Network Security
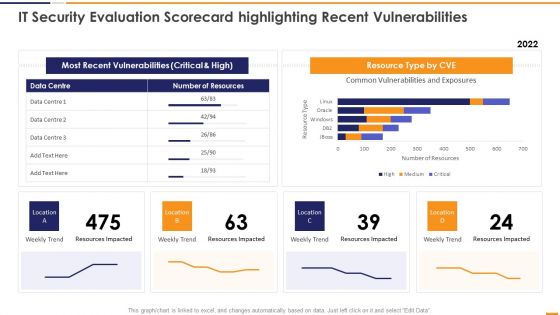
IT Security Evaluation Scorecard Highlighting Recent Vulnerabilities Introduction PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard Highlighting Recent Vulnerabilities Introduction PDF bundle. Topics like Most Recent Vulnerabilities, Resource Type CVE, Weekly Trend Location can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
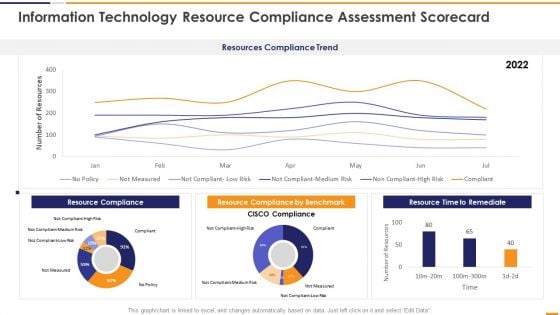
IT Security Evaluation Scorecard Information Technology Resource Compliance Background PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard Information Technology Resource Compliance Background PDF. Use them to share invaluable insights on Resources Compliance Trend, Resource Compliance 2022, Resource Compliance Benchmark, Resource Time Remediate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
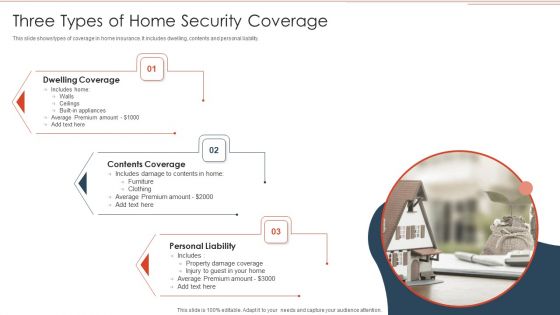
Three Types Of Home Security Coverage Demonstration PDF
This slide shows types of coverage in home insurance. It includes dwelling, contents and personal liability. Showcasing this set of slides titled Three Types Of Home Security Coverage Demonstration PDF. The topics addressed in these templates are Contents Coverage, Dwelling Coverage, Personal Liability. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Security Threats Contract Breaches With Clients Download PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Presenting Cloud Security Threats Contract Breaches With Clients Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Organization, Business Partners, Information Could. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
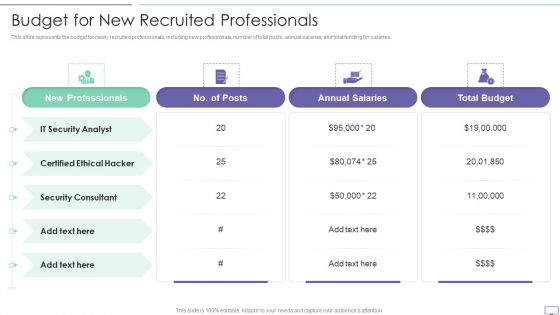
IT Security Hacker Budget For New Recruited Professionals Infographics PDF
This slide represents the budget for newly recruited professionals, including new professionals, number of total posts, annual salaries, and total funding for salaries.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Budget For New Recruited Professionals Infographics PDF. Use them to share invaluable insights on New Professionals, Certified Ethical, Annual Salaries and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
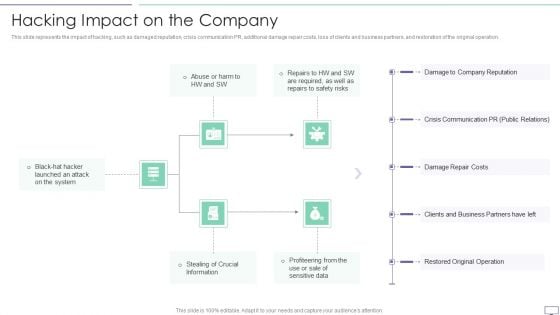
IT Security Hacker Hacking Impact On The Company Information PDF
This slide represents the impact of hacking, such as damaged reputation, crisis communication PR, additional damage repair costs, loss of clients and business partners, and restoration of the original operation. Deliver an awe inspiring pitch with this creative IT Security Hacker Hacking Impact On The Company Information PDF bundle. Topics like Company Reputation, Crisis Communication, Damage Repair can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
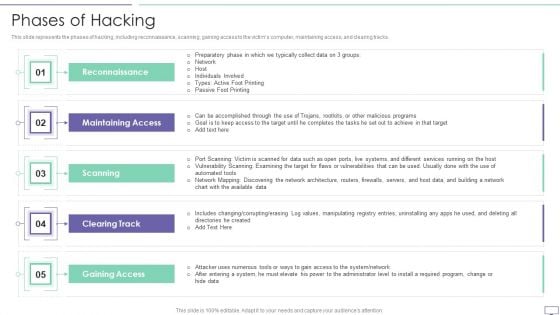
IT Security Hacker Phases Of Hacking Topics PDF
This slide represents the phases of hacking, including reconnaissance, scanning, gaining access to the victims computer, maintaining access, and clearing tracks.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Phases Of Hacking Topics PDF. Use them to share invaluable insights on Maintaining Access, Reconnaissance, Gaining Access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
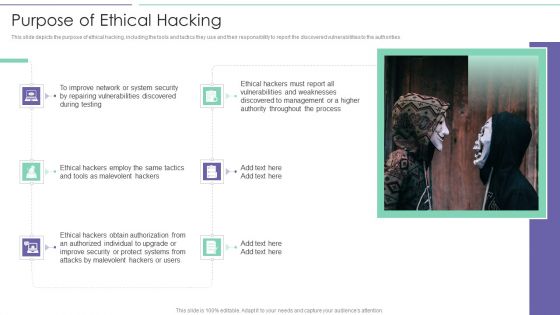
IT Security Hacker Purpose Of Ethical Hacking Slides PDF
This slide depicts the purpose of ethical hacking, including the tools and tactics they use and their responsibility to report the discovered vulnerabilities to the authorities.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Purpose Of Ethical Hacking Slides PDF. Use them to share invaluable insights on Vulnerabilities Discovered, Malevolent Hackers, Malevolent Hackers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
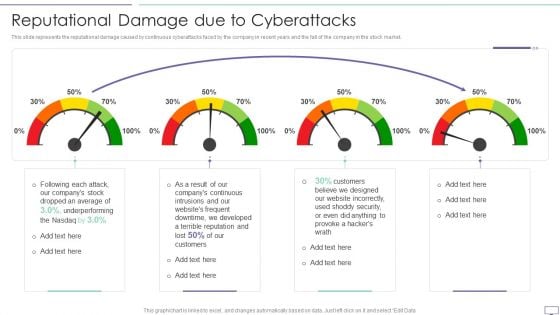
