Purpose Slides
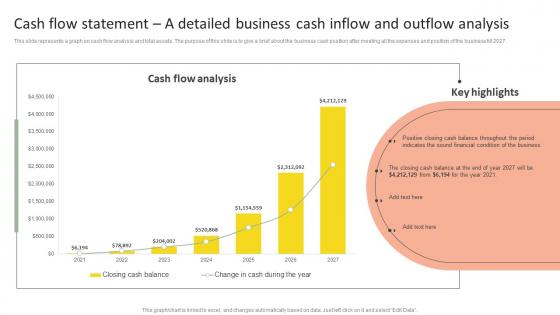
Cash Flow Statement A Detailed Insurance Agency Startup Business Plan Go To Market Strategy Rules Pdf
This slide represents a graph on cash flow analysis and total assets. The purpose of this slide is to give a brief about the business cash position after meeting all the expenses and position of the business till 2027. Boost your pitch with our creative Cash Flow Statement A Detailed Insurance Agency Startup Business Plan Go To Market Strategy Rules Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents a graph on cash flow analysis and total assets. The purpose of this slide is to give a brief about the business cash position after meeting all the expenses and position of the business till 2027.

Benefits Of Sidechain Blockchain Different Architectures Of Blockchain Infographics Pdf
This slide represents the advantages of the sidechain blockchain network. The purpose of this slide is to showcase the different benefits of sidechain blockchain technology, including scalability, experimentation or upgradeability, and diversification. Take your projects to the next level with our ultimate collection of Benefits Of Sidechain Blockchain Different Architectures Of Blockchain Infographics Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents the advantages of the sidechain blockchain network. The purpose of this slide is to showcase the different benefits of sidechain blockchain technology, including scalability, experimentation or upgradeability, and diversification.
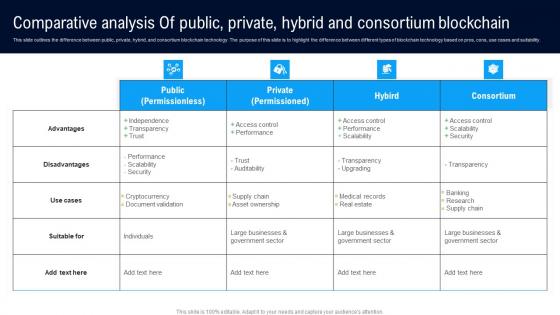
Comparative Analysis Public Private Different Architectures Of Blockchain Background Pdf
This slide outlines the difference between public, private, hybrid, and consortium blockchain technology. The purpose of this slide is to highlight the difference between different types of blockchain technology based on pros, cons, use cases and suitability. Find a pre designed and impeccable Comparative Analysis Public Private Different Architectures Of Blockchain Background Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the difference between public, private, hybrid, and consortium blockchain technology. The purpose of this slide is to highlight the difference between different types of blockchain technology based on pros, cons, use cases and suitability.
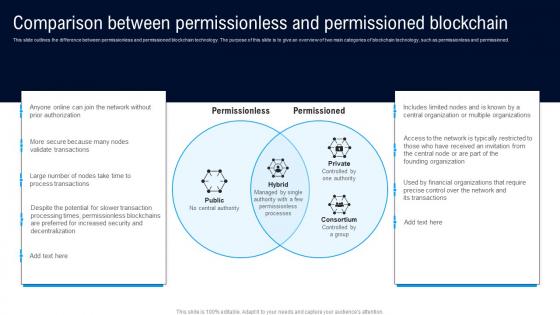
Comparison Between Permissionless Different Architectures Of Blockchain Mockup Pdf
This slide outlines the difference between permissionless and permissioned blockchain technology. The purpose of this slide is to give an overview of two main categories of blockchain technology, such as permissionless and permissioned. Boost your pitch with our creative Comparison Between Permissionless Different Architectures Of Blockchain Mockup Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the difference between permissionless and permissioned blockchain technology. The purpose of this slide is to give an overview of two main categories of blockchain technology, such as permissionless and permissioned.
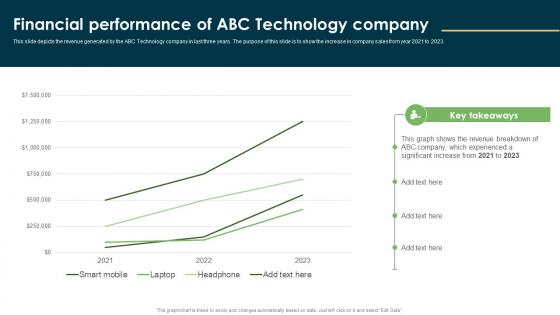
Financial Performance Of ABC Technology Wearable Technology Funding Guidelines PDF
This slide depicts the revenue generated by the ABC Technology company in last three years. The purpose of this slide is to show the increase in company sales from year 2021 to 2023. Want to ace your presentation in front of a live audience Our Financial Performance Of ABC Technology Wearable Technology Funding Guidelines PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide depicts the revenue generated by the ABC Technology company in last three years. The purpose of this slide is to show the increase in company sales from year 2021 to 2023.

Overview Of Abc Technology LTD Company Wearable Technology Funding Microsoft PDF
The purpose of this slide is to represent the overview of ABC Technology company. The main slide components include company information, vision and mission of ABC Technology Ltd. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Overview Of Abc Technology LTD Company Wearable Technology Funding Microsoft PDF can be your best option for delivering a presentation. Represent everything in detail using Overview Of Abc Technology LTD Company Wearable Technology Funding Microsoft PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The purpose of this slide is to represent the overview of ABC Technology company. The main slide components include company information, vision and mission of ABC Technology Ltd.
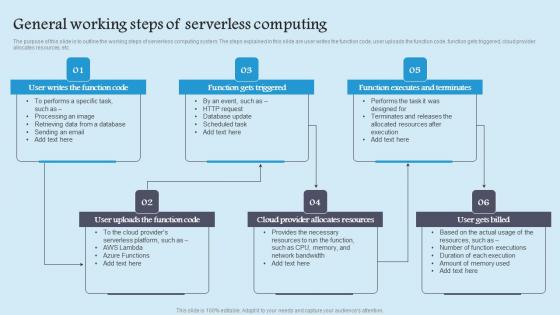
General Working Steps Role Serverless Computing Modern Technology Professional Pdf
The purpose of this slide is to outline the working steps of serverless computing system. The steps explained in this slide are user writes the function code, user uploads the function code, function gets triggered, cloud provider allocates resources, etc. Take your projects to the next level with our ultimate collection of General Working Steps Role Serverless Computing Modern Technology Professional Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The purpose of this slide is to outline the working steps of serverless computing system. The steps explained in this slide are user writes the function code, user uploads the function code, function gets triggered, cloud provider allocates resources, etc.

