Safety Dashboard

Understanding Security Risk Related Importance Of Unstructured Data Ppt Sample
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Understanding Security Risk Related Importance Of Unstructured Data Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Our Understanding Security Risk Related Importance Of Unstructured Data Ppt Sample are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
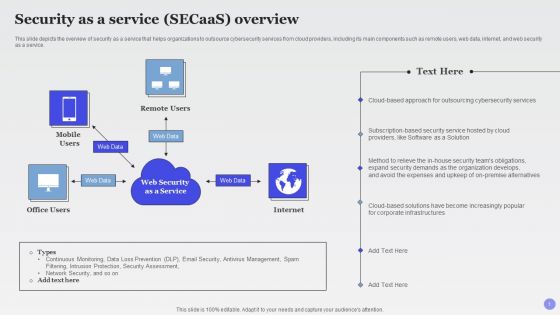
Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF
This slide depicts the overview of security as a service that helps organizations to outsource cybersecurity services from cloud providers, including its main components such as remote users, web data, internet, and web security as a service.Deliver and pitch your topic in the best possible manner with this Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF. Use them to share invaluable insights on Outsourcing Cybersecurity, Software Solution, Expenses Upkeep and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Icon Of Security Computer System Interface For Securing Information Ppt Professional Background PDF
Persuade your audience using this Icon Of Security Computer System Interface For Securing Information Ppt Professional Background PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Icon Security Computer, System Interface Securing, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
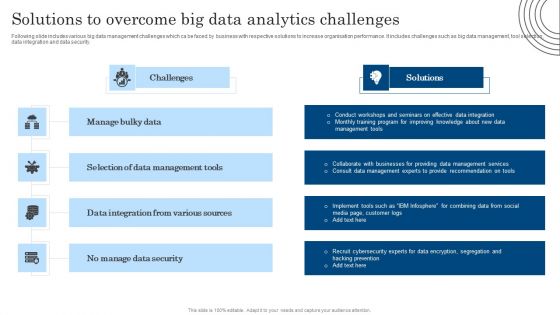
Solutions To Overcome Big Data Analytics Challenges Download PDF
Following slide includes various big data management challenges which ca be faced by business with respective solutions to increase organisation performance. It includes challenges such as big data management, tool selection, data integration and data security. Showcasing this set of slides titled Solutions To Overcome Big Data Analytics Challenges Download PDF. The topics addressed in these templates are Data Management Tools, Data Integration, Various Sources. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
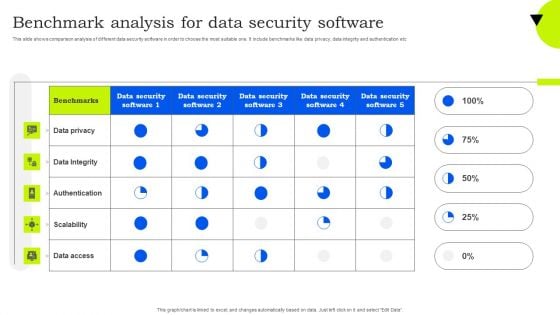
Benchmark Analysis For Data Security Software Mockup PDF
This slide shows comparison analysis of different data security software in order to choose the most suitable one. It include benchmarks like data privacy, data integrity and authentication etc. Showcasing this set of slides titled Benchmark Analysis For Data Security Software Mockup PDF. The topics addressed in these templates are Data Privacy, Data Integrity, Authentication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass or fail rate of employees who received the security awareness training and fail rate by age. Find highly impressive Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Internet Security Kpis And Metrics Ppt PowerPoint Presentation Gallery Outline PDF
Showcasing this set of slides titled internet security kpis and metrics ppt powerpoint presentation gallery outline pdf. The topics addressed in these templates are threat detection, risk and compliance, services compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
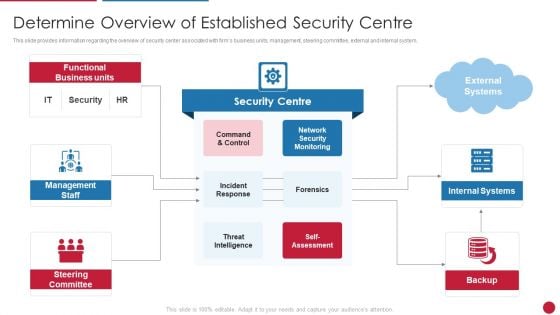
Facilitating IT Intelligence Architecture Determine Overview Of Established Security Centre Introduction PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Facilitating IT Intelligence Architecture Determine Overview Of Established Security Centre Introduction PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security Monitoring, Internal Systems, Steering Committee You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
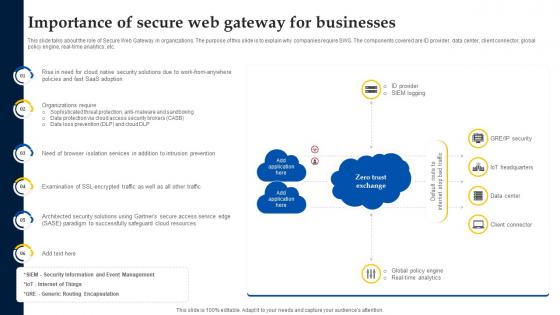
Web Access Control Solution Importance Of Secure Web Gateway For Businesses
This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc. Explore a selection of the finest Web Access Control Solution Importance Of Secure Web Gateway For Businesses here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Web Access Control Solution Importance Of Secure Web Gateway For Businesses to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc.
