Purpose Slides
Key Survey Findings Of Competitive HR Retention Techniques For Business Owners Introduction Pdf
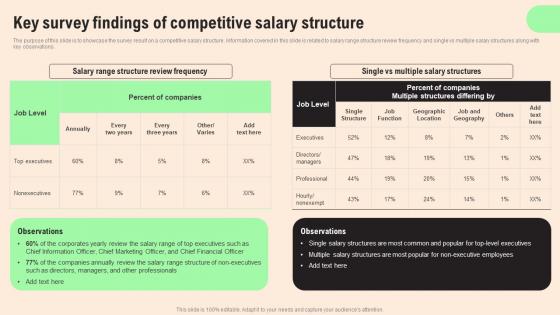
The purpose of this slide is to showcase the survey result on a competitive salary structure. Information covered in this slide is related to salary range structure review frequency and single vs multiple salary structures along with key observations. Create an editable Key Survey Findings Of Competitive HR Retention Techniques For Business Owners Introduction Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Key Survey Findings Of Competitive HR Retention Techniques For Business Owners Introduction Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The purpose of this slide is to showcase the survey result on a competitive salary structure. Information covered in this slide is related to salary range structure review frequency and single vs multiple salary structures along with key observations.

Quarterly Employee Turnover HR Retention Techniques For Business Owners Designs Pdf
The purpose of this slide is to highlight employee turnover in different departments of the organization such as sales, finance, human resource HR, customer support, digital marketing, etc. Information covered in this slide is related to quarterly employee turnover and the percentage of employees left. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Quarterly Employee Turnover HR Retention Techniques For Business Owners Designs Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Quarterly Employee Turnover HR Retention Techniques For Business Owners Designs Pdf today and make your presentation stand out from the rest The purpose of this slide is to highlight employee turnover in different departments of the organization such as sales, finance, human resource HR, customer support, digital marketing, etc. Information covered in this slide is related to quarterly employee turnover and the percentage of employees left.

Solutions To Overcome Employee HR Retention Techniques For Business Owners Structure Pdf
The purpose of this slide is to outline different solutions which will assist businesses in overcoming the staff retention challenges. The solutions mentioned in the slide is related to Salary Dissatisfaction, Better Opportunities, Hiring the wrong candidate, Unrealistic expectations of employees, No job rotation. Find highly impressive Solutions To Overcome Employee HR Retention Techniques For Business Owners Structure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Solutions To Overcome Employee HR Retention Techniques For Business Owners Structure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to outline different solutions which will assist businesses in overcoming the staff retention challenges. The solutions mentioned in the slide is related to Salary Dissatisfaction, Better Opportunities, Hiring the wrong candidate, Unrealistic expectations of employees, No job rotation.

Various Types E Learning Courses HR Retention Techniques For Business Owners Download Pdf
The purpose of this slide is to showcase different types of online courses through which managers can enhance the existing skills of the workforce. Graphic designing cyber security, ethical hacking, digital marketing and web development are the major courses that are mentioned in the slide. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Various Types E Learning Courses HR Retention Techniques For Business Owners Download Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The purpose of this slide is to showcase different types of online courses through which managers can enhance the existing skills of the workforce. Graphic designing cyber security, ethical hacking, digital marketing and web development are the major courses that are mentioned in the slide.
Checklist For Various Stages In Product Lifecycle Comprehensive Guide To Product Lifecycle Diagrams Pdf
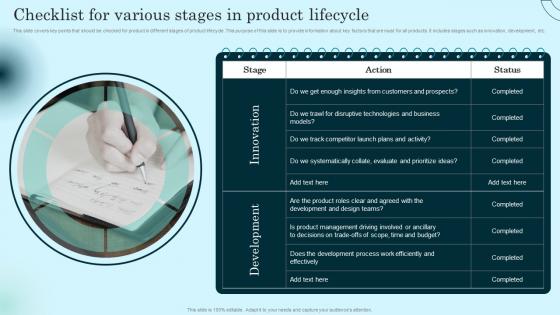
This slide covers key points that should be checked for product in different stages of product lifecycle. This purpose of this slide is to provide information about key factors that are must for all products. It includes stages such as innovation, development, etc. Want to ace your presentation in front of a live audience Our Checklist For Various Stages In Product Lifecycle Comprehensive Guide To Product Lifecycle Diagrams Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide covers key points that should be checked for product in different stages of product lifecycle. This purpose of this slide is to provide information about key factors that are must for all products. It includes stages such as innovation, development, etc.
Identify New Target Market By Entry Product Idea Comprehensive Guide To Product Lifecycle Introduction Pdf
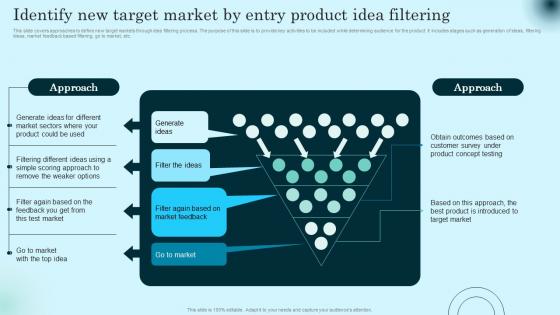
This slide covers approaches to define new target markets through idea filtering process. The purpose of this slide is to provide key activities to be included while determining audience for the product. It includes stages such as generation of ideas, filtering ideas, market feedback based filtering, go to market, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Identify New Target Market By Entry Product Idea Comprehensive Guide To Product Lifecycle Introduction Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Identify New Target Market By Entry Product Idea Comprehensive Guide To Product Lifecycle Introduction Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide covers approaches to define new target markets through idea filtering process. The purpose of this slide is to provide key activities to be included while determining audience for the product. It includes stages such as generation of ideas, filtering ideas, market feedback based filtering, go to market, etc.

