Patch
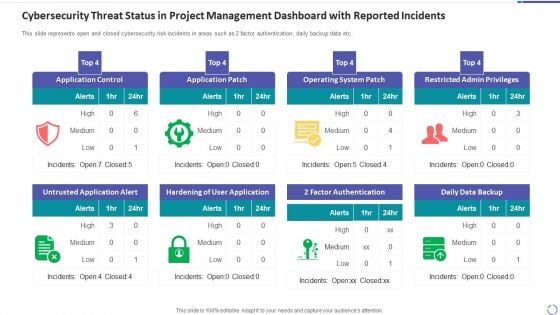
Cybersecurity Threat Status In Project Management Dashboard With Reported Incidents Introduction PDF
This slide represents open and closed cybersecurity risk incidents in areas such as 2 factor authentication, daily backup data etc. Showcasing this set of slides titled cybersecurity threat status in project management dashboard with reported incidents introduction pdf. The topics addressed in these templates are application control, application patch, operating system patch, restricted admin privileges, untrusted application alert. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
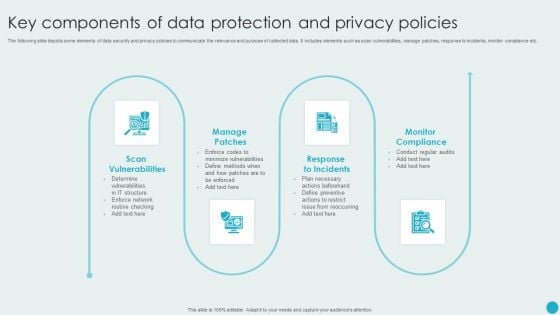
Key Components Of Data Protection And Privacy Policies Graphics PDF
The following slide depicts some elements of data security and privacy policies to communicate the relevance and purpose of collected data. It includes elements such as scan vulnerabilities, manage patches, response to incidents, monitor compliance etc. Presenting Key Components Of Data Protection And Privacy Policies Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Patches, Response To Incidents, Monitor Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
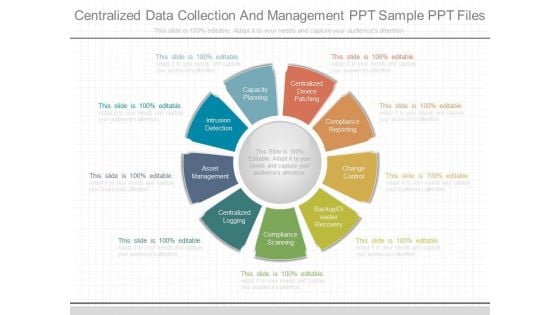
Centralized Data Collection And Management Ppt Sample Ppt Files
This is a centralized data collection and management ppt sample ppt files. This is a nine stage process. The stages in this process are capacity planning, centralized device patching, compliance reporting, change control, backup disaster recovery, compliance scanning, centralized logging, asset management.

Customer 360 Overview Training Schedule Timeline Ppt Styles Pictures PDF
Presenting this set of slides with name customer 360 overview training schedule timeline ppt styles pictures pdf. This is a seven stage process. The stages in this process are training phase, time, security patch, timeline. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
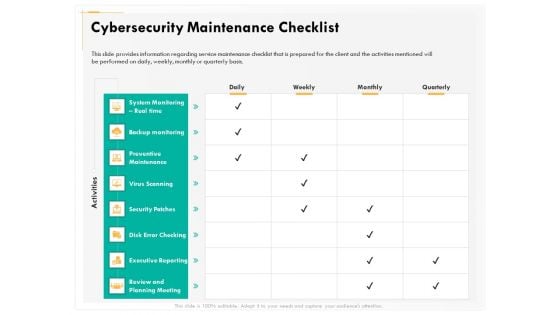
Computer Security Incident Handling Cybersecurity Maintenance Checklist Background PDF
Presenting this set of slides with name computer security incident handling cybersecurity maintenance checklist background pdf. The topics discussed in these slides are system monitoring real time, backup monitoring, preventive maintenance, virus scanning, security patches, executive reporting, review and planning meeting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
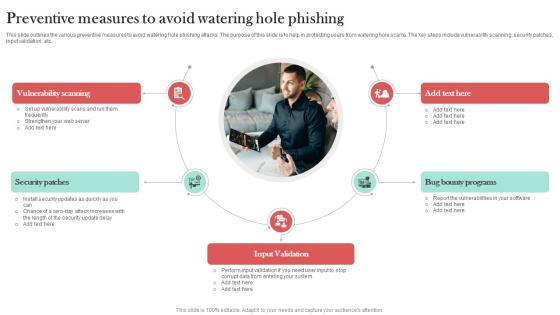
Preventive Measures To Avoid Watering Man In The Middle Phishing IT
This slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc. Present like a pro with Preventive Measures To Avoid Watering Man In The Middle Phishing IT. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc.