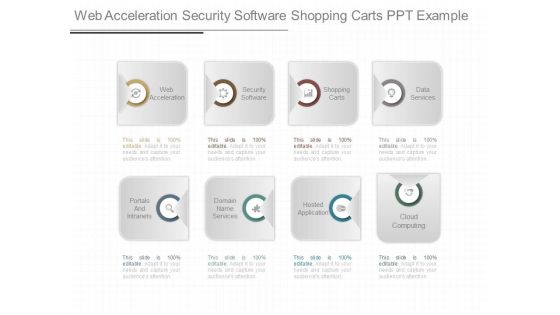
Web Acceleration Security Software Shopping Carts Ppt Example
This is a web acceleration security software shopping carts ppt example. This is a eight stage process. The stages in this process are web acceleration, security software, shopping carts, data services, portals and intranets, domain name services, hosted application, cloud computing.
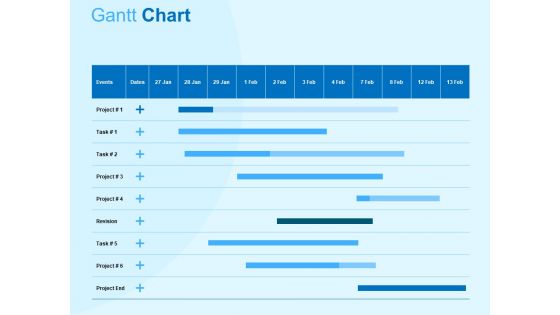
Damage Security Insurance Proposal Gantt Chart Ppt Gallery Graphic Tips PDF
Your complex projects can be managed and organized simultaneously using this detailed damage security insurance proposal gantt chart ppt gallery graphic tips pdf template. Track the milestones, tasks, phases, activities, and subtasks to get an updated visual of your project. Share your planning horizon and release plan with this well crafted presentation template. This exemplary template can be used to plot various dependencies to distinguish the tasks in the pipeline and their impact on the schedules and deadlines of the project. Apart from this, you can also share this visual presentation with your team members and stakeholders. It a resourceful tool that can be incorporated into your business structure. Therefore, download and edit it conveniently to add the data and statistics as per your requirement.
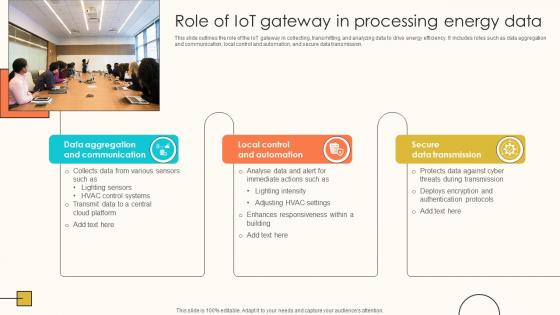
Role Of IoT Gateway In Processing Energy Data Internet Of Things Solutions To Enhance Energy IoT SS V
This slide outlines the role of the IoT gateway in collecting, transmitting, and analyzing data to drive energy efficiency. It includes roles such as data aggregation and communication, local control and automation, and secure data transmission. Do you know about Slidesgeeks Role Of IoT Gateway In Processing Energy Data Internet Of Things Solutions To Enhance Energy IoT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the role of the IoT gateway in collecting, transmitting, and analyzing data to drive energy efficiency. It includes roles such as data aggregation and communication, local control and automation, and secure data transmission.
Stock Photo 3d Blue Folder With Lock For Data Security PowerPoint Slide
This power point image template has been crafted with graphic of 3d blue folder and lock. This image contains the concept of data security. Use this image PPT for your technology and security related presentations.
