Network Security
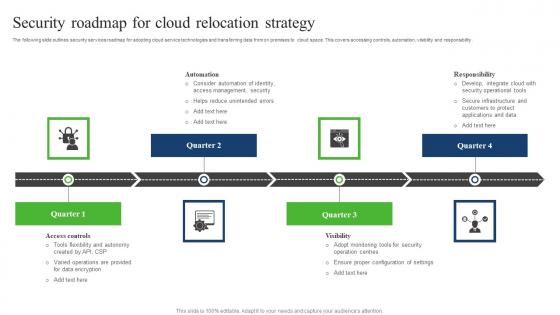
Security Roadmap For Cloud Relocation Strategy Sample Pdf
The following slide outlines security services roadmap for adopting cloud service technologies and transferring data from on premises to cloud space. This covers accessing controls, automation, visibility and responsibility. Showcasing this set of slides titled Security Roadmap For Cloud Relocation Strategy Sample Pdf. The topics addressed in these templates are Responsibility, Automation, Security Roadmap, Cloud Relocation Strategy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide outlines security services roadmap for adopting cloud service technologies and transferring data from on premises to cloud space. This covers accessing controls, automation, visibility and responsibility.
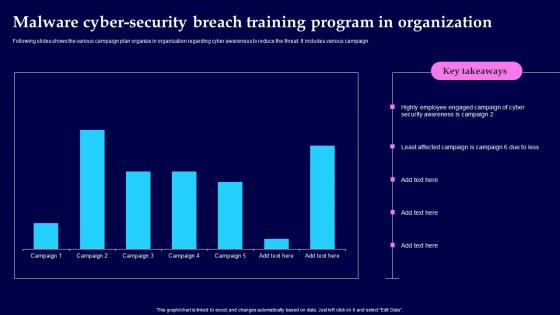
Malware Cyber Security Breach Training Program In Organization Designs Pdf
Following slides shows the various campaign plan organize in organization regarding cyber awareness to reduce the threat. It includes various campaign Pitch your topic with ease and precision using this Malware Cyber Security Breach Training Program In Organization Designs Pdf This layout presents information on Malware Cyber Security Breach, Training Program In Organization It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slides shows the various campaign plan organize in organization regarding cyber awareness to reduce the threat. It includes various campaign
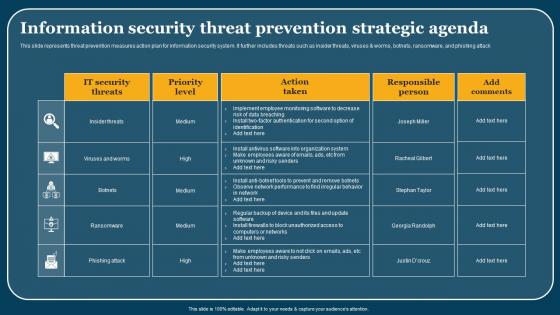
Information Security Threat Prevention Strategic Agenda Introduction Pdf
This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack. Pitch your topic with ease and precision using this Information Security Threat Prevention Strategic Agenda Introduction Pdf. This layout presents information on Security Threats, Priority Level, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack.
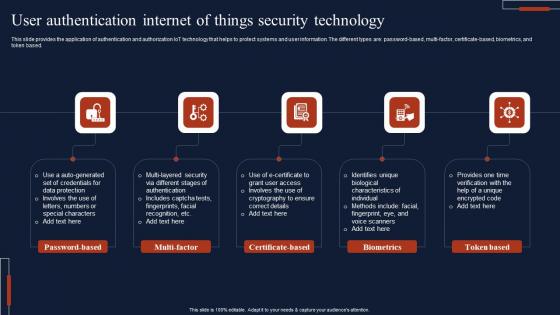
User Authentication Internet Of Things Security Technology Microsoft Pdf
This slide provides the application of authentication and authorization IoT technology that helps to protect systems and user information. The different types are password based, multi-factor, certificate-based, biometrics, and token based. Pitch your topic with ease and precision using this User Authentication Internet Of Things Security Technology Microsoft Pdf This layout presents information on Password Based, Multi Factor, Certificate Based It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide provides the application of authentication and authorization IoT technology that helps to protect systems and user information. The different types are password based, multi-factor, certificate-based, biometrics, and token based.

It Security Training Courses Strategic Agenda To Employees Portrait Pdf
This slide represents action plan for various training courses. It includes training courses such as complete cyber security courses, etc and their description, mode, duration, and budget. Showcasing this set of slides titled It Security Training Courses Strategic Agenda To Employees Portrait Pdf. The topics addressed in these templates are Training Courses, Description, Trainer Name. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan for various training courses. It includes training courses such as complete cyber security courses, etc and their description, mode, duration, and budget.
