Purpose Slides

Real Life Example Of AIOT London City Airport AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase real-life example of Artificial Intelligence of Things AIoT. The slide provides information about how London city airport improves its operational efficiency by enhancing security, passenger experience, and baggage handling. Present like a pro with Real Life Example Of AIOT London City Airport AIOT Applications For Various Industries IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The purpose of this slide is to showcase real-life example of Artificial Intelligence of Things AIoT. The slide provides information about how London city airport improves its operational efficiency by enhancing security, passenger experience, and baggage handling.

Zero Trust Model Case Study Intellectual Property Protection
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Model Case Study Intellectual Property Protection will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.

Zero Trust Model Challenges Of VPN Based Remote Access Solutions
This slide outlines the limitations of virtual private network-based remote access services. The purpose of this slide is to showcase the various challenges of the VPN network system and how the zero trust network model can overcome those issues. Present like a pro with Zero Trust Model Challenges Of VPN Based Remote Access Solutions. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the limitations of virtual private network-based remote access services. The purpose of this slide is to showcase the various challenges of the VPN network system and how the zero trust network model can overcome those issues.

Zero Trust Model Endpoint Initiated Zero Trust Network Topology Model
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Model Endpoint Initiated Zero Trust Network Topology Model. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.

Zero Trust Model Microsegmentation Overview And Working
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Are you searching for a Zero Trust Model Microsegmentation Overview And Working that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Model Microsegmentation Overview And Working from Slidegeeks today. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.

Zero Trust Model Step 4 And 5 Available Technology Review And Zero Trust
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Model Step 4 And 5 Available Technology Review And Zero Trust will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.
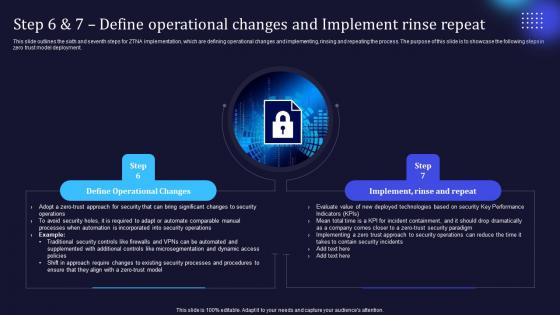
Zero Trust Model Step 6 And 7 Define Operational Changes And Implement
This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Present like a pro with Zero Trust Model Step 6 And 7 Define Operational Changes And Implement. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment.

Zero Trust Model Types Of Zero Trust Network Access ZTNA Models
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Model Types Of Zero Trust Network Access ZTNA Models. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.

Fibers IT Imaging Technology Overview And Use Cases
This slide describes the overview of imaging technology used in photonics. The purpose of this slide is to highlight the main use cases of the technology in biological and medical imaging, material characterizations, manufacturing and quality control, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Fibers IT Imaging Technology Overview And Use Cases. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide describes the overview of imaging technology used in photonics. The purpose of this slide is to highlight the main use cases of the technology in biological and medical imaging, material characterizations, manufacturing and quality control, and so on.
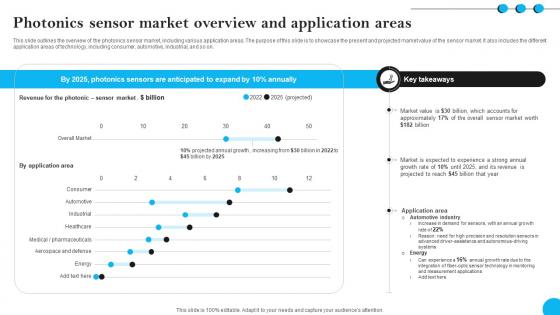
Fibers IT Photonics Sensor Market Overview And Application Areas
This slide outlines the overview of the photonics sensor market, including various application areas. The purpose of this slide is to showcase the present and projected market value of the sensor market. It also includes the different application areas of technology, including consumer, automotive, industrial, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Fibers IT Photonics Sensor Market Overview And Application Areas will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines the overview of the photonics sensor market, including various application areas. The purpose of this slide is to showcase the present and projected market value of the sensor market. It also includes the different application areas of technology, including consumer, automotive, industrial, and so on.
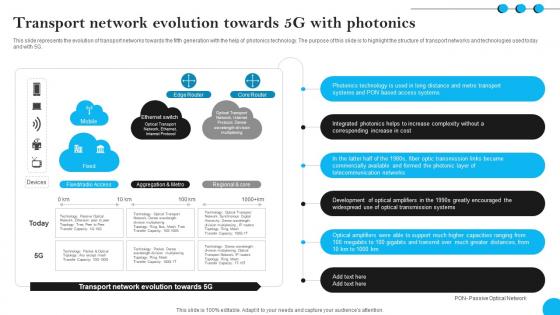
Fibers IT Transport Network Evolution Towards 5g With Photonics
This slide represents the evolution of transport networks towards the fifth generation with the help of photonics technology. The purpose of this slide is to highlight the structure of transport networks and technologies used today and with 5G. Make sure to capture your audiences attention in your business displays with our gratis customizable Fibers IT Transport Network Evolution Towards 5g With Photonics. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the evolution of transport networks towards the fifth generation with the help of photonics technology. The purpose of this slide is to highlight the structure of transport networks and technologies used today and with 5G.

