Problem

Internet Security Threat Analysis Report Chart Introduction PDF
Following slide exhibits security and data breach report chart it includes major statistics such as- loss or theft of data, failure to redirect data and data posting to incorrect recipient. Pitch your topic with ease and precision using this internet security threat analysis report chart introduction pdf. This layout presents information on internet security threat analysis report chart. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
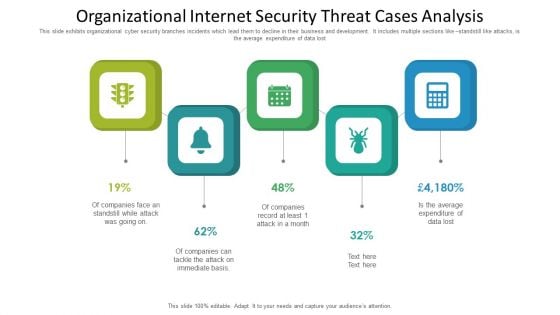
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Process For Responding To Internet Security Threats Template PDF
This slide exhibits process for responding to security data breach. It includes multiple steps such as- analyzing the current damage, keeping record how much damage is caused and so on. Pitch your topic with ease and precision using this process for responding to internet security threats template pdf. This layout presents information on process for responding to internet security threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
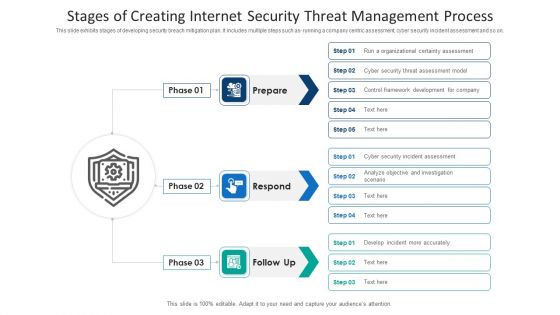
Stages Of Creating Internet Security Threat Management Process Information PDF
This slide exhibits stages of developing security breach mitigation plan. It includes multiple steps such as- running a company centric assessment, cyber security incident assessment and so on. Presenting stages of creating internet security threat management process information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including stages of creating internet security threat management process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Video Meeting Internet Security Threat Analysis Measures Brochure PDF
Following slide showcase video meeting security breach control tasks and actions. It includes multiple actions such as- run the recent version of application, utilizing corporate mails to send meeting links and so on. Persuade your audience using this video meeting internet security threat analysis measures brochure pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including video meeting internet security threat analysis measures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
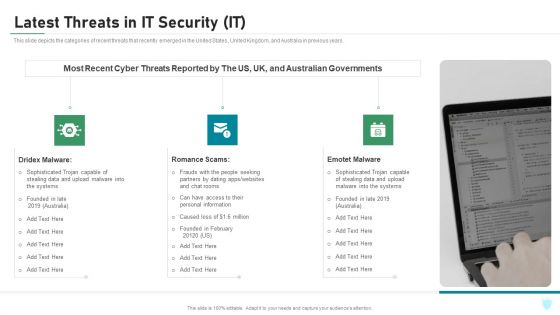
Latest Threats In IT Security IT Ppt Gallery Elements PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting latest threats in it security it ppt gallery elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dridex malware, romance scams, emotet malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
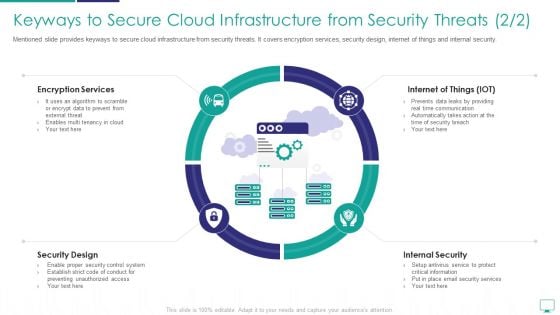