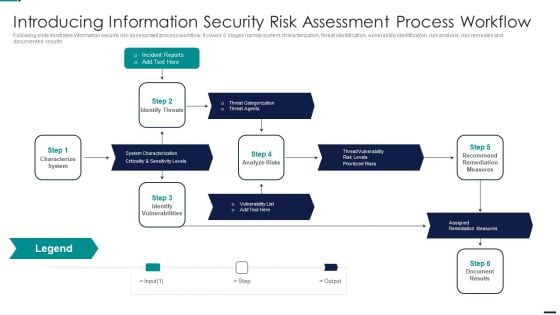
Risk Management Model For Data Introducing Information Security Risk Assessment Process Sample PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. This is a Risk Management Model For Data Introducing Information Security Risk Assessment Process Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incident Reports, Characterize System, Identify Vulnerabilities, Assigned Remediation Measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Information And Event Management Strategies For Financial Audit And Compliance Fully Managed Service Model Portrait PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance fully managed service model portrait pdf. Use them to share invaluable insights on correlation, aggregation, collection, event sources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
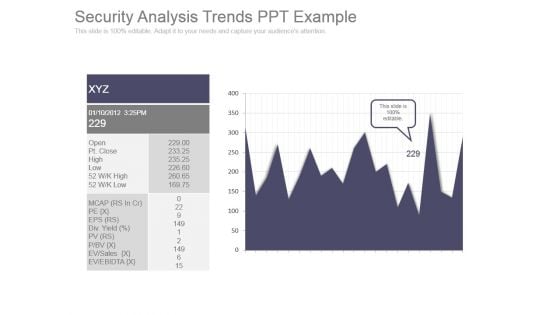
Security Analysis Trends Ppt Example
This is a security analysis trends ppt example. This is a one stage process. The stages in this process are open, pt close, high, low, mcap, pe, eps, div, pv, p bv, ev sales, ev ebidta.

Computer Bug And Cyber Security Vector Illustration Ppt PowerPoint Presentation Portfolio Skills PDF
Presenting this set of slides with name computer bug and cyber security vector illustration ppt powerpoint presentation portfolio skills pdf. This is a three stage process. The stages in this process are computer bug and cyber security vector illustration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Risk Assessment Icon With Magnifying Glass Ppt PowerPoint Presentation File Templates PDF
Presenting this set of slides with name security risk assessment icon with magnifying glass ppt powerpoint presentation file templates pdf. This is a three stage process. The stages in this process are security risk assessment icon with magnifying glass. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Network Security Vs Firewall Ppt PowerPoint Presentation Infographic Template Gridlines Cpb
Presenting this set of slides with name network security vs firewall ppt powerpoint presentation infographic template gridlines cpb. This is an editable Powerpoint five stages graphic that deals with topics like network security vs firewall to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Security Awareness KPI For Tracking Project Impact On Communication Plan Ideas Pdf
This slide showcases KPIs to track security awareness program. This template focuses on evaluating and measuring security awareness in organisation. It includes information related to phishing rates, cost of security breaches, audit hits, etc.Pitch your topic with ease and precision using this Security Awareness KPI For Tracking Project Impact On Communication Plan Ideas Pdf This layout presents information on Program Participation, Security Breaches, Phishing Rate It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases KPIs to track security awareness program. This template focuses on evaluating and measuring security awareness in organisation. It includes information related to phishing rates, cost of security breaches, audit hits, etc.
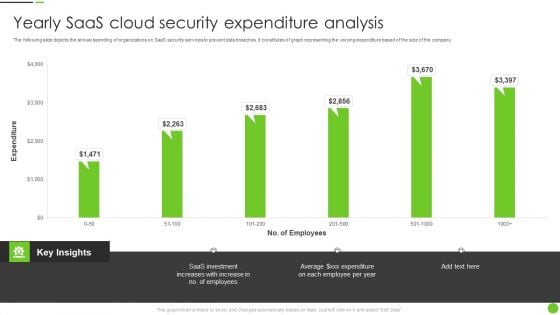
Yearly Saas Cloud Security Expenditure Analysis Ppt PowerPoint Presentation File Deck PDF
The following slide depicts the annual spending of organizations on SaaS security services to prevent data breaches. It constitutes of graph representing the varying expenditure based of the size of the company. Pitch your topic with ease and precision using this Yearly Saas Cloud Security Expenditure Analysis Ppt PowerPoint Presentation File Deck PDF. This layout presents information on Saas Investment, Employees. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Internet Security And Electronic Payment System Ppt Slides
This is a internet security and electronic payment system ppt slides. This is a six stage process. The stages in this process are internet security and electronic payment system, eviction of eco implementation, eco site life cycle, promotion and marketing, net readiness evaluation, eco investment and opportunity.
