Network Security

Cybersecurity Guidelines IT What Happens In The Absence Of IT Policies And Procedures Structure PDF
This slide represents the consequences of not having IT policies and procedures. Effects include disrupted and inconsistent operational duties, communication gaps between staff and employees, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cybersecurity Guidelines IT What Happens In The Absence Of IT Policies And Procedures Structure PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cybersecurity Guidelines IT What Happens In The Absence Of IT Policies And Procedures Structure PDF today and make your presentation stand out from the rest.
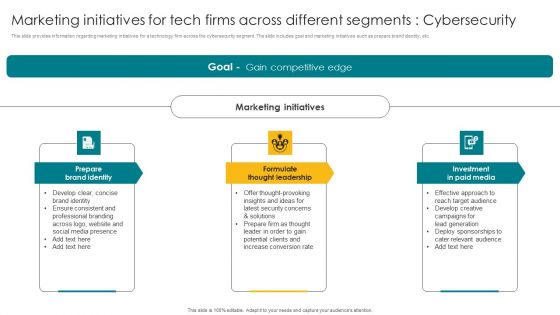
Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Microsoft PDF
This slide provides information regarding marketing initiatives for a technology firm across the cybersecurity segment. The slide includes goal and marketing initiatives such as prepare brand identity, etc. Present like a pro with Marketing Initiatives For Tech Firms Across Different Segments Cybersecurity Microsoft PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

IT Reducing Costs And Management Tips Marketing Initiatives For Tech Firms Across Segments Cybersecurity Pictures PDF
This slide provides information regarding marketing initiatives for a technology firm across the cybersecurity segment. The slide includes goal and marketing initiatives such as prepare brand identity, etc. Welcome to our selection of the IT Reducing Costs And Management Tips Marketing Initiatives For Tech Firms Across Segments Cybersecurity Pictures PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
Cybersecurity Operations Cybersecops Metrics To Track Secops Impact On Business Icons PDF
This slide refers to the key metrics to track the impact of SecOps implementation on business. The purpose of this slide is to highlight the key metrics for SecOps tracking, including mean time to acknowledge, mean time to resolve, incidents remediated and escalations between each tier. Get a simple yet stunning designed Cybersecurity Operations Cybersecops Metrics To Track Secops Impact On Business Icons PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cybersecurity Operations Cybersecops Metrics To Track Secops Impact On Business Icons PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
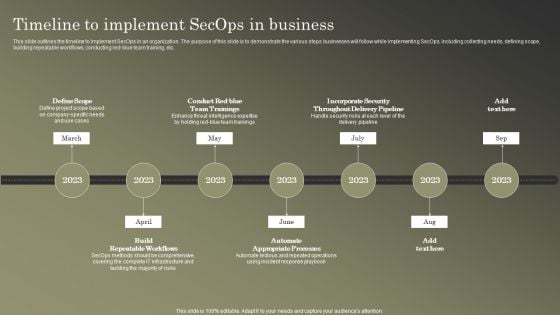
Cybersecurity Operations Cybersecops Timeline To Implement Secops In Business Structure PDF
This slide outlines the timeline to implement SecOps in an organization. The purpose of this slide is to demonstrate the various steps businesses will follow while implementing SecOps, including collecting needs, defining scope, building repeatable workflows, conducting red-blue team training, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cybersecurity Operations Cybersecops Timeline To Implement Secops In Business Structure PDF can be your best option for delivering a presentation. Represent everything in detail using Cybersecurity Operations Cybersecops Timeline To Implement Secops In Business Structure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cybersecurity Operations Cybersecops Roadmap To Implement Secops In Business Background PDF