Major Limitations Of Serverless Role Serverless Computing Modern Technology Graphics Pdf
This slide talks about the limitations of serverless computing systems. The purpose of this slide is to briefly explain the several drawbacks of serverless architecture. These include security, reliance on outside sources, architecture complexity, etc. Want to ace your presentation in front of a live audience Our Major Limitations Of Serverless Role Serverless Computing Modern Technology Graphics Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide talks about the limitations of serverless computing systems. The purpose of this slide is to briefly explain the several drawbacks of serverless architecture. These include security, reliance on outside sources, architecture complexity, etc.
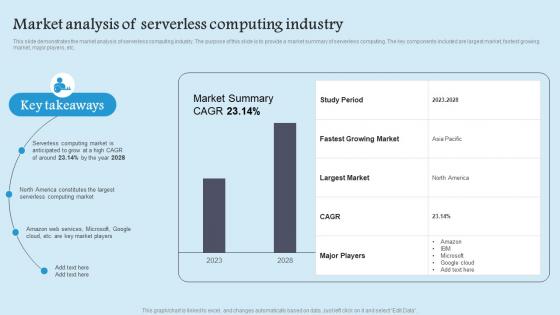
Market Analysis Serverless Role Serverless Computing Modern Technology Formats Pdf
This slide demonstrates the market analysis of serverless computing industry. The purpose of this slide is to provide a market summary of serverless computing. The key components included are largest market, fastest growing market, major players, etc. There are so many reasons you need a Market Analysis Serverless Role Serverless Computing Modern Technology Formats Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide demonstrates the market analysis of serverless computing industry. The purpose of this slide is to provide a market summary of serverless computing. The key components included are largest market, fastest growing market, major players, etc.
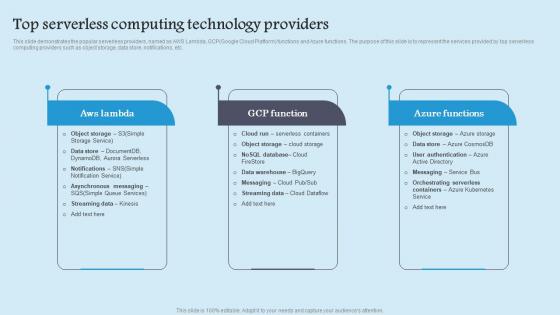
Top Serverless Computing Role Serverless Computing Modern Technology Rules Pdf
This slide demonstrates the popular serverless providers, named as AWS Lambda, GCPGoogle Cloud Platform functions and Azure functions. The purpose of this slide is to represent the services provided by top serverless computing providers such as object storage, data store, notifications, etc. Want to ace your presentation in front of a live audience Our Top Serverless Computing Role Serverless Computing Modern Technology Rules Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide demonstrates the popular serverless providers, named as AWS Lambda, GCPGoogle Cloud Platform functions and Azure functions. The purpose of this slide is to represent the services provided by top serverless computing providers such as object storage, data store, notifications, etc.
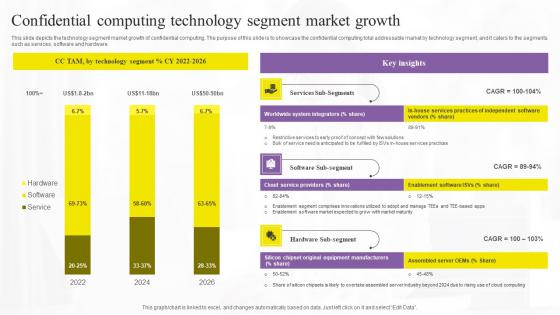
Confidential Computing Technology Segment Market Growth Mockup Pdf
This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. Find a pre-designed and impeccable Confidential Computing Technology Segment Market Growth Mockup Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware.
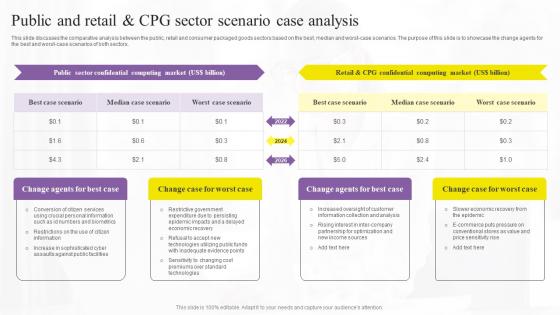
Public And Retail And Cpg Sector Confidential Computing Technologies Graphics Pdf
This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Want to ace your presentation in front of a live audience Our Public And Retail And Cpg Sector Confidential Computing Technologies Graphics Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors.

What Is Trusted Execution Environment Confidential Computing Technologies Microsoft Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Find a pre-designed and impeccable What Is Trusted Execution Environment Confidential Computing Technologies Microsoft Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments.
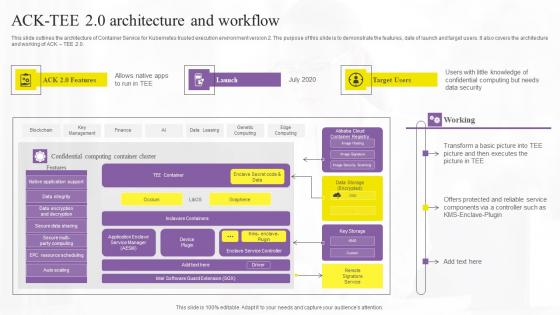
ACK Tee 20 Architecture And Workflow Confidential Computing Technologies Structure Pdf
This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Find a pre-designed and impeccable ACK Tee 20 Architecture And Workflow Confidential Computing Technologies Structure Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.