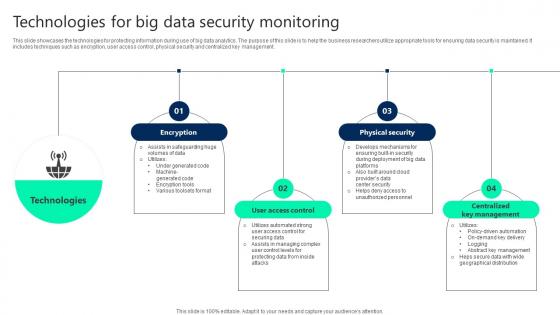
Technologies For Big Data Security Monitoring Summary pdf
This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management. Showcasing this set of slides titled Technologies For Big Data Security Monitoring Summary pdf. The topics addressed in these templates are User Access Control, Physical Security, Centralized Key Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management.
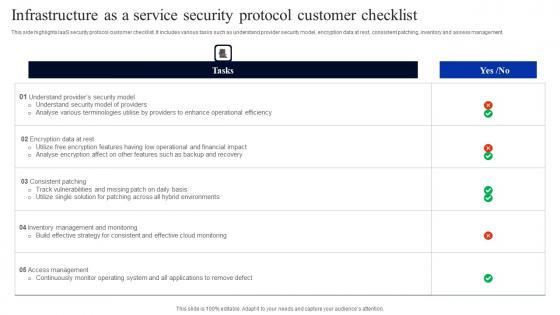
Infrastructure As A Service Security Protocol Customer Checklist Elements Pdf
This side highlights IaaS security protocol customer checklist. It includes various tasks such as understand provider security model, encryption data at rest, consistent patching, inventory and assess management. Showcasing this set of slides titled Infrastructure As A Service Security Protocol Customer Checklist Elements Pdf. The topics addressed in these templates are Encryption Data Rest, Consistent Patching, Inventory Assess Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This side highlights IaaS security protocol customer checklist. It includes various tasks such as understand provider security model, encryption data at rest, consistent patching, inventory and assess management.
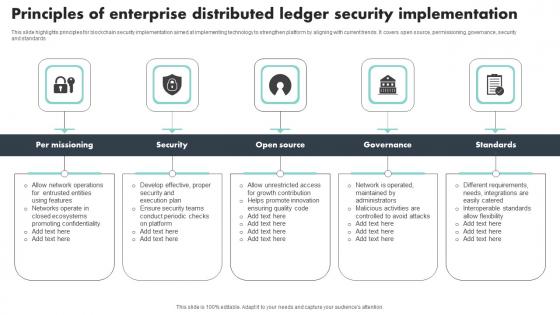
Principles Of Enterprise Distributed Ledger Security Implementation Brochure Pdf
This slide highlights principles for blockchain security implementation aimed at implementing technology to strengthen platform by aligning with current trends. It covers open source, permissioning, governance, security and standards Pitch your topic with ease and precision using this Principles Of Enterprise Distributed Ledger Security Implementation Brochure Pdf This layout presents information on Per Missioning, Security, Governance, Standards It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights principles for blockchain security implementation aimed at implementing technology to strengthen platform by aligning with current trends. It covers open source, permissioning, governance, security and standards
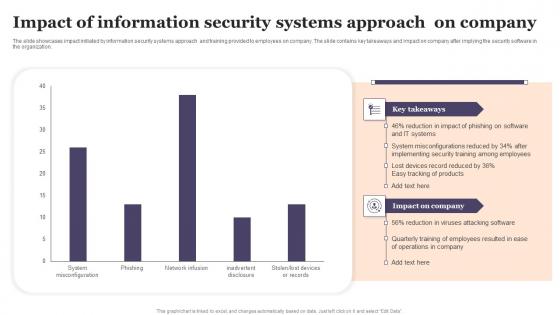
Impact Of Information Security Systems Approach On Company Designs Pdf
The slide showcases impact initiated by information security systems approach and training provided to employees on company. The slide contains key takeaways and impact on company after implying the security software in the organization. Showcasing this set of slides titled Impact Of Information Security Systems Approach On Company Designs Pdf The topics addressed in these templates are Impact Of Information, Security Systems, Approach On Company All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide showcases impact initiated by information security systems approach and training provided to employees on company. The slide contains key takeaways and impact on company after implying the security software in the organization.

Data Encryption Features In Application Security Testing Ppt Powerpoint Portrait
This slide outlines the characteristics of encryption in application security such as security, easy-to-use, document support, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Encryption Features In Application Security Testing Ppt Powerpoint Portrait was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Encryption Features In Application Security Testing Ppt Powerpoint Portrait This slide outlines the characteristics of encryption in application security such as security, easy-to-use, document support, etc.