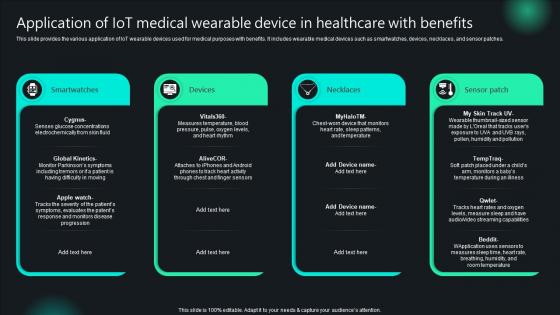
Application Of IoT Medical Wearable Device In Healthcare Unlocking Potential IoTs Application IoT SS V
This slide provides the various application of IoT wearable devices used for medical purposes with benefits. It includes wearable medical devices such as smartwatches, devices, necklaces, and sensor patches. Create an editable Application Of IoT Medical Wearable Device In Healthcare Unlocking Potential IoTs Application IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Application Of IoT Medical Wearable Device In Healthcare Unlocking Potential IoTs Application IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides the various application of IoT wearable devices used for medical purposes with benefits. It includes wearable medical devices such as smartwatches, devices, necklaces, and sensor patches.

Unlocking Potential IoTs Application Architecture Of Healthcare IoT Framework IoT SS V
This slide presents the framework model for the implementation of IoT in healthcare architecture. It includes sensor patches, wearable applications, networks, cloud storage, physicians, medical researchers, health insurance companies, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Unlocking Potential IoTs Application Architecture Of Healthcare IoT Framework IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Unlocking Potential IoTs Application Architecture Of Healthcare IoT Framework IoT SS V today and make your presentation stand out from the rest This slide presents the framework model for the implementation of IoT in healthcare architecture. It includes sensor patches, wearable applications, networks, cloud storage, physicians, medical researchers, health insurance companies, etc.
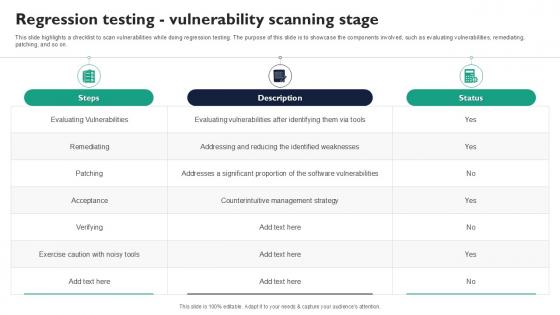
Regression Testing Vulnerability Scanning Stage Corrective Regression Testing Ppt Example
This slide highlights a checklist to scan vulnerabilities while doing regression testing. The purpose of this slide is to showcase the components involved, such as evaluating vulnerabilities, remediating, patching, and so on. Boost your pitch with our creative Regression Testing Vulnerability Scanning Stage Corrective Regression Testing Ppt Example. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights a checklist to scan vulnerabilities while doing regression testing. The purpose of this slide is to showcase the components involved, such as evaluating vulnerabilities, remediating, patching, and so on.

Regression Testing Applications And Use Cases Corrective Regression Testing Ppt Sample
This slide discusses the applications and use cases of regression testing. The purpose of this slide is to showcase the use cases and applications such as new releases, integration testing, security patches, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Regression Testing Applications And Use Cases Corrective Regression Testing Ppt Sample and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide discusses the applications and use cases of regression testing. The purpose of this slide is to showcase the use cases and applications such as new releases, integration testing, security patches, and so on.

