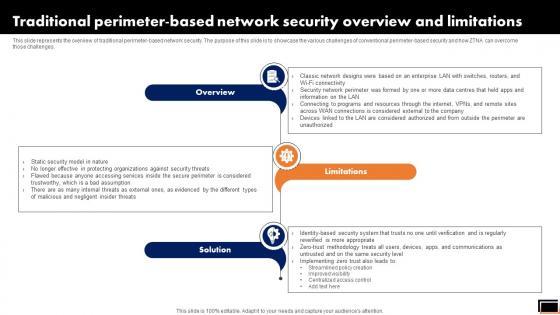
Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. If you are looking for a format to display your unique thoughts, then the professionally designed Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.
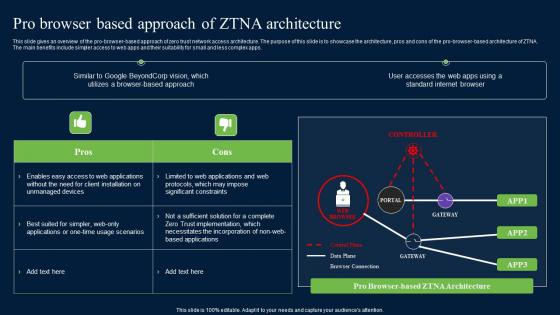
Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf
The main benefits include simpler access to web apps and their suitability for small and less complex apps. Presenting this PowerPoint presentation, titled Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The main benefits include simpler access to web apps and their suitability for small and less complex apps.
IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Are you searching for a IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF from Slidegeeks today.

Organizational Network Security Awareness Staff Learning Table Of Contents Introduction PDF
Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning table of contents introduction pdf. Use them to share invaluable insights on security awareness training, organization impact metrics, security awareness, communication plan, budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Boost your pitch with our creative Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
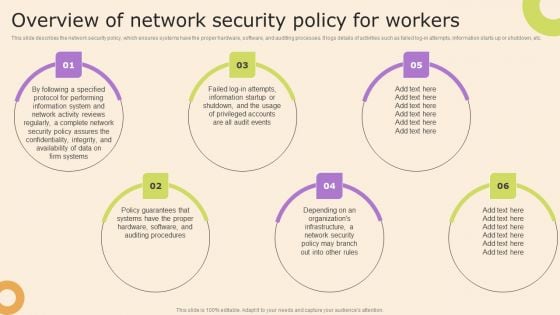
Information Technology Policy And Processes Overview Of Network Security Policy For Workers Pictures PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Information Technology Policy And Processes Overview Of Network Security Policy For Workers Pictures PDF from Slidegeeks and deliver a wonderful presentation.
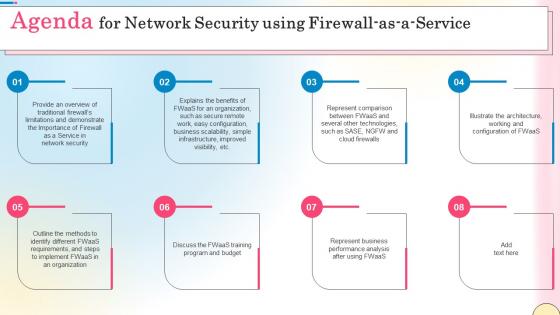
Agenda For Network Security Using Firewall As A Service Diagrams Pdf
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Agenda For Network Security Using Firewall As A Service Diagrams Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Our Agenda For Network Security Using Firewall As A Service Diagrams Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
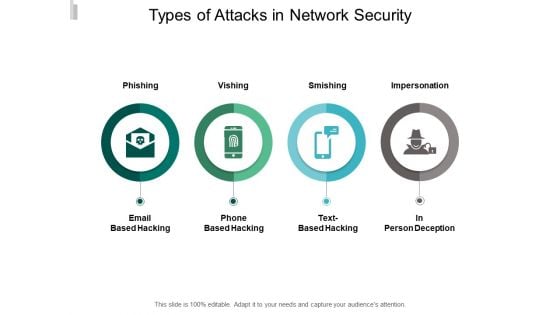
Types Of Attacks In Network Security Ppt PowerPoint Presentation Portfolio Layouts
Presenting this set of slides with name types of attacks in network security ppt powerpoint presentation portfolio layouts. This is a four stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf
This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. Find highly impressive Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access.