Introducing A New Product Based On Survey Comprehensive Guide To Product Lifecycle Download Pdf
This slide covers brief summary of launching a new product in the market after getting customers approval via survey. The purpose of this slide is to provide information about ways to introduce a product in the market. It includes techniques such as exclusive previews, introductory offers and running social media contests, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Introducing A New Product Based On Survey Comprehensive Guide To Product Lifecycle Download Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Introducing A New Product Based On Survey Comprehensive Guide To Product Lifecycle Download Pdf This slide covers brief summary of launching a new product in the market after getting customers approval via survey. The purpose of this slide is to provide information about ways to introduce a product in the market. It includes techniques such as exclusive previews, introductory offers and running social media contests, etc.
Strategies To Win Market Competition Product Comprehensive Guide To Product Lifecycle Guidelines Pdf
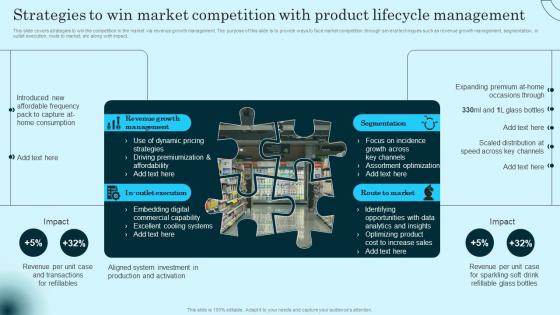
This slide covers strategies to win the competition in the market via revenue growth management. The purpose of this slide is to provide ways to face market competition through several techniques such as revenue growth management, segmentation, in outlet execution, route to market, etc along with impact. Boost your pitch with our creative Strategies To Win Market Competition Product Comprehensive Guide To Product Lifecycle Guidelines Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide covers strategies to win the competition in the market via revenue growth management. The purpose of this slide is to provide ways to face market competition through several techniques such as revenue growth management, segmentation, in outlet execution, route to market, etc along with impact.
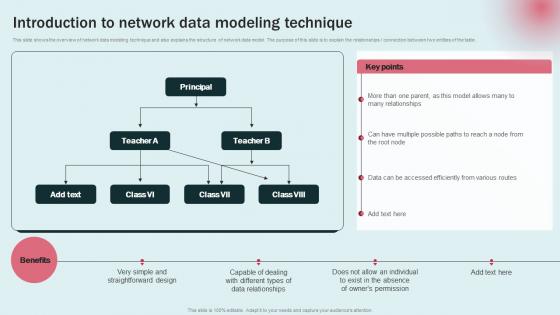
Data Modeling Approaches For Modern Analytics Introduction To Network Data Modeling Graphics Pdf
This slide shows the overview of network data modeling technique and also explains the structure of network data model. The purpose of this slide is to explain the relationships connection between two entities of the table. Slidegeeks is here to make your presentations a breeze with Data Modeling Approaches For Modern Analytics Introduction To Network Data Modeling Graphics Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide shows the overview of network data modeling technique and also explains the structure of network data model. The purpose of this slide is to explain the relationships connection between two entities of the table.

Executive Summary A Brief Insurance Agency Startup Business Plan Go To Market Strategy Topics Pdf
This slide covers a brief glimpse of what the business will be offering to the customer with market information. The purpose of this slide is to provide a brief overview of insurance agency and its future impact and what business will be offering to the customers. Want to ace your presentation in front of a live audience Our Executive Summary A Brief Insurance Agency Startup Business Plan Go To Market Strategy Topics Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide covers a brief glimpse of what the business will be offering to the customer with market information. The purpose of this slide is to provide a brief overview of insurance agency and its future impact and what business will be offering to the customers.
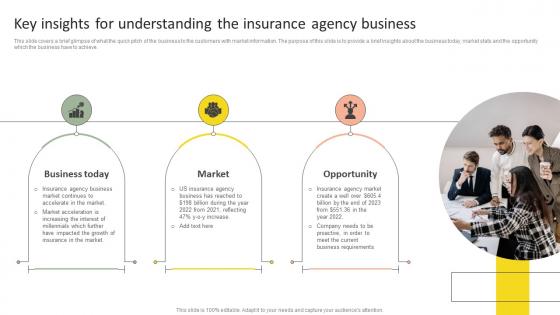
Key Insights For Understanding Insurance Agency Startup Business Plan Go To Market Strategy Portrait Pdf
This slide covers a brief glimpse of what the quick pitch of the business to the customers with market information. The purpose of this slide is to provide a brief insights about the business today, market stats and the opportunity which the business have to achieve. Get a simple yet stunning designed Key Insights For Understanding Insurance Agency Startup Business Plan Go To Market Strategy Portrait Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Key Insights For Understanding Insurance Agency Startup Business Plan Go To Market Strategy Portrait Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers a brief glimpse of what the quick pitch of the business to the customers with market information. The purpose of this slide is to provide a brief insights about the business today, market stats and the opportunity which the business have to achieve.
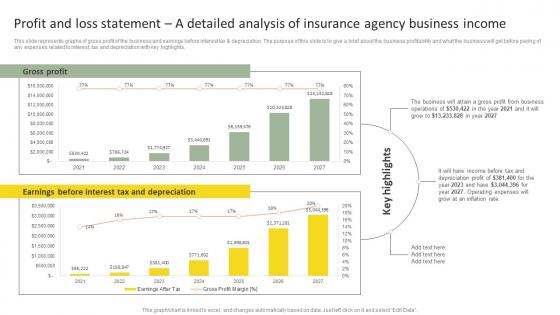
Profit And Loss Statement A Insurance Agency Startup Business Plan Go To Market Strategy Topics Pdf
This slide represents graphs of gross profit of the business and earnings before interest tax and depreciation. The purpose of this slide is to give a brief about the business profitability and what the business will get before paying of any expenses related to interest, tax and depreciation with key highlights. Slidegeeks is here to make your presentations a breeze with Profit And Loss Statement A Insurance Agency Startup Business Plan Go To Market Strategy Topics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents graphs of gross profit of the business and earnings before interest tax and depreciation. The purpose of this slide is to give a brief about the business profitability and what the business will get before paying of any expenses related to interest, tax and depreciation with key highlights.