Keyways To Secure Cloud Infrastructure From Security Threats Formats PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a keyways to secure cloud infrastructure from security threats formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encryption services, internet of things, security design. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Latest Threats In Computer Security Inspiration PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting desktop security management latest threats in computer security inspiration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like financial, information, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
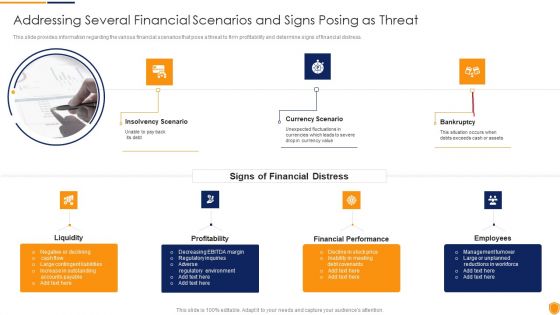
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Several Financial Diagrams PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. This is a mitigating cybersecurity threats and vulnerabilities addressing several financial diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like insolvency scenario, currency scenario, bankruptcy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
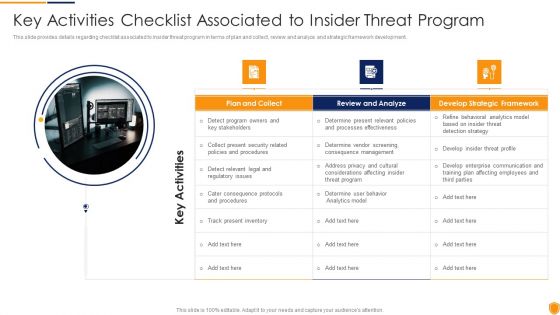
Mitigating Cybersecurity Threats And Vulnerabilities Key Activities Checklist Diagrams PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. This is a mitigating cybersecurity threats and vulnerabilities key activities checklist diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plan and collect, review and analyze, develop strategic framework. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
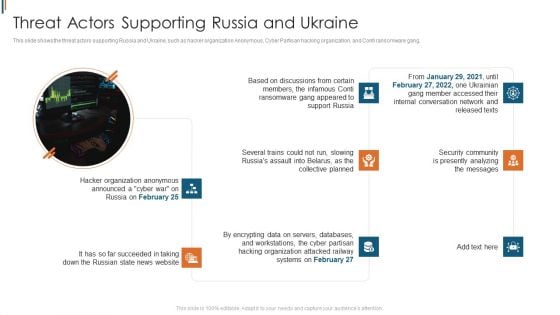
Ukraine Cyberwarfare Threat Actors Supporting Russia And Ukraine Graphics Pdf
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. This is a ukraine cyberwarfare threat actors supporting russia and ukraine graphics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security community is presently analyzing the messages, hacker organization anonymous announced, several trains could not run, slowing russias assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
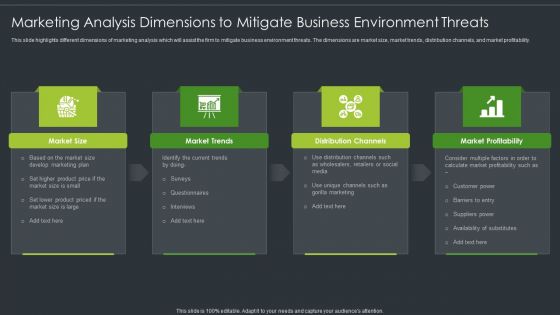
Marketing Analysis Dimensions To Mitigate Business Environment Threats Clipart PDF
This slide highlights different dimensions of marketing analysis which will assist the firm to mitigate business environment threats. The dimensions are market size, market trends, distribution channels, and market profitability. Persuade your audience using this Marketing Analysis Dimensions To Mitigate Business Environment Threats Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Market Size, Market Trends, Distribution Channels. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
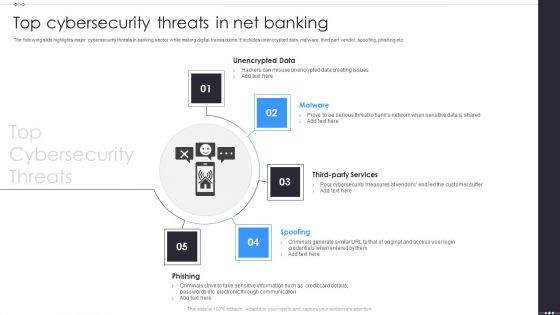
Top Cybersecurity Threats In Net Banking Download PDF
