Network Security

Desktop Security Management Key Elements Of Computer Security Download PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a desktop security management key elements of computer security download pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, information security, application security, network security, cloud security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
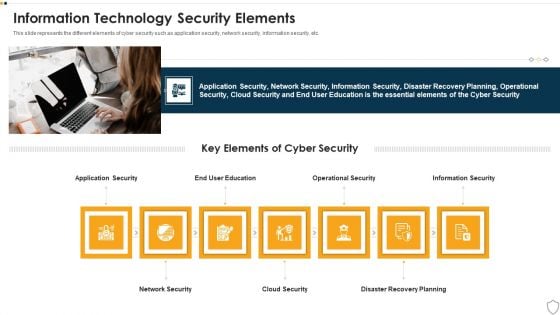
IT Security Information Technology Security Elements Ppt Images PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a it security information technology security elements ppt images pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, cloud security, disaster recovery planning, operational security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
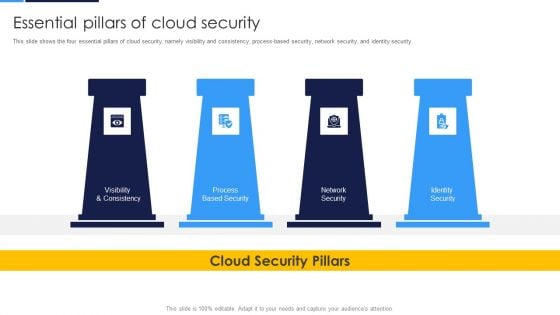
Cloud Security Assessment Essential Pillars Of Cloud Security Clipart PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process based security, network security, and identity security.Presenting Cloud Security Assessment Essential Pillars Of Cloud Security Clipart PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Visibility And Consistency, Network Security, Identity Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Application Security Performance Monitoring Application Security Testing
This slide showcases the performance tracking dashboard for application security to analyze and monitor security of application. Want to ace your presentation in front of a live audience Our Application Security Performance Monitoring Application Security Testing can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases the performance tracking dashboard for application security to analyze and monitor security of application.
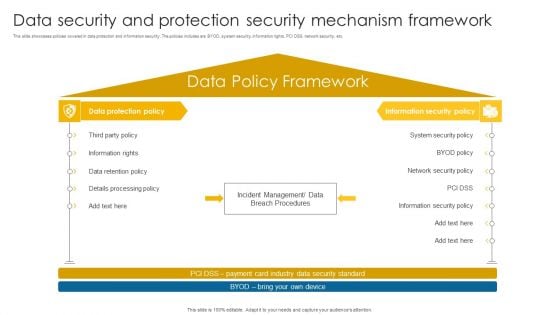
Data Security And Protection Security Mechanism Framework Background PDF
This slide showcases policies covered in data protection and information security. The policies includes are BYOD, system security, information rights, PCI DSS, network security, etc.Pitch your topic with ease and precision using this Data Security And Protection Security Mechanism Framework Background PDF. This layout presents information on Information Rights, Retention Policy, Details Processing. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
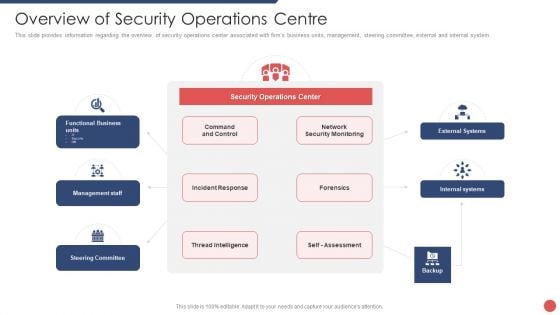
Security Functioning Centre Overview Of Security Operations Centre Summary PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this security functioning centre overview of security operations centre summary pdf. Use them to share invaluable insights on management, thread intelligence, network security monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
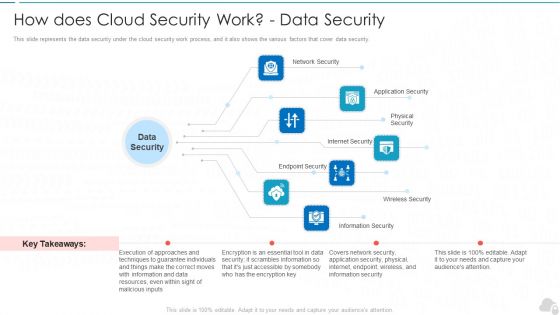
