Risk Communication

Customer Getting Threat For The System Failure Ppt PowerPoint Presentation Gallery Layouts PDF
Presenting customer getting threat for the system failure ppt powerpoint presentation gallery layouts pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including customer getting threat for the system failure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Settings To Prevent Online Threats Ppt PowerPoint Presentation Gallery Structure PDF
Presenting security settings to prevent online threats ppt powerpoint presentation gallery structure pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including security settings to prevent online threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon Indicating Malware Detection In Business Threats Landscape Ppt Layouts Influencers PDF
Presenting Icon Indicating Malware Detection In Business Threats Landscape Ppt Layouts Influencers PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Icon Indicating, Malware Detection, Business Threats Landscape. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Survey Insights On Data Breach Threats Incidents Icon Ppt Infographics Sample PDF
Presenting Survey Insights On Data Breach Threats Incidents Icon Ppt Infographics Sample PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Survey Insights, Data Breach Threats, Incidents Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
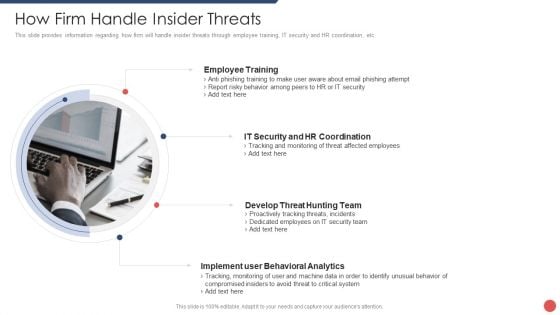
Security Functioning Centre How Firm Handle Insider Threats Ppt Summary Background Image PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a security functioning centre how firm handle insider threats ppt summary background image pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Types Of Threats In IT Security IT Ppt Summary Graphics Tutorials PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting types of threats in it security it ppt summary graphics tutorials pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
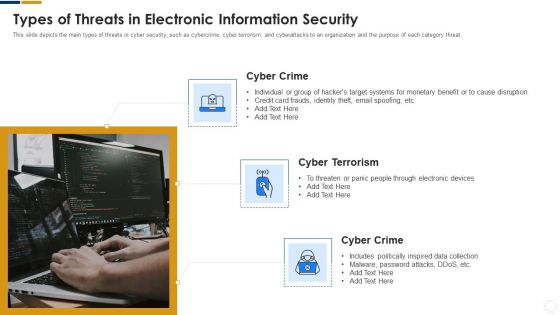
Cybersecurity Types Of Threats In Electronic Information Security Ppt Examples PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a cybersecurity types of threats in electronic information security ppt examples pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber crime. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
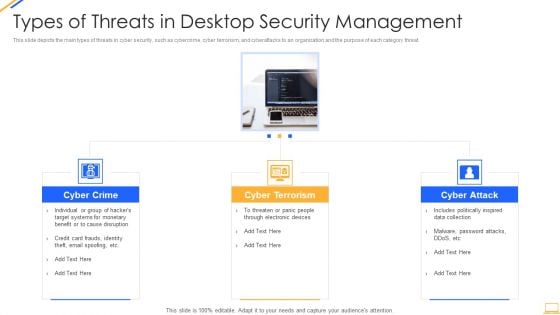
Desktop Security Management Types Of Threats In Desktop Security Management Themes PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting desktop security management types of threats in desktop security management themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like target systems, devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Determine Sequence Phases For Mitigating Cybersecurity Threats And Vulnerabilities Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a determine sequence phases for mitigating cybersecurity threats and vulnerabilities inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Different Kinds Of Insider Information PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a mitigating cybersecurity threats and vulnerabilities different kinds of insider information pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like different kinds of insider digital threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
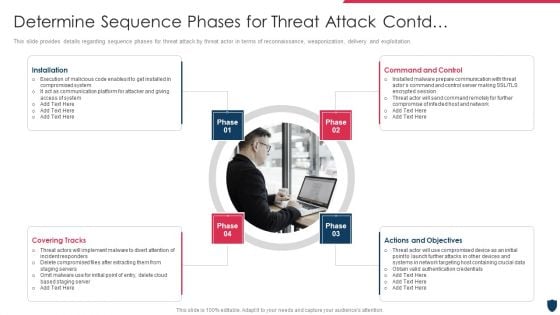
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Contd Control Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber safety incident management determine sequence phases for threat attack contd control inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, covering tracks, actions and objectives, command and control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
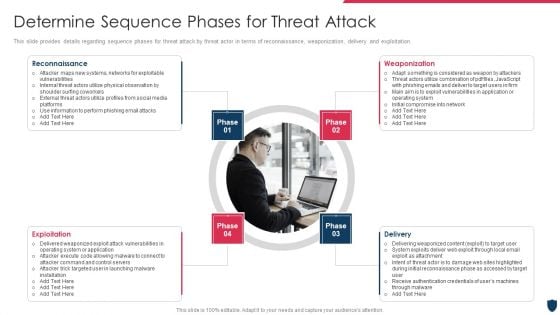
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Rules PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting cyber safety incident management determine sequence phases for threat attack rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, exploitation, delivery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Next Evolution Of SIEM Software Sample PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. This is a real time assessment of security threats next evolution of siem software sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network traffic analysis, endpoint monitoring, threat intelligence, siem foundation, security orchestration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
