Problem
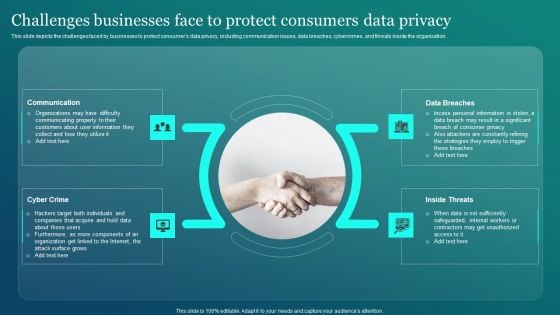
Information Security Challenges Businesses Face To Protect Consumers Data Privacy Professional PDF
This slide depicts the challenges faced by businesses to protect consumers data privacy, including communication issues, data breaches, cybercrimes, and threats inside the organization. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Security Challenges Businesses Face To Protect Consumers Data Privacy Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Threats Associated With Service Quality Ppt PowerPoint Presentation Layouts
This is a threats associated with service quality ppt powerpoint presentation layouts. This is a four stage process. The stages in this process are customer expectation often change, each customer contact is a moment of truth.
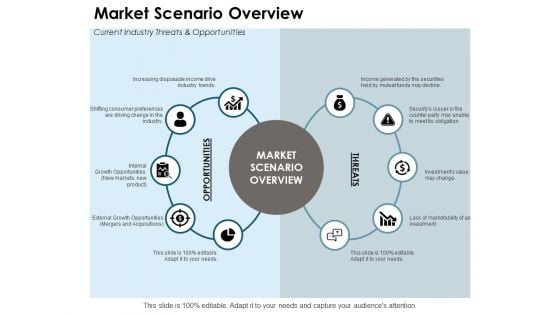
Market Scenario Overview Threats Ppt PowerPoint Presentation Slides Guidelines
This is a market scenario overview threats ppt powerpoint presentation slides guidelines. This is a six stage process. The stages in this process are management, marketing, planning, strategy, business.
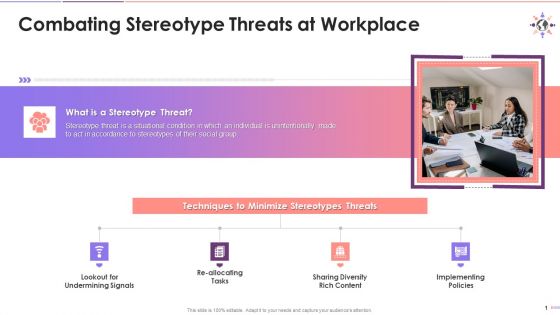
Approach To Fight Stereotype Threats In Organization Training Ppt
This slide explains in brief few methods used to combat stereotype threats at workplace. The methods are lookout for undermining signals, re-allocating tasks, sharing diversity-rich content, and implementing policies focusing on equality at workplace.