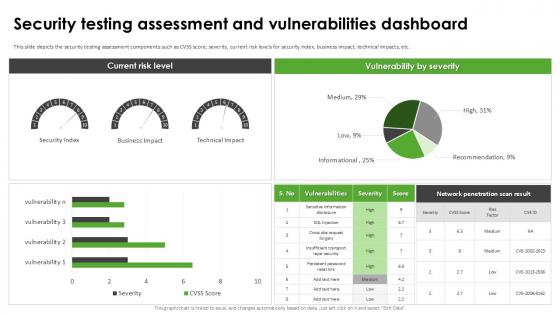
Security Testing Assessment Harnessing The World Of Ethical Ppt Example
This slide depicts the security testing assessment components such as CVSS score, severity, current risk levels for security index, business impact, technical impacts, etc. This Security Testing Assessment Harnessing The World Of Ethical Ppt Example is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Security Testing Assessment Harnessing The World Of Ethical Ppt Example features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts the security testing assessment components such as CVSS score, severity, current risk levels for security index, business impact, technical impacts, etc.

Internet Security Management In Powerpoint And Google Slides Cpb
Introducing our well designed Internet Security Management In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Internet Security Management. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Internet Security Management In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
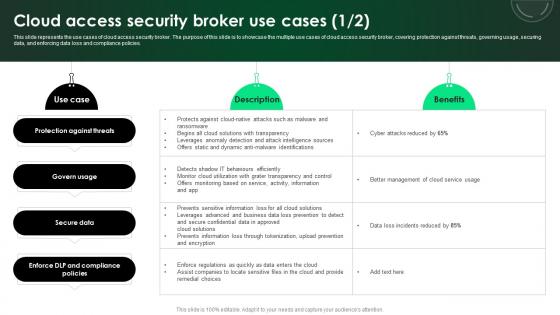
CASB 2 0 IT Cloud Access Security Broker Use Cases
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Presenting this PowerPoint presentation, titled CASB 2 0 IT Cloud Access Security Broker Use Cases, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CASB 2 0 IT Cloud Access Security Broker Use Cases. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CASB 2 0 IT Cloud Access Security Broker Use Cases that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies.
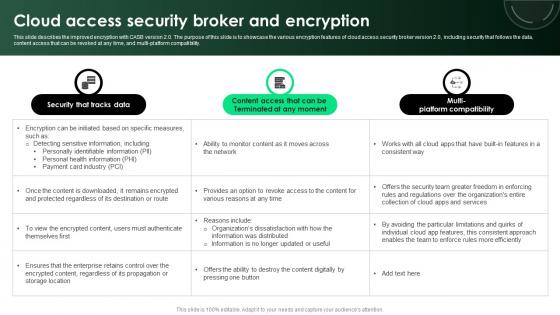
CASB 2 0 IT Cloud Access Security Broker And Encryption
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Make sure to capture your audiences attention in your business displays with our gratis customizable CASB 2 0 IT Cloud Access Security Broker And Encryption. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility.

CASB 2 0 IT Emerging Cloud Security Risks And Threats
This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Boost your pitch with our creative CASB 2 0 IT Emerging Cloud Security Risks And Threats. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on.
Data Security Strategic Agenda Checklist Icon Mockup Pdf
Pitch your topic with ease and precision using this Data Security Strategic Agenda Checklist Icon Mockup Pdf. This layout presents information on Data Security Strategic, Agenda Checklist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Data Security Strategic Agenda Checklist Icon Mockup Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
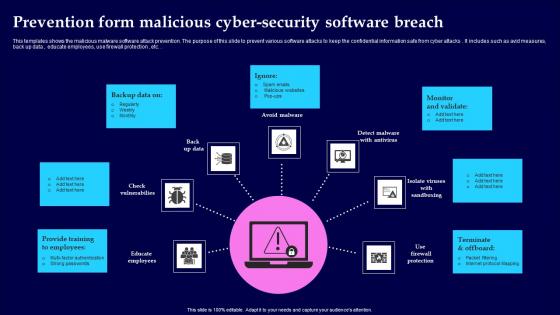
Prevention Form Malicious Cyber Security Software Breach Portrait Pdf
This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc. Showcasing this set of slides titled Prevention Form Malicious Cyber Security Software Breach Portrait Pdf The topics addressed in these templates are Provide Training, Monitor And Validate, Terminate And Offboard All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc.
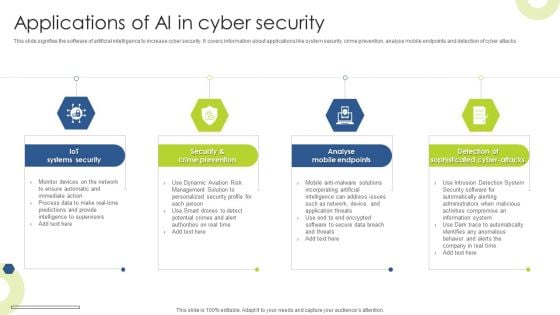
Applications Of AI In Cyber Security Infographics PDF
This slide signifies the software of artificial intelligence to increase cyber security. It covers information about applications like system security, crime prevention, analyse mobile endpoints and detection of cyber attacks Presenting Applications Of AI In Cyber Security Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Iot Systems Security, Crime Prevention, Analyse Mobile Endpoints. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
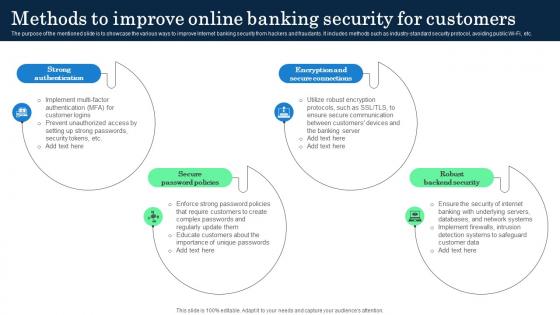
Methods To Improve Online Banking Security Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc. Do you know about Slidesgeeks Methods To Improve Online Banking Security Incorporating Banking Operational Growth These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc.