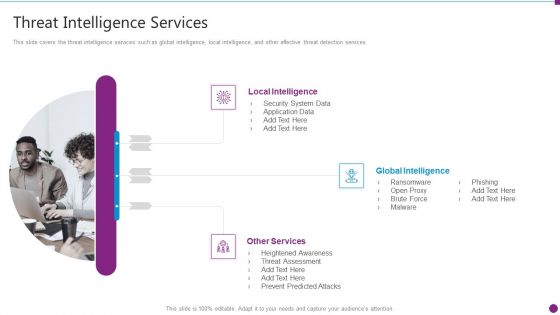
Security Information And Event Management Strategies For Financial Audit And Compliance Threat Intelligence Services Graphics PDF
This slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. Presenting security information and event management strategies for financial audit and compliance threat intelligence services graphics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like local intelligence, global intelligence, other services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Types Of Threats In Information Technology Security Ppt Summary Aids PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting it security types of threats in information technology security ppt summary aids pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
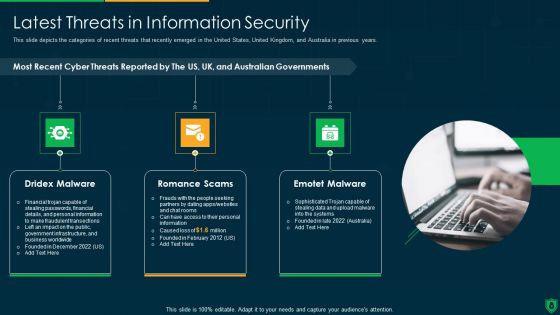
Info Security Latest Threats In Information Security Ppt PowerPoint Presentation Gallery Shapes PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. This is a info security latest threats in information security ppt powerpoint presentation gallery shapes pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like most recent, cyber threats reported, dridex malware, romance scams, emotet malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Security Types Of Threats In Information Security Ppt PowerPoint Presentation Gallery Layout Ideas PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting info security types of threats in information security ppt powerpoint presentation gallery layout ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
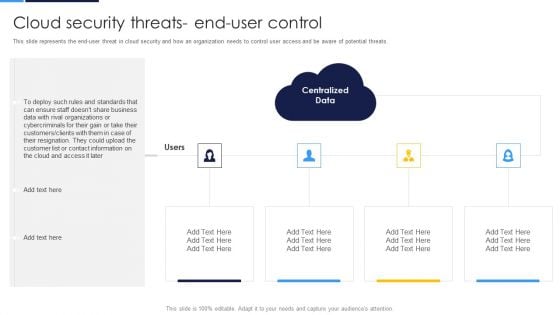
Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF
This slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats.This is a Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Rival Organizations, Cybercriminals, Contact Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing Threats Associated With Apple That Negatively Impacts Business Guidelines PDF
This slide provides information regarding threats of brand that impose negative impact over firms success. Key Apples threats include rigorous competition, lawsuits, pandemic, etc. Find a pre designed and impeccable Addressing Threats Associated With Apple That Negatively Impacts Business Guidelines PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Advanced Cyber Threat Analytics Ppt PowerPoint Presentation Summary Example Cpb Pdf
Presenting this set of slides with name advanced cyber threat analytics ppt powerpoint presentation summary example cpb pdf. This is an editable Powerpoint one stages graphic that deals with topics like advanced cyber threat analytics to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Cyber Security Threat With Hacker Icon On The Screen Ppt PowerPoint Presentation Infographic Template PDF
Persuade your audience using this cyber security threat with hacker icon on the screen ppt powerpoint presentation infographic template pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cyber security threat with hacker icon on the screen. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Internet Security Ransomware Hacking And Data Loss Threat Ppt PowerPoint Presentation File Formats PDF
Persuade your audience using this internet security ransomware hacking and data loss threat ppt powerpoint presentation file formats pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including internet security ransomware hacking and data loss threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Password Protection For Cyber Security Threat Ppt PowerPoint Presentation Icon Show PDF
Persuade your audience using this password protection for cyber security threat ppt powerpoint presentation icon show pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including password protection for cyber security threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Vector Showing Computer Security Threats Ppt PowerPoint Presentation Ideas Introduction PDF