Network Security Using Firewall As A Service Ppt PowerPoint Presentation Complete Deck With Slides
This Network Security Using Firewall As A Service Ppt PowerPoint Presentation Complete Deck With Slides is designed to help you retain your audiences attention. This content-ready PowerPoint Template enables you to take your audience on a journey and share information in a way that is easier to recall. It helps you highlight the crucial parts of your work so that the audience does not get saddled with information download. This eight three slide PPT Deck comes prepared with the graphs and charts you could need to showcase your information through visuals. You only need to enter your own data in them. Download this editable PowerPoint Theme and walk into that meeting with confidence. Our Network Security Using Firewall As A Service Ppt PowerPoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Zero Trust Network Security Ppt PowerPoint Presentation Complete Deck With Slides
Use this Zero Trust Network Security Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in eighty nine slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now. Our Zero Trust Network Security Ppt PowerPoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
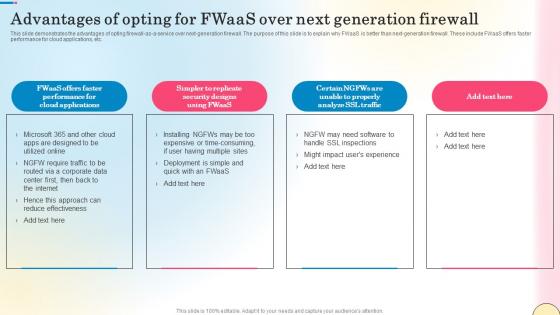
Advantages Of Opting For Fwaas Over Next Network Security Diagrams Pdf
This slide demonstrates the advantages of opting firewall-as-a-service over next-generation firewall. The purpose of this slide is to explain why FWaaS is better than next-generation firewall. These include FWaaS offers faster performance for cloud applications, etc. Create an editable Advantages Of Opting For Fwaas Over Next Network Security Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Advantages Of Opting For Fwaas Over Next Network Security Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the advantages of opting firewall-as-a-service over next-generation firewall. The purpose of this slide is to explain why FWaaS is better than next-generation firewall. These include FWaaS offers faster performance for cloud applications, etc.
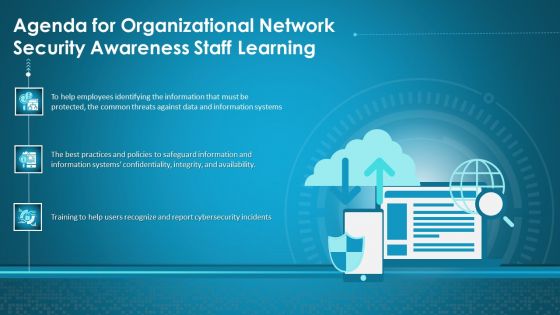
Agenda For Organizational Network Security Awareness Staff Learning Ppt Styles Master Slide PDF
Deliver an awe-inspiring pitch with this creative agenda for organizational network security awareness staff learning ppt styles master slide pdf bundle. Topics like employees identifying, cybersecurity incidents, information systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
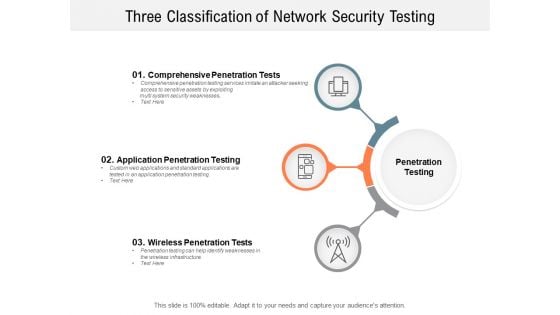
Three Classification Of Network Security Testing Ppt PowerPoint Presentation Slides Demonstration
Presenting this set of slides with name three classification of network security testing ppt powerpoint presentation slides demonstration. This is a three stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
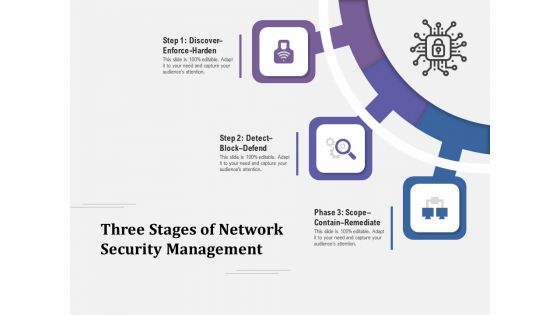
Three Stages Of Network Security Management Ppt PowerPoint Presentation Layouts Influencers PDF
Presenting three stages of network security management ppt powerpoint presentation layouts influencers pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, detect block defend, scope contain remediate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Three Phases Of Network Security Issues Ppt PowerPoint Presentation Icon Portrait PDF
Presenting three phases of network security issues ppt powerpoint presentation icon portrait pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, detect block defend, scope contain remediate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
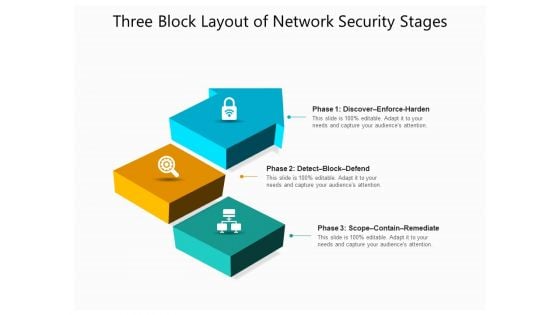
Three Block Layout Of Network Security Stages Ppt PowerPoint Presentation File Graphics Design PDF
Presenting three block layout of network security stages ppt powerpoint presentation file graphics design pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, detect block defend, scope contain remediate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Organizational Network Security Awareness Staff Learning Icons Slide Ppt Designs Download PDF
Download our innovative and attention-grabbing organizational network security awareness staff learning icons slide ppt designs download pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.

