Process Safety

Investment Banking Security Underwriting Pitchbook Leadership Senior Executive Team Inspiration PDF
The slide provides the name and designation of the key management team members CEO, CFO, department head etc. Of the company. It also provides the major transaction experience work experience of the executives.This is a Investment Banking Security Underwriting Pitchbook Leadership Senior Executive Team Inspiration PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Transaction Experience, Designation, Introduced You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Based Email Security Market Report Issues Faced By Companies Data Ppt Icon Templates PDF
Various issues faced by the end user in E Mail marketing Industry are shown in this slide. Presenting cloud based email security market report issues faced by companies data ppt icon templates pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
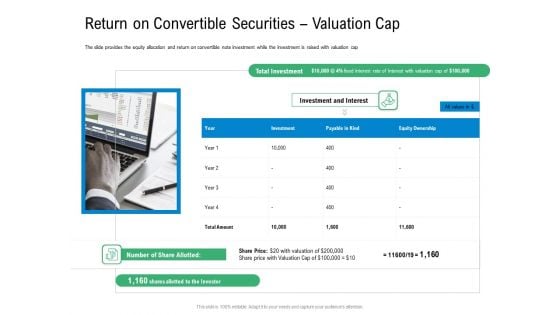
Convertible Preferred Stock Funding Pitch Deck Return On Convertible Securities Valuation Cap Slides PDF
The slide provides the equity allocation and return on convertible note investment while the investment is raised with valuation cap. Presenting convertible preferred stock funding pitch deck return on convertible securities valuation cap slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like return on convertible securities valuation cap. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Types Of Threats In IT Security IT Ppt Summary Graphics Tutorials PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting types of threats in it security it ppt summary graphics tutorials pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
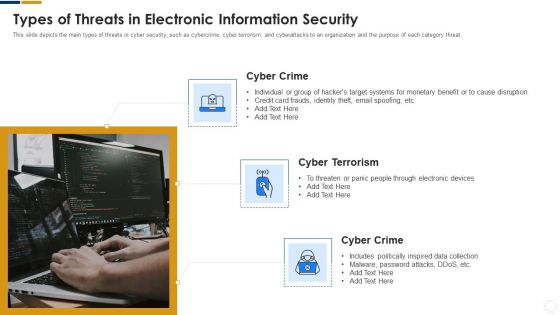
Cybersecurity Types Of Threats In Electronic Information Security Ppt Examples PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a cybersecurity types of threats in electronic information security ppt examples pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber crime. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats Next Evolution Of SIEM Software Sample PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. This is a real time assessment of security threats next evolution of siem software sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network traffic analysis, endpoint monitoring, threat intelligence, siem foundation, security orchestration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
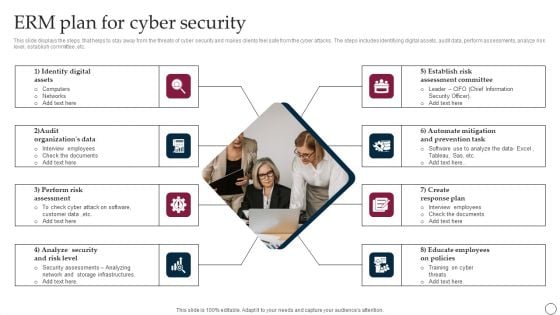
ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF
This slide displays the steps that helps to stay away from the threats of cyber security and makes clients feel safe from the cyber attacks. The steps includes Identifying digital assets, audit data, perform assessments, analyze risk level, establish committee ,etc. Persuade your audience using this ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Establish Risk Assessment Committee, Create Response Plan, Educate Employees On Policies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organization Impact Metrics Strategic Hacking Prevention Awareness Training For IT Security Graphics PDF