The following slide highlights major cybersecurity threats in banking sector while making digital transactions. It includes unencrypted data, malware, third part vendor, spoofing, phishing etc. Persuade your audience using this Top Cybersecurity Threats In Net Banking Download PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Unencrypted Data, Spoofing, Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Threats Loss Of Data Guidelines PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. This is a Cloud Security Threats Loss Of Data Guidelines PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategies, Service Provider, Organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
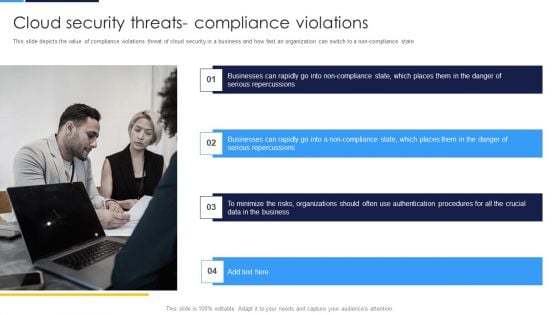
Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non compliance state.This is a Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Serious Repercussions, Data In The Business, Organizations Should You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss.This is a Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Information Exfiltration, Protection Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
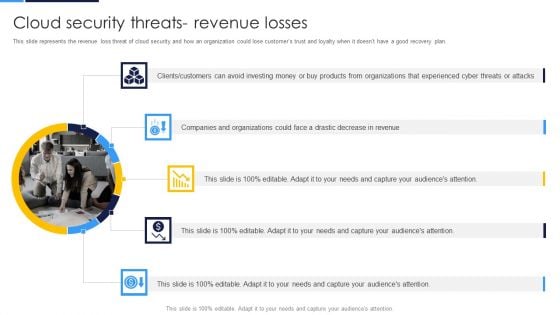
Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan.Presenting Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Clients Or Customers, Companies And Organizations, Organizations That Experienced. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.Presenting Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Encryption Services, Internal Security, Security Design. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Safety And Security Threat Report With Action Plan Mockup PDF
This slide shows report which can be used by an organization to prepare server security threat report. It includes date, time, description, action plan and remarks related to incident. Presenting Safety And Security Threat Report With Action Plan Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Action Plan, Remarks, Diagnostic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
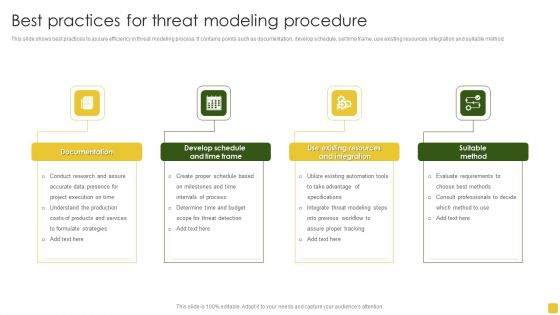
Best Practices For Threat Modeling Procedure Themes PDF
This slide shows best practices to assure efficiency in threat modeling process. It contains points such as documentation, develop schedule, set time frame, use existing resources, integration and suitable method.Presenting Best Practices For Threat Modeling Procedure Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Project Execution, Determine Budget, Existing Resources. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
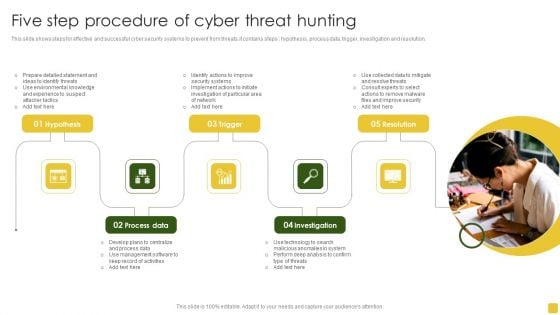
Five Step Procedure Of Cyber Threat Hunting Introduction PDF
This slide shows steps for effective and successful cyber security systems to prevent from threats.it contains steps hypothesis, process data, trigger, investigation and resolution. Persuade your audience using this Five Step Procedure Of Cyber Threat Hunting Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Detailed, Management Software, Management Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