This slide represents the roadmap to implement SecOps in an organization. The purpose of this slide is to demonstrate the various steps businesses will follow while implementing SecOps, including collecting needs, defining scope, building repeatable workflows, conducting red-blue team training, etc. This Cybersecurity Operations Cybersecops Roadmap To Implement Secops In Business Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cybersecurity Operations Cybersecops Roadmap To Implement Secops In Business Background PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Strategies For Reducing Cybersecurity Risks In Abs Healthcare Company Ppt File Images PDF
This is a strategies for reducing cybersecurity risks in abs healthcare company ppt file images pdf. template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data management, updated software, proper employee training, strategy, procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Approaches To Implement Advanced Cybersecurity Monitoring Plan 30 60 90 Days Plan Portrait PDF
Presenting approaches to implement advanced cybersecurity monitoring plan 30 60 90 days plan portrait pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Approaches To Implement Advanced Cybersecurity Monitoring Plan Post It Notes Mockup PDF
This is a approaches to implement advanced cybersecurity monitoring plan post it notes mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
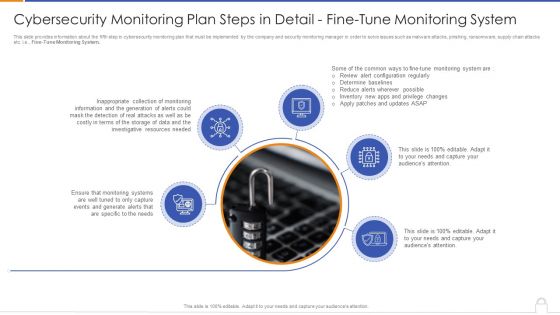
Cybersecurity Monitoring Plan Steps In Detail Fine Tune Monitoring System Portrait PDF
This is a cybersecurity monitoring plan steps in detail fine tune monitoring system portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine baselines, reduce alerts wherever possible, inappropriate collection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Monitoring Plan Steps In Detail Monitoring User Activity Themes PDF
Presenting cybersecurity monitoring plan steps in detail monitoring user activity themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like accidental misuse of systems, regulatory constraints, suspicious activity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Monitoring Plan Steps In Detail Setting Up A Centralized Collection And Analysis Capability Microsoft PDF
Presenting cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability microsoft pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like develop and deploy, solution architecture, interpret information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
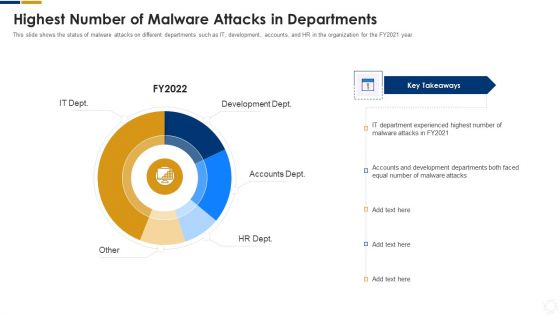
Cybersecurity Highest Number Of Malware Attacks In Departments Ppt Styles Graphic Images PDF
This slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2021 year. Deliver an awe inspiring pitch with this creative cybersecurity highest number of malware attacks in departments ppt styles graphic images pdf bundle. Topics like highest number of malware attacks in departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
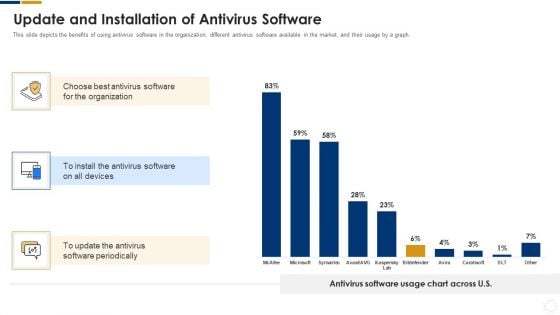
Cybersecurity Update And Installation Of Antivirus Software Ppt Pictures Images PDF
This slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver an awe inspiring pitch with this creative cybersecurity update and installation of antivirus software ppt pictures images pdf bundle. Topics like update and installation of antivirus software can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
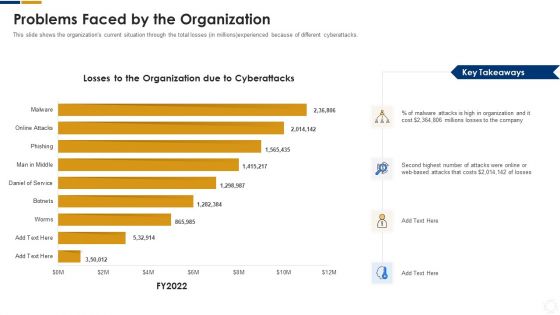
Cybersecurity Problems Faced By The Organization Ppt Portfolio Clipart Images PDF
This slide shows the organizations current situation through the total losses in millions experienced because of different cyberattacks. Deliver an awe inspiring pitch with this creative cybersecurity problems faced by the organization ppt portfolio clipart images pdf bundle. Topics like problems faced by the organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mitigating Cybersecurity Threats And Vulnerabilities Comparative Assessment Of Various Background PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities comparative assessment of various background pdf bundle. Topics like social engineering, insider threat, maintenance threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
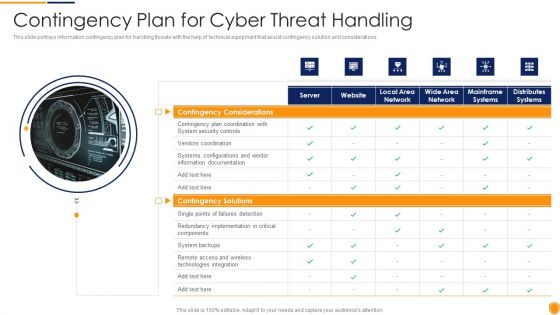
Mitigating Cybersecurity Threats And Vulnerabilities Contingency Plan For Cyber Infographics PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities contingency plan for cyber infographics pdf. Use them to share invaluable insights on contingency solutions, contingency considerations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
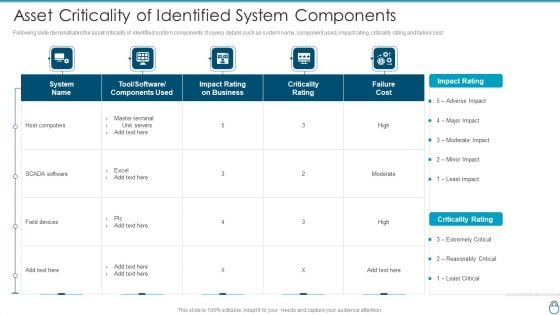
Cybersecurity Risk Administration Plan Asset Criticality Of Identified System Components Professional PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Asset Criticality Of Identified System Components Professional PDF bundle. Topics like Impact Rating On Business, Criticality Rating, Impact Rating can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Incident Management Tool We Will Use Summary PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Incident Management Tool We Will Use Summary PDF bundle. Topics like Automated Workflow, Notify Employee, Feature Description can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
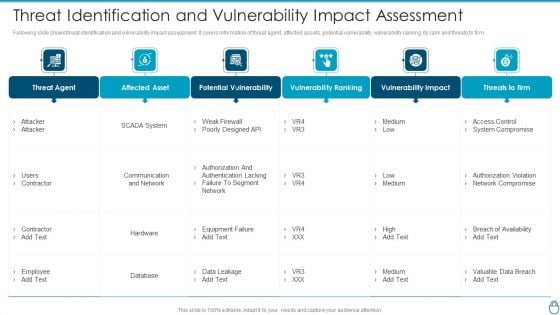
Cybersecurity Risk Administration Plan Threat Identification And Vulnerability Impact Assessment Slides PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Threat Identification And Vulnerability Impact Assessment Slides PDF bundle. Topics like Potential Vulnerability, Vulnerability Ranking, Vulnerability Impact can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
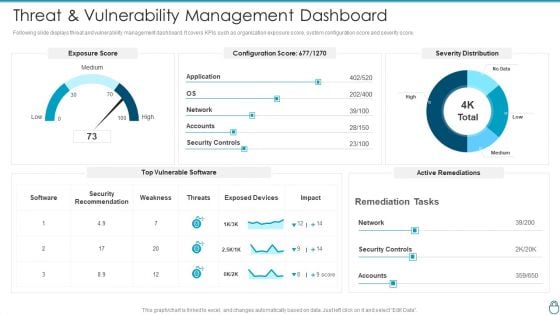
Cybersecurity Risk Administration Plan Threat And Vulnerability Management Dashboard Elements PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Threat And Vulnerability Management Dashboard Elements PDF Use them to share invaluable insights on Exposure Score, Remediation Tasks, Severity Distribution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

30 60 90 Days Plan Cybersecurity Risk Assessment And Administration Plan Formats PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable 30 60 90 Days Plan Cybersecurity Risk Assessment And Administration Plan Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