Budget For Implementing Confidential Confidential Computing Technologies Template Pdf
This slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Want to ace your presentation in front of a live audience Our Budget For Implementing Confidential Confidential Computing Technologies Template Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance.
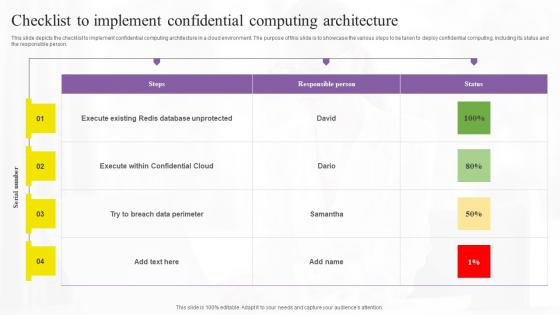
Checklist To Implement Confidential Confidential Computing Technologies Elements Pdf
This slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Get a simple yet stunning designed Checklist To Implement Confidential Confidential Computing Technologies Elements Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Checklist To Implement Confidential Confidential Computing Technologies Elements Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person.
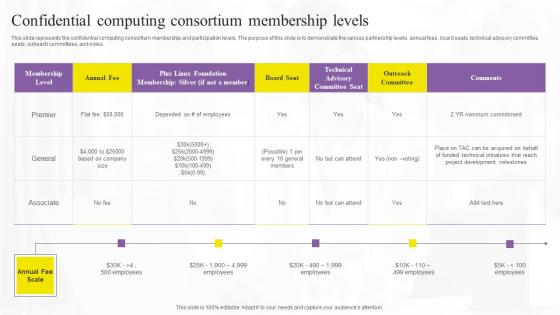
Confidential Computing Consortium Confidential Computing Technologies Microsoft Pdf
This slide represents the confidential computing consortium membership and participation levels. The purpose of this slide is to demonstrate the various partnership levels, annual fees, board seats, technical advisory committee seats, outreach committees, and notes. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing Consortium Confidential Computing Technologies Microsoft Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing Consortium Confidential Computing Technologies Microsoft Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the confidential computing consortium membership and participation levels. The purpose of this slide is to demonstrate the various partnership levels, annual fees, board seats, technical advisory committee seats, outreach committees, and notes.
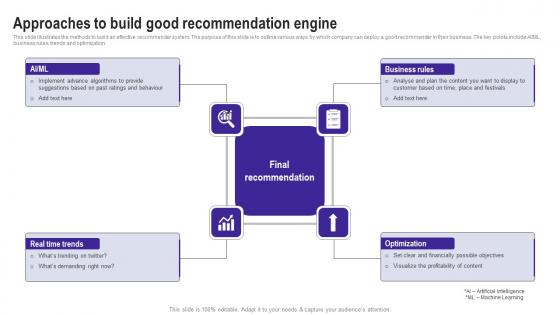
Approaches To Build Good Recommendation Use Cases Of Filtering Methods Diagrams Pdf
This slide illustrates the methods to build an effective recommender system. The purpose of this slide is to outline various ways by which company can deploy a good recommender in their business. The key points include AIML, business rules, trends and optimization. Want to ace your presentation in front of a live audience Our Approaches To Build Good Recommendation Use Cases Of Filtering Methods Diagrams Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide illustrates the methods to build an effective recommender system. The purpose of this slide is to outline various ways by which company can deploy a good recommender in their business. The key points include AIML, business rules, trends and optimization.
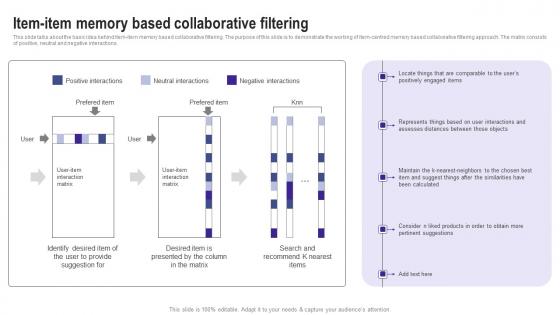
Item Item Memory Based Collaborative Filtering Use Cases Of Filtering Methods Introduction Pdf
This slide talks about the basic idea behind item item memory based collaborative filtering. The purpose of this slide is to demonstrate the working of item centred memory based collaborative filtering approach. The matrix consists of positive, neutral and negative interactions. Find a pre designed and impeccable Item Item Memory Based Collaborative Filtering Use Cases Of Filtering Methods Introduction Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the basic idea behind item item memory based collaborative filtering. The purpose of this slide is to demonstrate the working of item centred memory based collaborative filtering approach. The matrix consists of positive, neutral and negative interactions.