This slide the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Presenting organization impact metrics strategic hacking prevention awareness training for it security graphics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like organization, policy violations, data loss incidents, human resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
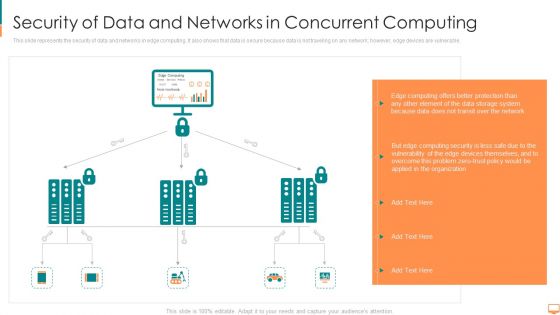
Security Of Data And Networks In Concurrent Computing Ppt File Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. This is a security of data and networks in concurrent computing ppt file themes pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like computing, transit, storage, system, protection, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT OT Convergence Security Objectives Challenges Catalysts And Benefits Designs PDF
This slide covers objectives challenges catalysts and benefits of the Security in IT OT convergence and Reduce systems cyberattack surface. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IT OT Convergence Security Objectives Challenges Catalysts And Benefits Designs PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IT OT Convergence Security Objectives Challenges Catalysts And Benefits Designs PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
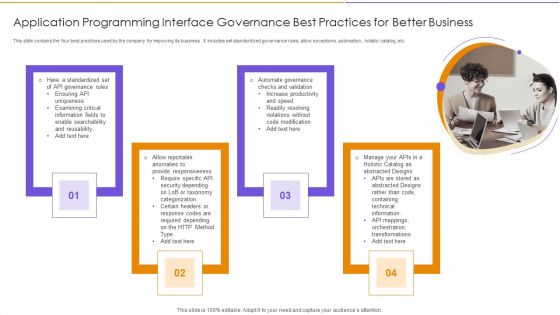
Application Programming Interface Governance Best Practices For Better Business Diagrams PDF
This slide contains the four best practices used by the company for improving its business . It includes set standardized governance rules, allow exceptions, automation , holistic catalog, etc. Presenting Application Programming Interface Governance Best Practices For Better Business Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Depending, Increase Productivity, Technical Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Enhancing Information Technology With Strategic Information Security And Governance Icons PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Enhancing Information Technology With Strategic Information Security And Governance Icons PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Communication Plan For Information Technology Security Based On Audience Type Demonstration PDF
This slide consists of a communication plan information technology security to be deployed by managers based on the type of audience. Key elements include communication, frequency, communication goal, owner, etc. Presenting Communication Plan For Information Technology Security Based On Audience Type Demonstration PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Project Status Report, Team Standup, Task Progress Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
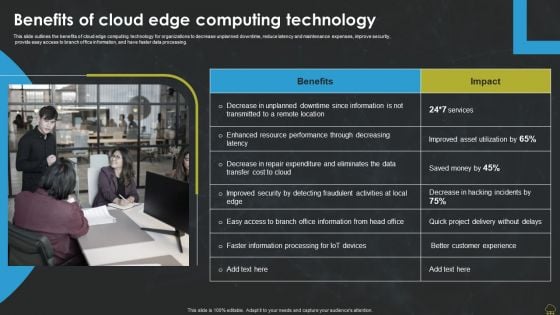
Integrating Edge Computing To Enhance Operational Efficiency Benefits Of Cloud Edge Computing Technology Designs PDF
This slide outlines the benefits of cloud edge computing technology for organizations to decrease unplanned downtime, reduce latency and maintenance expenses, improve security, provide easy access to branch office information, and have faster data processing. Want to ace your presentation in front of a live audience Our Integrating Edge Computing To Enhance Operational Efficiency Benefits Of Cloud Edge Computing Technology Designs PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
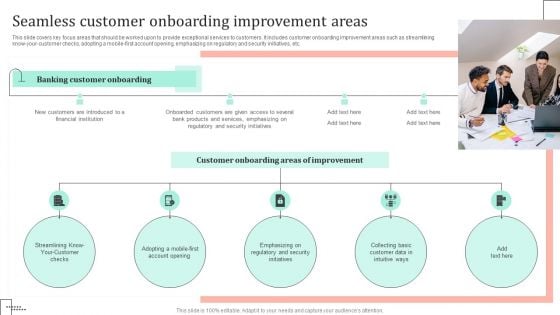
Omnichannel Strategy Implementation For Banking Solutions Seamless Customer Onboarding Improvement Areas Guidelines PDF