How Does Cloud Security Work Data Security Cloud Computing Security IT Ppt Ideas Slide Download PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. Presenting how does cloud security work data security cloud computing security it ppt ideas slide download pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network security, internet security, endpoint security, wireless security, physical security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
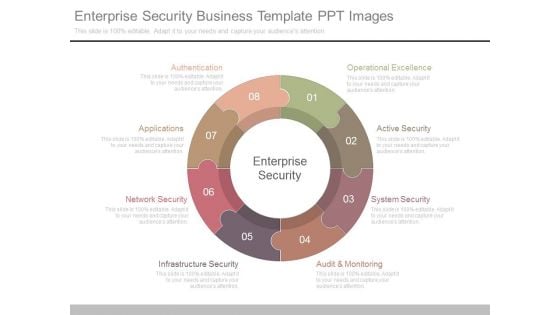
Enterprise Security Business Template Ppt Images
This is a enterprise security business template ppt images. This is a eight stage process. The stages in this process are enterprise security, authentication, applications, network security, infrastructure security, audit and monitoring, system security, active security, operational excellence.
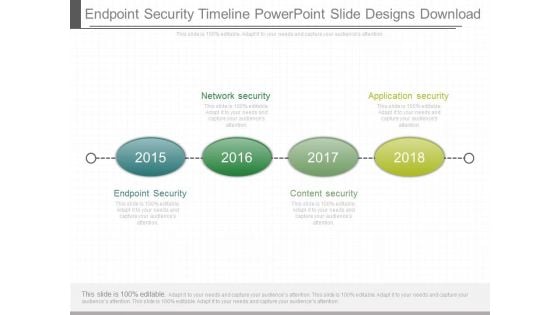
Endpoint Security Timeline Powerpoint Slide Designs Download
This is a endpoint security timeline powerpoint slide designs download. This is a four stage process. The stages in this process are network security, application security, endpoint security, content security.
Security Administration Powerpoint Shapes
This is a security administration powerpoint shapes. This is a three stage process. The stages in this process are storage management, directory service administration, security administration.
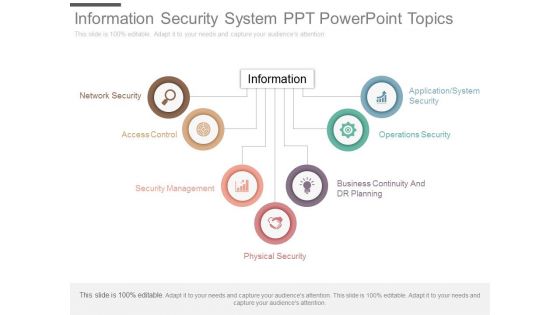
Information Security System Ppt Powerpoint Topics
This is a information security system ppt powerpoint topics. This is a seven stage process. The stages in this process are network security, access control, security management, physical security, business continuity and dr planning, operations security, application system security, information.
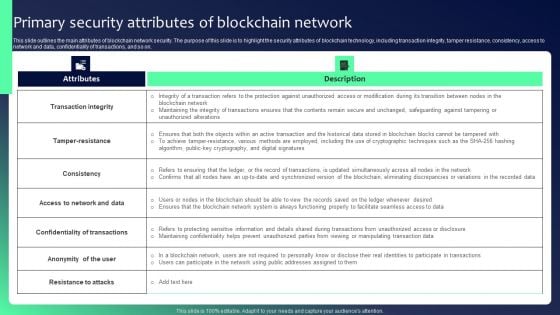
Blockchain Security Solutions Deployment Primary Security Attributes Structure PDF
This slide outlines the main attributes of blockchain network security. The purpose of this slide is to highlight the security attributes of blockchain technology, including transaction integrity, tamper resistance, consistency, access to network and data, confidentiality of transactions, and so on. The Blockchain Security Solutions Deployment Primary Security Attributes Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Elements Of Information Technology Security Information Technology Security Ppt Inspiration Icons PDF
This slide represents the network security element of network security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting elements of information technology security information technology security ppt inspiration icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like network security methods, tools, techniques, respond. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
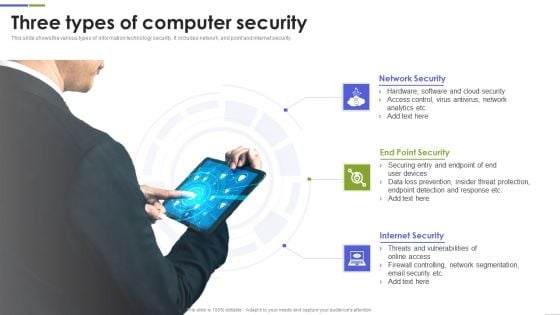
Three Types Of Computer Security Designs PDF