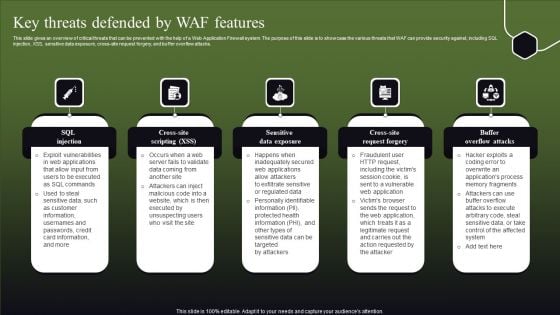
Key Threats Defended By WAF Features Ppt Pictures Elements PDF
This slide gives an overview of critical threats that can be prevented with the help of a Web Application Firewall system. The purpose of this slide is to showcase the various threats that WAF can provide security against, including SQL injection, XSS, sensitive data exposure, cross-site request forgery, and buffer overflow attacks. Explore a selection of the finest Key Threats Defended By WAF Features Ppt Pictures Elements PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Threats Defended By WAF Features Ppt Pictures Elements PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Types Cyber Threats Ppt PowerPoint Presentation Model Designs Cpb
Presenting this set of slides with name types cyber threats ppt powerpoint presentation model designs cpb. This is an editable Powerpoint four stages graphic that deals with topics like types cyber threats to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Cyber Threat Intelligence Platform Ppt PowerPoint Presentation Model Example Cpb
Presenting this set of slides with name cyber threat intelligence platform ppt powerpoint presentation model example cpb. This is an editable Powerpoint graphic that deals with topics like cyber threat intelligence platform to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Cyber Threat Intelligence Services Ppt PowerPoint Presentation Infographics Portfolio Cpb
Presenting this set of slides with name cyber threat intelligence services ppt powerpoint presentation infographics portfolio cpb. This is an editable Powerpoint six stages graphic that deals with topics like cyber threat intelligence services to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Cyber Threat Intelligence Products Ppt PowerPoint Presentation Pictures Designs Cpb
Presenting this set of slides with name cyber threat intelligence products ppt powerpoint presentation pictures designs cpb. This is an editable Powerpoint four stages graphic that deals with topics like cyber threat intelligence products to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Threat Intelligence Service Ppt PowerPoint Presentation Show Objects Cpb
Presenting this set of slides with name threat intelligence service ppt powerpoint presentation show objects cpb. This is an editable Powerpoint three stages graphic that deals with topics like threat intelligence service to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Types Security Threats Organizations Ppt PowerPoint Presentation Layouts Designs Cpb
Presenting this set of slides with name types security threats organizations ppt powerpoint presentation layouts designs cpb. This is an editable Powerpoint four stages graphic that deals with topics like types security threats organizations to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Current Cyber Threats Ppt PowerPoint Presentation Model Shapes Cpb
Presenting this set of slides with name current cyber threats ppt powerpoint presentation model shapes cpb. This is an editable Powerpoint five stages graphic that deals with topics like current cyber threats to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Vendor Threat Management Ppt PowerPoint Presentation Infographics Files Cpb
Presenting this set of slides with name vendor threat management ppt powerpoint presentation infographics files cpb. This is an editable Powerpoint three stages graphic that deals with topics like vendor threat management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Advanced Threat Protection Ppt PowerPoint Presentation Pictures Example Cpb