G6 Table Of Contents For Cybersecurity Risk Assessment And Administration Plan Pictures PDF
Boost your pitch with our creative G6 Table Of Contents For Cybersecurity Risk Assessment And Administration Plan Pictures PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Post It Notes Cybersecurity Risk Assessment And Administration Plan Rules PDF
Create an editable Post It Notes Cybersecurity Risk Assessment And Administration Plan Rules PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. ZZZZZZZZZZZZZZZZZZ is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
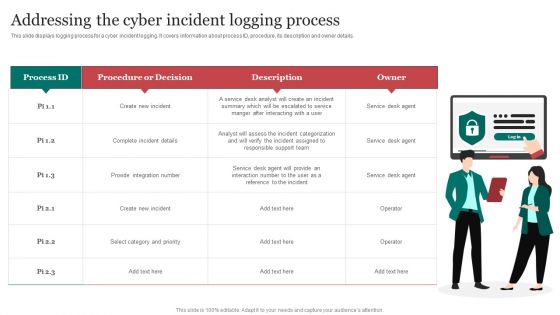
Addressing The Cyber Incident Logging Process Improving Cybersecurity Incident Summary PDF
This slide displays logging process for a cyber incident logging. It covers information about process ID, procedure, its description and owner details.Find a pre-designed and impeccable Addressing The Cyber Incident Logging Process Improving Cybersecurity Incident Summary PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Backup Methods For Cyber Defense Planning Improving Cybersecurity With Incident Information PDF
Following slide shows various backup methods as well as backup options that can be chosen for cyber defense planning. Methods covered are full, differential and incremental.There are so many reasons you need a Backup Methods For Cyber Defense Planning Improving Cybersecurity With Incident Information PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Implementing Cybersecurity Awareness Program To Prevent Attacks Table Of Contents Elements PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Cybersecurity Awareness Program To Prevent Attacks Table Of Contents Elements PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
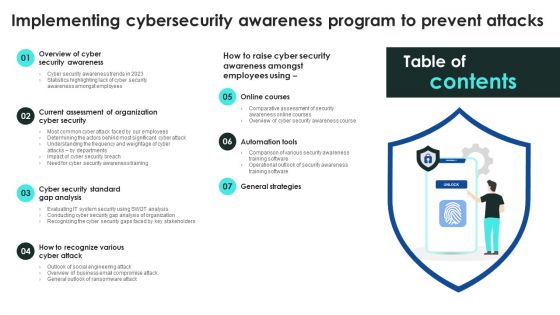
Table Of Contents Implementing Cybersecurity Awareness Program To Prevent Attacks Slides PDF
Boost your pitch with our creative Table Of Contents Implementing Cybersecurity Awareness Program To Prevent Attacks Slides PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
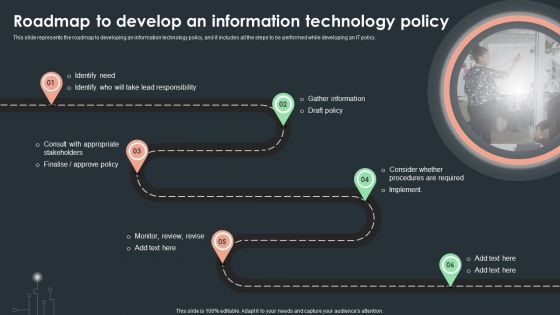
Cybersecurity Guidelines IT Roadmap To Develop An Information Technology Policy Pictures PDF
This slide represents the roadmap to developing an information technology policy, and it includes all the steps to be performed while developing an IT policy. There are so many reasons you need a Cybersecurity Guidelines IT Roadmap To Develop An Information Technology Policy Pictures PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Cybersecurity Guidelines IT Post It Notes Ppt PowerPoint Presentation File Template PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Cybersecurity Guidelines IT Post It Notes Ppt PowerPoint Presentation File Template PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Table Of Contents Cybersecurity Guidelines IT Ppt PowerPoint Presentation File Templates PDF
The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Table Of Contents Cybersecurity Guidelines IT Ppt PowerPoint Presentation File Templates PDF from Slidegeeks and deliver a wonderful presentation.

