Network Security
Security Incident Response Communication Plan Icon Professional Pdf
Showcasing this set of slides titled Security Incident Response Communication Plan Icon Professional Pdf The topics addressed in these templates are Security Incident, Response Communication, Plan Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Security Incident Response Communication Plan Icon Professional Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Strategic Agenda For Hotels Icon Professional Pdf
Showcasing this set of slides titled Security Strategic Agenda For Hotels Icon Professional Pdf. The topics addressed in these templates are Security Strategic, Agenda For Hotels. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Security Strategic Agenda For Hotels Icon Professional Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
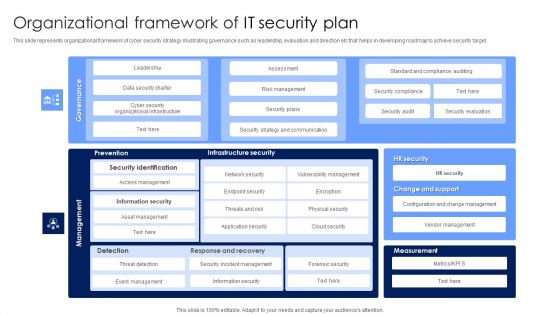
Organizational Framework Of IT Security Plan Microsoft PDF
This slide represents organizational framework of cyber security strategy illustrating governance such as leadership, evaluation and direction etc that helps in developing roadmap to achieve security target. Showcasing this set of slides titled Organizational Framework Of IT Security Plan Microsoft PDF. The topics addressed in these templates are Infrastructure Security, Management, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
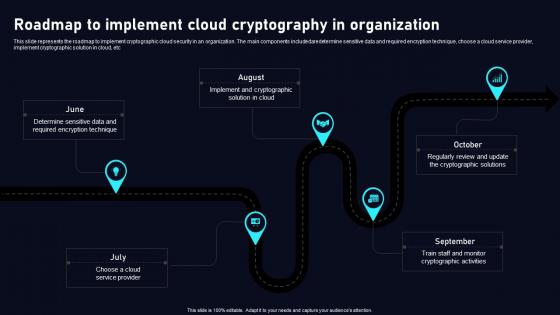
Roadmap To Implement Cloud Data Security Using Cryptography Information Pdf
This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components includedaredetermine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Roadmap To Implement Cloud Data Security Using Cryptography Information Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Roadmap To Implement Cloud Data Security Using Cryptography Information Pdf today and make your presentation stand out from the rest This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components includedaredetermine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc

Application Security Testing Tools Reference Model Ppt Powerpoint Ideas
This slide showcases the application security testing tools reference model along with the workflow. Get a simple yet stunning designed Application Security Testing Tools Reference Model Ppt Powerpoint Ideas. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Application Security Testing Tools Reference Model Ppt Powerpoint Ideas can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases the application security testing tools reference model along with the workflow.
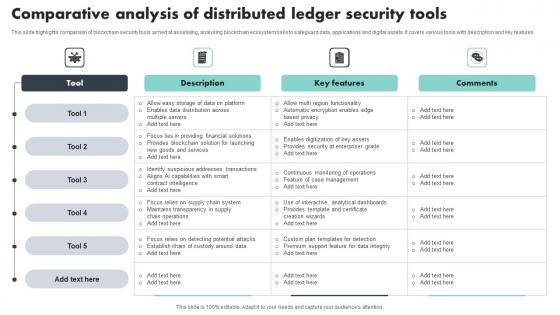
Comparative Analysis Of Distributed Ledger Security Tools Sample Pdf
This slide highlights comparison of blockchain security tools aimed at assessing, analysing blockchain ecosystem risks to safeguard data, applications and digital assets. It covers various tools with description and key features Showcasing this set of slides titled Comparative Analysis Of Distributed Ledger Security Tools Sample Pdf The topics addressed in these templates are Key Features, Comparative Analysis, Security Tools All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights comparison of blockchain security tools aimed at assessing, analysing blockchain ecosystem risks to safeguard data, applications and digital assets. It covers various tools with description and key features

