Process Safety
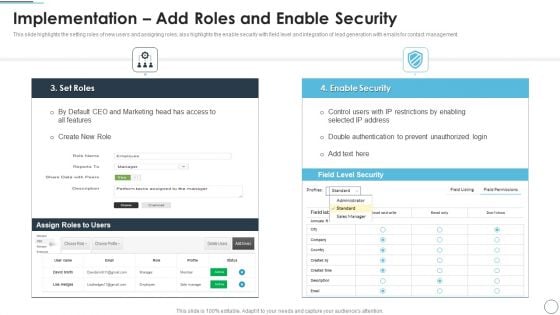
CRM Solutions Implementation Strategy Implementation Add Roles And Enable Security Information PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative CRM Solutions Implementation Strategy Implementation Add Roles And Enable Security Information PDF bundle. Topics like Restrictions By Enabling, Prevent Unauthorized, Double Authentication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
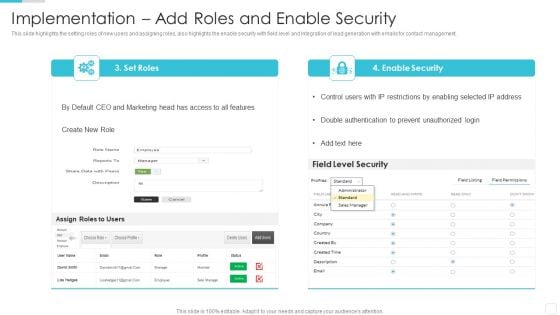
Sales CRM Cloud Solutions Deployment Implementation Add Roles And Enable Security Designs PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative Sales CRM Cloud Solutions Deployment Implementation Add Roles And Enable Security Designs PDF bundle. Topics like Restrictions By Enabling, Double Authentication, Prevent Unauthorized can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
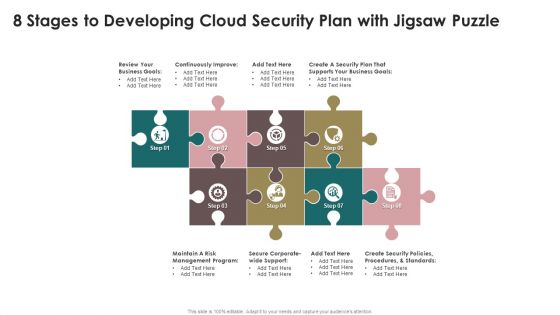
8 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Rules PDF
Persuade your audience using this 8 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Rules PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Business Goals, Security Plan, Management Program. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Identifying Employees For Information Security Training Programme Cybersecurity Risk Assessment Pictures PDF
This slide showcases plan that can help organization to conduct training for employees for information security risk management. It will enable employees to monitor risks and resolve them in timely manner. There are so many reasons you need a Identifying Employees For Information Security Training Programme Cybersecurity Risk Assessment Pictures PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
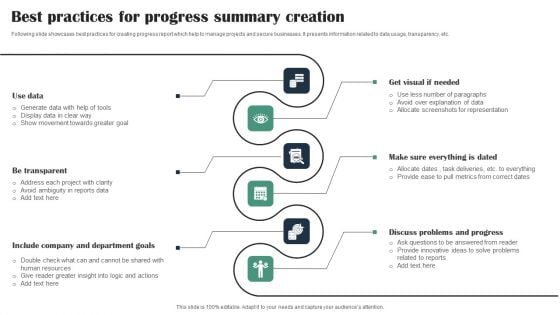
Best Practices For Progress Summary Creation Ideas PDF
Following slide showcases best practices for creating progress report which help to manage projects and secure businesses. It presents information related to data usage, transparency, etc. Presenting Best Practices For Progress Summary Creation Ideas PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Use Data, Be Transparent, Include Company Department Goals. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
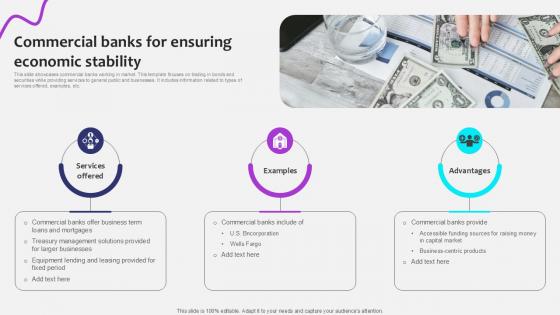
Commercial Banks For Ensuring Initiating Globalization Of Banking Ppt Powerpoint
This slide showcases commercial banks working in market. This template focuses on trading in bonds and securities while providing services to general public and businesses. It includes information related to types of services offered, examples, etc. There are so many reasons you need a Commercial Banks For Ensuring Initiating Globalization Of Banking Ppt Powerpoint. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases commercial banks working in market. This template focuses on trading in bonds and securities while providing services to general public and businesses. It includes information related to types of services offered, examples, etc.
