Network Security

Healthcare Information Security Risk Management And Management Plan Information PDF
This slide shows information security risk treatment and acceptance plan for hospitals which can benefit them in securing their data. It contains details such as possession type, risk acceptance criteria, treating the risk, techniques and approaches for risk, residual risk acceptance measures, etc. Pitch your topic with ease and precision using this Healthcare Information Security Risk Management And Management Plan Information PDF. This layout presents information on Measures, Risk Acceptance Criteria, Treating The Risk. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Data Security Management Tool Assessment Matrix Microsoft PDF
This slide highlights a tools comparison matrix for data security governance and management. It includes key components such as threat intelligence, advanced data governance, source score, data helpdesk, price and customer satisfaction. Persuade your audience using this Data Security Management Tool Assessment Matrix Microsoft PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Threat Intelligence, Advanced Data Governance, Secure Score. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
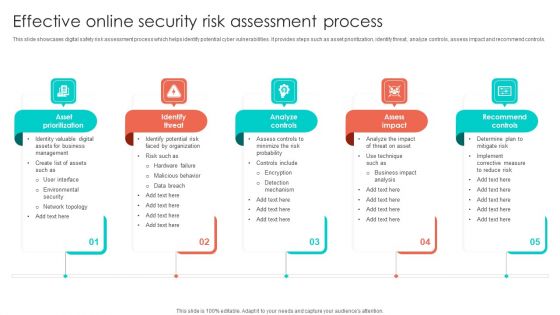
Effective Online Security Risk Assessment Process Inspiration PDF
This slide showcases digital safety risk assessment process which helps identify potential cyber vulnerabilities. It provides steps such as asset prioritization, identify threat, analyze controls, assess impact and recommend controls. Persuade your audience using this Effective Online Security Risk Assessment Process Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Card Data Security, Cross Border Transactions, Payment Methods. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
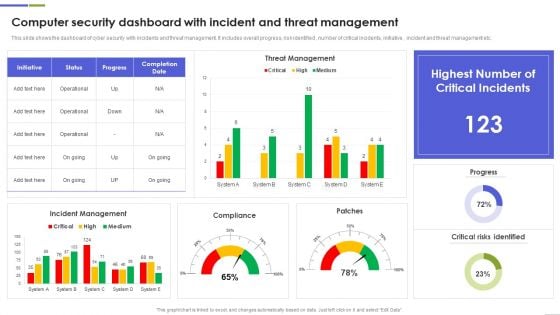
Computer Security Dashboard With Incident And Threat Management Rules PDF
This slide shows the dashboard of cyber security with incidents and threat management. It includes overall progress, risk identified , number of critical incidents, initiative , incident and threat management etc.Showcasing this set of slides titled Computer Security Dashboard With Incident And Threat Management Rules PDF The topics addressed in these templates are Critical Incidents, Risks Identified, Compliance All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Security Hacker Dashboard For Threat Tracking Rules PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report.Deliver an awe inspiring pitch with this creative IT Security Hacker Dashboard For Threat Tracking Rules PDF bundle. Topics like Threat Dashboard, Loss Of Information, Regulations And Contracts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Security Team Analytics Dashboard With KPI Themes PDF
This slide elaborates about the number of incidents that have taken place in cyber security and the malware types with per incident. It also includes the number of open and resolved ticked. Showcasing this set of slides titled Information Technology Security Team Analytics Dashboard With KPI Themes PDF. The topics addressed in these templates are Open Incidents, Resolved Incidents, Open Tickets, Resolved Tickets. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Defense Plan Maturity Evaluation Information PDF
This slide represents cyber security defense strategy maturity evaluation mode illustrating culture and organization, governance, visibility and controls, focused defense and intelligence operations. Persuade your audience using this IT Security Defense Plan Maturity Evaluation Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization, Focused Defense, Intelligence Operations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