Application Security Testing Tool Pyramid Ppt Powerpoint Download
This slide represents the application security testing tool pyramid which includes tools such as correlation tools, test coverage analysis, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Application Security Testing Tool Pyramid Ppt Powerpoint Download a try. Our experts have put a lot of knowledge and effort into creating this impeccable Application Security Testing Tool Pyramid Ppt Powerpoint Download. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the application security testing tool pyramid which includes tools such as correlation tools, test coverage analysis, etc.
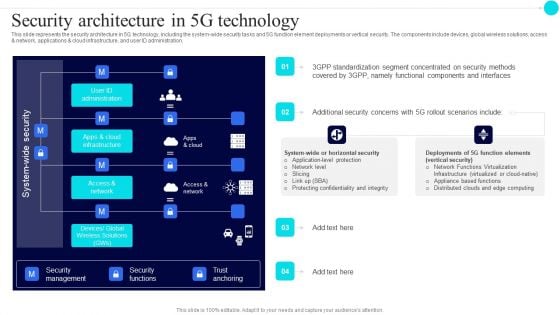
Security Architecture In 5G Technology 5G Functional Architecture Topics PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration.Deliver an awe inspiring pitch with this creative Security Architecture In 5G Technology 5G Functional Architecture Topics PDF bundle. Topics like Standardization Segment, Concentrated Security, Components Interfaces can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slide For Zero Trust Security Template Pdf
Introducing our well designed Icons Slide For Zero Trust Security Template Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Zero Trust Security Template Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icons Slide For Cloud Data Security Using Cryptography Diagrams Pdf
Introducing our well designed Icons Slide For Cloud Data Security Using Cryptography Diagrams Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Cloud Data Security Using Cryptography Diagrams Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icons Slide For Tokenization Strategies For Data Security PPT Presentation
Introducing our well designed Icons Slide For Tokenization Strategies For Data Security PPT Presentation set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Tokenization Strategies For Data Security PPT Presentation are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
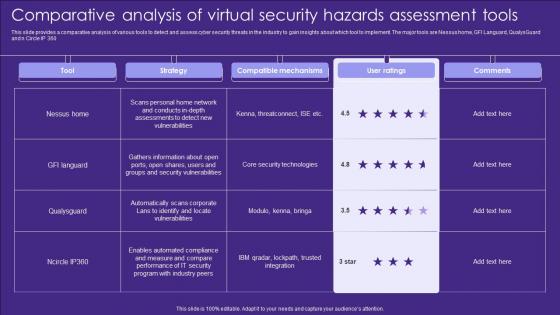
Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf
This slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360 Pitch your topic with ease and precision using this Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf. This layout presents information on Strategy, Compatible Mechanisms, Ratings. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360
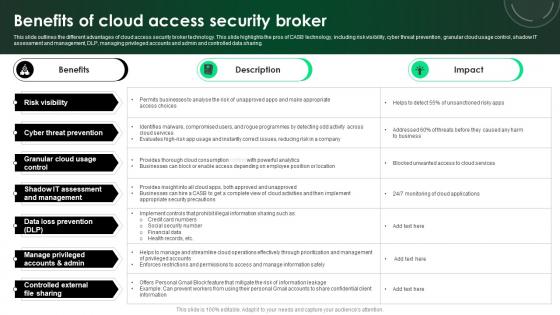
CASB 2 0 IT Benefits Of Cloud Access Security Broker
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. There are so many reasons you need a CASB 2 0 IT Benefits Of Cloud Access Security Broker. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing.
Cybersecurity Security Incident Investigation In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Cybersecurity Security Incident Investigation In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Cybersecurity Security Incident Investigation that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Cybersecurity Security Incident Investigation In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
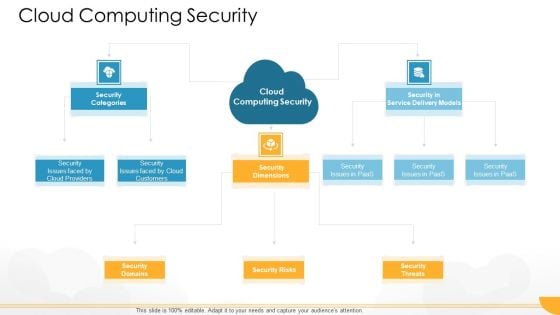
Technology Guide For Serverless Computing Cloud Computing Security Designs PDF
Presenting technology guide for serverless computing cloud computing security designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security categories, security domains, security risks, security threats, security dimensions. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
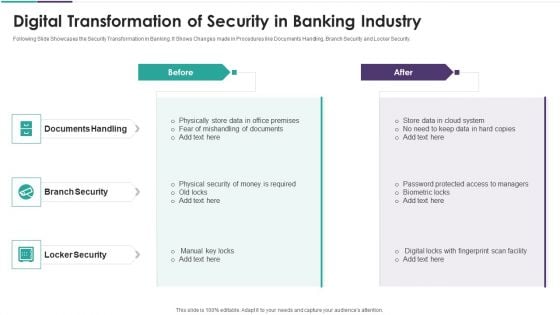
Digital Transformation Of Security In Banking Industry Elements PDF
Following Slide Showcases the Security Transformation in Banking. It Shows Changes made in Procedures like Documents Handling, Branch Security and Locker Security. Presenting digital transformation of security in banking industry elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including documents handling, branch security, locker security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Access Control Safeguards In Application Security Testing Ppt Powerpoint Download
This slide highlights the introduction of access control safeguards in application security for preventing malicious attacks in applications. Boost your pitch with our creative Access Control Safeguards In Application Security Testing Ppt Powerpoint Download. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the introduction of access control safeguards in application security for preventing malicious attacks in applications.