IT Security Hacker Reputational Damage Due To Cyberattacks Guidelines PDF
This slide represents the reputational damage caused by continuous cyberattacks faced by the company in recent years and the fall of the company in the stock market.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Reputational Damage Due To Cyberattacks Guidelines PDF. Use them to share invaluable insights on Website Incorrectly, Underperforming, Dropped An Average and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For IT Security Hacker Background PDF
This is a Table Of Contents For IT Security Hacker Background PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Current Situation, Impact Of Hacking, Repairing Damages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
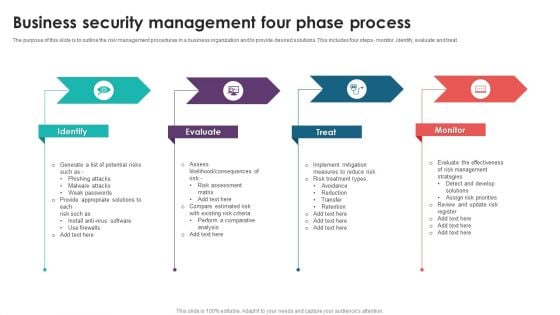
Business Security Management Four Phase Process Topics PDF
The purpose of this slide is to outline the risk management procedures in a business organization and to provide desired solutions. This includes four steps- monitor, identify, evaluate and treat. Presenting Business Security Management Four Phase Process Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Identify, Evaluate, Treat, Monitor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
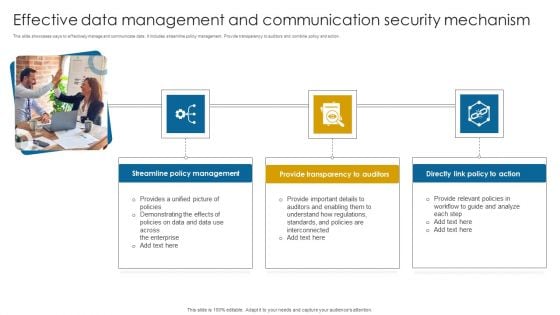
Effective Data Management And Communication Security Mechanism Themes PDF
This slide showcases ways to effectively manage and communicate data. It includes streamline policy management. Provide transparency to auditors and combine policy and action. Presenting Effective Data Management And Communication Security Mechanism Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Streamline Policy Management, Provide Transparency, Directly Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
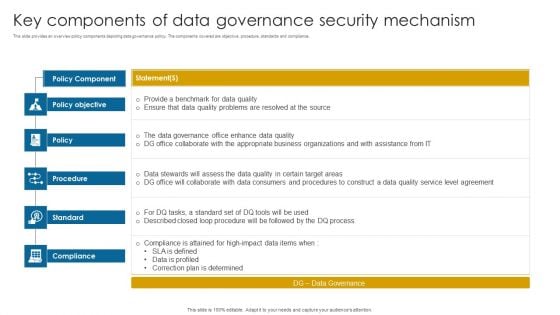
Key Components Of Data Governance Security Mechanism Information PDF
This slide provides an overview policy components depicting data governance policy. The components covered are objective, procedure, standards and compliance.Pitch your topic with ease and precision using this Key Components Of Data Governance Security Mechanism Information PDF. This layout presents information on Data Governance, Compliance Attained, Correction Determined. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Agenda Security Automation To Analyze And Mitigate Cyberthreats Brochure PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Agenda Security Automation To Analyze And Mitigate Cyberthreats Brochure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Information Systems Security And Risk Management Plan Quotes Guidelines PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Systems Security And Risk Management Plan Quotes Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Timeframe For Incident Management In Security Centre Portrait PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Timeframe For Incident Management In Security Centre Portrait PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
Security Software Company Investor Funding Pitch Deck Quotes Background PDF
This Security Software Company Investor Funding Pitch Deck Quotes Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
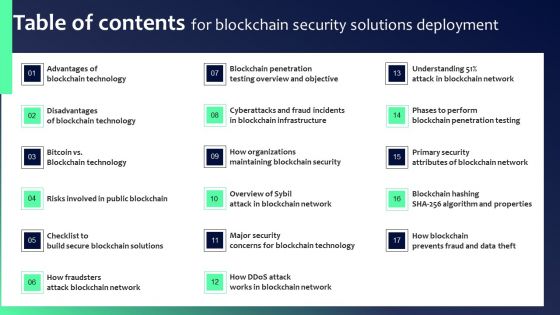
Table Of Contents For Blockchain Security Solutions Deployment Ideas PDF