Table Of Contents Cybersecurity Guidelines IT Ppt PowerPoint Presentation Gallery Format PDF
The Table Of Contents Cybersecurity Guidelines IT Ppt PowerPoint Presentation Gallery Format PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
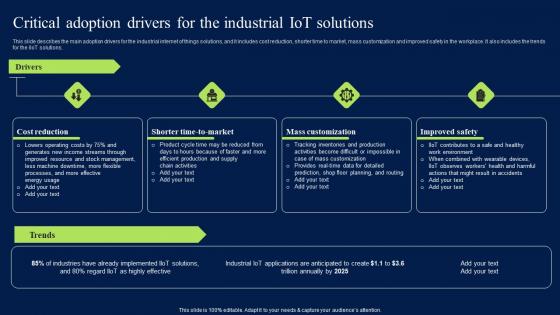
Critical Adoption Drivers For The Industrial Iot Solutions Sample PDF
This slide describes the main adoption drivers for the industrial internet of things solutions, and it includes cost reduction, shorter time to market, mass customization and improved safety in the workplace. It also includes the trends for the IIoT solutions. Retrieve professionally designed Critical Adoption Drivers For The Industrial Iot Solutions Sample PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the main adoption drivers for the industrial internet of things solutions, and it includes cost reduction, shorter time to market, mass customization and improved safety in the workplace. It also includes the trends for the IIoT solutions.

IoT Application In Global Retail IoT Solutions Offered By At And T Guidelines PDF
The following slide highlights the technology solutions provided by ATandT for enabling retailers to implement internet of things in retail sector. It shows personalized offers solution, multi access edge computing and wait time management. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created IoT Application In Global Retail IoT Solutions Offered By At And T Guidelines PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The following slide highlights the technology solutions provided by ATandT for enabling retailers to implement internet of things in retail sector. It shows personalized offers solution, multi access edge computing and wait time management.
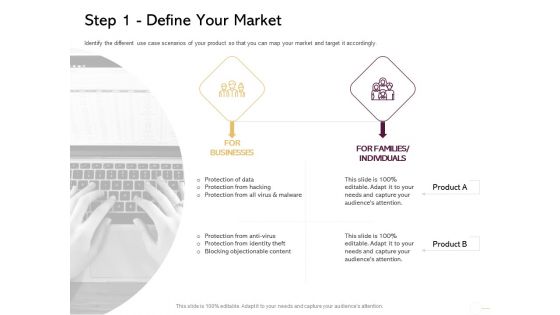
Managing Portfolio Growth Options Step 1 Define Your Market Ppt Outline Show PDF
Presenting this set of slides with name managing portfolio growth options step 1 define your market ppt outline show pdf. This is an editable Powerpoint two stages graphic that deals with topics like protection of data, protection from hacking, protection from all virus and malware, protection from anti virus, protection from identity theft, blocking objectionable content to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Effective Cybersecurity Training To Raise Awareness Ppt PowerPoint Presentation Complete With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This effective cybersecurity training to raise awareness ppt powerpoint presentation complete with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty one slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.
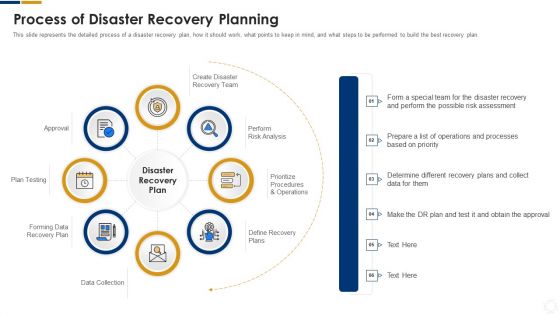
Cybersecurity Process Of Disaster Recovery Planning Ppt Infographic Template Elements PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a cybersecurity process of disaster recovery planning ppt infographic template elements pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like recovery plan, recovery team, risk analysis, prioritize procedures, data collection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Strategies To Manage Cyber Risks Ppt Infographic Template Graphics Template PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a cybersecurity strategies to manage cyber risks ppt infographic template graphics template pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strategic, risk, implementation, awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