Network Security Using Firewall As A Service Table Of Contents Designs Pdf
This slide demonstrates the flow of traffic within a network secured with firewall. The purpose of this slide is to illustrate the meaning of good and bad traffic. This slide also highlights the factors which are used to analyze the nature of data packets. This Network Security Using Firewall As A Service Table Of Contents Designs Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide demonstrates the flow of traffic within a network secured with firewall. The purpose of this slide is to illustrate the meaning of good and bad traffic. This slide also highlights the factors which are used to analyze the nature of data packets.
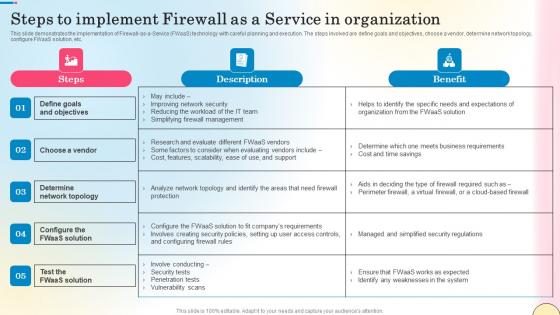
Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf
This slide demonstrates the implementation of Firewall-as-a-Service FWaaS technology with careful planning and execution. The steps involved are define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc. Get a simple yet stunning designed Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide demonstrates the implementation of Firewall-as-a-Service FWaaS technology with careful planning and execution. The steps involved are define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc.
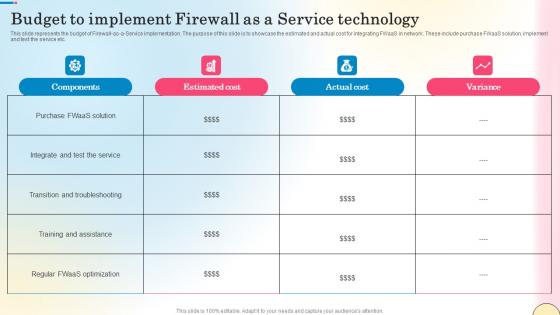
Budget To Implement Firewall As A Service Technology Network Security Diagrams Pdf
This slide represents the budget of Firewall-as-a-Service implementation. The purpose of this slide is to showcase the estimated and actual cost for integrating FWaaS in network. These include purchase FWaaS solution, implement and test the service etc. Get a simple yet stunning designed Budget To Implement Firewall As A Service Technology Network Security Diagrams Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Budget To Implement Firewall As A Service Technology Network Security Diagrams Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the budget of Firewall-as-a-Service implementation. The purpose of this slide is to showcase the estimated and actual cost for integrating FWaaS in network. These include purchase FWaaS solution, implement and test the service etc.