Slidegeeks has constructed Table Of Contents For Blockchain Security Solutions Deployment Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Emergency Security Theme PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Emergency Security Theme PowerPoint Templates PPT Backgrounds For Slides 0413.Present our Shapes PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds. Use our Business PowerPoint Templates because You should Throw the gauntlet with our PowerPoint Templates and Slides. They are created to take up any challenge. Download and present our Success PowerPoint Templates because Our PowerPoint Templates and Slides team portray an attitude of elegance. Personify this quality by using them regularly. Use our Finance PowerPoint Templates because Our PowerPoint Templates and Slides help you meet the demand of the Market. Just browse and pick the slides that appeal to your intuitive senses. Download our People PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas.Use these PowerPoint slides for presentations relating to Emergency security, people, shapes, business, success, finance. The prominent colors used in the PowerPoint template are Blue, White, Red. Propose awesome plans with our Emergency Security Theme PowerPoint Templates Ppt Backgrounds For Slides 0413. Download without worries with our money back guaranteee.
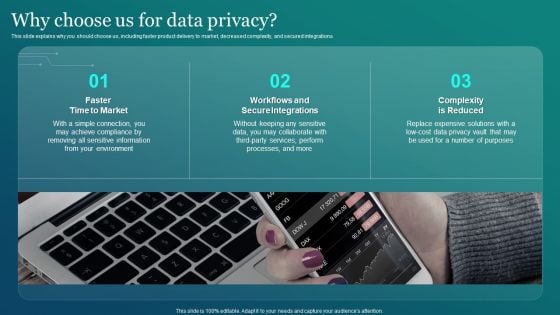
Information Security Why Choose Us For Data Privacy Graphics PDF
This slide explains why you should choose us, including faster product delivery to market, decreased complexity, and secured integrations. Slidegeeks is here to make your presentations a breeze with Information Security Why Choose Us For Data Privacy Graphics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Online Security Training Program For Employees Background PDF
This slide represents digital safety training program courses used to spread awareness amongst employees. It provides information regarding courses offered, delivery mode, duration, trainer and certification. Pitch your topic with ease and precision using this Online Security Training Program For Employees Background PDF. This layout presents information on Digital Risk Analysis, Securing Data And Information, Employees. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
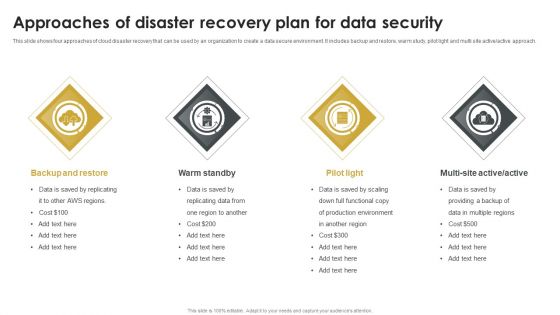
Approaches Of Disaster Recovery Plan For Data Security Topics PDF
This slide shows four approaches of cloud disaster recovery that can be used by an organization to create a data secure environment. It includes backup and restore, warm study, pilot light and multi site active or active approach. Presenting Approaches Of Disaster Recovery Plan For Data Security Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Warm Standby, Backup And Restore, Pilot Light. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
7 Stages Of Functional Information Security Business Plan PowerPoint Slides
We present our 7 stages of functional information security business plan PowerPoint Slides .Download and present our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Download our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time. Present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download and present our Flow Charts PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination.Use these PowerPoint slides for presentations relating to Abstract, arrows, balance, business, chart, company, concept, data, diagram, document, finance, financial, report, graph, market, marketing, price, profit, report, statistics, stock, success, trade, work. The prominent colors used in the PowerPoint template are Purple, White, Gray. Presenters tell us our 7 stages of functional information security business plan PowerPoint Slides are designed by professionals Customers tell us our business PowerPoint templates and PPT Slides are designed by professionals Professionals tell us our 7 stages of functional information security business plan PowerPoint Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. Professionals tell us our concept PowerPoint templates and PPT Slides will impress their bosses and teams. Presenters tell us our 7 stages of functional information security business plan PowerPoint Slides are designed by a team of presentation professionals. People tell us our balance PowerPoint templates and PPT Slides will save the presenter time. Ask any favour of our 7 Stages Of Functional Information Security Business Plan PowerPoint Slides. You will find them truly accomodating.

