Patch
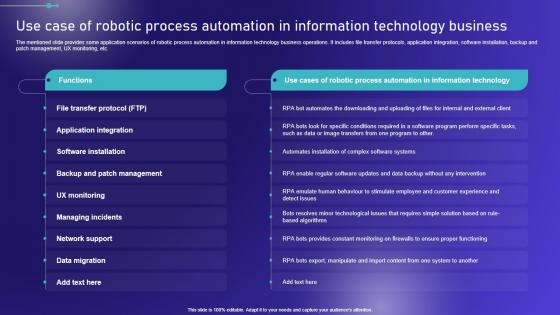
Use Case Of Robotic Process Automation In Embracing Robotic Process Diagrams PDF
The mentioned slide provides some application scenarios of robotic process automation in information technology business operations. It includes file transfer protocols, application integration, software installation, backup and patch management, UX monitoring, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Use Case Of Robotic Process Automation In Embracing Robotic Process Diagrams PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The mentioned slide provides some application scenarios of robotic process automation in information technology business operations. It includes file transfer protocols, application integration, software installation, backup and patch management, UX monitoring, etc.
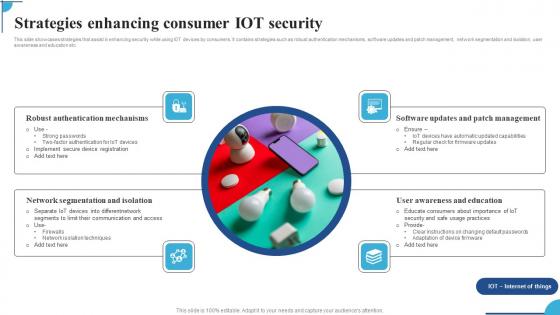
Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf
This slide showcases strategies that assist in enhancing security while using IOT devices by consumers. It contains strategies such as robust authentication mechanisms,software updates and patch management,network segmentation and isolation,user awareness and education etc. Pitch your topic with ease and precision using this Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf. This layout presents information on Robust Authentication Mechanisms,Network Segmentation Isolation,Software Updates. It is also available for immediate download and adjustment. So,changes can be made in the color,design,graphics or any other component to create a unique layout. This slide showcases strategies that assist in enhancing security while using IOT devices by consumers. It contains strategies such as robust authentication mechanisms,software updates and patch management,network segmentation and isolation,user awareness and education etc.
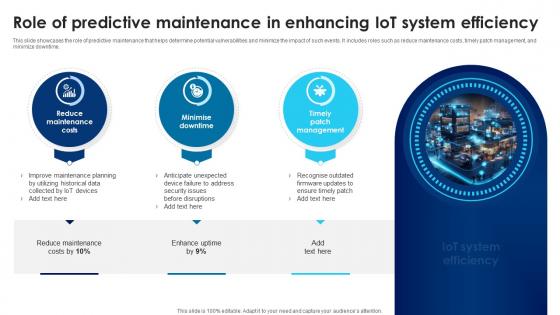
Building Trust With IoT Security Role Of Predictive Maintenance In Enhancing IoT System Efficiency IoT SS V
This slide showcases the role of predictive maintenance that helps determine potential vulnerabilities and minimize the impact of such events. It includes roles such as reduce maintenance costs, timely patch management, and minimize downtime. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Building Trust With IoT Security Role Of Predictive Maintenance In Enhancing IoT System Efficiency IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases the role of predictive maintenance that helps determine potential vulnerabilities and minimize the impact of such events. It includes roles such as reduce maintenance costs, timely patch management, and minimize downtime.
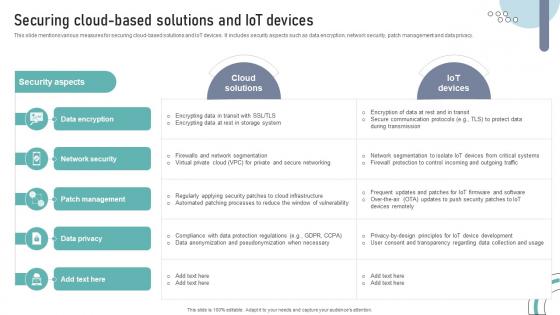
Securing Cloud Based Solutions And IOT Devices DT SS V
This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy. Slidegeeks has constructed Securing Cloud Based Solutions And IOT Devices DT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy.
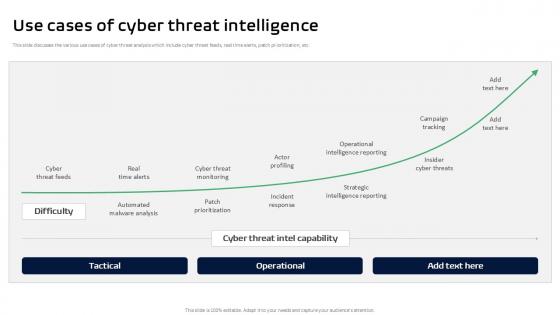
Use Cases Of Cyber Threat Intelligence Threat Intelligence Ppt Example
This slide discusses the various use cases of cyber threat analysis which include cyber threat feeds, real time alerts, patch prioritization, etc. Presenting this PowerPoint presentation, titled Use Cases Of Cyber Threat Intelligence Threat Intelligence Ppt Example, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Use Cases Of Cyber Threat Intelligence Threat Intelligence Ppt Example. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Use Cases Of Cyber Threat Intelligence Threat Intelligence Ppt Example that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide discusses the various use cases of cyber threat analysis which include cyber threat feeds, real time alerts, patch prioritization, etc.