About Sidechain Blockchain Network Different Architectures Of Blockchain Guidelines Pdf
This slide highlights the overview and examples of sidechain blockchain networks. The purpose of this slide is to give an overview of the sidechain, including its workflow and examples. The examples cater to parachain, plasma, and rootstock. This About Sidechain Blockchain Network Different Architectures Of Blockchain Guidelines Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide highlights the overview and examples of sidechain blockchain networks. The purpose of this slide is to give an overview of the sidechain, including its workflow and examples. The examples cater to parachain, plasma, and rootstock.
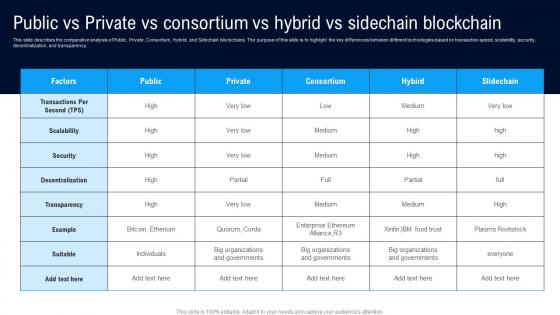
Public Vs Private Vs Consortium Vs Hybrid Different Architectures Of Blockchain Template Pdf
This slide describes the comparative analysis of Public, Private, Consortium, Hybrid, and Sidechain blockchains. The purpose of this slide is to highlight the key differences between different technologies based on transaction speed, scalability, security, decentralization, and transparency. Slidegeeks is here to make your presentations a breeze with Public Vs Private Vs Consortium Vs Hybrid Different Architectures Of Blockchain Template Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the comparative analysis of Public, Private, Consortium, Hybrid, and Sidechain blockchains. The purpose of this slide is to highlight the key differences between different technologies based on transaction speed, scalability, security, decentralization, and transparency.
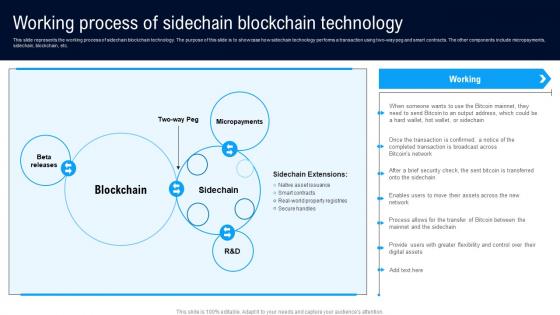
Working Process Of Sidechain Different Architectures Of Blockchain Microsoft Pdf
This slide represents the working process of sidechain blockchain technology. The purpose of this slide is to showcase how sidechain technology performs a transaction using two way peg and smart contracts. The other components include micropayments, sidechain, blockchain, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Working Process Of Sidechain Different Architectures Of Blockchain Microsoft Pdf can be your best option for delivering a presentation. Represent everything in detail using Working Process Of Sidechain Different Architectures Of Blockchain Microsoft Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the working process of sidechain blockchain technology. The purpose of this slide is to showcase how sidechain technology performs a transaction using two way peg and smart contracts. The other components include micropayments, sidechain, blockchain, etc.
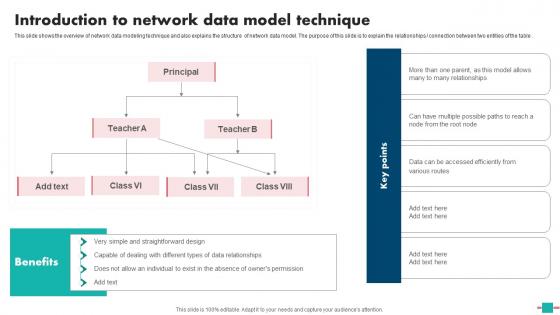
Database Modeling Introduction To Network Data Model Technique Topics Pdf
This slide shows the overview of network data modeling technique and also explains the structure of network data model. The purpose of this slide is to explain the relationships connection between two entities of the table. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Database Modeling Introduction To Network Data Model Technique Topics Pdf can be your best option for delivering a presentation. Represent everything in detail using Database Modeling Introduction To Network Data Model Technique Topics Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide shows the overview of network data modeling technique and also explains the structure of network data model. The purpose of this slide is to explain the relationships connection between two entities of the table.

Database Modeling Relational Data Model Technique In DBMs Template Pdf
This slide shows the overview of relational data modeling technique which represents information in the form of tables. The purpose of this slide is to explain the different constraints of relational data modeling technique. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Database Modeling Relational Data Model Technique In DBMs Template Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Database Modeling Relational Data Model Technique In DBMs Template Pdf This slide shows the overview of relational data modeling technique which represents information in the form of tables. The purpose of this slide is to explain the different constraints of relational data modeling technique.
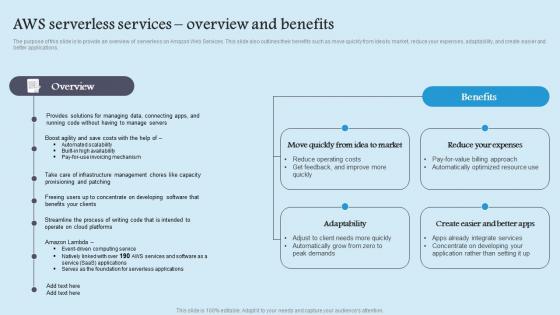
AWS Serverless Services Role Serverless Computing Modern Technology Mockup Pdf
The purpose of this slide is to provide an overview of serverless on Amazon Web Services. This slide also outlines their benefits such as move quickly from idea to market, reduce your expenses, adaptability, and create easier and better applications. Find highly impressive AWS Serverless Services Role Serverless Computing Modern Technology Mockup Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download AWS Serverless Services Role Serverless Computing Modern Technology Mockup Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to provide an overview of serverless on Amazon Web Services. This slide also outlines their benefits such as move quickly from idea to market, reduce your expenses, adaptability, and create easier and better applications.
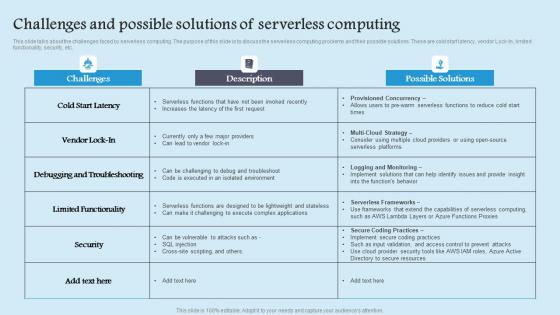
Challenges And Possible Solutions Role Serverless Computing Modern Technology Clipart Pdf
This slide talks about the challenges faced by serverless computing. The purpose of this slide is to discuss the serverless computing problems and their possible solutions. These are cold start latency, vendor Lock In, limited functionality, security, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Challenges And Possible Solutions Role Serverless Computing Modern Technology Clipart Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the challenges faced by serverless computing. The purpose of this slide is to discuss the serverless computing problems and their possible solutions. These are cold start latency, vendor Lock In, limited functionality, security, etc.
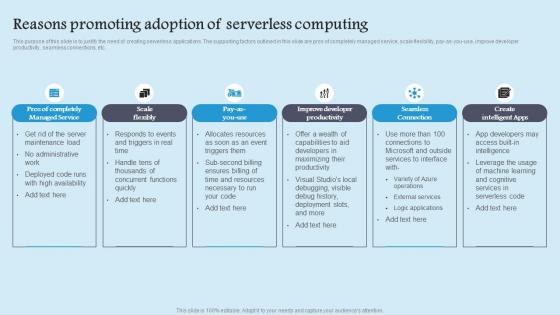
Reasons Promoting Adoption Role Serverless Computing Modern Technology Topics Pdf
This purpose of this slide is to justify the need of creating serverless applications. The supporting factors outlined in this slide are pros of completely managed service, scale flexibility, pay as you use, improve developer productivity, seamless connections, etc. Slidegeeks is here to make your presentations a breeze with Reasons Promoting Adoption Role Serverless Computing Modern Technology Topics Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This purpose of this slide is to justify the need of creating serverless applications. The supporting factors outlined in this slide are pros of completely managed service, scale flexibility, pay as you use, improve developer productivity, seamless connections, etc.