Key Benefits Of Implementing Online Security Management System Infographics PDF
This slide showcases key benefits of implementing digital safety management system which help focus on higher priority business tasks. It provides information regarding quality data, improves productivity, compliance requirements, minimize error and reporting and tracking. Presenting Key Benefits Of Implementing Online Security Management System Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Improves Productivity, Quality Data, Minimize Error. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Conducting Vulnerability Comprehensive Guide To Blockchain Digital Security Mockup Pdf
The following slide showcases blockchain cybersecurity vulnerability assessment framework to optimize resilience and transparency. It includes key elements such as identify, protect, respond, recover, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Conducting Vulnerability Comprehensive Guide To Blockchain Digital Security Mockup Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide showcases blockchain cybersecurity vulnerability assessment framework to optimize resilience and transparency. It includes key elements such as identify, protect, respond, recover, etc.
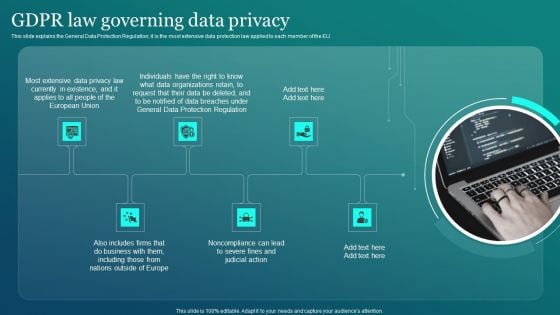
Information Security GDPR Law Governing Data Privacy Formats PDF
This slide explains the General Data Protection Regulation it is the most extensive data protection law applied to each member of the EU. Welcome to our selection of the Information Security GDPR Law Governing Data Privacy Formats PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

User Authentication And Authorization Security Management Technology Summary PDF
This slide provides the use of multiple authentication and authorization technology which are used to protect systems and user information. Key categories are password based, multi factor, certificate based, biometrics and token based. Persuade your audience using this User Authentication And Authorization Security Management Technology Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Based, Multi Factor, Certificate Based, Biometrics, Token Based. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Home Security Company Services And Contact Information Structure PDF
This slide showcases services provided to insured against losses from insurance company. The services provided are interior and exterior renovation and remodeling, general contracting and new home construction. Showcasing this set of slides titled Home Security Company Services And Contact Information Structure PDF. The topics addressed in these templates are Reimbursement, Contract For Protection, Representing Services Provided. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Phases Of Information IT Security Awareness Training Program Mockup PDF
This slide covers phases of information cybersecurity awareness training program. It involves four phases such as design, development, execution and continual improvement. Persuade your audience using this Phases Of Information IT Security Awareness Training Program Mockup PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Design, Development, Execution, Continual Improvement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Risk Management Plan Implementation Stages Summary PDF
This slide explains various steps for implementation of cybersecurity risk management plan in the organization to ensure time and budget compliance. It includes elements such as current state analysis, assessment, target state, etc. Presenting IT Security Risk Management Plan Implementation Stages Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State Analysis, Assessment, Target State, Roadmap. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