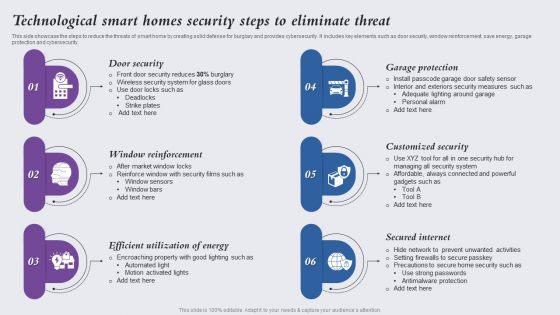
Technological Smart Homes Security Steps To Eliminate Threat Themes PDF
This side showcase the steps to reduce the threats of smart home by creating solid defense for burglary and provides cybersecurity. It includes key elements such as door security, window reinforcement, save energy, garage protection and cybersecurity. Presenting Technological Smart Homes Security Steps To Eliminate Threat Themes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Door Security, Window Reinforcement, Efficient Utilization Energy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
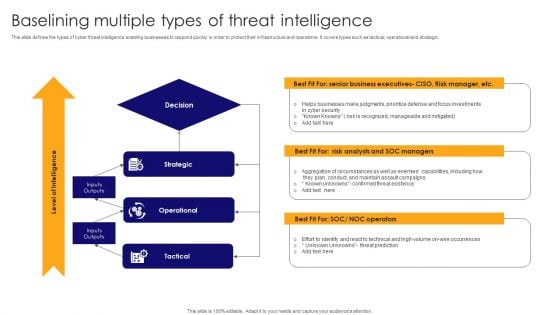
Baselining Multiple Types Of Threat Intelligence Pictures PDF
This slide defines the types of cyber threat intelligence enabling businesses to respond quickly in order to protect their infrastructure and operations. It covers types such as tactical, operational and strategic. Presenting Baselining Multiple Types Of Threat Intelligence Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Strategic, Operational, Tactical . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
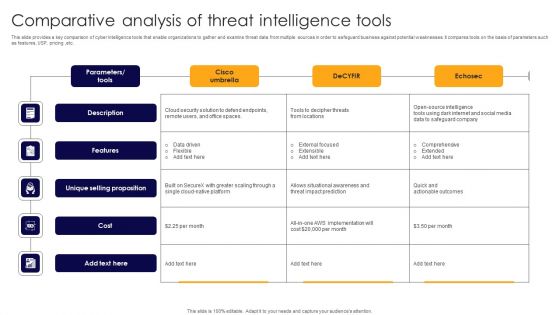
Comparative Analysis Of Threat Intelligence Tools Rules PDF
This slide provides a key comparison of cyber intelligence tools that enable organizations to gather and examine threat data from multiple sources in order to safeguard business against potential weaknesses. It compares tools on the basis of parameters such as features, USP, pricing ,etc. Showcasing this set of slides titled Comparative Analysis Of Threat Intelligence Tools Rules PDF. The topics addressed in these templates are Description, Features, Unique Selling Proposition. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
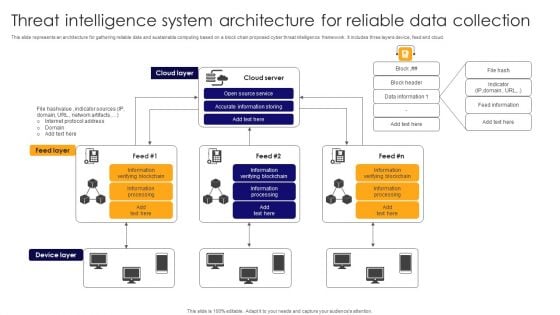
Threat Intelligence System Architecture For Reliable Data Collection Pictures PDF
This slide represents an architecture for gathering reliable data and sustainable computing based on a block chain proposed cyber threat intelligence framework . It includes three layers device, feed and cloud. Showcasing this set of slides titled Threat Intelligence System Architecture For Reliable Data Collection Pictures PDF. The topics addressed in these templates are Cloud Server, Accurate Information Storing, Open Source Service. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Chance Analysis Planning Ppt Layout Sample Files
This is a chance analysis planning ppt layout sample files. This is a four stage process. The stages in this process are evaluate risk, treat, identify, remove hazard.