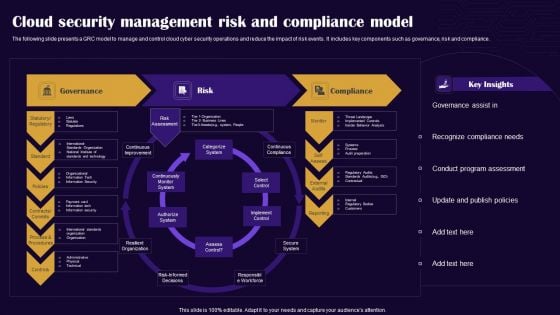
Cloud Security Management Risk And Compliance Model Summary PDF
The following slide presents a GRC model to manage and control cloud cyber security operations and reduce the impact of risk events. It includes key components such as governance, risk and compliance. Showcasing this set of slides titled Cloud Security Management Risk And Compliance Model Summary PDF. The topics addressed in these templates are Governance, Risk, Compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
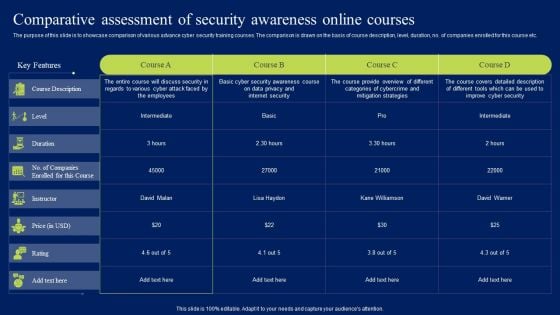
Comparative Assessment Of Security Awareness Online Courses Template PDF
The purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. Find a pre-designed and impeccable Comparative Assessment Of Security Awareness Online Courses Template PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
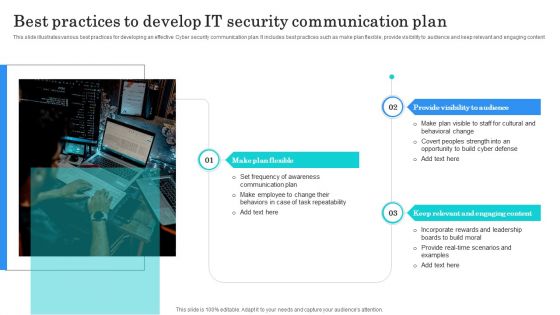
Best Practices To Develop IT Security Communication Plan Diagrams PDF
This slide illustrates various best practices for developing an effective Cyber security communication plan. It includes best practices such as make plan flexible, provide visibility to audience and keep relevant and engaging content. Presenting Best Practices To Develop IT Security Communication Plan Diagrams PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Make Plan Flexible, Provide Visibility Audience, Keep Relevant Engaging. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
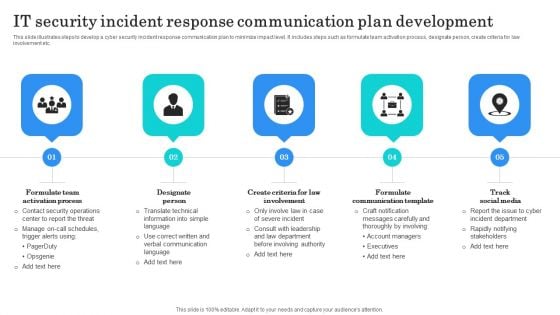
IT Security Incident Response Communication Plan Development Background PDF
This slide illustrates steps to develop a cyber security incident response communication plan to minimize impact level. It includes steps such as formulate team activation process, designate person, create criteria for law involvement etc. Presenting IT Security Incident Response Communication Plan Development Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Team Activation, Designate Person, Formulate Communication Template. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
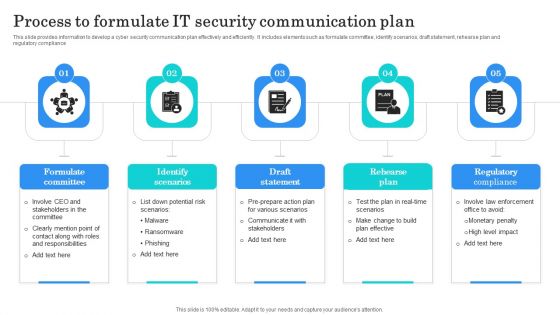
Process To Formulate IT Security Communication Plan Clipart PDF
This slide provides information to develop a cyber security communication plan effectively and efficiently. It includes elements such as formulate committee, identify scenarios, draft statement, rehearse plan and regulatory compliance. Presenting Process To Formulate IT Security Communication Plan Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Committee, Identify Scenarios, Draft Statement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
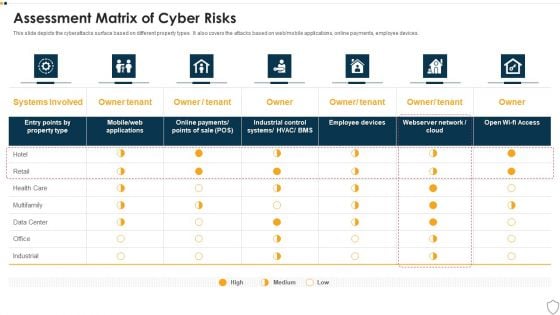
IT Security Assessment Matrix Of Cyber Risks Infographics PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative it security assessment matrix of cyber risks infographics pdf bundle. Topics like data center, industrial, retail, health care can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Disaster Recovery Planning Element Of Cyber Security Template PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. It also contains the types of disaster recovery plans and planning process. Slidegeeks is here to make your presentations a breeze with Disaster Recovery Planning Element Of Cyber Security Template PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Insurance Agent Protection Security PowerPoint Templates And PowerPoint Backgrounds 0711
Microsoft PowerPoint Template and Background with in the field giving you the best protection Presentation to a sizable audience. We've got your back with our Insurance Agent Protection Security PowerPoint Templates And PowerPoint Backgrounds 0711. You'll always stay ahead of the game.
