Safety Dashboard
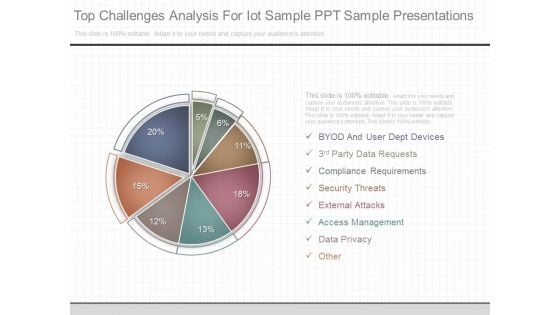
Top Challenges Analysis For Iot Sample Ppt Sample Presentations
This is a top challenges analysis for iot sample ppt sample presentations. This is a eight stage process. The stages in this process are byod and user dept devices, 3rd party data requests, compliance requirements, security threats, external attacks, access management, data privacy, other.
Analyzing Impact Of Blockchain Iot On Major Kpis Icons PDF
This slide showcases impact analysis of blockchain internet of things IoT on key performance indicators KPIs. It provides information about efficiency, security, risk, costs, business models, revenue resources, etc. Deliver an awe inspiring pitch with this creative Analyzing Impact Of Blockchain Iot On Major Kpis Icons PDF bundle. Topics like Blockchain Integration, Business Model, Revenue Sources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
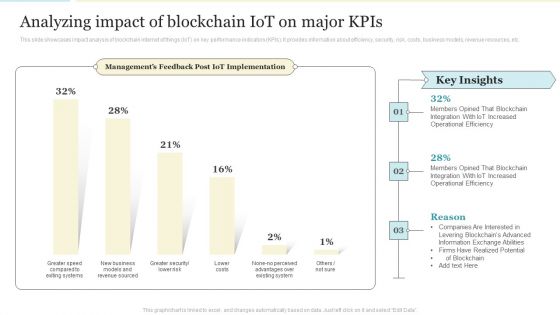
Analyzing Impact Of Blockchain Iot On Major Kpis Formats PDF
This slide showcases impact analysis of blockchain internet of things IoT on key performance indicators KPIs. It provides information about efficiency, security, risk, costs, business models, revenue resources, etc. Deliver an awe inspiring pitch with this creative Analyzing Impact Of Blockchain Iot On Major Kpis Formats PDF bundle. Topics like Operational Efficiency, Information, Existing System can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
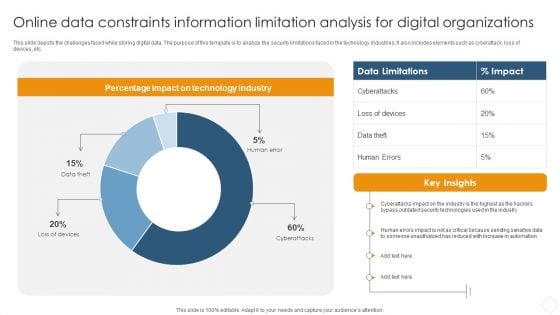
Online Data Constraints Information Limitation Analysis For Digital Organizations Information PDF
This slide depicts the challenges faced while storing digital data. The purpose of this template is to analyze the security limitations faced in the technology industries. It also includes elements such as cyberattack, loss of devices, etc.Pitch your topic with ease and precision using this Online Data Constraints Information Limitation Analysis For Digital Organizations Information PDF. This layout presents information on Percentage Impact, Technology Industry, Security Technologies. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
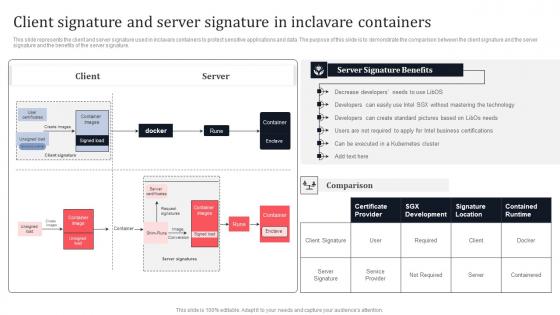
Client Signature And Server Signature In Inclavare Containers Secure Multi Party Mockup Pdf
This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. Want to ace your presentation in front of a live audience Our Client Signature And Server Signature In Inclavare Containers Secure Multi Party Mockup Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature.