This slide covers key focus areas that should be worked upon to provide exceptional services to customers. It includes customer onboarding improvement areas such as streamlining know your customer checks, adopting a mobile first account opening, emphasizing on regulatory and security initiatives, etc. The Omnichannel Strategy Implementation For Banking Solutions Seamless Customer Onboarding Improvement Areas Guidelines PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Develop Corporate Cyber Security Risk Mitigation Plan Organization Mission And Vision Statement Download PDF
Presenting develop corporate cyber security risk mitigation plan organization mission and vision statement download pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like vision, mission. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
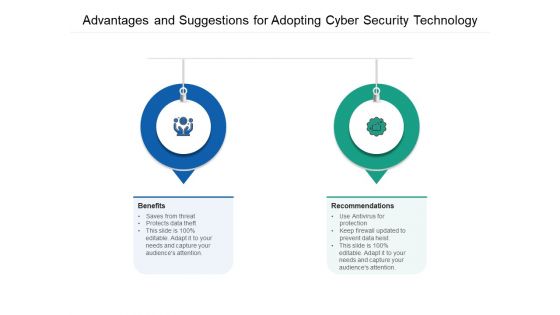
Advantages And Suggestions For Adopting Cyber Security Technology Ppt PowerPoint Presentation Gallery Example Topics PDF
Presenting advantages and suggestions for adopting cyber security technology ppt powerpoint presentation gallery example topics pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including benefits, recommendation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
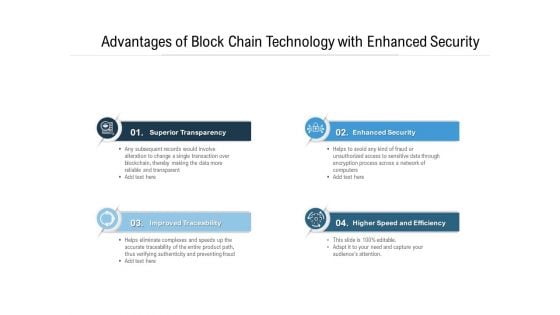
Advantages Of Block Chain Technology With Enhanced Security Ppt PowerPoint Presentation Gallery Good PDF
Presenting advantages of block chain technology with enhanced security ppt powerpoint presentation gallery good pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including transparency, traceability, efficiency. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Security Operations Center Workflow With Validation And Reporting Ppt Icon Background Designs PDF
Presenting cyber security operations center workflow with validation and reporting ppt icon background designs pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including workflow, document, reference. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
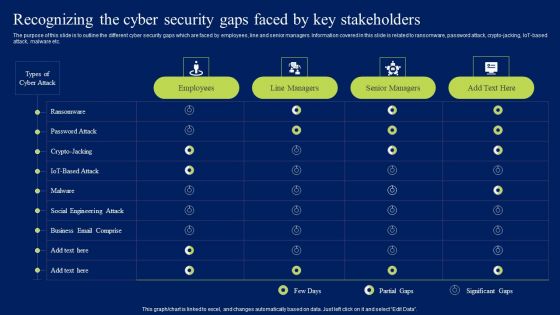
Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Get a simple yet stunning designed Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
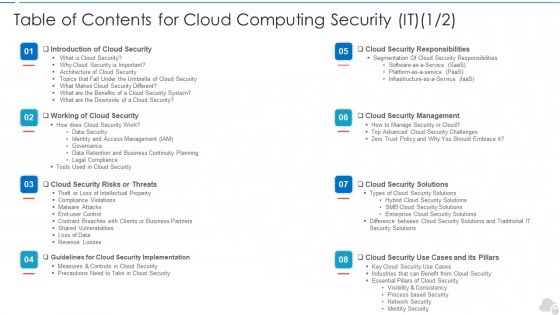
Table Of Contents For Cloud Computing Security IT Business Ppt File Inspiration PDF
Deliver an awe inspiring pitch with this creative table of contents for cloud computing security it business ppt file inspiration pdf bundle. Topics like cloud security implementation, cloud security responsibilities, cloud security management, cloud security solutions, cloud security risks or threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Complete Beginners Guide Multisignature Wallets To Enhance Wallet Security Fin SS V
This slide shows details regarding Multisignature wallets which can be used by Bitcoin holders to improve the security of accounts. It includes information about features and traction authorization. Slidegeeks has constructed Complete Beginners Guide Multisignature Wallets To Enhance Wallet Security Fin SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide shows details regarding Multisignature wallets which can be used by Bitcoin holders to improve the security of accounts. It includes information about features and traction authorization.