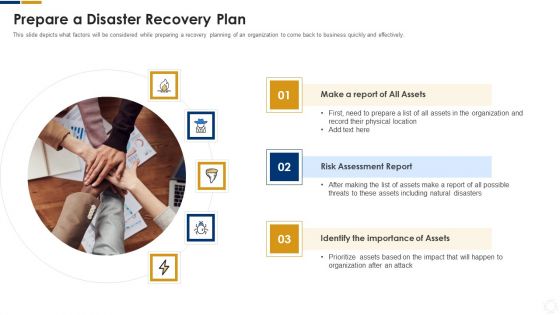
Cybersecurity Prepare A Disaster Recovery Plan Ppt Infographic Template Good PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a cybersecurity prepare a disaster recovery plan ppt infographic template good pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, risk, physical location. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
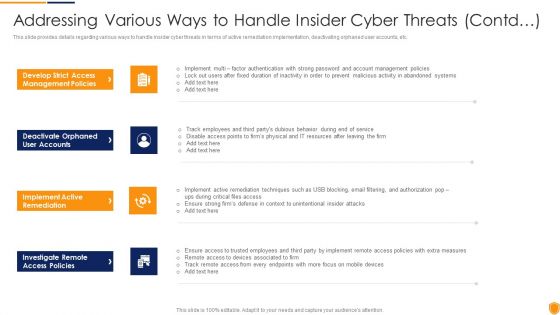
Addressing Various Ways To Handle Mitigating Cybersecurity Threats And Vulnerabilities Template PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a addressing various ways to handle mitigating cybersecurity threats and vulnerabilities template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like user accounts, implement active remediation, management policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Determine Sequence Phases For Mitigating Cybersecurity Threats And Vulnerabilities Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a determine sequence phases for mitigating cybersecurity threats and vulnerabilities inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
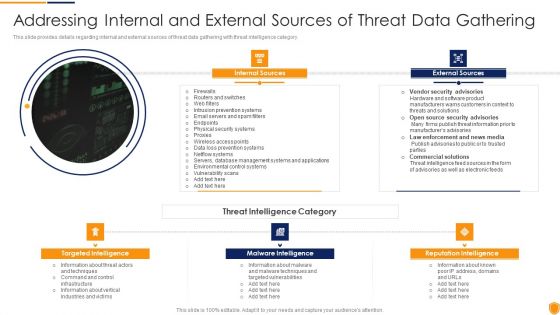
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Internal And External Clipart PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. This is a mitigating cybersecurity threats and vulnerabilities addressing internal and external clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal sources, external sources, targeted intelligence, malware intelligence, reputation intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Different Kinds Of Insider Information PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a mitigating cybersecurity threats and vulnerabilities different kinds of insider information pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like different kinds of insider digital threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
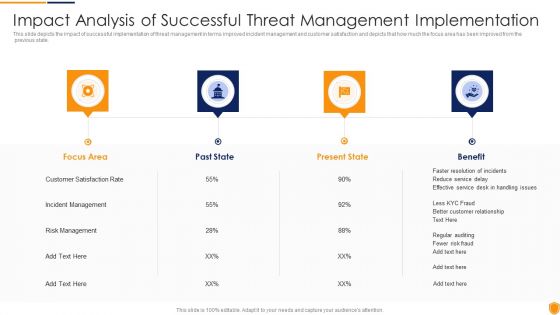
Mitigating Cybersecurity Threats And Vulnerabilities Impact Analysis Of Successful Threat Slides PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Presenting mitigating cybersecurity threats and vulnerabilities impact analysis of successful threat slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like focus area, past state, present state, benefit. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Threat Management Action Plan Mockup PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities threat management action plan mockup pdf. Use them to share invaluable insights on threat identification, threat treatment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Various Types Of Workplace Download PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a mitigating cybersecurity threats and vulnerabilities various types of workplace download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threatening behavior, stalking, assault harassment, property damage. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Role Of Technical Competence In Organizational It Professional Upskilling For Cybersecurity Guidelines PDF