Key Strategies For Data Protection And Privacy Rules PDF
The following slide showcases some techniques to ensure data security and privacy. It includes elements such as authentication, data encryption, network security, access controls etc. Persuade your audience using this Key Strategies For Data Protection And Privacy Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authentication, Data Encryption, Network Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Topics That Fall Under The Umbrella Of Cloud Security Cloud Computing Security IT Ppt Model Example Introduction PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. Presenting topics that fall under the umbrella of cloud security cloud computing security it ppt model example introduction pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like data centre security, threat prevention, access control, threat detection, threat mitigation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

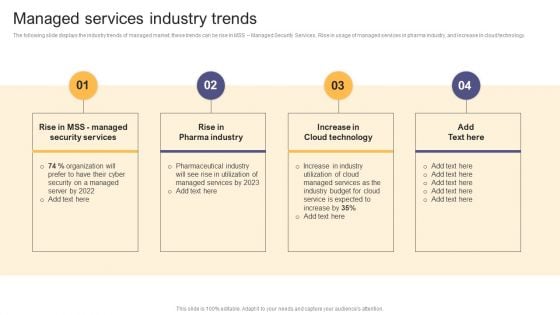
A LA Carte Business Strategy Managed Services Industry Trends Pictures PDF
The following slide displays the industry trends of managed market, these trends can be rise in MSS Managed Security Services, Rise in usage of managed services in pharma industry, and increase in cloud technology. Create an editable A LA Carte Business Strategy Managed Services Industry Trends Pictures PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. A LA Carte Business Strategy Managed Services Industry Trends Pictures PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Per Device Pricing Strategy For Managed Solutions Managed Services Industry Trends Mockup PDF
The following slide displays the industry trends of managed market, these trends can be rise in MSS Managed Security Services, Rise in usage of managed services in pharma industry, and increase in cloud technology. Are you searching for a Per Device Pricing Strategy For Managed Solutions Managed Services Industry Trends Mockup PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Per Device Pricing Strategy For Managed Solutions Managed Services Industry Trends Mockup PDF from Slidegeeks today.
Data Security Protection Ppt PowerPoint Presentation Icon Graphics Download Cpb
Presenting this set of slides with name data security protection ppt powerpoint presentation icon graphics download cpb. This is an editable Powerpoint three stages graphic that deals with topics like data security protection to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Data Security Strategy Ppt PowerPoint Presentation Portfolio Infographic Template Cpb
Presenting this set of slides with name data security strategy ppt powerpoint presentation portfolio infographic template cpb. This is an editable Powerpoint three stages graphic that deals with topics like data security strategy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Big Data Security Ppt PowerPoint Presentation Model Example Cpb
Presenting this set of slides with name big data security ppt powerpoint presentation model example cpb. This is an editable Powerpoint six stages graphic that deals with topics like big data security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Data Security Statistics Ppt PowerPoint Presentation Infographic Template Cpb
Presenting this set of slides with name data security statistics ppt powerpoint presentation infographic template cpb. This is an editable Powerpoint three stages graphic that deals with topics like data security statistics to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Secure Data Access Ppt PowerPoint Presentation Inspiration Guidelines Cpb
Presenting this set of slides with name secure data access ppt powerpoint presentation inspiration guidelines cpb. This is an editable Powerpoint four stages graphic that deals with topics like secure data access to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Data Protection Security Controls Ppt PowerPoint Presentation Layouts Shapes Cpb
Presenting this set of slides with name data protection security controls ppt powerpoint presentation layouts shapes cpb. This is an editable Powerpoint four stages graphic that deals with topics like data protection security controls to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Financial Data Security Ppt PowerPoint Presentation Model Master Slide Cpb
Presenting this set of slides with name financial data security ppt powerpoint presentation model master slide cpb. This is an editable Powerpoint five stages graphic that deals with topics like financial data security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Mobile Data Security Ppt PowerPoint Presentation Model Slides Cpb
Presenting this set of slides with name mobile data security ppt powerpoint presentation model slides cpb. This is an editable Powerpoint three stages graphic that deals with topics like mobile data security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Data Security Privacy Ppt PowerPoint Presentation Icon Deck Cpb