Regression Testing Vulnerability Automated Regression Testing And Achieving PPT Template
This slide highlights a checklist to scan vulnerabilities while doing regression testing. The purpose of this slide is to showcase the components involved, such as evaluating vulnerabilities, remediating, patching, and so on. This Regression Testing Vulnerability Automated Regression Testing And Achieving PPT Template is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Regression Testing Vulnerability Automated Regression Testing And Achieving PPT Template features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide highlights a checklist to scan vulnerabilities while doing regression testing. The purpose of this slide is to showcase the components involved, such as evaluating vulnerabilities, remediating, patching, and so on.
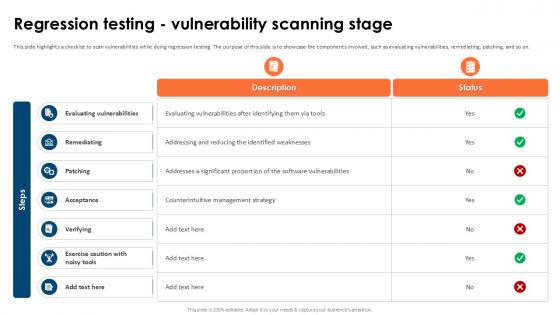
Regression Testing Vulnerability Partial Regression Testing For A Best PPT Example
This slide highlights a checklist to scan vulnerabilities while doing regression testing. The purpose of this slide is to showcase the components involved, such as evaluating vulnerabilities, remediating, patching, and so on. This Regression Testing Vulnerability Partial Regression Testing For A Best PPT Example is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Regression Testing Vulnerability Partial Regression Testing For A Best PPT Example features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide highlights a checklist to scan vulnerabilities while doing regression testing. The purpose of this slide is to showcase the components involved, such as evaluating vulnerabilities, remediating, patching, and so on.
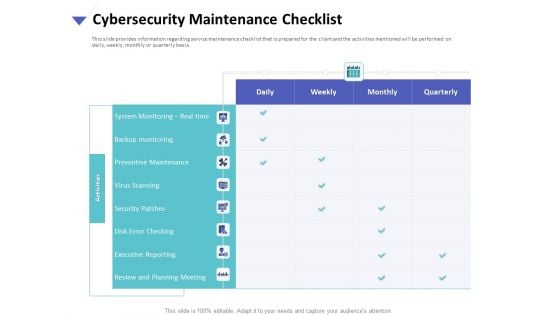
Strategies To Mitigate Cyber Security Risks Cybersecurity Maintenance Checklist Ppt Slides Graphics Tutorials PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity maintenance checklist ppt slides graphics tutorials pdf. The topics discussed in these slides are system monitoring, real time, backup monitoring, preventive maintenance, virus scanning, security patches, disk error checking, executive reporting, review and planning meeting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
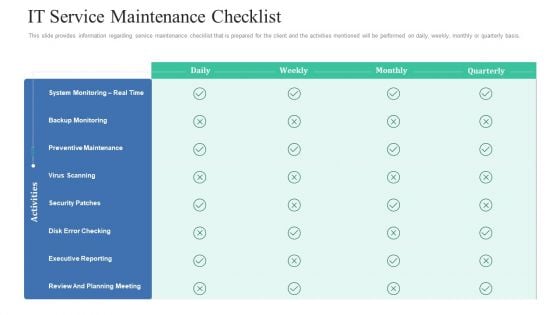
Retaining Clients Improving Information Technology Facilities IT Service Maintenance Checklist Graphics PDF
This slide provides information regarding service maintenance checklist that is prepared for the client and the activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver an awe-inspiring pitch with this creative retaining clients improving information technology facilities it service maintenance checklist graphics pdf bundle. Topics like preventive maintenance, security patches, executive reporting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
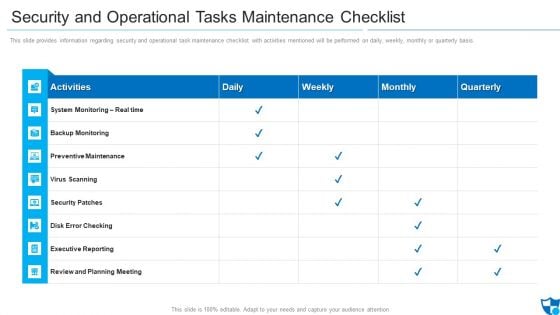
Security And Operational Tasks Maintenance Checklist Infographics PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis.Deliver an awe inspiring pitch with this creative security and operational tasks maintenance checklist infographics pdf bundle. Topics like preventive maintenance, security patches, review and planning meeting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