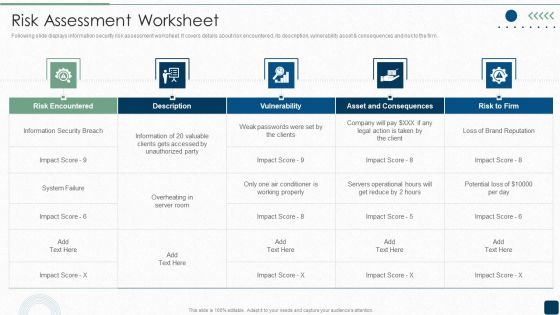
ISO 27001 Certification Procedure Risk Assessment Worksheet Diagrams PDF
Following slide displays information security risk assessment worksheet. It covers details about risk encountered, its description, vulnerability asset consequences and risk to the firm.Deliver an awe inspiring pitch with this creative ISO 27001 Certification Procedure Risk Assessment Worksheet Diagrams PDF bundle. Topics like Risk Encountered, Asset And Consequences, Information Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ISO 27001 Organizational Qualifying Procedure Risk Assessment Worksheet Information PDF
Following slide displays information security risk assessment worksheet. It covers details about risk encountered, its description, vulnerability asset consequences and risk to the firm.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Risk Assessment Worksheet Information PDF bundle. Topics like Information Security, Risk Encountered, Asset And Consequences can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
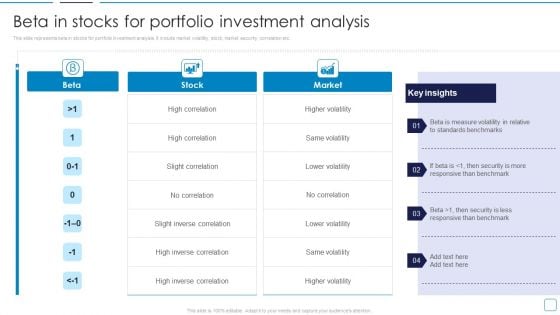
Portfolio Wealth Management Beta In Stocks For Portfolio Investment Analysis Elements PDF
This slide represents beta in stocks for portfolio investment analysis. It include market volatility, stock, market security, correlation etc. Deliver an awe inspiring pitch with this creative Portfolio Wealth Management Beta In Stocks For Portfolio Investment Analysis Elements PDF bundle. Topics like Standards Benchmarks, Security, Stock, Market can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Tools To Be Implemented Portrait PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring tools to be implemented portrait pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring user activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
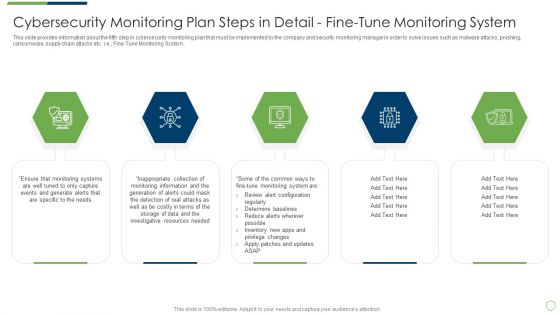
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Fine Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail fine sample pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail monitoring network traffic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Real Time Assessment Of Security Threats Need For SIEM Software In Your Company Template PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management. Presenting real time assessment of security threats need for siem software in your company template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detecting incidents, compliance with regulations, efficient incident management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Template PDF
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Template PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

SDN Security Architecture Table Of Contents Ppt PowerPoint Presentation File Example PDF
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download SDN Security Architecture Table Of Contents Ppt PowerPoint Presentation File Example PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
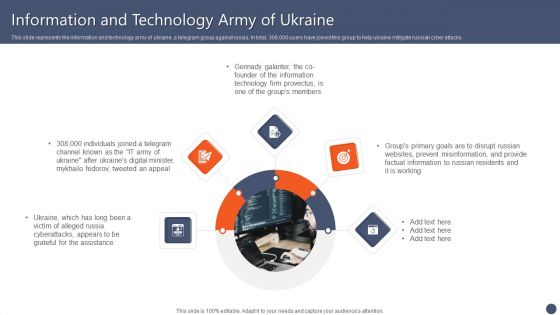
Series Of Cyber Security Attacks Against Ukraine 2022 Information And Technology Army Of Ukraine Diagrams PDF