RPA Security Framework In Powerpoint And Google Slides Cpb
Introducing our well designed RPA Security Framework In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like RPA Security Framework. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our RPA Security Framework In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Security Knowledge Framework In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Knowledge Framework In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Knowledge Framework that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Knowledge Framework In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
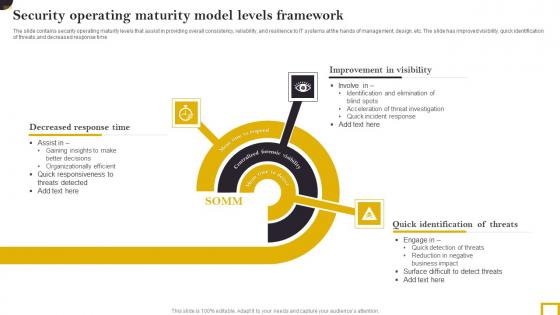
Security Operating Maturity Model Levels Framework Elements Pdf
The slide contains security operating maturity levels that assist in providing overall consistency, reliability, and resilience to IT systems at the hands of management, design, etc. The slide has improved visibility, quick identification of threats,and decreased response time. Pitch your topic with ease and precision using this Security Operating Maturity Model Levels Framework Elements Pdf. This layout presents information on Decreased Response Time,Improvement Visibility, Quick Identification Threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide contains security operating maturity levels that assist in providing overall consistency, reliability, and resilience to IT systems at the hands of management, design, etc. The slide has improved visibility, quick identification of threats,and decreased response time.