Presenting this set of slides with name advanced threat protection ppt powerpoint presentation pictures example cpb. This is an editable Powerpoint five stages graphic that deals with topics like advanced threat protection to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
API Threat Protection Ppt PowerPoint Presentation Model Good Cpb
Presenting this set of slides with name api threat protection ppt powerpoint presentation model good cpb. This is an editable Powerpoint five stages graphic that deals with topics like api threat protection to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Weakness Threat Strategies Ppt PowerPoint Presentation Professional Styles Cpb
Presenting this set of slides with name weakness threat strategies ppt powerpoint presentation professional styles cpb. This is an editable Powerpoint three stages graphic that deals with topics like weakness threat strategies to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Physical Threat Detection Ppt PowerPoint Presentation Gallery Icons Cpb Pdf
Presenting this set of slides with name physical threat detection ppt powerpoint presentation gallery icons cpb pdf. This is an editable Powerpoint six stages graphic that deals with topics like physical threat detection to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Tactical Threat Intelligence Ppt PowerPoint Presentation Professional Graphics Cpb Pdf
Presenting this set of slides with name tactical threat intelligence ppt powerpoint presentation professional graphics cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like tactical threat intelligence to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Threat Intelligence Sources Ppt PowerPoint Presentation Pictures Designs Cpb Pdf
Presenting this set of slides with name threat intelligence sources ppt powerpoint presentation pictures designs cpb pdf. This is an editable Powerpoint eleven stages graphic that deals with topics like threat intelligence sources to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Analyzing Threat Intelligence Ppt PowerPoint Presentation Styles Example Cpb Pdf
Presenting this set of slides with name analyzing threat intelligence ppt powerpoint presentation styles example cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like analyzing threat intelligence to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Endpoint Threat Management Ppt PowerPoint Presentation Layouts Slideshow Cpb Pdf
Presenting this set of slides with name endpoint threat management ppt powerpoint presentation layouts slideshow cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like endpoint threat management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Endpoint Threat Management Ppt PowerPoint Presentation Outline Templates Cpb Pdf
Presenting this set of slides with name endpoint threat management ppt powerpoint presentation outline templates cpb pdf. This is an editable Powerpoint one stages graphic that deals with topics like endpoint threat management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Security Threat Report Ppt PowerPoint Presentation Background Cpb Pdf
Presenting this set of slides with name security threat report ppt powerpoint presentation background cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like security threat report to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

API Threat Protection Ppt PowerPoint Presentation File Inspiration Cpb Pdf
