Network Security
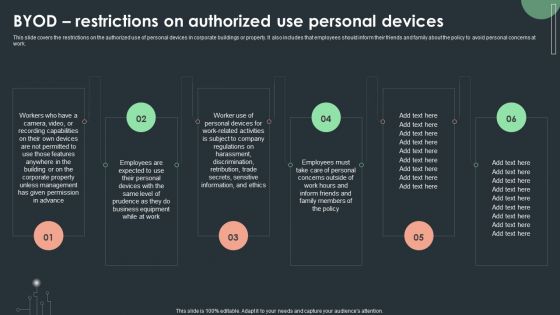
Cybersecurity Guidelines IT Byod Restrictions On Authorized Use Personal Devices Professional PDF
This slide covers the restrictions on the authorized use of personal devices in corporate buildings or property. It also includes that employees should inform their friends and family about the policy to avoid personal concerns at work. There are so many reasons you need a Cybersecurity Guidelines IT Byod Restrictions On Authorized Use Personal Devices Professional PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
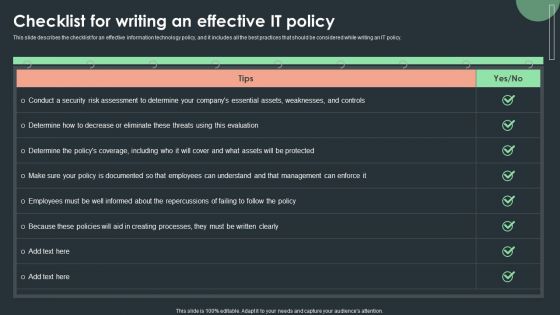
Cybersecurity Guidelines IT Checklist For Writing An Effective IT Policy Rules PDF
This slide describes the checklist for an effective information technology policy, and it includes all the best practices that should be considered while writing an IT policy. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Cybersecurity Guidelines IT Checklist For Writing An Effective IT Policy Rules PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
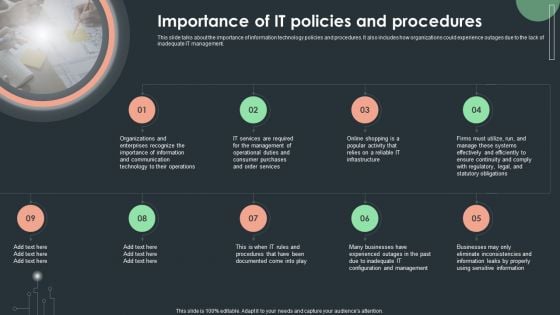
Cybersecurity Guidelines IT Importance Of IT Policies And Procedures Rules PDF
This slide talks about the importance of information technology policies and procedures. It also includes how organizations could experience outages due to the lack of inadequate IT management. Make sure to capture your audiences attention in your business displays with our gratis customizable Cybersecurity Guidelines IT Importance Of IT Policies And Procedures Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cybersecurity Guidelines IT Overview Of Information Retention Policy For Employees Microsoft PDF
This slide talks about the data retention policy, including the involved data types such as documents, customer records, transactional information, email communication, and contracts. Find a pre-designed and impeccable Cybersecurity Guidelines IT Overview Of Information Retention Policy For Employees Microsoft PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cybersecurity Guidelines IT Termination Of Employment And Violation Of Byod Policy Themes PDF
This slide talks about the termination of employment and violation of BYOD policy. Both include the actions to be performed if any employee leaves or violates the BYOD policy. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Cybersecurity Guidelines IT Termination Of Employment And Violation Of Byod Policy Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
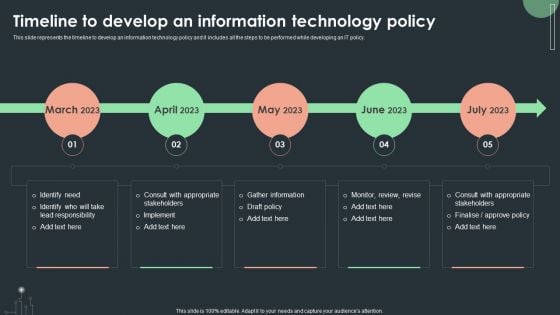
Cybersecurity Guidelines IT Timeline To Develop An Information Technology Policy Introduction PDF
This slide represents the timeline to develop an information technology policy and it includes all the steps to be performed while developing an IT policy. Present like a pro with Cybersecurity Guidelines IT Timeline To Develop An Information Technology Policy Introduction PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
Cybersecurity Guidelines IT Column Chart Ppt PowerPoint Presentation Icon Show PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cybersecurity Guidelines IT Column Chart Ppt PowerPoint Presentation Icon Show PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Cybersecurity Guidelines IT Our Target Ppt PowerPoint Presentation Gallery Visual Aids PDF
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cybersecurity Guidelines IT Our Target Ppt PowerPoint Presentation Gallery Visual Aids PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
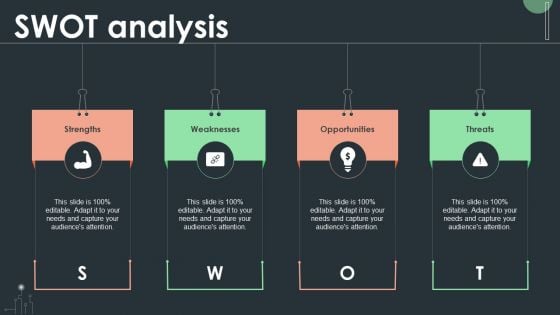
Cybersecurity Guidelines IT SWOT Analysis Ppt PowerPoint Presentation File Background Images PDF
This modern and well-arranged Cybersecurity Guidelines IT SWOT Analysis Ppt PowerPoint Presentation File Background Images PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cybersecurity Guidelines IT Venn Diagram Ppt PowerPoint Presentation File Smartart PDF
Welcome to our selection of the Cybersecurity Guidelines IT Venn Diagram Ppt PowerPoint Presentation File Smartart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Pharming Phishing Types And Prevention Man In The Middle Phishing IT
This slide demonstrates the different types pf pharming phishing scams. The primary types include malware-based pharming and DNS pharming. This slide also outlines the ways which helps to prevent a pharming attack such as verify the URL, install VPN, etc. Want to ace your presentation in front of a live audience Our Pharming Phishing Types And Prevention Man In The Middle Phishing IT can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide demonstrates the different types pf pharming phishing scams. The primary types include malware-based pharming and DNS pharming. This slide also outlines the ways which helps to prevent a pharming attack such as verify the URL, install VPN, etc.