Persuade your audience using this vector showing computer security threats ppt powerpoint presentation ideas introduction pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including vector showing computer security threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Virus On Screen Online Crime Threat From Hacker Vector Icon Ppt PowerPoint Presentation Gallery Smartart PDF
Presenting virus on screen online crime threat from hacker vector icon ppt powerpoint presentation gallery smartart pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including virus on screen online crime threat from hacker vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Network Security Protection Ensuring Safety From Online Threat Ppt PowerPoint Presentation Portfolio Influencers PDF
Persuade your audience using this network security protection ensuring safety from online threat ppt powerpoint presentation portfolio influencers pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including network security protection ensuring safety from online threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Network And Information Threat Safety Vector Icon Ppt PowerPoint Presentation File Example PDF
Persuade your audience using this network and information threat safety vector icon ppt powerpoint presentation file example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including network and information threat safety vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
System Failure With Threat Symbol On Screen Icon Ppt PowerPoint Presentation Gallery Templates PDF
Persuade your audience using this system failure with threat symbol on screen icon ppt powerpoint presentation gallery templates pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including system failure with threat symbol on screen icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Employee Configuring Cloud Technology System For Eliminating Threats Ppt PowerPoint Presentation File Diagrams PDF
Persuade your audience using this employee configuring cloud technology system for eliminating threats ppt powerpoint presentation file diagrams pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including employee configuring cloud technology system for eliminating threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Software Engineer Creating Cloud Computing Structure For Reducing Operational Threats Ppt PowerPoint Presentation File Skills PDF
Persuade your audience using this software engineer creating cloud computing structure for reducing operational threats ppt powerpoint presentation file skills pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including software engineer creating cloud computing structure for reducing operational threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Coder Checking Business Internet Security Threats Ppt PowerPoint Presentation Gallery Model PDF
Persuade your audience using this coder checking business internet security threats ppt powerpoint presentation gallery model pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including coder checking business internet security threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
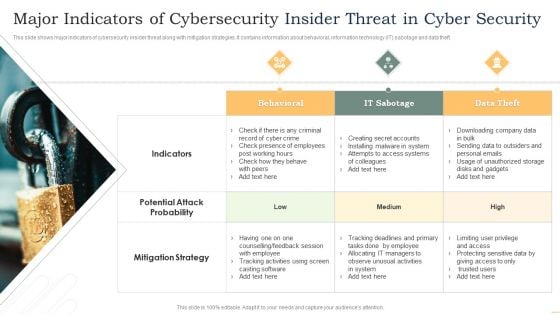
Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF
This slide shows major indicators of cybersecurity insider threat along with mitigation strategies. It contains information about behavioral, information technology IT sabotage and data theft. Presenting Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Behavioral, IT Sabotage, Data Theft. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Threats Management Of Confidential Data Reports Icon Ppt Ideas Summary PDF
Persuade your audience using this Threats Management Of Confidential Data Reports Icon Ppt Ideas Summary PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Threats Management, Confidential Data Reports, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Critical Measures For Ensuring How Firm Handle Various Insider Threats At Workplace Graphics PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Critical Measures For Ensuring How Firm Handle Various Insider Threats At Workplace Graphics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Critical Measures For Ensuring How Firm Handle Various Insider Threats At Workplace Graphics PDF.