Presenting this set of slides with name api threat protection ppt powerpoint presentation file inspiration cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like api threat protection to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Business Value Threat Intelligence Ppt PowerPoint Presentation Summary Pictures Cpb
Presenting this set of slides with name business value threat intelligence ppt powerpoint presentation summary pictures cpb. This is an editable Powerpoint four stages graphic that deals with topics like business value threat intelligence to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Threat Detection Response Ppt PowerPoint Presentation Gallery Good Cpb
Presenting this set of slides with name threat detection response ppt powerpoint presentation gallery good cpb. This is an editable Powerpoint four stages graphic that deals with topics like threat detection response to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Threat Investigation Ppt PowerPoint Presentation Ideas Format Ideas Cpb Pdf
Presenting this set of slides with name threat investigation ppt powerpoint presentation ideas format ideas cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like threat investigation to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Types Insider Threats Ppt PowerPoint Presentation Infographics Background Cpb Pdf
Presenting this set of slides with name types insider threats ppt powerpoint presentation infographics background cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like types insider threats to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Organizational Security Solutions Contingency Plan For Threat Handling Pictures PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative organizational security solutions contingency plan for threat handling pictures pdf bundle. Topics like contingency considerations, mainframe systems, security, implementation, technologies integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Professional Presentation For Self Introduction Swot Analysis Threats Elements PDF
This is a professional presentation for self introduction swot analysis threats elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threats, strengths, opportunities, weaknesses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
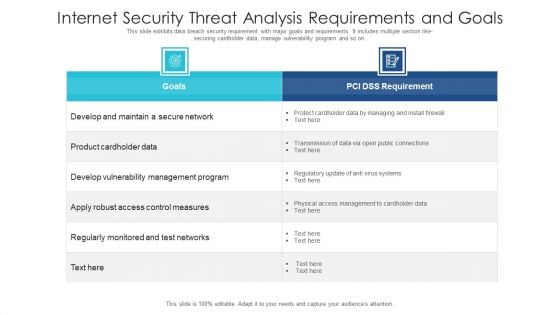
Internet Security Threat Analysis Requirements And Goals Ideas PDF
This slide exhibits data breach security requirement with major goals and requirements. It includes multiple section like- securing cardholder data, manage vulnerability program and so on. Showcasing this set of slides titled internet security threat analysis requirements and goals ideas pdf. The topics addressed in these templates are internet security threat analysis requirements and goals. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
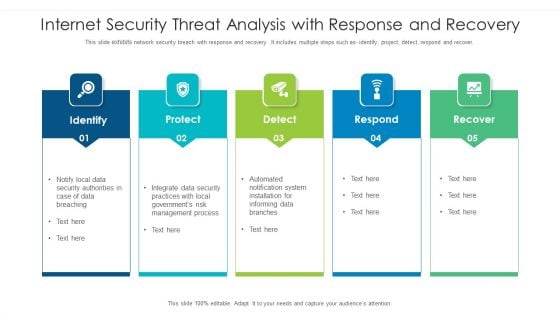
Internet Security Threat Analysis With Response And Recovery Information PDF
This slide exhibits network security breach with response and recovery .It includes multiple steps such as- identify, project, detect, respond and recover. Pitch your topic with ease and precision using this internet security threat analysis with response and recovery information pdf. This layout presents information on internet security threat analysis with response and recovery. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
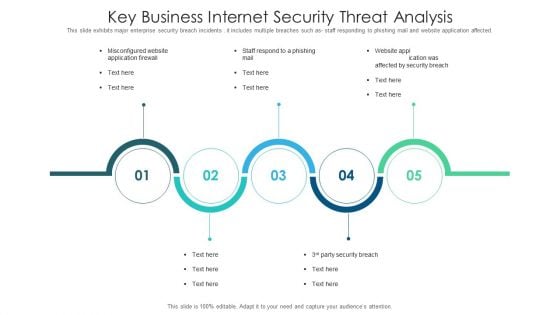
Key Business Internet Security Threat Analysis Slides PDF
This slide exhibits major enterprise security breach incidents . it includes multiple breaches such as staff responding to phishing mail and website application affected. Presenting key business internet security threat analysis slides pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including key business internet security threat analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