This slide represents the information and technology army of ukraine, a telegram group against russia. In total, 308,000 users have joined this group to help ukraine mitigate russian cyber attacks. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Series Of Cyber Security Attacks Against Ukraine 2022 Information And Technology Army Of Ukraine Diagrams PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Series Of Cyber Security Attacks Against Ukraine 2022 Information And Technology Army Of Ukraine Diagrams PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Email Security Encryption And Data Loss Prevention 30 60 90 Days Plan Diagrams PDF
This is a email security encryption and data loss prevention 30 60 90 days plan diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
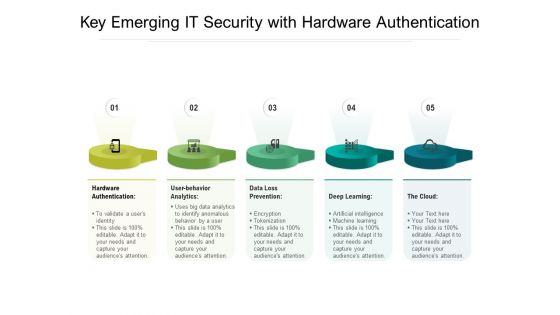
Key Emerging IT Security With Hardware Authentication Ppt PowerPoint Presentation Gallery File Formats PDF
Persuade your audience using this key emerging it security with hardware authentication ppt powerpoint presentation gallery file formats pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including hardware authentication, user behavior analytics, data loss prevention, deep learning, the cloud. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
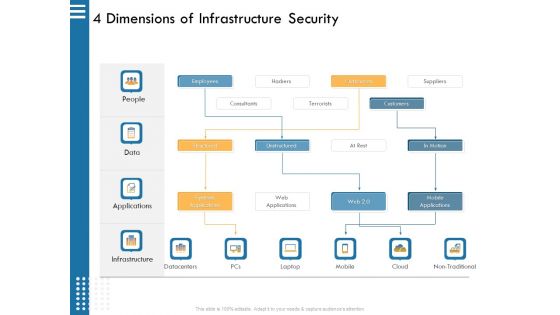
IT Infrastructure Governance 4 Dimensions Of Infrastructure Security Ppt File Example PDF
This is a it infrastructure governance 4 dimensions of infrastructure security ppt file example pdf. template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employees, outsources, hackers, terrorists, consultants. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
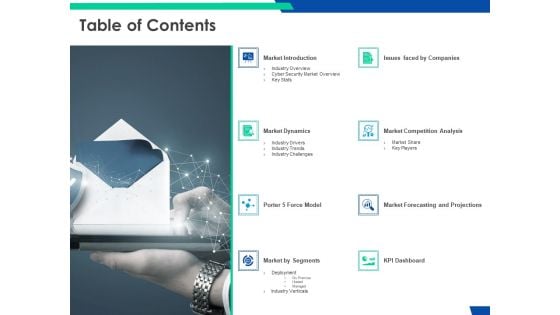
Cloud Based Email Security Market Report Table Of Contents Ppt Inspiration Vector PDF
Presenting cloud based email security market report table of contents ppt inspiration vector pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like market introduction, market dynamics, issues faced by companies, kpi dashboard, market by segments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
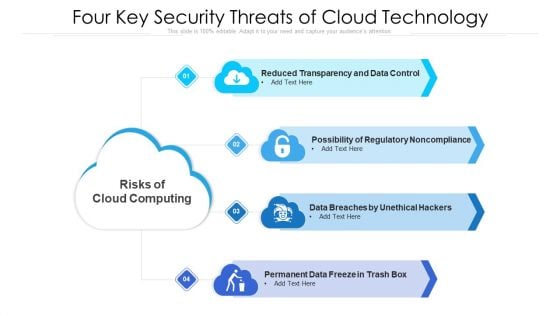
Four Key Security Threats Of Cloud Technology Ppt PowerPoint Presentation Gallery Introduction PDF
Presenting four key security threats of cloud technology ppt powerpoint presentation gallery introduction pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data breaches by unethical hackers, permanent data freeze in trash box, possibility of regulatory noncompliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Addressing Mission Vision And Core Values Associated To Firm Food Security Excellence Ppt Ideas Demonstration PDF
This slide provides information regarding the mission, vision and core values associated to firm. Presenting addressing mission vision and core values associated to firm food security excellence ppt ideas demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like mission, vision, core values. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Employee Awareness Training Budget For FY2022 Ppt Show Slide PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Presenting it security employee awareness training budget for fy2022 ppt show slide pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like training, duration, budget, capability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
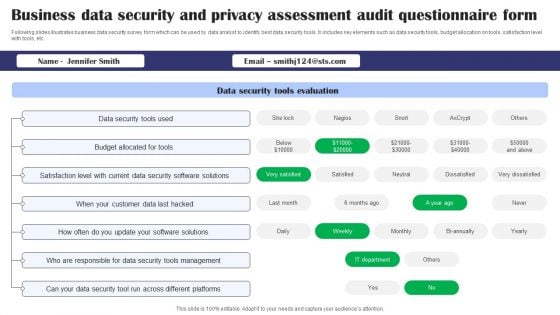
Business Data Security And Privacy Assessment Audit Questionnaire Form Survey SS