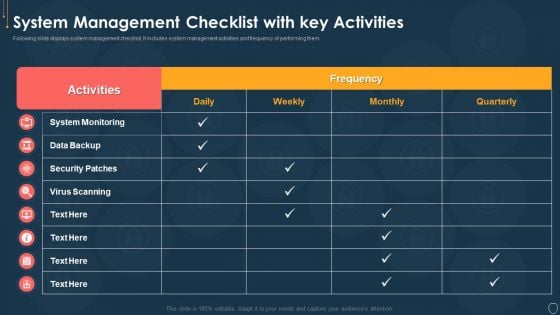
Cyber Security Risk Management Plan System Management Checklist With Key Activities Structure PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative cyber security risk management plan system management checklist with key activities structure pdf bundle. Topics like system monitoring, data backup, security patches, virus scanning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
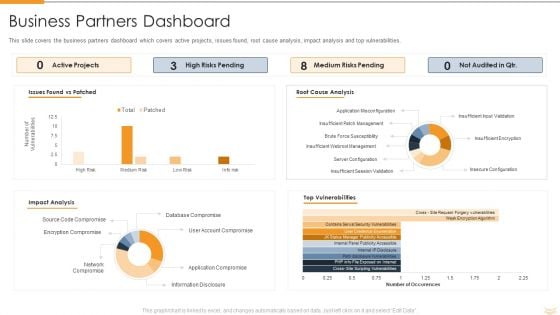
Strategic Partnership Management Plan Business Partners Dashboard Mockup PDF
This slide covers the business partners dashboard which covers active projects, issues found, root cause analysis, impact analysis and top vulnerabilities. Deliver an awe inspiring pitch with this creative strategic partnership management plan business partners dashboard mockup pdf bundle. Topics like issues found vs patched, impact analysis, root cause analysis, top vulnerabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
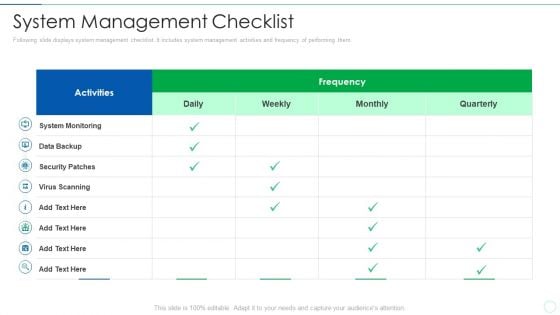
Effective IT Risk Management Process System Management Checklist Brochure PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver and pitch your topic in the best possible manner with this effective it risk management process system management checklist brochure pdf. Use them to share invaluable insights on security patches, data backup, system monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
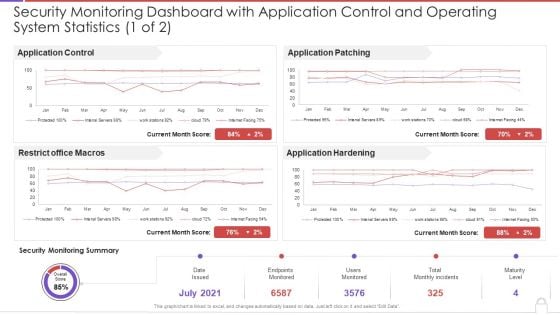
Security Monitoring Dashboard With Application Control And Operating System Statistics Template PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this security monitoring dashboard with application control and operating system statistics template pdf. Use them to share invaluable insights on application control, restrict office macros, application patching, application hardening and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management Model For Data Security System Management Checklist With Key Activities Guidelines PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security System Management Checklist With Key Activities Guidelines PDF bundle. Topics like System Monitoring, Data Backup, Security Patches, Virus Scanning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan System Management Checklist Background PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan System Management Checklist Background PDF Use them to share invaluable insights on System Monitoring, Security Patches, Virus Scanning and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
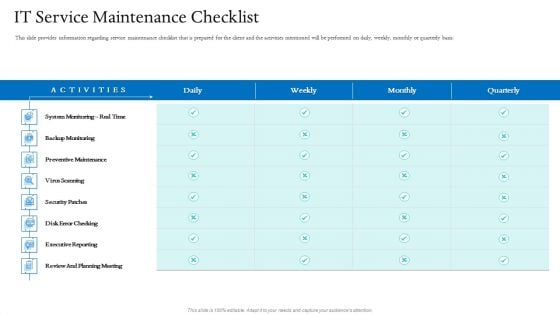
Information Technology Facilities Governance IT Service Maintenance Checklist Ppt Styles Graphics Tutorials PDF