Key Considerations Assumptions Of The Shipping Industry Report Maritime Shipping Industry IR SS V
The slide presents the key assumptions and limitations considered while building the shipping industry report. The purpose of this slide is to provide the foundation for analysis and projections in addition to acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Considerations Assumptions Of The Shipping Industry Report Maritime Shipping Industry IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The slide presents the key assumptions and limitations considered while building the shipping industry report. The purpose of this slide is to provide the foundation for analysis and projections in addition to acknowledging uncertainties and potential risks in the future.

Green Computing Disposal Process In Green Cloud Computing
This slide gives an overview of the disposal procedure of green computing. The purpose of this slide is to showcase the benefits of recycling computers, points to consider before recycling, recyclable components, dangerous recycling techniques, and state-of-art recycling methods. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Green Computing Disposal Process In Green Cloud Computing will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide gives an overview of the disposal procedure of green computing. The purpose of this slide is to showcase the benefits of recycling computers, points to consider before recycling, recyclable components, dangerous recycling techniques, and state-of-art recycling methods.
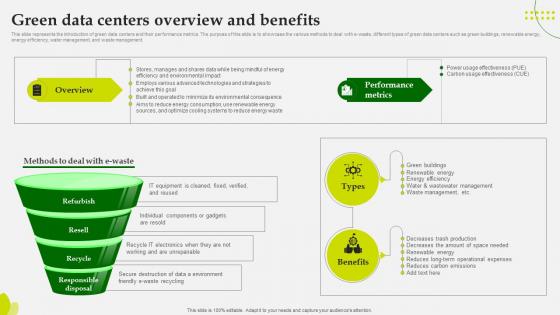
Green Computing Green Data Centers Overview And Benefits
This slide represents the introduction of green data centers and their performance metrics. The purpose of this slide is to showcase the various methods to deal with e-waste, different types of green data centers such as green buildings, renewable energy, energy efficiency, water management, and waste management. Make sure to capture your audiences attention in your business displays with our gratis customizable Green Computing Green Data Centers Overview And Benefits These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the introduction of green data centers and their performance metrics. The purpose of this slide is to showcase the various methods to deal with e-waste, different types of green data centers such as green buildings, renewable energy, energy efficiency, water management, and waste management.
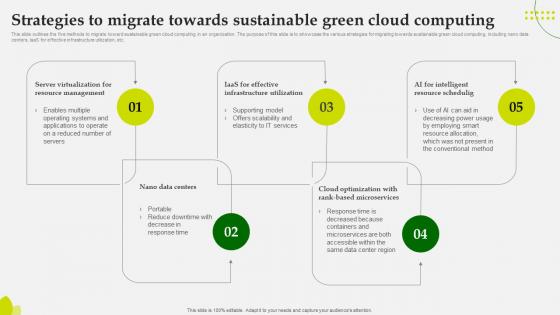
Green Computing Strategies To Migrate Towards Sustainable Green Cloud Computing
This slide outlines the five methods to migrate toward sustainable green cloud computing in an organization. The purpose of this slide is to showcase the various strategies for migrating towards sustainable green cloud computing, including nano data centers, IaaS for effective infrastructure utilization, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Green Computing Strategies To Migrate Towards Sustainable Green Cloud Computing will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines the five methods to migrate toward sustainable green cloud computing in an organization. The purpose of this slide is to showcase the various strategies for migrating towards sustainable green cloud computing, including nano data centers, IaaS for effective infrastructure utilization, etc.
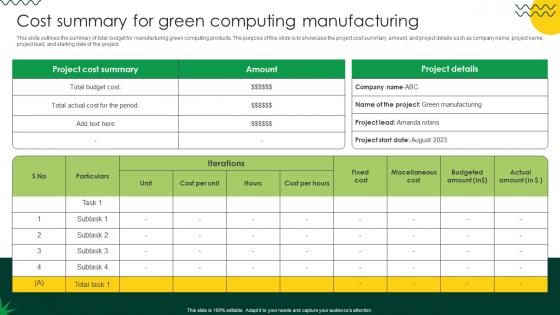
Sustainable Cost Summary For Green Computing Manufacturing
This slide outlines the summary of total budget for manufacturing green computing products. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. Make sure to capture your audiences attention in your business displays with our gratis customizable Sustainable Cost Summary For Green Computing Manufacturing. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the summary of total budget for manufacturing green computing products. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project.

Sustainable Nano Data Center Overview And Advantages
This slide describes the role of nano data centers in green cloud computing, including their benefits. The purpose of this slide is to showcase the various advantages of nano data centers, including energy efficiency, reduced costs, scalability, improved performance, flexibility, and resilience. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Sustainable Nano Data Center Overview And Advantages will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the role of nano data centers in green cloud computing, including their benefits. The purpose of this slide is to showcase the various advantages of nano data centers, including energy efficiency, reduced costs, scalability, improved performance, flexibility, and resilience.

Sustainable Steps To Offset Greenhouse Gas Emissions
This slide represents the steps to offset greenhouse gas emissions. The purpose of this slide is to showcase the different measures to take while offsetting greenhouse gas emissions and the actions include measuring emissions, reducing emissions, offsetting the rest, and receiving a credit. Make sure to capture your audiences attention in your business displays with our gratis customizable Sustainable Steps To Offset Greenhouse Gas Emissions. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the steps to offset greenhouse gas emissions. The purpose of this slide is to showcase the different measures to take while offsetting greenhouse gas emissions and the actions include measuring emissions, reducing emissions, offsetting the rest, and receiving a credit.