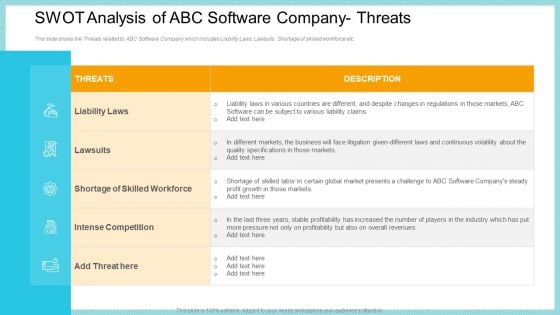
SWOT Analysis Of ABC Software Company Threats Structure PDF
This slide shows the Threats related to ABC Software Company which includes Liability Laws, Lawsuits, Shortage of skilled workforce etc. Presenting swot analysis of abc software company threats structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like revenues, profitability, quality. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda Of How To Intensify Project Threats Portrait PDF
This is a agenda of how to intensify project threats portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda of how to intensify project threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
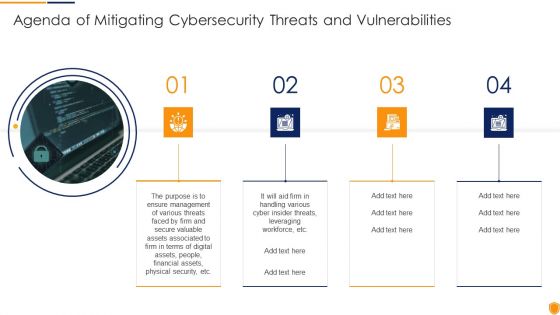
Agenda Of Mitigating Cybersecurity Threats And Vulnerabilities Guidelines PDF
Presenting agenda of mitigating cybersecurity threats and vulnerabilities guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like agenda of mitigating cybersecurity threats and vulnerabilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Indicators Associated Icons PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Presenting mitigating cybersecurity threats and vulnerabilities addressing indicators associated icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like user accounts, authentication levels, data exfiltration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents Mitigating Cybersecurity Threats And Vulnerabilities Portrait PDF
Presenting table of contents mitigating cybersecurity threats and vulnerabilities portrait pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, secure digital assets, physical security, natural calamity threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
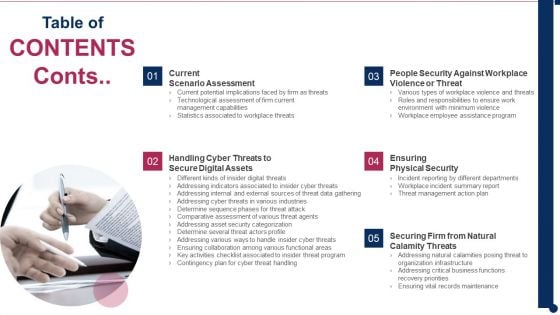
Threat Management At Workplace Contents Conts Diagrams Pdf
This is a threat management at workplace contents conts diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring physical security, current scenario assessment, people security against workplace violence or threat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Security Considerations For 5G For Threat Handling Elements PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Key Security Considerations For 5G For Threat Handling Elements PDF bundle. Topics like System Configuration, Security Policies, Information Interception can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
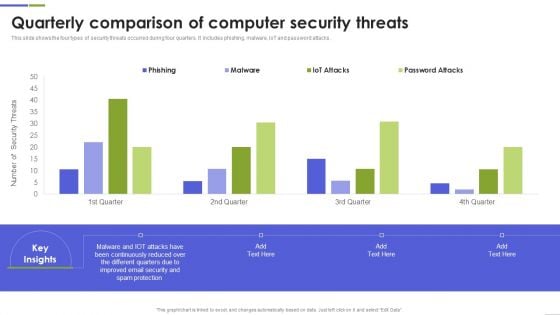
Quarterly Comparison Of Computer Security Threats Mockup PDF
This slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Computer Security Threats Mockup PDF This layout presents information on Continuously Reduced, Different Quarters, Spam Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Security Threats Contract Breaches With Clients Download PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Presenting Cloud Security Threats Contract Breaches With Clients Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Organization, Business Partners, Information Could. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Key Security Considerations For 5G For Threat Handling Icons PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling Icons PDF. Use them to share invaluable insights on Denial Of Service, Information Interception, Application Plane Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Insider Threat Detection In Computer System Icon Sample PDF