This slide shows the various types of information technology security. It includes network, end point and internet security. Presenting Three Types Of Computer Security Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Network Security, Point Security, Internet Security This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Essential Pillars Of Cloud Security Brochure PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. This is a Essential Pillars Of Cloud Security Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Process Based Security, Network Security, Identity Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security Architecture Ppt Infographic Template
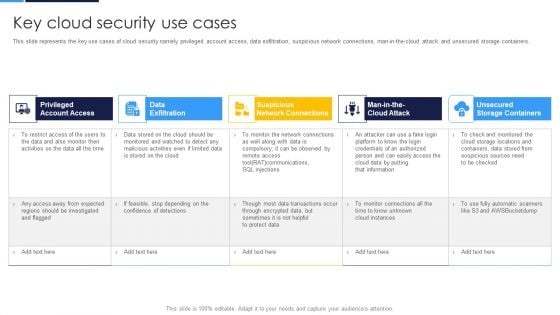
Cloud Security Assessment Key Cloud Security Use Cases Diagrams PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man-in-the-cloud attack, and unsecured storage containers.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Key Cloud Security Use Cases Diagrams PDF Use them to share invaluable insights on Account Access, Data Exfiltration, Network Connections and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
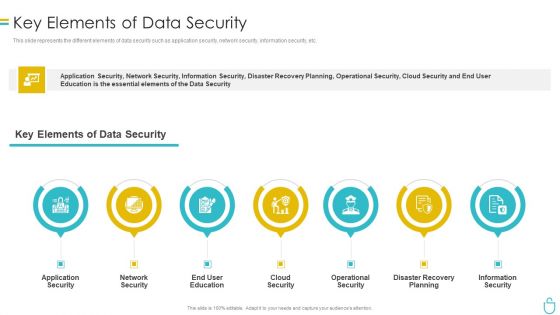
Information Security Key Elements Of Data Security Ppt Pictures Show PDF
This slide represents the different elements of data security such as application security, network security, information security, etc. Presenting information security key elements of data security ppt pictures show pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like network security, application security, cloud security, operational security, information security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Elements Of Computer Security Information Security Portrait PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. Presenting desktop security management elements of computer security information security portrait pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like social media, information security, organization, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Essential Pillars Of Cloud Security Cloud Computing Security IT Ppt Design Ideas PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. Presenting essential pillars of cloud security cloud computing security it ppt design ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like visibility and consistency, process based security, network security, identity security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Essential Pillars Of Cloud Security Ppt File Elements PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. This is a Cloud Information Security Essential Pillars Of Cloud Security Ppt File Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security, Identity Security, Visibility Consistency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
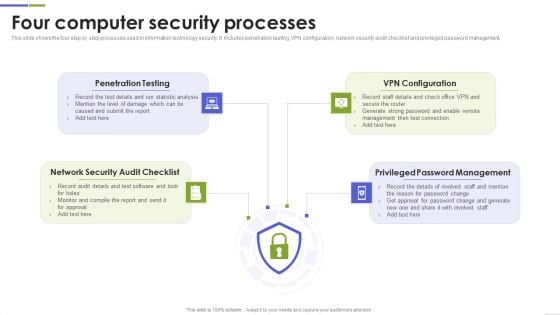
Four Computer Security Processes Portrait PDF