Role Of Cloud Providers Role Serverless Computing Modern Technology Inspiration Pdf
This slide talks about the role of cloud providers in serverless computing. The purpose of this slide is to explain the two main categories of cloud computing services. These types are known as Backend as a Service BaaS and Function as a Service FaaS. Find highly impressive Role Of Cloud Providers Role Serverless Computing Modern Technology Inspiration Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Cloud Providers Role Serverless Computing Modern Technology Inspiration Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide talks about the role of cloud providers in serverless computing. The purpose of this slide is to explain the two main categories of cloud computing services. These types are known as Backend as a Service BaaS and Function as a Service FaaS.
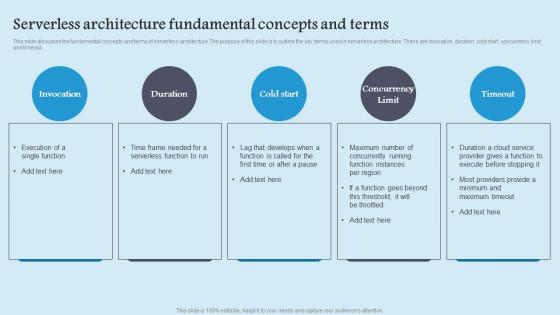
Serverless Architecture Fundamental Role Serverless Computing Modern Technology Structure Pdf
This slide discusses the fundamental concepts and terms of serverless architecture. The purpose of this slide is to outline the key terms used in serverless architecture. These are invocation, duration, cold start, concurrency limit and timeout. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Serverless Architecture Fundamental Role Serverless Computing Modern Technology Structure Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Serverless Architecture Fundamental Role Serverless Computing Modern Technology Structure Pdf This slide discusses the fundamental concepts and terms of serverless architecture. The purpose of this slide is to outline the key terms used in serverless architecture. These are invocation, duration, cold start, concurrency limit and timeout.
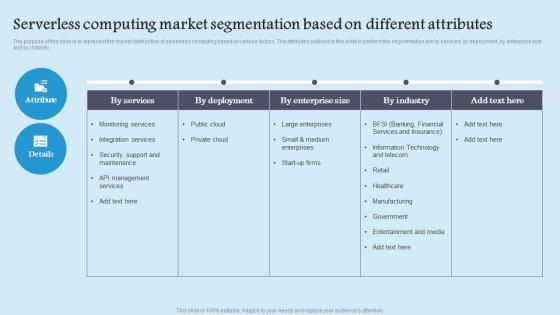
Serverless Computing Market Role Serverless Computing Modern Technology Diagrams Pdf
The purpose of this slide is to represent the market distribution of serverless computing based on various factors. The attributes outlined in this slide to perform the segmentation are by services, by deployment, by enterprise size and by industry. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Serverless Computing Market Role Serverless Computing Modern Technology Diagrams Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The purpose of this slide is to represent the market distribution of serverless computing based on various factors. The attributes outlined in this slide to perform the segmentation are by services, by deployment, by enterprise size and by industry.
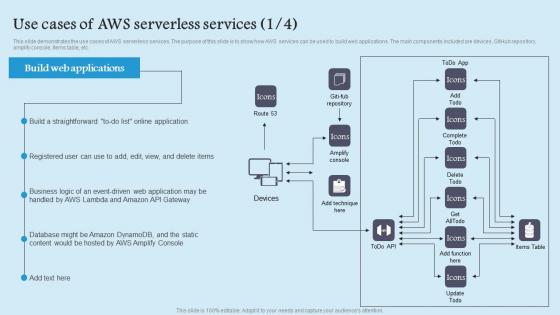
Use Cases Of Aws Serverless Role Serverless Computing Modern Technology Rules Pdf
This slide demonstrates the use cases of AWS serverless services. The purpose of this slide is to show how AWS services can be used to build web applications. The main components included are devices, GitHub repository, amplify console, items table, etc. Get a simple yet stunning designed Use Cases Of Aws Serverless Role Serverless Computing Modern Technology Rules Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Use Cases Of Aws Serverless Role Serverless Computing Modern Technology Rules Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide demonstrates the use cases of AWS serverless services. The purpose of this slide is to show how AWS services can be used to build web applications. The main components included are devices, GitHub repository, amplify console, items table, etc.
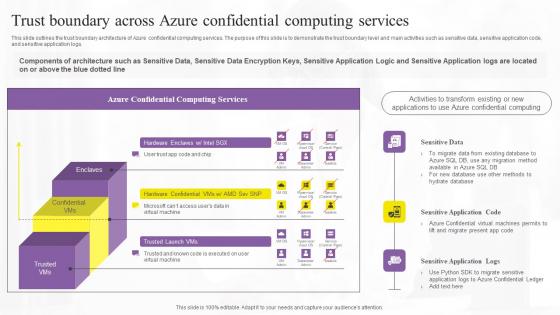
Trust Boundary Across Azure Confidential Computing Technologies Themes Pdf
This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Slidegeeks is here to make your presentations a breeze with Trust Boundary Across Azure Confidential Computing Technologies Themes Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs.