CASB 2 0 IT Cloud Access Security Broker Pillar Overview
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Are you searching for a CASB 2 0 IT Cloud Access Security Broker Pillar Overview that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CASB 2 0 IT Cloud Access Security Broker Pillar Overview from Slidegeeks today. This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security.
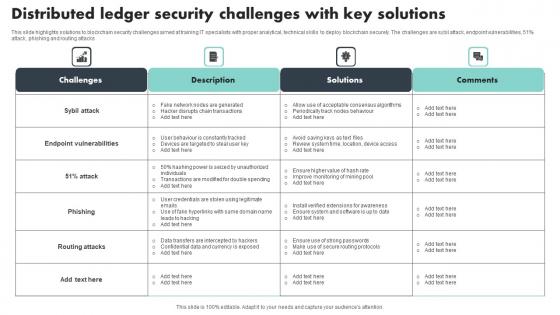
Distributed Ledger Security Challenges With Key Solutions Introduction Pdf
This slide highlights solutions to blockchain security challenges aimed at training IT specialists with proper analytical, technical skills to deploy blockchain securely. The challenges are sybil attack, endpoint vulnerabilities, 51percent attack, phishing and routing attacks Showcasing this set of slides titled Distributed Ledger Security Challenges With Key Solutions Introduction Pdf The topics addressed in these templates are Endpoint Vulnerabilities, Routing Attacks, Phishing All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights solutions to blockchain security challenges aimed at training IT specialists with proper analytical, technical skills to deploy blockchain securely. The challenges are sybil attack, endpoint vulnerabilities, 51 percent attack, phishing and routing attacks

Web Consulting Business Website Security Management Action Plan
Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc. The Web Consulting Business Website Security Management Action Plan is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc.

Managing Technical And Non Website Security Management Action Plan
Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc. Welcome to our selection of the Managing Technical And Non Website Security Management Action Plan. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc.

Comprehensive Guide For Website Website Security Management Action Plan
Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc. Welcome to our selection of the Comprehensive Guide For Website Website Security Management Action Plan. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc.
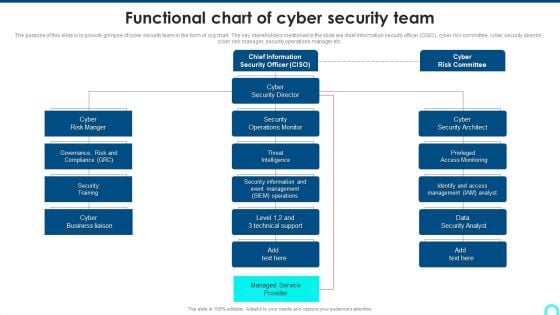
Functional Chart Of Cyber Security Team Diagrams PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc.Deliver an awe inspiring pitch with this creative Functional Chart Of Cyber Security Team Diagrams PDF bundle. Topics like Access Monitoring, Security Architect, Security Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Systems Trendy Business Ppt PowerPoint Presentation Gallery Objects
This is a security systems trendy business ppt powerpoint presentation gallery objects. This is a six stage process. The stages in this process are security systems, trendy business.
Private Security Organizational Structure Ppt PowerPoint Presentation Inspiration Pictures
This is a private security organizational structure ppt powerpoint presentation inspiration pictures. This is a five stage process. The stages in this process are private security organizational structure.
Information Security Tool Ppt PowerPoint Presentation Summary Portrait Cpb
This is a information security tool ppt powerpoint presentation summary portrait cpb. This is a three stage process. The stages in this process are information security tool.
Security Growth Ppt Powerpoint Presentation Show Infographic Template Cpb
This is a security growth ppt powerpoint presentation show infographic template cpb. This is a six stage process. The stages in this process are security growth.

Enterprise Security Tools Ppt PowerPoint Presentation Infographics Skills Cpb
This is a enterprise security tools ppt powerpoint presentation infographics skills cpb. This is a four stage process. The stages in this process are enterprise security tools.
Security Workforce Ppt PowerPoint Presentation Infographics Format Ideas Cpb
This is a security workforce ppt powerpoint presentation infographics format ideas cpb. This is a five stage process. The stages in this process are security workforce.
Types Data Security Ppt PowerPoint Presentation Styles Objects Cpb
This is a types data security ppt powerpoint presentation styles objects cpb. This is a ten stage process. The stages in this process are types data security.
Online Security Ppt PowerPoint Presentation Pictures Layout Ideas Cpb
This is a online security ppt powerpoint presentation pictures layout ideas cpb. This is a four stage process. The stages in this process are online security.