This slide shows the four step by step processes used in information technology security. It includes penetration testing, VPN configuration, network security audit checklist and privileged password management. Presenting Four Computer Security Processes Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Penetration Testing, Configuration, Password Management This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Spending On Security Software Against Cyber Security Attack Ppt Icon Show PDF
Showcasing this set of slides titled Spending On Security Software Against Cyber Security Attack Ppt Icon Show PDF. The topics addressed in these templates are Endpoint Security, Network Security, Messaging Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
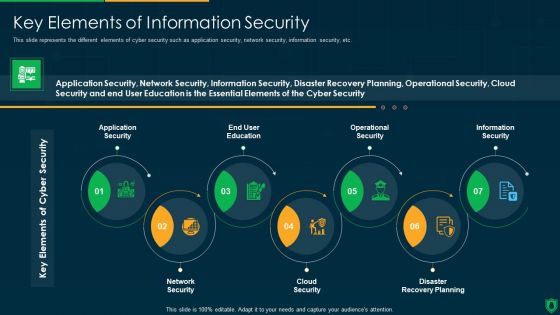
Info Security Key Elements Of Information Security Ppt PowerPoint Presentation Gallery Slide Download PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. Presenting info security key elements of information security ppt powerpoint presentation gallery slide download pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like application security, end user education, operational security, information security, network security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
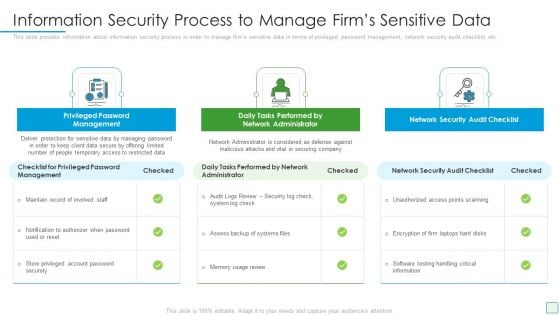
Developing Firm Security Strategy Plan Information Security Process To Manage Firms Sensitive Data Introduction PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. This is a developing firm security strategy plan information security process to manage firms sensitive data introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
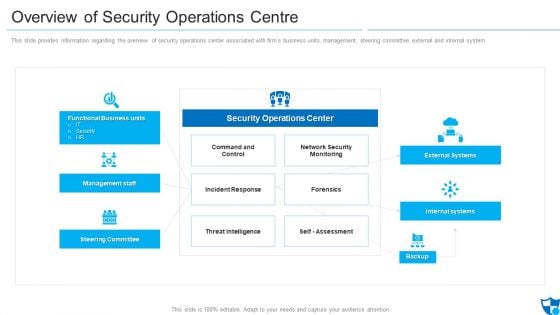
Overview Of Security Operations Centre Sample PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system.Deliver and pitch your topic in the best possible manner with this overview of security operations centre sample pdf. Use them to share invaluable insights on command and control, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
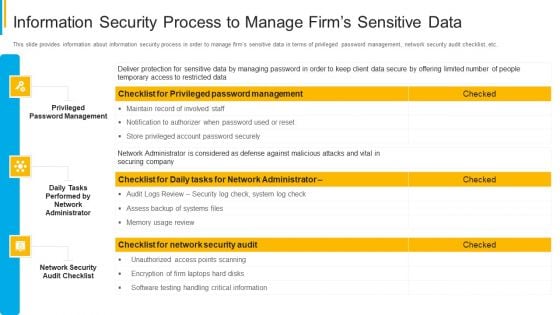
Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Summary PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative project security administration it information security process to manage firms sensitive data summary pdf bundle. Topics like privileged password management, daily tasks performed by network administrator, network security audit checklist can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Operations Cyber Security Protection Icon Rules PDF
Persuade your audience using this Security Operations Cyber Security Protection Icon Rules PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Operations Cyber, Security Protection Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security Operations Cyber Security Icon With Lock Clipart PDF