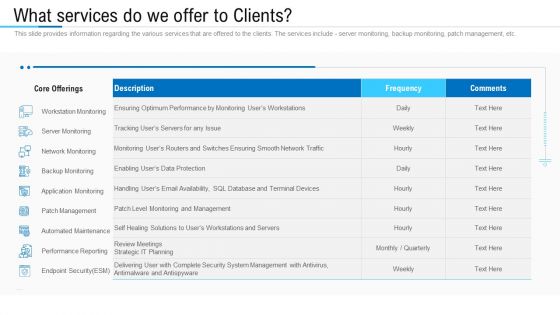
ITIL Strategy Service Excellence What Services Do We Offer To Clients Ppt PowerPoint Presentation Pictures Structure PDF
Presenting this set of slides with name itil strategy service excellence what services do we offer to clients ppt powerpoint presentation pictures structure pdf. The topics discussed in these slides are core offerings, server monitoring, network monitoring, backup monitoring, application monitoring, patch management, automated maintenance, performance reporting, endpoint security esm. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
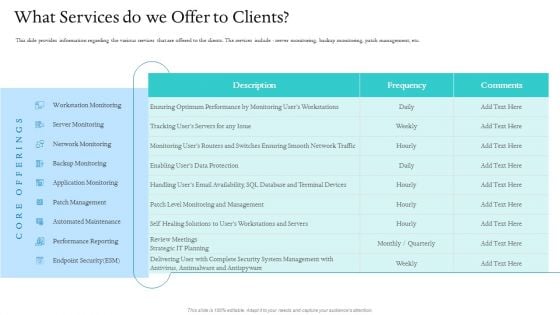
Information Technology Facility Flow Administration What Services Do We Offer To Clients Sample PDF
This slide provides information regarding the various services that are offered to the clients. The services include server monitoring, backup monitoring, patch management, etc. Deliver and pitch your topic in the best possible manner with this information technology facility flow administration what services do we offer to clients sample pdf. Use them to share invaluable insights on automated maintenance, performance reporting, network monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
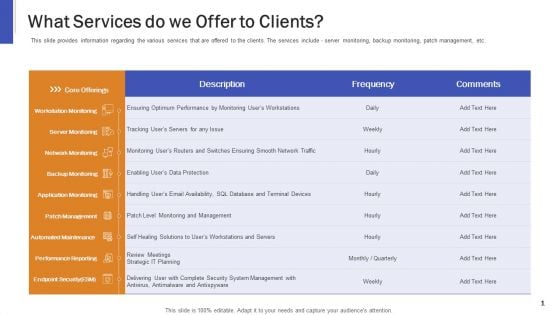
Information Technology Facilities Governance What Services Do We Offer To Clients Ppt Infographics Inspiration PDF
This slide provides information regarding the various services that are offered to the clients. The services include - server monitoring, backup monitoring, patch management, etc. Deliver an awe inspiring pitch with this creative information technology facilities governance what services do we offer to clients ppt infographics inspiration pdf bundle. Topics like performance reporting, endpoint security, network monitoring, server monitoring, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Impeccable Information Technology Facility What Services Do We Offer To Clients Infographics PDF
This slide provides information regarding the various services that are offered to the clients. The services include server monitoring, backup monitoring, patch management, etc. Deliver an awe-inspiring pitch with this creative impeccable information technology facility what services do we offer to clients infographics pdf bundle. Topics like performance reporting, application monitoring, network monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Retaining Clients Improving Information Technology Facilities What Services Do We Offer To Clients Sample PDF
This slide provides information regarding the various services that are offered to the clients. The services include - server monitoring, backup monitoring, patch management, etc. Deliver an awe-inspiring pitch with this creative retaining clients improving information technology facilities what services do we offer to clients sample pdf bundle. Topics like automated maintenance, application monitoring, network monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
VID Dashboard For Tracking Downloads In End User Computing Environment Infographics PDF
This slide represents the dashboard for tracking downloads of apps in end user computing environment by covering details of average patch time, quality updates and so on.Deliver an awe inspiring pitch with this creative VID Dashboard For Tracking Downloads In End User Computing Environment Infographics PDF bundle. Topics like Distribution Pilot, Average, Windows Devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
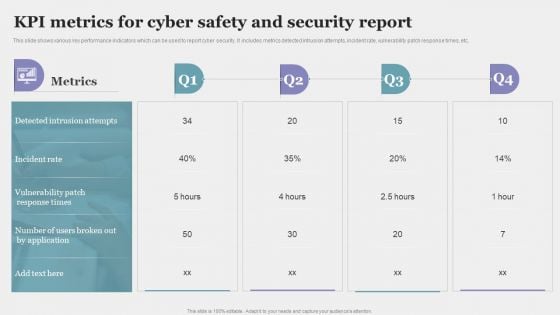
KPI Metrics For Cyber Safety And Security Report Elements PDF
This slide shows various key performance indicators which can be used to report cyber security. It includes metrics detected intrusion attempts, incident rate, vulnerability patch response times, etc. Showcasing this set of slides titled KPI Metrics For Cyber Safety And Security Report Elements PDF. The topics addressed in these templates are Incident Rate, Application, Metrics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Dashboard For Tracking Downloads In End User Computing Environment Introduction PDF