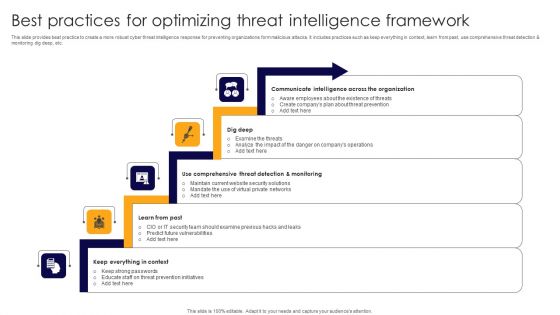
Best Practices For Optimizing Threat Intelligence Framework Formats PDF
This slide provides beat practice to create a more robust cyber threat intelligence response for preventing organizations form malicious attacks. It includes practices such as keep everything in context, learn from past, use comprehensive threat detection and monitoring dig deep, etc. Presenting Best Practices For Optimizing Threat Intelligence Framework Formats PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Communicate Intelligence, Dig Deep, Comprehensive Threat Detection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
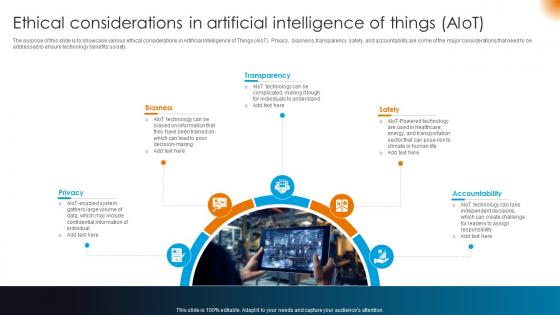
Integrating AI With IoT Ethical Considerations In Artificial Intelligence Of Things AIoT IoT SS V
The purpose of this slide is to showcase various ethical considerations in Artificial Intelligence of Things AIoT. Privacy, biasness, transparency, safety, and accountability are some of the major considerations that need to be addressed to ensure technology benefits society. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Integrating AI With IoT Ethical Considerations In Artificial Intelligence Of Things AIoT IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Integrating AI With IoT Ethical Considerations In Artificial Intelligence Of Things AIoT IoT SS V effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The purpose of this slide is to showcase various ethical considerations in Artificial Intelligence of Things AIoT. Privacy, biasness, transparency, safety, and accountability are some of the major considerations that need to be addressed to ensure technology benefits society.

Audit Commission Strengthening Cybersecurity Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured audit commission strengthening cybersecurity ppt powerpoint presentation complete deck with slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twenty seven slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Cybersecurity Risk Assessment And Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides
Take advantage of this well-researched and professionally-designed Cybersecurity Risk Assessment And Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides to ace your next business meeting. Use this PPT complete deck to impress the management with your ideas for business growth and revenue increase. Use the seventy two slide Template Bundle to leave no stone unturned as you present each step of your process. Employ the visual tools within the slides such as graphs, charts, and tables to ensure that the audience can never look away from the presentation. With attractive visuals, easy to understand structure, and your knowledge, your presentation will have the attention it deserves. Download this PPT Template from the link below.

Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Implementing Cybersecurity Awareness Program To Prevent Attacks Dos And Donts Of Prevention Inspiration PDF
The purpose of this slide is to showcase the Does and do nots of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Slidegeeks is here to make your presentations a breeze with Implementing Cybersecurity Awareness Program To Prevent Attacks Dos And Donts Of Prevention Inspiration PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
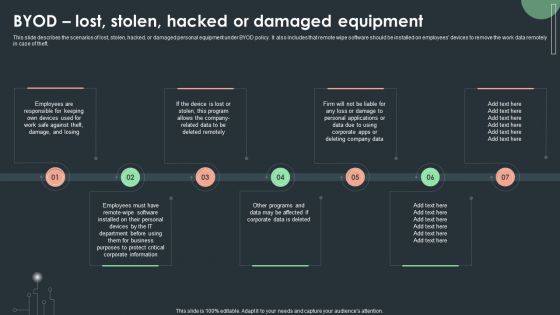
Cybersecurity Guidelines IT Byod Lost Stolen Hacked Or Damaged Equipment Designs PDF
This slide describes the scenarios of lost, stolen, hacked, or damaged personal equipment under BYOD policy. It also includes that remote wipe software should be installed on employees devices to remove the work data remotely in case of theft. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Guidelines IT Byod Lost Stolen Hacked Or Damaged Equipment Designs PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
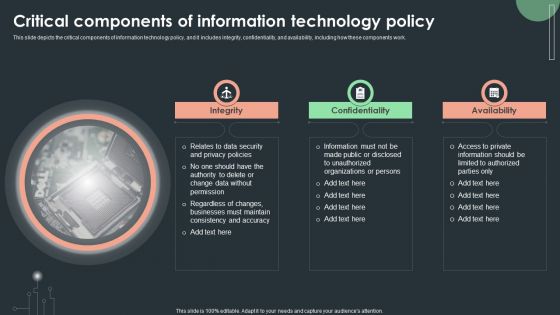
Cybersecurity Guidelines IT Critical Components Of Information Technology Policy Structure PDF
This slide depicts the critical components of information technology policy, and it includes integrity, confidentiality, and availability, including how these components work. Slidegeeks is here to make your presentations a breeze with Cybersecurity Guidelines IT Critical Components Of Information Technology Policy Structure PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cybersecurity Guidelines IT Vendor Management Policy Overview And Considerations Diagrams PDF
This slide represents the vendor management policy, and it also includes points to be considered when choosing a vendor. This policy is about the vendor with whom organizations share their critical information. Slidegeeks is here to make your presentations a breeze with Cybersecurity Guidelines IT Vendor Management Policy Overview And Considerations Diagrams PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cybersecurity Guidelines IT Company Stipend For Bring Your Own Device Policy Download PDF
This slide represents the company stipend for BYOD policy, including the stats for 2022, such as percent the age of employees using their personal devices, BYOD generated value of each worker per year, and so on. Present like a pro with Cybersecurity Guidelines IT Company Stipend For Bring Your Own Device Policy Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
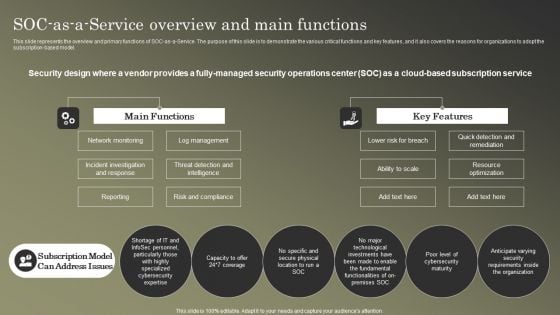
Cybersecurity Operations Cybersecops SOC As A Service Overview And Main Functions Rules PDF
This slide represents the overview and primary functions of SOC-as-a-Service. The purpose of this slide is to demonstrate the various critical functions and key features, and it also covers the reasons for organizations to adopt the subscription-based model. Slidegeeks is here to make your presentations a breeze with Cybersecurity Operations Cybersecops SOC As A Service Overview And Main Functions Rules PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
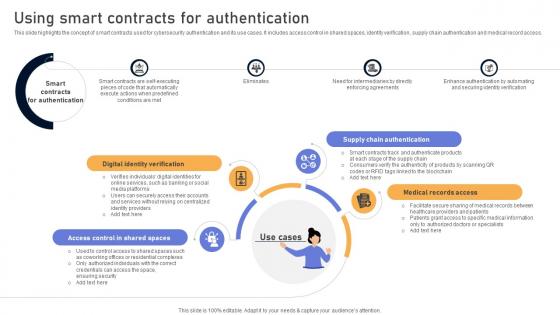
Comprehensive Look At Blockchain Using Smart Contracts For Authentication BCT SS V
This slide highlights the concept of smart contracts used for cybersecurity authentication and its use cases. It includes access control in shared spaces, identity verification, supply chain authentication and medical record access. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Comprehensive Look At Blockchain Using Smart Contracts For Authentication BCT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Comprehensive Look At Blockchain Using Smart Contracts For Authentication BCT SS V This slide highlights the concept of smart contracts used for cybersecurity authentication and its use cases. It includes access control in shared spaces, identity verification, supply chain authentication and medical record access.

Optimization Of IoT Remote Monitoring Smart Speakers Used By Home Owners For Remote Controlling IoT SS V
This slide provides an overview of the smart speaker systems used in homes that provides assistance in house tasks by following voice commands. It further includes benefits, factors to consider, privacy concerns, safety tips and working. Create an editable Optimization Of IoT Remote Monitoring Smart Speakers Used By Home Owners For Remote Controlling IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Optimization Of IoT Remote Monitoring Smart Speakers Used By Home Owners For Remote Controlling IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides an overview of the smart speaker systems used in homes that provides assistance in house tasks by following voice commands. It further includes benefits, factors to consider, privacy concerns, safety tips and working.