ACK TEE Introduction And Version 10 Confidential Computing Technologies Diagrams Pdf
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. Boost your pitch with our creative ACK TEE Introduction And Version 10 Confidential Computing Technologies Diagrams Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.
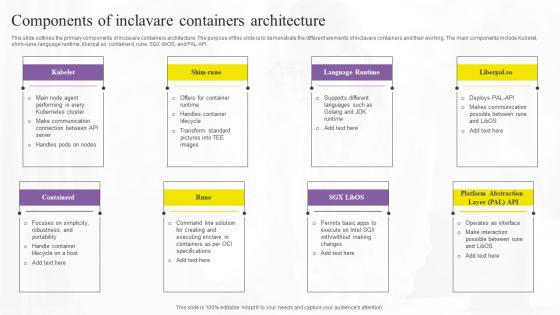
Components Of Inclavare Containers Confidential Computing Technologies Diagrams Pdf
This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Slidegeeks is here to make your presentations a breeze with Components Of Inclavare Containers Confidential Computing Technologies Diagrams Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API.
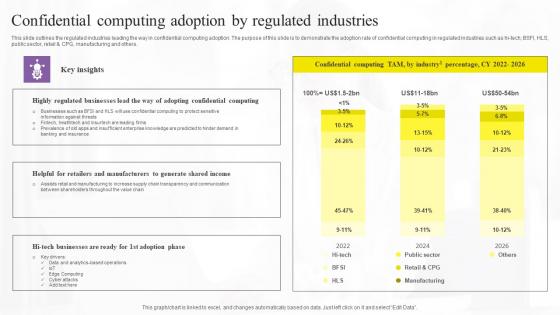
Confidential Computing Adoption By Confidential Computing Technologies Elements Pdf
This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Confidential Computing Adoption By Confidential Computing Technologies Elements Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Confidential Computing Adoption By Confidential Computing Technologies Elements Pdf today and make your presentation stand out from the rest This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others.
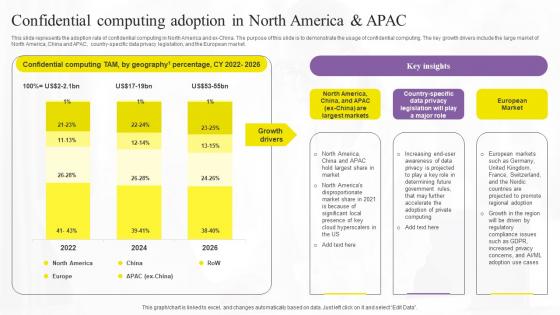
Confidential Computing Adoption In Confidential Computing Technologies Download Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Adoption In Confidential Computing Technologies Download Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Adoption In Confidential Computing Technologies Download Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
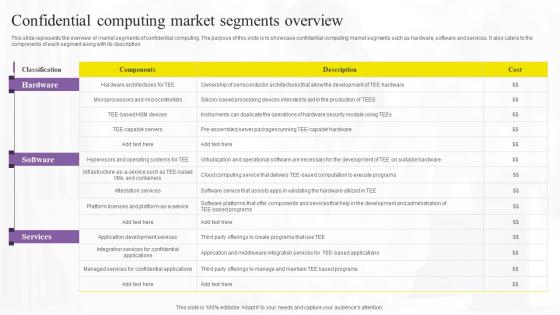
Confidential Computing Market Confidential Computing Technologies Diagrams Pdf
This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing Market Confidential Computing Technologies Diagrams Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description.
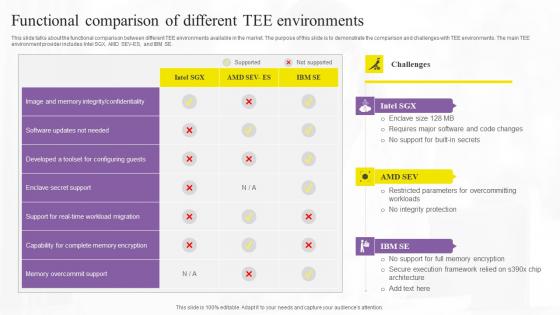
Functional Comparison Of Different Confidential Computing Technologies Inspiration Pdf
This slide talks about the functional comparison between different TEE environments available in the market. The purpose of this slide is to demonstrate the comparison and challenges with TEE environments. The main TEE environment provider includes Intel SGX, AMD SEV-ES, and IBM SE. This Functional Comparison Of Different Confidential Computing Technologies Inspiration Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the functional comparison between different TEE environments available in the market. The purpose of this slide is to demonstrate the comparison and challenges with TEE environments. The main TEE environment provider includes Intel SGX, AMD SEV-ES, and IBM SE.

Occlum System Architecture And Confidential Computing Technologies Professional Pdf
This slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Take your projects to the next level with our ultimate collection of Occlum System Architecture And Confidential Computing Technologies Professional Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on.