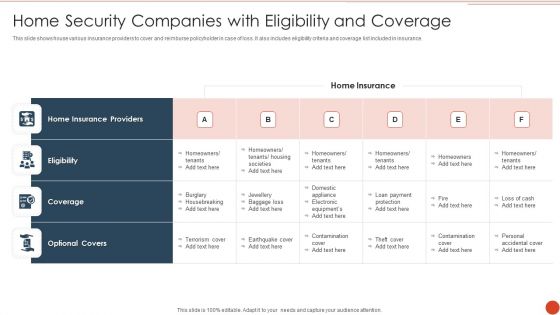
Home Security Companies With Eligibility And Coverage Infographics PDF
This slide shows house various insurance providers to cover and reimburse policyholder in case of loss. It also includes eligibility criteria and coverage list included in insurance. Showcasing this set of slides titled Home Security Companies With Eligibility And Coverage Infographics PDF. The topics addressed in these templates are Home Insurance Providers, Home Insurance, Loan Payment Protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
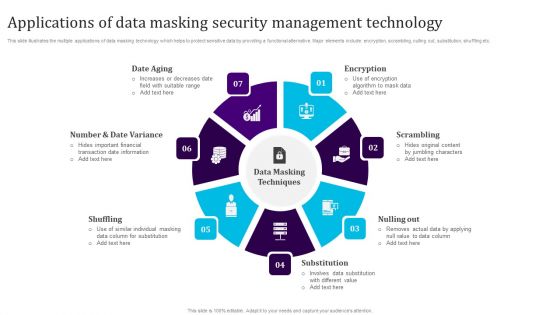
Applications Of Data Masking Security Management Technology Sample PDF
This slide illustrates the multiple applications of data masking technology which helps to protect sensitive data by providing a functional alternative. Major elements include encryption, scrambling, nulling out, substitution, shuffling etc. Persuade your audience using this Applications Of Data Masking Security Management Technology Sample PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Date Aging, Shuffling, Substitution, Nulling Out, Scrambling, Encryption. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Desktop Security Management Implementation Of Strong Password Policy Brochure PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. This is a desktop security management implementation of strong password policy brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation of strong password policy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Data Privacy In Educational Institutions Introduction PDF
This slide depicts data privacy in educational Information , institutions should issue a notice period of two days for approval before disclosing any information. This modern and well arranged Information Security Data Privacy In Educational Institutions Introduction PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
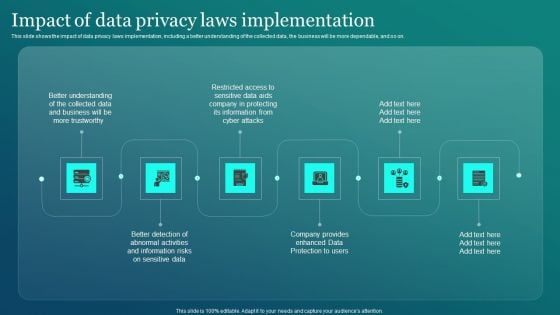
Information Security Impact Of Data Privacy Laws Implementation Slides PDF
This slide shows the impact of data privacy laws implementation, including a better understanding of the collected data, the business will be more dependable, and so on. Take your projects to the next level with our ultimate collection of Information Security Impact Of Data Privacy Laws Implementation Slides PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
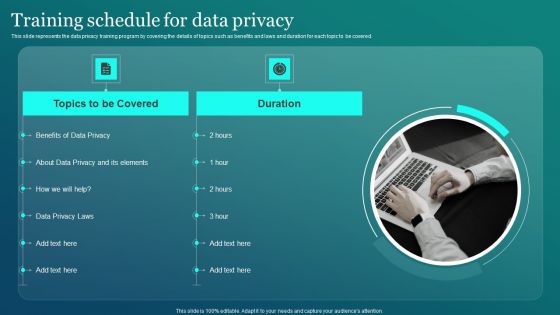
Information Security Training Schedule For Data Privacy Microsoft PDF
This slide represents the data privacy training program by covering the details of topics such as benefits and laws and duration for each topic to be covered. Present like a pro with Information Security Training Schedule For Data Privacy Microsoft PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cyber Security Dashboard Ppt PowerPoint Presentation Complete With Slides
Improve your presentation delivery using this Cyber Security Dashboard Ppt PowerPoint Presentation Complete With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising tweleve this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.

Business Cyber Security Assessment Ppt PowerPoint Presentation Complete With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Business Cyber Security Assessment Ppt PowerPoint Presentation Complete With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the tweleve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Infra Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Infra Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of seventeen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.