This slide represents the dashboard for tracking downloads of apps in end user computing environment by covering details of average patch time, quality updates and so on.Deliver and pitch your topic in the best possible manner with this Dashboard For Tracking Downloads In End User Computing Environment Introduction PDF. Use them to share invaluable insights on Windows Devices, Security Update, Last Quality and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Stages Of Internet Security Threat Minimization Summary PDF
This slide exhibits cyber security breach minimization steps, it includes several steps such as- provide insights to all the users to not share company insights, malware attack prevention, assessment of all networks and so on. Pitch your topic with ease and precision using this stages of internet security threat minimization summary pdf. This layout presents information on patch management, monitoring, malware protection, secure configuration, user education. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key Security Controls To Be Addressed In The Program Ppt Professional Vector PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. This is a key security controls to be addressed in the program ppt professional vector pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like key security controls to be addressed in the program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Techniques Used In Ethical Hacking Ppt Infographics Guide PDF
This slide represents the techniques of ethical hacking such as port scanning, analyzing and sniffing network traffic, detection of SQL injections, an inspection of patch installation. This is a techniques used in ethical hacking ppt infographics guide pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, methods, analyzing, network, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
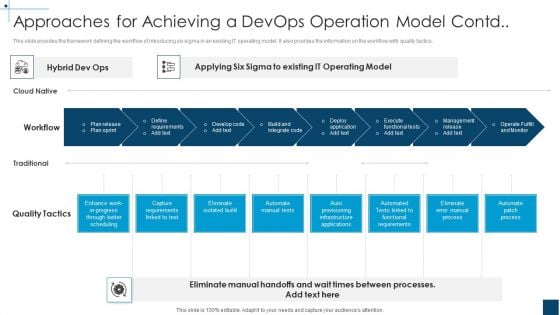
Devops Principles For Hybrid Cloud IT Approaches For Achieving A Devops Operation Model Contd Template PDF
This slide provides the framework defining the workflow of introducing six sigma in an existing IT operating model. It also provides the information on the workflow with quality tactics.Deliver an awe inspiring pitch with this creative devops principles for hybrid cloud it approaches for achieving a devops operation model contd template pdf bundle. Topics like eliminate isolated build, automate manual tests, automate patch process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Customer Mesh Computing IT Dashboard For Tracking Downloads In End User Computing Environment Elements PDF
This slide represents the dashboard for tracking downloads of apps in end user computing environment by covering details of average patch time, quality updates and so on. Deliver and pitch your topic in the best possible manner with this customer mesh computing it dashboard for tracking downloads in end user computing environment elements pdf. Use them to share invaluable insights ondashboard for tracking downloads in end user computing environment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Key Security Controls To Be Addressed In The Program Ppt Infographics Samples PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Presenting handling cyber threats digital era key security controls to be addressed in the program ppt infographics samples pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like prevents attacks, limits extent of attacks, data recovery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Safety Initiatives Key Security Controls To Be Addressed In The Program Summary PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an awe inspiring pitch with this creative data safety initiatives key security controls to be addressed in the program summary pdf bundle. Topics like prevents attacks, limits extent of attacks, data recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
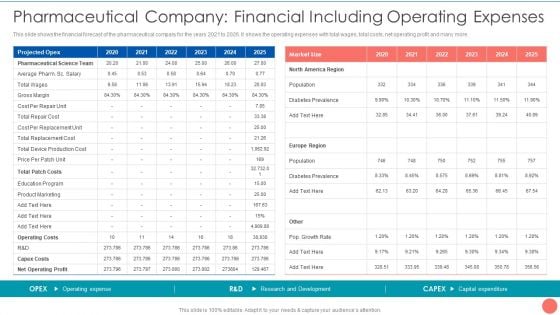
Tactics To Achieve Sustainability Pharmaceutical Company Financial Including Operating Expenses Diagrams PDF