Medical Check Up Campaign To Increase Health Healthcare Promotion Pictures Pdf
The following slide outlines brief introduction to health check up campaign covering title, overview, goals, activities, and evaluation. The purpose of this slide is to assist medical care companies in raising awareness of continuous regular check-ups amongst target audience and educate them on how to prioritize their wellbeing. Take your projects to the next level with our ultimate collection of Medical Check Up Campaign To Increase Health Healthcare Promotion Pictures Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide outlines brief introduction to health check up campaign covering title, overview, goals, activities, and evaluation. The purpose of this slide is to assist medical care companies in raising awareness of continuous regular check-ups amongst target audience and educate them on how to prioritize their wellbeing.
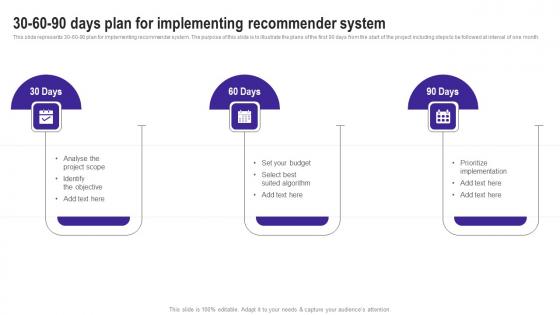
30 60 90 Days Plan For Implementing Use Cases Of Filtering Methods Background Pdf
This slide represents 30 60 90 plan for implementing recommender system. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Take your projects to the next level with our ultimate collection of 30 60 90 Days Plan For Implementing Use Cases Of Filtering Methods Background Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents 30 60 90 plan for implementing recommender system. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.
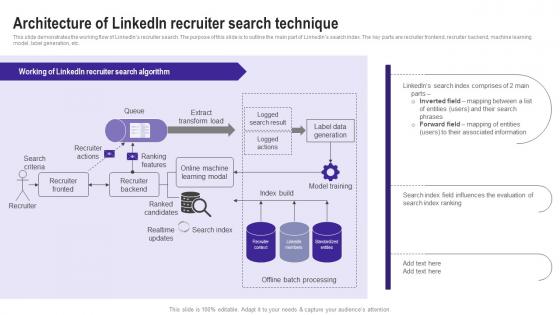
Architecture Of Linkedin Use Cases Of Filtering Methods Rules Pdf
This slide demonstrates the working flow of LinkedIns recruiter search. The purpose of this slide is to outline the main part of LinkedIns search index. The key parts are recruiter frontend, recruiter backend, machine learning model, label generation, etc. Get a simple yet stunning designed Architecture Of Linkedin Use Cases Of Filtering Methods Rules Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Architecture Of Linkedin Use Cases Of Filtering Methods Rules Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide demonstrates the working flow of LinkedIns recruiter search. The purpose of this slide is to outline the main part of LinkedIns search index. The key parts are recruiter frontend, recruiter backend, machine learning model, label generation, etc.
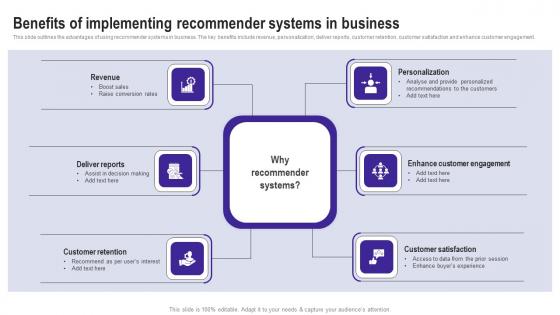
Benefits Of Implementing Recommender Systems Use Cases Of Filtering Methods Graphics Pdf
This slide talks about the major cold start problem experienced while implementing some recommendation techniques. The purpose of this slide is to outline the types and reasons of cold start issue. The reasons include new users, low interaction, etc. Slidegeeks is here to make your presentations a breeze with Benefits Of Implementing Recommender Systems Use Cases Of Filtering Methods Graphics Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the major cold start problem experienced while implementing some recommendation techniques. The purpose of this slide is to outline the types and reasons of cold start issue. The reasons include new users, low interaction, etc.
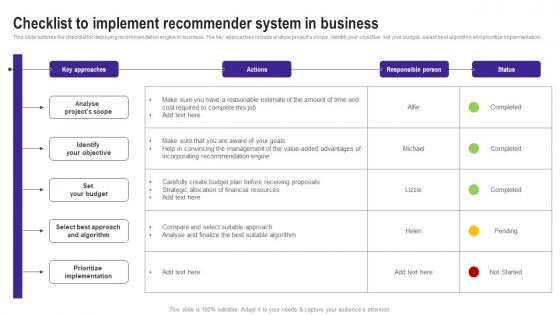
Checklist To Implement Recommender System Business Use Cases Of Filtering Methods Rules Pdf
This slide represents the user user and item item memory based collaborative filtering recommendation techniques. The purpose of this slide is to compare the two memory based collaborative filtering recommendation methods based on different factors. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Checklist To Implement Recommender System Business Use Cases Of Filtering Methods Rules Pdf can be your best option for delivering a presentation. Represent everything in detail using Checklist To Implement Recommender System Business Use Cases Of Filtering Methods Rules Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the user user and item item memory based collaborative filtering recommendation techniques. The purpose of this slide is to compare the two memory based collaborative filtering recommendation methods based on different factors.
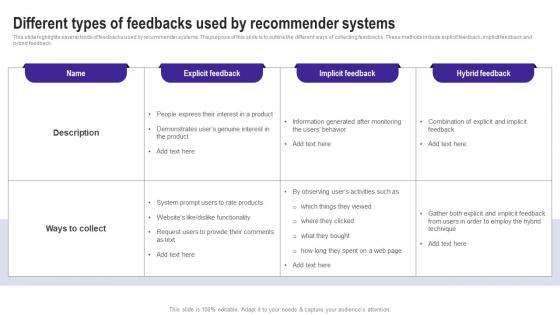
Different Types Of Feedbacks Used By Recommender Use Cases Of Filtering Methods Rules Pdf
This slide highlights several kinds of feedbacks used by recommender systems. The purpose of this slide is to outline the different ways of collecting feedbacks. These methods include explicit feedback, implicit feedback and hybrid feedback. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Different Types Of Feedbacks Used By Recommender Use Cases Of Filtering Methods Rules Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide highlights several kinds of feedbacks used by recommender systems. The purpose of this slide is to outline the different ways of collecting feedbacks. These methods include explicit feedback, implicit feedback and hybrid feedback.
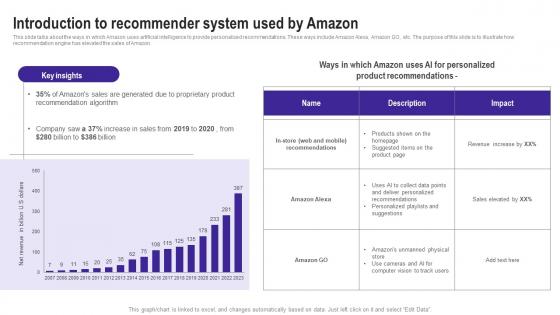
Introduction To Recommender System Used By Amazon Use Cases Of Filtering Methods Summary Pdf
This slide talks about the ways in which Amazon uses artificial intelligence to provide personalized recommendations. These ways include Amazon Alexa, Amazon GO, etc. The purpose of this slide is to illustrate how recommendation engine has elevated the sales of Amazon. This Introduction To Recommender System Used By Amazon Use Cases Of Filtering Methods Summary Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the ways in which Amazon uses artificial intelligence to provide personalized recommendations. These ways include Amazon Alexa, Amazon GO, etc. The purpose of this slide is to illustrate how recommendation engine has elevated the sales of Amazon.