Finance And Accounting Online Conversion Plan Key Challenges In Achieving Objectives Icons PDF
The slide provides the key challenges faced by the company while achieving the objective of accounting and finance transformation. Key issues include responsiveness to business needs efficiency and cost pressures technical issues governance, risk and compliance etc. Presenting Finance And Accounting Online Conversion Plan Key Challenges In Achieving Objectives Icons PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Finance Function, Responsiveness Business, Technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Diagram Umbrella For Protection Against External Threats Presentation Template
This business diagram is designed with graphics of umbrella. You may use this business slide to present protection against external threats. This diagram provides an effective way of displaying information you can edit text, color, shade and style as per you need.

Four Steps Of Threat Management Process Ppt Show Inspiration PDF
Presenting this set of slides with name four steps of threat management process ppt show inspiration pdf. This is a four stage process. The stages in this process are prevention, mitigation, preparedness, response, recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Analysis Process Planning Management Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name threat analysis process planning management ppt powerpoint presentation complete deck. The topics discussed in these slides are process, planning, management, evaluation, organization. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
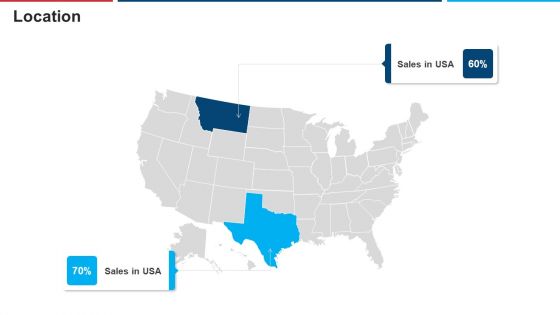
Mitigation Strategies For Operational Threat Location Ppt Portfolio Introduction PDF
This is a mitigation strategies for operational threat location ppt portfolio introduction pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like location. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
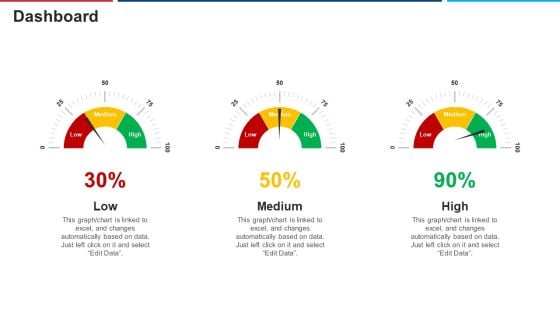
Mitigation Strategies For Operational Threat Dashboard Ppt Layouts Topics PDF
Deliver an awe inspiring pitch with this creative mitigation strategies for operational threat dashboard ppt layouts topics pdf bundle. Topics like dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slide For How To Intensify Project Threats Elements PDF
Download our innovative and attention grabbing icons slide for how to intensify project threats elements pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.