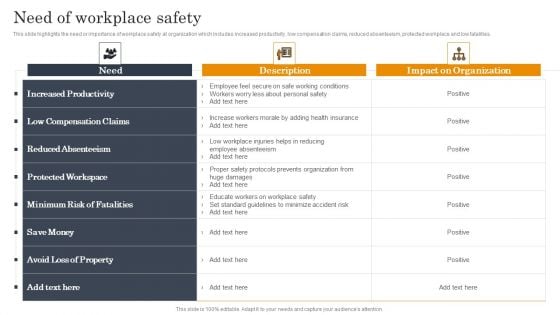
Employee Health And Safety Need Of Workplace Safety Professional PDF
This slide highlights the need or importance of workplace safety at organization which includes increased productivity, low compensation claims, reduced absenteeism, protected workplace and low fatalities. Find a pre-designed and impeccable Employee Health And Safety Need Of Workplace Safety Professional PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Technology Guide For Serverless Computing Disadvantages Of Private Cloud Facilities Background PDF
This is a technology guide for serverless computing disadvantages of private cloud facilities background pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like user facilities, corporate vpn, data centers, and data center interconnect. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
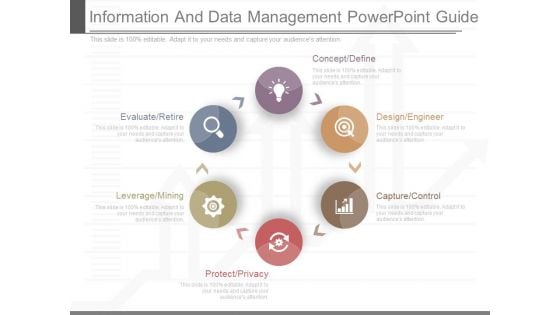
Information And Data Management Powerpoint Guide
This is a information and data management powerpoint guide. This is a six stage process. The stages in this process are concept define, design engineer, capture control, evaluate retire, leverage mining, protect privacy.
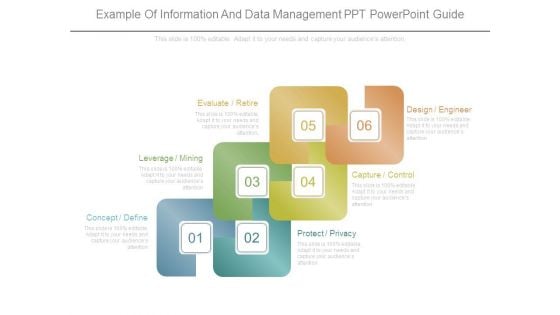
Example Of Information And Data Management Ppt Powerpoint Guide
This is a example of information and data management ppt powerpoint guide. This is a six stage process. The stages in this process are concept define, leverage mining, evaluate retire, design engineer, capture control, protect privacy.
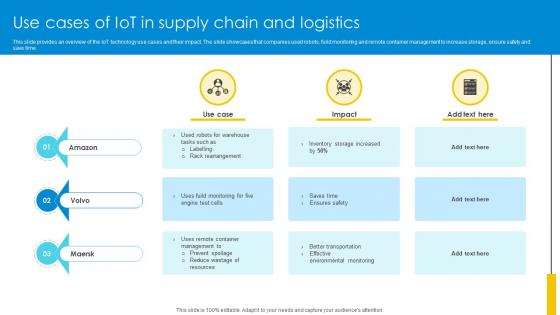
Use Cases Of IoT In Supply Chain And Logistics Optimizing Inventory Management IoT SS V
This slide provides an overview of the IoT technology use cases and their impact. The slide showcases that companies used robots, fuild monitoring and remote container management to increase storage, ensure safety and save time. Find a pre-designed and impeccable Use Cases Of IoT In Supply Chain And Logistics Optimizing Inventory Management IoT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides an overview of the IoT technology use cases and their impact. The slide showcases that companies used robots, fuild monitoring and remote container management to increase storage, ensure safety and save time.
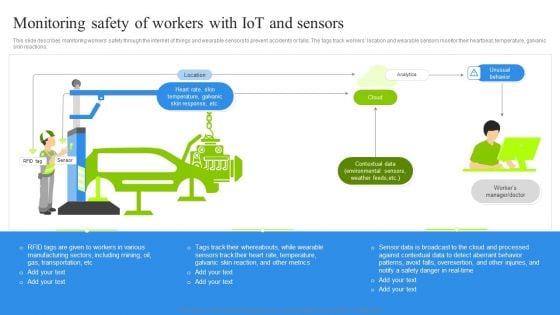
Monitoring Safety Of Workers With Iot And Sensors Professional PDF
This slide describes monitoring workers safety through the internet of things and wearable sensors to prevent accidents or falls. The tags track workers location and wearable sensors monitor their heartbeat, temperature, galvanic skin reactions. This Monitoring Safety Of Workers With Iot And Sensors Professional PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Overview Sharing Access Over Ownership Business Model DT SS V
This slide presents an overview of sharing model or access over ownership model detailing its benefits. It also mentions the framework of sharing economy model including three main components seeker, platform and owner.This Overview Sharing Access Over Ownership Business Model DT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide presents an overview of sharing model or access over ownership model detailing its benefits. It also mentions the framework of sharing economy model including three main components seeker, platform and owner.