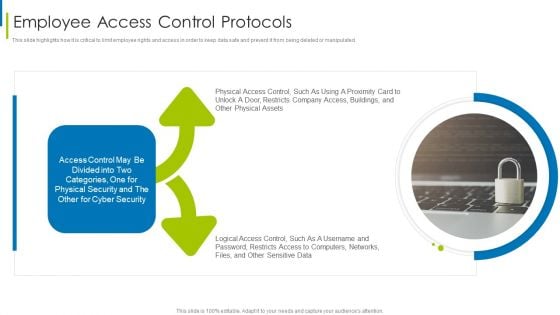
Cyber Terrorism Assault Employee Access Control Protocols Diagrams PDF
This slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated.This is a cyber terrorism assault employee access control protocols diagrams pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Distributed Denial Of Service DDOS As Cyber Terrorism Tool You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
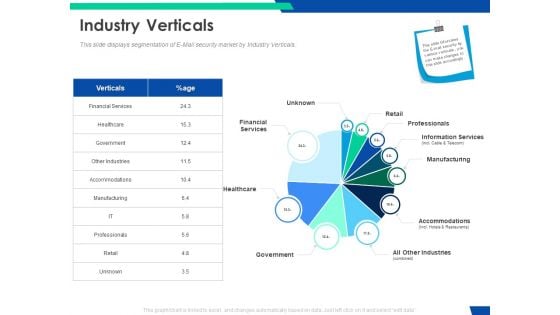
Cloud Based Email Security Market Report Industry Verticals Ppt Layouts Background Designs PDF
This slide displays segmentation of E Mail security market by Industry Verticals. Deliver and pitch your topic in the best possible manner with this cloud based email security market report industry verticals ppt layouts background designs pdf. Use them to share invaluable insights on financial services, retail, professionals, information services, manufacturing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
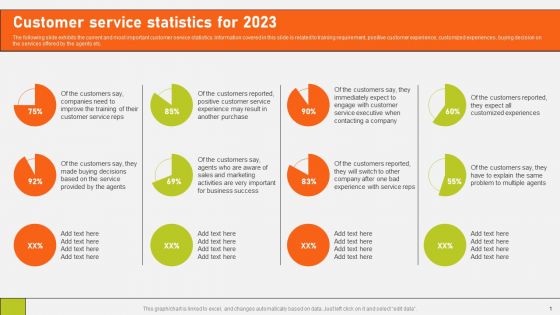
Securing Market Leadership Through Competitive Excellence Customer Service Statistics For 2023 Infographics PDF
The following slide exhibits the current and most important customer service statistics. Information covered in this slide is related to training requirement, positive customer experience, customized experiences, buying decision on the services offered by the agents etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Securing Market Leadership Through Competitive Excellence Customer Service Statistics For 2023 Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
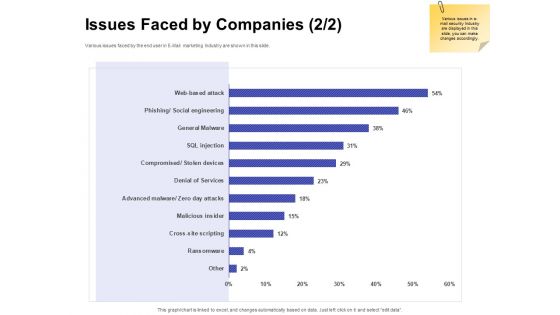
Global Cloud Based Email Security Market Issues Faced By Companies Services Portrait PDF
Presenting this set of slides with name global cloud based email security market issues faced by companies services portrait pdf. The topics discussed in these slides are security for confidential data, protection against malware, protection phishing scams, threat of weak password. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
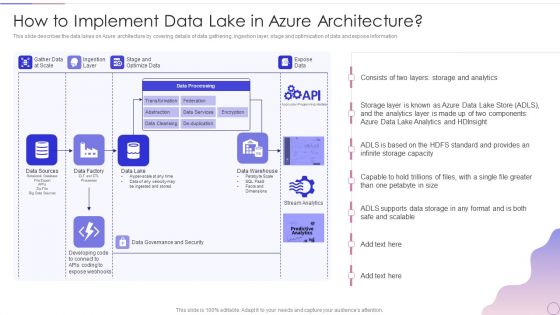
Data Lake Architecture Future Of Data Analysis How To Implement Data Lake In Azure Architecture Slides PDF
This slide describes the data lakes on Azure architecture by covering details of data gathering, ingestion layer, stage and optimization of data and expose information.Deliver an awe inspiring pitch with this creative Data Lake Architecture Future Of Data Analysis How To Implement Data Lake In Azure Architecture Slides PDF bundle. Topics like Data Processing, Storage And Analytics, Governance And Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
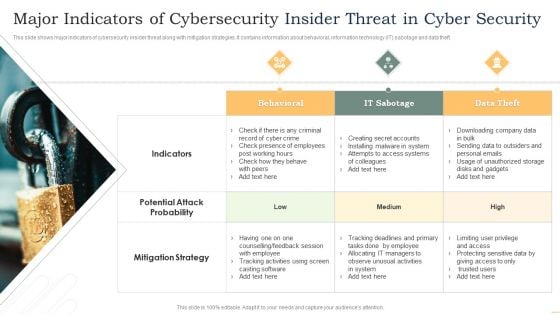
Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF
This slide shows major indicators of cybersecurity insider threat along with mitigation strategies. It contains information about behavioral, information technology IT sabotage and data theft. Presenting Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Behavioral, IT Sabotage, Data Theft. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
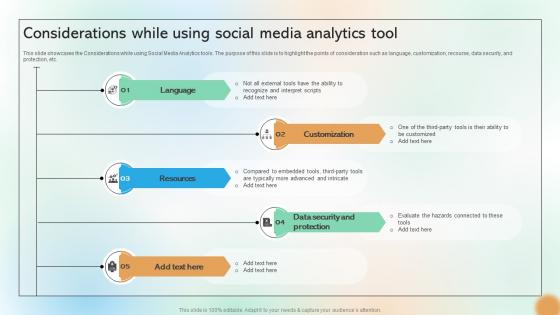
Considerations While Using Social Media Analytics Tool Cracking The Code Of Social Media
This slide showcases the Considerations while using Social Media Analytics tools. The purpose of this slide is to highlight the points of consideration such as language, customization, recourse, data security, and protection, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Considerations While Using Social Media Analytics Tool Cracking The Code Of Social Media will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases the Considerations while using Social Media Analytics tools. The purpose of this slide is to highlight the points of consideration such as language, customization, recourse, data security, and protection, etc.