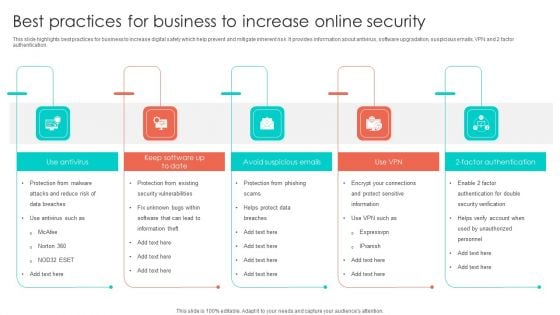
Best Practices For Business To Increase Online Security Introduction PDF
This slide highlights best practices for business to increase digital safety which help prevent and mitigate inherent risk. It provides information about antivirus, software upgradation, suspicious emails, VPN and 2 factor authentication. Presenting Best Practices For Business To Increase Online Security Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Vulnerabilities, Factor Authentication, Avoid Suspicious Emails. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
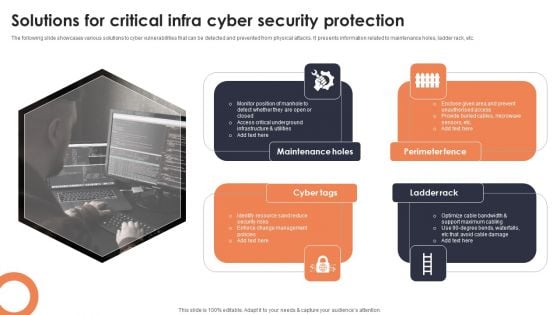
Solutions For Critical Infra Cyber Security Protection Download PDF
The following slide showcases various solutions to cyber vulnerabilities that can be detected and prevented from physical attacks. It presents information related to maintenance holes, ladder rack, etc. Presenting Solutions For Critical Infra Cyber Security Protection Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Maintenance Holes, Perimeter Fence, Ladder Rack . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
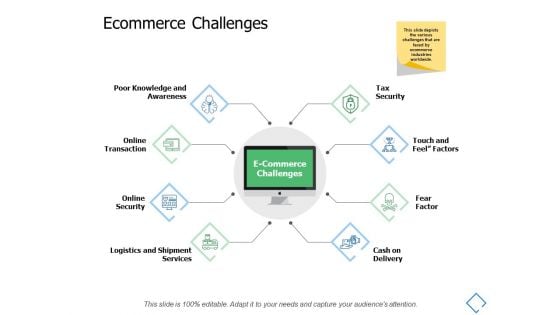
Ecommerce Challenges Online Security Ppt PowerPoint Presentation Styles Gridlines
Presenting this set of slides with name ecommerce challenges online security ppt powerpoint presentation styles gridlines. This is a eight stage process. The stages in this process are process, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Ecommerce Challenges Online Security Ppt PowerPoint Presentation Icon Show
Presenting this set of slides with name ecommerce challenges online security ppt powerpoint presentation icon show. This is a eight stage process. The stages in this process are process, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
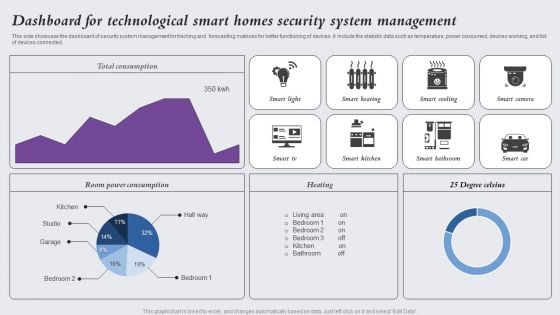
Dashboard For Technological Smart Homes Security System Management Designs PDF
This side showcase the dashboard of security system management for tracking and forecasting matrices for better functioning of devices. It include the statistic data such as temperature, power consumed, devices working, and list of devices connected. Showcasing this set of slides titled Dashboard For Technological Smart Homes Security System Management Designs PDF. The topics addressed in these templates are Smart Light, Smart Heating, Smart Cooling. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Comparative Analysis Of Vulnerability Scanning Application Security Testing
This slide showcases the difference between vulnerability scanning and penetration testing based on aspects such as nature, purpose, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Comparative Analysis Of Vulnerability Scanning Application Security Testing and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases the difference between vulnerability scanning and penetration testing based on aspects such as nature, purpose, etc.

Difference Between Authentication And Authorization Application Security Testing
This slide showcase the difference between authentication and authorization in application security on aspects such as purpose, operation, etc. This modern and well-arranged Difference Between Authentication And Authorization Application Security Testing provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide showcase the difference between authentication and authorization in application security on aspects such as purpose, operation, etc.