This slide shows the financial forecast of the pharmaceutical company for the years 2021 to 2026. It shows the operating expenses with total wages, total costs, net operating profit and many more. Deliver an awe inspiring pitch with this creative Tactics To Achieve Sustainability Pharmaceutical Company Financial Including Operating Expenses Diagrams PDF bundle. Topics like Cost Per Repair, Total Patch Costs, Education Program Marketing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
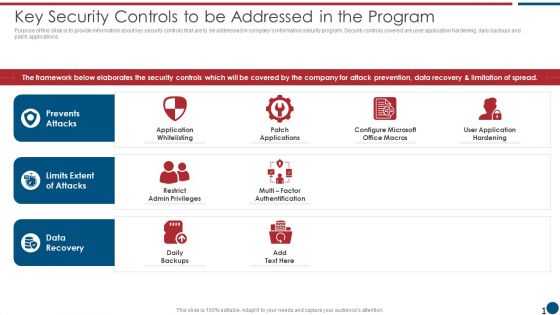
Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF bundle. Topics like Prevents Attacks, Limits Extent, Data Recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
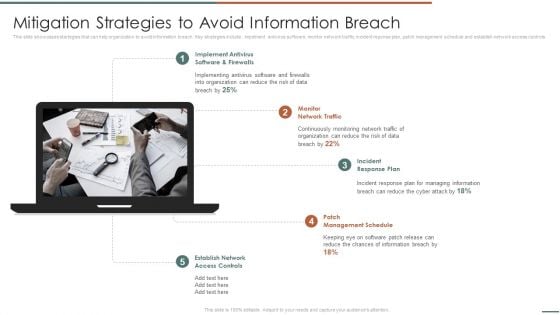
Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls .This is a Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Schedule, Incident Response, Implement Antivirus . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Center Architecture Management Best Practices Introduction PDF
This slide covers data center infrastructure management best practices. It involves gauge resource requirements, adopt consistence system of record, implement monitoring and patch servers. Persuade your audience using this Data Center Architecture Management Best Practices Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Implement Ongoing Monitoring, Consistence System Of Record, Gauge Resource Requirements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
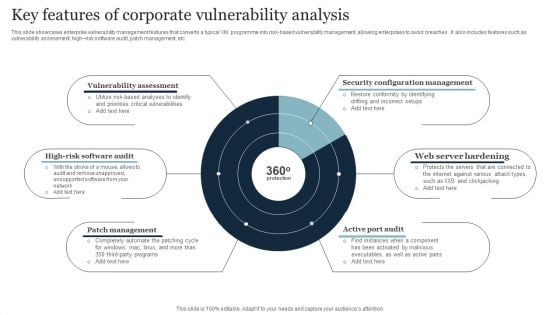
Key Features Of Corporate Vulnerability Analysis Inspiration PDF
This slide showcases enterprise vulnerability management features that converts a typical VM programme into risk-based vulnerability management, allowing enterprises to avoid breaches . It also includes features such as vulnerability assessment, high risk software audit, patch management, etc. Presenting Key Features Of Corporate Vulnerability Analysis Inspiration PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Security Configuration Management, Web Server Hardening, Active Port Audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Fitness Product Promotion Campaigns NBA Marketing Strategies For Products And Brands Professional PDF
The following slide showcases National Basketball Alliance NBA marketing strategies which can guide brands in promoting their products. It provides information about jersey patch ads, in-game advertising, all-stars, on the floor, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Fitness Product Promotion Campaigns NBA Marketing Strategies For Products And Brands Professional PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
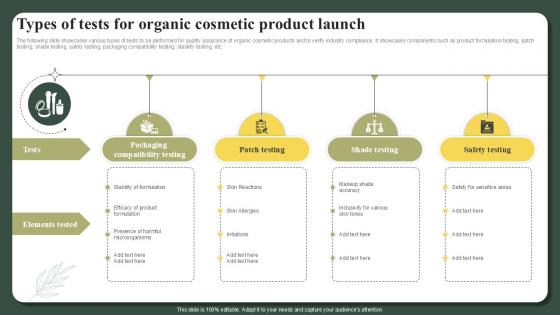
Types Of Tests For Organic Cosmetic Product Launch Successful Launch Ppt Presentation
The following slide showcases various types of tests to be performed for quality assurance of organic cosmetic products and to verify industry compliance. It showcases components such as product formulation testing, patch testing, shade testing, safety testing, packaging compatibility testing, stability testing, etc. Slidegeeks has constructed Types Of Tests For Organic Cosmetic Product Launch Successful Launch Ppt Presentation after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The following slide showcases various types of tests to be performed for quality assurance of organic cosmetic products and to verify industry compliance. It showcases components such as product formulation testing, patch testing, shade testing, safety testing, packaging compatibility testing, stability testing, etc.
Dashboard For Tracking Downloads In End User Computing Environment Mockup PDF
This slide represents the dashboard for tracking downloads of apps in end user computing environment by covering details of average patch time, quality updates and so on. Presenting this PowerPoint presentation, titled Dashboard For Tracking Downloads In End User Computing Environment Mockup PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Dashboard For Tracking Downloads In End User Computing Environment Mockup PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Dashboard For Tracking Downloads In End User Computing Environment Mockup PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