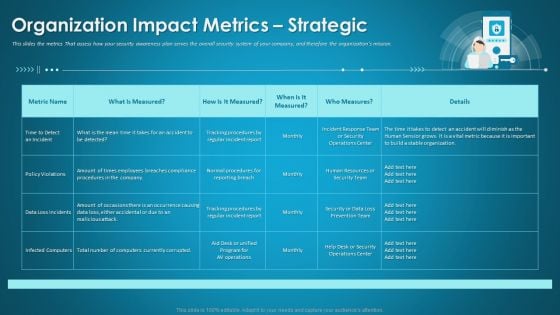
Organizational Network Security Awareness Staff Learning Organization Impact Metrics Strategic Structure PDF
This slides the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning organization impact metrics strategic structure pdf. Use them to share invaluable insights on human resources, security operations, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
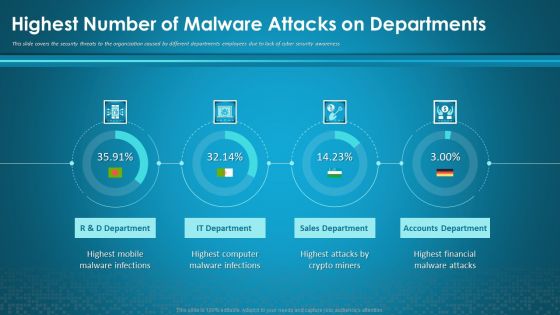
Organizational Network Security Awareness Staff Learning Highest Number Of Malware Attacks On Departments Information PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning highest number of malware attacks on departments information pdf. Use them to share invaluable insights on sales department, accounts department, financial, computer, mobile and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizational Network Security Awareness Staff Learning Communication Plan General Format Infographics PDF
This slide covers the schedule communication plan for security awareness program including brief description, frequency and audience. Deliver an awe-inspiring pitch with this creative organizational network security awareness staff learning communication plan general format infographics pdf bundle. Topics like communication, security awareness, organizations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf
This slide represents the dashboard to track the performance of Firewall-as-a-Service deployed by different organizations. The purpose of this slide is to showcase the overall performance of FWaaS by demonstrating statistics of monthly threat status, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the dashboard to track the performance of Firewall-as-a-Service deployed by different organizations. The purpose of this slide is to showcase the overall performance of FWaaS by demonstrating statistics of monthly threat status, etc.
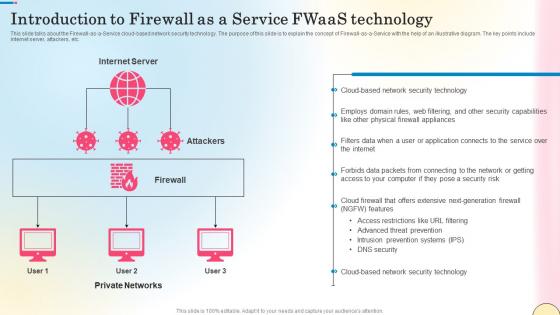
Introduction To Firewall As A Service Fwaas Technology Network Security Professional Pdf
This slide talks about the Firewall-as-a-Service cloud-based network security technology. The purpose of this slide is to explain the concept of Firewall-as-a-Service with the help of an illustrative diagram. The key points include internet server, attackers, etc. Retrieve professionally designed Introduction To Firewall As A Service Fwaas Technology Network Security Professional Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the Firewall-as-a-Service cloud-based network security technology. The purpose of this slide is to explain the concept of Firewall-as-a-Service with the help of an illustrative diagram. The key points include internet server, attackers, etc.
Cloud Network Security Dimensions And Sections Ppt PowerPoint Presentation Icon Background Images PDF
Presenting cloud network security dimensions and sections ppt powerpoint presentation icon background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, service, threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
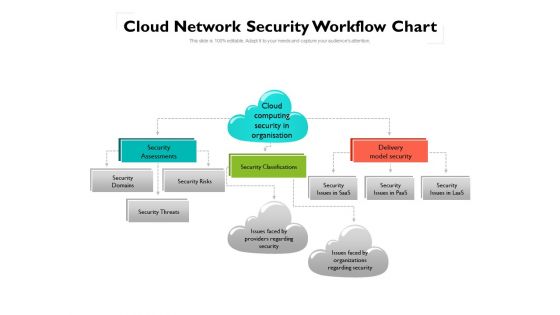
Cloud Network Security Workflow Chart Ppt PowerPoint Presentation Gallery Ideas PDF
This is a cloud network security workflow chart ppt powerpoint presentation gallery ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, organizations, domains. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizational Network Security Awareness Staff Learning Organization Impact Metrics Behaviours Portrait PDF
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people. Deliver an awe-inspiring pitch with this creative organizational network security awareness staff learning organization impact metrics behaviours portrait pdf bundle. Topics like organization impact metrics behaviours can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
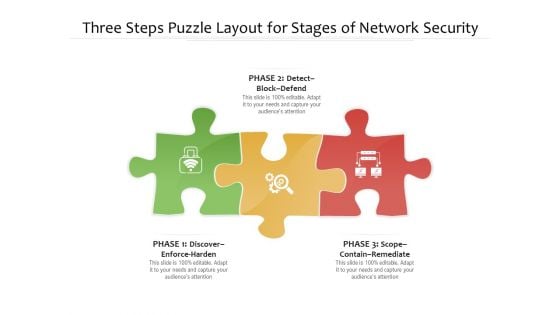
Three Steps Puzzle Layout For Stages Of Network Security Ppt PowerPoint Presentation File Vector PDF
Persuade your audience using this three steps puzzle layout for stages of network security ppt powerpoint presentation file vector pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including detect block defend, discover enforce harden, scope contain remediate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