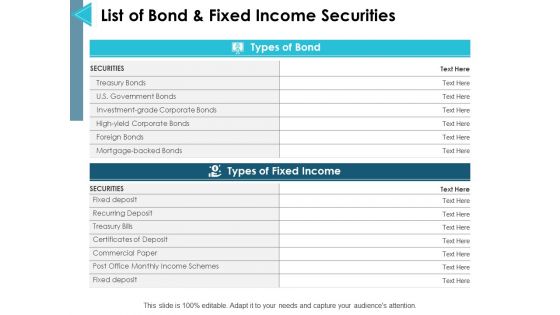
List Of Bond And Fixed Income Securities Ppt PowerPoint Presentation Layouts Graphics Design
This is a list of bond and fixed income securities ppt powerpoint presentation layouts graphics design. The topics discussed in this diagram are management, marketing, business, strategy, planning. This is a completely editable PowerPoint presentation, and is available for immediate download.

Cyber Security For Your Organization Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name cyber security for your organization ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are risk management, business, analysis, goal, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
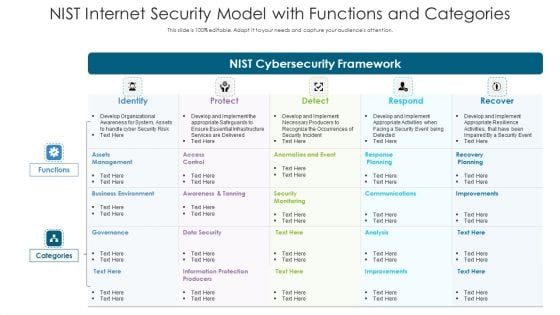
NIST Internet Security Model With Functions And Categories Ppt PowerPoint Presentation Model Show PDF
Showcasing this set of slides titled NIST internet security model with functions and categories ppt powerpoint presentation model show pdf. The topics addressed in these templates are assets management, recovery planning, information protection producers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
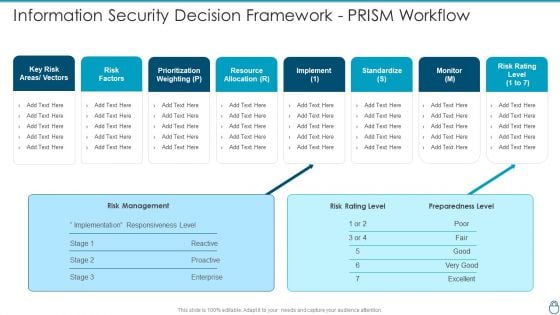
Cybersecurity Risk Administration Plan Information Security Decision Framework PRISM Workflow Topics PDF
Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Information Security Decision Framework PRISM Workflow Topics PDF Use them to share invaluable insights on Prioritization Weighting, Resource Allocation, Risk Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
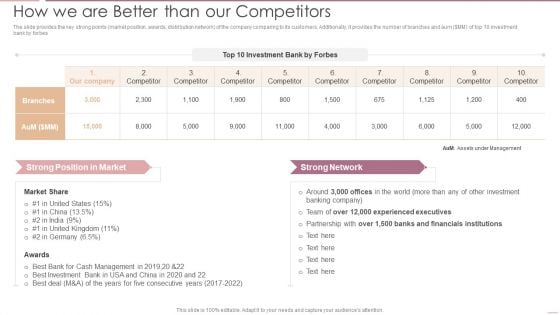
Investment Banking Security Underwriting Pitchbook How We Are Better Than Our Competitors Introduction PDF
Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook How We Are Better Than Our Competitors Introduction PDF bundle. Topics like Experienced Executives, Financials Institutions, Cash Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
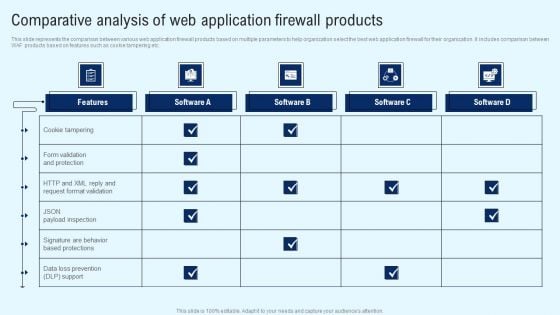
Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Boost your pitch with our creative Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Comprehensive Guide For Ensuring IT Infrastructure Security Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Comprehensive Guide For Ensuring IT Infrastructure Security Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

Enhancing Cloud Security With CASB Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Enhancing Cloud Security With CASB Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

IT Project Roadmap Of Product Delivery Ppt PowerPoint Presentation Summary Graphics Design PDF
Presenting this set of slides with name it project roadmap of product delivery ppt powerpoint presentation summary graphics design pdf. The topics discussed in these slides are delivery, security, inception, promotion stream, continuous improvement, low risk, medium risk, high risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