Following slides illustrates business data security survey form which can be used by data analyst to identify best data security tools. It includes key elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Showcasing this set of slides titled Business Data Security And Privacy Assessment Audit Questionnaire Form Survey SS. The topics addressed in these templates are Data Security Tools Evaluation, Data Security Tools Used, Budget Allocated For Tools, Data Security Software Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
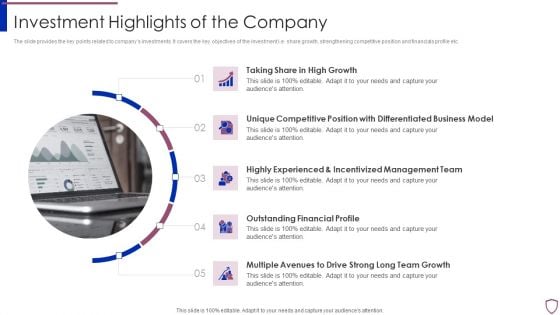
Financing Catalogue For Security Underwriting Agreement Investment Highlights Of The Company Sample PDF
The slide provides the key points related to companys investments. It covers the key objectives of the investment i.e. share growth, strengthening competitive position and financials profile etc. Presenting financing catalogue for security underwriting agreement investment highlights of the company sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like growth, business, management, financial. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
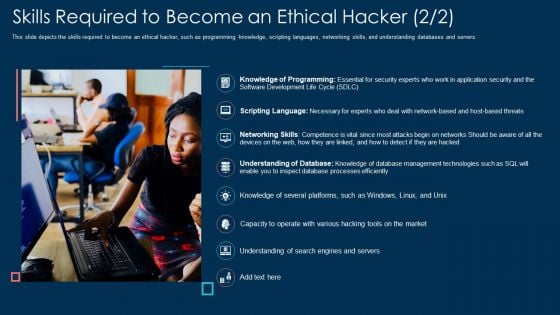
Skills Required To Become An Ethical Hacker Security Ppt Layouts Guide PDF
This slide depicts the skills required to become an ethical hacker, such as programming knowledge, scripting languages, networking skills, and understanding databases and servers. Presenting skills required to become an ethical hacker security ppt layouts guide pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like networking, technologies, management, database. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
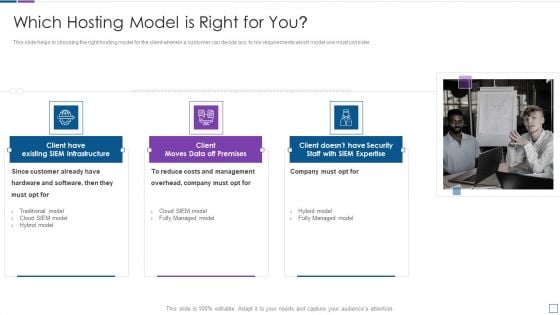
Real Time Assessment Of Security Threats Which Hosting Model Is Right For You Clipart PDF
This slide helps in choosing the right hosting model for the client wherein a customer can decide acc. to his requirements which model one must consider. This is a real time assessment of security threats which hosting model is right for you clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like costs and management, company, hardware and software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training. If you are looking for a format to display your unique thoughts, then the professionally designed Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
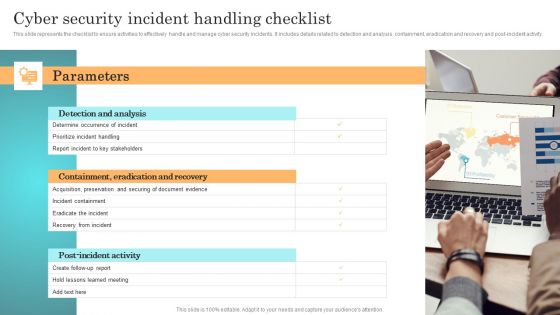
Incident Response Techniques Deployement Cyber Security Incident Handling Checklist Infographics PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF

User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. If you are looking for a format to display your unique thoughts, then the professionally designed User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Find highly impressive Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
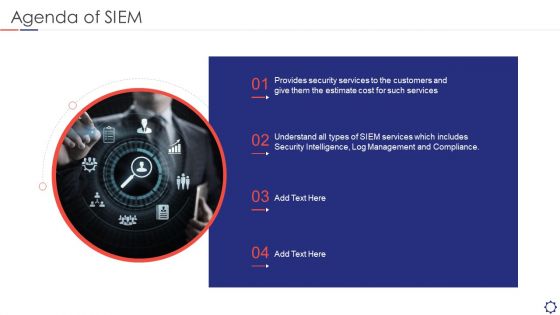
Agenda Of SIEM Ppt Pictures Model PDF
This is a agenda of siem ppt pictures model pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management, Security Intelligence, Services, cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Alert On Computer Keyboard Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Computer PowerPoint Templates because they pinpoint the core values of your organisation. Use our Technology PowerPoint Templates because these ideas abound in the strong branches of your brain. Download our Signs PowerPoint Templates because health of the determines the quality of our lives. Present our Business PowerPoint Templates because your fledgling career is in the chrysallis stage. Nurture it and watch