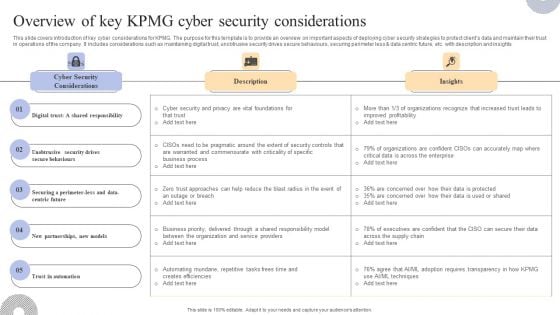
Overview Of Key KPMG Cyber Security Considerations Inspiration PDF
This slide covers an introduction to KPMG company ESG strategy to improve reporting to stakeholders. The purpose of this template is to provide overview on introducing ESG strategy, benefits along with reporting insights. It includes benefits such as helping organization assess and improve sustainable performance, establishing strong reputation and trust, attracting investors and customers, etc. Welcome to our selection of the Overview Of Key KPMG Cyber Security Considerations Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
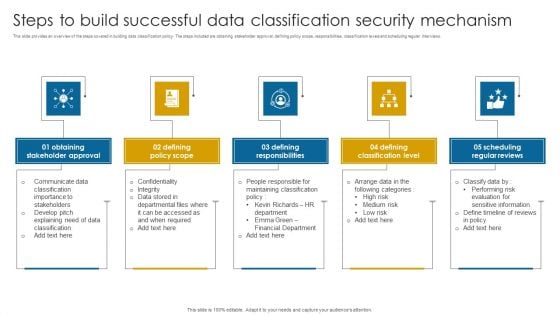
Steps To Build Successful Data Classification Security Mechanism Structure PDF
This slide provides an overview of the steps covered in building data classification policy. The steps included are obtaining stakeholder approval, defining policy scope, responsibilities, classification levels and scheduling regular interviews.Presenting Steps To Build Successful Data Classification Security Mechanism Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Stakeholder Approval, Defining Policy Scope, Defining Responsibilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Hacker Email Prevention Guidelines For Employees Information PDF
This slide depicts the email prevention guidelines for employees, including spam filters and multi factor authentication for email login credentials.This is a IT Security Hacker Email Prevention Guidelines For Employees Information PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Process, Pieces Of Information, Factor Authentication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
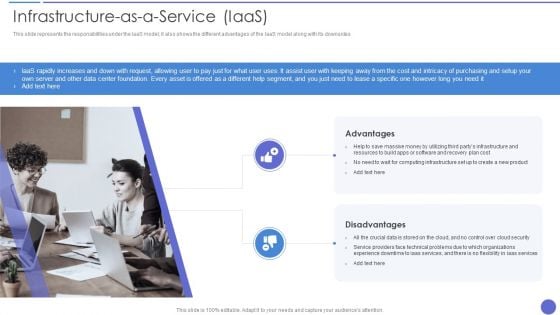
Cloud Data Security Infrastructure As A Service Iaas Demonstration PDF
This slide represents the responsibilities under the IaaS model it also shows the different advantages of the IaaS model along with its downsides. This is a Cloud Data Security Infrastructure As A Service Iaas Demonstration PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Advantages, Disadvantages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
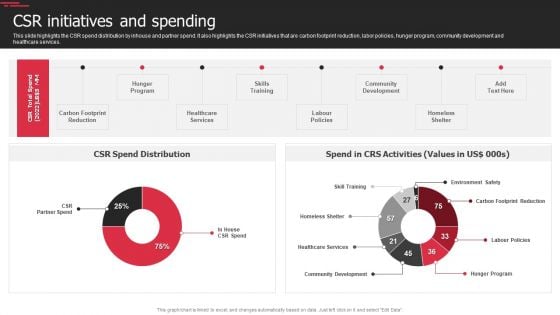
Security Agency Business Profile Csr Initiatives And Spending Mockup PDF
This slide highlights the CSR spend distribution by inhouse and partner spend. It also highlights the CSR initiatives that are carbon footprint reduction, labor policies, hunger program, community development and healthcare services. Deliver and pitch your topic in the best possible manner with this Security Agency Business Profile Csr Initiatives And Spending Mockup PDF. Use them to share invaluable insights on Healthcare Services, Environment Safety, Community Development and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
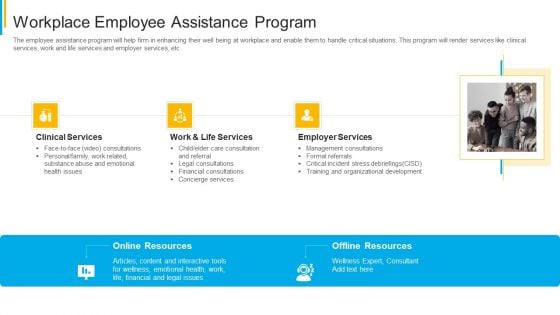
Project Security Administration IT Workplace Employee Assistance Program Structure PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. This is a project security administration it workplace employee assistance program structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like clinical services, work and life services, employer services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Blockchain Security Technology For Healthcare Industry Icons PDF
This slide highlights the importance of blockchain technology in healthcare industry which is used to preserve data and promote workflow authenticity. Key components are supply chain, electronic health records, safety access and staff verification.Persuade your audience using this Blockchain Security Technology For Healthcare Industry Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authenticity Medicine, Electronic Health, Ensures Only Trusted. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