Persuade your audience using this Security Operations Cyber Security Icon With Lock Clipart PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Operations Cyber, Security Icon With Lock. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Mobile Security Powerpoint Presentation Slides
You will save yourself your energy and hours of time when you choose to use this impactful PowerPoint Deck. This Mobile Security Powerpoint Presentation Slides has been tailor-made to your business needs which ensures that you will always be prepared for that next meeting. Worry can not touch you when you present in your area of expertise using this PPT Template Bundle. With a modern design and easy to follow structure, this PowerPoint Presentation has Mobile Threat Defense, Mobile Authentication, Mobile Encryption, Mobile Privacy, Mobile Vulnerability Management-slides, which ensures that you can cover you need to without much work. Create your next presentation using this PPT Theme to deliver a memorable performance. The mobile security powerpoint template covers key aspects of mobile security, including threats, vulnerabilities, best practices, and implementation strategies.
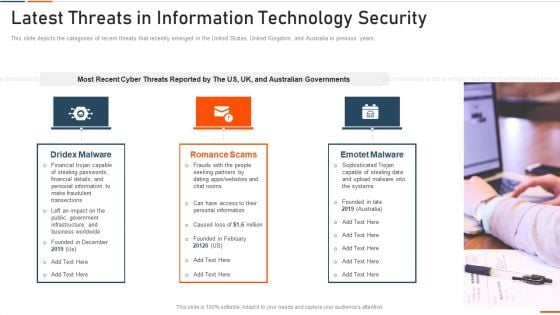
Latest Threats In Information Technology Security Ppt Pictures Designs PDF
This slide represents the different elements of Network security such as application security, network security, information security, etc. This is a latest threats in information technology security ppt pictures designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network security, cloud security, application security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
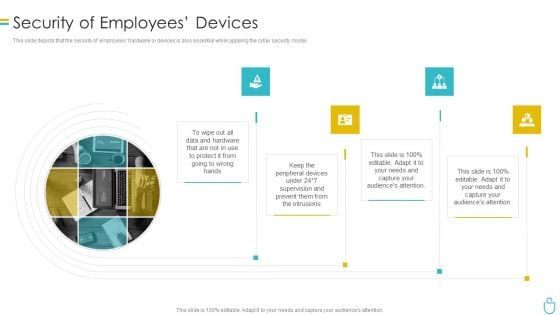
Information Security Security Of Employees Devices Ppt Model Infographics PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Presenting information security security of employees devices ppt model infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security of employees devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
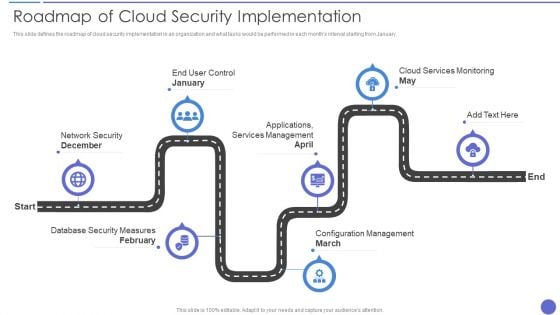
Roadmap Of Cloud Security Implementation Infographics PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Presenting Roadmap Of Cloud Security Implementation Infographics PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Applications Services Management, Cloud Services Monitoring, Network Security December. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Internet Security Framework For Data Security Summary Pdf
This slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete , respond and recover.Showcasing this set of slides titled Internet Security Framework For Data Security Summary Pdf The topics addressed in these templates are Policies And Standard, Data Collection, Establish Firewall All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete , respond and recover.