CASB 2 0 IT Cloud Security Standards And Control Frameworks
This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. This CASB 2 0 IT Cloud Security Standards And Control Frameworks from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA.

Overview Flow Chart Of Cyber Security Breach Summary Pdf
This templates shows the schematic illustration of a malware attack. The purpose of this slide to elaborate through various phases attack get implemented by attacker . The process starts withs cyber attackers send spam emails and various commands which ends with stealing data with devices Pitch your topic with ease and precision using this Overview Flow Chart Of Cyber Security Breach Summary Pdf This layout presents information on Email Delivered, Sending Commands, Injected Into It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the schematic illustration of a malware attack. The purpose of this slide to elaborate through various phases attack get implemented by attacker . The process starts withs cyber attackers send spam emails and various commands which ends with stealing data with devices
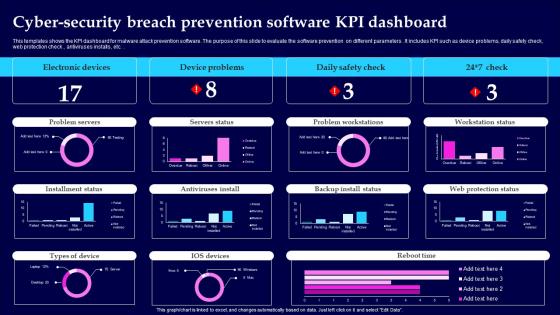
Cyber Security Breach Prevention Software KPI Dashboard Information Pdf
This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc. Showcasing this set of slides titled Cyber Security Breach Prevention Software KPI Dashboard Information Pdf The topics addressed in these templates are Electronic Devices, Device Problems, Daily Safety Check All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc.
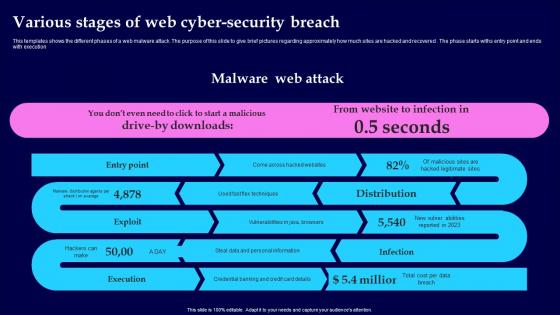
Various Stages Of Web Cyber Security Breach Introduction Pdf
This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution Pitch your topic with ease and precision using this Various Stages Of Web Cyber Security Breach Introduction Pdf This layout presents information on Malware Web Attack, Various Stages, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution

Laptop With Lock Information Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Laptop With Lock Information Security PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides are focused like a searchlight beam. They highlight your ideas for your target audience. Use our Technology PowerPoint Templates because You can Score a slam dunk with our PowerPoint Templates and Slides. Watch your audience hang onto your every word. Download our Security PowerPoint Templates because It can Leverage your style with our PowerPoint Templates and Slides. Charm your audience with your ability. Use our Network Diagrams PowerPoint Templates because It can Conjure up grand ideas with our magical PowerPoint Templates and Slides. Leave everyone awestruck by the end of your presentation. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime.Use these PowerPoint slides for presentations relating to 3d illustration of laptop with lock, business, computer, security, network diagrams, technology . The prominent colors used in the PowerPoint template are Blue, Gray, Yellow. Your career will soar away. Our Laptop With Lock Information Security PowerPoint Templates Ppt Backgrounds For Slides 0213 will give it wings.