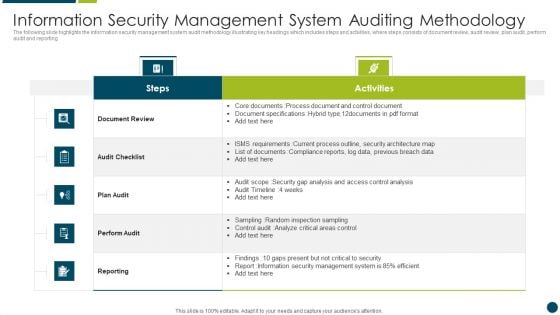
Information Security Management System Auditing Methodology Download PDF
The following slide highlights the information security system audit framework illustrating key headings which includes act, plan, do and check which are used for update and improve isms, establish isms, implement policy and control and monitor and review performance Presenting Information Security Management System Auditing Methodology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Analysis, Data, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Home Security System Vector Icon Ppt PowerPoint Presentation File Influencers
Presenting this set of slides with name home security system vector icon ppt powerpoint presentation file influencers. This is a four stage process. The stages in this process are iot icon, smartphone vector, headphones. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
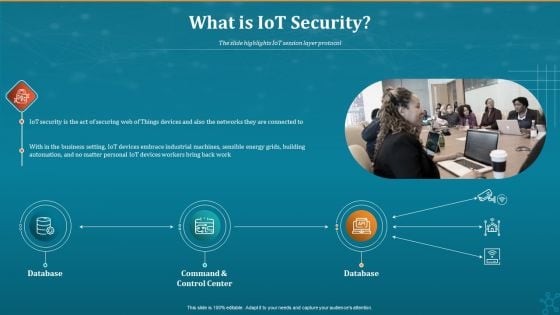
Machine To Machine Communication What Is Iot Security Portrait PDF
The slide highlights IoT session layer protocol.This is a machine to machine communication what is iot security portrait pdf. template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like database, command and control center. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Computer Security Incident Handling Cybersecurity Management Action Plan Graphics PDF
Presenting this set of slides with name computer security incident handling cybersecurity management action plan graphics pdf. The topics discussed in these slides are risk identification, risk treatment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Cybersecurity Risk Management Worksheet Ideas PDF
Presenting this set of slides with name computer security incident handling cybersecurity risk management worksheet ideas pdf. The topics discussed in these slides are identified risk, risk likelihood, risk severity, implement controls, risk treatment, responsible person. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Present Concerns Impeding Cybersecurity Formats PDF
Presenting this set of slides with name computer security incident handling present concerns impeding cybersecurity formats pdf. The topics discussed in these slides are reported financial losses due to increase in cybercrimes, data branches and records exposed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Digital Banking Security Management Technology Trends Introduction PDF
The following slide provides the integration of security technology with banking which helps to provide improved and enhanced customer experience. Key components are login protection, artificial intelligence and cloud computing. Presenting Digital Banking Security Management Technology Trends Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Login Protection, Ai, Cloud Computing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
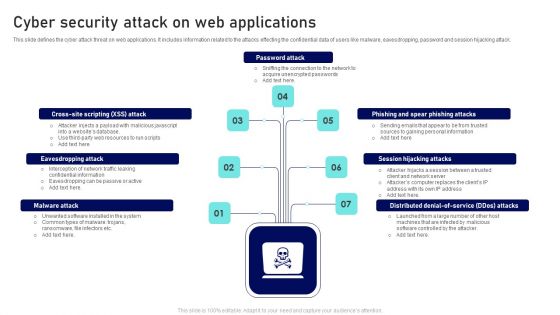
Cyber Security Attack On Web Applications Ppt Outline Files PDF
This slide defines the cyber attack threat on web applications. It includes information related to the attacks effecting the confidential data of users like malware, eavesdropping, password and session hijacking attack. Presenting Cyber Security Attack On Web Applications Ppt Outline Files PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Password Attack, Session Hijacking Attacks, Eavesdropping Attack. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
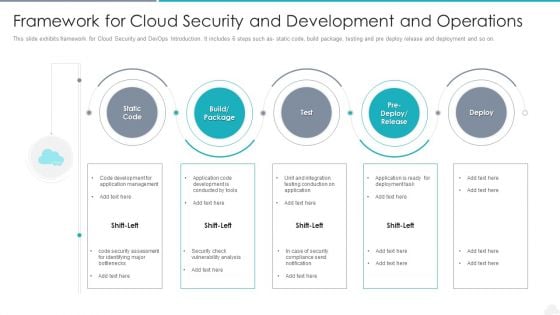
Framework For Cloud Security And Development And Operations Elements PDF