This slide provides information regarding service maintenance checklist that is prepared for the client and the activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this information technology facilities governance IT service maintenance checklist ppt styles graphics tutorials pdf. Use them to share invaluable insights on backup monitoring, executive reporting, review and planning meeting, security patches, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. This is a Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Monitoring, Data Backup, Security Patches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
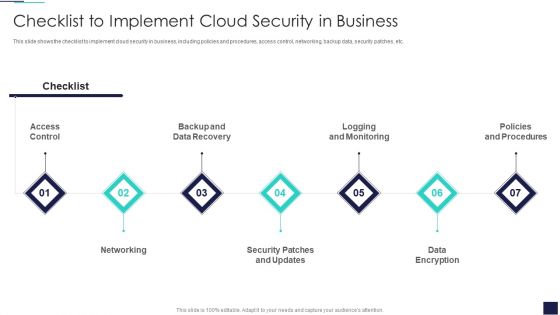
Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. This is a Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Policies And Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Risk Management Approach Introduction Checklist For Effectively Managing Asset Security Sample PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. This is a IT Security Risk Management Approach Introduction Checklist For Effectively Managing Asset Security Sample PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Monitoring, Data Backup, Security Patches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Various Kpis To Measure Computer Security System Portrait PDF
This slide shows the different KPIs used to measure IT security system. These are level of preparedness, intrusion attempts, days to patch, incidents reported etc. Persuade your audience using this Various Kpis To Measure Computer Security System Portrait PDF This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Performance Indicators, Excepted Results, Actual Results Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.This is a Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Logging And Monitoring You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
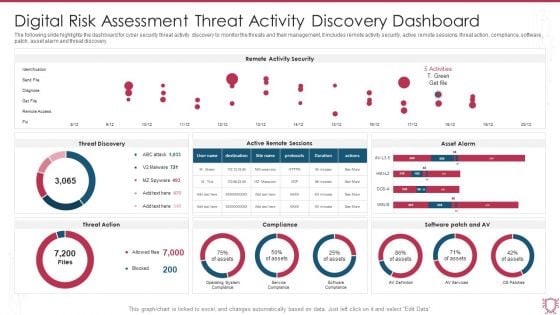
Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF
The following slide highlights the dashboard for cyber security threat activity discovery to monitor the threats and their management, it includes remote activity security, active remote sessions, threat action, compliance, software patch, asset alarm and threat discovery. Pitch your topic with ease and precision using this Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF. This layout presents information on Remote Activity Security, Threat Discovery, Asset Alarm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
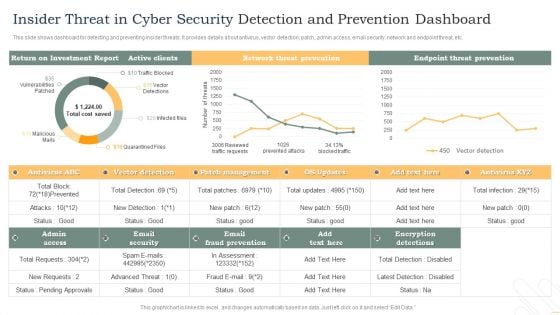
Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF
This slide shows dashboard for detecting and preventing insider threats. It provides details about antivirus, vector detection, patch, admin access, email security, network and endpoint threat, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF. This layout presents information on Active Clients, Network Threat Prevention, Endpoint Threat Prevention. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
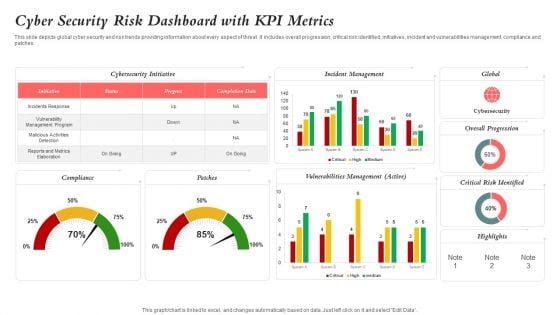
Cyber Security Risk Dashboard With KPI Metrics Elements PDF