Comparative Assessment Of Ztna Version 1 0 And 2 0 Software Defined Perimeter SDP
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparative Assessment Of Ztna Version 1 0 And 2 0 Software Defined Perimeter SDP will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.

Future And Emerging Trends In Ztna Model Software Defined Perimeter SDP
This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Future And Emerging Trends In Ztna Model Software Defined Perimeter SDP. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on.
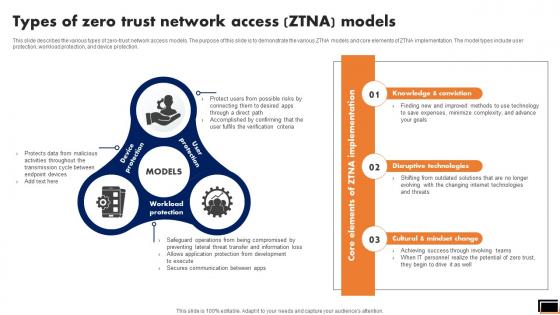
Types Of Zero Trust Network Access Ztna Models Software Defined Perimeter SDP
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Make sure to capture your audiences attention in your business displays with our gratis customizable Types Of Zero Trust Network Access Ztna Models Software Defined Perimeter SDP. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.
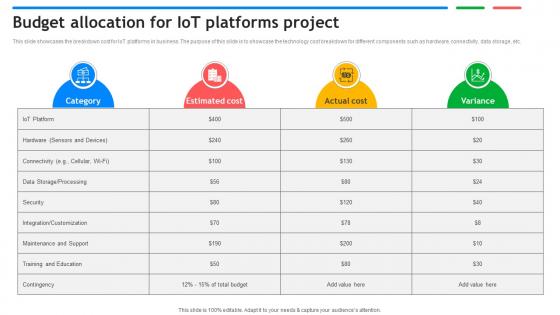
Budget Allocation For IoT Platforms Project Exploring Google Cloud IoT Platform
This slide showcases the breakdown cost for IoT platforms in business. The purpose of this slide is to showcase the technology cost breakdown for different components such as hardware, connectivity, data storage, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Budget Allocation For IoT Platforms Project Exploring Google Cloud IoT Platform will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases the breakdown cost for IoT platforms in business. The purpose of this slide is to showcase the technology cost breakdown for different components such as hardware, connectivity, data storage, etc.
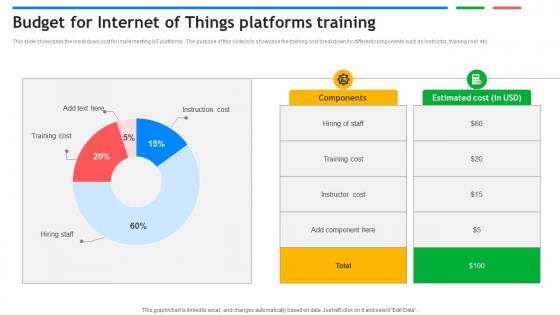
Budget For Internet Of Things Platforms Training Exploring Google Cloud IoT Platform
This slide showcases the breakdown cost for implementing IoT platforms . The purpose of this slide is to showcase the training cost breakdown for different components such as instructor, training cost, etc. Present like a pro with Budget For Internet Of Things Platforms Training Exploring Google Cloud IoT Platform Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases the breakdown cost for implementing IoT platforms . The purpose of this slide is to showcase the training cost breakdown for different components such as instructor, training cost, etc.
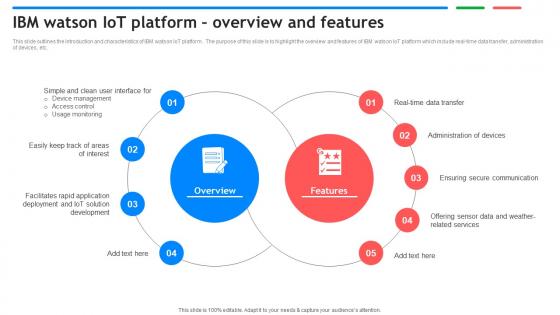
IBM Watson IoT Platform Overview And Features Exploring Google Cloud IoT Platform
This slide outlines the introduction and characteristics of IBM watson IoT platform . The purpose of this slide is to highlight the overview and features of IBM watson IoT platform which include real time data transfer, administration of devices, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable IBM Watson IoT Platform Overview And Features Exploring Google Cloud IoT Platform These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the introduction and characteristics of IBM watson IoT platform . The purpose of this slide is to highlight the overview and features of IBM watson IoT platform which include real time data transfer, administration of devices, etc.
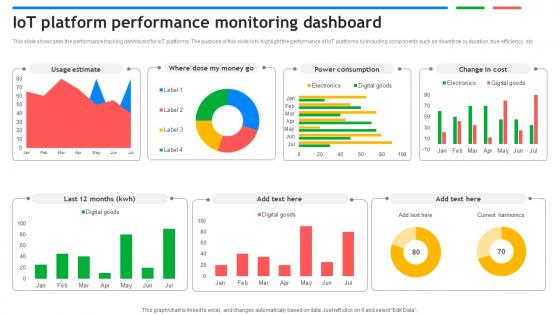
IoT Platform Performance Monitoring Dashboard Exploring Google Cloud IoT Platform
This slide showcases the performance tracking dashboard for IoT platforms. The purpose of this slide is to highlight the performance of IoT platforms by including components such as downtime by duration, true efficiency, etc. Are you searching for a IoT Platform Performance Monitoring Dashboard Exploring Google Cloud IoT Platform that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IoT Platform Performance Monitoring Dashboard Exploring Google Cloud IoT Platform from Slidegeeks today. This slide showcases the performance tracking dashboard for IoT platforms. The purpose of this slide is to highlight the performance of IoT platforms by including components such as downtime by duration, true efficiency, etc.