Logical Process Of Recommender System Technology Use Cases Of Filtering Methods Sample Pdf
This slide outlines the step by step process of a recommender system. The purpose of this slide is to represent the flow of the working of a recommendation engine. The key points include user, application, user feedback and recommender system. Boost your pitch with our creative Logical Process Of Recommender System Technology Use Cases Of Filtering Methods Sample Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the step by step process of a recommender system. The purpose of this slide is to represent the flow of the working of a recommendation engine. The key points include user, application, user feedback and recommender system.
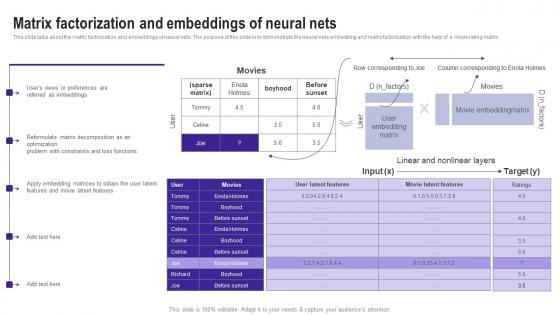
Matrix Factorization And Embeddings Of Neural Nets Use Cases Of Filtering Methods Structure Pdf
This slide talks about the matrix factorization and embeddings of neural nets. The purpose of this slide is to demonstrate the neural nets embedding and matrix factorization with the help of a movie rating matrix. Create an editable Matrix Factorization And Embeddings Of Neural Nets Use Cases Of Filtering Methods Structure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Matrix Factorization And Embeddings Of Neural Nets Use Cases Of Filtering Methods Structure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the matrix factorization and embeddings of neural nets. The purpose of this slide is to demonstrate the neural nets embedding and matrix factorization with the help of a movie rating matrix.
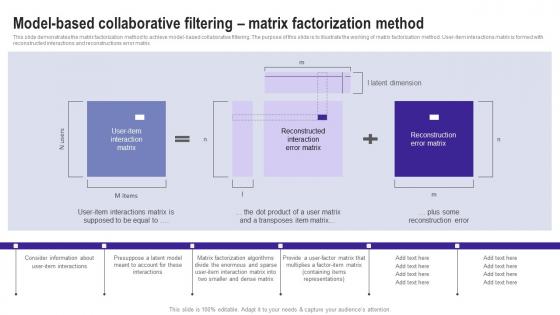
Model Based Collaborative Filtering Matrix Factorization Use Cases Of Filtering Methods Mockup Pdf
This slide demonstrates the matrix factorization method to achieve model based collaborative filtering. The purpose of this slide is to illustrate the working of matrix factorization method. User item interactions matrix is formed with reconstructed interactions and reconstructions error matrix. Want to ace your presentation in front of a live audience Our Model Based Collaborative Filtering Matrix Factorization Use Cases Of Filtering Methods Mockup Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide demonstrates the matrix factorization method to achieve model based collaborative filtering. The purpose of this slide is to illustrate the working of matrix factorization method. User item interactions matrix is formed with reconstructed interactions and reconstructions error matrix.
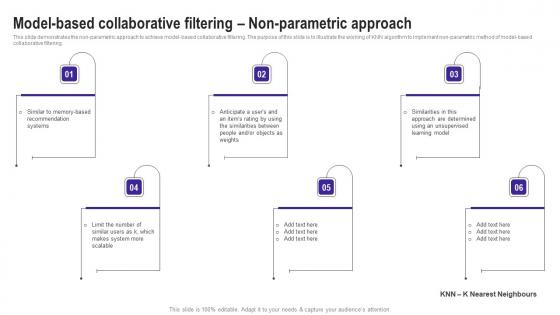
Model Based Collaborative Filtering Non Parametric Use Cases Of Filtering Methods Rules Pdf
This slide demonstrates the non parametric approach to achieve model based collaborative filtering. The purpose of this slide is to illustrate the working of KNN algorithm to implement non parametric method of model based collaborative filtering. There are so many reasons you need a Model Based Collaborative Filtering Non Parametric Use Cases Of Filtering Methods Rules Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide demonstrates the non parametric approach to achieve model based collaborative filtering. The purpose of this slide is to illustrate the working of KNN algorithm to implement non parametric method of model based collaborative filtering.

Primary Steps To Build Recommender System Use Cases Of Filtering Methods Portrait Pdf
This slide talks about four steps to build a recommender system. The purpose of this slide is to explain the procedure of developing a recommendation engine. These steps include pre processing, learning, evaluation and prediction. Get a simple yet stunning designed Primary Steps To Build Recommender System Use Cases Of Filtering Methods Portrait Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Primary Steps To Build Recommender System Use Cases Of Filtering Methods Portrait Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about four steps to build a recommender system. The purpose of this slide is to explain the procedure of developing a recommendation engine. These steps include pre processing, learning, evaluation and prediction.

Other Major Giveaway Freebie Strategies Sales Techniques For Achieving Information Pdf
This slide covers significant giveaways and free deals, such as free gift cards, photo contests, story content, and free tutorials. The purpose of this slide is to illustrate various types of free offers that companies can use. Take your projects to the next level with our ultimate collection of Other Major Giveaway Freebie Strategies Sales Techniques For Achieving Information Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide covers significant giveaways and free deals, such as free gift cards, photo contests, story content, and free tutorials. The purpose of this slide is to illustrate various types of free offers that companies can use.
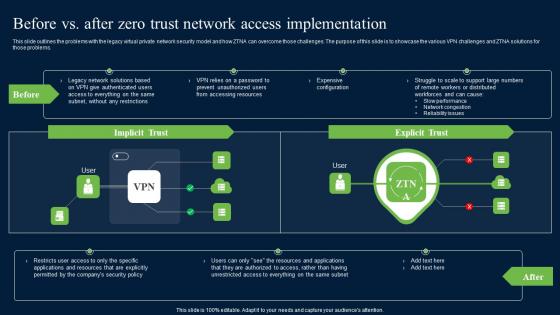
Before Vs After Zero Trust Network Access Brochure Pdf
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Challenges Of Vpn Based Remote Access Zero Trust Network Security Ideas Pdf
This slide outlines the limitations of virtual private network-based remote access services. The purpose of this slide is to showcase the various challenges of the VPN network system and how the zero trust network model can overcome those issues. There are so many reasons you need a Challenges Of Vpn Based Remote Access Zero Trust Network Security Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the limitations of virtual private network-based remote access services. The purpose of this slide is to showcase the various challenges of the VPN network system and how the zero trust network model can overcome those issues.

Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf
This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. Find highly impressive Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access.
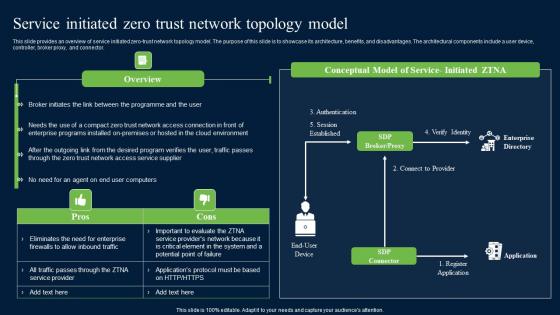
Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Find a pre-designed and impeccable Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.
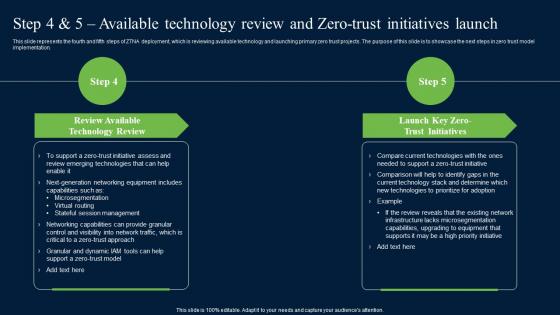
Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. There are so many reasons you need a Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.
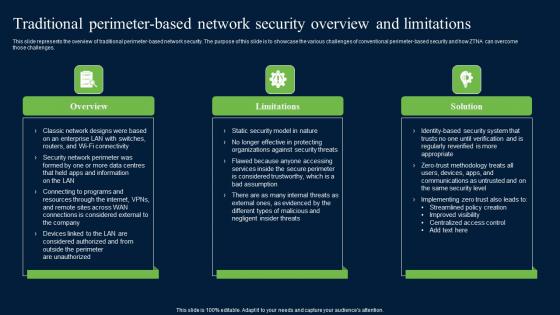
Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. Find highly impressive Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.

Training Program For Zero Trust Network Access Model Security Inspiration Pdf
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Find a pre-designed and impeccable Training Program For Zero Trust Network Access Model Security Inspiration Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training.
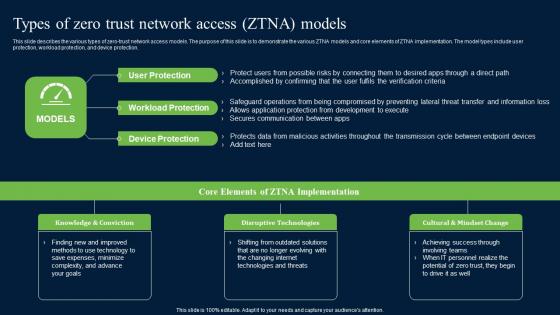
Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Boost your pitch with our creative Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.
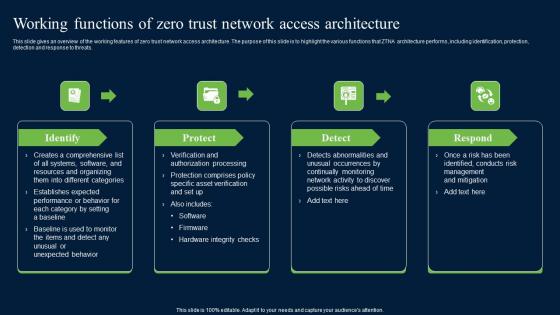
Working Functions Of Zero Trust Network Access Security Infographics Pdf
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Create an editable Working Functions Of Zero Trust Network Access Security Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Working Functions Of Zero Trust Network Access Security Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.
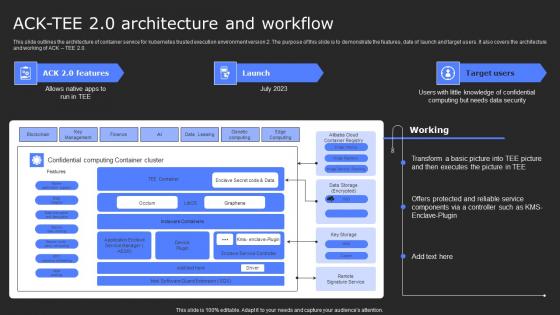
Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf
This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Boost your pitch with our creative Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.
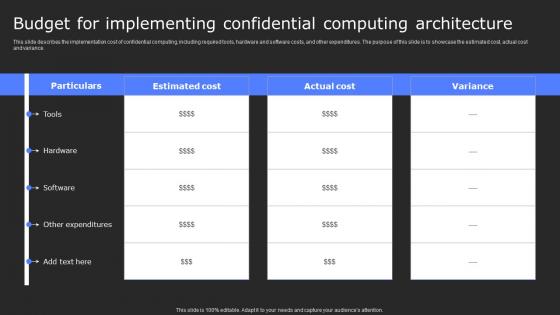
Budget For Implementing Confidential Secure Computing Framework Clipart Pdf
This slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Want to ace your presentation in front of a live audience Our Budget For Implementing Confidential Secure Computing Framework Clipart Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance.