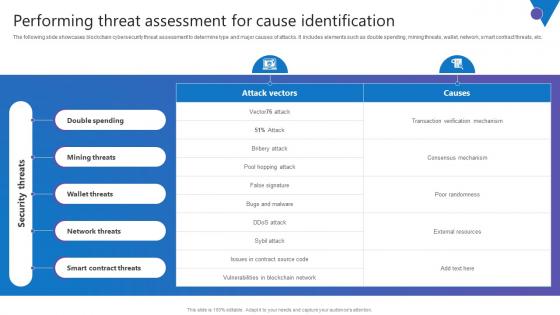
Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf
The following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf. The following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc.

Various Types Of Crypto Comprehensive Guide To Blockchain Digital Security Clipart Pdf
The following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. qDo you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Various Types Of Crypto Comprehensive Guide To Blockchain Digital Security Clipart Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Various Types Of Crypto Comprehensive Guide To Blockchain Digital Security Clipart Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc.
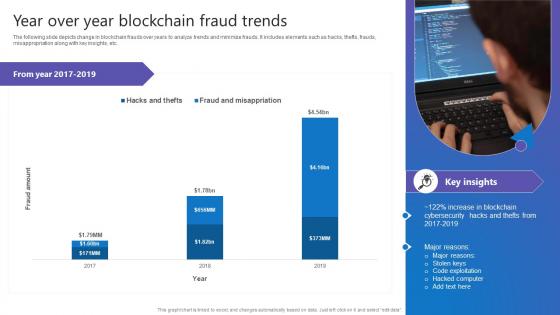
Year Over Year Blockchain Fraud Comprehensive Guide To Blockchain Digital Security Background Pdf
The following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Year Over Year Blockchain Fraud Comprehensive Guide To Blockchain Digital Security Background Pdf can be your best option for delivering a presentation. Represent everything in detail using Year Over Year Blockchain Fraud Comprehensive Guide To Blockchain Digital Security Background Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc.
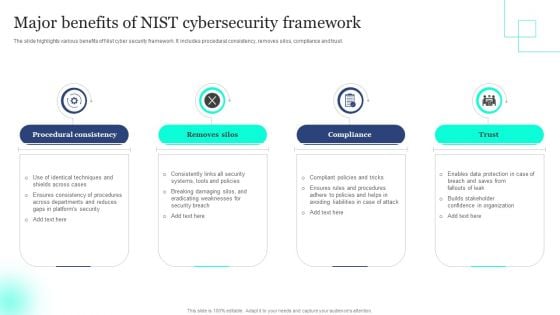
Major Benefits Of NIST Cybersecurity Framework Elements PDF
The slide highlights various benefits of Nist cyber security framework. It includes procedural consistency, removes silos, compliance and trust. Presenting Major Benefits Of NIST Cybersecurity Framework Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Procedural Consistency, Removes Silos, Compliance . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Financial Impact Of Information Security Attacks Cybersecurity Risk Assessment Template PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Slidegeeks has constructed Financial Impact Of Information Security Attacks Cybersecurity Risk Assessment Template PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
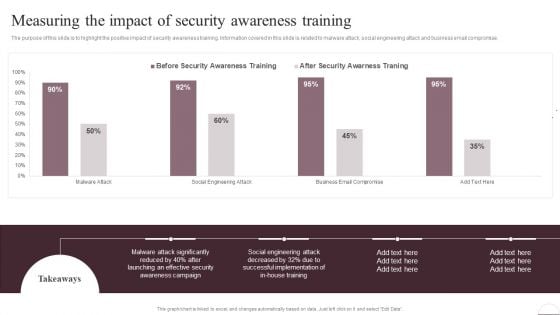
Prevention Of Information Measuring The Impact Of Security Awareness Training Ideas PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Prevention Of Information Measuring The Impact Of Security Awareness Training Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
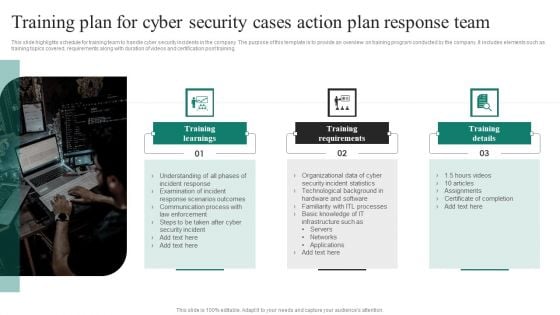
Training Plan For Cyber Security Cases Action Plan Response Team Ppt PowerPoint Presentation Gallery Format PDF