Persuade your audience using this Insider Threat Detection In Computer System Icon Sample PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Insider Threat Detection, Computer System, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Threat Assessment Process Icon With Statistics Ppt Slides Styles PDF
Persuade your audience using this Threat Assessment Process Icon With Statistics Ppt Slides Styles PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Threat Assessment Process, Icon With Statistics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
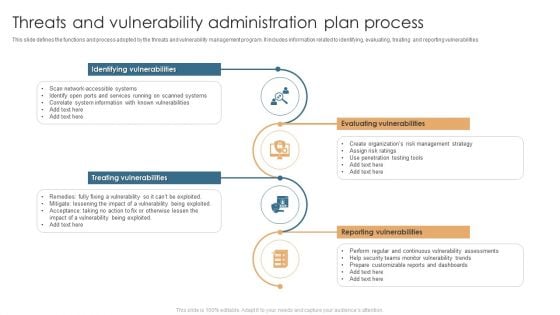
Threats And Vulnerability Administration Plan Process Guidelines PDF
This slide defines the functions and process adopted by the threats and vulnerability management program. It includes information related to identifying, evaluating, treating and reporting vulnerabilities. Presenting Threats And Vulnerability Administration Plan Process Guidelines PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Evaluating Vulnerabilities, Reporting Vulnerabilities, Treating Vulnerabilities, Identifying Vulnerabilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Threats And Vulnerability Administration Plan Requirement Icon Pictures PDF
Persuade your audience using this Threats And Vulnerability Administration Plan Requirement Icon Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Threats And Vulnerability, Administration Plan, Requirement Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
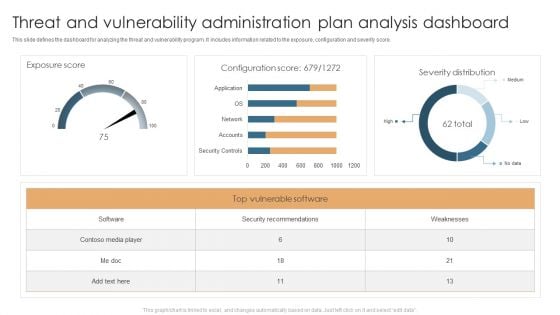
Threat And Vulnerability Administration Plan Analysis Dashboard Slides PDF
This slide defines the dashboard for analyzing the threat and vulnerability program. It includes information related to the exposure, configuration and severity score. Showcasing this set of slides titled Threat And Vulnerability Administration Plan Analysis Dashboard Slides PDF. The topics addressed in these templates are Exposure Score, Configuration Score, Severity Distribution. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
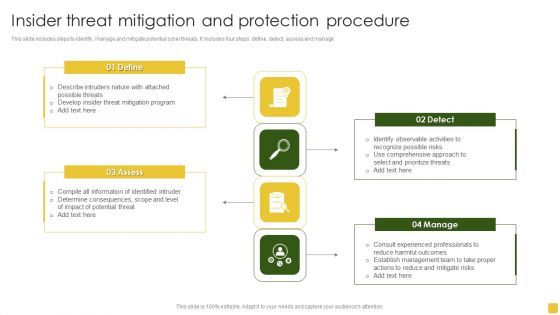
Insider Threat Mitigation And Protection Procedure Professional PDF
This slide includes steps to identify, manage and mitigate potential cyber threats. It includes four steps define, detect, assess and manage.Presenting Insider Threat Mitigation And Protection Procedure Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mitigation Program, Compile Information, Determine Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
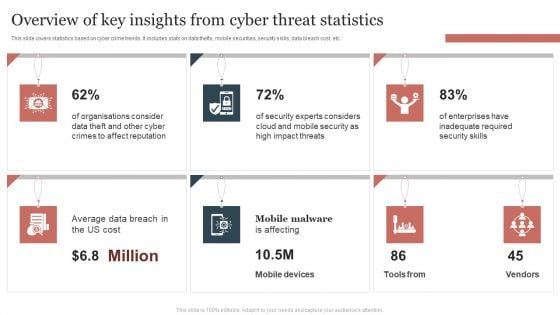
Overview Of Key Insights From Cyber Threat Statistics Themes PDF
This slide covers statistics based on cyber crime trends. It includes stats on data thefts, mobile securities, security skills, data breach cost, etc. Showcasing this set of slides titled Overview Of Key Insights From Cyber Threat Statistics Themes PDF. The topics addressed in these templates are Overview Of Key Insights, Cyber Threat Statistics . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
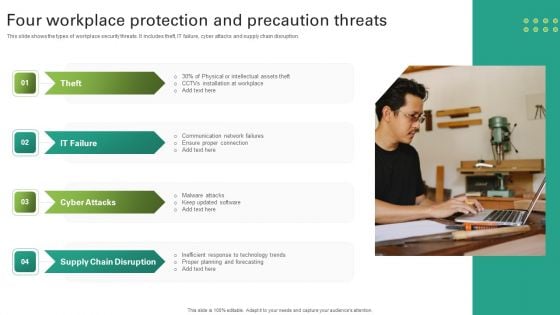
Four Workplace Protection And Precaution Threats Template PDF
This slide shows the types of workplace security threats. It includes theft, IT failure, cyber attacks and supply chain disruption. Presenting Four Workplace Protection And Precaution Threats Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Theft, It Failure, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Threats Affecting Infra Cyber Security In Market Icons PDF