How To Intensify Project Threats Post It Notes Clipart PDF
Presenting how to intensify project threats post it notes clipart pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like post it notes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
How To Intensify Project Threats Roadmap Slides PDF
Presenting how to intensify project threats roadmap slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like roadmap. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
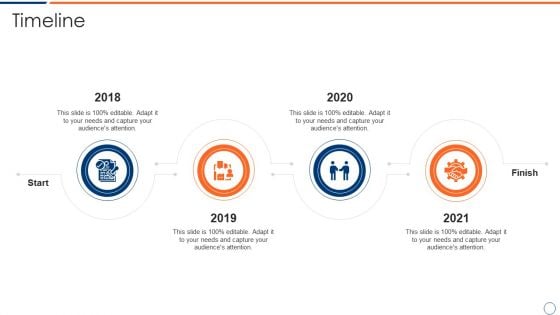
How To Intensify Project Threats Timeline Themes PDF
This is a how to intensify project threats timeline themes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2018 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Icons Slide For Threat Administration Bundle Guidelines PDF
Introducing our well designed icons slide for threat administration bundle guidelines pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Threat Administration Bundle Table Of Contents Microsoft PDF
Presenting threat administration bundle table of contents microsoft pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like business, organization, management, communication, action plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Icons Slide For Mitigating Cybersecurity Threats And Vulnerabilities Microsoft PDF
Introducing our well designed icons slide for mitigating cybersecurity threats and vulnerabilities microsoft pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Threat Management At Workplace Elements Pdf
Introducing our well designed icons slide for threat management at workplace elements pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For IT Threats Response Playbook Download PDF
Download our innovative and attention grabbing Icons Slide For IT Threats Response Playbook Download PDF template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
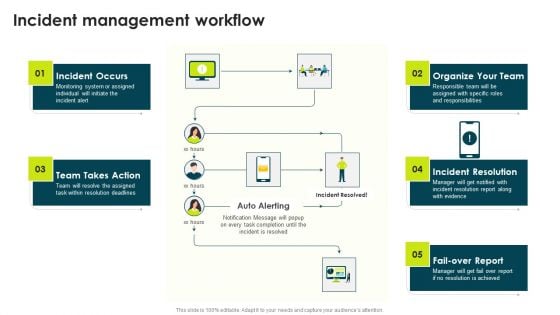
IT Threats Response Playbook Incident Management Workflow Themes PDF
Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Incident Management Workflow Themes PDF bundle. Topics like Incident Occurs, Incident Resolution, Resolution Achieved can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
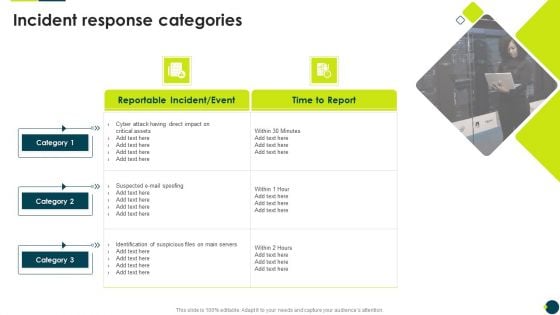
IT Threats Response Playbook Incident Response Categories Rules PDF
Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Incident Response Categories Rules PDF. Use them to share invaluable insights on Identification Suspicious, Direct Impact, Time To Report and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Threats Response Playbook SWOT Analysis Professional PDF