Cyber Security Breach Ppt Powerpoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Cyber Security Breach Ppt Powerpoint Presentation Complete Deck With Slides Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twenty this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now. Our Cyber Security Breach Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
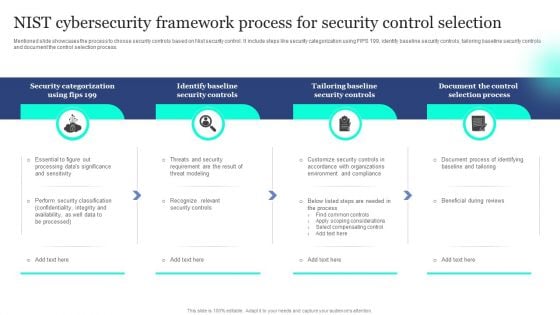
NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF
Mentioned slide showcases the process to choose security controls based on Nist security control. It include steps like security categorization using FIPS 199, identify baseline security controls, tailoring baseline security controls and document the control selection process. Presenting NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Controls, Tailoring Baseline, Selection Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Laptop With Security Key Savings PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Laptop With Security Key Savings PowerPoint Templates PPT Backgrounds For Slides 0213.Download our Computer PowerPoint Templates because You can Channelise the thoughts of your team with our PowerPoint Templates and Slides. Urge them to focus on the goals you have set. Download our Technology PowerPoint Templates because It will let you Set new benchmarks with our PowerPoint Templates and Slides. They will keep your prospects well above par. Download our Security PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges. Download and present our Network Diagrams PowerPoint Templates because You can safely bank on our PowerPoint Templates and Slides. They will provide a growth factor to your valuable thoughts. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are created with admirable insight. Use them and give your group a sense of your logical mind.Use these PowerPoint slides for presentations relating to Key and a Laptop, business, computer, security, network diagrams, technology . The prominent colors used in the PowerPoint template are Blue, Gray, Red. Improve your organization with our Laptop With Security Key Savings PowerPoint Templates Ppt Backgrounds For Slides 0213. Download without worries with our money back guaranteee.
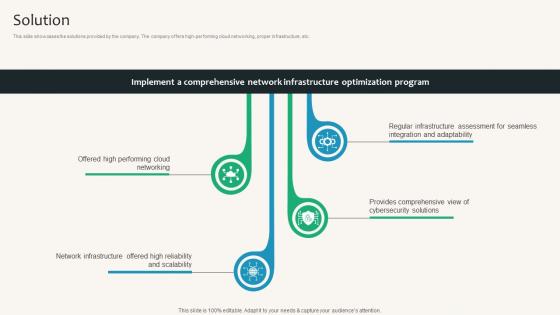
Solution Security Service Provider Business Model BMC SS V
This slide showcases the solutions provided by the company. The company offers high-performing cloud networking, proper infrastructure, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Security Service Provider Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases the solutions provided by the company. The company offers high-performing cloud networking, proper infrastructure, etc.
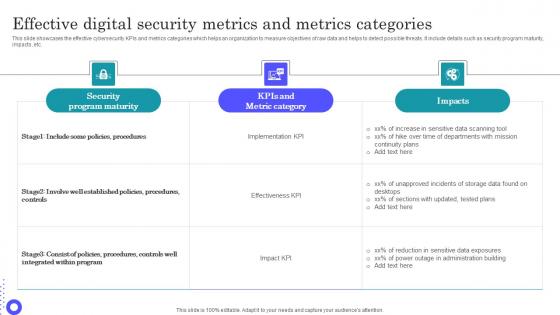
Effective Digital Security Metrics And Metrics Categories Microsoft Pdf
Pitch your topic with ease and precision using this Effective Digital Security Metrics And Metrics Categories Microsoft Pdf This layout presents information on Security Program Maturity, Metric Category, Sensitive Data Scanning It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the effective cybersecurity KPIs and metrics categories which helps an organization to measure objectives of raw data and helps to detect possible threats. It include details such as security program maturity, impacts, etc.
Cyber Security Milestones In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Cyber Security Milestones In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Cyber Security Milestones that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Cyber Security Milestones In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cloud Computing Engineering Data Security Service Icon Portrait Pdf
Showcasing this set of slides titled Cloud Computing Engineering Data Security Service Icon Portrait Pdf The topics addressed in these templates are Cloud Computing, Engineering Data Security, Service Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Cloud Computing Engineering Data Security Service Icon Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Business Ppt PowerPoint Presentation Inspiration Example Introduction Cpb
This is a cyber security business ppt powerpoint presentation inspiration example introduction cpb. This is a two stage process. The stages in this process are cyber security business.
Cyber Security Solutions Ppt PowerPoint Presentation Layouts Icon Cpb
This is a cyber security solutions ppt powerpoint presentation layouts icon cpb. This is a six stage process. The stages in this process are cyber security solutions.

Cyber Security Relationship Ppt PowerPoint Presentation Layouts Designs Download Cpb
This is a cyber security relationship ppt powerpoint presentation layouts designs download cpb. This is a four stage process. The stages in this process are cyber security relationship.
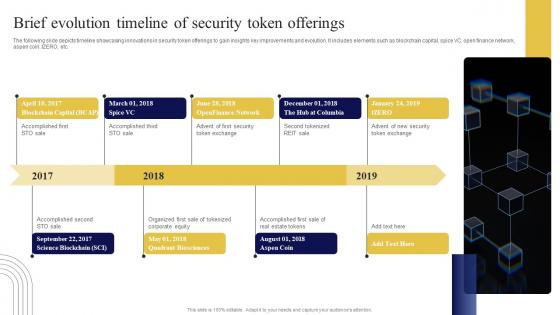
Brief Evolution Timeline Of Security Exploring Investment Opportunities Portrait Pdf
The following slide depicts timeline showcasing innovations in security token offerings to gain insights key improvements and evolution. It includes elements such as blockchain capital, spice VC, open finance network, aspen coin, tZERO, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Brief Evolution Timeline Of Security Exploring Investment Opportunities Portrait Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Brief Evolution Timeline Of Security Exploring Investment Opportunities Portrait Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide depicts timeline showcasing innovations in security token offerings to gain insights key improvements and evolution. It includes elements such as blockchain capital, spice VC, open finance network, aspen coin, tZERO, etc.