This slide highlights schedule for training team to handle cyber security incidents in the company. The purpose of this template is to provide an overview on training program conducted by the company. It includes elements such as training topics covered, requirements along with duration of videos and certification post training. Persuade your audience using this Training Plan For Cyber Security Cases Action Plan Response Team Ppt PowerPoint Presentation Gallery Format PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Training Learnings, Training Requirements, Training Details. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Security Monitoring Key Portrait PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. This is a continuous development evaluation plan eliminate cyber attacks current security monitoring key portrait pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware attacks, pnishing attacks, ransomware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
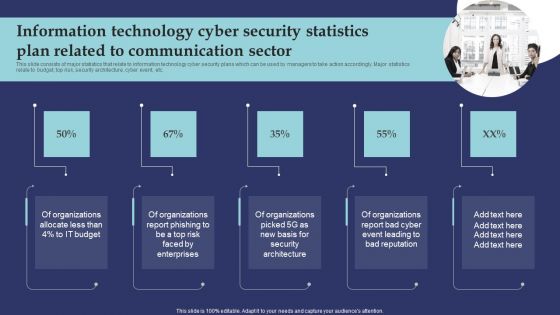
Information Technology Cyber Security Statistics Plan Related To Communication Sector Microsoft PDF
This slide consists of major statistics that relate to information technology cyber security plans which can be used by managers to take action accordingly. Major statistics relate to budget, top risk, security architecture, cyber event, etc. Presenting Information Technology Cyber Security Statistics Plan Related To Communication Sector Microsoft PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Organizations Allocate, Organizations Report Phishing, Organizations Report Bad Cyber. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
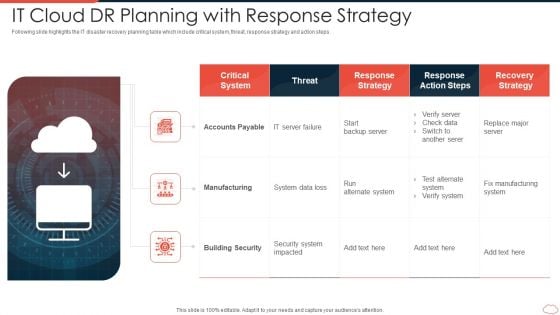
IT Cloud DR Planning With Response Strategy Template PDF
Following slide highlights the IT disaster recovery planning table which include critical system, threat, response strategy and action steps. Showcasing this set of slides titled it cloud dr planning with response strategy template pdf. The topics addressed in these templates are accounts payable, manufacturing, building security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Integrating AML And Transaction Key Members Of Financial Security Department Slides PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This Integrating AML And Transaction Key Members Of Financial Security Department Slides PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. TheIntegrating AML And Transaction Key Members Of Financial Security Department Slides PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

5 Key Practices To Prevent Cyber Phishing Scams And Attacks Graphics PDF
Mentioned slide showcases best practices which can be implemented to prevent cyber phishing. The practices are recognizing hyperlinks attached in an email, backup system copies, secure robust HTTPs connections, installing a firewall and using anti spam tools. Presenting 5 key practices to prevent cyber phishing scams and attacks graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including secure, device, reduced. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Ppt PowerPoint Presentation Complete Deck
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fourtytwo slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.