Steps To Select Optimal IoT Platform Exploring Google Cloud IoT Platform
This slide discusses selecting best IoT platform for an organization that is most suitable. The purpose of this slide is to highlight the factors to be considered for optimal selection of IoT platform which include development stage consideration and industry understanding. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Steps To Select Optimal IoT Platform Exploring Google Cloud IoT Platform will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide discusses selecting best IoT platform for an organization that is most suitable. The purpose of this slide is to highlight the factors to be considered for optimal selection of IoT platform which include development stage consideration and industry understanding.
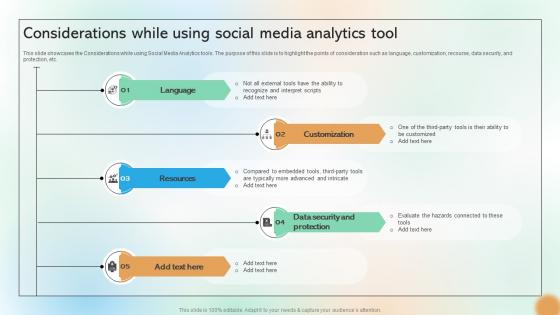
Considerations While Using Social Media Analytics Tool Cracking The Code Of Social Media
This slide showcases the Considerations while using Social Media Analytics tools. The purpose of this slide is to highlight the points of consideration such as language, customization, recourse, data security, and protection, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Considerations While Using Social Media Analytics Tool Cracking The Code Of Social Media will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases the Considerations while using Social Media Analytics tools. The purpose of this slide is to highlight the points of consideration such as language, customization, recourse, data security, and protection, etc.

Introduction And Platforms Of Social Media Analysis Cracking The Code Of Social Media
This slide discusses the overview of Social Media Analytics and platforms of social media. The purpose of this slide is to highlight those platforms such as facebook, twitter, instagram, tumblr, linkedin, Naukri, buffer, youtube etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Introduction And Platforms Of Social Media Analysis Cracking The Code Of Social Media will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide discusses the overview of Social Media Analytics and platforms of social media. The purpose of this slide is to highlight those platforms such as facebook, twitter, instagram, tumblr, linkedin, Naukri, buffer, youtube etc.
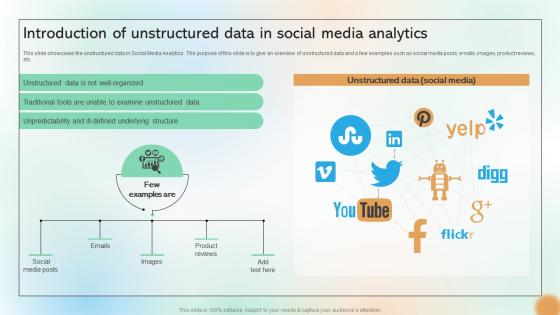
Introduction Of Unstructured Data In Social Media Analytics Cracking The Code Of Social Media
This slide showcases the unstructured data in Social Media Analytics. The purpose of this slide is to give an overview of unstructured data and a few examples such as social media posts, emails, images, product reviews, etc. Present like a pro with Introduction Of Unstructured Data In Social Media Analytics Cracking The Code Of Social Media. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with This slide showcases the unstructured data in Social Media Analytics. The purpose of this slide is to give an overview of unstructured data and a few examples such as social media posts, emails, images, product reviews, etc.

Predictive And Prescriptive Analytics In Social Media Cracking The Code Of Social Media
This slide showcases the types of Social Media Analytics on businesses. The purpose of this slide is to briefly explain two types of Social Media Analytics which are predictive and prescriptive analytics which are proactive in nature. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Predictive And Prescriptive Analytics In Social Media Cracking The Code Of Social Media will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases the types of Social Media Analytics on businesses. The purpose of this slide is to briefly explain two types of Social Media Analytics which are predictive and prescriptive analytics which are proactive in nature.
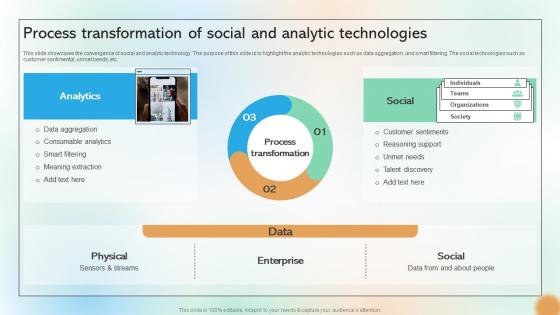
Process Transformation Of Social And Analytic Technologies Cracking The Code Of Social Media
This slide showcases the convergence of social and analytic technology. The purpose of this slide is to highlight the analytic technologies such as data aggregation, and smart filtering. The social technologies such as customer sentimental, unmet needs, etc. Present like a pro with Process Transformation Of Social And Analytic Technologies Cracking The Code Of Social Media. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with This slide showcases the convergence of social and analytic technology. The purpose of this slide is to highlight the analytic technologies such as data aggregation, and smart filtering. The social technologies such as customer sentimental, unmet needs, etc.

Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost.

Importance Of Secure Web Gateway For Businesses Web Threat Protection System
This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Importance Of Secure Web Gateway For Businesses Web Threat Protection System. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc.

Steps To Integrate Secure Web Gateway Into Organization Web Threat Protection System
This slide demonstrates the steps for successful implementation of SWG into firms. The purpose of this slide is to outline the procedure of Secure Web integration. The steps included are determine use case, select best solution, plan deployment, etc. Present like a pro with Steps To Integrate Secure Web Gateway Into Organization Web Threat Protection System. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide demonstrates the steps for successful implementation of SWG into firms. The purpose of this slide is to outline the procedure of Secure Web integration. The steps included are determine use case, select best solution, plan deployment, etc.
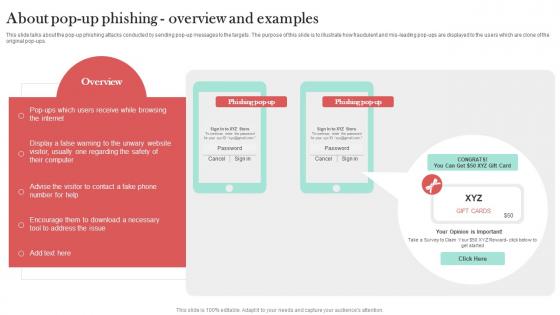
About Pop Up Phishing Overview And Examples Man In The Middle Phishing IT
This slide talks about the pop-up phishing attacks conducted by sending pop-up messages to the targets. The purpose of this slide is to illustrate how fraudulent and mis-leading pop-ups are displayed to the users which are clone of the original pop-ups. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. About Pop Up Phishing Overview And Examples Man In The Middle Phishing IT will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the pop-up phishing attacks conducted by sending pop-up messages to the targets. The purpose of this slide is to illustrate how fraudulent and mis-leading pop-ups are displayed to the users which are clone of the original pop-ups.
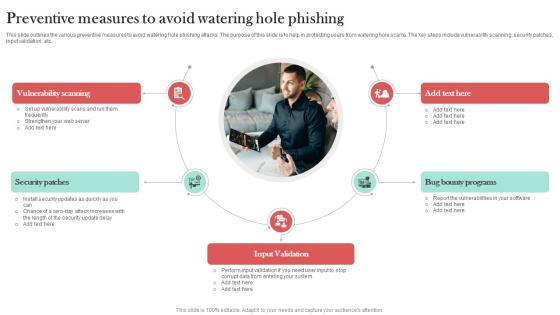
Preventive Measures To Avoid Watering Man In The Middle Phishing IT
This slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc. Present like a pro with Preventive Measures To Avoid Watering Man In The Middle Phishing IT. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc.
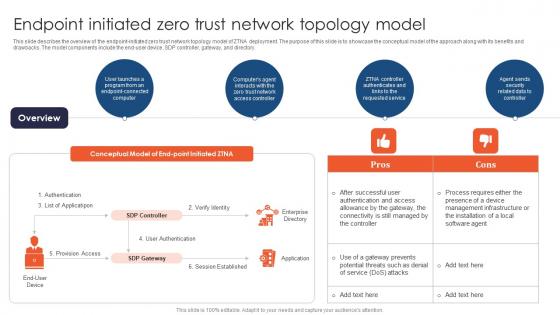
Endpoint Initiated Zero Trust Network Topology Model Zero Trust Network Access
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Endpoint Initiated Zero Trust Network Topology Model Zero Trust Network Access will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.
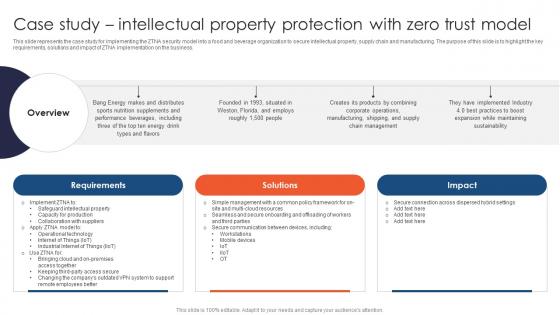
Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.

Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.
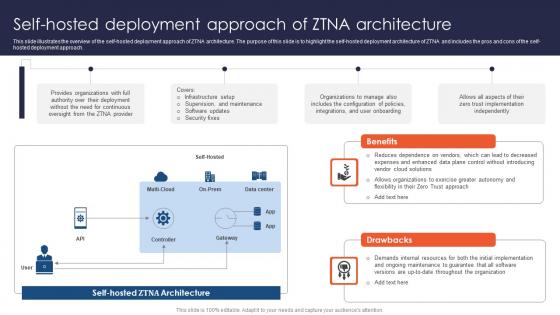
Zero Trust Network Access Self Hosted Deployment Approach Of ZTNA Architecture
This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach. Present like a pro with Zero Trust Network Access Self Hosted Deployment Approach Of ZTNA Architecture. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach.