it grow into a beautiful butterfly. Download and present our Triangles PowerPoint Templates because it unravels each one for your audience while setting key timelines as you go along.Use these PowerPoint slides for presentations relating to Alert button on a black computer keyboard, computer, technology, signs, business, triangles. The prominent colors used in the PowerPoint template are Red, Black, Yellow. We assure you our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Breathtaking. Customers tell us our keyboard PowerPoint templates and PPT Slides are Classic. You can be sure our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Beautiful. People tell us our a PowerPoint templates and PPT Slides are Splendid. Presenters tell us our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Adorable. People tell us our technology PowerPoint templates and PPT Slides are Efficient. Spread your ideas far and wide. Our Alert On Computer Keyboard Security PowerPoint Templates Ppt Backgrounds For Slides 1212 are dependable carriers.

Strategic IT Infrastructure Augmentation Roadmap Ppt PowerPoint Presentation File Example PDF
This slide provides information regarding the strategic IT infrastructure augmentation roadmap. The focus areas include testing, improvement, integration and security, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Strategic IT Infrastructure Augmentation Roadmap Ppt PowerPoint Presentation File Example PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Strategic IT Infrastructure Augmentation Roadmap Ppt PowerPoint Presentation File Example PDF today and make your presentation stand out from the rest.
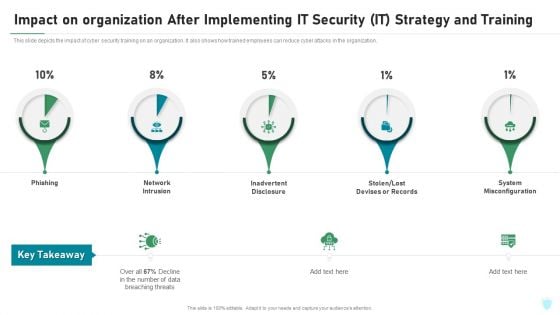
Impact On Organization After Implementing IT Security IT Strategy And Training Ppt File Portrait PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this impact on organization after implementing it security it strategy and training ppt file portrait pdf. Use them to share invaluable insights on phishing, network intrusion, inadvertent disclosure, stolen or lost devises or records, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
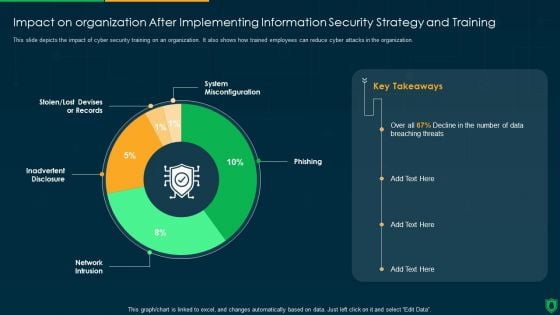
Impact On Organization After Implementing Information Security Strategy Ppt PowerPoint Presentation Gallery Deck PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this impact on organization after implementing information security strategy ppt powerpoint presentation gallery deck pdf. Use them to share invaluable insights on system misconfiguration, phishing, network intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Digitalization Of Operative Enterprises IT OT Convergence Security Objectives Challenges Catalysts And Benefits Download PDF
This slide covers objectives challenges catalysts and benefits of the security in IT or OT convergence and reduce systems cyberattack surface. This is a Digitalization Of Operative Enterprises IT OT Convergence Security Objectives Challenges Catalysts And Benefits Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
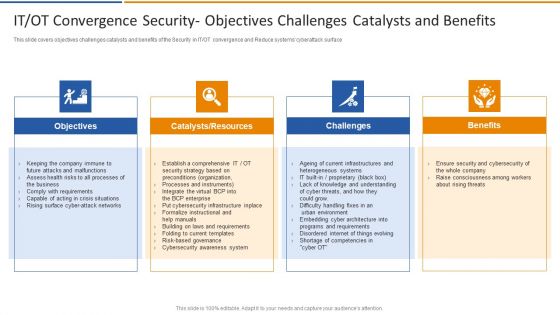
IT OT Convergence Security Objectives Challenges Smart Venture Digitial Transformation Designs PDF
This slide covers objectives challenges catalysts and benefits of the Security in IT or OT convergence and Reduce systems cyberattack surface. This is a IT OT Convergence Security Objectives Challenges Smart Venture Digitial Transformation Designs PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Catalysts, Resources, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