Presenting this set of slides with name data security privacy ppt powerpoint presentation icon deck cpb. This is an editable Powerpoint six stages graphic that deals with topics like data security privacy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Medical Data Security Ppt PowerPoint Presentation Infographic Template Cpb
Presenting this set of slides with name medical data security ppt powerpoint presentation infographic template cpb. This is an editable Powerpoint two stages graphic that deals with topics like medical data security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
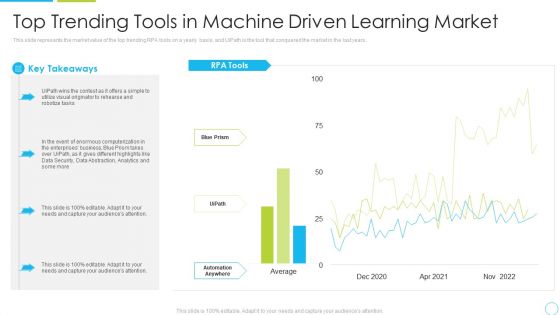
Top Trending Tools In Machine Driven Learning Market Ppt Pictures Example PDF
This slide represents the market value of the top trending RPA tools on a yearly basis, and UiPath is the tool that conquered the market in the last years. Deliver an awe inspiring pitch with this creative top trending tools in machine driven learning market ppt pictures example pdf bundle. Topics like analytics, enterprises, data security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Online Settlement Revolution Payment Security And Fraud Management Solutions Analysis Ppt Slides File Formats PDF
From prevention to detection and resolution, Data Fraud Management solutions allow you to leverage proven technologies to create customized strategies that help limit losses while maintaining a high level of customer satisfaction. Presenting online settlement revolution payment security and fraud management solutions analysis ppt slides file formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like before the payment, on the payment page, after the payment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF
The Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
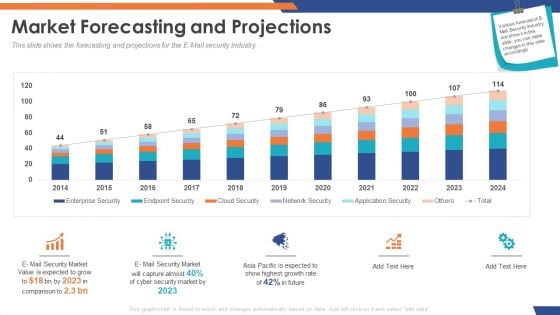
Email Security Market Research Report Market Forecasting And Projections Infographics PDF
Presenting this set of slides with name email security market research report market forecasting and projections infographics pdf. The topics discussed in these slides are network security, cloud security, endpoint security, enterprise security, application security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Impact Of Network Marketing Software On Direct Selling Business Multi Level Marketing Slides Pdf
This slide represents key impacts of network marketing on business growth. It covers benefits such as high productivity, multi level security, business growth opportunity and salesforce motivation. The Impact Of Network Marketing Software On Direct Selling Business Multi Level Marketing Slides Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents key impacts of network marketing on business growth. It covers benefits such as high productivity, multi level security, business growth opportunity and salesforce motivation.
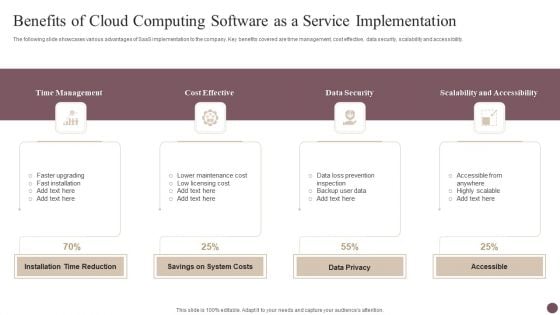
Benefits Of Cloud Computing Software As A Service Implementation Slides PDF
The following slide showcases various advantages of SaaS implementation to the company. Key benefits covered are time management, cost effective, data security, scalability and accessibility. Presenting Benefits Of Cloud Computing Software As A Service Implementation Slides PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Time Management, Cost Effective, Data Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Slidegeeks has constructed Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
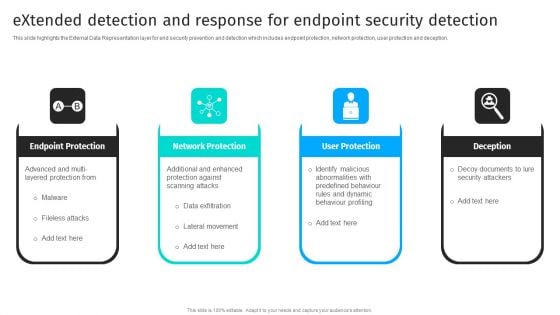
Extended Detection And Response For Endpoint Security Detection Information PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception.There are so many reasons you need a Extended Detection And Response For Endpoint Security Detection Information PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Dollars With Lock And Chain Money Investment PowerPoint Templates And PowerPoint Themes 1012
Dollars With Lock And Chain Money Investment PowerPoint Templates And PowerPoint Themes 1012-Create dynamic Microsoft office PPT Presentations with our professional templates containing a graphic of dollars with lock and chain. This image signifies the concept of data security and money investment. This image has been conceived to enable you to emphatically communicate your ideas in your Business and Financial PPT presentations on finance, protection and banking. Our PPT images are so perfectly designed that it reveals the very basis of our PPT template to make your clients understand.-Dollars With Lock And Chain Money Investment PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Dollars chained and locked, business, security, finance, money, chains Buzz the right word with our Dollars With Lock And Chain Money Investment PowerPoint Templates And PowerPoint Themes 1012. You will come out on top.