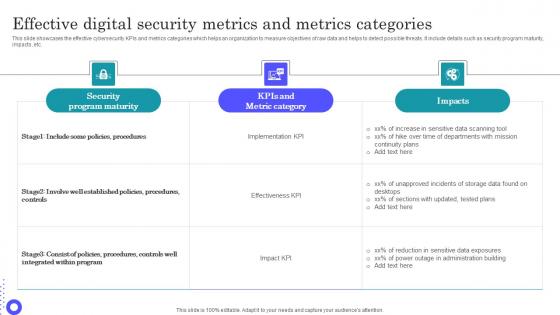
Effective Digital Security Metrics And Metrics Categories Microsoft Pdf
Pitch your topic with ease and precision using this Effective Digital Security Metrics And Metrics Categories Microsoft Pdf This layout presents information on Security Program Maturity, Metric Category, Sensitive Data Scanning It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the effective cybersecurity KPIs and metrics categories which helps an organization to measure objectives of raw data and helps to detect possible threats. It include details such as security program maturity, impacts, etc.

Cloud Information Security What Are The Downsides Of A Cloud Security Ppt Infographics Files PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Presenting Cloud Information Security What Are The Downsides Of A Cloud Security Ppt Infographics Files PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Data Loss, Loss Control, Insider Theft, Data Breaches. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
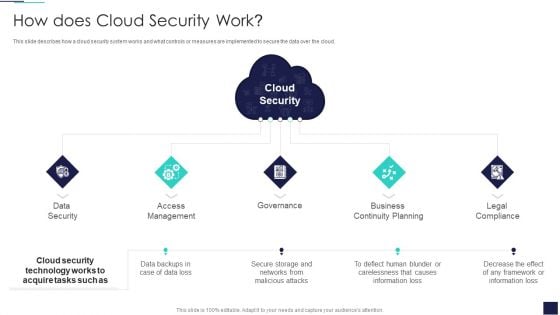
Cloud Information Security How Does Cloud Security Work Ppt Inspiration Graphics PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. This is a Cloud Information Security How Does Cloud Security Work Ppt Inspiration Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Security, Access Management, Legal Compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Integrating Data Privacy System Importance Of Data Privacy Ppt Summary Shapes PDF
This slide illustrates the importance of data privacy in terms of developing trust with customers that value privacy and assisting with data management. This modern and well-arranged Integrating Data Privacy System Importance Of Data Privacy Ppt Summary Shapes PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
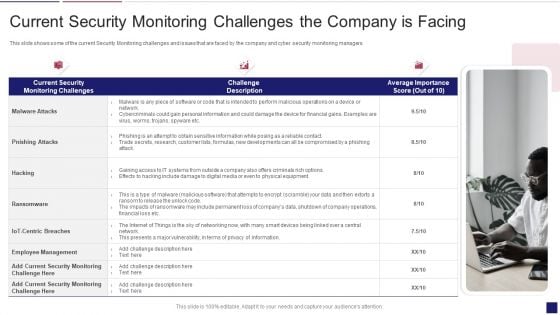
Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Security Monitoring Infographics PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks current security monitoring infographics pdf bundle. Topics like monitoring, service, parameters can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
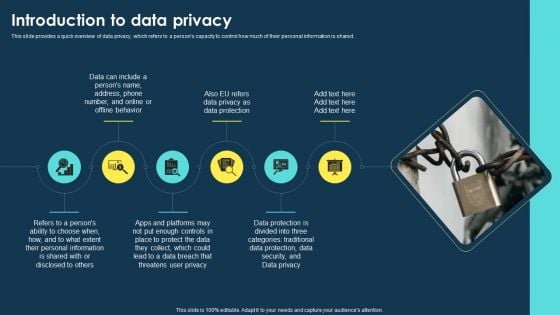
Integrating Data Privacy System Introduction To Data Privacy Ppt Ideas Outline PDF
This slide provides a quick overview of data privacy, which refers to a persons capacity to control how much of their personal information is shared. This Integrating Data Privacy System Introduction To Data Privacy Ppt Ideas Outline PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Integrating Data Privacy System Introduction To Data Privacy Ppt Ideas Outline PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
Saas Application Cloud Security Infrastructure Icon Ppt PowerPoint Presentation Gallery Introduction PDF
Persuade your audience using this Saas Application Cloud Security Infrastructure Icon Ppt PowerPoint Presentation Gallery Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Saas Application, Cloud Security, Infrastructure Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Managing Cyber Security Incident Response Icon Ppt Portfolio Model PDF
Persuade your audience using this IT Managing Cyber Security Incident Response Icon Ppt Portfolio Model PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including IT Managing, Cyber Security, Incident Response, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Information Security Why Cloud Security Is Important Ppt Diagrams PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. This is a Cloud Information Security Why Cloud Security Is Important Ppt Diagrams PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cost Effective, Diminished Administration, Centralized Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Computing Services Disadvantages Of Iaas Cloud Computing Layer Introduction PDF
This slide shows the disadvantages of the IaaS cloud computing layer based on security, maintenance and upgrade, and interoperability issues. This is a Cloud Computing Services Disadvantages Of Iaas Cloud Computing Layer Introduction PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Maintenance And Upgrade, Security, Interoperability Issues. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digital Security Metrics Used By Threat Analysts Graphics Pdf
Showcasing this set of slides titled Digital Security Metrics Used By Threat Analysts Graphics Pdf The topics addressed in these templates are Regulatory Requirements, Large Increase, Scanning Outweighs All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the cybersecurity KPIs used by threat analysts which helps an organization to drive strategic decision making particularly in regard to long term objectives. It include details such as cost per incident, uptime, regulatory requirements, etc.