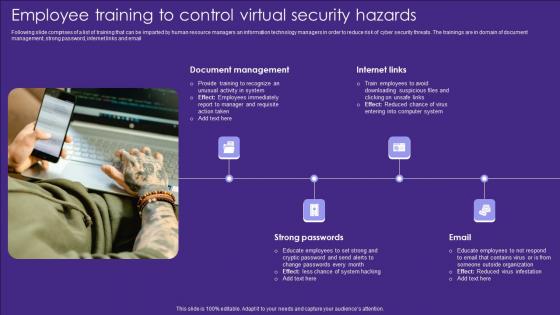
Employee Training To Control Virtual Security Hazards Designs Pdf
Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email Pitch your topic with ease and precision using this Employee Training To Control Virtual Security Hazards Designs Pdf. This layout presents information on Internet Links, Email, Strong Passwords. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email
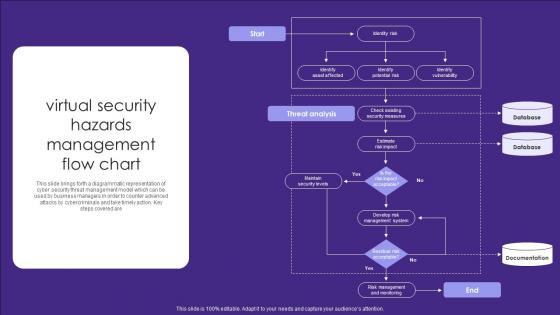
Virtual Security Hazards Management Flow Chart Infographics Pdf
This slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are Showcasing this set of slides titled Virtual Security Hazards Management Flow Chart Infographics Pdf. The topics addressed in these templates are Security Measures, Database, Documentation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are
Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf
Pitch your topic with ease and precision using this Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf This layout presents information on Digital Security, Metrics Icon, Showcasing Threat Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Complete Guide To Launch Website Security Management Strategic Plan
Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Slidegeeks has constructed Complete Guide To Launch Website Security Management Strategic Plan after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc.
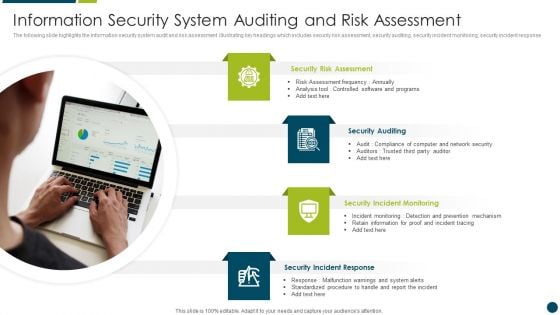
Information Security System Auditing And Risk Assessment Elements PDF
The following slide highlights the information security system audit and risk assessment illustrating key headings which includes security risk assessment, security auditing, security incident monitoring, security incident response Persuade your audience using this Information Security System Auditing And Risk Assessment Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Risk Assessment, Security Auditing, Security Incident Monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Smart Phone Security Key Aspects For Growing Revenue Icons PDF
This slide shows every aspect of phone security model that should be considered while framing security policy for organization. It include aspects such as compliance security, product security and infrastructure security etc. Presenting Smart Phone Security Key Aspects For Growing Revenue Icons PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Compliance Security, Product Security, Infrastructure Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Main Goals Of Application Level Encryption Application Security Testing
This slide showcases the objectives of application-level encryption in application security which include data protection, increased security, etc. Retrieve professionally designed Main Goals Of Application Level Encryption Application Security Testing to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide showcases the objectives of application-level encryption in application security which include data protection, increased security, etc.