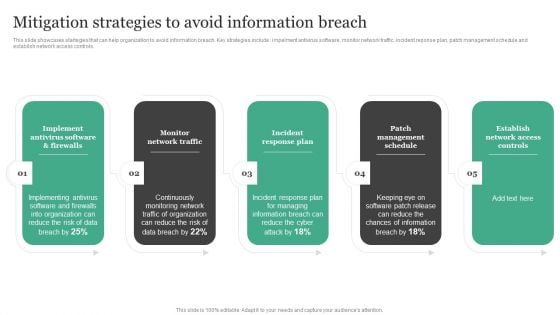
Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Presenting this PowerPoint presentation, titled Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Website Audit To Increase Conversion Rate Tools To Perform Technical SEO Audit Mockup PDF
This slide highlights the technical SEO audit tools which includes screaming frog, google search, smart SEO and Ayima redirect patch with features and cost. Slidegeeks is here to make your presentations a breeze with Website Audit To Increase Conversion Rate Tools To Perform Technical SEO Audit Mockup PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
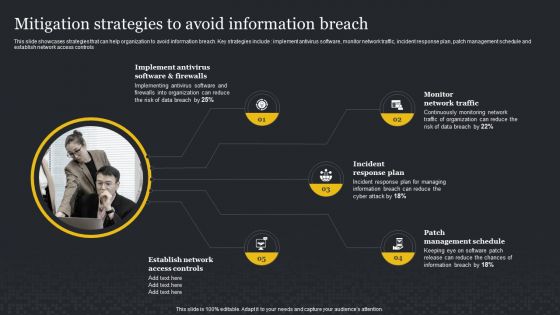
Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Present like a pro with Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Integrating Sports Marketing Campaign Nba Marketing Strategies For Products And Brands Guidelines PDF
The following slide showcases National Basketball Alliance NBA marketing strategies which can guide brands in promoting their products. It provides information about jersey patch ads, in-game advertising, all-stars, on the floor, etc. Find highly impressive Integrating Sports Marketing Campaign Nba Marketing Strategies For Products And Brands Guidelines PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Integrating Sports Marketing Campaign Nba Marketing Strategies For Products And Brands Guidelines PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Explore a selection of the finest Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Conduct Third Party Risk Assessment Ppt PowerPoint Presentation File Ideas PDF
The following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Conduct Third Party Risk Assessment Ppt PowerPoint Presentation File Ideas PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
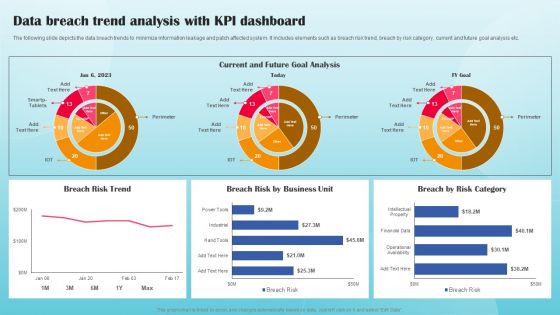
Data Breach Trend Analysis With KPI Dashboard Ppt PowerPoint Presentation File Portfolio PDF
The following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. This modern and well arranged Data Breach Trend Analysis With KPI Dashboard Ppt PowerPoint Presentation File Portfolio PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
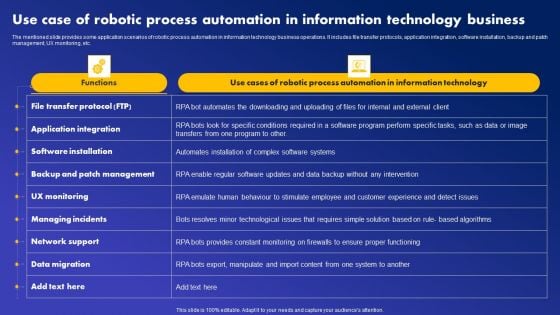
Use Case Of Robotic Process Automation In Information Technology Business Elements PDF
The mentioned slide provides some application scenarios of robotic process automation in information technology business operations. It includes file transfer protocols, application integration, software installation, backup and patch management, UX monitoring, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Use Case Of Robotic Process Automation In Information Technology Business Elements PDF can be your best option for delivering a presentation. Represent everything in detail using Use Case Of Robotic Process Automation In Information Technology Business Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
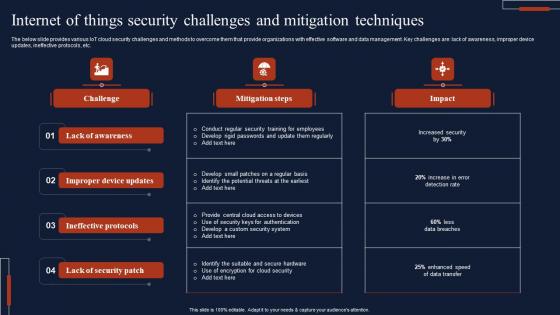
Internet Of Things Security Challenges And Mitigation Techniques Mockup Pdf
The below slide provides various IoT cloud security challenges and methods to overcome them that provide organizations with effective software and data management. Key challenges are lack of awareness, improper device updates, ineffective protocols, etc. Pitch your topic with ease and precision using this Internet Of Things Security Challenges And Mitigation Techniques Mockup Pdf This layout presents information on Lack Of Awareness, Ineffective Protocols, Lack Of Security Patch It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The below slide provides various IoT cloud security challenges and methods to overcome them that provide organizations with effective software and data management. Key challenges are lack of awareness, improper device updates, ineffective protocols, etc.
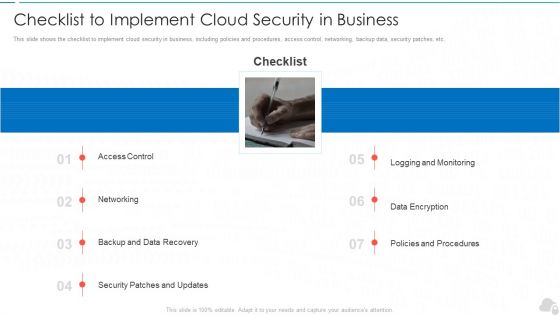