This is a IT Threats Response Playbook SWOT Analysis Professional PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strengths, Weaknesses, Opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For IT Threats Response Playbook Clipart PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For IT Threats Response Playbook Clipart PDF. Use them to share invaluable insights on Security Incidents, Figures And Statistics, Ransom Payment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Icons Slides For Fraud Threat Administration Guide Pictures PDF
Introducing our well designed Icons Slides For Fraud Threat Administration Guide Pictures PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
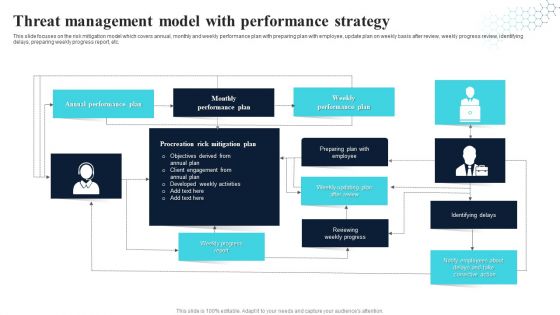
Threat Management Model With Performance Strategy Topics PDF
Showcasing this set of slides titled Threat Management Model With Performance Strategy Topics PDF. The topics addressed in these templates are Monthly Performance Plan, Weekly Performance Plan, Annual Performance Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icons Slide For Information Technology Threat Mitigation Methods Icons PDF
Presenting our innovatively structured Icons Slide For Information Technology Threat Mitigation Methods Icons PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
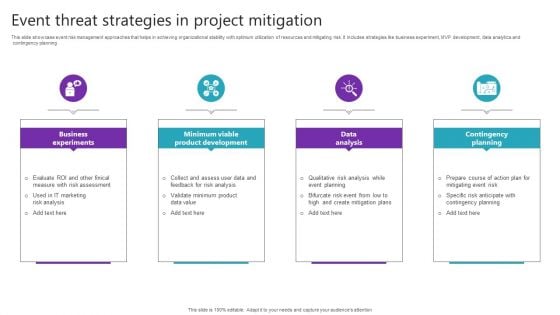
Event Threat Strategies In Project Mitigation Diagrams PDF
Presenting Event Threat Strategies In Project Mitigation Diagrams PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Business Experiments, Minimum Viable, Product Development. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
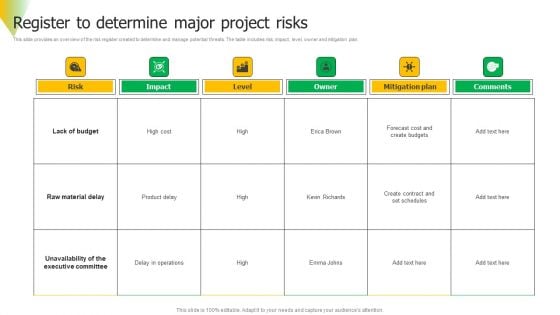
Risk Assessment Register To Determine Major Project Risks Background PDF
This slide provides an overview of the risk register created to determine and manage potential threats. The table includes risk, impact, level, owner and mitigation plan. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Risk Assessment Register To Determine Major Project Risks Background PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Risk Assessment Register To Determine Major Project Risks Background PDF today and make your presentation stand out from the rest
Our Offerings For House Snow Removal Solutions Proposal Ppt File Icons PDF
This slide represents key offerings for snow removal contract proposal including snow and ice management, sidewalk management, roof snow removal, snow hauling and relocation and risk assessment. Boost your pitch with our creative Our Offerings For House Snow Removal Solutions Proposal Ppt File Icons PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
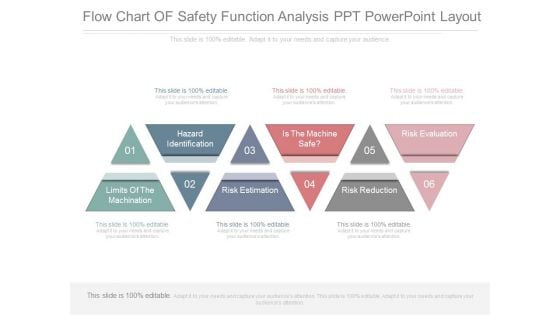
Flow Chart Of Safety Function Analysis Ppt Powerpoint Layout
This is a flow chart of safety function analysis ppt powerpoint layout. This is a six stage process. The stages in this process are hazard identification, limits of the machination, risk estimation, is the machine safe, risk reduction, risk evaluation.