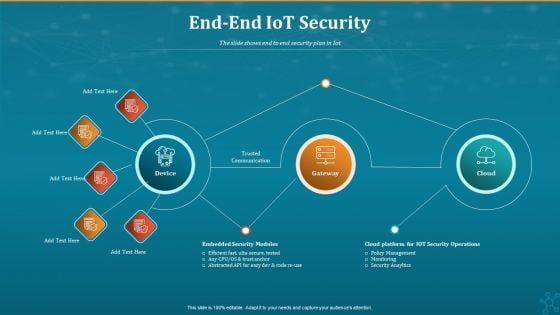
Machine To Machine Communication End End Iot Security Inspiration PDF
The slide shows end to end security plan in Iot.Deliver an awe-inspiring pitch with this creative machine to machine communication end end iot security inspiration pdf. bundle. Topics like trusted communication, gateway, embedded security modules, cloud platform for iot security operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Unauthorized Computer Access Icon Causing Virtual Security Hazards Guidelines Pdf
Showcasing this set of slides titled Unauthorized Computer Access Icon Causing Virtual Security Hazards Guidelines Pdf. The topics addressed in these templates are Unauthorized Computer, Access, Causing Virtual Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Unauthorized Computer Access Icon Causing Virtual Security Hazards Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Teamwork Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Teamwork Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Teamwork Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Teamwork Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Endpoint Security Checklist In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Endpoint Security Checklist In Powerpoint And Google Slides Cpb This completely editable PowerPoint graphic exhibits Endpoint Security Checklist that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Endpoint Security Checklist In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
National Security Budget In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled National Security Budget In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits National Security Budget that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our National Security Budget In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
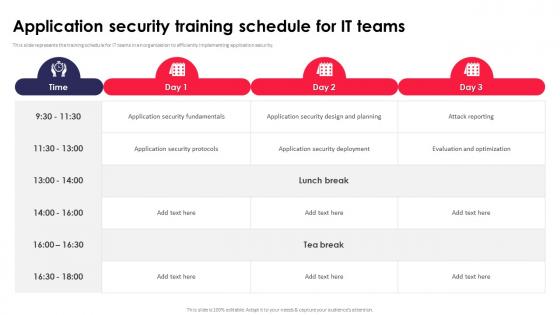
Application Security Training Schedule For IT Teams Ppt Powerpoint Portrait
This slide represents the training schedule for IT teams in an organization to efficiently implementing application security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Application Security Training Schedule For IT Teams Ppt Powerpoint Portrait will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the training schedule for IT teams in an organization to efficiently implementing application security.

Concerns And Solution For Application Security Testing Ppt Powerpoint Infographics
This slide outlines the problems and relevant solutions of application security deployment to ensure smooth functioning. Make sure to capture your audiences attention in your business displays with our gratis customizable Concerns And Solution For Application Security Testing Ppt Powerpoint Infographics. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the problems and relevant solutions of application security deployment to ensure smooth functioning.
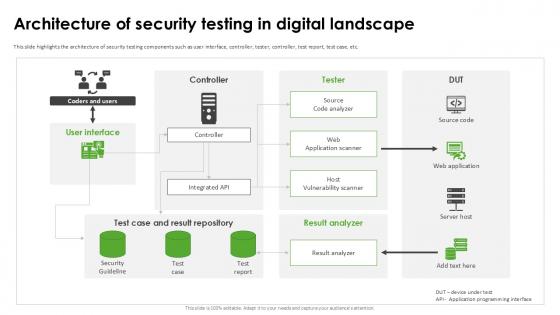
Architecture Of Security Harnessing The World Of Ethical Ppt Template
This slide highlights the architecture of security testing components such as user interface, controller, tester, controller, test report, test case, etc. There are so many reasons you need a Architecture Of Security Harnessing The World Of Ethical Ppt Template The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide highlights the architecture of security testing components such as user interface, controller, tester, controller, test report, test case, etc.

Cyber Deals Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Cyber Deals Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Deals Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cyber Deals Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
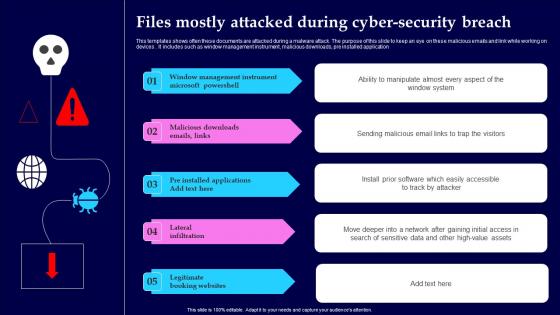
Files Mostly Attacked During Cyber Security Breach Structure Pdf
This templates shows often these documents are attacked during a malware attack. The purpose of this slide to keep an eye on these malicious emails and link while working on devices. It includes such as window management instrument, malicious downloads, pre installed application Showcasing this set of slides titled Files Mostly Attacked During Cyber Security Breach Structure Pdf The topics addressed in these templates are Window Management, Instrument Microsoft, Lateral Infiltration All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows often these documents are attacked during a malware attack. The purpose of this slide to keep an eye on these malicious emails and link while working on devices. It includes such as window management instrument, malicious downloads, pre installed application