This slide depicts global cyber security and risk trends providing information about every aspect of threat. It includes overall progression, critical risk identified, initiatives, incident and vulnerabilities management, compliance and patches. Showcasing this set of slides titled Cyber Security Risk Dashboard With KPI Metrics Elements PDF. The topics addressed in these templates are Vulnerability Management Program, Reports And Metrics Elaboration, Critical Risk Identified. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
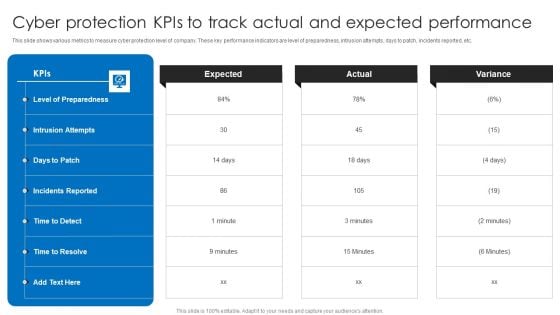
Cyber Protection Kpis To Track Actual And Expected Performance Structure PDF
This slide shows various metrics to measure cyber protection level of company. These key performance indicators are level of preparedness, intrusion attempts, days to patch, incidents reported, etc. Pitch your topic with ease and precision using this Cyber Protection Kpis To Track Actual And Expected Performance Structure PDF. This layout presents information on Cyber Protection Kpis, Track Actual Expected Performance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
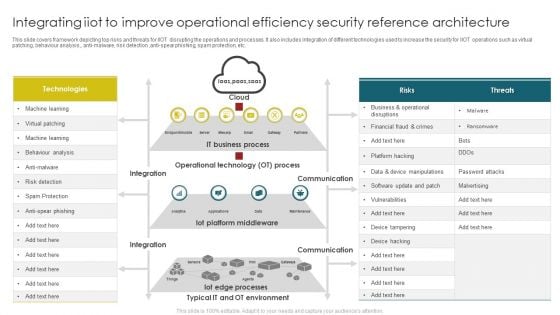
Integrating Iiot To Improve Operational Efficiency Security Reference Architecture Themes PDF
This slide covers framework depicting top risks and threats for IIOT disrupting the operations and processes. It also includes integration of different technologies used to increase the security for IIOT operations such as virtual patching, behaviour analysis, anti malware, risk detection, anti spear phishing, spam protection, etc. Pitch your topic with ease and precision using this Integrating Iiot To Improve Operational Efficiency Security Reference Architecture Themes PDF. This layout presents information on Operational Technology, IT Business Process, Iot Platform Middleware . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Information Technology Security KPI With Measures Taken By The Company Formats PDF
This slide covers the KPIs of the company used for the security of data or privacy of the customers or businesss own confidential information. It also includes the things that is to be covered under each KPI. Some of them are NHT, days to patch, intrusion attempts ,etc. Presenting Information Technology Security KPI With Measures Taken By The Company Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Key Performance Indicators, Measures Taken, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Data Encryption Performance Tracking Client Side Encryption PPT Presentation
This slide represents the dashboard which can be utilized by organization to monitor cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, patches, highest number of critical incidents, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Data Encryption Performance Tracking Client Side Encryption PPT Presentation is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Encryption Performance Tracking Client Side Encryption PPT Presentation and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the dashboard which can be utilized by organization to monitor cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, patches, highest number of critical incidents, etc.


 Continue with Email
Continue with Email

 Home
Home


