Safety First Workplace Poster Ppt PowerPoint Presentation Gallery Guidelines PDF
Showcasing this set of slides titled safety first workplace poster ppt powerpoint presentation gallery guidelines pdf. The topics addressed in these templates are wear vest, wear face mask, wear head protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
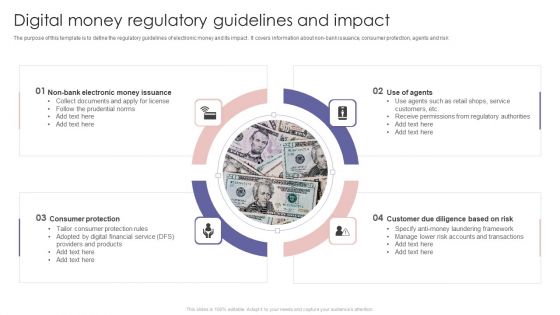
Digital Money Regulatory Guidelines And Impact Ppt PowerPoint Presentation File Deck PDF
The purpose of this template is to define the regulatory guidelines of electronic money and its impact . It covers information about non bank issuance, consumer protection, agents and risk. Persuade your audience using this Digital Money Regulatory Guidelines And Impact Ppt PowerPoint Presentation File Deck PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Collect Documents, Consumer Protection, Providers Products . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
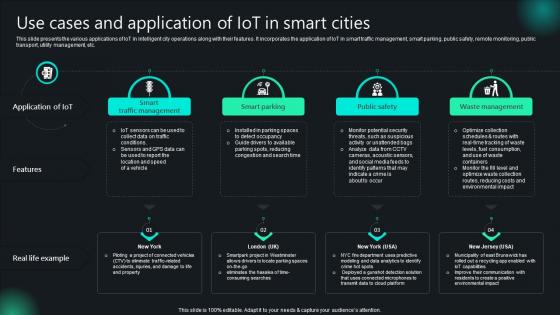
Use Cases And Application Of IoT In Smart Cities Unlocking Potential IoTs Application IoT SS V
This slide presents the various applications of IoT in intelligent city operations along with their features. It incorporates the application of IoT in smart traffic management, smart parking, public safety, remote monitoring, public transport, utility management, etc. Do you know about Slidesgeeks Use Cases And Application Of IoT In Smart Cities Unlocking Potential IoTs Application IoT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide presents the various applications of IoT in intelligent city operations along with their features. It incorporates the application of IoT in smart traffic management, smart parking, public safety, remote monitoring, public transport, utility management, etc.
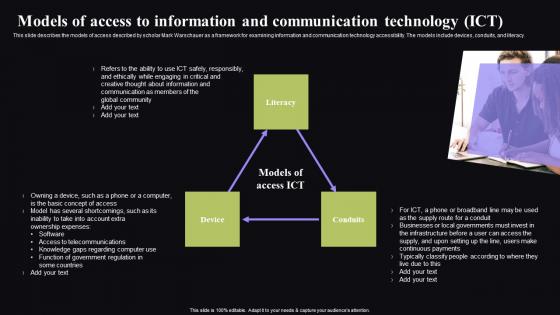
Models Of Access To Information Video Conferencing In Corporate Inspiration Pdf
This slide describes the models of access described by scholar Mark Warschauer as a framework for examining information and communication technology accessibility. The models include devices, conduits, and literacy. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Models Of Access To Information Video Conferencing In Corporate Inspiration Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide describes the models of access described by scholar Mark Warschauer as a framework for examining information and communication technology accessibility. The models include devices, conduits, and literacy.
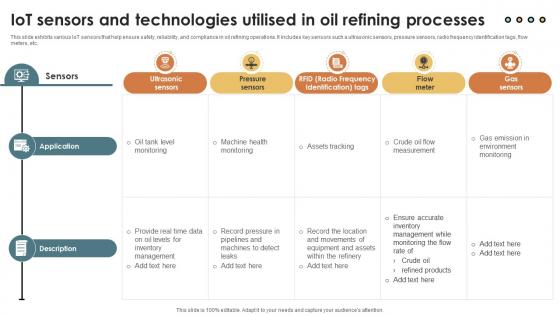
IoT Solutions For Oil IoT Sensors And Technologies Utilised In Oil Refining IoT SS V
This slide exhibits various IoT sensors that help ensure safety, reliability, and compliance in oil refining operations. It includes key sensors such a ultrasonic sensors, pressure sensors, radio frequency identification tags, flow meters, etc. Retrieve professionally designed IoT Solutions For Oil IoT Sensors And Technologies Utilised In Oil Refining IoT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide exhibits various IoT sensors that help ensure safety, reliability, and compliance in oil refining operations. It includes key sensors such a ultrasonic sensors, pressure sensors, radio frequency identification tags, flow meters, etc.
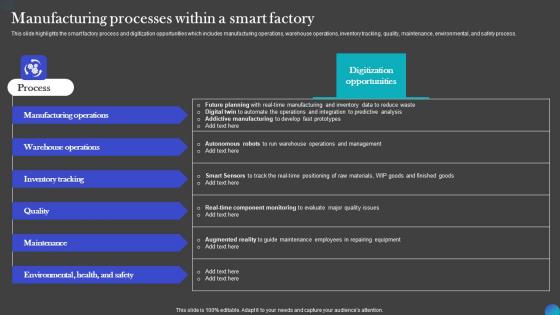
Manufacturing Processes Within A Smart Factory IOT Adoption Manufacturing Structure PDF
This slide highlights the smart factory process and digitization opportunities which includes manufacturing operations, warehouse operations, inventory tracking, quality, maintenance, environmental, and safety process. Presenting this PowerPoint presentation, titled Manufacturing Processes Within A Smart Factory IOT Adoption Manufacturing Structure PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Manufacturing Processes Within A Smart Factory IOT Adoption Manufacturing Structure PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Manufacturing Processes Within A Smart Factory IOT Adoption Manufacturing Structure PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide highlights the smart factory process and digitization opportunities which includes manufacturing operations, warehouse operations, inventory tracking, quality, maintenance, environmental, and safety process.