Media Security Ppt PowerPoint Presentation Inspiration File Formats Cpb
This is a media security ppt powerpoint presentation inspiration file formats cpb. This is a three stage process. The stages in this process are media security.
Security Identity Management Ppt Powerpoint Presentation Pictures Portrait Cpb
This is a security identity management ppt powerpoint presentation pictures portrait cpb. This is a eight stage process. The stages in this process are security identity management.
Employee Incentives Icon For Healthcare And Financial Security Designs Pdf
Showcasing this set of slides titled Employee Incentives Icon For Healthcare And Financial Security Designs Pdf The topics addressed in these templates are Employee Incentives, Icon For Healthcare, Financial Security All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Employee Incentives Icon For Healthcare And Financial Security Designs Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf
Pitch your topic with ease and precision using this Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf This layout presents information on Data Transfer Security, Distributed Ledger, Technology Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Distributed Ledger Security Protocol List Icon Structure Pdf
Pitch your topic with ease and precision using this Distributed Ledger Security Protocol List Icon Structure Pdf This layout presents information on Data Transfer Security, Distributed Ledger, Technology Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Distributed Ledger Security Protocol List Icon Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf
Showcasing this set of slides titled Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf The topics addressed in these templates are Ecommerce Payment Security, Distributed Ledger, Technology Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security System In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security System In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security System that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security System In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Wireless In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Wireless In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Wireless that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Wireless In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Application Security Program In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Application Security Program In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Application Security Program that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Application Security Program In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Wifi Systems Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Wifi Systems Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Wifi Systems Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Wifi Systems Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Computer Personal Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Computer Personal Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Computer Personal Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Computer Personal Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
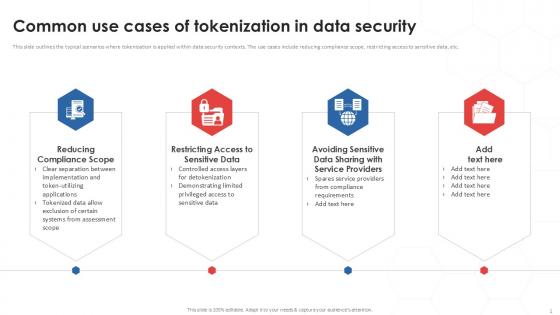
Common Use Cases Of Tokenization In Data Security PPT Template
This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc. Find a pre-designed and impeccable Common Use Cases Of Tokenization In Data Security PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc.

Framework Of Information IT Security Action Program Slides PDF
This slide focuses on information security action program framework which covers governance plan, security standards, stakeholder engagement and operational management to manage risks, handling threat, data security management, etc.Showcasing this set of slides titled Framework Of Information IT Security Action Program Slides PDF The topics addressed in these templates are Security Standards, Data Protection, Response Structure All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Unified Security Management Ppt Template Example Of Ppt Presentation
This is a unified security management ppt template example of ppt presentation. This is a four stage process. The stages in this process are assess the network, find threats, data loss prevention, gateway anti virus.

Steps For Internet Security Risk Assessment And Evaluation Microsoft Pdf
This slide showcase cyber risk assessment with standard risk identification to align organizational objective . It includes context establishment, risk identification, risk assessment and risk evaluation. Showcasing this set of slides titled Steps For Internet Security Risk Assessment And Evaluation Microsoft Pdf The topics addressed in these templates are Risk Identification, Risk Assessment, Risk Evaluation All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber risk assessment with standard risk identification to align organizational objective . It includes context establishment, risk identification, risk assessment and risk evaluation.
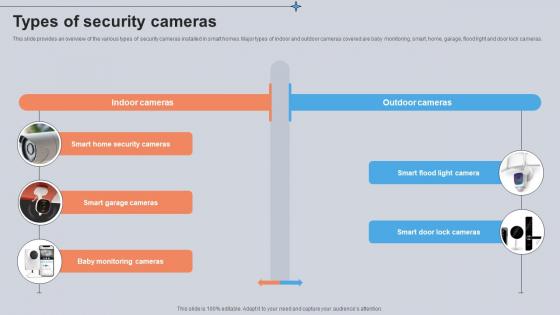
Types Of Security Cameras Utilizing Smart Appliances IoT SS V
This slide provides an overview of the various types of security cameras installed in smart homes. Major types of indoor and outdoor cameras covered are baby monitoring, smart, home, garage, flood light and door lock cameras. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Types Of Security Cameras Utilizing Smart Appliances IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Types Of Security Cameras Utilizing Smart Appliances IoT SS V today and make your presentation stand out from the rest This slide provides an overview of the various types of security cameras installed in smart homes. Major types of indoor and outdoor cameras covered are baby monitoring, smart, home, garage, flood light and door lock cameras.