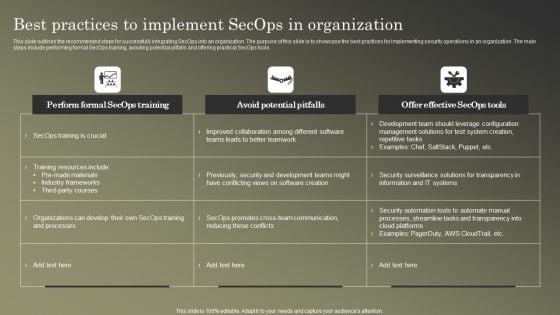
Cybersecurity Operations Cybersecops Best Practices To Implement Secops Information PDF
This slide outlines the recommended steps for successfully integrating SecOps into an organization. The purpose of this slide is to showcase the best practices for implementing security operations in an organization. The main steps include performing formal SecOps training, avoiding potential pitfalls and offering practical SecOps tools. Make sure to capture your audiences attention in your business displays with our gratis customizable Cybersecurity Operations Cybersecops Best Practices To Implement Secops Information PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Emergency Response Management Action Plan With Communication Channels Elements Pdf
This slide provide information about incident management action plan to communicate it to key stakeholder. It includes elements such as IT security manager, business manger, senior management, functional head and business unit Showcasing this set of slides titled Emergency Response Management Action Plan With Communication Channels Elements Pdf The topics addressed in these templates are Incident Management Action Plan, Business Manager All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide provide information about incident management action plan to communicate it to key stakeholder. It includes elements such as IT security manager, business manger, senior management, functional head and business unit

Padlock On Laptop Internet Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download our Technology PowerPoint Templates because It will Give impetus to the hopes of your colleagues. Our PowerPoint Templates and Slides will aid you in winning their trust. Download our Internet PowerPoint Templates because It can Bubble and burst with your ideas. Use our Computer PowerPoint Templates because You can Zap them with our PowerPoint Templates and Slides. See them reel under the impact. Download and present our Shapes PowerPoint Templates because you can Add colour to your speech with our PowerPoint Templates and Slides. Your presentation will leave your audience speechless. Download our Network diagrams PowerPoint Templates because You should Press the right buttons with our PowerPoint Templates and Slides. They will take your ideas down the perfect channel.Use these PowerPoint slides for presentations relating to protect your computer, security concept, network diagrams, technology, computer, internet, shapes. The prominent colors used in the PowerPoint template are Blue, Gray, Yellow. PowerPoint presentation experts tell us our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. PowerPoint presentation experts tell us our network PowerPoint templates and PPT Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. You can be sure our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. PowerPoint presentation experts tell us our computer PowerPoint templates and PPT Slides are designed by a team of presentation professionals. Presenters tell us our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. PowerPoint presentation experts tell us our security PowerPoint templates and PPT Slides are designed by a team of presentation professionals. Publicize your views with our Padlock On Laptop Internet Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Download without worries with our money back guaranteee.
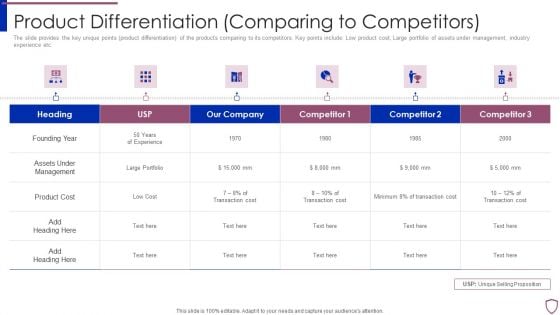
Financing Catalogue For Security Underwriting Agreement Product Differentiation Comparing Professional PDF
The slide provides the key unique points product differentiation of the products comparing to its competitors. Key points include Low product cost, Large portfolio of assets under management, industry experience etc. Deliver and pitch your topic in the best possible manner with this financing catalogue for security underwriting agreement product differentiation comparing professional pdf. Use them to share invaluable insights on founding year, assets under management, product cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
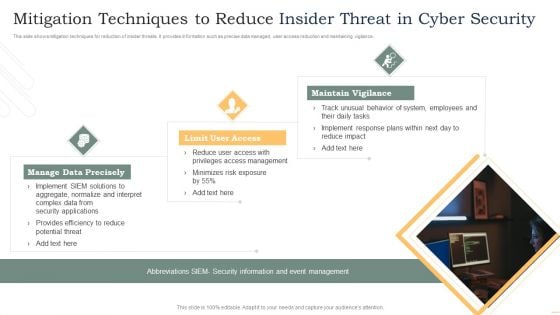
Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF
This slide covers cybersecurity awareness training to enhance effectiveness of employees. It involves document management, passwords and authentication and social engineering and phishing. Persuade your audience using this IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Document Management, Passwords And Authentication, Social, Engineering And Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Loss Prevention Checklist To Minimize Inventory Shrinkage Elements PDF
Following slide illustrates an effective checklist used for loss prevention in the retail sector. The checklist covers key points such as physical security, cash handling, product and staff. Showcasing this set of slides titled Loss Prevention Checklist To Minimize Inventory Shrinkage Elements PDF. The topics addressed in these templates are Physical Security, Product, Functioning Alarm System. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

The Digital Project Managers Deployment Of Cloud Project Management Model
This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc. If you are looking for a format to display your unique thoughts, then the professionally designed The Digital Project Managers Deployment Of Cloud Project Management Model is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download The Digital Project Managers Deployment Of Cloud Project Management Model and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc.