Approaches To Implement Advanced Cybersecurity Monitoring Plan Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fortyfour slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of seventy slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Cybersecurity Risk Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fifty eight slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Privacy Management Framework Example Of Ppt Presentation
This is a privacy management framework example of ppt presentation. This is a four stage process. The stages in this process are embed, stablish, evaluate, enhance.
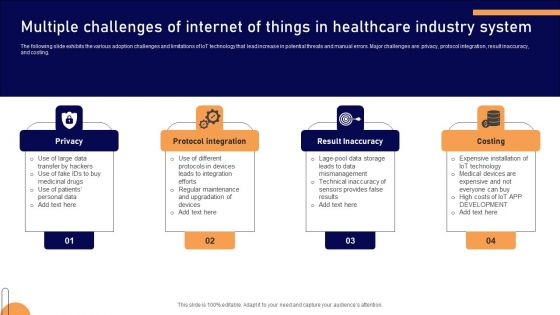
Multiple Challenges Of Internet Of Things In Healthcare Industry System Slides PDF
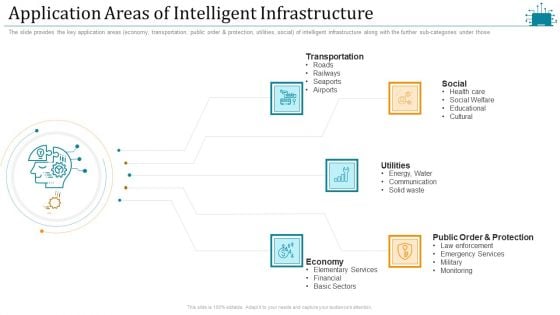
Cloud Intelligence Framework For Application Consumption Application Areas Of Intelligent Infrastructure Slides PDF
The slide provides the key application areas economy, transportation, public order and protection, utilities, social of intelligent infrastructure along with the further sub-categories under those. This is a cloud intelligence framework for application consumption application areas of intelligent infrastructure slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like social, communication, financial, public order protection, social welfare. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Smart Manufacturing With Iot Monitoring Safety Of Workers With Iot And Sensors Themes PDF
This slide describes monitoring workers safety through the internet of things and wearable sensors to prevent accidents or falls. The tags track workers location and wearable sensors monitor their heartbeat, temperature, galvanic skin reactions. The Smart Manufacturing With Iot Monitoring Safety Of Workers With Iot And Sensors Themes PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
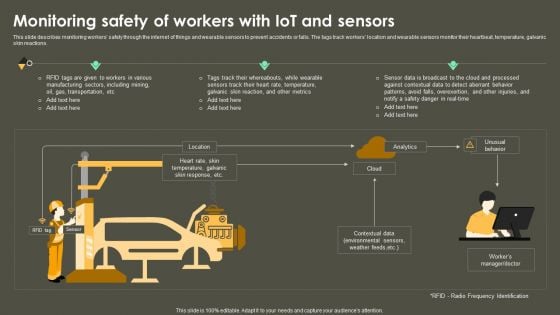
Iot Integration In Manufacturing Monitoring Safety Of Workers With Iot And Sensors Template PDF
This slide describes monitoring workers safety through the internet of things and wearable sensors to prevent accidents or falls. The tags track workers location and wearable sensors monitor their heartbeat, temperature, galvanic skin reactions. Slidegeeks is here to make your presentations a breeze with Iot Integration In Manufacturing Monitoring Safety Of Workers With Iot And Sensors Template PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
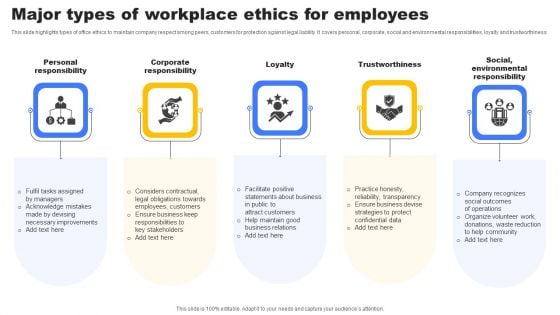
Major Types Of Workplace Ethics For Employees Themes PDF
This slide highlights types of office ethics to maintain company respect among peers, customers for protection against legal liability. It covers personal, corporate, social and environmental responsibilities, loyalty and trustworthiness. Presenting Major Types Of Workplace Ethics For Employees Themes PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Personal Responsibility, Corporate Responsibility, Loyalty . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
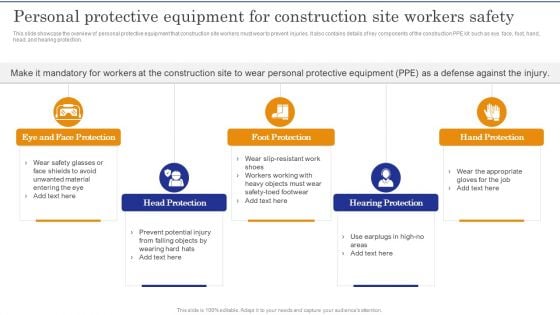
Construction Site Safety Measure Personal For Construction Site Workers Safety Infographics PDF
This slide showcase the overview of personal protective equipment that construction site workers must wear to prevent injuries. It also contains details of key components of the construction PPE kit such as eye, face, foot, hand, head, and hearing protection.Do you know about Slidesgeeks Construction Site Safety Measure Personal For Construction Site Workers Safety Infographics PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
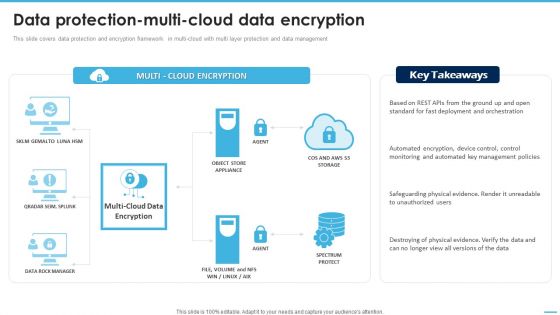
Data Protectionmulticloud Data Encryption Managing Complexity Of Multiple Cloud Platforms Introduction PDF
This slide covers data protection and encryption framework in multi-cloud with multi layer protection and data management. Find a pre-designed and impeccable Data Protectionmulticloud Data Encryption Managing Complexity Of Multiple Cloud Platforms Introduction PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Different Methods Of Blockchain Technology In Banking Ppt PowerPoint Presentation Gallery Icon PDF