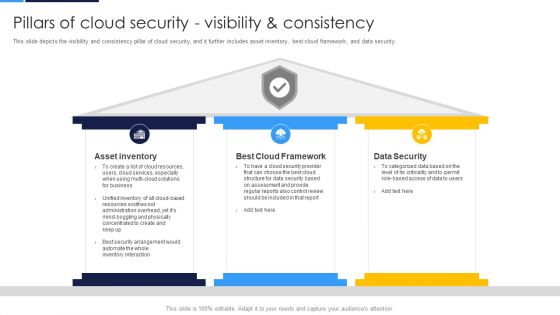
Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF
This slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security.Presenting Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Asset Inventory, Cloud Framework, Data Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
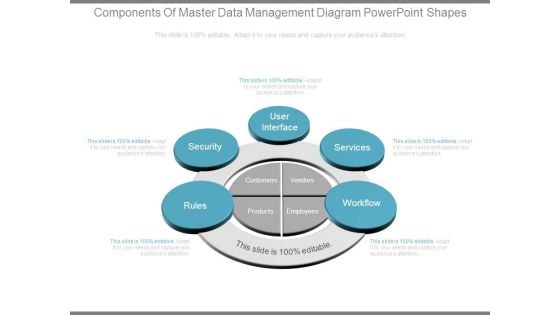
Components Of Master Data Management Diagram Powerpoint Shapes
This is a components of master data management diagram powerpoint shapes. This is a five stage process. The stages in this process are rules, security, user interface, services, workflow, customers, vendors, products, employees.

Various Data Mining Challenges With Solutions To Overcome Summary PDF
Following slide showcases data mining challenges such as noisy and incomplete data, data privacy and security and interpretation challenges. This slide also provide information about the various solutions that can assist company in overcoming those challenges.Showcasing this set of slides titled Various Data Mining Challenges With Solutions To Overcome Summary PDF The topics addressed in these templates are Incomplete Data, Data Privacy, Mining Interpretation All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
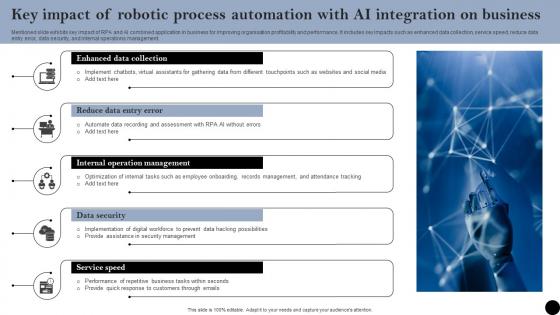
Key Impact Of Robotic Process Automation With AI Integration On Business Infographics Pdf
Mentioned slide exhibits key impact of RPA and AI combined application in business for improving organisation profitability and performance. It includes key impacts such as enhanced data collection, service speed, reduce data entry error, data security, and internal operations management. Showcasing this set of slides titled Key Impact Of Robotic Process Automation With AI Integration On Business Infographics Pdf. The topics addressed in these templates are Reduce Data Entry, Data Security, Internal Operations Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Mentioned slide exhibits key impact of RPA and AI combined application in business for improving organisation profitability and performance. It includes key impacts such as enhanced data collection, service speed, reduce data entry error, data security, and internal operations management.