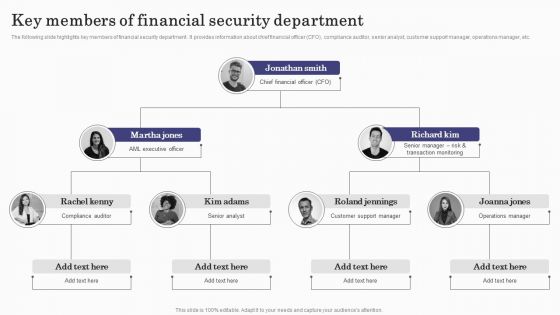
Deploying Banking Transaction Key Members Of Financial Security Department Guidelines PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This modern and well-arranged Deploying Banking Transaction Key Members Of Financial Security Department Guidelines PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
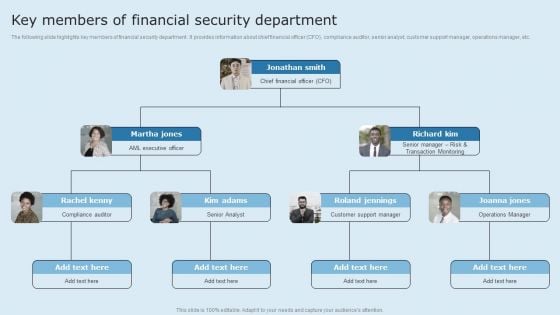
Actual Time Transaction Monitoring Software And Strategies Key Members Of Financial Security Department Diagrams PDF
The following slide highlights key members of financial security department. It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Actual Time Transaction Monitoring Software And Strategies Key Members Of Financial Security Department Diagrams PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
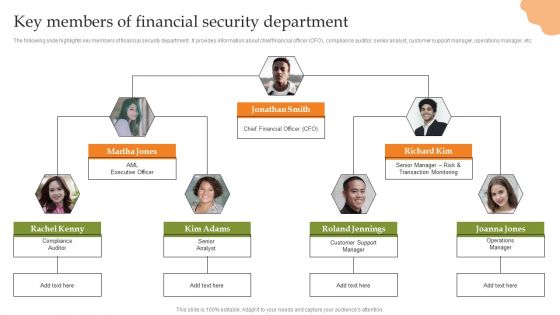
Creating Transaction Monitoring Key Members Of Financial Security Department Summary PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This modern and well-arranged Creating Transaction Monitoring Key Members Of Financial Security Department Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Deploying AML Transaction Monitoring Key Members Of Financial Security Department Ideas PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. Welcome to our selection of the Deploying AML Transaction Monitoring Key Members Of Financial Security Department Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
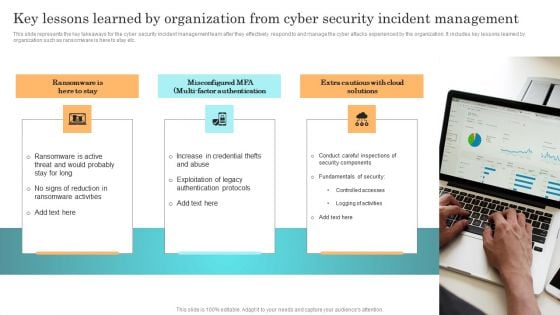
Incident Response Techniques Deployement Key Lessons Learned By Organization From Cyber Security Incident Formats PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Key Lessons Learned By Organization From Cyber Security Incident Formats PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
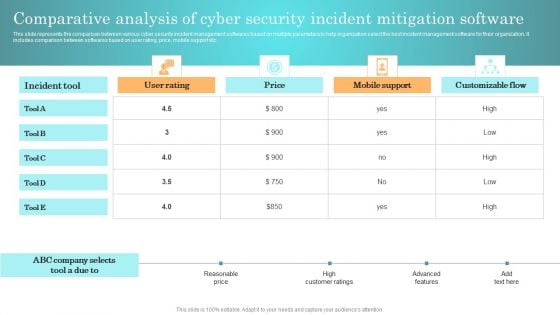
Incident Response Techniques Deployement Comparative Analysis Of Cyber Security Incident Mitigation Software Summary PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Incident Response Techniques Deployement Comparative Analysis Of Cyber Security Incident Mitigation Software Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
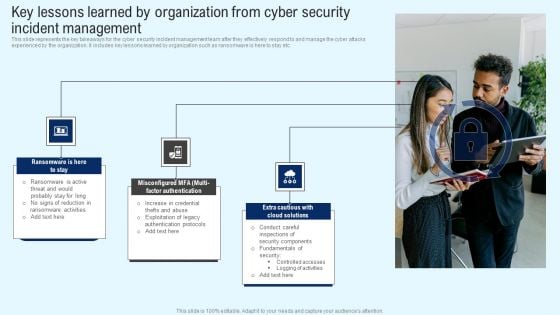
Implementing Cyber Security Incident Key Lessons Learned By Organization From Cyber Inspiration PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. Present like a pro with Implementing Cyber Security Incident Key Lessons Learned By Organization From Cyber Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