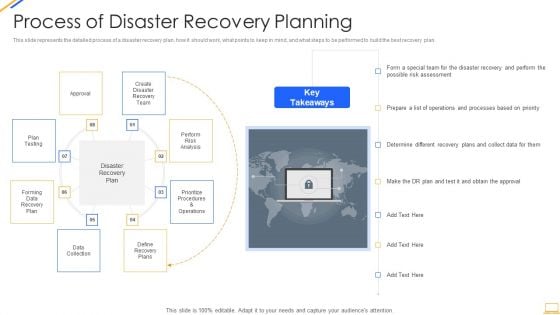
Desktop Security Management Process Of Disaster Recovery Planning Professional PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a desktop security management process of disaster recovery planning professional pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plans, team, risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
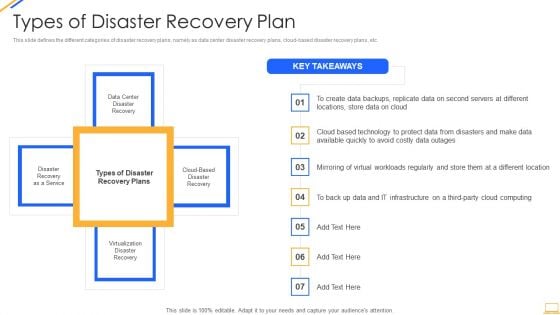
Desktop Security Management Types Of Disaster Recovery Plan Topics PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc. This is a desktop security management types of disaster recovery plan topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, locations, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Backup Of Sensitive Information Ideas PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization.This is a IT Security Hacker Backup Of Sensitive Information Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Different Service, Emergency Access, Natural Disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
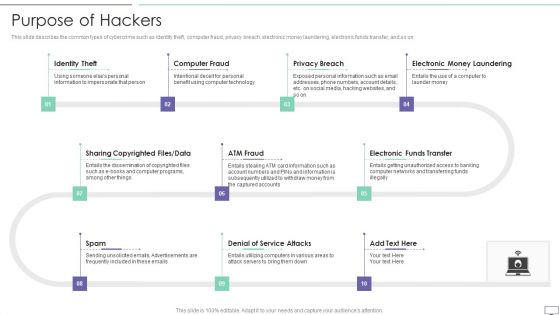
IT Security Hacker Purpose Of Hackers Mockup PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a IT Security Hacker Purpose Of Hackers Mockup PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Identity Theft, Computer Fraud, Privacy Breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
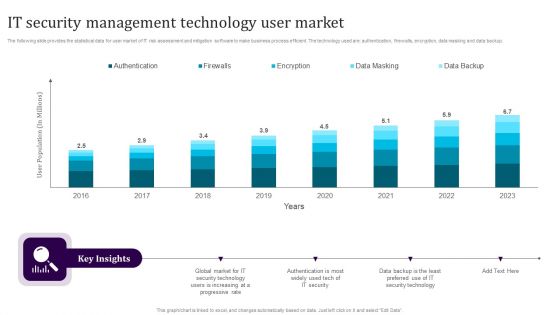
IT Security Management Technology User Market Guidelines PDF
The following slide provides the statistical data for user market of IT risk assessment and mitigation software to make business process efficient. The technology used are authentication, firewalls, encryption, data masking and data backup. Showcasing this set of slides titled IT Security Management Technology User Market Guidelines PDF. The topics addressed in these templates are Authentication, Firewalls, Encryption, Data Masking, Data Backup. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Hacker Hacking Of Email Domain Inspiration PDF
This slide represents the hacking of the company email domain by hackers by sending spam emails to employees and stealing money from clients and customers.This is a IT Security Hacker Hacking Of Email Domain Inspiration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like After Entering, Passwords And Other, Technological Upgrades. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
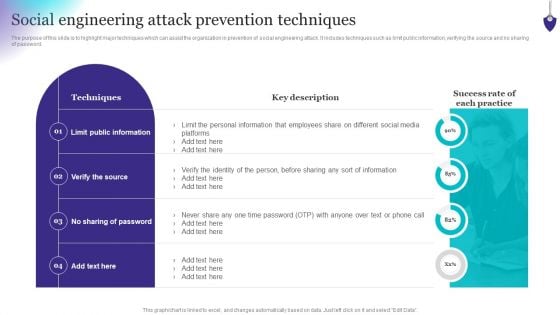
Organizing Security Awareness Social Engineering Attack Prevention Techniques Rules PDF
The purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Want to ace your presentation in front of a live audience Our Organizing Security Awareness Social Engineering Attack Prevention Techniques Rules PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
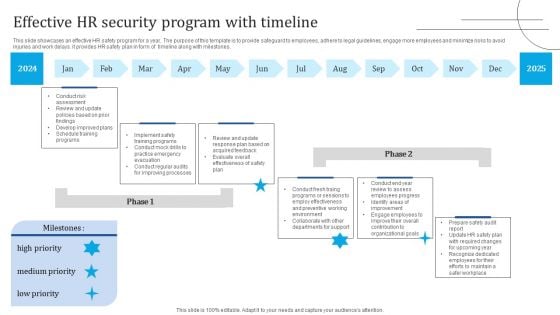
Effective HR Security Program With Timeline Portrait PDF
This slide showcases an effective HR safety program for a year. The purpose of this template is to provide safeguard to employees, adhere to legal guidelines, engage more employees and minimize risks to avoid injuries and work delays. it provides HR safety plan in form of timeline along with milestones. Showcasing this set of slides titled Effective HR Security Program With Timeline Portrait PDF. The topics addressed in these templates are Implement Safety Training Programs, Develop Improved Plans, Review Update. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Track Record Of Our Company Themes PDF