Checklist To Implement Cloud Security In Business Cloud Computing Security IT Ppt Infographic Template Example File
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Deliver an awe inspiring pitch with this creative checklist to implement cloud security in business cloud computing security it ppt infographic template example file bundle. Topics like networking, policies and procedures, logging and monitoring, data encryption, security patches and updates can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
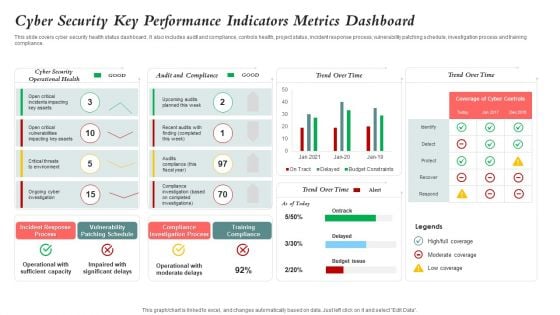
Cyber Security Key Performance Indicators Metrics Dashboard Mockup PDF
This slide covers cyber security health status dashboard . It also includes audit and compliance, controls health, project status, incident response process, vulnerability patching schedule, investigation process and training compliance. Pitch your topic with ease and precision using this Cyber Security Key Performance Indicators Metrics Dashboard Mockup PDF. This layout presents information on Cyber Security, Vulnerability Patching Schedule, Compliance Investigation Process. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
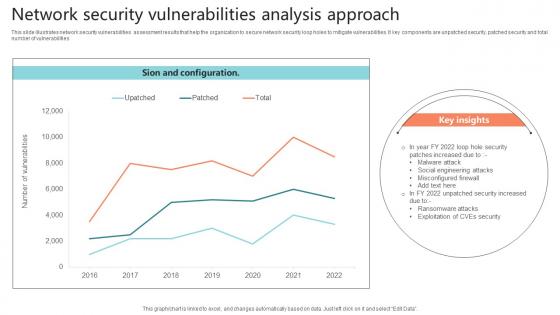
Network Security Vulnerabilities Analysis Approach Sample Pdf
This slide illustrates network security vulnerabilities assessment results that help the organization to secure network security loop holes to mitigate vulnerabilities. It key components are unpatched security, patched security and total number of vulnerabilities.Showcasing this set of slides titled Network Security Vulnerabilities Analysis Approach Sample Pdf The topics addressed in these templates are Misconfigured Firewall, Malware Attack, Social Engineering Attacks All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates network security vulnerabilities assessment results that help the organization to secure network security loop holes to mitigate vulnerabilities. It key components are unpatched security, patched security and total number of vulnerabilities
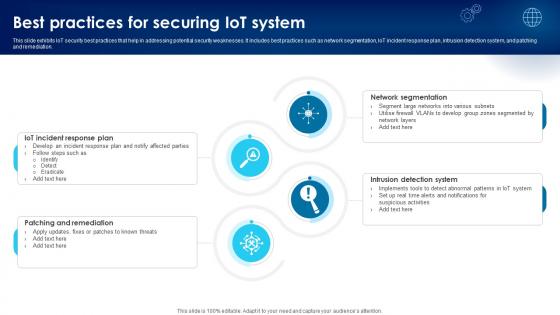
Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V
This slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation. Want to ace your presentation in front of a live audience Our Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation.

Machine To Machine Communication Iot Best Practices Template PDF
The slide highlights the best IoT practices which companies should follow.Presenting machine to machine communication iot best practices template pdf. to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like understand your endpoints, consider patching and remediation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
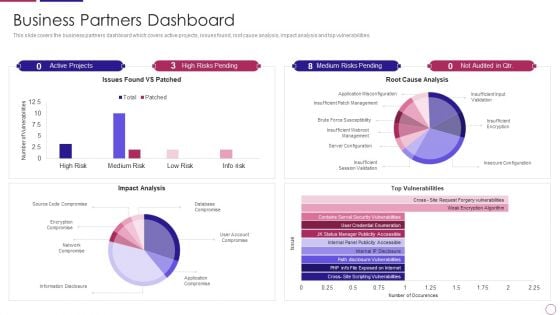
PRM To Streamline Business Processes Business Partners Dashboard Introduction PDF
This slide covers the business partners dashboard which covers active projects, issues found, root cause analysis, impact analysis and top vulnerabilities. Deliver and pitch your topic in the best possible manner with this prm to streamline business processes business partners dashboard introduction pdf. Use them to share invaluable insights on impact analysis, top vulnerabilities, server configuration, network compromise, issues found vs patched and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Safety Initiatives Checklist For Effectively Managing Asset Security Themes PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Deliver and pitch your topic in the best possible manner with this data safety initiatives checklist for effectively managing asset security themes pdf. Use them to share invaluable insights on system monitoring, data backup, security patches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
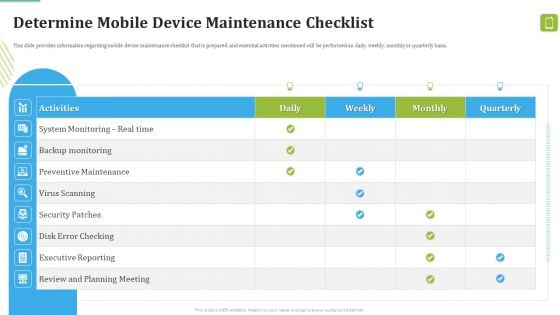
MDM Strategies At Office Determine Mobile Device Maintenance Checklist Download PDF
This slide provides information regarding mobile device maintenance checklist that is prepared, and essential activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this MDM Strategies At Office Determine Mobile Device Maintenance Checklist Download PDF. Use them to share invaluable insights on Preventive Maintenance, Virus Scanning, Security Patches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