Data Interpretation And Analysis Playbook Business Intelligence And Predictive Analytics Challenges Template PDF
This template covers the problems while implementing BI and predictive analytics in the organization. The challenges are undefined KPIs and metrics, and unable to hire right data science talent. Presenting data interpretation and analysis playbook business intelligence and predictive analytics challenges template pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like security vulnerabilities, operationalizing, perform analysis, deployed. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
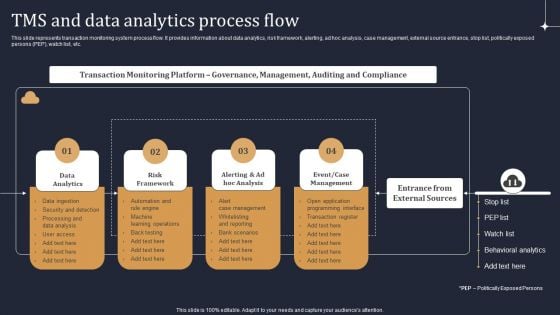
KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF
This slide represents transaction monitoring system process flow. It provides information about data analytics, risk framework, alerting, ad hoc analysis, case management, external source entrance, stop list, politically exposed persons PEP, watch list, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
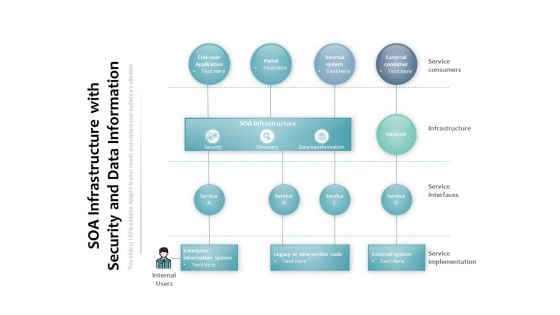
SOA Infrastructure With Security And Data Information Ppt PowerPoint Presentation Pictures Images
Presenting this set of slides with name soa infrastructure with security and data information ppt powerpoint presentation pictures images. The topics discussed in these slides are soa infrastructure, enterprise information system, external consumer, service consumers, infrastructure, service interfaces, service implementation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
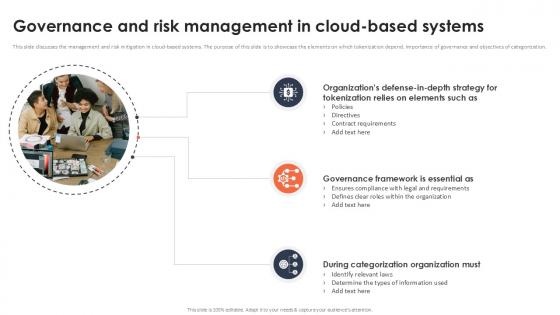
Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example
This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. This modern and well-arranged Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization.

Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Presenting Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Regulations Transparency, Standards Policies, Requirements Governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Green Computing Improving Security By Green Computing Technology
This slide outlineshow green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. The Green Computing Improving Security By Green Computing Technology is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide outlineshow green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.

Civil Infrastructure Designing Services Management 4 Dimensions Of Infrastructure Security Slides PDF
Deliver an awe inspiring pitch with this creative civil infrastructure designing services management 4 dimensions of infrastructure security slides pdf bundle. Topics like applications, data, infrastructure, outsources, employees can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
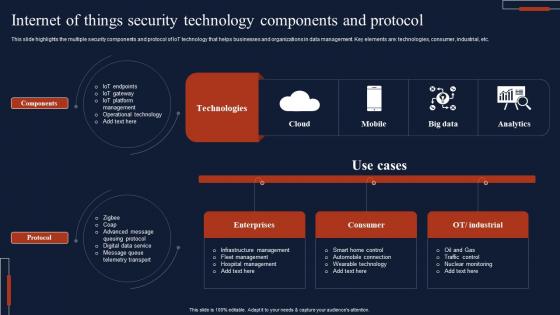
Internet Of Things Security Technology Components And Protocol Rules Pdf
This slide highlights the multiple security components and protocol of IoT technology that helps businesses and organizations in data management. Key elements are technologies, consumer, industrial, etc. Pitch your topic with ease and precision using this Internet Of Things Security Technology Components And Protocol Rules Pdf This layout presents information on Components, Protocol, Technologies, Consumer It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights the multiple security components and protocol of IoT technology that helps businesses and organizations in data management. Key elements are technologies, consumer, industrial, etc.