Checklist To Implement Confidential Secure Computing Framework Rules Pdf
This slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Get a simple yet stunning designed Checklist To Implement Confidential Secure Computing Framework Rules Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Checklist To Implement Confidential Secure Computing Framework Rules Pdfcan be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person.
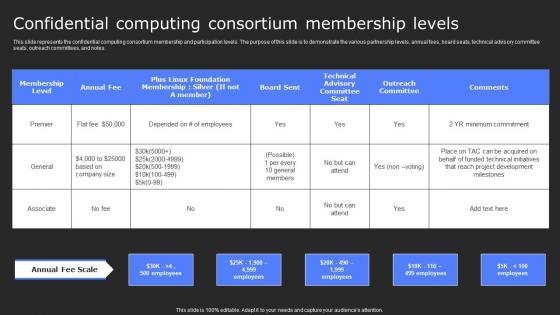
Confidential Computing Consortium Membership Secure Computing Framework Template Pdf
This slide represents the confidential computing consortium membership and participation levels. The purpose of this slide is to demonstrate the various partnership levels, annual fees, board seats, technical advisory committee seats, outreach committees, and notes. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing Consortium Membership Secure Computing Framework Template Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing Consortium Membership Secure Computing Framework Template Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the confidential computing consortium membership and participation levels. The purpose of this slide is to demonstrate the various partnership levels, annual fees, board seats, technical advisory committee seats, outreach committees, and notes.
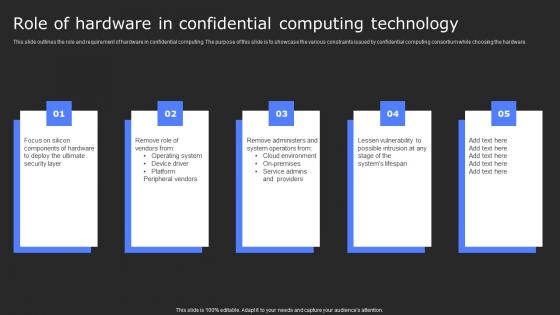
Role Of Hardware In Confidential Computing Secure Computing Framework Brochure Pdf
This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware. Find highly impressive Role Of Hardware In Confidential Computing Secure Computing Framework Brochure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Hardware In Confidential Computing Secure Computing Framework Brochure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware.
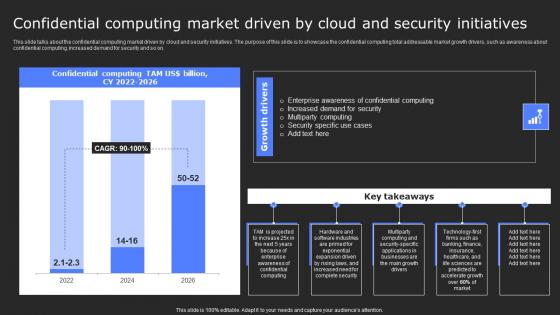
Secure Computing Framework Confidential Computing Market Driven By Mockup Pdf
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Find a pre-designed and impeccable Secure Computing Framework Confidential Computing Market Driven By Mockup Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on.
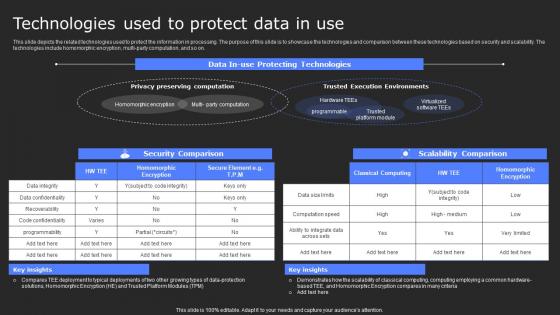
Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. There are so many reasons you need a Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.

About Cryptography Overview Cloud Data Security Using Cryptography Designs Pdf
This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc. Slidegeeks is here to make your presentations a breeze with About Cryptography Overview Cloud Data Security Using Cryptography Designs Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc.
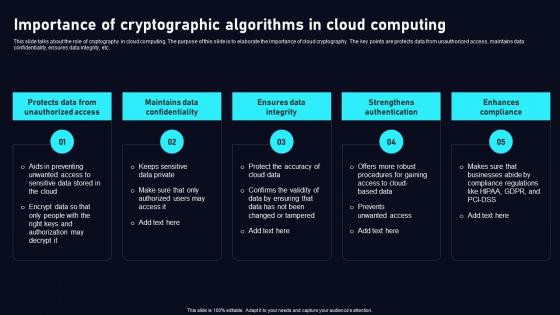
Importance Of Cryptographic Algorithms Cloud Data Security Using Cryptography Graphics Pdf
This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc. Boost your pitch with our creative Importance Of Cryptographic Algorithms Cloud Data Security Using Cryptography Graphics Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc.
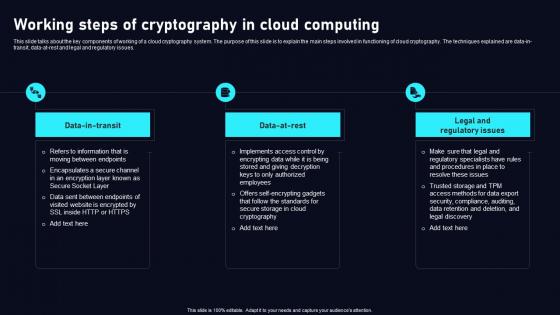
Working Steps Of Cryptography In Cloud Data Security Using Cryptography Infographics Pdf
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues. There are so many reasons you need aWorking Steps Of Cryptography In Cloud Data Security Using Cryptography Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues.

Applications Of Rapid Application Comparing RAD And Other Software Summary Pdf
This slide outlines the possible applications of the rapid application development model. The purpose of this slide is to represent the scenarios where the rapid application development model can be used, such as sufficient budget, modularized systems, and high availability of modelling designers. Find a pre-designed and impeccable Applications Of Rapid Application Comparing RAD And Other Software Summary Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the possible applications of the rapid application development model. The purpose of this slide is to represent the scenarios where the rapid application development model can be used, such as sufficient budget, modularized systems, and high availability of modelling designers.
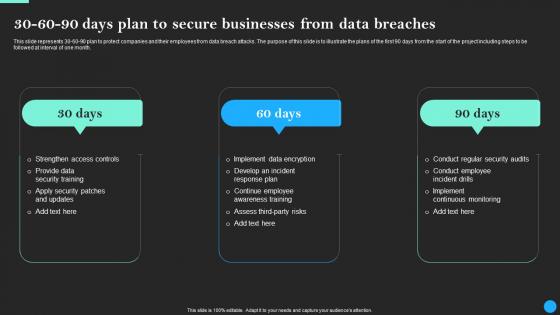
30 60 90 Days Plan To Secure Businesses From Data Breach Prevention Portrait Pdf
This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Businesses From Data Breach Prevention Portrait Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.
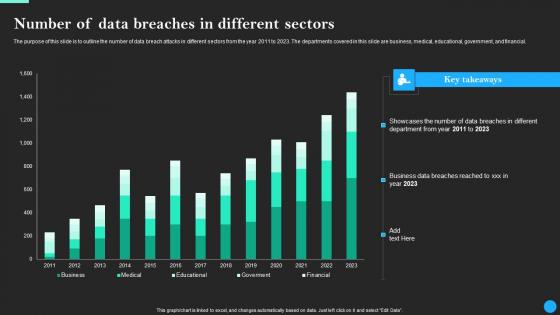
Number Of Data Breaches In Different Sectors Data Breach Prevention Microsoft Pdf
The purpose of this slide is to outline the number of data breach attacks in different sectors from the year 2011 to 2023. The departments covered in this slide are business, medical, educational, government, and financial. Take your projects to the next level with our ultimate collection of Number Of Data Breaches In Different Sectors Data Breach Prevention Microsoft Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The purpose of this slide is to outline the number of data breach attacks in different sectors from the year 2011 to 2023. The departments covered in this slide are business, medical, educational, government, and financial.