Top Web Application Security Threats Application Security Testing
This slide discusses the vulnerabilities and security threats in web application such as SQL injection, cross-site scripting, etc. Presenting this PowerPoint presentation, titled Top Web Application Security Threats Application Security Testing, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Top Web Application Security Threats Application Security Testing. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Top Web Application Security Threats Application Security Testing that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide discusses the vulnerabilities and security threats in web application such as SQL injection, cross-site scripting, etc.

Regulations Of Security Tokenization Strategies For Data Security PPT Template
This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc. Find a pre-designed and impeccable Regulations Of Security Tokenization Strategies For Data Security PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc.

Application Security Testing Cloud Native Application Security Overview
The purpose of this slide is to highlight the introduction of second type of web security, that is, cloud native application security. There are so many reasons you need a Application Security Testing Cloud Native Application Security Overview. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The purpose of this slide is to highlight the introduction of second type of web security, that is, cloud native application security.

Best Practices For Implementing Application Security Application Security Testing
This slide discusses the best approaches for application security deployment which include assess threats, shift security left, control rights, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Best Practices For Implementing Application Security Application Security Testing can be your best option for delivering a presentation. Represent everything in detail using Best Practices For Implementing Application Security Application Security Testing and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide discusses the best approaches for application security deployment which include assess threats, shift security left, control rights, etc.
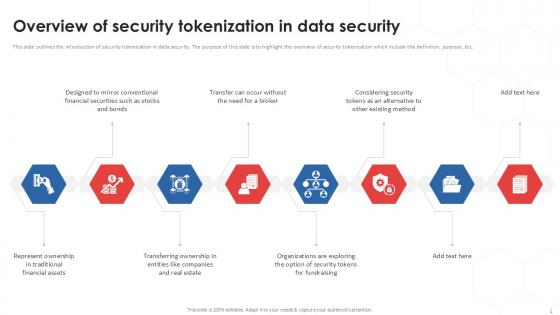
Overview Of Security Tokenization In Data Security PPT Sample
This slide outlines the introduction of security tokenization in data security. The purpose of this slide is to highlight the overview of security tokenization which include the definition, purpose, etc. Boost your pitch with our creative Overview Of Security Tokenization In Data Security PPT Sample. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the introduction of security tokenization in data security. The purpose of this slide is to highlight the overview of security tokenization which include the definition, purpose, etc.

Checklist To Implement Effective Application Security Application Security Testing
This slide showcases the actions performed while deploying application security, person responsible, status and comments for the same. If you are looking for a format to display your unique thoughts, then the professionally designed Checklist To Implement Effective Application Security Application Security Testing is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Checklist To Implement Effective Application Security Application Security Testing and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases the actions performed while deploying application security, person responsible, status and comments for the same.

Introduction Of Application Security For Data Privacy Application Security Testing
This slide discusses the overview of application security which includes its objectives such as protecting data, minimize risk, etc. Explore a selection of the finest Introduction Of Application Security For Data Privacy Application Security Testing here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Introduction Of Application Security For Data Privacy Application Security Testing to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide discusses the overview of application security which includes its objectives such as protecting data, minimize risk, etc.

Internet Security PowerPoint Template 0910
Blue Earth globe and padlock isolated over white background Embrace changes with our Internet Security PowerPoint Template 0910. Develop the correct attitude for it.