Five Arrows Process With Text Holders Ppt PowerPoint Presentation File Deck
This is a five arrows process with text holders ppt powerpoint presentation file deck. This is a five stage process. The stages in this process are risk management, risk factors, risk variable.
Five Steps In Control Process Ppt PowerPoint Presentation Inspiration Master Slide
This is a five steps in control process ppt powerpoint presentation inspiration master slide. This is a five stage process. The stages in this process are risk management, risk factors, risk variable.
Five Steps Of Productivity Improvement Innovation And Security Ppt PowerPoint Presentation Layouts Inspiration
This is a five steps of productivity improvement innovation and security ppt powerpoint presentation layouts inspiration. This is a five stage process. The stages in this process are risk management, risk factors, risk variable.
Four Steps Marketing Research Process Ppt PowerPoint Presentation Infographic Template Graphics
This is a four steps marketing research process ppt powerpoint presentation infographic template graphics. This is a four stage process. The stages in this process are risk management, risk factors, risk variable.

Six Bullet Points With Text Boxes Ppt PowerPoint Presentation Outline Layouts
This is a six bullet points with text boxes ppt powerpoint presentation outline layouts. This is a six stage process. The stages in this process are risk management, risk factors, risk variable.
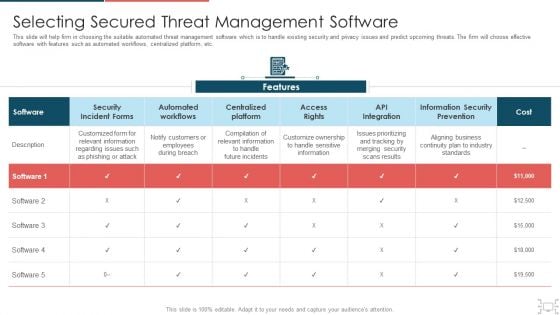
Cyber Security Administration In Organization Selecting Secured Threat Management Software Themes PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization selecting secured threat management software themes pdf. Use them to share invaluable insights on selecting secured threat management software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
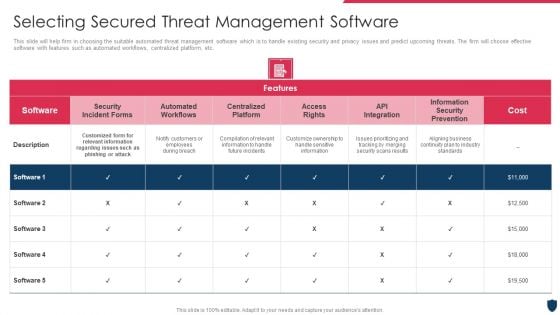
Cyber Safety Incident Management Selecting Secured Threat Management Software Information PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative cyber safety incident management selecting secured threat management software information pdf bundle. Topics like selecting secured threat management software can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
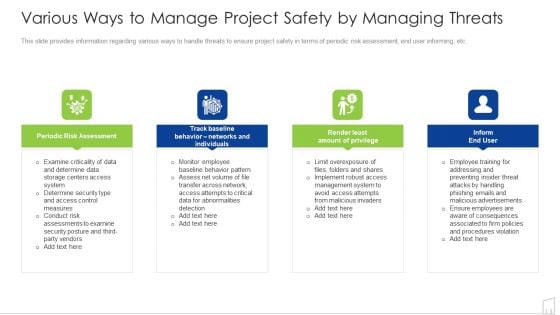
Various Ways To Manage Project Safety By Managing Threats Ppt Ideas Deck PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Presenting various ways to manage project safety by managing threats ppt ideas deck pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like determine, system, data, risk, periodic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