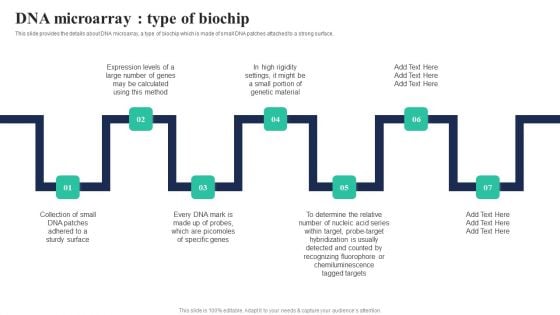
Biochips Use Cases Dna Microarray Type Of Biochip Ppt Layouts Smartart PDF
This slide provides the details about DNA microarray, a type of biochip which is made of small DNA patches attached to a strong surface. There are so many reasons you need a Biochips Use Cases Dna Microarray Type Of Biochip Ppt Layouts Smartart PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
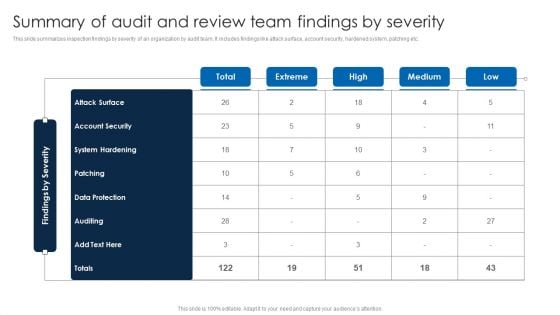
Summary Of Audit And Review Team Findings By Severity Download PDF
This slide summarizes inspection findings by severity of an organization by audit team. It includes findings like attack surface, account security, hardened system, patching etc.Showcasing this set of slides titled Summary Of Audit And Review Team Findings By Severity Download PDF. The topics addressed in these templates are System Hardening, Data Protection, Account Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
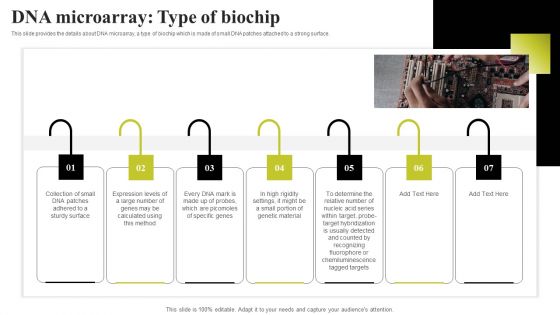
Biochip Technology Dna Microarray Type Of Biochip Ppt PowerPoint Presentation File Model PDF
This slide provides the details about DNA microarray, a type of biochip which is made of small DNA patches attached to a strong surface.There are so many reasons you need a Biochip Technology Dna Microarray Type Of Biochip Ppt PowerPoint Presentation File Model PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Machine To Machine Communication Outline Iot Best Practices Ppt Inspiration Model PDF
The slide highlights the best IoT practices which companies should follow. This is a machine to machine communication outline iot best practices ppt inspiration model pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like understand your endpoints, track and manage your devices, identify what it security cannot address, consider patching and remediation, use a risk driven strategy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
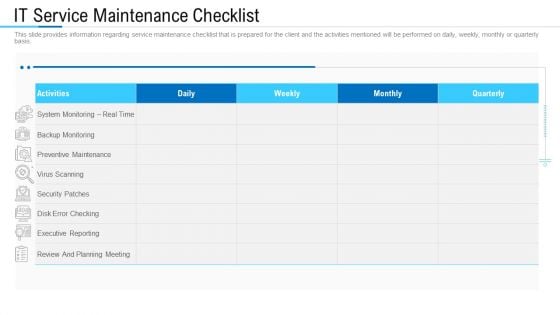
Information Technology Facility Flow Administration IT Service Maintenance Checklist Inspiration PDF
This slide provides information regarding service maintenance checklist that is prepared for the client and the activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this information technology facility flow administration it service maintenance checklist inspiration pdf. Use them to share invaluable insights on review and planning meeting, monitoring, security patches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
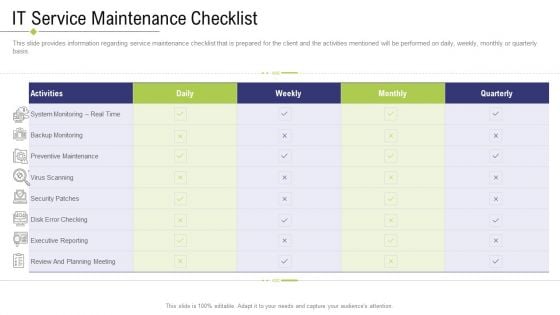
Technology Facility Maintenance And Provider IT Service Maintenance Checklist Ppt Model Background Image PDF
This slide provides information regarding service maintenance checklist that is prepared for the client and the activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this technology facility maintenance and provider IT service maintenance checklist ppt model background image pdf. Use them to share invaluable insights on planning meeting, preventive maintenance, security patches executive reporting, activities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
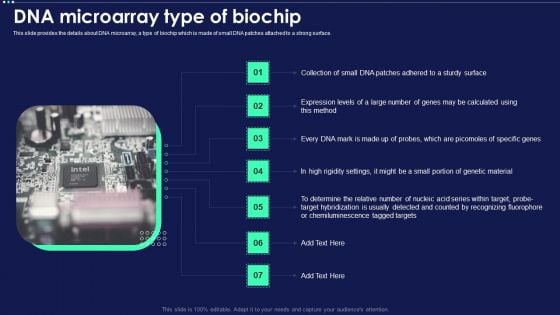
Micro Chip Dna Microarray Type Of Biochip Ppt PowerPoint Presentation Gallery Guide PDF
This slide provides the details about DNA microarray, a type of biochip which is made of small DNA patches attached to a strong surface. This is a Micro Chip Dna Microarray Type Of Biochip Ppt PowerPoint Presentation Gallery Guide PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Sturdy Surface, Expression Levels, DNA Mark, Specific Genes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
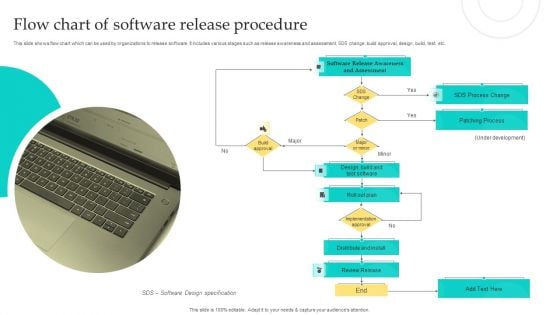
Flow Chart Of Software Release Procedure Professional PDF
This slide shows flow chart which can be used by organizations to release software. It includes various stages such as release awareness and assessment, SDS change, build approval, design, build, test, etc. Persuade your audience using this Flow Chart Of Software Release Procedure Professional PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Design, Patching Process, Development. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