30 60 90 Days Plan To Implement Firewall As A Service Technology Formats Pdf
This slide represents 30-60-90 plan for integrating Firewall-as-a-Service into organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Implement Firewall As A Service Technology Formats Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan for integrating Firewall-as-a-Service into organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.
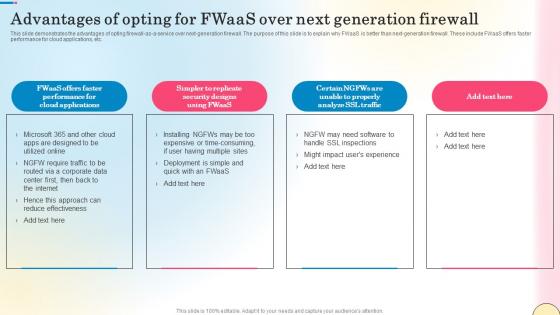
Advantages Of Opting For Fwaas Over Next Network Security Diagrams Pdf
This slide demonstrates the advantages of opting firewall-as-a-service over next-generation firewall. The purpose of this slide is to explain why FWaaS is better than next-generation firewall. These include FWaaS offers faster performance for cloud applications, etc. Create an editable Advantages Of Opting For Fwaas Over Next Network Security Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Advantages Of Opting For Fwaas Over Next Network Security Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the advantages of opting firewall-as-a-service over next-generation firewall. The purpose of this slide is to explain why FWaaS is better than next-generation firewall. These include FWaaS offers faster performance for cloud applications, etc.
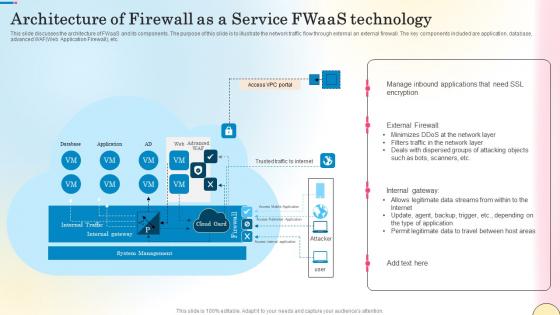
Architecture Of Firewall As A Service Fwaas Technology Network Security Themes Pdf
This slide discusses the architecture of FWaaS and its components. The purpose of this slide is to illustrate the network traffic flow through external an external firewall. The key components included are application, database, advanced WAFWeb Application Firewall, etc. Want to ace your presentation in front of a live audience Our Architecture Of Firewall As A Service Fwaas Technology Network Security Themes Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide discusses the architecture of FWaaS and its components. The purpose of this slide is to illustrate the network traffic flow through external an external firewall. The key components included are application, database, advanced WAFWeb Application Firewall, etc.
Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf
This slide represents the dashboard to track the performance of Firewall-as-a-Service deployed by different organizations. The purpose of this slide is to showcase the overall performance of FWaaS by demonstrating statistics of monthly threat status, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the dashboard to track the performance of Firewall-as-a-Service deployed by different organizations. The purpose of this slide is to showcase the overall performance of FWaaS by demonstrating statistics of monthly threat status, etc.
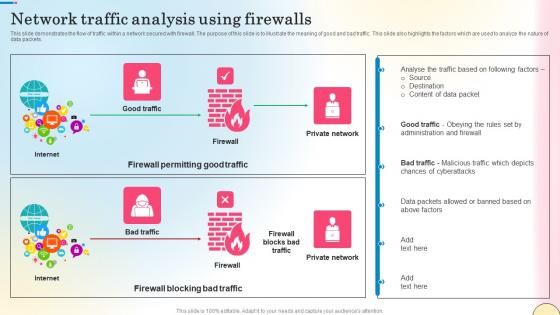
Network Traffic Analysis Using Firewalls Network Security Themes Pdf
This slide represents the architecture of Next generation Firewall as a Service technology. The purpose of this slide is to explain the working of next-generation FWaaS. The main components are branch, data center, internet, client, cloud, firewall, etc. Take your projects to the next level with our ultimate collection of Network Traffic Analysis Using Firewalls Network Security Themes Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents the architecture of Next generation Firewall as a Service technology. The purpose of this slide is to explain the working of next-generation FWaaS. The main components are branch, data center, internet, client, cloud, firewall, etc.
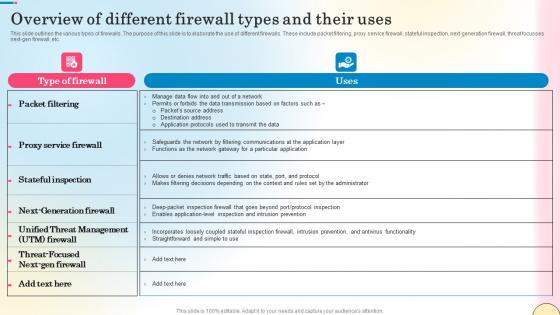
Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf
This slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc. Find a pre-designed and impeccable Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc.
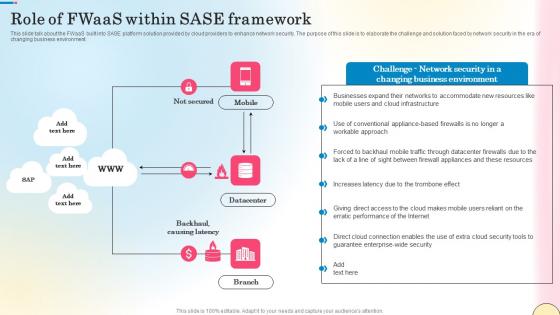
Role Of Fwaas Within Sase Framework Network Security Elements Pdf
This slide talk about the FWaaS built into SASE platform solution provided by cloud providers to enhance network security. The purpose of this slide is to elaborate the challenge and solution faced by network security in the era of changing business environment. Want to ace your presentation in front of a live audience Our Role Of Fwaas Within Sase Framework Network Security Elements Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talk about the FWaaS built into SASE platform solution provided by cloud providers to enhance network security. The purpose of this slide is to elaborate the challenge and solution faced by network security in the era of changing business environment.