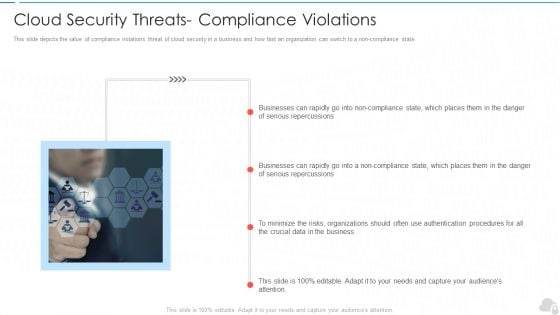
Cloud Security Threats Compliance Violations Cloud Computing Security IT Ppt Layouts Slide Portrait PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non-compliance state. This is a cloud security threats compliance violations cloud computing security it ppt layouts slide portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like businesses, organizations, serious repercussions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Malware Attacks Cloud Computing Security IT Ppt Show Diagrams PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. Presenting cloud security threats malware attacks cloud computing security it ppt show diagrams pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like cloud administrations, cyber criminals, technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
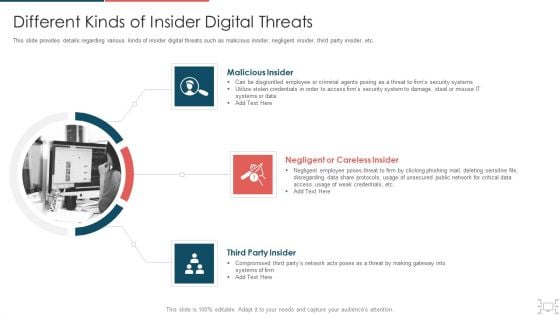
Cyber Security Administration In Organization Different Kinds Of Insider Digital Threats Microsoft PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber security administration in organization different kinds of insider digital threats microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disgruntled, employee, criminal, agents, damage, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Different Kinds Of Insider Digital Threats Download PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber safety incident management different kinds of insider digital threats download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malicious insider, negligent or careless insider, third party insider. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
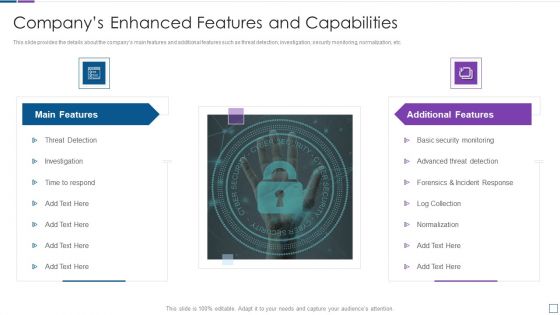
Real Time Assessment Of Security Threats Companys Enhanced Features And Capabilities Introduction PDF
This slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. Presenting real time assessment of security threats companys enhanced features and capabilities introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like main features, additional features. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
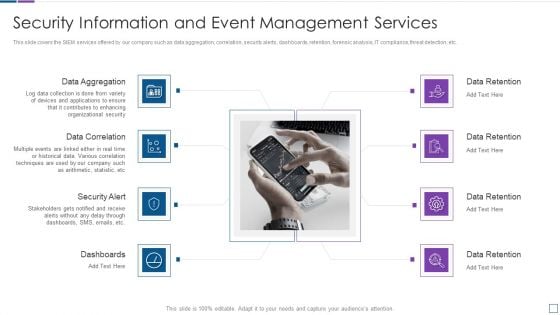
Real Time Assessment Of Security Threats Security Information And Event Management Services Information PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting real time assessment of security threats security information and event management services information pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like data aggregation, data correlation, security alert, dashboards, data retention. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