Compound Annual Growth Rate CAGR Of Application Security Testing
This slide depicts the market growth of application security by software tools such as white-box testing, black-box testing, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Compound Annual Growth Rate CAGR Of Application Security Testing template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Compound Annual Growth Rate CAGR Of Application Security Testing that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide depicts the market growth of application security by software tools such as white-box testing, black-box testing, etc.
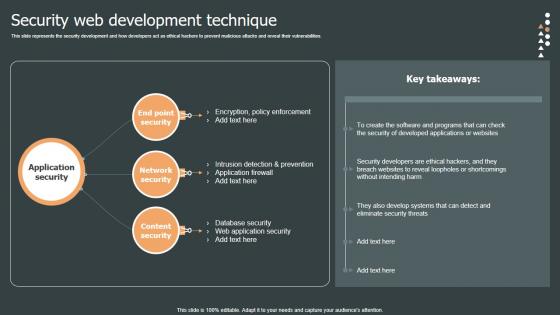
Security Web Development Role Web Designing User Engagement Topics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Are you searching for a Security Web Development Role Web Designing User Engagement Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Web Development Role Web Designing User Engagement Topics PDF from Slidegeeks today. This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.
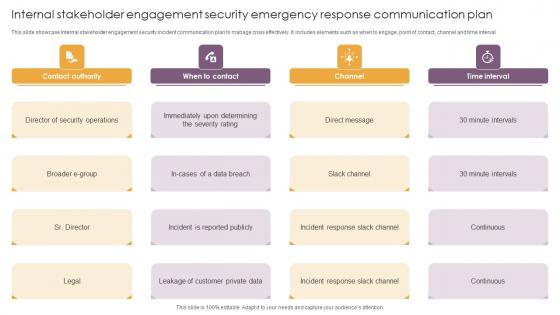
Internal Stakeholder Engagement Security Emergency Response Communication Plan Introduction Pdf
This slide showcase Internal stakeholder engagement security incident communication plan to manage crisis effectively. It includes elements such as when to engage, point of contact, channel and time interval Showcasing this set of slides titled Internal Stakeholder Engagement Security Emergency Response Communication Plan Introduction Pdf The topics addressed in these templates are Contact Authority, Time Interval, Director Of Security Operations All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase Internal stakeholder engagement security incident communication plan to manage crisis effectively. It includes elements such as when to engage, point of contact, channel and time interval
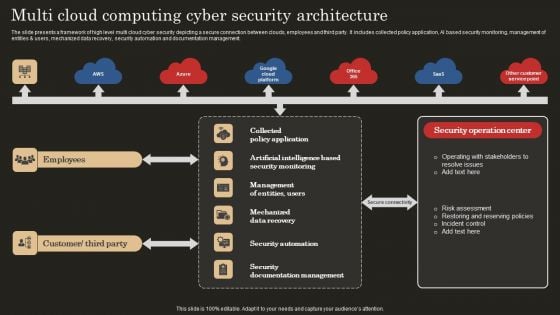
Multi Cloud Computing Cyber Security Architecture Microsoft PDF
The slide presents a framework of high level multi cloud cyber security depicting a secure connection between clouds, employees and third party. It includes collected policy application, AI based security monitoring, management of entities and users, mechanized data recovery, security automation and documentation management. Showcasing this set of slides titled Multi Cloud Computing Cyber Security Architecture Microsoft PDF. The topics addressed in these templates are Mechanized Data Recovery, Security Automation, Employees. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
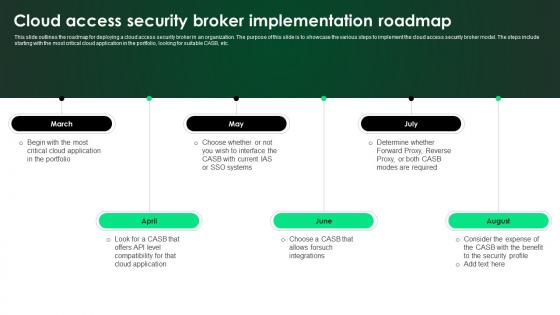
CASB 2 0 IT Cloud Access Security Broker Implementation Roadmap
This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Welcome to our selection of the CASB 2 0 IT Cloud Access Security Broker Implementation Roadmap. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc.
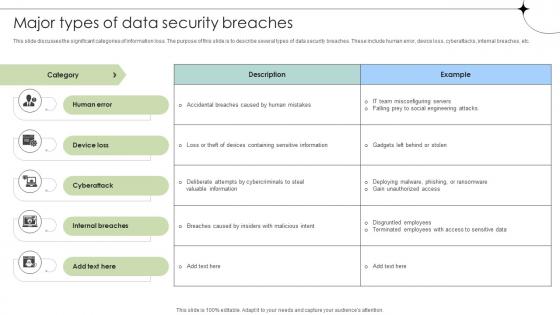