Before Vs After Implementation Of Application Security Application Security Testing
This slide showcases the comparative analysis of the before versus after implementation of application security situation of an organization. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Before Vs After Implementation Of Application Security Application Security Testing. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Before Vs After Implementation Of Application Security Application Security Testing today and make your presentation stand out from the rest This slide showcases the comparative analysis of the before versus after implementation of application security situation of an organization.

Security Testing Types Vulnerability Scanning Application Security Testing
This slide outlines the overview of vulnerability scanning in security testing for application security. Do you know about Slidesgeeks Security Testing Types Vulnerability Scanning Application Security Testing These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the overview of vulnerability scanning in security testing for application security.

Security Testing Types Penetration Testing Application Security Testing
This slide discusses the overview of penetration testing for application security which includes the purpose of penetration testing. Take your projects to the next level with our ultimate collection of Security Testing Types Penetration Testing Application Security Testing. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide discusses the overview of penetration testing for application security which includes the purpose of penetration testing.

Budget Allocation For Implementing Application Security Application Security Testing
This slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc. Find highly impressive Budget Allocation For Implementing Application Security Application Security Testing on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Budget Allocation For Implementing Application Security Application Security Testing for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc.

Authentication In Application Security For Data Protection Application Security Testing
This slide discusses about the overview of authentication in application security and the various elements of MFA. Present like a pro with Authentication In Application Security For Data Protection Application Security Testing. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide discusses about the overview of authentication in application security and the various elements of MFA.

Tools For Vulnerability Scanning In Security Testing Application Security Testing
This slide highlights the tools used for vulnerability scanning in security testing in application security which include Acunetix, Akto, etc. Retrieve professionally designed Tools For Vulnerability Scanning In Security Testing Application Security Testing to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide highlights the tools used for vulnerability scanning in security testing in application security which include Acunetix, Akto, etc.
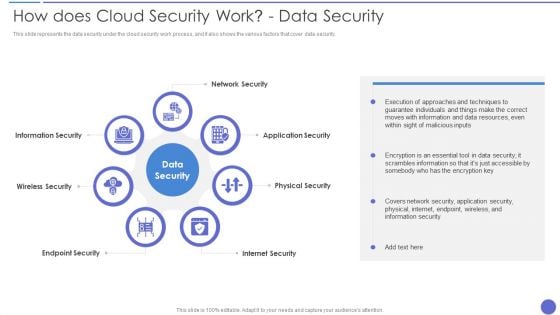
How Does Cloud Security Work Data Security Infographics PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. This is a How Does Cloud Security Work Data Security Infographics PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Application Security, Physical Security, Internet Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
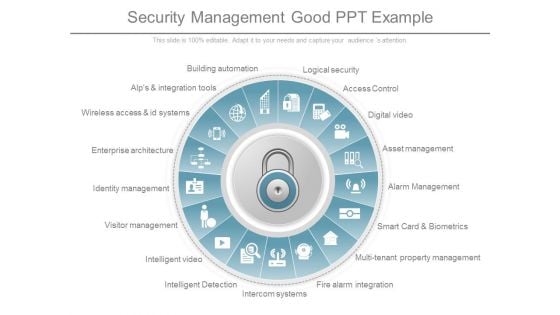
Security Management Good Ppt Example
This is a security management good ppt example. This is a thirteen stage process. The stages in this process are logical security, access control, digital video , asset management, alarm, management, multi tenant property management, fire alarm integration.

Authorization In Application Security For Data Privacy Application Security Testing
This slide discusses the overview of authorization in application security for authorized access of resource. Slidegeeks is here to make your presentations a breeze with Authorization In Application Security For Data Privacy Application Security Testing With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide discusses the overview of authorization in application security for authorized access of resource.

Desktop Security Management Security Of Employees Devices Microsoft PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Deliver an awe inspiring pitch with this creative desktop security management security of employees devices microsoft pdf bundle. Topics like security of employees devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Major Impact Of Application Security On Organization Application Security Testing
This slide showcases the after application security impact on business along with factors that have improved the overall performance. Slidegeeks has constructed Major Impact Of Application Security On Organization Application Security Testing after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases the after application security impact on business along with factors that have improved the overall performance.