Presenting framework for cloud security and development and operations elements pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including management, application, development. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
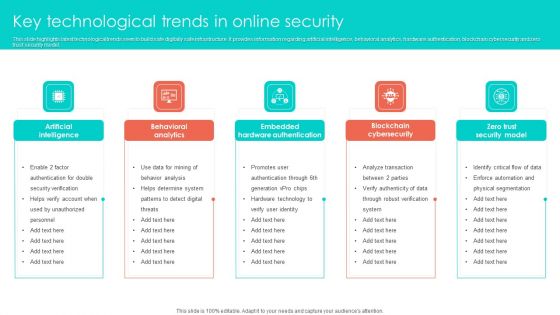
Key Technological Trends In Online Security Clipart PDF
This slide highlights latest technological trends seen to build safe digitally safe infrastructure. It provides information regarding artificial intelligence, behavioral analytics, hardware authentication, blockchain cybersecurity and zero trust security model. Persuade your audience using this Key Technological Trends In Online Security Clipart PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Behavioral Analytics, Artificial Intelligence, Embedded Hardware Authentication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
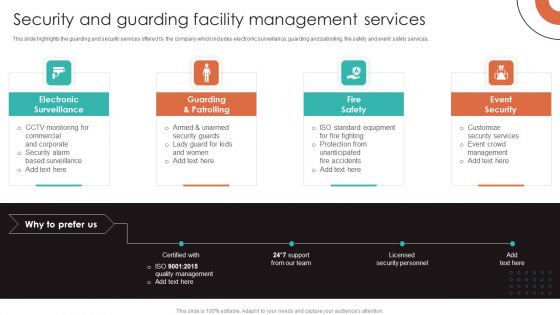
Security And Guarding Facility Management Services Introduction PDF
This slide highlights the guarding and security services offered by the company which includes electronic surveillance, guarding and patrolling, fire safety and event safety services. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Security And Guarding Facility Management Services Introduction PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Security And Guarding Facility Management Services Introduction PDF today and make your presentation stand out from the rest.

Cloud Computing Application Security Architecture Audit Checklist Structure PDF
The slide shows a checklist containing number of tasks needed to be done while performing application security audit. It includes tasks like developing password policies, making multi factor confirmation mandatory, supervising SaaS license, etc. Showcasing this set of slides titled Cloud Computing Application Security Architecture Audit Checklist Structure PDF. The topics addressed in these templates are Develop Password Policies, Validate Anti Attacking Protections, Set Message Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
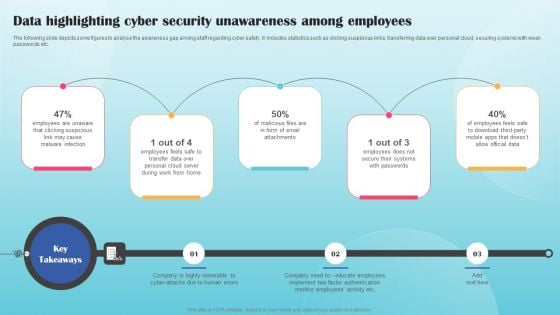
Data Highlighting Cyber Security Unawareness Among Employees Summary PDF
The following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Create an editable Data Highlighting Cyber Security Unawareness Among Employees Summary PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Data Highlighting Cyber Security Unawareness Among Employees Summary PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Allocating Budget For Information Security Risk Management Programme Brochure PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for area like cybersecurity awareness, threat detection and risk management.The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Allocating Budget For Information Security Risk Management Programme Brochure PDF from Slidegeeks and deliver a wonderful presentation.
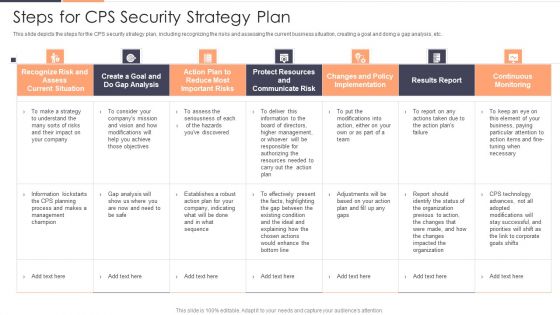
Steps For CPS Security Strategy Plan Ppt Pictures Portfolio PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Deliver and pitch your topic in the best possible manner with this Steps For CPS Security Strategy Plan Ppt Pictures Portfolio PDF. Use them to share invaluable insights on Recognize Risk, Communicate Risk, Protect Resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
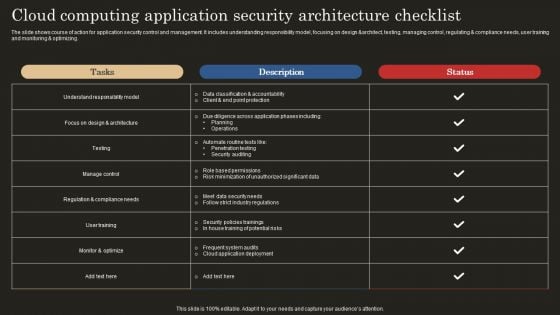
Cloud Computing Application Security Architecture Checklist Template PDF