Zero Trust Network Access Technologies Used In Zero Trust Network Access
This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Network Access Technologies Used In Zero Trust Network Access. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer.

CASB 2 0 IT CASB Application In Accounting And Finance Sector
This slide outlines the application of the CASB model in the accounting and banking sectors. The purpose of this slide is to give an overview and represent the challenges that occur due to cloud data exchange and how CASB can overcome those challenges. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. CASB 2 0 IT CASB Application In Accounting And Finance Sector will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines the application of the CASB model in the accounting and banking sectors. The purpose of this slide is to give an overview and represent the challenges that occur due to cloud data exchange and how CASB can overcome those challenges.
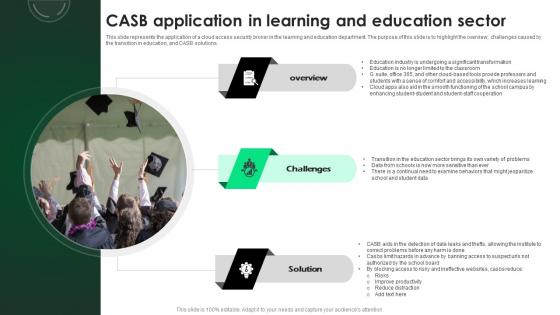
CASB 2 0 IT CASB Application In Learning And Education Sector
This slide represents the application of a cloud access security broker in the learning and education department. The purpose of this slide is to highlight the overview, challenges caused by the transition in education, and CASB solutions. Present like a pro with CASB 2 0 IT CASB Application In Learning And Education Sector. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the application of a cloud access security broker in the learning and education department. The purpose of this slide is to highlight the overview, challenges caused by the transition in education, and CASB solutions.
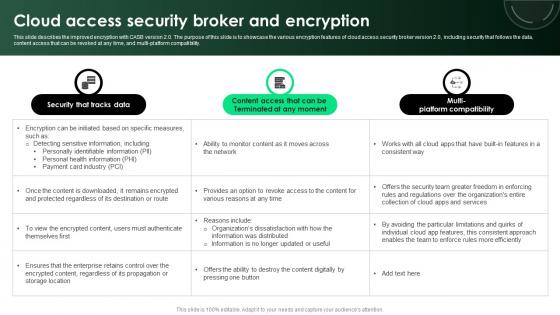
CASB 2 0 IT Cloud Access Security Broker And Encryption
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Make sure to capture your audiences attention in your business displays with our gratis customizable CASB 2 0 IT Cloud Access Security Broker And Encryption. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility.
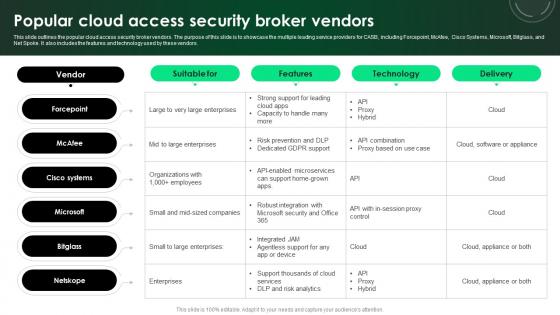
CASB 2 0 IT Popular Cloud Access Security Broker Vendors
This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. CASB 2 0 IT Popular Cloud Access Security Broker Vendors will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors.

CASB 2 0 IT Primary Types Of Reverse Proxy Server Deployment
This slide outlines the main types of reverse proxy server deployment, covering regular reverse proxies and load balancers. The purpose of this slide is to showcase how both methods work to manage traffic and offer security features to organizations. Present like a pro with CASB 2 0 IT Primary Types Of Reverse Proxy Server Deployment. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the main types of reverse proxy server deployment, covering regular reverse proxies and load balancers. The purpose of this slide is to showcase how both methods work to manage traffic and offer security features to organizations.

Create A Restaurant Marketing Email Marketing Plan For Restaurant
This slide shows various email promotional strategies for the food industry. The purpose of this slide is to implement these strategies in the best possible way. The strategies are to create eye-catching designs, provide exclusive offers, share customer testimonials, etc. Present like a pro with Create A Restaurant Marketing Email Marketing Plan For Restaurant. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide shows various email promotional strategies for the food industry. The purpose of this slide is to implement these strategies in the best possible way. The strategies are to create eye-catching designs, provide exclusive offers, share customer testimonials, etc.