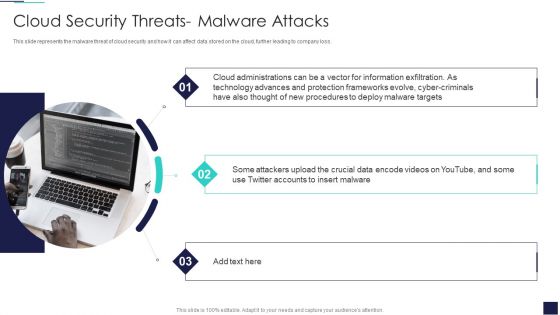
Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. This is a Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Cyber Criminals, Deploy Malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
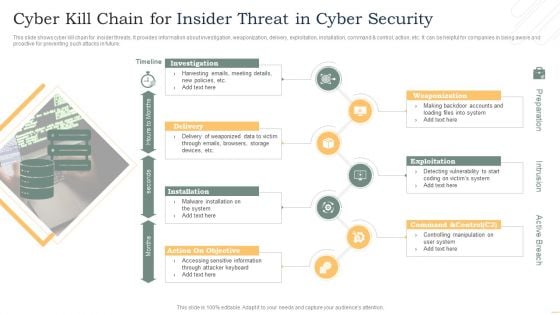
Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF
This slide shows cyber kill chain for insider threats. It provides information about investigation, weaponization, delivery, exploitation, installation, command and control, action, etc. It can be helpful for companies in being aware and proactive for preventing such attacks in future. Presenting Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Investigation, Delivery, Installation, Exploitation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
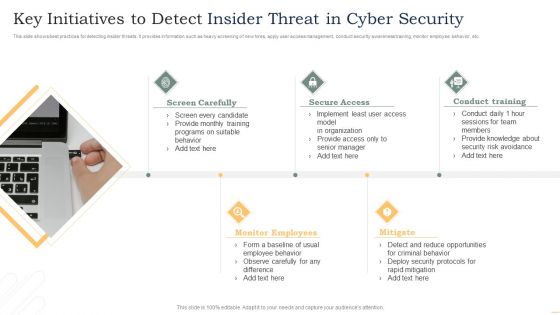
Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF
This slide shows best practices for detecting insider threats. It provides information such as heavy screening of new hires, apply user access management, conduct security awareness training, monitor employee behavior, etc. Presenting Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Screen Carefully, Secure Access, Conduct Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
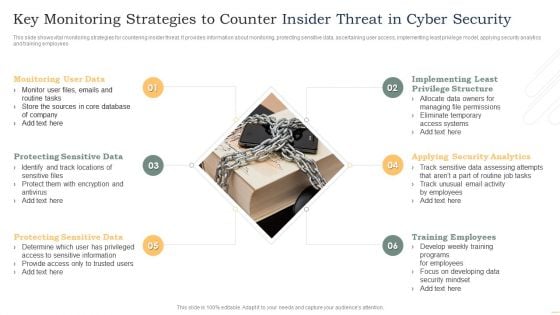
Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF
This slide shows vital monitoring strategies for countering insider threat. It provides information about monitoring, protecting sensitive data, ascertaining user access, implementing least privilege model, applying security analytics and training employees. Persuade your audience using this Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitoring User Data, Protecting Sensitive Data, Protecting Sensitive Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
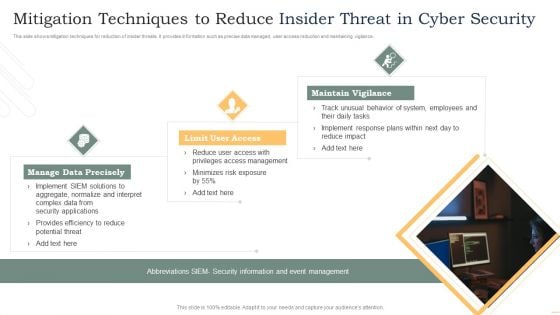
Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
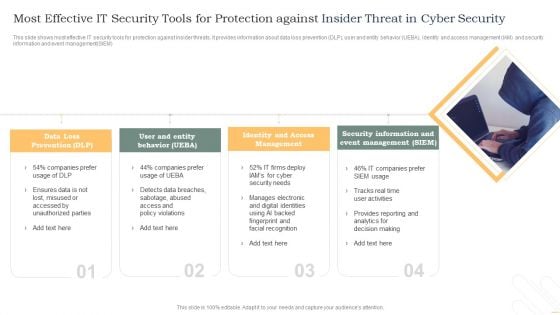
Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Table Of Contents Overview On Mitigating Workplace IT Threats Slides PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Table Of Contents Overview On Mitigating Workplace IT Threats Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Table Of Contents Overview On Mitigating Workplace IT Threats Slides PDF.