Major Types Of Data Security Breaches Data Fortification Strengthening Defenses
This slide discusses the significant categories of information loss. The purpose of this slide is to describe several types of data security breaches. These include human error, device loss, cyberattacks, internal breaches, etc. Presenting this PowerPoint presentation, titled Major Types Of Data Security Breaches Data Fortification Strengthening Defenses, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Major Types Of Data Security Breaches Data Fortification Strengthening Defenses. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Major Types Of Data Security Breaches Data Fortification Strengthening Defenses that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide discusses the significant categories of information loss. The purpose of this slide is to describe several types of data security breaches. These include human error, device loss, cyberattacks, internal breaches, etc.
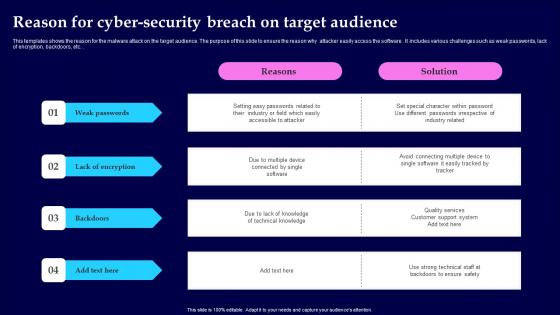
Reason For Cyber Security Breach On Target Audience Microsoft Pdf
This templates shows the reason for the malware attack on the target audience. The purpose of this slide to ensure the reason why attacker easily access the software . It includes various challenges such as weak passwords, lack of encryption, backdoors, etc. Showcasing this set of slides titled Reason For Cyber Security Breach On Target Audience Microsoft Pdf The topics addressed in these templates are Weak Passwords, Lack Of Encryption, Backdoors All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the reason for the malware attack on the target audience. The purpose of this slide to ensure the reason why attacker easily access the software . It includes various challenges such as weak passwords, lack of encryption, backdoors, etc.

Complete Guide To Launch Best Practices For Website Security Management
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Get a simple yet stunning designed Complete Guide To Launch Best Practices For Website Security Management. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Complete Guide To Launch Best Practices For Website Security Management can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc.
Icons Slide For Data Security In Cloud Computing Ppt Presentation
Download our innovative and attention grabbing Icons Slide For Data Security In Cloud Computing Ppt Presentation template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele. Our Icons Slide For Data Security In Cloud Computing Ppt Presentation are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Instalation Proposal In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Instalation Proposal In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Instalation Proposal that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Instalation Proposal In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