6 Stage Yearly Business Planning Cycle For Cyber Security Project Icons PDF
This slide signifies the six step yearly planning life cycle for cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor.Persuade your audience using this 6 Stage Yearly Business Planning Cycle For Cyber Security Project Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Money Laundering, System Malfunction, Financial Transaction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
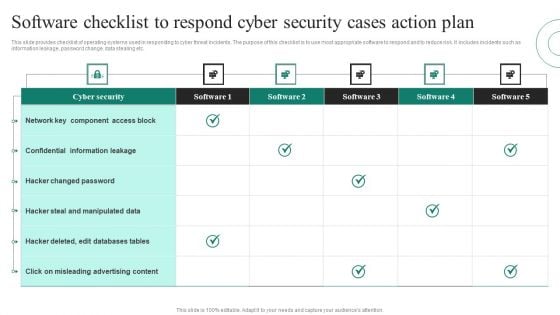
Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF
This slide provides checklist of operating systems used in responding to cyber threat incidents. The purpose of this checklist is to use most appropriate software to respond and to reduce risk. It includes incidents such as information leakage, password change, data stealing etc. Pitch your topic with ease and precision using this Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF. This layout presents information on Cyber Security, Confidential Information Leakage, Hacker Changed Password. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
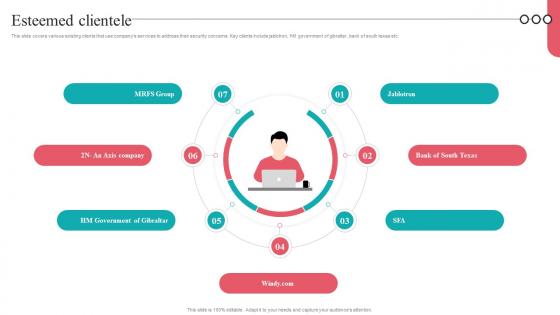
Esteemed Clientele Camera Management Platform Investor Funding Elevator Pitch Deck
This slide covers various existing clients that use companys services to address their security concerns. Key clients include jablotron, HM government of gibraltar, bank of south texas etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Esteemed Clientele Camera Management Platform Investor Funding Elevator Pitch Deck a try. Our experts have put a lot of knowledge and effort into creating this impeccable Esteemed Clientele Camera Management Platform Investor Funding Elevator Pitch Deck. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers various existing clients that use companys services to address their security concerns. Key clients include jablotron, HM government of gibraltar, bank of south texas etc.

Analyse And Rank Impact Of Cyber Threat Ppt PowerPoint Presentation Diagram PDF
The following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Analyse And Rank Impact Of Cyber Threat Ppt PowerPoint Presentation Diagram PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Analyse And Rank Impact Of Cyber Threat Ppt PowerPoint Presentation Diagram PDF today and make your presentation stand out from the rest.
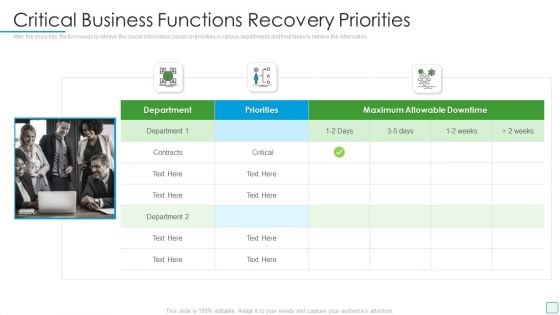
Developing Firm Security Strategy Plan Critical Business Functions Recovery Priorities Infographics PDF
After the crisis hits, the firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. This is a developing firm security strategy plan critical business functions recovery priorities infographics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like critical business functions recovery priorities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Determine Staff Training Schedule For Skills Enhancement Infographics PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting developing firm security strategy plan determine staff training schedule for skills enhancement infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like determine staff training schedule for skills enhancement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