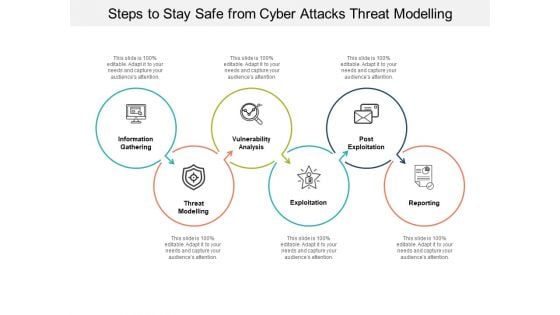
Steps To Stay Safe From Cyber Attacks Threat Modelling Ppt PowerPoint Presentation Infographics Gallery
Presenting this set of slides with name steps to stay safe from cyber attacks threat modelling ppt powerpoint presentation infographics gallery. This is a six stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
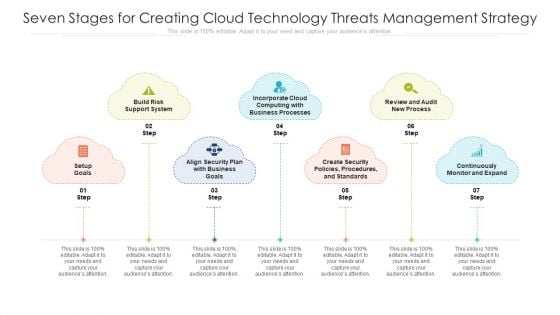
Seven Stages For Creating Cloud Technology Threats Management Strategy Ppt PowerPoint Presentation File Inspiration PDF
Presenting seven stages for creating cloud technology threats management strategy ppt powerpoint presentation file inspiration pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including business goals, security policies, continuously monitor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
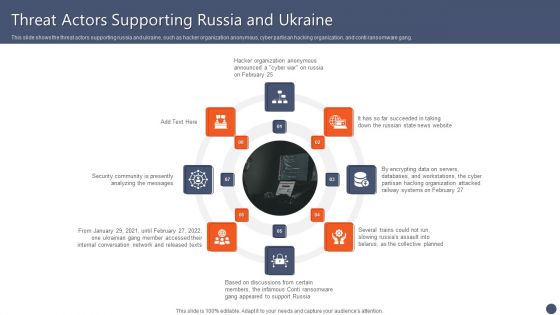
Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF
This slide shows the threat actors supporting russia and ukraine, such as hacker organization anonymous, cyber partisan hacking organization, and conti ransomware gang. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Key Data Threats For School Information Management Systems Ppt PowerPoint Presentation Slides Examples PDF
Presenting key data threats for school information management systems ppt powerpoint presentation slides examples pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including malware, theft and loss, unsafe data, negligence, third party apis application programming interface institutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
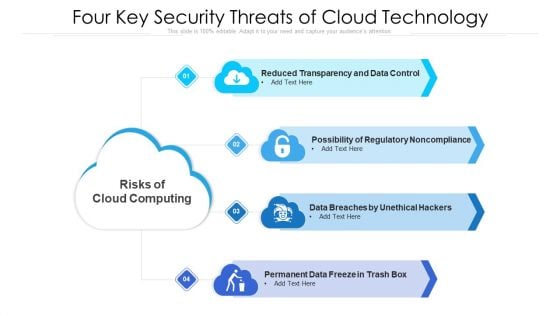
Four Key Security Threats Of Cloud Technology Ppt PowerPoint Presentation Gallery Introduction PDF
Presenting four key security threats of cloud technology ppt powerpoint presentation gallery introduction pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data breaches by unethical hackers, permanent data freeze in trash box, possibility of regulatory noncompliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
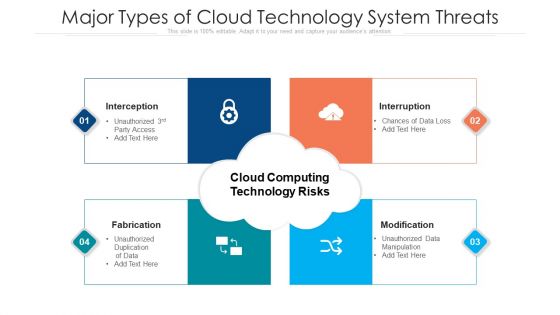
Major Types Of Cloud Technology System Threats Ppt PowerPoint Presentation File Graphic Images PDF
Persuade your audience using this major types of cloud technology system threats ppt powerpoint presentation file graphic images pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including interception, fabrication, interruption. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Solution Evaluation Criteria Assessment And Threat Impact Matrix Table Of Contents Sample PDF
Presenting solution evaluation criteria assessment and threat impact matrix table of contents sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like analysis, management, requirements, organizational. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Handling Cyber Threats Digital Era Security Lifecycle Ppt Summary Brochure PDF