Information Security Storage Limitation Principle Of GDPR Law Designs PDF
This slide conveys the GDPR laws storage limitation principle, which prohibits you from holding personal data for longer than is required and requires you to justify your reasons for maintaining data. Get a simple yet stunning designed Information Security Storage Limitation Principle Of GDPR Law Designs PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Security Storage Limitation Principle Of GDPR Law Designs PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
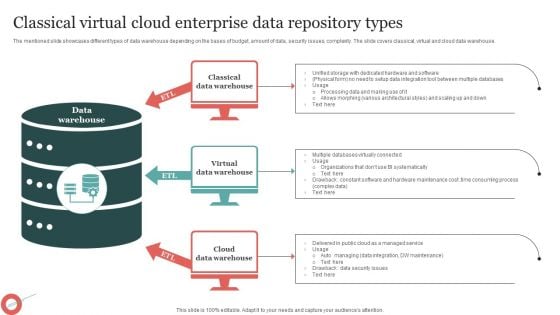
Classical Virtual Cloud Enterprise Data Repository Types Microsoft PDF
The mentioned slide showcases different types of data warehouse depending on the bases of budget, amount of data, security issues, complexity. The slide covers classical, virtual and cloud data warehouse. Pitch your topic with ease and precision using this Classical Virtual Cloud Enterprise Data Repository Types Microsoft PDF. This layout presents information on Data Warehouse, Virtual, Cloud. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Operational Outlook Of Security Awareness Training Software Icons PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Deliver an awe inspiring pitch with this creative Operational Outlook Of Security Awareness Training Software Icons PDF bundle. Topics like Educate Employees, Dynamic Training, Customized Content can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Implementing Cybersecurity Awareness Program To Prevent Attacks Cyber Security Awareness Trends Download PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2023. Increase malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Cybersecurity Awareness Program To Prevent Attacks Cyber Security Awareness Trends Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
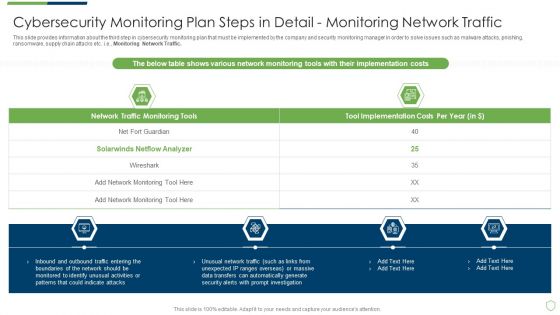
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps Elements PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps elements pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail review and risk analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
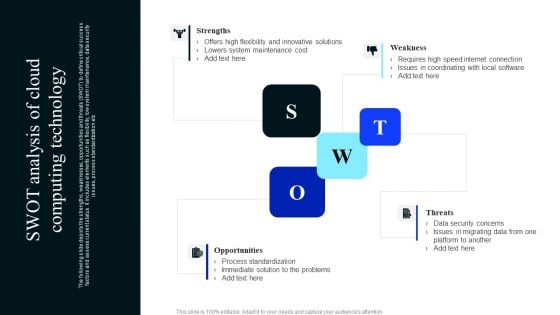
SWOT Analysis Of Cloud Computing Technology Download PDF
The following slide depicts the strengths, weaknesses, opportunities and threats SWOT to define critical success factors and assess current status. It includes elements such as flexibility, low system maintenance, data security issues, process standardization etc. Presenting SWOT Analysis Of Cloud Computing Technology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strengths, Weakness, Threats, Opportunities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
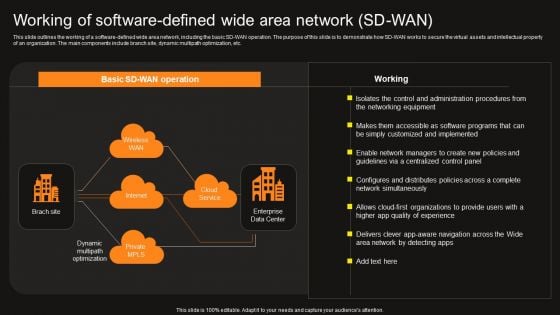
Virtual WAN Architecture Working Of Software Defined Wide Area Network SD WAN Elements PDF
This slide outlines the working of a software-defined wide area network, including the basic sd wan operation. the purpose of this slide is to demonstrate how sd wan works to secure the virtual assets and intellectual property of an organization the main components include branch site, dynamic multipath optimization, etc. There are so many reasons you need a Virtual WAN Architecture Working Of Software Defined Wide Area Network SD WAN Elements PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Common Drawbacks Of Electronic Data Interchange Document Transport Icons PDF
This slide provides glimpse about key challenges of using Electronic Data Interchange EDI system. It includes drawbacks such as for a complex B2B network, growing electronic data interchange volumes, etc.Showcasing this set of slides titled Common Drawbacks Of Electronic Data Interchange Document Transport Icons PDF. The topics addressed in these templates are More Transparency, Security Concerns, Skyrocketing Costs. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Organizing Security Awareness Operational Outlook Of Security Awareness Training Ideas PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Retrieve professionally designed Organizing Security Awareness Operational Outlook Of Security Awareness Training Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