The following slide showcases threats in infrastructure security which can cause electrical blackouts, breaches of national secrets, etc. It presents information related to phishing, ransomware, botnets, etc. Presenting Threats Affecting Infra Cyber Security In Market Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Phishing, Ransomware, Botnets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
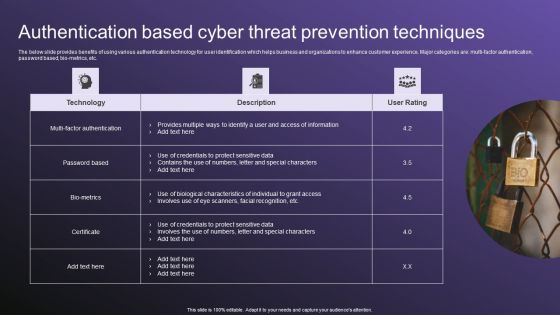
Authentication Based Cyber Threat Prevention Techniques Download PDF
The below slide provides benefits of using various authentication technology for user identification which helps business and organizations to enhance customer experience. Major categories are multi factor authentication, password based, bio-metrics, etc. Showcasing this set of slides titled Authentication Based Cyber Threat Prevention Techniques Download PDF. The topics addressed in these templates are Techniques, Authentication, Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
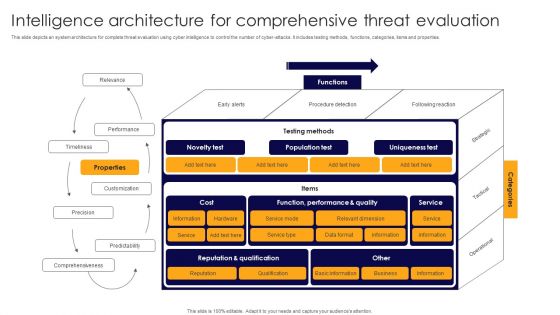
Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF
This slide depicts an system architecture for complete threat evaluation using cyber intelligence to control the number of cyber-attacks. It includes testing methods, functions, categories, items and properties. Showcasing this set of slides titled Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF. The topics addressed in these templates are Performance, Timeliness, Customization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
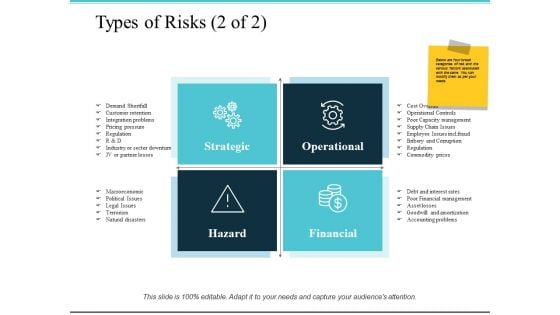
Types Of Risks Ppt PowerPoint Presentation Slides Portfolio
This is a types of risks ppt powerpoint presentation slides portfolio. This is a four stage process. The stages in this process are political issues, legal issues, terrorism, natural disasters.
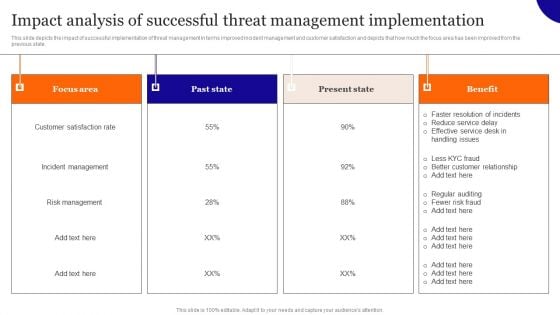
Impact Analysis Of Successful Threat Management Implementation Background PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Analysis Of Successful Threat Management Implementation Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Analysis Of Successful Threat Management Implementation Background PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF
This slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. The Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Real Time Assessment Of Security Threats Icons Slide For Real Time Assessment Of Security Threats Sample PDF
Presenting our innovatively structured real time assessment of security threats icons slide for real time assessment of security threats sample pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
SWOT Analysis Of ABC Software Company Threats Icons PDF
This slide shows the Threats related to ABC Software Company which includes Liability Laws, Lawsuits, Shortage of skilled workforce etc. Presenting swot analysis of abc software company threats icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like liability laws, intense competition, shortage of skilled workforce. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
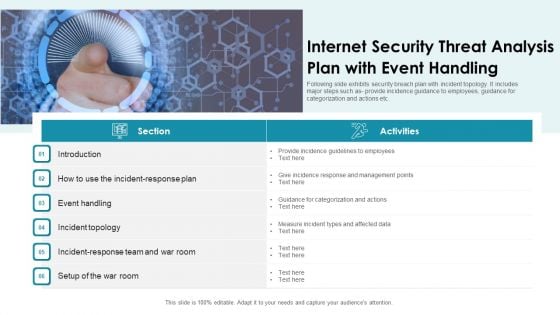
Internet Security Threat Analysis Plan With Event Handling Summary PDF
Following slide exhibits security breach plan with incident topology. It includes major steps such as- provide incidence guidance to employees, guidance for categorization and actions etc. Presenting internet security threat analysis plan with event handling summary pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including internet security threat analysis plan with event handling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