This slide highlights our past track record as a data privacy provider company and outlines that we promise 100 percent client satisfaction. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Security Track Record Of Our Company Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
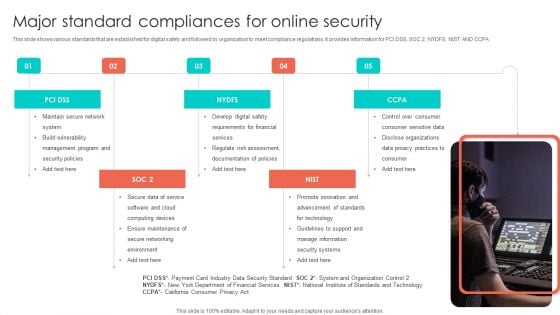
Major Standard Compliances For Online Security Pictures PDF
This slide shows various standards that are established for digital safety and followed by organization to meet compliance regulations. It provides information for PCI DSS, SOC 2, NYDFS, NIST AND CCPA. Persuade your audience using this Major Standard Compliances For Online Security Pictures PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Develop Digital Safety, Requirements For Financial, Regulate Risk Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Need Of Implementing HR Security Programs At Workplace Pictures PDF
This slide highlights the need of importance of workplace safety in an organization. This template aims to provide details regarding workplace safety to increase productivity, reduce turnover rates, safe working conditions, reduction in risk factors, avoid loss of resources, reduction in expenses, foster employee wellbeing and follow legal guidelines, etc. Showcasing this set of slides titled Need Of Implementing HR Security Programs At Workplace Pictures PDF. The topics addressed in these templates are Productivity, Working Environment, Absenteeism. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Workplace Risk Mitigation Strategies For HR Security Portrait PDF
This slide highlights techniques for minimizing risk factors in the workplace. the purpose of this template is to employ effective strategies for ensuring workforce safety eventually enhancing overall productivity and efficiency. It also provides details regarding the status of performance along with insights. Showcasing this set of slides titled Workplace Risk Mitigation Strategies For HR Security Portrait PDF. The topics addressed in these templates are Risk Assessment Management, Safety Training And Education, Compliance Regulations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
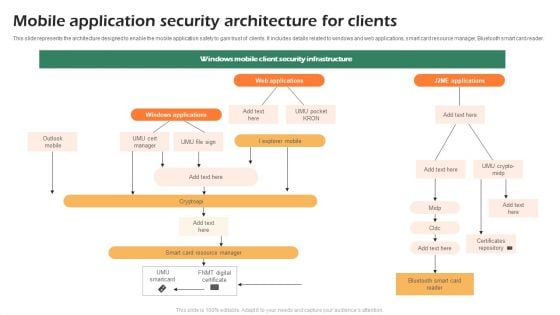
Mobile Application Security Architecture For Clients Summary PDF
This slide represents the architecture designed to enable the mobile application safety to gain trust of clients. It includes details related to windows and web applications, smart card resource manager, Bluetooth smart card reader. Pitch your topic with ease and precision using this Mobile Application Security Architecture For Clients Summary PDF. This layout presents information on Windows Applications, Web Applications, Resource Manager. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Checklist For Online Security Threat And Risk Assessment Designs PDF
This slide represents digital safety threat and assessment checklist which ensure risk management in cost effective manner. It provides information regarding conducting assessment, perform threat analysis, risk mitigation and process completion. Showcasing this set of slides titled Checklist For Online Security Threat And Risk Assessment Designs PDF. The topics addressed in these templates are Perform Threat Analysis, Conduct Assessment, Risk Mitigation And Recommendations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