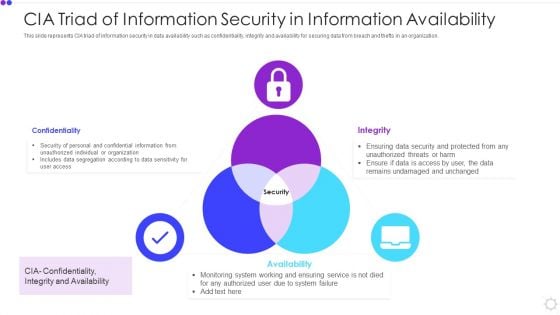
Cia Triad Of Information Security In Information Availability Microsoft PDF
This slide represents CIA triad of information security in data availability such as confidentiality, integrity and availability for securing data from breach and thefts in an organization. Presenting cia triad of information security in information availability microsoft pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including confidentiality, integrity, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

ITIL Strategy Service Excellence What Services Do We Offer To Clients Ppt PowerPoint Presentation Pictures Structure PDF
Presenting this set of slides with name itil strategy service excellence what services do we offer to clients ppt powerpoint presentation pictures structure pdf. The topics discussed in these slides are core offerings, server monitoring, network monitoring, backup monitoring, application monitoring, patch management, automated maintenance, performance reporting, endpoint security esm. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
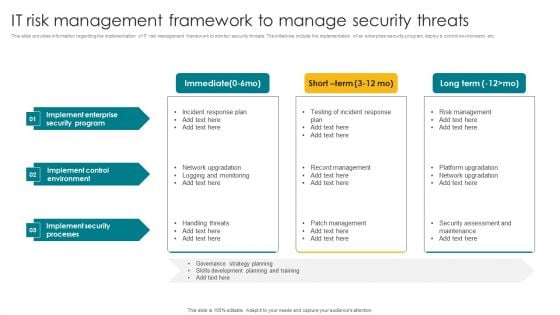
IT Risk Management Framework To Manage Security Threats Template PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. The IT Risk Management Framework To Manage Security Threats Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
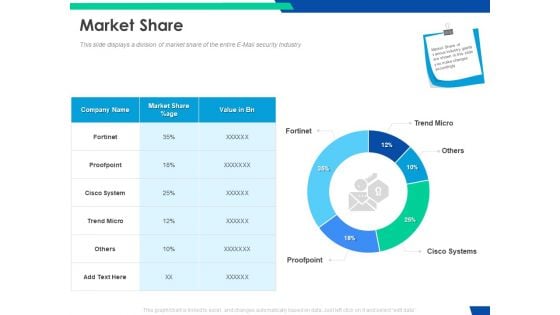
Cloud Based Email Security Market Report Market Share Ppt File Background PDF
This slide displays a division of market share of the entire E Mail security Industry. Deliver an awe inspiring pitch with this creative cloud based email security market report market share ppt file background pdf bundle. Topics like market share can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Artificiel Intelligence Components Template Data Ppt PowerPoint Presentation Outline Graphic Images
Presenting this set of slides with name artificiel intelligence components template data ppt powerpoint presentation outline graphic images. This is a three stage process. The stages in this process are technology, marketing, planning, business, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Classification Of Business Data With Restricted Sensitive And Public Ppt PowerPoint Presentation Infographics Icon PDF
Presenting this set of slides with name classification of business data with restricted sensitive and public ppt powerpoint presentation infographics icon pdf. This is a three stage process. The stages in this process are public, sensitive, restricted, levels. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Organizational Security Solutions Prerequisites For Effective Secops Implementation Summary PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a organizational security solutions prerequisites for effective secops implementation summary pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cyber Security Technology Trends Ppt PowerPoint Presentation Model Graphics Download Cpb
Presenting this set of slides with name cyber security technology trends ppt powerpoint presentation model graphics download cpb. This is an editable Powerpoint four stages graphic that deals with topics like cyber security technology trends to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
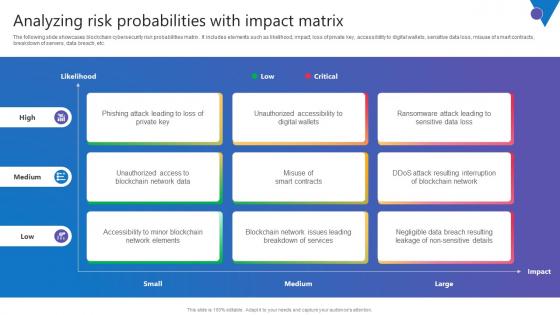
Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf
The following slide showcases blockchain cybersecurity risk probabilities matrix . It includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc. Presenting this PowerPoint presentation, titled Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide showcases blockchain cybersecurity risk probabilities matrix . It includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc.