Presenting different methods of blockchain technology in banking ppt powerpoint presentation gallery icon pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including management, cost effective, cyber crime reduction. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
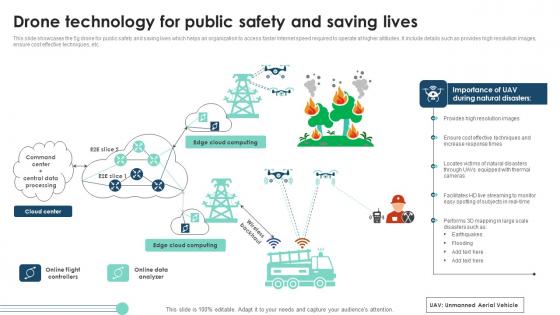
Drone Technology For Public Safety And Saving Lives Themes Pdf
This slide showcases the 5g drone for public safety and saving lives which helps an organization to access faster internet speed required to operate at higher altitudes. It include details such as provides high resolution images, ensure cost effective techniques, etc. Showcasing this set of slides titled Drone Technology For Public Safety And Saving Lives Themes Pdf The topics addressed in these templates are Cloud Center, Drone Technology, Saving Lives All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the 5g drone for public safety and saving lives which helps an organization to access faster internet speed required to operate at higher altitudes. It include details such as provides high resolution images, ensure cost effective techniques, etc.
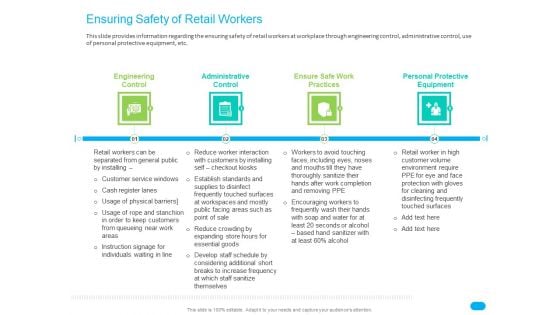
Post COVID Recovery Strategy For Retail Industry Ensuring Safety Of Retail Workers Slides PDF
This slide provides information regarding the ensuring safety of retail workers at workplace through engineering control, administrative control, use of personal protective equipment, etc. This is a post covid recovery strategy for retail industry ensuring safety of retail workers slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like engineering control, administrative control, ensure safe work practices, personal protective equipment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
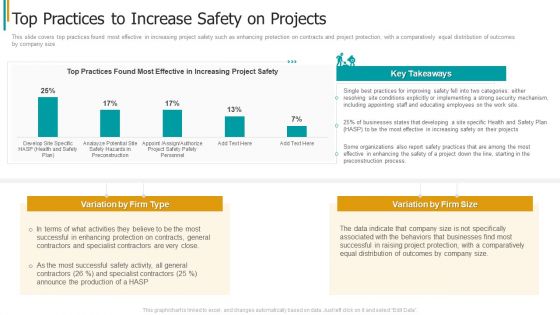
Construction Sector Project Risk Management Top Practices To Increase Safety On Projects Graphics PDF
This slide covers top practices found most effective in increasing project safety such as enhancing protection on contracts and project protection, with a comparatively equal distribution of outcomes by company size. Deliver and pitch your topic in the best possible manner with this construction sector project risk management top practices to increase safety on projects graphics pdf. Use them to share invaluable insights on process, organizations, effective, businesses, developing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Upgrading Total Project Safety IT Addressing Three Essential Attributes Of Information Associated Formats PDF
This slide provides information about essential attributes of information associated to IT project in terms of protecting confidentiality, ensuring integrity and maintaining availability. Presenting upgrading total project safety it addressing three essential attributes of information associated formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like protecting confidentiality, ensuring integrity, maintaining availability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
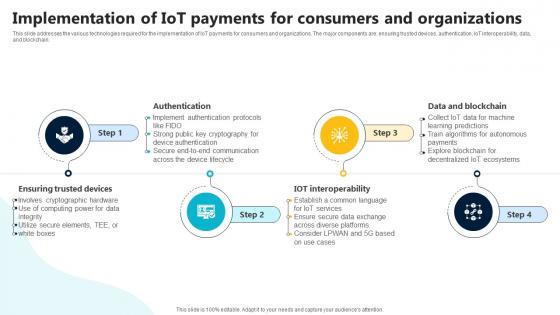
Implementation Of IoT Payments For Consumers In Depth Guide To Digital Wallets Fin SS V
This slide addresses the various technologies required for the implementation of IoT payments for consumers and organizations. The major components are ensuring trusted devices, authentication, IoT interoperability, data, and blockchain. This Implementation Of IoT Payments For Consumers In Depth Guide To Digital Wallets Fin SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide addresses the various technologies required for the implementation of IoT payments for consumers and organizations. The major components are ensuring trusted devices, authentication, IoT interoperability, data, and blockchain.