Create A Restaurant Marketing Overview Print Advertisement For Restaurant
This slide shows various print ads and promotional strategies for the food industry. The purpose of this slide is to aware the target audience using various methods. It includes such as billboards, pamphlets, etc. Are you searching for a Create A Restaurant Marketing Overview Print Advertisement For Restaurant that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Create A Restaurant Marketing Overview Print Advertisement For Restaurant from Slidegeeks today. This slide shows various print ads and promotional strategies for the food industry. The purpose of this slide is to aware the target audience using various methods. It includes such as billboards, pamphlets, etc.
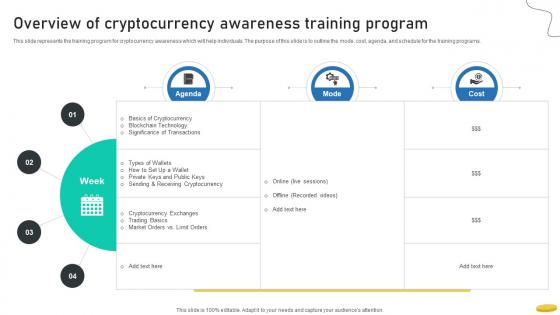
Overview Of Cryptocurrency Awareness Training Program Cryptocurrency Management With Blockchain
This slide represents the training program for cryptocurrency awareness which will help individuals. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Overview Of Cryptocurrency Awareness Training Program Cryptocurrency Management With Blockchain will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the training program for cryptocurrency awareness which will help individuals. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.
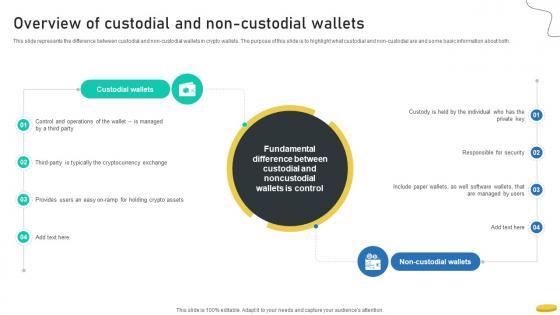
Overview Of Custodial And Non Custodial Wallets Cryptocurrency Management With Blockchain
This slide represents the difference between custodial and non-custodial wallets in crypto wallets. The purpose of this slide is to highlight what custodial and non-custodial are and some basic information about both.Present like a pro with Overview Of Custodial And Non Custodial Wallets Cryptocurrency Management With Blockchain. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the difference between custodial and non-custodial wallets in crypto wallets. The purpose of this slide is to highlight what custodial and non-custodial are and some basic information about both.
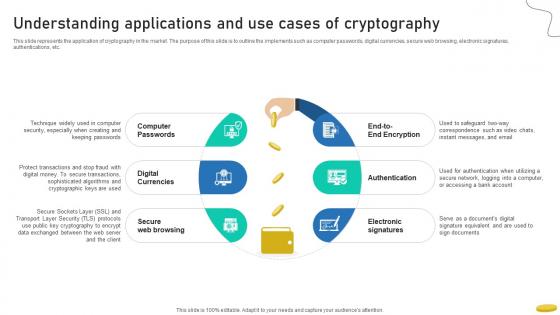
Understanding Applications And Use Cases Of Cryptography Cryptocurrency Management With Blockchain
This slide represents the application of cryptography in the market. The purpose of this slide is to outline the implements such as computer passwords, digital currencies, secure web browsing, electronic signatures, authentications, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Understanding Applications And Use Cases Of Cryptography Cryptocurrency Management With Blockchain. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the application of cryptography in the market. The purpose of this slide is to outline the implements such as computer passwords, digital currencies, secure web browsing, electronic signatures, authentications, etc.

Checklist To Implement Data Integration Process Data Integration Strategies For Business
This slide represents the checklist to implement a data integration plan in an organization. The purpose of this slide is to provide key functional requirements for implementing and deploying data integration in an enterprise environment. Present like a pro with Checklist To Implement Data Integration Process Data Integration Strategies For Business. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the checklist to implement a data integration plan in an organization. The purpose of this slide is to provide key functional requirements for implementing and deploying data integration in an enterprise environment.

Data Integration Training Schedule For Staff Data Integration Strategies For Business
This slide represents the data integration training schedule for staff. The purpose of this slide is to manage and monitor data integration training procedures. It includes the time slots for training, the total days of training, and the modules to be covered in the training. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Integration Training Schedule For Staff Data Integration Strategies For Business. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the data integration training schedule for staff. The purpose of this slide is to manage and monitor data integration training procedures. It includes the time slots for training, the total days of training, and the modules to be covered in the training.
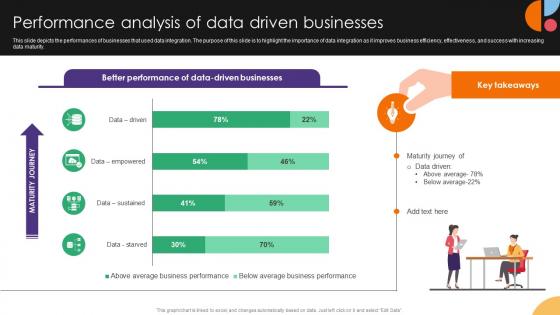
Performance Analysis Of Data Driven Businesses Data Integration Strategies For Business
This slide depicts the performances of businesses that used data integration. The purpose of this slide is to highlight the importance of data integration as it improves business efficiency, effectiveness, and success with increasing data maturity. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Performance Analysis Of Data Driven Businesses Data Integration Strategies For Business will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide depicts the performances of businesses that used data integration. The purpose of this slide is to highlight the importance of data integration as it improves business efficiency, effectiveness, and success with increasing data maturity.