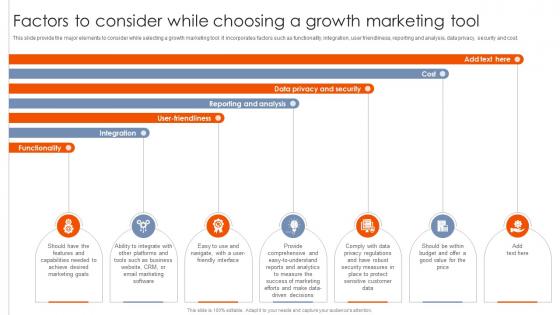
Best Practices For Using Growth Factors To Consider While Choosing A Growth MKT SS V
This slide provide the major elements to consider while selecting a growth marketing tool. It incorporates factors such as functionality, integration, user friendliness, reporting and analysis, data privacy, security and cost. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices For Using Growth Factors To Consider While Choosing A Growth MKT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices For Using Growth Factors To Consider While Choosing A Growth MKT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide provide the major elements to consider while selecting a growth marketing tool. It incorporates factors such as functionality, integration, user friendliness, reporting and analysis, data privacy, security and cost.
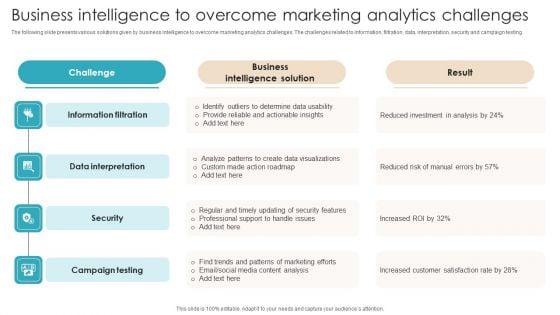
Business Intelligence To Overcome Marketing Analytics Challenges Mockup PDF
The following slide presents various solutions given by business intelligence to overcome marketing analytics challenges. The challenges related to information, filtration, data, interpretation, security and campaign testing. Presenting Business Intelligence To Overcome Marketing Analytics Challenges Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Information Filtration, Data Interpretation, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
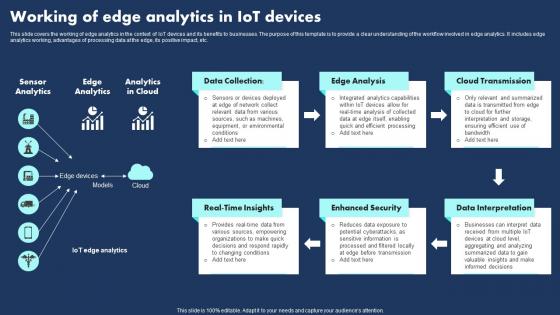
Working Of Edge Analytics In Iot Devices Themes Pdf
This slide covers the working of edge analytics in the context of IoT devices and its benefits to businesses. The purpose of this template is to provide a clear understanding of the workflow involved in edge analytics. It includes edge analytics working, advantages of processing data at the edge, its positive impact, etc.Showcasing this set of slides titled Working Of Edge Analytics In Iot Devices Themes Pdf The topics addressed in these templates are Enhanced Security, Data Interpretation, Cloud Transmission All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide covers the working of edge analytics in the context of IoT devices and its benefits to businesses. The purpose of this template is to provide a clear understanding of the workflow involved in edge analytics. It includes edge analytics working, advantages of processing data at the edge, its positive impact, etc.