The following slide provides information about the key roles of the ML Architect along with the role description. Major roles included in the slide are Data Scientist Citizen Data Scientist, ML architect, AI Architect, and AI Engineer This is a Role Of Technical Competence In Organizational It Professional Upskilling For Cybersecurity Guidelines PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Scientist Or Citizen, Data Scientist Extracting Knowledge, Functions To Operationalize You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
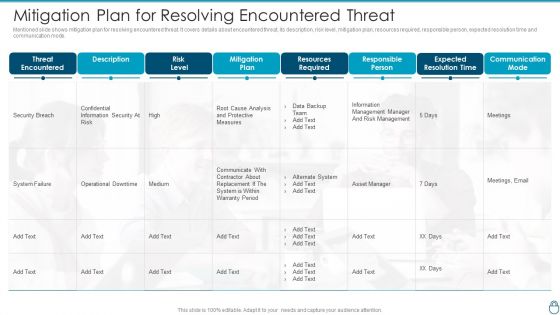
Cybersecurity Risk Administration Plan Mitigation Plan For Resolving Encountered Threat Professional PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Mitigation Plan For Resolving Encountered Threat Professional PDF Use them to share invaluable insights on Resources Required, Responsible Person, Expected Resolution Time and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
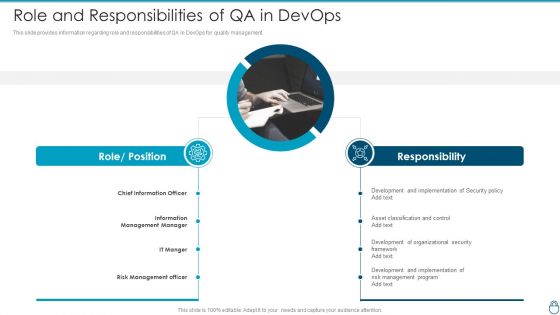
Cybersecurity Risk Administration Plan Role And Responsibilities Of QA In Devops Diagrams PDF
This slide provides information regarding role and responsibilities of QA in DevOps for quality management. This is a Cybersecurity Risk Administration Plan Role And Responsibilities Of QA In Devops Diagrams PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development And Implementation, Asset Classification And Control, Development Of Organizational You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
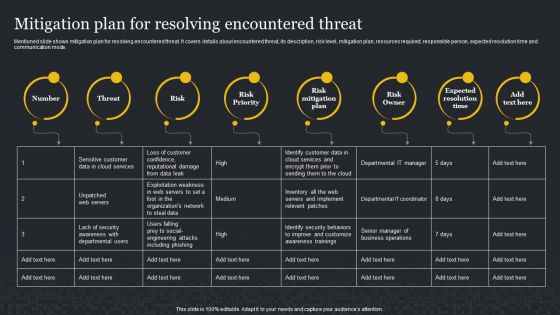
Mitigation Plan For Resolving Encountered Threat Cybersecurity Risk Assessment Demonstration PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mitigation Plan For Resolving Encountered Threat Cybersecurity Risk Assessment Demonstration PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Assessing Cost Of Information Breach In Different Countries Cybersecurity Risk Assessment Background PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Assessing Cost Of Information Breach In Different Countries Cybersecurity Risk Assessment Background PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
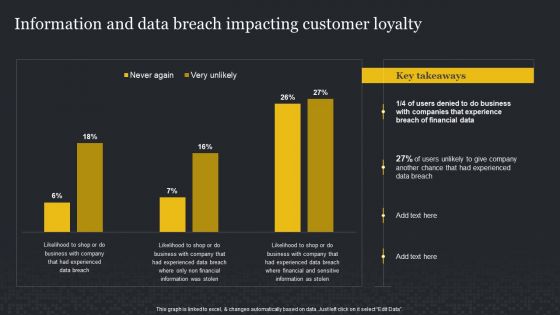
Information And Data Breach Impacting Customer Loyalty Cybersecurity Risk Assessment Infographics PDF
Retrieve professionally designed Information And Data Breach Impacting Customer Loyalty Cybersecurity Risk Assessment Infographics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
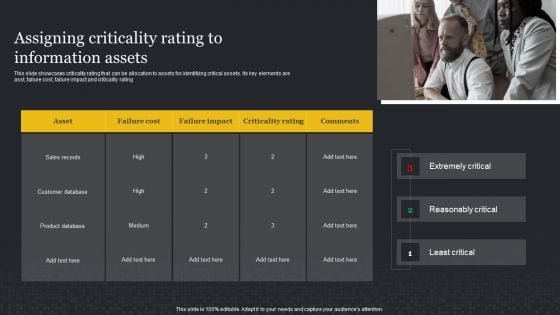
Assigning Criticality Rating To Information Assets Cybersecurity Risk Assessment Template PDF
This slide showcases criticality rating that can be allocation to assets for identifying critical assets. Its key elements are asst, failure cost, failure impact and criticality rating. Take your projects to the next level with our ultimate collection of Assigning Criticality Rating To Information Assets Cybersecurity Risk Assessment Template PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest.