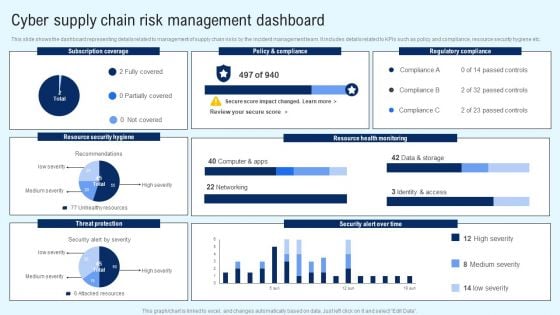
Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Slidegeeks is here to make your presentations a breeze with Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Template PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Sample PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
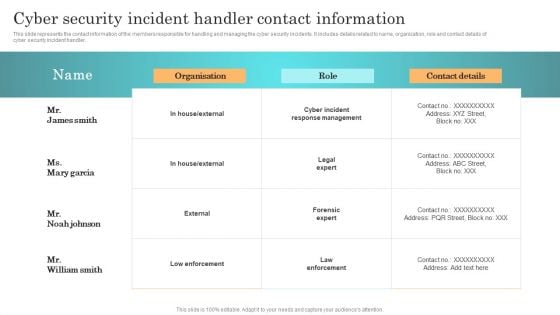
Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Get a simple yet stunning designed Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
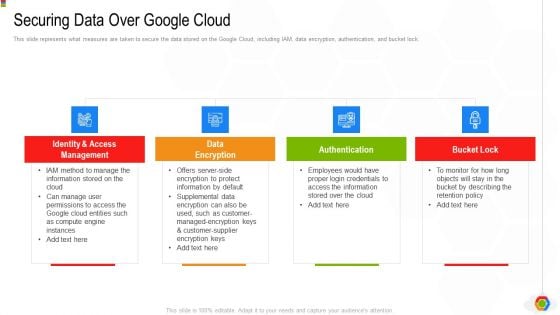
Google Cloud Console IT Securing Data Over Google Cloud Ppt Pictures Slides PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock. This is a google cloud console it securing data over google cloud ppt pictures slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identity and access management, data encryption, authentication, bucket lock. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
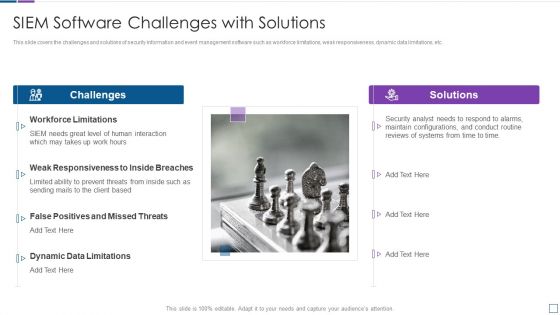
Real Time Assessment Of Security Threats SIEM Software Challenges With Solutions Inspiration PDF
This slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. This is a real time assessment of security threats siem software challenges with solutions inspiration pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like challenges, solutions, workforce limitations, false positives and missed threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Cyber Threats Digital Era Information Security Program Values To Business Ppt Slides Background Designs PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. This is a handling cyber threats digital era information security program values to business ppt slides background designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security program values to business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Artificial Intelligence For IT Operations Playbook Stage Five Security Breach Readiness Checklist Rules PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions.Presenting Artificial Intelligence For IT Operations Playbook Stage Five Security Breach Readiness Checklist Rules PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Management Training, Potential Mitigation, Already Developed In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Overcome The Security Awareness Training Program Challenges Clipart PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. Deliver and pitch your topic in the best possible manner with this How To Overcome The Security Awareness Training Program Challenges Clipart PDF. Use them to share invaluable insights on Burden On Administrators, Employee Participation, Lose Interest and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF
This slide shows user tracking sheet for insider threat with impact assessment. It provides details such as user behavior, indicator type, impact on security information and event manage SIEM, impact on interference framework, etc. Showcasing this set of slides titled Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF. The topics addressed in these templates are Indicator Type, Impact On SIEM, Interference Framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
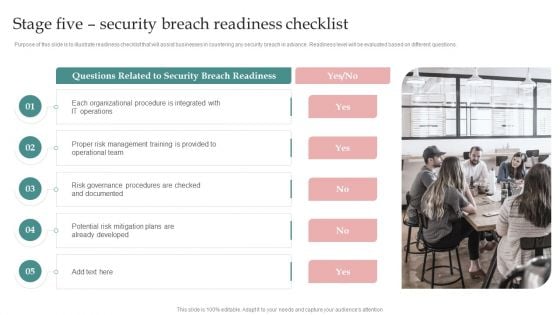
AI Playbook For Business Stage Five Security Breach Readiness Checklist Microsoft PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. This is a AI Playbook For Business Stage Five Security Breach Readiness Checklist Microsoft PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Operations, Organizations Transforming, Related To Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
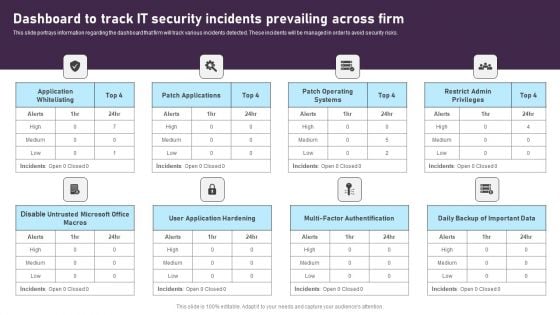
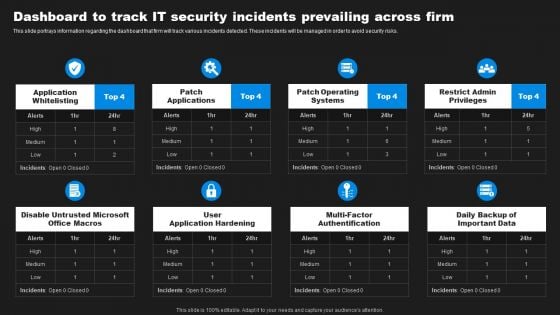
Dashboard To Track IT Security Incidents Prevailing Across Firm Inspiration PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Dashboard To Track IT Security Incidents Prevailing Across Firm Inspiration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF

Security Software Company Investor Funding Pitch Deck Client Testimonials Diagrams PDF
The following slide showcases perceptive of expert analysts about IT company i.e. Awake Society. It showcase reviews of IT manager, chief information security officer and IT director. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security Software Company Investor Funding Pitch Deck Client Testimonials Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Enhancing Information Technology With Strategic Dashboard To Track IT Security Summary PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Enhancing Information Technology With Strategic Dashboard To Track IT Security Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Security Operations Center Strategic Tactical Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this security operations center strategic tactical ppt powerpoint presentation complete deck with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.


 Continue with Email
Continue with Email

 Home
Home


