The slide shows course of action for application security control and management. It includes understanding responsibility model, focusing on design andarchitect, testing, managing control, regulating and compliance needs, user training and monitoring and optimizing. Showcasing this set of slides titled Cloud Computing Application Security Architecture Checklist Template PDF. The topics addressed in these templates are Data Classification Accountability, Client Point Protection, Penetration Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Automation Dashboard Highlighting Resolved Events And Workload Diagrams PDF
This slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. Explore a selection of the finest Security Automation Dashboard Highlighting Resolved Events And Workload Diagrams PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Security Automation Dashboard Highlighting Resolved Events And Workload Diagrams PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
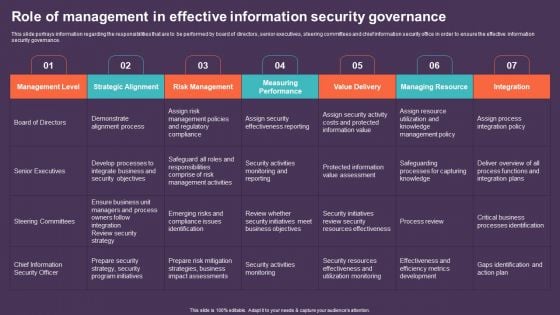
Role Of Management In Effective Information Security Governance Topics PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Slidegeeks has constructed Role Of Management In Effective Information Security Governance Topics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Role Of Management In Security Governance Across Firm Summary PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Explore a selection of the finest Role Of Management In Security Governance Across Firm Summary PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Role Of Management In Security Governance Across Firm Summary PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
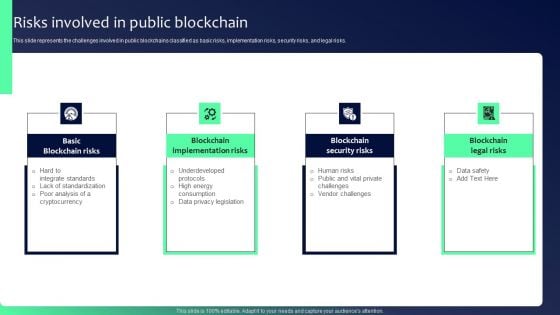
Blockchain Security Solutions Deployment Risks Involved In Public Rules PDF
This slide represents the challenges involved in public blockchains classified as basic risks, implementation risks, security risks, and legal risks. Are you searching for a Blockchain Security Solutions Deployment Risks Involved In Public Rules PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Blockchain Security Solutions Deployment Risks Involved In Public Rules PDF from Slidegeeks today.
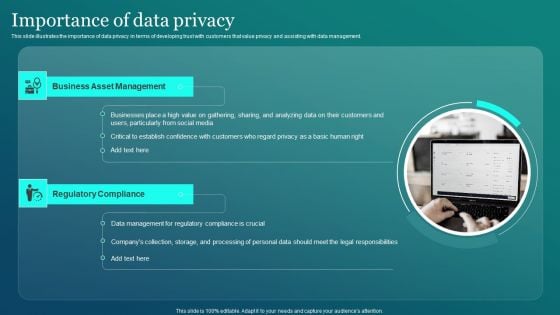
Information Security Importance Of Data Privacy Demonstration PDF
This slide illustrates the importance of data privacy in terms of developing trust with customers that value privacy and assisting with data management. Explore a selection of the finest Information Security Importance Of Data Privacy Demonstration PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Security Importance Of Data Privacy Demonstration PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
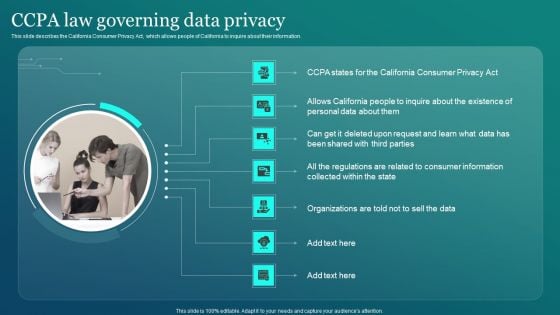
Information Security CCPA Law Governing Data Privacy Clipart PDF
This slide describes the California Consumer Privacy Act, which allows people of California to inquire about their information. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information Security CCPA Law Governing Data Privacy Clipart PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information Security CCPA Law Governing Data Privacy Clipart PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Information Security Data Privacy In Financial Institutions Mockup PDF