This is a handling cyber threats digital era security lifecycle ppt summary brochure pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security lifecycle. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Safety Initiatives For Effective IT Security Threats Administration Table Of Contents Themes PDF
Presenting data safety initiatives for effective it security threats administration table of contents themes pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like global market insights, gap identification, defining business priorities, about security program, companies digitization levels. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Ready To Eat Food Market Analysis General Mills Threats Graphics PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Ready To Eat Food Market Analysis General Mills Threats Graphics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
How To Intensify Project Threats Issue And Escalation Process Flow Chart Icons PDF
This slide provides the glimpse about the issue and escalation process flowchart which covers various steps involved in this process. Presenting how to intensify project threats issue and escalation process flow chart icons pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like analysis, validation and prioritization, tracking and reporting, escalation, resolution and closure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
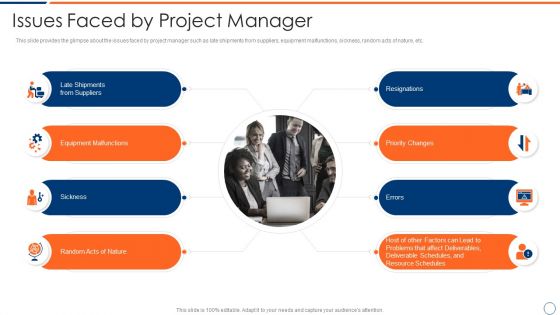
How To Intensify Project Threats Issues Faced By Project Manager Elements PDF
This slide provides the glimpse about the issues faced by project manager such as late shipments from suppliers, equipment malfunctions, sickness, random acts of nature, etc. This is a how to intensify project threats issues faced by project manager elements pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like priority changes, sickness, random acts of nature, equipment malfunctions, resignations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How To Intensify Project Threats Why It Is Difficult To Escalate Mockup PDF
This slide provides the glimpse about the reasons why it is difficult to escalate the issues such as clash creator, fear of backlash, avoiding escalation against experienced members, and deceived perception. This is a how to intensify project threats why it is difficult to escalate mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like clash creator, fear of backlash, avoiding escalation against experienced members, deceived perception. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