Statistical Measures To Evaluate Accuracy Of Use Cases Of Filtering Methods Introduction Pdf
This slide talks about the various methods of evaluating the performance of a recommender systems. The purpose of this slide is to illustrate the ways to check if a recommendation system is good enough or not. These methods include K fold cross validation, MAE and RMSD. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Statistical Measures To Evaluate Accuracy Of Use Cases Of Filtering Methods Introduction Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Statistical Measures To Evaluate Accuracy Of Use Cases Of Filtering Methods Introduction Pdf This slide talks about the various methods of evaluating the performance of a recommender systems. The purpose of this slide is to illustrate the ways to check if a recommendation system is good enough or not. These methods include K fold cross validation, MAE and RMSD.
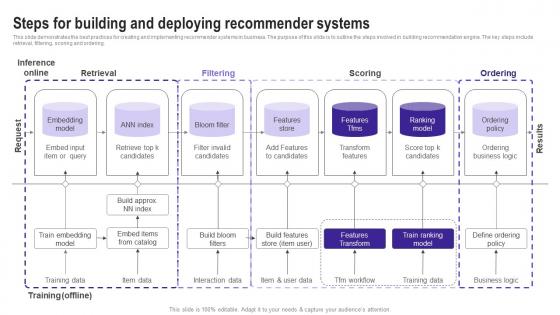
Steps For Building And Deploying Recommender Use Cases Of Filtering Methods Clipart Pdf
This slide demonstrates the best practices for creating and implementing recommender systems in business. The purpose of this slide is to outline the steps involved in building recommendation engine. The key steps include retrieval, filtering, scoring and ordering. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Steps For Building And Deploying Recommender Use Cases Of Filtering Methods Clipart Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide demonstrates the best practices for creating and implementing recommender systems in business. The purpose of this slide is to outline the steps involved in building recommendation engine. The key steps include retrieval, filtering, scoring and ordering.
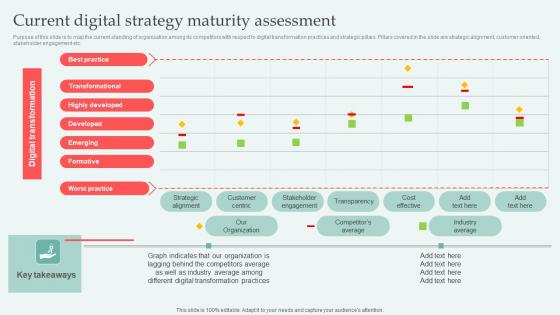
Current Digital Strategy Maturity Digital Approaches To Increase Business Growth Structure Pdf
Purpose of this slide is to map the current standing of organization among its competitors with respect to digital transformation practices and strategic pillars. Pillars covered in the slide are strategic alignment, customer oriented, stakeholder engagement etc. This Current Digital Strategy Maturity Digital Approaches To Increase Business Growth Structure Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. Purpose of this slide is to map the current standing of organization among its competitors with respect to digital transformation practices and strategic pillars. Pillars covered in the slide are strategic alignment, customer oriented, stakeholder engagement etc.

As A Service Deployment Approach Zero Trust Network Security Microsoft Pdf
This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. Boost your pitch with our creative As A Service Deployment Approach Zero Trust Network Security Microsoft Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software.

Case Study Intellectual Property Protection With Zero Trust Network Security Inspiration Pdf
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Want to ace your presentation in front of a live audience Our Case Study Intellectual Property Protection With Zero Trust Network Security Inspiration Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.
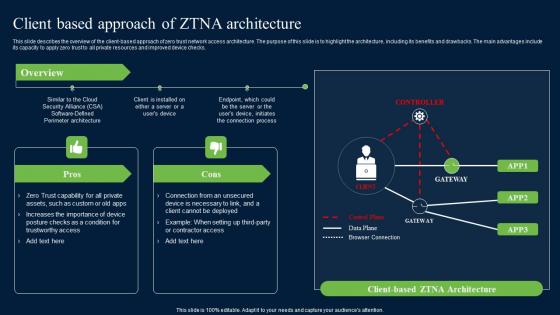
Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Get a simple yet stunning designed Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.
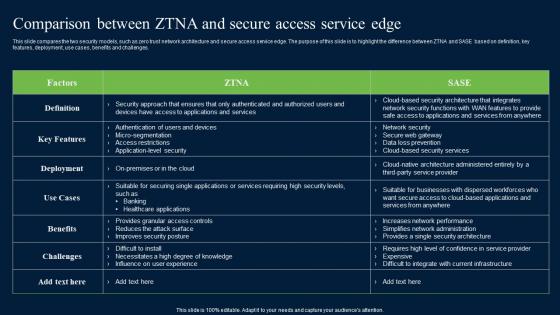
Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Slidegeeks is here to make your presentations a breeze with Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.