This slide represents the data privacy in financial institutions which decreases the possibility of fines and reputational damage as a result of unlawful disclosure. This Information Security Data Privacy In Financial Institutions Mockup PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Information Security Data Privacy In Financial Institutions Mockup PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Asset Identification For Information Security Risk Management Topics PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack This is a Asset Identification For Information Security Risk Management Topics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customers Database, Products Database, Sales Database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
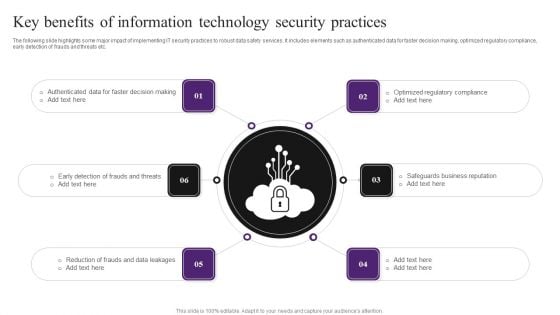
Key Benefits Of Information Technology Security Practices Summary PDF
The following slide highlights some major impact of implementing IT security practices to robust data safety services. It includes elements such as authenticated data for faster decision making, optimized regulatory compliance, early detection of frauds and threats etc. Presenting Key Benefits Of Information Technology Security Practices Summary PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Data Leakages, Reduction Of Frauds, Safeguards Business Reputation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
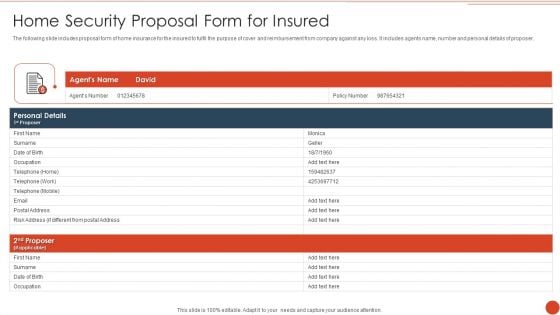
Home Security Proposal Form For Insured Elements PDF
The following slide includes proposal form of home insurance for the insured to fulfil the purpose of cover and reimbursement from company against any loss. It includes agents name, number and personal details of proposer. Showcasing this set of slides titled Home Security Proposal Form For Insured Elements PDF. The topics addressed in these templates are Home Security, Proposal Form Insured. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
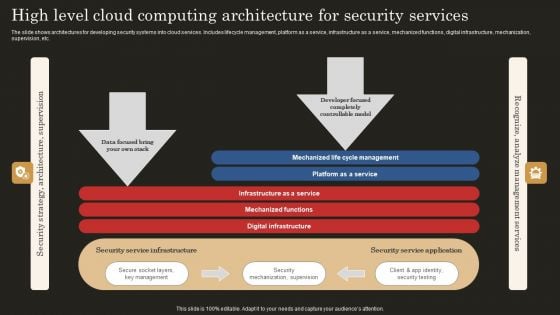
High Level Cloud Computing Architecture For Security Services Ideas PDF
The slide shows architectures for developing security systems into cloud services. Includes lifecycle management, platform as a service, infrastructure as a service, mechanized functions, digital infrastructure, mechanization, supervision, etc. Showcasing this set of slides titled High Level Cloud Computing Architecture For Security Services Ideas PDF. The topics addressed in these templates are Infrastructure Service, Mechanized Functions, Digital Infrastructure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
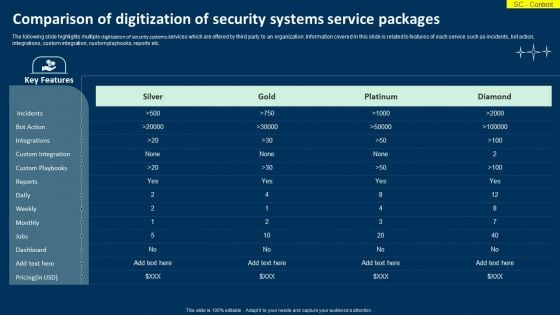
Comparison Of Digitization Of Security Systems Service Packages Information PDF
The following slide highlights multiple digitization of security systems services which are offered by third party to an organization. Information covered in this slide is related to features of each service such as incidents, bot action, integrations, custom integration, custom playbooks, reports etc. Showcasing this set of slides titled Comparison Of Digitization Of Security Systems Service Packages Information PDF. The topics addressed in these templates are Key Features, Custom Integration, Custom Playbooks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
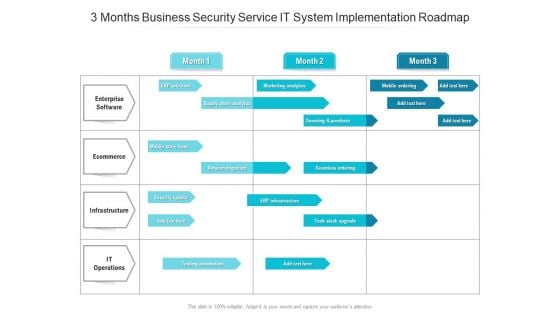
3 Months Business Security Service IT System Implementation Roadmap Rules
We present our 3 months business security service it system implementation roadmap rules. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched 3 months business security service it system implementation roadmap rules in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
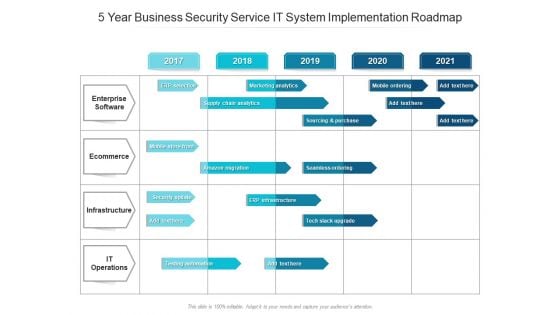
5 Year Business Security Service IT System Implementation Roadmap Information