Types Of Data Integration Data Virtualization Data Integration Strategies For Business
This slide discusses data virtualization, a type of data integration. The purpose of this slide is to explain the functioning of data virtualization, which involves unifying data from multiple sources, creating a logical view of required data, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Types Of Data Integration Data Virtualization Data Integration Strategies For Business. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide discusses data virtualization, a type of data integration. The purpose of this slide is to explain the functioning of data virtualization, which involves unifying data from multiple sources, creating a logical view of required data, etc.
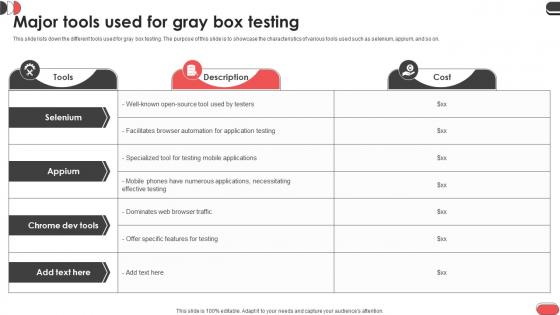
Major Tools Used For Gray Box Testing Gray Box Testing Best Practices
This slide lists down the different tools used for gray box testing. The purpose of this slide is to showcase the characteristics of various tools used such as selenium, appium, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Major Tools Used For Gray Box Testing Gray Box Testing Best Practices. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide lists down the different tools used for gray box testing. The purpose of this slide is to showcase the characteristics of various tools used such as selenium, appium, and so on.
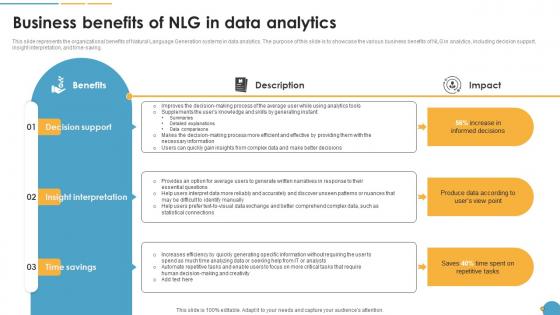
Business Benefits Of NLG In Data Analytics Natural Language Automation
This slide represents the organizational benefits of Natural Language Generation systems in data analytics. The purpose of this slide is to showcase the various business benefits of NLG in analytics, including decision support, insight interpretation, and time-saving. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Business Benefits Of NLG In Data Analytics Natural Language Automation will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the organizational benefits of Natural Language Generation systems in data analytics. The purpose of this slide is to showcase the various business benefits of NLG in analytics, including decision support, insight interpretation, and time-saving.

Evaluation Of Natural Language Generation Models Natural Language Automation
This slide illustrates how Natural Language Generation models are assessed. The purpose of this slide is to showcase the various methods and parameters to evaluate NLG models, including black box evaluation, glass box evaluation, accuracy, fluency, word-based metrics, grammar-based metrics, and semantic similarity metrics. Make sure to capture your audiences attention in your business displays with our gratis customizable Evaluation Of Natural Language Generation Models Natural Language Automation. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide illustrates how Natural Language Generation models are assessed. The purpose of this slide is to showcase the various methods and parameters to evaluate NLG models, including black box evaluation, glass box evaluation, accuracy, fluency, word-based metrics, grammar-based metrics, and semantic similarity metrics.
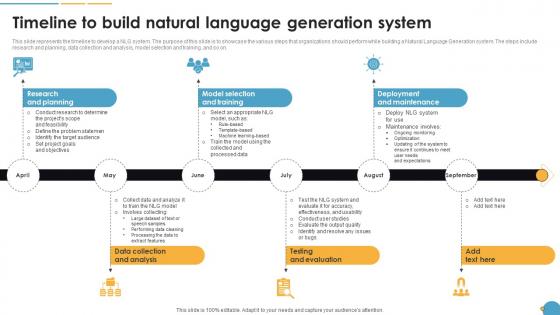
Timeline To Build Natural Language Generation System Natural Language Automation
This slide represents the timeline to develop a NLG system. The purpose of this slide is to showcase the various steps that organizations should perform while building a Natural Language Generation system. The steps include research and planning, data collection and analysis, model selection and training, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Timeline To Build Natural Language Generation System Natural Language Automation. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the timeline to develop a NLG system. The purpose of this slide is to showcase the various steps that organizations should perform while building a Natural Language Generation system. The steps include research and planning, data collection and analysis, model selection and training, and so on.
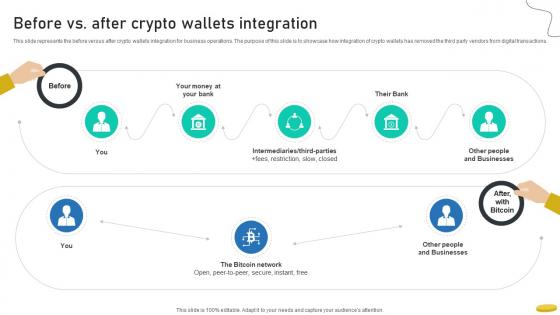
Before Vs After Crypto Wallets Integration Cryptocurrency Management With Blockchain
This slide represents the before versus after crypto wallets integration for business operations. The purpose of this slide is to showcase how integration of crypto wallets has removed the third party vendors from digital transactions.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Before Vs After Crypto Wallets Integration Cryptocurrency Management With Blockchain will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the before versus after crypto wallets integration for business operations. The purpose of this slide is to showcase how integration of crypto wallets has removed the third party vendors from digital transactions.


 Continue with Email
Continue with Email

 Home
Home


