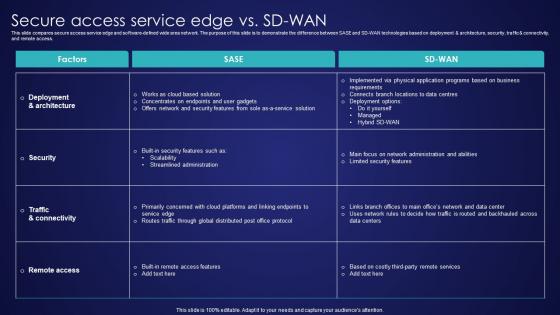
Secure Access Service Edge Vs SD Wan Wide Area Network Services Structure Pdf
This slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Take your projects to the next level with our ultimate collection of Secure Access Service Edge Vs SD Wan Wide Area Network Services Structure Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access.
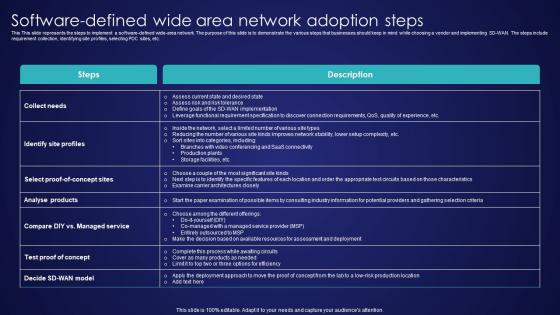
Software Defined Wide Area Network Adoption Steps Wide Area Network Services Portrait Pdf
This This slide represents the steps to implement a software-defined wide-area network. The purpose of this slide is to demonstrate the various steps that businesses should keep in mind while choosing a vendor and implementing SD-WAN. The steps include requirement collection, identifying site profiles, selecting POC sites, etc. Find a pre-designed and impeccable Software Defined Wide Area Network Adoption Steps Wide Area Network Services Portrait Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This This slide represents the steps to implement a software-defined wide-area network. The purpose of this slide is to demonstrate the various steps that businesses should keep in mind while choosing a vendor and implementing SD-WAN. The steps include requirement collection, identifying site profiles, selecting POC sites, etc.
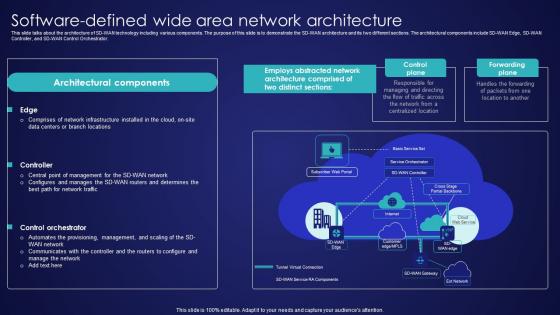
Software Defined Wide Area Network Architecture Wide Area Network Services Summary Pdf
This slide talks about the architecture of SD-WAN technology including various components. The purpose of this slide is to demonstrate the SD-WAN architecture and its two different sections. The architectural components include SD-WAN Edge, SD-WAN Controller, and SD-WAN Control Orchestrator. Boost your pitch with our creative Software Defined Wide Area Network Architecture Wide Area Network Services Summary Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the architecture of SD-WAN technology including various components. The purpose of this slide is to demonstrate the SD-WAN architecture and its two different sections. The architectural components include SD-WAN Edge, SD-WAN Controller, and SD-WAN Control Orchestrator.
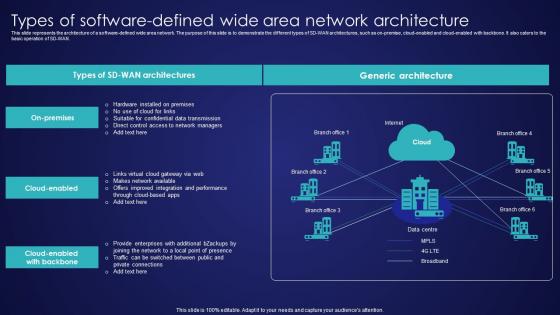
Types Of Software Defined Wide Area Network Architecture Wide Area Network Services Infographics Pdf
This slide represents the architecture of a software-defined wide area network. The purpose of this slide is to demonstrate the different types of SD-WAN architectures, such as on-premise, cloud-enabled and cloud-enabled with backbone. It also caters to the basic operation of SD-WAN. There are so many reasons you need a Types Of Software Defined Wide Area Network Architecture Wide Area Network Services Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the architecture of a software-defined wide area network. The purpose of this slide is to demonstrate the different types of SD-WAN architectures, such as on-premise, cloud-enabled and cloud-enabled with backbone. It also caters to the basic operation of SD-WAN.

Checklist For Ongoing MLOps Project For An Exploring Machine Learning Operations Elements Pdf
This slide describes the checklist for ongoing MLOps project for an organization . The purpose of this slide is to give step by step instruction there outcomes and the person in charge of the process to optimize the project. Take your projects to the next level with our ultimate collection of Checklist For Ongoing MLOps Project For An Exploring Machine Learning Operations Elements Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide describes the checklist for ongoing MLOps project for an organization . The purpose of this slide is to give step by step instruction there outcomes and the person in charge of the process to optimize the project.

Comparison Between DevOps And MLOps Exploring Machine Learning Operations Formats Pdf
This slide focuses on the comparison and relationship between two practices in software development DevOps and MLOps. The purpose of this slide is to discuss the similarities and differences between the two practices. Boost your pitch with our creative Comparison Between DevOps And MLOps Exploring Machine Learning Operations Formats Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide focuses on the comparison and relationship between two practices in software development DevOps and MLOps. The purpose of this slide is to discuss the similarities and differences between the two practices.


 Continue with Email
Continue with Email

 Home
Home


