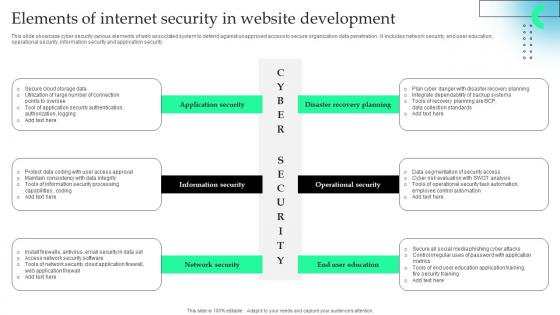
Elements Of Internet Security In Website Development Formats Pdf
This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.Pitch your topic with ease and precision using this Elements Of Internet Security In Website Development Formats Pdf This layout presents information on Information Security, Network Security, Operational Security It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.
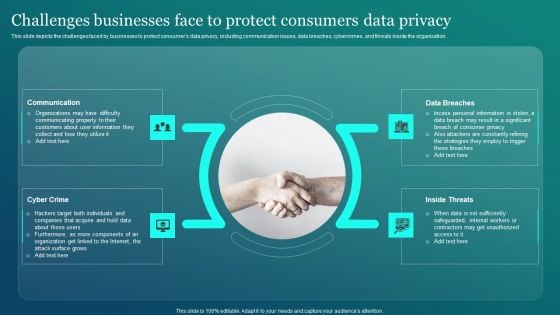
Information Security Challenges Businesses Face To Protect Consumers Data Privacy Professional PDF
This slide depicts the challenges faced by businesses to protect consumers data privacy, including communication issues, data breaches, cybercrimes, and threats inside the organization. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Security Challenges Businesses Face To Protect Consumers Data Privacy Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Sustainable Improving Security By Green Computing Technology
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Create an editable Sustainable Improving Security By Green Computing Technology that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Sustainable Improving Security By Green Computing Technology is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.
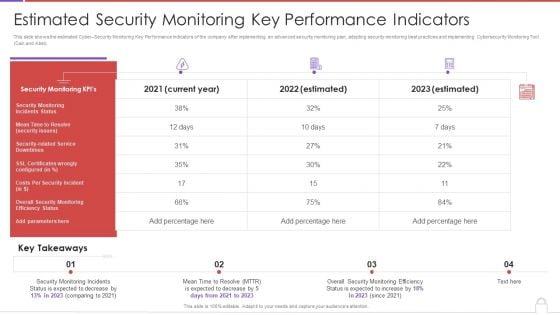
Methods To Develop Advanced Estimated Security Monitoring Key Performance Indicators Structure PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver an awe inspiring pitch with this creative methods to develop advanced estimated security monitoring key performance indicators structure pdf bundle. Topics like security monitoring kpis, costs per security incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
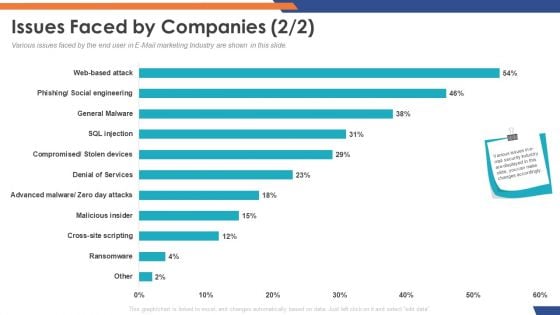
Email Security Market Research Report Issues Faced By Companies Cross Site Download PDF
Presenting this set of slides with name email security market research report issues faced by companies cross site download pdf. The topics discussed in these slides are general malware, social engineering, cross site scripting, denial of service, web based attack. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
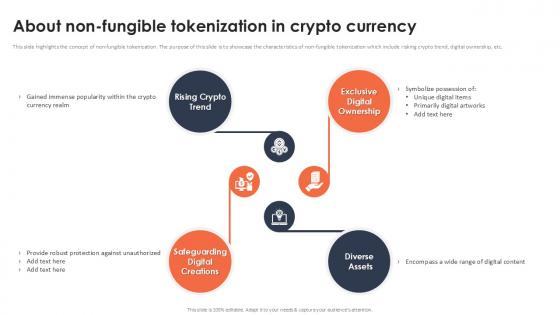
About Non Fungible Tokenization In Crypto Currency Securing Your Data Ppt Slide
This slide highlights the concept of non-fungible tokenization. The purpose of this slide is to showcase the characteristics of non-fungible tokenization which include risking crypto trend, digital ownership, etc. Boost your pitch with our creative About Non Fungible Tokenization In Crypto Currency Securing Your Data Ppt Slide Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the concept of non-fungible tokenization. The purpose of this slide is to showcase the characteristics of non-fungible tokenization which include risking crypto trend, digital ownership, etc.