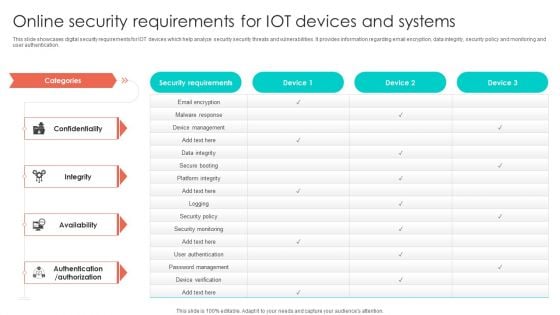
Online Security Requirements For Iot Devices And Systems Graphics PDF
This slide showcases digital security requirements for IOT devices which help analyze security security threats and vulnerabilities. It provides information regarding email encryption, data integrity, security policy and monitoring and user authentication. Pitch your topic with ease and precision using this Online Security Requirements For Iot Devices And Systems Graphics PDF. This layout presents information on Device Management, Security Policy, Security Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
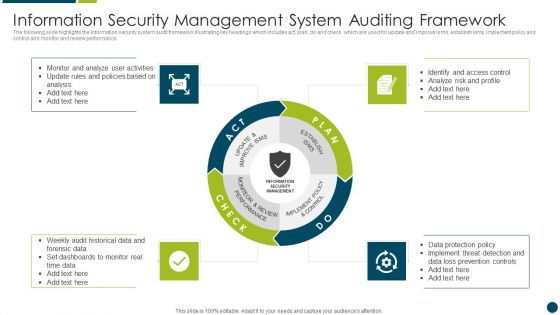
Information Security Management System Auditing Framework Microsoft PDF
The following slide highlights the information security management system audit checklist illustrating matrix consisting of domain, objective, description, identification and audit for information security policies, information security organization and human resource security Showcasing this set of slides titled Information Security Management System Auditing Framework Microsoft PDF. The topics addressed in these templates are Information Security Organization, Information Security Policies, Human Resource Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting
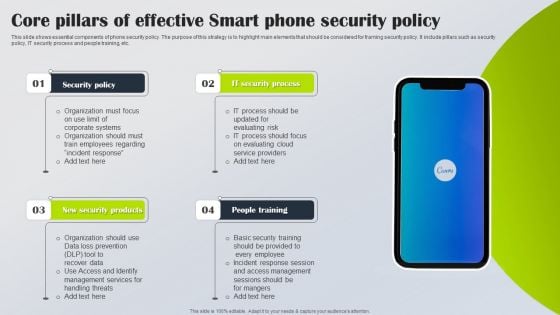
Core Pillars Of Effective Smart Phone Security Policy Slides PDF
This slide shows essential components of phone security policy. The purpose of this strategy is to highlight main elements that should be considered for framing security policy. It include pillars such as security policy, IT security process and people training, etc. Persuade your audience using this Core Pillars Of Effective Smart Phone Security Policy Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Policy, IT Security Process, New Security Products. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
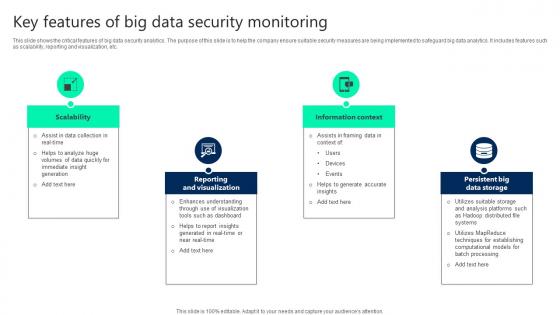
Key Features Of Big Data Security Monitoring Ideas pdf
This slide shows the critical features of big data security analytics. The purpose of this slide is to help the company ensure suitable security measures are being implemented to safeguard big data analytics. It includes features such as scalability, reporting and visualization, etc. Pitch your topic with ease and precision using this Key Features Of Big Data Security Monitoring Ideas pdf. This layout presents information on Scalability, Reporting And Visualization, Information Context. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows the critical features of big data security analytics. The purpose of this slide is to help the company ensure suitable security measures are being implemented to safeguard big data analytics. It includes features such as scalability, reporting and visualization, etc.

Information Security Program Strategic Agenda Process Microsoft Pdf
This slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc. Showcasing this set of slides titled Information Security Program Strategic Agenda Process Microsoft Pdf. The topics addressed in these templates are Assets And Inventory, Evaluate Risk, Manage Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc.

Overview Of Platform Tokenization In Data Security PPT Sample
This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc. Find a pre-designed and impeccable Overview Of Platform Tokenization In Data Security PPT Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc.
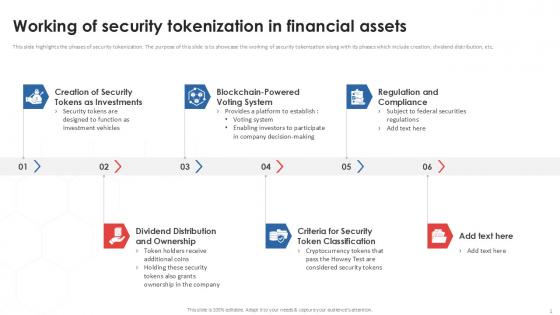
Working Of Security Tokenization In Financial Assets PPT Powerpoint
This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc. Find a pre-designed and impeccable Working Of Security Tokenization In Financial Assets PPT Powerpoint. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc.
Data Breach Security Communication Plan Icon Demonstration Pdf
Showcasing this set of slides titled Data Breach Security Communication Plan Icon Demonstration Pdf The topics addressed in these templates are Data Breach, Security Communication, Plan Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Data Breach Security Communication Plan Icon Demonstration Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