Critical Principles Of Zero Trust Network Access Security Formats Pdf
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Critical Principles Of Zero Trust Network Access Security Formats Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Critical Principles Of Zero Trust Network Access Security Formats Pdf today and make your presentation stand out from the rest This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything.
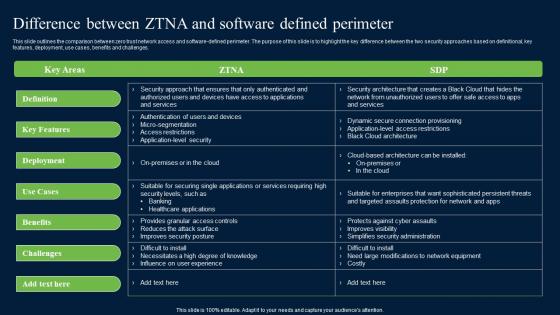
Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf can be your best option for delivering a presentation. Represent everything in detail using Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
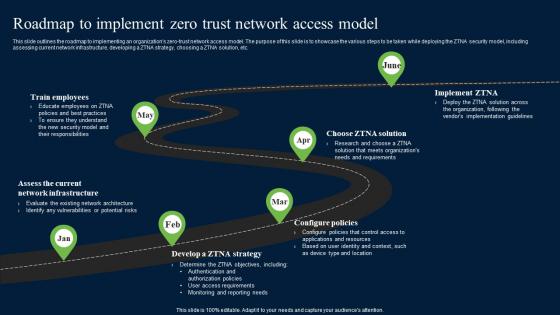
Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.
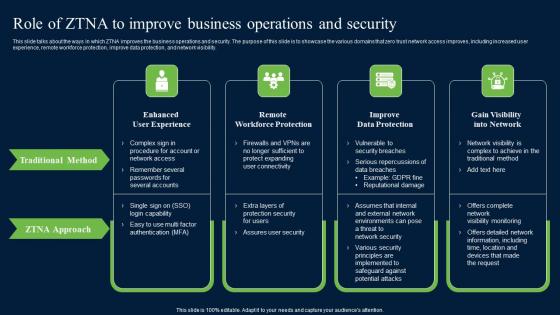
Role Of ZTNA To Improve Business Operations And Security Zero Trust Network Security Inspiration Pdf
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Take your projects to the next level with our ultimate collection of Role Of ZTNA To Improve Business Operations And Security Zero Trust Network Security Inspiration Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.

Solutions To Overcome ZTNA Implementation Challenges Zero Trust Network Security Designs Pdf
This slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind. Boost your pitch with our creative Solutions To Overcome ZTNA Implementation Challenges Zero Trust Network Security Designs Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind.

Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf
This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members. Create an editable Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members.
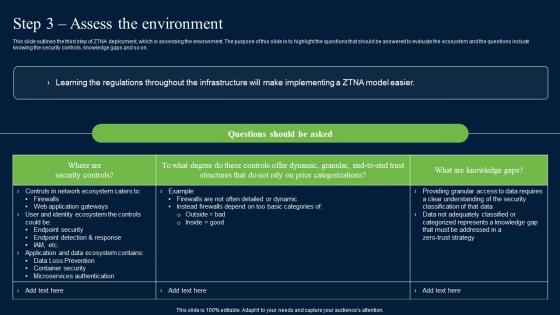
Step 3 Assess The Environment Zero Trust Network Security Brochure Pdf
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Want to ace your presentation in front of a live audience Our Step 3 Assess The Environment Zero Trust Network Security Brochure Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.
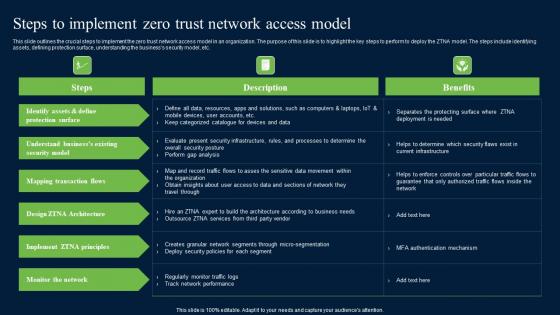
Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Get a simple yet stunning designed Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.

Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf can be your best option for delivering a presentation. Represent everything in detail using Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on.
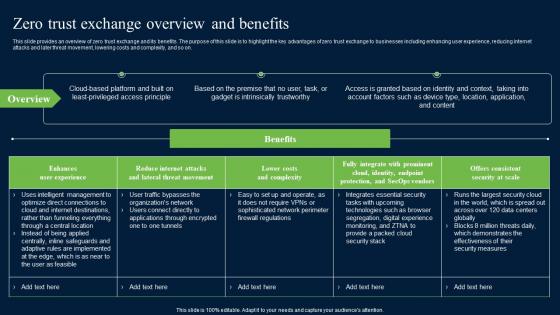
Zero Trust Exchange Overview And Benefits Zero Trust Network Security Introduction Pdf
This slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on. Want to ace your presentation in front of a live audience Our Zero Trust Exchange Overview And Benefits Zero Trust Network Security Introduction Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
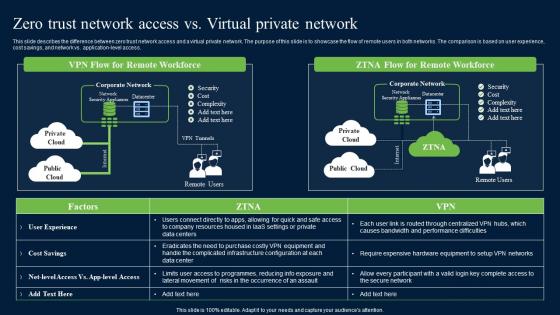
Zero Trust Network Access Vs Virtual Private Network Mockup Pdf
This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Network Access Vs Virtual Private Network Mockup Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Network Access Vs Virtual Private Network Mockup Pdf today and make your presentation stand out from the rest This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access.
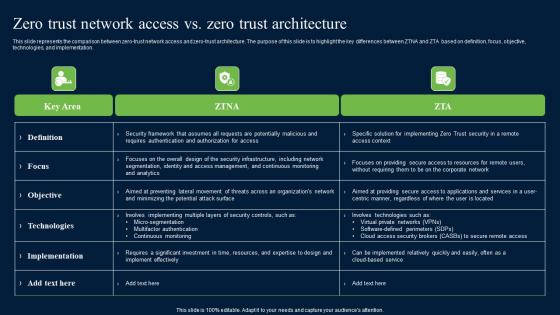
Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation.

Zero Trust Network Access ZTNA Introduction Graphics Pdf
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Find highly impressive Zero Trust Network Access ZTNA Introduction Graphics Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Network Access ZTNA Introduction Graphics Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.


 Continue with Email
Continue with Email

 Home
Home


