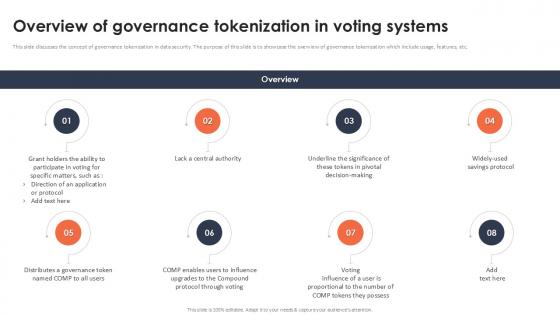
Overview Of Governance Tokenization In Voting Systems Securing Your Data Ppt Powerpoint
This slide discusses the concept of governance tokenization in data security. The purpose of this slide is to showcase the overview of governance tokenization which include usage, features, etc. Presenting this PowerPoint presentation, titled Overview Of Governance Tokenization In Voting Systems Securing Your Data Ppt Powerpoint with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Overview Of Governance Tokenization In Voting Systems Securing Your Data Ppt Powerpoint Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Overview Of Governance Tokenization In Voting Systems Securing Your Data Ppt Powerpoint that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide discusses the concept of governance tokenization in data security. The purpose of this slide is to showcase the overview of governance tokenization which include usage, features, etc.
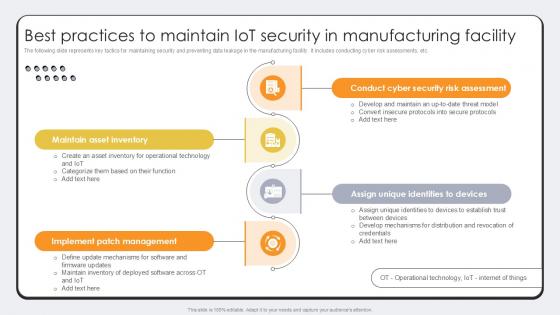
Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. There are so many reasons you need a Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc.
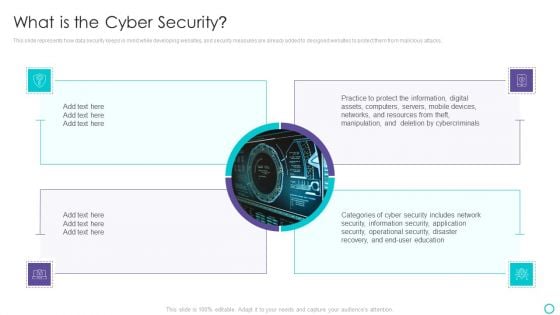
Website Designing And Development Service What Is The Cyber Security Diagrams PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Website Designing And Development Service What Is The Cyber Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Practice To Protect, Information Digital, Operational Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
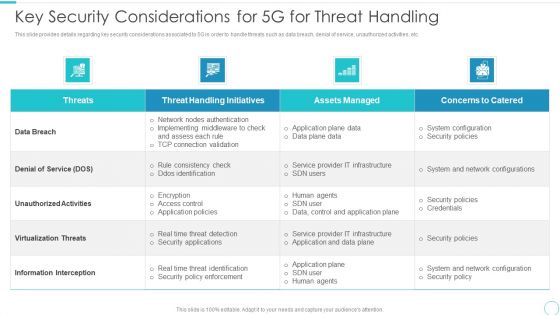
5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this 5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF Use them to share invaluable insights on Concerns To Catered, Handling Initiatives, Implementing Middleware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Need For Cyber Security Awareness Training Ppt Gallery Template PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Welcome to our selection of the Need For Cyber Security Awareness Training Ppt Gallery Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
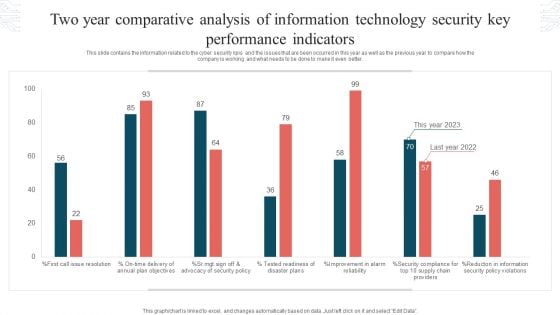
Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF
This slide contains the information related to the cyber security kpis and the issues that are been occurred in this year as well as the previous year to compare how the company is working and what needs to be done to make it even better. Showcasing this set of slides titled Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF. The topics addressed in these templates are Tested Readiness, Disaster Plans, Security Policy Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