Improving Cybersecurity With Incident Response Playbook Ppt PowerPoint Presentation Complete Deck With Slides
Grab this Improving Cybersecurity With Incident Response Playbook Ppt PowerPoint Presentation Complete Deck With Slides to craft a unique and engaging business proposal for your clients. This PowerPoint complete Deck of fivtyslides covers essentials points all essential points that makes it an excellent choice for exhibiting an idea to the stakeholders. You can use this presentation template, even, to give a product demo to highlight its credibility and usage. The presentation template is also equipped to do this with its 100 precent editable and customizable capability. Download now.

Asset Criticality Of Identified System Improving Cybersecurity With Incident Themes PDF
Mentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Asset Criticality Of Identified System Improving Cybersecurity With Incident Themes PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
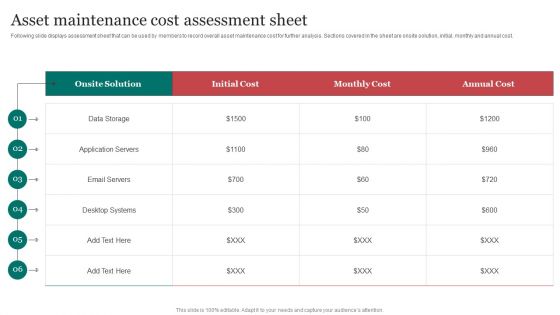
Asset Maintenance Cost Assessment Sheet Improving Cybersecurity With Incident Download PDF
Following slide displays assessment sheet that can be used by members to record overall asset maintenance cost for further analysis. Sections covered in the sheet are onsite solution, initial, monthly and annual cost.Want to ace your presentation in front of a live audience Our Asset Maintenance Cost Assessment Sheet Improving Cybersecurity With Incident Download PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
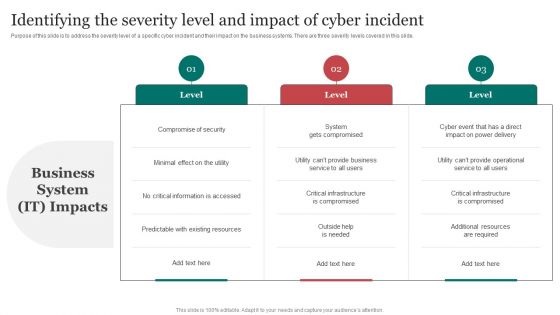
Identifying The Severity Level And Impact Improving Cybersecurity With Incident Introduction PDF
Purpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide.Make sure to capture your audiences attention in your business displays with our gratis customizable Identifying The Severity Level And Impact Improving Cybersecurity With Incident Introduction PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Implementing Cybersecurity Awareness Program To Prevent Attacks Tracking Sheet To Monitor The Performance Introduction PDF
Present like a pro with Implementing Cybersecurity Awareness Program To Prevent Attacks Tracking Sheet To Monitor The Performance Introduction PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cybersecurity Guidelines IT Acceptable Use Of Equipment Policy Overview Slides PDF
This slide outlines the acceptable use policy, and it includes how official computers should be used, risks associated with improper usage, and appropriate behavior while handling sensitive information. Find a pre-designed and impeccable Cybersecurity Guidelines IT Acceptable Use Of Equipment Policy Overview Slides PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
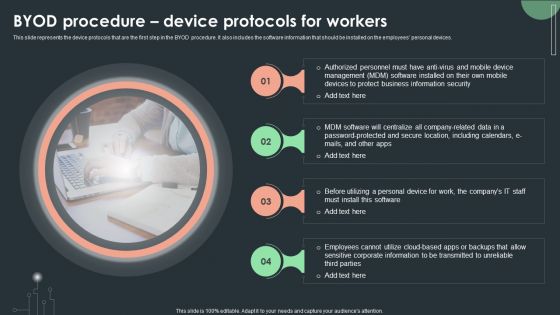
Cybersecurity Guidelines IT Byod Procedure Device Protocols For Workers Guidelines PDF
This slide represents the device protocols that are the first step in the BYOD procedure. It also includes the software information that should be installed on the employees personal devices. Want to ace your presentation in front of a live audience Our Cybersecurity Guidelines IT Byod Procedure Device Protocols For Workers Guidelines PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.


 Continue with Email
Continue with Email

 Home
Home


