We present our 5 year business security service it system implementation roadmap information. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched 5 year business security service it system implementation roadmap information in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

6 Months Business Security Service IT System Implementation Roadmap Slides
We present our 6 months business security service it system implementation roadmap slides. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched 6 months business security service it system implementation roadmap slides in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Half Yearly Business Security Service IT System Implementation Roadmap Icons
We present our half yearly business security service it system implementation roadmap icons. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched half yearly business security service it system implementation roadmap icons in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
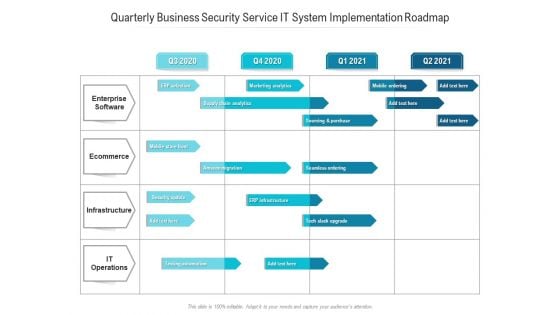
Quarterly Business Security Service IT System Implementation Roadmap Template
We present our quarterly business security service it system implementation roadmap template. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched quarterly business security service it system implementation roadmap template in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
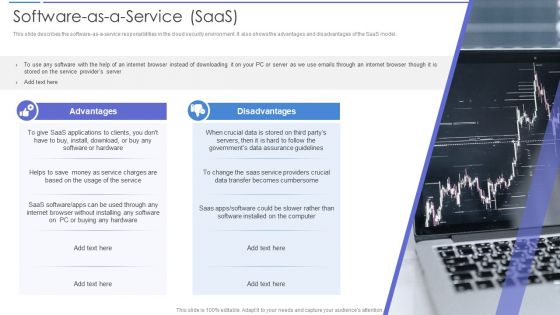
Cloud Data Security Software As A Service Saas Portrait PDF
This slide describes the software as a service responsibilities in the cloud security environment. It also shows the advantages and disadvantages of the SaaS model. Presenting Cloud Data Security Software As A Service Saas Portrait PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Advantages, Disadvantages. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
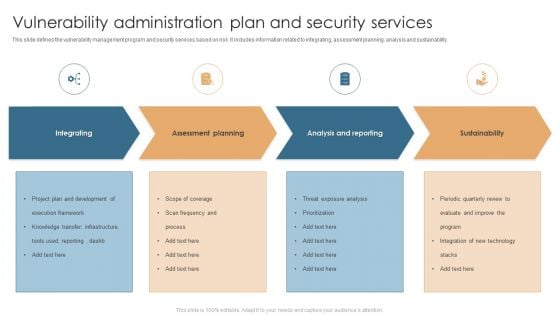
Vulnerability Administration Plan And Security Services Topics PDF
This slide defines the vulnerability management program and security services based on risk. It includes information related to integrating, assessment planning, analysis and sustainability. Persuade your audience using this Vulnerability Administration Plan And Security Services Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Integrating, Assessment Planning, Analysis And Reporting, Sustainability. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Scope For Security Camera Services One Pager Sample Example Document
This slide depicts the project scope providing information about the multiple activities to be performed by the bidding company for the client. Presenting you an exemplary Scope For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Scope For Security Camera Services One Pager Sample Example Document brilliant piece now.

Data Security Agreement Operate Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name data security agreement operate ppt powerpoint presentation complete deck. The topics discussed in these slides are operate, data, accountability framework, data privacy, public interest, risk assessment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
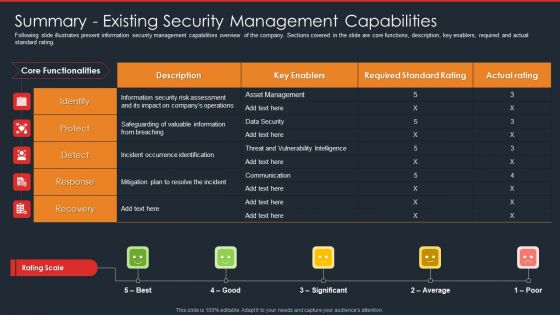
Data Safety Initiatives Summary Existing Security Management Capabilities Topics PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver and pitch your topic in the best possible manner with this data safety initiatives summary existing security management capabilities topics pdf. Use them to share invaluable insights on key enablers, rating scale, incident occurrence identification, asset management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