Security Log Management Best Practices Application Security Testing
This slide highlights the best approaches of logging implementation which include preventing inappropriate actions, employ logging tools, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Security Log Management Best Practices Application Security Testing to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Security Log Management Best Practices Application Security Testing. This slide highlights the best approaches of logging implementation which include preventing inappropriate actions, employ logging tools, etc.

Top Five Application Security Trends Application Security Testing
This slide showcases the five trends of application security which include, AppSec and CloudSec merge, expanding attack surfaces, etc. Slidegeeks has constructed Top Five Application Security Trends Application Security Testing after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases the five trends of application security which include, AppSec and CloudSec merge, expanding attack surfaces, etc.

Security Testing Types Code Review Application Security Testing
This slide outlines the introduction of secure code review in application security for efficient working of an application. This Security Testing Types Code Review Application Security Testing from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the introduction of secure code review in application security for efficient working of an application.
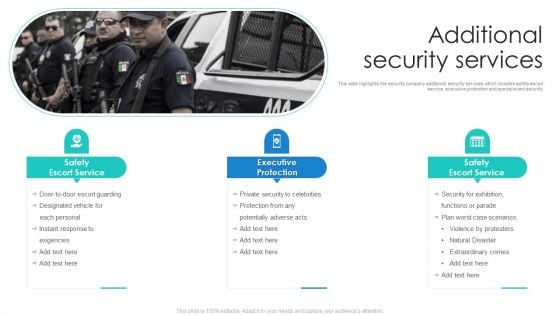
Manpower Corporate Security Business Profile Additional Security Services Formats PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Additional Security Services Formats PDF bundle. Topics like Safety Escort Service, Executive Protection, Safety Escort Service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
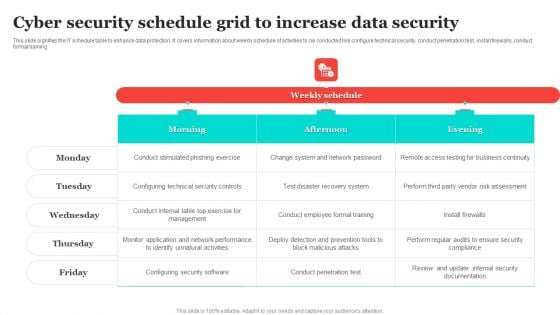
Cyber Security Schedule Grid To Increase Data Security Structure PDF
This slide signifies the IT schedule table to enhance data protection. It covers information about weekly schedule of activities to be conducted like configure technical security, conduct penetration test, install firewalls, conduct formal training. Pitch your topic with ease and precision using this Cyber Security Schedule Grid To Increase Data Security Structure PDF. This layout presents information on Recovery System, Vendor Risk Assessment, Configuring Security Software. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
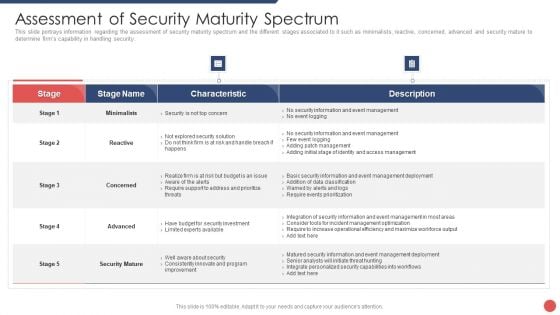
Security Functioning Centre Assessment Of Security Maturity Spectrum Slides PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative security functioning centre assessment of security maturity spectrum slides pdf bundle. Topics like security mature, operational efficiency, security capabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Confidential Files Security Template 1010
illustration of confidential files security in computer generated image Our Confidential Files Security Template 1010 are up for any experiment. They are ready to establish new benchmarks.


 Continue with Email
Continue with Email

 Home
Home


