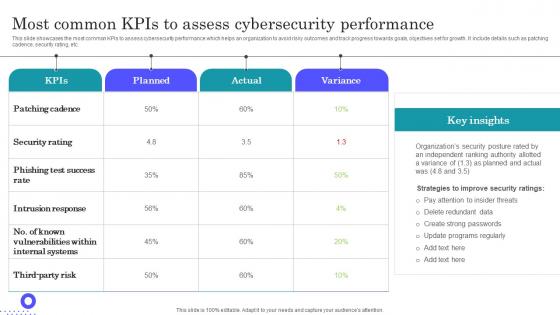
Most Common KPIs To Assess Cybersecurity Performance Slides Pdf
Showcasing this set of slides titled Most Common KPIs To Assess Cybersecurity Performance Slides Pdf The topics addressed in these templates are Intrusion Response, Phishing Test Success, Security Rating All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the most common KPIs to assess cybersecurity performance which helps an organization to avoid risky outcomes and track progress towards goals, objectives set for growth. It include details such as patching cadence, security rating, etc.
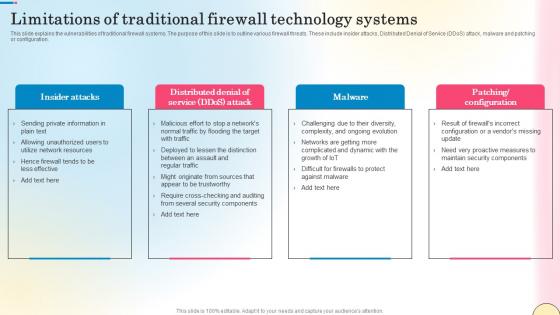
Limitations Of Traditional Firewall Technology Systems Network Security Pictures Pdf
This slide explains the vulnerabilities of traditional firewall systems. The purpose of this slide is to outline various firewall threats. These include insider attacks, Distributed Denial of Service DDoS attack, malware and patching or configuration. Presenting this PowerPoint presentation, titled Limitations Of Traditional Firewall Technology Systems Network Security Pictures Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Limitations Of Traditional Firewall Technology Systems Network Security Pictures Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Limitations Of Traditional Firewall Technology Systems Network Security Pictures Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide explains the vulnerabilities of traditional firewall systems. The purpose of this slide is to outline various firewall threats. These include insider attacks, Distributed Denial of Service DDoS attack, malware and patching or configuration.

WAF Introduction Web Application Firewall Use Cases Topics PDF
This slide outlines the main application areas of web application firewall systems. The purpose of this slide is to showcase the various use cases of WAF, including patching vulnerabilities, complying with security and regulatory regulations, enforcing content policies, securing websites and applications, and so on. Presenting this PowerPoint presentation, titledWAF Introduction Web Application Firewall Use Cases Topics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting thisWAF Introduction Web Application Firewall Use Cases Topics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizableWAF Introduction Web Application Firewall Use Cases Topics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
IT Security Risk Management And Incident Management Dashboard Icons PDF
This slide displays dashboard to help company in designing initiatives to mitigate cybersecurity risks. It includes kpis such as incident management, patches, compliance, vulnerabilities, etc. Showcasing this set of slides titled IT Security Risk Management And Incident Management Dashboard Icons PDF. The topics addressed in these templates are Compliance, Patches, Incident Management, Vulnerabilities Management, Cybersecurity Initiatives. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
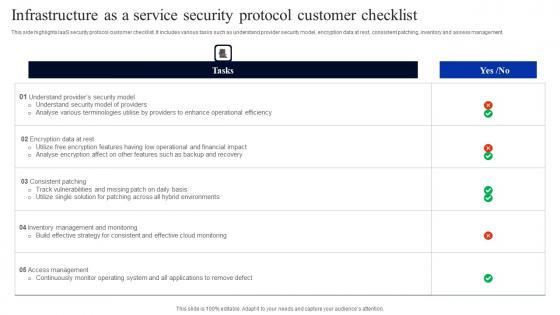
Infrastructure As A Service Security Protocol Customer Checklist Elements Pdf
This side highlights IaaS security protocol customer checklist. It includes various tasks such as understand provider security model, encryption data at rest, consistent patching, inventory and assess management. Showcasing this set of slides titled Infrastructure As A Service Security Protocol Customer Checklist Elements Pdf. The topics addressed in these templates are Encryption Data Rest, Consistent Patching, Inventory Assess Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This side highlights IaaS security protocol customer checklist. It includes various tasks such as understand provider security model, encryption data at rest, consistent patching, inventory and assess management.


 Continue with Email
Continue with Email

 Home
Home


