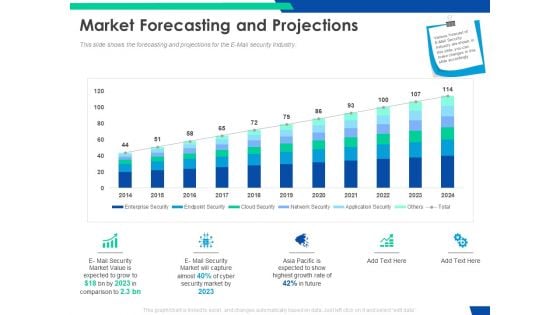
Cloud Based Email Security Market Report Market Forecasting And Projections Ppt Infographics Themes PDF
This slide shows the forecasting and projections for the E Mail security Industry. Deliver and pitch your topic in the best possible manner with this cloud based email security market report market forecasting and projections ppt infographics themes pdf. Use them to share invaluable insights on market forecasting and projections and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Business Analysis Ability Mapping Model With Techniques Sample Pdf
This slide shows the techniques for mapping business analysis competencies. The purpose of this slides to enhance usability and scalability .It includes various methods of business task under cyber security , data analytics, scrum,etc. Showcasing this set of slides titled Business Analysis Ability Mapping Model With Techniques Sample Pdf The topics addressed in these templates are Business Competency, Proficiency Scale, Specialized Areas All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows the techniques for mapping business analysis competencies. The purpose of this slides to enhance usability and scalability .It includes various methods of business task under cyber security , data analytics, scrum,etc.
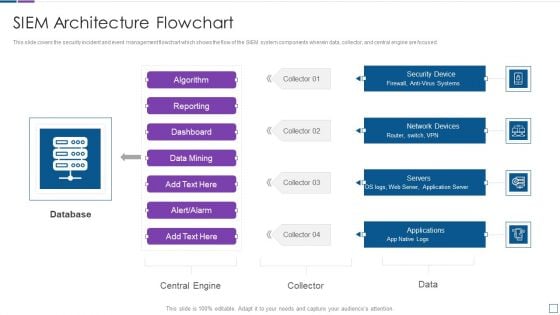
Real Time Assessment Of Security Threats SIEM Architecture Flowchart Sample PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Deliver an awe inspiring pitch with this creative real time assessment of security threats siem architecture flowchart sample pdf bundle. Topics like database, network devices, security device, servers, applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
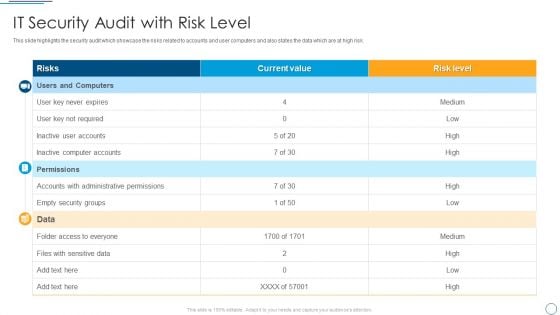
Digital Assessment To Analyze Social Media Brand Presence IT Security Audit With Risk Level Designs PDF
This slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk.Deliver an awe inspiring pitch with this creative Digital Assessment To Analyze Social Media Brand Presence IT Security Audit With Risk Level Designs PDF bundle. Topics like Administrative Permissions, Empty Security, Computer Accounts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Growing Cyber Security Issues Portrait PDF
Deliver and pitch your topic in the best possible manner with this growing cyber security issues portrait pdf. Use them to share invaluable insights on unprecedented attacks, cyber espionage, data theft and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Email Security Market Research Report Market Share Ppt Show Infographics PDF
Presenting this set of slides with name email security market research report market share ppt show infographics pdf. The topics discussed in these slides are company name, market share, value. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
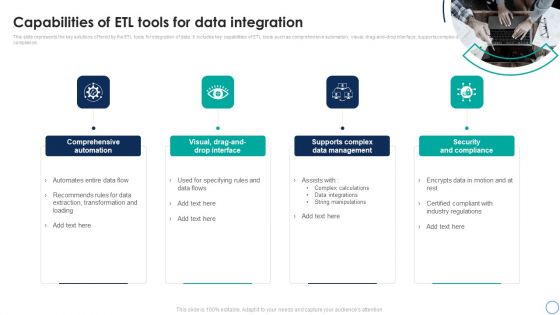
Business Analytics Application Capabilities Of ETL Tools For Data Integration Inspiration PDF
This slide represents the key solutions offered by the ETL tools for integration of data. It includes key capabilities of ETL tools such as comprehensive automation, visual, drag-and-drop interface, supports complex data management and security and compliance. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Business Analytics Application Capabilities Of ETL Tools For Data Integration Inspiration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Business Analytics Application Capabilities Of ETL Tools For Data Integration Inspiration PDF today and make your presentation stand out from the rest.


 Continue with Email
Continue with Email

 Home
Home


