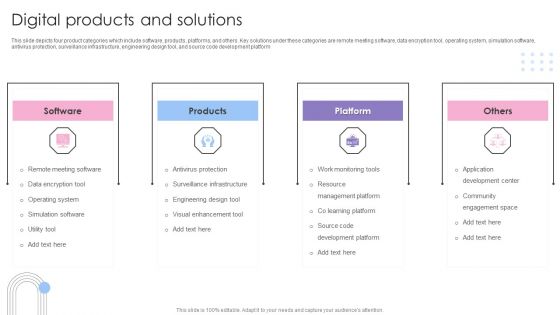
Software Products And Solutions Firm Details Digital Products And Solutions Slides PDF
This slide depicts four product categories which include software, products, platforms, and others. Key solutions under these categories are remote meeting software, data encryption tool, operating system, simulation software, antivirus protection, surveillance infrastructure, engineering design tool, and source code development platform. This is a Software Products And Solutions Firm Details Digital Products And Solutions Slides PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Software, Products, Platform, Others. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Robotic Surgery Devices For Smart Deploying IoT Solutions For Enhanced Healthcare Infographics Pdf
Following slide showcases surgical robots medical devices that uses technology for effective and authentic treatment. It includes elements such as overview, benefits and key statistics. Explore a selection of the finest Robotic Surgery Devices For Smart Deploying IoT Solutions For Enhanced Healthcare Infographics Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Robotic Surgery Devices For Smart Deploying IoT Solutions For Enhanced Healthcare Infographics Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Following slide showcases surgical robots medical devices that uses technology for effective and authentic treatment. It includes elements such as overview, benefits and key statistics.

Image Of Virus Concept In 3d Style PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Image Of Virus Concept In 3D Style PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Present our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides are the chords of your song. String them along and provide the lilt to your views. Download and present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download and present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are designed to help you succeed. They have all the ingredients you need.Use these PowerPoint slides for presentations relating to Internet Browser with Virus Symbol, Computer, Technology, Shapes, Business, Success. The prominent colors used in the PowerPoint template are Yellow, Gray, White. Dont let anybody mess up your presentation. Use our professional slides to win with our Image Of Virus Concept In 3d Style PowerPoint Templates Ppt Backgrounds For Slides 0213. You will be at the top of your game.
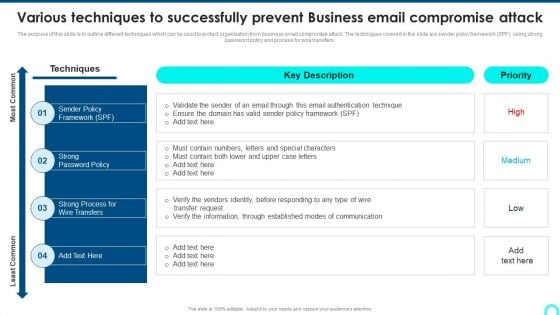
Various Techniques To Successfully Prevent Business Email Compromise Attack Sample PDF
The purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Deliver and pitch your topic in the best possible manner with this Various Techniques To Successfully Prevent Business Email Compromise Attack Sample PDF. Use them to share invaluable insights on Through Established, Authentication Technique, Through Established and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Trends In Business Management Template Ppt Design
This is a trends in business management template ppt design. This is a three stage process. The stages in this process are business strategy focus on growth, corporate strategy, preventing cyber attacks.

Global Digital Education Edtech Sector Laws And Regulations IR SS V
This slide showcases the EdTech industry laws and regulations which includes data privacy and protection, intellectual property, accessibility and consumer protection. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Global Digital Education Edtech Sector Laws And Regulations IR SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Global Digital Education Edtech Sector Laws And Regulations IR SS V today and make your presentation stand out from the rest This slide showcases the EdTech industry laws and regulations which includes data privacy and protection, intellectual property, accessibility and consumer protection.


 Continue with Email
Continue with Email

 Home
Home


































